CloudPassage Offers Halo Cloud Secure for Public Cloud Security
CloudPassage offers Halo Cloud Secure for security of public cloud infrastructure – a game-changer in the world of cloud security. This isn’t just another security tool; it’s a comprehensive solution designed to protect your valuable data and applications from the ever-evolving landscape of cyber threats. We’ll dive into the features, benefits, and real-world applications of Halo Cloud Secure, exploring how it helps organizations navigate the complexities of securing their public cloud environments.
Get ready to learn how this platform can bolster your security posture and give you peace of mind in the cloud.
Halo Cloud Secure offers a robust suite of features, including vulnerability management, intrusion detection and prevention, and compliance support for standards like PCI DSS and HIPAA. Its seamless integration with major cloud providers like AWS, Azure, and GCP makes deployment and management straightforward. But the real power lies in its ability to adapt to your growing infrastructure needs, scaling seamlessly as your cloud footprint expands.
We’ll explore real-world examples of how businesses have leveraged Halo Cloud Secure to prevent breaches, respond to zero-day exploits, and maintain compliance, ultimately reducing risk and improving their overall security posture.
CloudPassage Halo Cloud Secure
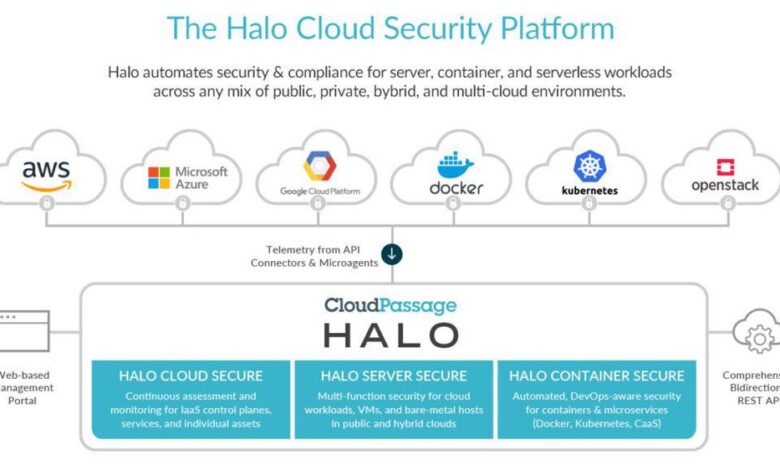
CloudPassage Halo Cloud Secure is a comprehensive cloud workload protection platform (CWPP) designed to enhance the security posture of public cloud environments. It offers a unified approach to securing virtual machines, containers, and serverless functions, providing visibility and control across your entire cloud infrastructure. Unlike many point solutions, Halo consolidates multiple security functions into a single agent, simplifying management and reducing complexity.Halo Cloud Secure protects public cloud infrastructure by continuously monitoring and analyzing workloads for malicious activity and vulnerabilities.
It leverages a combination of techniques, including runtime application self-protection (RASP), vulnerability assessment, and threat detection, to identify and respond to threats in real-time. This proactive approach helps organizations prevent breaches and minimize the impact of successful attacks.
Halo Cloud Secure Core Features
Halo Cloud Secure’s core functionality revolves around providing comprehensive visibility and control over cloud workloads. This includes features like continuous vulnerability assessment, identifying known and unknown vulnerabilities within applications and operating systems. It also provides real-time threat detection, analyzing system calls and network traffic for suspicious behavior, alerting administrators to potential threats. Furthermore, its runtime application self-protection (RASP) capabilities actively monitor application behavior and block malicious actions before they can compromise the system.
Finally, the platform offers detailed compliance reporting, assisting organizations in meeting industry regulations.
Halo Cloud Secure Deployment Models
Halo Cloud Secure supports multiple deployment models to cater to various organizational needs and infrastructure setups. The platform can be deployed as a cloud-based SaaS solution, managed by CloudPassage, offering a simple and scalable approach. Alternatively, organizations can opt for a self-managed deployment, providing greater control over the platform’s configuration and infrastructure. This flexibility allows businesses to choose the model that best aligns with their security and operational requirements.
For example, a small startup might find the SaaS model more appealing due to its ease of use and reduced operational overhead, whereas a large enterprise with stringent security requirements might prefer a self-managed deployment.
Halo Cloud Secure Compared to Other Solutions
Compared to other CWPP solutions, Halo Cloud Secure distinguishes itself through its unified agent architecture, providing comprehensive protection without the need for multiple agents or point solutions. This simplifies management and reduces the overhead associated with managing multiple security tools. While other solutions may focus primarily on vulnerability scanning or intrusion detection, Halo Cloud Secure integrates these functionalities with RASP, providing a more holistic and proactive approach to security.
This integrated approach often results in a lower total cost of ownership (TCO) compared to managing a suite of disparate security products. For example, unlike some competitors who require separate agents for vulnerability scanning and intrusion detection, Halo manages both functions from a single agent, reducing deployment complexity and operational overhead.
Security Capabilities of Halo Cloud Secure
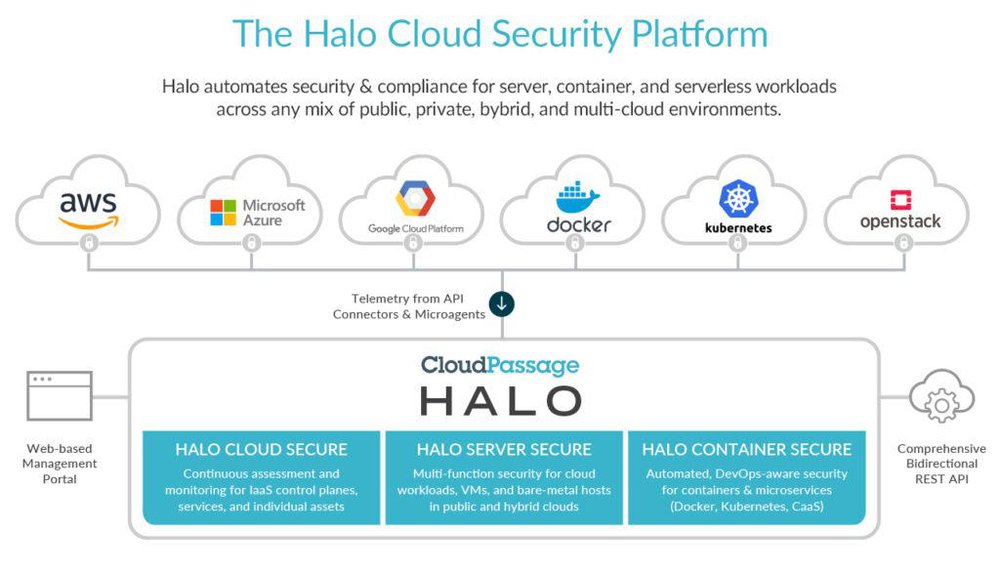
CloudPassage Halo Cloud Secure offers a robust suite of security capabilities designed to protect your public cloud infrastructure from a wide range of threats. It goes beyond basic security monitoring, providing proactive threat detection and response mechanisms crucial for maintaining compliance and minimizing risk. Its layered approach ensures comprehensive protection across your cloud environment.Halo Cloud Secure’s core strength lies in its ability to continuously assess and manage vulnerabilities, detect intrusions, and enforce security policies, all while minimizing operational overhead.
CloudPassage’s Halo Cloud Secure is a powerful tool for securing your public cloud infrastructure, offering comprehensive protection against various threats. Understanding the broader landscape of cloud security is crucial, and that’s where resources like this article on bitglass and the rise of cloud security posture management become invaluable. Ultimately, solutions like Halo Cloud Secure are essential components of a robust cloud security strategy, ensuring your data remains safe and compliant.
This integrated approach simplifies security management, allowing teams to focus on strategic initiatives rather than reactive troubleshooting.
Vulnerability Management Capabilities
Halo Cloud Secure actively scans your cloud infrastructure for known vulnerabilities, using a constantly updated database of known exploits and weaknesses. This proactive approach allows for the rapid identification and remediation of security gaps before they can be exploited by attackers. The system provides detailed reports on identified vulnerabilities, including their severity, location, and recommended remediation steps. This detailed information facilitates prioritization and efficient patching, reducing your overall attack surface.
For example, if a critical vulnerability is found in a specific instance, Halo Cloud Secure will immediately alert the administrator, providing specific instructions and contextual information to facilitate the patching process. This contrasts with reactive approaches that only identify vulnerabilities after an attack has occurred.
Intrusion Detection and Prevention Mechanisms
Halo Cloud Secure employs advanced intrusion detection and prevention (IDP) techniques to monitor network traffic and system activity for malicious behavior. This includes real-time analysis of logs, system calls, and network connections to detect anomalies indicative of an intrusion attempt. The system utilizes machine learning algorithms to identify patterns and behaviors that might indicate malicious activity, even if they don’t match known attack signatures.
If a suspicious event is detected, Halo Cloud Secure can automatically take action, such as blocking malicious traffic or isolating compromised instances. This proactive approach minimizes the impact of successful attacks and helps to contain breaches quickly. For instance, if an unusual amount of outbound traffic is detected from a specific instance, Halo Cloud Secure can trigger an alert and automatically initiate an investigation.
Threat Mitigation Capabilities
Halo Cloud Secure is designed to mitigate a wide range of threats targeting public cloud environments. This includes threats such as malware infections, data breaches, denial-of-service attacks, and unauthorized access. The platform addresses both known and unknown threats by combining signature-based detection with anomaly detection and behavioral analysis. Its comprehensive approach addresses the entire attack lifecycle, from initial reconnaissance to post-exploitation activities.
For example, the system can detect and block attempts to exploit known vulnerabilities, such as those in web servers or databases, even before they are publicly disclosed.
Compliance Requirements Handling, Cloudpassage offers halo cloud secure for security of public cloud infrastructure
Halo Cloud Secure assists organizations in meeting various compliance requirements, such as PCI DSS and HIPAA. The platform provides comprehensive audit trails, detailed reporting, and automated security controls that demonstrate adherence to regulatory standards. For example, the system can help organizations meet PCI DSS requirements by providing detailed logs of all access attempts to sensitive data, ensuring compliance with access control and audit logging requirements.
Similarly, it can assist with HIPAA compliance by monitoring access to protected health information (PHI) and ensuring that appropriate security measures are in place to prevent unauthorized access or disclosure. The platform’s detailed reporting capabilities make it easy to demonstrate compliance to auditors.
Integration and Management of Halo Cloud Secure
Integrating CloudPassage Halo Cloud Secure into your existing cloud infrastructure is a crucial step towards robust security. This process varies slightly depending on your cloud provider (AWS, Azure, or GCP), but the core principles remain consistent. The platform’s intuitive management console allows for streamlined policy configuration and insightful reporting, providing a centralized view of your security posture across multiple cloud environments.
Halo Cloud Secure leverages agentless technology, minimizing the impact on your cloud workloads. This means you don’t need to install additional software on each server or instance, simplifying the integration process considerably. The platform connects directly to your cloud provider’s APIs, allowing for continuous monitoring and assessment of your resources.
Integration with Cloud Providers
CloudPassage Halo Cloud Secure integrates seamlessly with AWS, Azure, and GCP through their respective APIs. The integration process typically involves providing Halo Cloud Secure with appropriate credentials and authorizing it to access your cloud resources. This grants the platform visibility into your virtual machines, storage, and networking configurations. Detailed documentation and support are available from CloudPassage for each provider, guiding you through the specific steps involved.
For example, with AWS, you might grant access using IAM roles, while Azure utilizes service principals. GCP integration typically involves creating a service account with the necessary permissions. Once connected, Halo Cloud Secure automatically discovers and begins monitoring your assets.
Halo Cloud Secure User Interface and Management Console
The Halo Cloud Secure management console provides a user-friendly interface for managing your cloud security posture. The dashboard presents a high-level overview of your security status, highlighting any critical vulnerabilities or compliance issues. From the console, you can navigate to detailed views of individual assets, review security events, and manage policies. The interface is designed to be intuitive, with clear navigation and comprehensive documentation available.
Key features are easily accessible, allowing for efficient monitoring and response to security threats. Think of it as a single pane of glass providing complete visibility into your cloud security.
Configuring Basic Security Policies
Setting up basic security policies in Halo Cloud Secure is a straightforward process. Here’s a step-by-step guide:
- Access the Policies Section: Navigate to the policies section within the management console.
- Create a New Policy: Click on the “Create Policy” button. You’ll be prompted to provide a name and description for your policy.
- Define Rules: This is where you specify the security rules. For example, you might create a rule to alert you if a server is found to be missing critical security patches or if unauthorized access attempts are detected. Halo Cloud Secure offers a variety of pre-built templates to simplify this process. You can select a template or create a custom rule set based on your specific needs.
- Assign the Policy: Once defined, assign the policy to the specific resources or groups of resources you want to protect. This could be specific virtual machines, subnets, or entire cloud accounts.
- Activate the Policy: Finally, activate the policy to begin monitoring and enforcing the defined rules. You will receive alerts based on the defined criteria.
Generating and Interpreting Security Reports
Halo Cloud Secure offers comprehensive reporting capabilities. You can generate reports on various aspects of your security posture, including vulnerability assessments, compliance checks, and security events. These reports can be customized to include specific timeframes and filters, allowing you to focus on relevant information. The reports typically include clear visualizations, such as charts and graphs, making it easy to identify trends and potential issues.
For instance, a report might show the number of vulnerabilities discovered over time, categorized by severity level, helping you prioritize remediation efforts. Understanding these reports allows you to effectively manage your cloud security risks and ensure compliance with industry standards and regulations.
Cost and Scalability of Halo Cloud Secure
Understanding the cost and scalability of CloudPassage Halo Cloud Secure is crucial for organizations looking to secure their cloud infrastructure. The pricing model isn’t a one-size-fits-all solution, and the overall cost depends heavily on the size and complexity of your environment, as well as the specific features you utilize. Scalability is equally important, ensuring the platform can adapt to your growing needs without significant performance degradation or cost overruns.
Pricing Models Offered by CloudPassage
CloudPassage typically offers a subscription-based pricing model. The exact cost is determined by several factors including the number of instances protected, the features activated, and the overall support level required. While specific pricing details aren’t publicly available without a direct engagement with a CloudPassage sales representative, it’s generally structured around a per-instance or per-node pricing scheme, meaning you pay for the resources actively monitored and protected by Halo Cloud Secure.
This allows for granular control and cost management, paying only for what you use. Higher tiers of service may include enhanced features like advanced threat detection, prioritized support, and access to more advanced analytics.
Cost Analysis Model for Implementing Halo Cloud Secure
To illustrate a cost analysis, let’s consider three hypothetical scenarios. Scenario A represents a small startup with 50 cloud instances. Scenario B is a mid-sized company with 500 instances, and Scenario C is a large enterprise with 5000 instances. In each scenario, we’ll assume a basic subscription level. While exact pricing isn’t publicly available, a simplified model might look like this: Scenario A could potentially cost a few hundred dollars per month, Scenario B several thousand, and Scenario C tens of thousands.
These are rough estimates and the actual costs would depend on the specific features and support level selected. A detailed cost analysis would involve working directly with CloudPassage to assess your specific needs and receive a tailored quote. This includes considering factors like the number of users, the level of support required, and any add-on services needed.
Scalability of Halo Cloud Secure
Halo Cloud Secure is designed for scalability. As your cloud infrastructure expands, the platform should be able to handle the increasing workload without requiring significant manual intervention. The platform’s architecture allows for efficient scaling both horizontally (adding more agents to monitor additional instances) and vertically (upgrading to higher tiers of service to handle increased data processing demands). This scalability is essential for businesses experiencing rapid growth or frequent changes in their cloud environments.
For example, a company rapidly expanding its e-commerce operations during peak seasons could seamlessly scale Halo Cloud Secure to accommodate the increased number of active servers and applications without experiencing performance bottlenecks.
Examples of Halo Cloud Secure Adapting to Changing Infrastructure Needs
A company migrating from an on-premises data center to a multi-cloud environment can easily integrate Halo Cloud Secure across various cloud providers. The platform’s agent-based architecture allows for seamless deployment and management across AWS, Azure, GCP, and other cloud platforms. Similarly, a company experiencing a sudden surge in traffic during a marketing campaign can rely on the platform’s scalability to continue monitoring and protecting its expanded infrastructure without performance degradation.
The platform adapts to changes in infrastructure by automatically scaling resources as needed, ensuring consistent security coverage regardless of the size or complexity of the cloud environment.
Case Studies and Real-World Applications
CloudPassage Halo Cloud Secure has proven its effectiveness across diverse industries, helping organizations significantly improve their cloud security posture. This section highlights several real-world examples showcasing Halo’s impact and the tangible benefits it delivers. We’ll explore specific use cases and quantify the improvements achieved through its implementation.
Halo Cloud Secure’s success stems from its comprehensive approach to cloud security, combining agentless monitoring, advanced threat detection, and automated remediation. This allows for rapid identification and mitigation of vulnerabilities, minimizing the risk of breaches and data loss. The platform’s adaptability allows it to seamlessly integrate into existing workflows, minimizing disruption and maximizing efficiency.
Financial Services Firm Improves Compliance and Reduces Risk
A major financial services firm implemented Halo Cloud Secure to enhance its compliance posture and mitigate risks associated with its cloud infrastructure. Prior to deployment, the organization struggled with manual security audits and lacked centralized visibility into its cloud environments. Halo Cloud Secure provided comprehensive visibility and automated reporting, streamlining compliance audits and significantly reducing the time spent on manual tasks.
The platform’s continuous monitoring capabilities also enabled the early detection and remediation of several critical vulnerabilities, preventing potential security breaches. This resulted in a substantial reduction in security incidents and improved overall operational efficiency.
Retail Company Enhances Data Protection and Prevents Breaches
A large retail company leveraged Halo Cloud Secure to bolster its data protection capabilities and prevent data breaches. The company’s cloud infrastructure was growing rapidly, making it difficult to maintain consistent security controls across all environments. Halo Cloud Secure’s agentless architecture enabled the company to quickly deploy the platform across its entire cloud footprint without impacting application performance.
The platform’s advanced threat detection capabilities identified and prevented several attempted breaches, protecting sensitive customer data and maintaining the company’s reputation. The automated remediation features also significantly reduced the time it took to respond to security incidents.
Healthcare Provider Improves HIPAA Compliance and Patient Data Security
A healthcare provider utilized Halo Cloud Secure to improve its HIPAA compliance and strengthen the security of its patient data. The organization needed a solution that could provide continuous monitoring and automated alerts for any potential security issues. Halo Cloud Secure’s real-time monitoring and automated reporting capabilities enabled the organization to quickly identify and address any potential HIPAA violations.
The platform’s robust security controls also helped to protect sensitive patient data from unauthorized access and breaches. This improved the organization’s compliance posture and enhanced the trust of its patients.
Impact of Halo Cloud Secure on Security Posture
| Organization | Before Implementation | After Implementation | Key Improvements |
|---|---|---|---|
| Financial Services Firm | Manual audits, limited visibility, high risk of breaches | Automated reporting, improved visibility, reduced security incidents | Streamlined compliance, reduced risk, improved operational efficiency |
| Retail Company | Inconsistent security controls, difficulty maintaining security across expanding cloud infrastructure, vulnerable to breaches | Comprehensive visibility, improved threat detection, automated remediation | Enhanced data protection, prevented breaches, improved response times |
| Healthcare Provider | Difficulty ensuring HIPAA compliance, vulnerable to data breaches | Improved HIPAA compliance, enhanced patient data security, reduced risk of violations | Strengthened security posture, improved patient trust, reduced regulatory risk |
Illustrative Scenarios
Let’s explore some real-world scenarios to demonstrate how CloudPassage Halo Cloud Secure protects your public cloud infrastructure. These examples highlight its proactive threat detection, rapid response capabilities, and overall contribution to a robust security posture.Halo Cloud Secure’s effectiveness stems from its multi-layered approach, combining runtime application self-protection (RASP), continuous vulnerability assessment, and detailed security information and event management (SIEM) integration.
This allows for a comprehensive view of your cloud environment and swift action against emerging threats.
Data Breach Prevention Scenario
Imagine a scenario where an attacker attempts to exploit a known vulnerability in a web application deployed on an Amazon EC2 instance. Halo Cloud Secure, constantly monitoring the application’s runtime behavior, detects suspicious activity. Specifically, it identifies attempts to access unauthorized database files. Before the attacker can exfiltrate any sensitive data, Halo Cloud Secure automatically triggers a response: it quarantines the compromised application instance, preventing further access and data leakage.
Simultaneously, it generates alerts, notifying security personnel of the incident and providing detailed logs for forensic analysis. This immediate response minimizes the impact of the attack, preventing a potential data breach.
Response to a Zero-Day Exploit
A zero-day exploit targeting a newly discovered vulnerability in a critical application running on a Google Cloud Platform (GCP) Compute Engine instance is discovered. Traditional signature-based security solutions would be ineffective. However, Halo Cloud Secure’s behavioral analysis capabilities detect anomalous activity within the application’s runtime environment, even without prior knowledge of the specific vulnerability. This anomalous behavior, such as unusual memory access patterns or system calls, triggers an alert.
Halo Cloud Secure isolates the affected instance, preventing further compromise and potential propagation to other parts of the infrastructure. The security team is immediately notified, allowing them to investigate the root cause, patch the vulnerability (if a patch is available), and restore the affected instance from a clean backup.
Detection and Response to Malicious Insider Activity
An employee with elevated privileges attempts to download sensitive customer data from an Azure virtual machine. Halo Cloud Secure’s user and entity behavior analytics (UEBA) capabilities identify this activity as deviating significantly from the employee’s normal access patterns. The system flags this as a potential insider threat, triggering an alert. The system also logs the specific files accessed, the time of access, and the user’s IP address.
This detailed information allows security personnel to investigate the incident, identify the cause of the malicious activity (e.g., compromised credentials, disgruntled employee), and take appropriate disciplinary and remediation actions. The data download attempt is blocked, preventing data loss.
Hypothetical System Architecture with Halo Cloud Secure Integration
This architecture involves several key components working together:
| Component | Description | Interaction with Halo Cloud Secure |
|---|---|---|
| Public Cloud Infrastructure (AWS, Azure, GCP) | Compute instances, storage, databases, networks. | Halo Cloud Secure agents deployed on each instance monitor runtime behavior and network traffic. |
| CloudPassage Halo Cloud Secure Agents | Lightweight agents deployed on each cloud instance. | Collect data, enforce security policies, and communicate with the Halo Cloud Secure management console. |
| Halo Cloud Secure Management Console | Centralized management interface. | Provides visibility into the security posture of the entire cloud environment, manages security policies, and receives alerts. |
| SIEM System (e.g., Splunk, QRadar) | Security Information and Event Management system. | Receives alerts from Halo Cloud Secure and integrates them into the overall security monitoring and incident response workflow. |
| Cloud Security Posture Management (CSPM) Tool | Assesses the security configuration of cloud resources. | Integrates with Halo Cloud Secure to provide a comprehensive view of security posture, combining runtime and configuration assessments. |
The Halo Cloud Secure agents continuously monitor the runtime behavior of applications and system processes on each cloud instance. Any suspicious activity is immediately flagged and reported to the management console, triggering alerts and enabling automated response actions such as isolation or quarantine. The integration with a SIEM system allows for centralized security monitoring and incident response, correlating data from various sources to provide a holistic view of security events.
The CSPM tool further strengthens the security posture by identifying and remediating misconfigurations. This integrated approach provides a comprehensive and robust security solution for public cloud environments.
CloudPassage’s Halo Cloud Secure is a lifesaver for securing your public cloud infrastructure, ensuring peace of mind in a complex digital landscape. But even with robust security, efficient app development is key, which is why I’ve been exploring the exciting advancements in domino app dev, the low-code and pro-code future , to streamline workflows. Ultimately, strong security like Halo Cloud Secure is essential, no matter how efficient your development process becomes.
Wrap-Up: Cloudpassage Offers Halo Cloud Secure For Security Of Public Cloud Infrastructure
In short, CloudPassage Halo Cloud Secure provides a powerful and adaptable solution for securing public cloud infrastructure. Its comprehensive features, seamless integration, and scalability make it an invaluable asset for organizations of all sizes. From preventing data breaches to ensuring compliance, Halo Cloud Secure empowers businesses to confidently embrace the benefits of the cloud while mitigating the inherent risks.
By understanding its capabilities and implementing it strategically, you can significantly strengthen your security posture and protect your most valuable assets in the ever-changing digital world.
FAQ Overview
What types of cloud environments does Halo Cloud Secure support?
Halo Cloud Secure supports major public cloud providers like AWS, Azure, and Google Cloud Platform (GCP).
Is Halo Cloud Secure easy to implement and manage?
Yes, Halo Cloud Secure boasts a user-friendly interface and integrates seamlessly with existing cloud workflows. The platform is designed for ease of use, even for those without extensive security expertise.
How does Halo Cloud Secure handle compliance requirements?
Halo Cloud Secure assists with compliance requirements by providing features that help organizations meet industry standards such as PCI DSS, HIPAA, and others. It offers reporting and auditing capabilities to demonstrate compliance.
What kind of customer support does CloudPassage offer?
CloudPassage offers various support options, ranging from self-service documentation to dedicated support engineers. The specific level of support depends on the chosen subscription plan.