CMMC vs DFARS vs NIST What Are the Differences?
Cmmc vs dfars vs nist what are the differences – CMMC vs DFARS vs NIST: What are the differences? This is a question plaguing many organizations, especially those working with government contracts. Navigating the complex world of cybersecurity compliance can feel like deciphering a secret code, but understanding the nuances between these three frameworks – the Cybersecurity Maturity Model Certification (CMMC), the Defense Federal Acquisition Regulation Supplement (DFARS), and the National Institute of Standards and Technology (NIST) frameworks – is crucial for success.
This post will break down each framework, comparing their goals, requirements, and applicability to help you determine which (or which combination) impacts your business.
We’ll explore the core differences in their maturity models, specific requirements, and the overall costs associated with achieving compliance. We’ll also delve into real-world examples, showing how these frameworks play out in practice for businesses of different sizes and sectors. By the end, you’ll have a clearer understanding of how these frameworks intersect and how you can strategically leverage them to bolster your organization’s cybersecurity posture and win government contracts.
Introduction

Navigating the complex world of cybersecurity compliance can feel like traversing a minefield, especially for organizations handling sensitive government data. Three major frameworks—CMMC, DFARS, and NIST—play crucial roles in defining and enforcing cybersecurity standards, but they differ significantly in their scope, implementation, and target audience. Understanding these differences is critical for any organization seeking to comply.This introduction provides a concise overview of each framework, highlighting their goals, intended audiences, and historical development.
We’ll examine the nuances that set them apart, helping to clarify the best approach for different organizations.
CMMC: Cybersecurity Maturity Model Certification
CMMC is a cybersecurity framework specifically designed for organizations that handle controlled unclassified information (CUI) on behalf of the Department of Defense (DoD). Its primary goal is to standardize and improve the cybersecurity posture of the DoD’s supply chain. The intended audience is businesses that contract with the DoD and handle CUI. CMMC evolved from the need for a more consistent and verifiable approach to cybersecurity compliance within the DoD supply chain, following concerns about data breaches and vulnerabilities.
Its development involved significant collaboration between the DoD and industry experts, resulting in a tiered maturity model reflecting increasing levels of cybersecurity capability. The framework includes specific practices and requirements organizations must meet to achieve certification at different maturity levels.
DFARS: Defense Federal Acquisition Regulation Supplement
DFARS is a supplement to the Federal Acquisition Regulation (FAR), specifically addressing the acquisition of goods and services by the DoD. Its primary goal is to ensure the protection of sensitive information throughout the acquisition lifecycle. The intended audience is far broader than CMMC, encompassing all contractors and subcontractors working with the DoD, regardless of whether they handle CUI.
DFARS’s cybersecurity requirements are less prescriptive than CMMC, often relying on NIST standards as a baseline. DFARS has evolved over time, reflecting the ever-changing landscape of cybersecurity threats and the increasing reliance on digital systems within the DoD. Amendments and updates to DFARS reflect the government’s ongoing efforts to strengthen its cybersecurity posture and that of its contractors.
NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) is a voluntary framework developed by the National Institute of Standards and Technology. Its primary goal is to provide a flexible and adaptable approach to managing cybersecurity risk. The intended audience is incredibly broad, encompassing organizations of all sizes and sectors, both public and private. NIST CSF is not a prescriptive standard but rather a framework that helps organizations identify, assess, and mitigate cybersecurity risks based on their specific needs and circumstances.
Its development began in response to the growing need for a comprehensive and adaptable cybersecurity framework that could be adopted by a wide range of organizations. The framework’s flexibility and adaptability have contributed to its widespread adoption and influence across various industries.
Maturity Levels and Requirements
Understanding the differences between CMMC, DFARS, and NIST cybersecurity frameworks requires a close look at their maturity models and the specific requirements they impose at different levels. While NIST provides a foundational framework, CMMC and DFARS build upon it, creating a tiered approach to cybersecurity compliance, each with its own specific demands. This analysis will clarify the nuances of each framework’s requirements across maturity levels.
CMMC Maturity Levels and Requirements
The Cybersecurity Maturity Model Certification (CMMC) framework uses a tiered system, ranging from Level 1 to Level 5, reflecting increasing levels of cybersecurity maturity. Lower levels focus on basic cybersecurity hygiene, while higher levels demand more sophisticated practices and controls. The specific requirements at each level are detailed in the CMMC model, and achieving certification requires demonstrating compliance through an independent assessment.
For example, Level 1 focuses on basic practices like access control, while Level 5 requires advanced capabilities such as incident response planning and advanced threat detection.
DFARS Cybersecurity Requirements
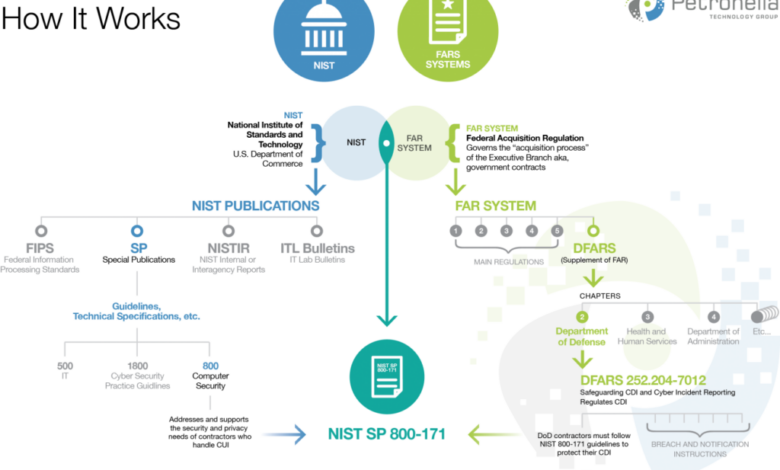
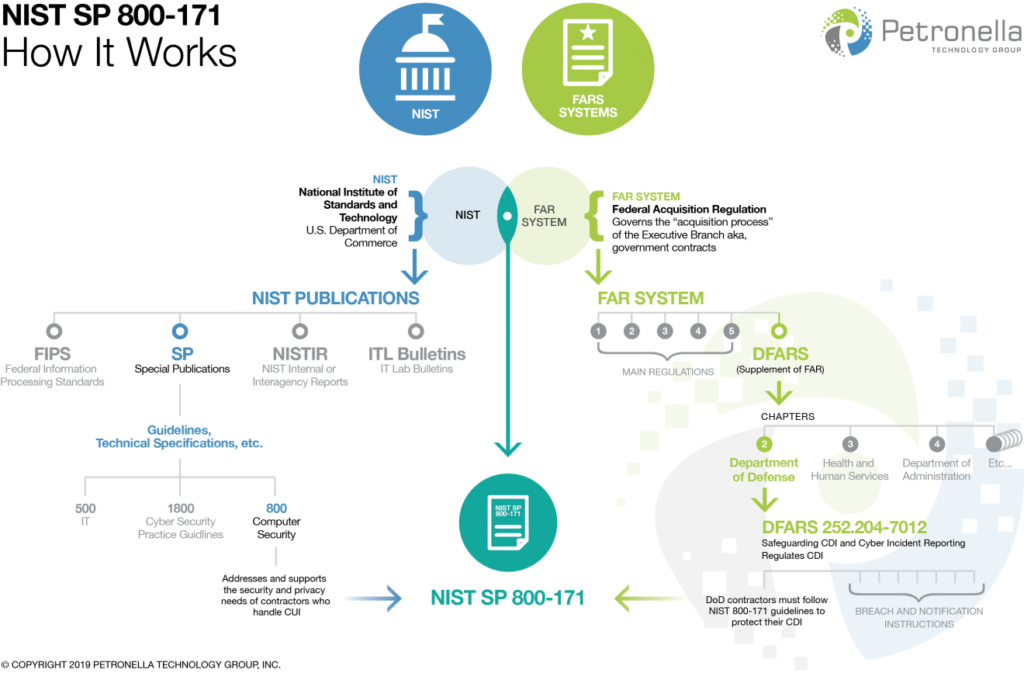
The Defense Federal Acquisition Regulation Supplement (DFARS) Clause 252.204-7012 incorporates NIST Special Publication 800-171 as a baseline for cybersecurity requirements for contractors handling Controlled Unclassified Information (CUI). Unlike CMMC, DFARS doesn’t have formally defined maturity levels. Instead, it mandates compliance with the 110 security requirements Artikeld in NIST SP 800-171. Meeting these requirements is a prerequisite for working with the Department of Defense.
Failure to comply can result in significant penalties, including contract termination.
NIST Cybersecurity Framework Requirements
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a voluntary framework that provides a flexible approach to managing cybersecurity risk. It doesn’t mandate specific controls or have formal maturity levels like CMMC. Instead, it offers a set of core functions (Identify, Protect, Detect, Respond, Recover) and a tiered approach to implementation (Tier 1 to Tier 4).
Organizations can adapt the framework to their specific needs and risk profiles, creating a customized cybersecurity program. While not mandatory for DoD contractors in the same way as DFARS, NIST CSF serves as the foundation for CMMC and informs many other cybersecurity standards.
Comparison Table: CMMC, DFARS, and NIST Requirements
| Framework | Requirement Category | Specific Requirement | Maturity Level (if applicable) |
|---|---|---|---|
| CMMC | Access Control | Implementation of access control lists (ACLs) to restrict access to sensitive data. | Level 1 |
| CMMC | Incident Response | Development and implementation of an incident response plan. | Level 3 |
| DFARS (via NIST SP 800-171) | Risk Assessment | Conducting regular risk assessments to identify vulnerabilities. | N/A |
| DFARS (via NIST SP 800-171) | Access Control | Implementing access controls based on the principle of least privilege. | N/A |
| NIST CSF | Identify | Asset management and inventory. | Tier 1-4 (Implementation varies) |
| NIST CSF | Respond | Incident response planning and capabilities. | Tier 1-4 (Implementation varies) |
Scope and Applicability
Understanding the scope and applicability of CMMC, DFARS, and NIST SP 800-171 is crucial for organizations handling Controlled Unclassified Information (CUI). Each framework targets different organizations and industries, carries unique contractual obligations, and has varying geographical limitations. This section clarifies these distinctions.The primary difference lies in the mandatory nature of compliance and the scope of covered information. While all three frameworks aim to improve cybersecurity posture, their enforcement mechanisms and the organizations they affect differ significantly.
Targeted Organizations and Industries, Cmmc vs dfars vs nist what are the differences
CMMC primarily targets organizations in the defense industrial base (DIB) that handle CUI. This includes contractors and subcontractors of the Department of Defense (DoD). The specific level of CMMC certification required depends on the type of CUI handled and the contract’s terms. DFARS, a broader regulation, applies to all contractors and subcontractors working with the DoD, encompassing a wider range of industries and not solely focused on CUI.
NIST SP 800-171, while not directly a contractual requirement in itself, serves as the foundation for many DoD contracts and is often incorporated into them. Its applicability is therefore widespread among organizations handling CUI for the DoD, even if not directly subject to a specific CMMC level. Organizations outside the DIB may also voluntarily adopt NIST SP 800-171 to enhance their cybersecurity posture.
So you’re trying to wrap your head around CMMC vs. DFARS vs. NIST – it’s a jungle out there! Understanding the nuances of each is crucial for compliance, but sometimes you need a break from the regulatory headaches. That’s where checking out the exciting advancements in domino app dev, the low-code and pro-code future , comes in handy.
It’s a great way to refresh and then tackle those CMMC, DFARS, and NIST differences with renewed focus.
Contractual Obligations
CMMC certification is becoming a mandatory requirement for many DoD contracts. Failure to achieve the required CMMC level can result in contract ineligibility or termination. DFARS clauses mandate compliance with specific cybersecurity requirements, including those based on NIST SP 800-171. Non-compliance can lead to penalties, contract suspension, or termination. NIST SP 800-171 itself doesn’t directly create contractual obligations, but its adoption is frequently mandated through DFARS clauses or other contractual agreements.
Essentially, the contractual obligation arises from the contract itself, referencing NIST SP 800-171 as the standard to meet.
Geographical Limitations
CMMC, DFARS, and NIST SP 800-171 are primarily focused on organizations within the United States that work with the DoD. While the frameworks don’t explicitly limit their applicability outside the US, their enforcement mechanisms are largely tied to US government contracts and regulations. International organizations working with US DoD contractors may need to comply with relevant aspects of these frameworks depending on the nature of their involvement and the contractual agreements.
However, direct enforcement outside US jurisdiction is limited.
Implementation and Compliance

Achieving compliance with CMMC, DFARS, and NIST SP 800-171 requires a multifaceted approach that goes beyond simply checking boxes. Successful implementation necessitates a deep understanding of each framework’s requirements, a commitment to continuous improvement, and the allocation of appropriate resources. This section Artikels practical steps, necessary resources, and a suggested implementation roadmap for organizations striving for compliance.
Practical Steps for Compliance
The journey to compliance begins with a thorough assessment of your current cybersecurity posture. This involves identifying existing controls, assessing gaps against the chosen framework’s requirements, and prioritizing remediation efforts. For CMMC, this might involve a self-assessment using the CMMC assessment methodology, potentially followed by a third-party assessment for certification. For DFARS, compliance often focuses on the NIST SP 800-171 requirements, often involving self-assessments and annual reports to the government.
NIST SP 800-171 implementation focuses on establishing and maintaining the specified security controls within the organization’s information systems and practices. Each framework has specific reporting and documentation requirements that must be met.
Resources and Tools for Implementation
Effective implementation relies heavily on the right tools and resources. This includes dedicated cybersecurity personnel, specialized software, and potentially external consulting services. For example, vulnerability scanners are crucial for identifying weaknesses in your systems. Security Information and Event Management (SIEM) systems can help monitor and analyze security logs, providing valuable insights into potential threats. Automated tools can assist with tasks like patching and configuration management, reducing the manual effort required.
External consultants can provide valuable expertise, particularly during the initial assessment and implementation phases, offering guidance and ensuring compliance with the specific requirements of each framework. Consider using tools that support automated compliance reporting to streamline the process.
Step-by-Step Guide to Compliance
A successful implementation strategy should follow a phased approach.
- Assessment: Conduct a thorough assessment of your current security posture against the chosen framework’s requirements (CMMC, DFARS, or NIST SP 800-171). Identify gaps and prioritize remediation efforts.
- Planning: Develop a comprehensive compliance plan outlining specific goals, timelines, and responsibilities. This plan should include resource allocation, budget considerations, and a clear communication strategy.
- Implementation: Implement the necessary security controls identified in the assessment and plan. This may involve purchasing new software, updating existing systems, and training employees on new security procedures. Regular testing and validation are critical at this stage.
- Monitoring and Review: Continuously monitor your security posture and conduct regular reviews to ensure ongoing compliance. This includes regular vulnerability scans, security audits, and updates to your security controls.
- Documentation: Maintain comprehensive documentation of your security controls, policies, procedures, and assessment results. This documentation is crucial for demonstrating compliance to auditors or government agencies.
This phased approach ensures a structured and manageable path to compliance, allowing organizations to address challenges systematically and efficiently. The specific steps and timelines will vary depending on the size and complexity of the organization, as well as the chosen framework. Regular updates and adaptation of the plan are necessary to maintain ongoing compliance in the ever-evolving cybersecurity landscape.
Cost and Resources
Navigating the complexities of CMMC, DFARS, and NIST compliance requires a significant investment, both in terms of time and money. Understanding the financial implications of each framework is crucial for organizations to effectively budget and plan their compliance journey. This section provides a comparative analysis of the estimated costs and resources needed for achieving compliance with each framework. Remember that these are estimates, and the actual costs can vary significantly based on the size and complexity of the organization, its existing security posture, and the chosen implementation strategy.The costs associated with achieving compliance are multifaceted, encompassing various expenses related to assessments, remediation, training, and ongoing maintenance.
It’s vital to factor in both direct and indirect costs, including personnel time dedicated to compliance efforts, which can often be a significant hidden expense.
Cost Comparison of CMMC, DFARS, and NIST Compliance
The following table provides a high-level comparison of the estimated costs and resources required for each framework. Note that these are rough estimates and can vary significantly depending on factors mentioned above. For accurate cost projections, a thorough risk assessment and gap analysis are recommended.
| Framework | Estimated Cost | Resource Type | Specific Resource Examples |
|---|---|---|---|
| CMMC | $10,000 – $100,000+ (depending on level) | Human | Security professionals, IT staff, compliance officers, consultants |
| Technological | Security Information and Event Management (SIEM) systems, vulnerability scanners, intrusion detection systems, endpoint protection | ||
| Financial | Assessment fees, remediation costs, training expenses, software licenses, consultant fees | ||
| DFARS | $5,000 – $50,000+ (depending on scope and existing security controls) | Human | Security professionals, IT staff, contract managers |
| Technological | Similar to CMMC, but potentially less extensive depending on the specific requirements | ||
| Financial | Assessment fees, remediation costs, training expenses, software licenses | ||
| NIST Cybersecurity Framework | $2,000 – $20,000+ (depending on implementation depth and scope) | Human | Security professionals, IT staff, risk managers |
| Technological | May involve some technological investments, but often focuses on process improvement and existing tool utilization | ||
| Financial | Training, risk assessment, documentation, internal process improvements |
Relationship and Overlap
The CMMC, DFARS, and NIST frameworks, while distinct, are deeply interconnected in their pursuit of enhanced cybersecurity. Understanding their relationships is crucial for organizations seeking to navigate the complex landscape of cybersecurity compliance. Effective implementation often involves leveraging synergies between these frameworks to achieve a more comprehensive and efficient security posture.The primary relationship lies in their shared goal of improving cybersecurity.
DFARS (Defense Federal Acquisition Regulation Supplement) mandates CMMC (Cybersecurity Maturity Model Certification) for defense contractors, effectively making CMMC a specific implementation of the broader cybersecurity requirements Artikeld in DFARS. NIST (National Institute of Standards and Technology) frameworks, particularly NIST SP 800-171, provide the foundational cybersecurity practices upon which both DFARS and CMMC are built. Therefore, compliance with NIST SP 800-171 often serves as a significant stepping stone towards achieving CMMC certification and meeting DFARS requirements.
CMMC’s Dependence on NIST and DFARS
CMMC’s maturity model is directly derived from NIST SP 800-171 and other NIST publications. The practices and controls Artikeld in CMMC’s various maturity levels are essentially subsets or elaborations of the controls found within NIST SP 800-171. DFARS Clause 252.204-7012 incorporates CMMC requirements, making compliance with CMMC a direct response to the government’s regulatory mandate under DFARS. Organizations aiming for CMMC certification must necessarily address the underlying principles and controls established by NIST and mandated by DFARS.
This inherent dependency creates a clear path for organizations to systematically improve their cybersecurity posture by progressing through NIST SP 800-171 requirements to achieve CMMC certification.
Leveraging Synergies for Improved Cybersecurity
A strategic approach to compliance involves recognizing the interconnectedness of these frameworks. For example, an organization already implementing NIST SP 800-171 controls will find the transition to CMMC certification smoother and less resource-intensive. Similarly, achieving CMMC certification demonstrates a strong foundation in cybersecurity best practices, which can readily translate to improved compliance with other regulatory frameworks and internal security initiatives.
By aligning their cybersecurity programs with the overlapping elements of these frameworks, organizations can streamline their efforts, reduce redundancy, and achieve a more robust and cost-effective security posture. This holistic approach prevents the need for disparate and potentially conflicting security programs, leading to improved efficiency and reduced operational complexity.
Practical Examples of Synergies
Consider a company implementing NIST SP 800-171’s access control requirements. Many of these controls directly map to CMMC’s requirements for access control and identity management. By meticulously documenting and implementing these controls according to NIST SP 800-171, the company significantly reduces the effort required to demonstrate compliance with the corresponding CMMC requirements. This streamlined approach minimizes the need for duplicate efforts and resources, thus leading to a more efficient compliance process.
Furthermore, this foundational work in access control would likely benefit the organization beyond compliance, reducing the risk of internal breaches and data loss.
Illustrative Examples
Understanding the nuances of CMMC, DFARS, and NIST Cybersecurity Frameworks requires examining real-world applications. These examples highlight how different organizations navigate the unique challenges presented by each framework, depending on their size, industry, and government contract involvement.Let’s explore how these frameworks manifest in the daily operations of both a small business and a large government contractor.
Small Business Scenario: A Cybersecurity Consulting Firm
Imagine a small cybersecurity consulting firm, “Secure Solutions,” that bids on government contracts requiring CMMC certification. They currently have a basic cybersecurity posture, but need to enhance it to meet the requirements.The challenges Secure Solutions faces include the significant upfront investment in time and resources required for CMMC certification. They may lack the internal expertise to implement all the necessary controls, and the cost of hiring external consultants could be substantial.
Furthermore, understanding the specific requirements of each CMMC level and mapping them to their existing processes can be a complex undertaking.
- CMMC Implementation: Secure Solutions must implement practices covering all aspects of their business, from asset management and access control to incident response and risk management. Achieving even a basic CMMC Level 1 requires significant effort in documentation and process improvement.
- DFARS Applicability: If Secure Solutions doesn’t hold government contracts, DFARS doesn’t directly apply. However, they may find some overlap with NIST SP 800-171, which is a foundation for CMMC.
- NIST SP 800-171 Impact: While not directly required for their contracts, adopting NIST SP 800-171 controls as a stepping stone towards CMMC provides a solid cybersecurity foundation and demonstrates a commitment to security best practices. This could improve their competitiveness even without immediate government contracts.
Large Government Contractor Scenario: A Major Defense Systems Integrator
Consider “DefenseTech,” a large defense systems integrator with numerous government contracts. They face different challenges compared to Secure Solutions.DefenseTech already has established cybersecurity programs, but must adapt them to meet the stringent requirements of CMMC and DFARS. The scale of their operations necessitates a more robust and comprehensive approach. They might face challenges integrating new tools and processes across multiple departments and locations.
Maintaining compliance across their vast network and supply chain becomes a significant undertaking, demanding significant resources and expertise.
- CMMC Implementation: DefenseTech needs a comprehensive, multi-layered approach to achieve higher CMMC maturity levels. This includes rigorous internal audits, continuous monitoring, and a well-defined incident response plan. They’ll likely need dedicated personnel and potentially specialized software to manage the complexity.
- DFARS Applicability: DFARS is directly applicable to DefenseTech, given their substantial government contracts. Compliance is not optional; failure to meet DFARS requirements can result in contract termination or penalties.
- NIST SP 800-171 Impact: NIST SP 800-171 serves as the foundation for CMMC, and DefenseTech’s existing DFARS compliance efforts likely already incorporate many of its controls. However, they will need to demonstrate a higher level of maturity and rigor to satisfy CMMC requirements.
Comparison of Challenges and Solutions
Both Secure Solutions and DefenseTech face unique challenges. Secure Solutions primarily grapple with the initial investment and resource constraints, while DefenseTech faces the complexities of scaling compliance across a large and diverse organization. Both, however, benefit from a phased approach, focusing on building a strong foundation and gradually maturing their cybersecurity posture. Utilizing existing frameworks like NIST SP 800-171 as a starting point can ease the transition to full CMMC compliance.
Investment in training and automation tools can significantly streamline the process and reduce the overall burden.
Summary: Cmmc Vs Dfars Vs Nist What Are The Differences
Successfully navigating the landscape of CMMC, DFARS, and NIST compliance requires a strategic approach. While seemingly disparate, these frameworks share overlapping goals – ultimately aiming to strengthen cybersecurity. By understanding their unique requirements and leveraging potential synergies, organizations can build a robust security posture that not only meets regulatory demands but also protects sensitive data and maintains a competitive edge.
Remember to thoroughly assess your specific needs and consider seeking expert guidance to tailor your compliance strategy effectively.
Questions Often Asked
What is the biggest difference between CMMC and DFARS?
DFARS sets the
-requirement* for cybersecurity, while CMMC provides the
-methodology* for demonstrating compliance with that requirement. DFARS is a broad regulation, and CMMC is a more specific framework for assessing and certifying compliance.
Does complying with NIST automatically mean I comply with CMMC?
No. While NIST provides foundational cybersecurity frameworks (like NIST SP 800-171), CMMC builds upon and extends those requirements, adding specific maturity levels and assessment processes tailored to the Department of Defense’s needs.
How much does CMMC compliance cost?
The cost varies significantly depending on your organization’s size, current cybersecurity posture, and the level of CMMC certification you’re pursuing. Expect to invest in assessments, remediation efforts, and ongoing maintenance.
Which framework applies to my small business?
It depends on whether you’re working with the Department of Defense. If you are a subcontractor handling controlled unclassified information (CUI), you’ll likely need to comply with CMMC. If not, DFARS may still apply indirectly through your prime contractor.
