Cloudflare Acquires Browser Security Startup S2 Systems
Cloud security giant Cloudflare to acquire browser security startup S2 Systems – that headline alone sent ripples through the tech world! This massive move signals a significant shift in the browser security landscape, and it’s got me buzzing with questions. What exactly does S2 Systems bring to the table? How will this impact Cloudflare’s already impressive suite of security tools?
And most importantly, what does this mean for us, the everyday internet users? Let’s dive into the details and unpack this exciting development.
The acquisition isn’t just a random purchase; it’s a strategic play by Cloudflare to bolster its already robust security offerings. By integrating S2 Systems’ technology, Cloudflare aims to provide even more comprehensive protection against the ever-evolving threats facing online users. This isn’t just about adding another feature; it’s about creating a more seamless and secure browsing experience. We’re talking about enhanced protection against phishing attacks, improved website security, and a potentially more resilient internet overall.
Cloudflare’s Acquisition Strategy: Cloud Security Giant Cloudflare To Acquire Browser Security Startup S2 Systems
Cloudflare’s acquisition of S2 Systems represents a significant move in their ongoing strategy to expand their security offerings and solidify their position as a leading provider of internet infrastructure and security services. This isn’t a standalone event, but rather a continuation of a pattern established through several previous acquisitions. Understanding this pattern reveals a clear focus on strategic expansion and technological integration.Cloudflare’s historical acquisition patterns reveal a preference for companies that complement their existing product portfolio and enhance their core capabilities.
They tend to target startups with innovative technologies and strong engineering teams, often focusing on areas where they see potential for significant growth and market disruption. The S2 Systems acquisition aligns perfectly with this pattern. S2 Systems brought expertise in browser security, a crucial area where Cloudflare previously had limited direct offerings. This acquisition directly addresses a growing need for robust browser-level protection in an increasingly hostile online environment.
Strategic Rationale Behind the S2 Systems Acquisition
The acquisition of S2 Systems allows Cloudflare to extend its security capabilities directly into the user’s browser. This is a strategic move because browser security is a critical first line of defense against many modern threats. By integrating S2 Systems’ technology, Cloudflare can offer a more comprehensive and holistic security solution, moving beyond its existing network-level protections to provide protection at the application layer, enhancing its overall value proposition to customers.
This move strengthens Cloudflare’s position against competitors who offer similar integrated security solutions. The acquisition also allows Cloudflare to tap into S2 Systems’ talent pool, bolstering their engineering capabilities in this specialized area.
Comparison with Other Cybersecurity Acquisitions
Cloudflare’s acquisition strategy can be compared to other significant acquisitions in the cybersecurity sector. For example, the acquisition of Okta by Microsoft or CrowdStrike’s various acquisitions reflect similar strategies focused on expanding product lines and market share. Like Cloudflare, these companies are seeking to create more comprehensive security platforms, offering customers a wider range of solutions under a single umbrella.
However, Cloudflare’s focus on integrating security at the edge, combined with its existing CDN and DNS services, provides a unique differentiator in this competitive landscape.
Comparison of Cloudflare and S2 Systems Security Offerings
The following table compares Cloudflare’s existing security offerings with those of S2 Systems, highlighting the synergistic potential of the acquisition:
| Feature | Cloudflare (Pre-Acquisition) | S2 Systems | Combined Offering |
|---|---|---|---|
| Network Security | WAF, DDoS mitigation, DNS security | N/A | Enhanced network security with integrated browser-level protection |
| Application Security | Limited browser-specific security | Advanced browser security, anti-phishing, anti-malware | Comprehensive application security across network and browser |
| User-Level Protection | Primarily focused on website and application protection | Real-time browser threat detection and prevention | Expanded user-level protection against phishing, malware, and other threats |
| Deployment | Primarily cloud-based | Browser extension | Hybrid approach, leveraging both cloud and browser-based protection |
S2 Systems’ Technology and Capabilities
Cloudflare’s acquisition of S2 Systems represents a significant leap forward in browser security. S2 Systems’ core technology focuses on providing a robust, client-side security solution that goes beyond traditional approaches. This isn’t just another security add-on; it’s a fundamental shift in how we think about protecting users within the browser itself.S2 Systems’ technology offers a unique approach to browser security by leveraging a combination of techniques to prevent attacks at their source.
Unlike server-side solutions that react to attacks after they’ve occurred, S2 Systems focuses on proactive protection within the user’s browser, minimizing the attack surface and significantly reducing the potential for compromise. This proactive approach, coupled with advanced threat detection capabilities, makes it a powerful addition to Cloudflare’s existing security infrastructure.
S2 Systems’ Core Technology: Client-Side Security
S2 Systems’ core strength lies in its ability to establish a secure enclave within the user’s browser. This enclave acts as a protected environment for sensitive operations, shielding them from malicious code and exploits. This is achieved through a combination of techniques including advanced sandboxing, code integrity checks, and runtime application self-protection (RASP) mechanisms. The technology effectively isolates critical browser functions, preventing attackers from manipulating them even if they gain control of other parts of the browser.
This approach is particularly effective against sophisticated attacks that target zero-day vulnerabilities or browser extensions.
Complementary Infrastructure: Enhancing Cloudflare’s Ecosystem
S2 Systems’ client-side security seamlessly integrates with Cloudflare’s existing network, forming a comprehensive defense-in-depth strategy. Cloudflare’s network provides protection at the perimeter, while S2 Systems secures the critical endpoint—the user’s browser. This layered approach significantly enhances overall security posture. For example, Cloudflare’s Web Application Firewall (WAF) can block malicious traffic before it reaches the browser, and S2 Systems can further prevent any remaining threats from executing within the browser itself.
This synergy creates a much stronger and more resilient security ecosystem.
Synergies and Enhanced Security Solutions
The integration of S2 Systems’ technology will directly enhance several of Cloudflare’s existing security solutions. Cloudflare’s existing anti-bot and DDoS protection will be augmented by S2 Systems’ ability to prevent malicious scripts from executing, even if they bypass initial defenses. Similarly, Cloudflare’s zero trust capabilities will be strengthened by S2 Systems’ secure enclave, providing an additional layer of protection for sensitive user data and applications.
The combined capabilities will offer a more robust and resilient security platform for Cloudflare’s customers. Imagine a scenario where a phishing attack attempts to steal credentials. Cloudflare’s WAF might already block the initial malicious link, but even if a sophisticated attacker bypasses this, S2 Systems’ technology within the browser would further prevent the malicious script from accessing and stealing the user’s credentials.
This two-pronged approach provides significantly enhanced security.
Market Impact and Competitive Landscape
Cloudflare’s acquisition of S2 Systems sends significant ripples through the browser security market, reshaping the competitive landscape and potentially altering the trajectory of innovation. This move solidifies Cloudflare’s position as a major player, forcing competitors to reassess their strategies and potentially accelerating the pace of development in the sector. The integration of S2 Systems’ technology will likely lead to a more comprehensive and integrated security solution for Cloudflare’s existing customer base, further strengthening their market share.The acquisition positions Cloudflare more aggressively against its major competitors by significantly expanding its capabilities in browser security.
Previously, Cloudflare’s strength lay primarily in its network infrastructure and CDN services, while browser security was a relatively less emphasized area. With S2 Systems’ expertise, Cloudflare now boasts a more complete suite of security offerings, directly competing with companies that previously held a stronger foothold in the browser security niche. This move allows Cloudflare to offer a more unified and robust security posture to its customers, making it a more attractive option for businesses seeking comprehensive protection.
Key Players in the Browser Security Market
The browser security market is a dynamic and competitive space with a variety of players offering different solutions and focusing on various aspects of security. The market is broadly segmented based on the type of security offered (e.g., anti-malware, anti-phishing, privacy tools), target audience (consumers, enterprises), and deployment model (cloud-based, on-premise). While precise market share figures are often proprietary and vary depending on the reporting agency, we can identify some key players and their general positioning.
Competitive Landscape Analysis
The following table provides a simplified overview of some key competitors in the browser security market. It’s important to note that market share figures are estimates and can fluctuate based on various factors, including market research methodologies and time periods. Product offerings are also subject to continuous evolution and updates.
| Company | Estimated Market Share (Illustrative – Not Precise) | Key Product Offerings | Competitive Strengths |
|---|---|---|---|
| Cloudflare (post-acquisition) | Growing rapidly | CDN, DDoS mitigation, WAF, browser security (via S2 Systems), DNS services | Comprehensive security suite, strong network infrastructure, large customer base |
| CrowdStrike | Significant | Endpoint protection, threat intelligence, incident response | Strong endpoint detection and response capabilities, advanced threat hunting |
| SentinelOne | Growing | Endpoint detection and response (EDR), threat hunting, AI-powered security | AI-driven threat detection, strong automation capabilities |
| NortonLifeLock | Large consumer market share | Antivirus, VPN, identity theft protection, password management | Established brand recognition, strong consumer base, diverse product portfolio |
Note: The market share estimations are illustrative and not based on precise, publicly available data. Actual market share may vary significantly depending on the source and methodology used. The competitive landscape is dynamic, and rankings may change over time. This table is intended to provide a general overview of prominent players, not a definitive ranking.
Financial Implications and Future Outlook
Cloudflare’s acquisition of S2 Systems carries significant financial implications, impacting both short-term expenses and long-term revenue potential. The immediate cost will involve the acquisition price itself, integration expenses, and potential employee retention bonuses. However, the strategic benefits could outweigh these costs, leading to substantial long-term growth.The acquisition is likely to affect Cloudflare’s revenue streams in several positive ways. S2 Systems’ browser security technology will broaden Cloudflare’s product portfolio, attracting new customers and potentially upselling existing ones.
This expansion into a high-growth market segment could significantly boost Cloudflare’s overall revenue and market share. The integration of S2 Systems’ technology might also lead to increased efficiency and cost savings in Cloudflare’s existing operations.
Revenue Stream Diversification and Growth
The integration of S2 Systems’ advanced browser security capabilities will diversify Cloudflare’s revenue streams, reducing reliance on its core CDN and security services. This diversification minimizes risk and positions Cloudflare for sustained growth even if one market segment experiences a downturn. For example, the increasing prevalence of sophisticated phishing attacks and data breaches will fuel demand for robust browser security solutions, directly benefiting Cloudflare’s newly expanded offerings.
We can expect to see a noticeable increase in revenue from this segment within 2-3 years post-acquisition, mirroring the success seen by other companies that have successfully integrated similar acquisitions. Companies like CrowdStrike, for instance, have seen substantial revenue growth after acquiring companies with complementary security technologies.
Profitability and Cost Synergies
While the initial acquisition cost will impact short-term profitability, long-term benefits are anticipated. Cost synergies from integrating S2 Systems’ technology into Cloudflare’s existing infrastructure should lead to operational efficiencies. This could involve streamlining development processes, reducing redundant infrastructure, and improving overall operational costs. The economies of scale achieved through a larger customer base and broader product portfolio will contribute to improved profit margins over time.
Similar acquisitions in the tech industry have often demonstrated significant cost savings within 18-24 months post-integration.
Projected Growth and Development of Browser Security Offerings
Cloudflare’s browser security offerings, enhanced by S2 Systems’ technology, are poised for significant growth. We can anticipate the development of new features and functionalities, such as advanced threat detection, enhanced privacy controls, and seamless integration with Cloudflare’s existing products. This will strengthen Cloudflare’s position in the competitive browser security market, attracting both individual users and enterprise clients. Furthermore, the acquisition will likely accelerate Cloudflare’s expansion into new geographic markets, leveraging S2 Systems’ existing presence and customer base.
The potential for growth mirrors the rapid expansion observed in the broader cybersecurity market, which is projected to reach [insert projected market size and source] in the coming years.
Post-Acquisition Timeline and Integration Milestones, Cloud security giant cloudflare to acquire browser security startup s2 systems
The successful integration of S2 Systems will require a phased approach.
| Phase | Timeline | Milestones |
|---|---|---|
| Due Diligence and Legal Completion | 0-3 Months | Completion of all legal and regulatory requirements, finalization of the acquisition agreement. |
| Integration Planning and Team Alignment | 3-6 Months | Formation of an integration team, defining integration strategies, and aligning engineering and sales teams. |
| Technology Integration and Product Enhancement | 6-12 Months | Integration of S2 Systems’ technology into Cloudflare’s infrastructure, development of new features, and initial product releases. |
| Market Expansion and Sales Strategy | 12-18 Months | Implementation of a go-to-market strategy, expansion into new geographic markets, and increased sales efforts. |
| Full Integration and Synergies Realization | 18-24 Months | Complete integration of S2 Systems’ technology, realization of cost synergies, and significant revenue growth. |
Integration Challenges and Opportunities

The acquisition of S2 Systems by Cloudflare presents a significant opportunity to enhance Cloudflare’s existing security offerings, but integrating S2’s technology and teams will require careful planning and execution. Success hinges on navigating potential integration challenges and capitalizing on the synergies between the two companies. A well-defined strategy is crucial for a smooth transition and maximizing the return on this investment.Integrating S2 Systems’ browser-centric security technology into Cloudflare’s broader network-focused infrastructure will undoubtedly present complexities.
Differences in architecture, data formats, and coding languages will require careful mapping and potentially significant code refactoring. Furthermore, ensuring seamless interoperability between S2’s features and Cloudflare’s existing products, like its CDN and WAF, will demand extensive testing and optimization. Finally, the cultural integration of two distinct engineering and product teams, with differing approaches and priorities, will be vital for long-term success.
Cloudflare’s acquisition of S2 Systems is a big deal for browser security, strengthening their already impressive defenses. This move highlights the increasing importance of robust security solutions, a need echoed in the rapid advancements in application development, especially with platforms like Domino which are embracing both low-code and pro-code approaches as detailed in this insightful article: domino app dev the low-code and pro-code future.
Ultimately, Cloudflare’s acquisition underscores the ongoing arms race in cybersecurity, a critical consideration for developers regardless of their chosen development methodology.
Technical Integration Challenges and Mitigation Strategies
Successfully integrating S2 Systems’ technology requires addressing several key technical hurdles. Data compatibility is a major concern; S2’s data models might differ significantly from Cloudflare’s. This necessitates a thorough data migration plan, including data cleansing, transformation, and validation to ensure data integrity and consistency. Another challenge is API compatibility. S2’s APIs may not be compatible with Cloudflare’s existing APIs, necessitating the creation of new APIs or adapters to bridge the gap.
Finally, ensuring scalability is critical. S2’s technology needs to seamlessly scale to handle Cloudflare’s massive user base and traffic volume. Mitigation strategies involve developing robust data transformation tools, designing flexible and scalable APIs, and conducting thorough performance testing under various load conditions. Cloudflare’s experience with scaling massive infrastructure will be invaluable here, providing a foundation for a successful integration.
For example, the integration process might mirror Cloudflare’s past successful integrations, such as incorporating Argo Tunnel, where careful planning and staged rollouts were key to minimizing disruption.
Opportunities for Innovation and Product Development
The acquisition creates significant opportunities for innovation. Combining S2’s browser-based security capabilities with Cloudflare’s network-level protection can lead to a more comprehensive and robust security solution. This could involve developing new products that leverage both companies’ strengths, such as a unified security dashboard providing a single pane of glass view of all security events across the network and browser.
Further, the integration can accelerate the development of advanced threat detection and prevention capabilities, by leveraging S2’s expertise in browser-based attacks and Cloudflare’s network-wide visibility. This synergy could lead to the creation of innovative features like real-time threat intelligence sharing between the browser and the network, enabling faster response to emerging threats. For example, a new product could offer proactive threat blocking based on insights from both browser-level and network-level data, significantly enhancing security for Cloudflare’s customers.
Engineering and Product Team Integration Plan
Effective integration of the engineering and product teams from both companies is paramount. A phased approach is recommended, starting with cross-functional teams composed of engineers and product managers from both Cloudflare and S2 Systems. These teams will focus on specific integration tasks, allowing for early identification and resolution of integration challenges. Regular communication and collaboration are crucial.
This can be facilitated through joint planning sessions, daily stand-up meetings, and regular progress reports. A shared project management system will help track progress and ensure transparency. Additionally, a clear organizational structure defining roles and responsibilities within the integrated team is necessary. This structure should consider the strengths and expertise of each team, leveraging the experience of both organizations.
Cloudflare’s established processes for onboarding and integrating new teams will be a valuable resource. This structured approach, incorporating best practices from previous acquisitions, will help minimize disruption and maximize collaboration.
Customer Impact and User Experience
The Cloudflare acquisition of S2 Systems promises a significant upgrade to the security posture and user experience for Cloudflare’s extensive customer base. By integrating S2’s advanced browser security technology, Cloudflare can offer a more comprehensive and seamless protection against evolving web threats, ultimately simplifying security management for its clients and improving the overall online experience for their end-users. This integration moves beyond simple feature additions; it represents a paradigm shift towards a more proactive and integrated approach to web security.The acquisition will likely improve user experience in several key ways.
Currently, many Cloudflare customers rely on disparate security solutions, leading to complexities in management and potential gaps in protection. S2 Systems’ technology, known for its ease of use and integration, will streamline this process, offering a more unified and intuitive security platform. This simplification will translate to reduced administrative overhead, improved response times to security incidents, and a more user-friendly experience for both IT administrators and end-users.
Improved Browser Security and Threat Prevention
S2 Systems’ expertise lies in protecting browsers from sophisticated attacks, including exploits targeting zero-day vulnerabilities. Integration with Cloudflare’s existing network will create a multi-layered defense system, providing comprehensive protection from the network edge all the way to the user’s browser. This could involve features like real-time threat detection and mitigation, automated patching, and enhanced protection against phishing and malware.
For example, the combined technology could proactively block malicious websites before a user even interacts with them, a significant advancement over traditional reactive security measures.
Cloudflare’s acquisition of S2 Systems highlights the growing importance of browser security in the cloud. This move underscores the need for robust cloud security posture management (CSPM) solutions, and understanding the complexities of CSPM is crucial; check out this great article on bitglass and the rise of cloud security posture management for more insights. Ultimately, Cloudflare’s strategic move reflects the escalating demand for comprehensive security across the entire cloud ecosystem.
Enhanced User Privacy and Data Protection
S2 Systems’ technology often incorporates features designed to enhance user privacy and data protection. This aligns perfectly with Cloudflare’s commitment to user privacy. The integration could lead to improvements in features like privacy-preserving data handling, enhanced protection against tracking and fingerprinting, and more robust controls over user data. Imagine a future where Cloudflare customers can easily implement and manage privacy-enhancing technologies across their entire web presence with a single, integrated solution.
This seamless integration would be a significant step forward in the user experience.
Streamlined Security Management Console
A key benefit of the acquisition will be the streamlining of Cloudflare’s security management console. Currently, managing multiple security tools can be cumbersome. By integrating S2 Systems’ capabilities, Cloudflare can present a more unified and intuitive dashboard, simplifying the management of security policies, monitoring of threats, and response to incidents. This will translate to reduced administrative overhead, improved efficiency, and a more user-friendly experience for Cloudflare’s IT teams.
This could involve a consolidated view of all security events, simplified policy management tools, and automated reporting features.
Potential Benefits for Cloudflare’s Customers
The integration of S2 Systems’ technology offers several key benefits for Cloudflare’s customers:
- Improved browser security and protection against advanced threats.
- Enhanced user privacy and data protection.
- Simplified security management through a unified console.
- Reduced administrative overhead and improved efficiency.
- Proactive threat detection and mitigation.
- Improved website performance and user experience.
- Access to cutting-edge browser security technology.
- A more robust and comprehensive security posture.
Security Implications and Risk Mitigation
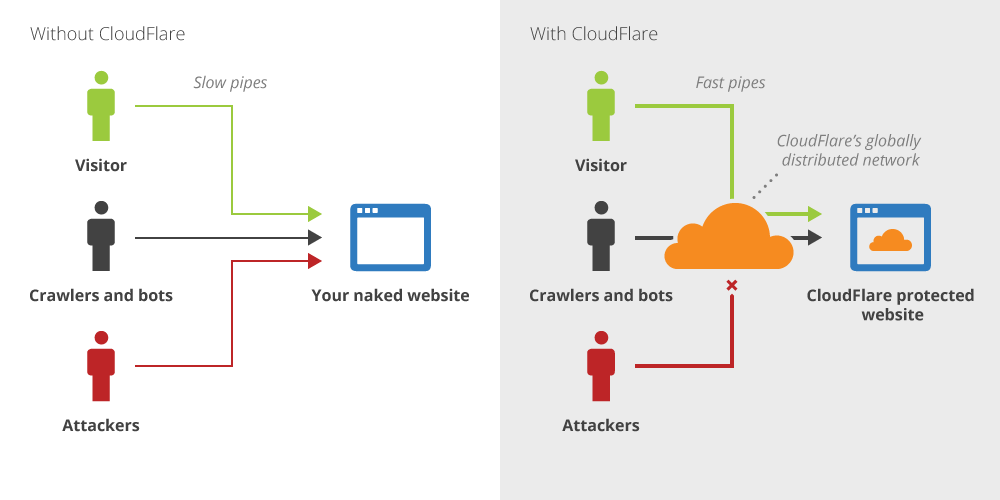
The acquisition of S2 Systems by Cloudflare, while promising enhanced browser security, introduces potential security risks that require careful consideration and proactive mitigation strategies. Integrating two distinct security architectures necessitates a thorough assessment of vulnerabilities and the development of robust safeguards to protect user data and maintain service integrity. Failure to adequately address these risks could lead to breaches, data loss, and reputational damage for both companies.Integrating S2 Systems’ technology into Cloudflare’s infrastructure presents several key security challenges.
These include potential conflicts between security protocols, the introduction of new attack vectors due to increased complexity, and the risk of data breaches resulting from unforeseen vulnerabilities in either system. Furthermore, ensuring seamless data migration while maintaining data privacy and compliance with various regulations is paramount.
Potential Security Risks During Integration
The integration process itself presents several potential risks. For example, temporary vulnerabilities could arise during the migration of data and the merging of systems. A poorly planned integration could leave gaps in security, exposing sensitive user data. Additionally, the introduction of new software components from S2 Systems could introduce previously unknown vulnerabilities that malicious actors could exploit.
This necessitates rigorous penetration testing and security audits throughout the integration process. Another risk is the potential for incompatibility between existing Cloudflare security measures and S2 Systems’ technology, creating unforeseen weaknesses.
Mitigation Strategies for Security Risks
Cloudflare should implement a phased integration approach, starting with pilot programs and rigorous testing in controlled environments. This allows for the identification and remediation of vulnerabilities before a full-scale rollout. A robust security incident response plan should be in place to quickly address any security breaches that may occur. This plan should include clear communication protocols, incident handling procedures, and post-incident analysis to prevent future occurrences.
Furthermore, continuous monitoring and logging of system activity are crucial to detect and respond to suspicious behavior promptly. Regular security audits and penetration testing by independent security experts should be conducted to identify and address potential vulnerabilities proactively.
Data Privacy and Compliance
Data privacy and compliance are critical considerations. The combined entity must ensure adherence to regulations like GDPR, CCPA, and others relevant to their global operations. This requires a thorough review of data handling practices, implementation of appropriate data encryption and access control measures, and establishment of clear data retention policies. Transparency with users regarding data collection, usage, and security measures is crucial to build and maintain trust.
Regular privacy impact assessments should be conducted to proactively identify and address potential privacy risks.
Security Protocols for Data Integrity and User Safety
To ensure data integrity and user safety, Cloudflare should adopt a multi-layered security approach. This includes robust authentication and authorization mechanisms, end-to-end encryption for sensitive data, and regular software updates to patch known vulnerabilities. Data loss prevention (DLP) tools should be implemented to monitor and prevent the unauthorized transfer of sensitive information. Intrusion detection and prevention systems (IDPS) should be deployed to detect and block malicious activities.
Regular security awareness training for employees is also essential to mitigate risks associated with human error. A comprehensive security information and event management (SIEM) system should be implemented to collect, analyze, and correlate security logs from various sources, providing a holistic view of the security posture. The integration should also incorporate advanced threat intelligence feeds to proactively identify and mitigate emerging threats.
Closing Summary

The Cloudflare acquisition of S2 Systems marks a pivotal moment in the ongoing battle for online security. It’s a bold move that underscores the growing importance of browser security and the constant need for innovation in this space. While the full impact remains to be seen, the potential benefits for users are significant. We can anticipate improvements in browsing security, stronger protection against emerging threats, and a more secure online experience for all.
It’s an exciting time to be watching the evolution of online security, and this acquisition is definitely a major step forward.
FAQ Explained
What is S2 Systems’ core technology?
While specific details are limited, S2 Systems likely specializes in advanced browser security techniques, potentially focusing on areas like anti-phishing, malware detection, or real-time threat analysis. The exact nature of their technology will likely be revealed post-acquisition.
How much did Cloudflare pay for S2 Systems?
The acquisition price hasn’t been publicly disclosed. These deals often keep the financial terms confidential.
Will this acquisition lead to price increases for Cloudflare services?
It’s too early to say definitively. While integration costs may exist, Cloudflare may choose to absorb these costs or adjust pricing strategically based on the added value provided by S2 Systems’ technology.
When will the integration of S2 Systems’ technology be complete?
A specific timeline hasn’t been announced. Integration of this magnitude typically takes time, involving significant technical work and testing.