Companies Taking Cyber Insurance Are Vulnerable to Ransomware Attacks
Companies taking cyber insurance are vulnerable to ransomware attacks – a seemingly paradoxical statement, yet one supported by unsettling evidence. Cybercriminals are increasingly sophisticated, employing advanced techniques to identify potential targets, and the existence of cyber insurance can inadvertently act as a beacon, highlighting lucrative victims. This isn’t about insurance being ineffective; it’s about understanding how the landscape of cybercrime is evolving and adapting to exploit new vulnerabilities.
The methods used to identify insured companies range from publicly available information like press releases announcing new insurance policies to more clandestine methods involving data breaches and dark web intelligence. The incentive is clear: a guaranteed payout makes insured companies attractive targets, leading to larger ransom demands and potentially higher payouts for successful attacks. This creates a complex scenario where the very measure intended to protect businesses might inadvertently increase their risk.
The Correlation Between Cyber Insurance and Ransomware Attacks
It’s a disturbing reality: the very act of obtaining cyber insurance might inadvertently increase a company’s risk of becoming a ransomware victim. This isn’t to say insurance causes attacks, but rather that the existence of insurance can create a more attractive target for cybercriminals. The reasons are complex and multifaceted, involving both the availability of funds and the potential for increased vulnerability.Cyber insurance policies often cover significant financial losses resulting from ransomware attacks, including data recovery costs, business interruption expenses, and legal fees.
This substantial payout potential makes insured companies particularly appealing to malicious actors. They know a successful attack could lead to a large financial windfall.
Methods Attackers Use to Identify Insured Companies
Attackers employ various methods to identify companies with cyber insurance. This isn’t always a direct process; it often involves piecing together information from publicly available sources and exploiting vulnerabilities. For example, data breaches at insurance companies themselves can expose lists of their clients. Furthermore, leaked internal documents, social media posts by employees, or even press releases announcing new insurance policies can inadvertently reveal valuable information.
It’s a crazy world out there – companies think cyber insurance is a silver bullet, but ransomware attacks still hit them hard. The truth is, robust security is key, and that’s where understanding solutions like bitglass and the rise of cloud security posture management becomes crucial. Investing in proactive security measures, rather than just relying on insurance payouts after a breach, is the smarter approach to mitigating the ever-present threat of ransomware.
Sophisticated attackers might even use dark web forums and marketplaces to buy lists of insured companies. Another approach is to directly target companies in high-risk sectors known to have high rates of cyber insurance adoption, such as healthcare, finance, and technology.
Examples of How Insurance Incentivizes Attacks
The presence of cyber insurance can directly incentivize ransomware attacks in several ways. First, the potential payout acts as a clear motivator. A successful attack against an insured company could yield a significantly larger ransom than one against an uninsured company. Second, insured companies may have less incentive to aggressively fight off an attack or negotiate a lower ransom, knowing their insurance will cover a significant portion of the costs.
This perceived leniency can embolden attackers. Third, the recovery process following a ransomware attack is often complex and expensive, even with insurance. However, insured companies might prioritize speed and ease of recovery, potentially overlooking critical security improvements that could prevent future attacks. This is a situation where the insurance payment might inadvertently subsidize future attacks. For example, a hospital paying a ransom to quickly restore patient records might not invest in robust security upgrades afterwards, making them a more attractive target for future attacks.
Comparison of Attack Vectors
The specific attack vectors used against insured and uninsured companies might not differ drastically, but the
- motivation* and
- potential payoff* are different. While both groups might face phishing attacks, malware infections, or exploitation of software vulnerabilities, the reward for attackers is higher when targeting insured organizations.
| Attack Vector | Insured Company | Uninsured Company | Impact Difference |
|---|---|---|---|
| Phishing | High likelihood; large potential payout. | High likelihood; potential payout limited to company resources. | Higher financial incentive for attackers targeting insured companies. |
| Malware Infection (Ransomware) | High likelihood; large potential ransom. | High likelihood; potential ransom limited to company resources. | Attackers may demand larger ransoms from insured companies, knowing insurance will cover a portion. |
| Exploitation of Software Vulnerabilities | High likelihood; potential for significant data breach and ransom. | High likelihood; potential for significant data breach, but limited ransom. | The potential financial damage, including the insurance payout, incentivizes targeting insured organizations. |
| Social Engineering | High likelihood; potentially easier to manipulate due to perceived resource availability. | High likelihood; more likely to fight back due to limited resources. | Attackers might use social engineering to extract information on the insurance coverage to determine their target’s vulnerability and potential payout. |
Data Breaches and Insurance Claims
Data breaches are a devastating reality for businesses in the digital age, and the impact extends far beyond the immediate loss of sensitive information. The financial consequences, particularly regarding cyber insurance premiums, can be substantial and long-lasting. Understanding how data breaches affect insurance claims and the intricacies of cyber insurance policies is crucial for mitigating risk and ensuring adequate protection.The relationship between data breaches, ransomware attacks, and insurance claims is complex.
A successful ransomware attack often leads to a data breach, triggering a claim process that hinges on the specifics of the policy and the nature of the incident. The severity of the breach, the type of data compromised, and the company’s response all influence the outcome of the claim.
Impact of Data Breaches on Insurance Premiums
Data breaches significantly impact a company’s cyber insurance premiums. Insurers assess risk based on various factors, including the frequency and severity of past incidents. A company experiencing a data breach, especially one resulting from a ransomware attack, will likely see a substantial increase in its premiums in the following renewal cycle. This is because insurers view the company as a higher risk, increasing the likelihood of future claims.
The premium increase can vary widely depending on the scale of the breach, the type of data compromised (e.g., personally identifiable information (PII), financial data), the regulatory fines incurred, and the company’s overall security posture. A company with weak security practices will likely face a more significant premium increase than one with robust security measures in place. For example, a company experiencing a breach involving the theft of thousands of customer credit card numbers would expect a far greater premium increase than a company suffering a breach involving only internal documents.
Ransomware Attack Claim Process
Filing a cyber insurance claim after a ransomware attack involves a multi-step process. First, the company must immediately notify its insurer, providing detailed information about the attack, including the type of ransomware used, the extent of data compromised, and the steps taken to mitigate the damage. This notification is typically required within a specific timeframe stipulated in the policy.
The insurer will then conduct an investigation to verify the claim and assess the damages. This investigation may involve reviewing forensic reports, incident response documentation, and other evidence. Once the investigation is complete, the insurer will determine the extent of its coverage and the amount it will reimburse. This process can be lengthy and complex, sometimes taking months or even years to resolve.
The company should maintain meticulous records of all expenses incurred as a result of the attack, including legal fees, public relations costs, and the cost of data recovery and restoration. These records are crucial for supporting the claim.
Common Clauses and Exclusions in Cyber Insurance Policies
Cyber insurance policies contain various clauses and exclusions that can significantly impact the outcome of a ransomware attack claim. Common exclusions may include attacks originating from within the company’s network (insider threats), breaches caused by failure to implement reasonable security measures, and losses resulting from pre-existing vulnerabilities. Policies often have specific clauses related to ransomware, such as limitations on coverage for ransom payments or exclusions for attacks involving specific types of malware.
For example, a policy might exclude coverage for ransomware attacks that exploit known vulnerabilities that the insured failed to patch despite receiving warnings or updates. Careful review of the policy’s wording is critical to understanding the extent of coverage and potential limitations. It’s essential to work closely with a qualified insurance broker to ensure the policy adequately addresses the company’s specific risks.
Real-World Examples of Insurance Claim Impacts
Several real-world cases illustrate how the nature of a ransomware attack can affect insurance claims. For example, the NotPetya ransomware attack in 2017 caused widespread disruption and significant financial losses for many companies. While some insurers honored claims, others argued that the attack was not a typical ransomware event, but rather a form of state-sponsored cyber warfare, leading to disputes over coverage.
Similarly, attacks targeting specific vulnerabilities or involving sophisticated evasion techniques may lead to claim denials if the policy excludes such scenarios or if the insured failed to maintain adequate security measures. In contrast, claims related to ransomware attacks where the company promptly notified the insurer, followed established incident response protocols, and had robust security measures in place are more likely to be approved and result in full or partial reimbursement.
The specific details of each case and the interpretation of the insurance policy are crucial in determining the outcome.
Security Practices and Insurance Coverage

Cyber insurance is becoming increasingly crucial for businesses of all sizes, but the level of security implemented significantly impacts both the cost of insurance and the effectiveness of the coverage. A proactive approach to cybersecurity isn’t just good practice; it’s a smart financial investment that can dramatically reduce risk and potentially save a company from significant financial losses in the event of a breach.
The relationship between a company’s security posture and its insurance policy is a dynamic one, influencing premiums, coverage limits, and the success of any claims.Companies with cyber insurance generally exhibit more robust cybersecurity practices than those without. This isn’t always a direct cause-and-effect relationship; some companies might invest heavily in security regardless of insurance. However, the process of obtaining insurance often requires a thorough security assessment, prompting companies to identify and address vulnerabilities.
This assessment frequently leads to improvements in their security posture, creating a positive feedback loop. In contrast, companies without insurance may be less inclined to invest in proactive security measures, viewing it as an unnecessary expense until a breach occurs. This reactive approach can prove far more costly in the long run.
The Impact of Robust Security Measures on Insurance Premiums and Coverage
Strong security measures directly influence both the cost of cyber insurance premiums and the extent of coverage offered. Insurers assess the risk profile of each applicant, factoring in their security controls, incident response plans, and overall security posture. Companies with robust security measures, such as multi-factor authentication, regular security audits, employee training programs, and incident response plans, are considered lower risk.
This translates to lower premiums and potentially higher coverage limits. Conversely, companies with weak security postures are viewed as high-risk, leading to higher premiums and potentially limited or restricted coverage. For example, an insurer might refuse coverage for a company that lacks basic security controls like firewalls and intrusion detection systems. The difference in premiums can be substantial, potentially saving a well-protected company thousands of dollars annually.
Hypothetical Scenario: Strong Security Mitigating a Ransomware Attack
Imagine a small marketing agency, “Adroit Marketing,” that invests heavily in cybersecurity. They employ multi-factor authentication for all employees, conduct regular penetration testing to identify vulnerabilities, and maintain a robust backup system stored offline. They also have a comprehensive incident response plan. Despite these precautions, they experience a sophisticated phishing attack, resulting in a ransomware infection. However, due to their strong security measures, the ransomware only encrypts a small portion of their data.
Their offline backups allow them to quickly restore their systems, minimizing downtime and data loss. When they file a claim with their cyber insurance provider, the insurer recognizes their proactive security posture and the minimal impact of the attack. The claim is processed efficiently, and Adroit Marketing receives a relatively small payout to cover the cost of incident response and data recovery, a fraction of what it would have cost had their security been weaker.
In contrast, a similar-sized agency with weaker security might face a complete system shutdown, extensive data loss, and a far larger insurance claim, potentially exceeding their policy limits.
Security Best Practices to Reduce Ransomware Risk and Improve Insurance Coverage
Implementing robust security measures is crucial for reducing the risk of ransomware attacks and improving the likelihood of successful insurance claims. Here’s a list of best practices:
- Regular Software Updates and Patching: Promptly update all software and operating systems to address known vulnerabilities. This is fundamental in preventing many ransomware attacks.
- Multi-Factor Authentication (MFA): Implement MFA for all accounts, especially those with administrative privileges. This adds an extra layer of security, making it much harder for attackers to gain access.
- Employee Security Awareness Training: Regularly train employees to recognize and avoid phishing scams and other social engineering attacks. Human error is a major cause of ransomware infections.
- Robust Backup and Recovery System: Maintain regular backups of critical data, storing them offline or in a geographically separate location. This ensures data can be restored quickly in the event of a ransomware attack.
- Network Segmentation: Segment the network to limit the impact of a breach. If one part of the network is compromised, the rest remains protected.
- Firewall and Intrusion Detection/Prevention Systems: Employ firewalls and intrusion detection/prevention systems to monitor network traffic and block malicious activity.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify and address vulnerabilities before attackers can exploit them.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan to guide actions during and after a cyberattack.
The Role of Insurance in Ransomware Response
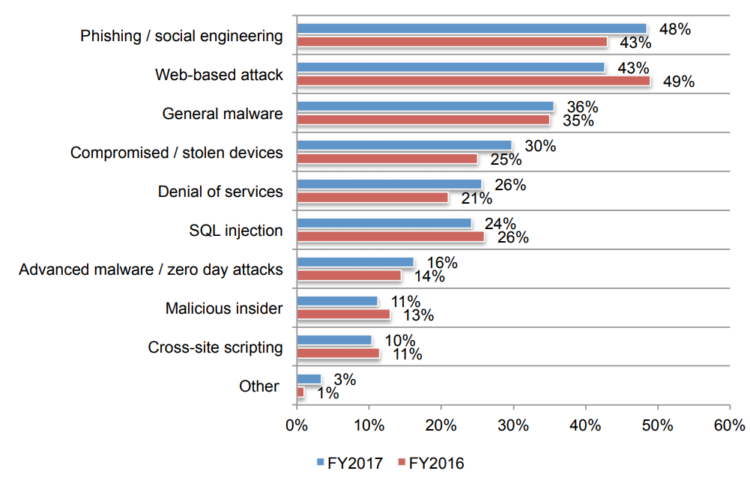
Cyber insurance plays a crucial role in mitigating the devastating effects of ransomware attacks. It’s not a silver bullet, but a vital component of a comprehensive cybersecurity strategy, offering financial and practical support during a crisis. A well-structured policy can significantly reduce the financial burden and streamline the recovery process.Cyber insurance doesn’t simply cover the ransom payment (although some policies do, with caveats).
Its value extends far beyond that, encompassing various aspects of incident response and recovery.
Incident Response and Data Recovery Support, Companies taking cyber insurance are vulnerable to ransomware attacks
Insurance companies provide various forms of support during a ransomware attack. This often begins with access to a dedicated incident response team. These teams are composed of cybersecurity experts who can guide the insured through the initial stages of the attack, helping to contain the damage and prevent further spread. This includes forensic analysis to determine the extent of the breach, guidance on communication strategies (with law enforcement and affected parties), and assistance in negotiating with attackers (though paying a ransom is often a last resort and depends on policy specifics).
Beyond this immediate response, insurers also often cover the costs associated with data recovery, whether that involves restoring data from backups or purchasing and implementing new systems. The level of support varies depending on the policy’s specifics and the severity of the attack.
Examples of Insurance Company Support During Ransomware Attacks
Consider a scenario where a small business suffers a ransomware attack, encrypting its critical financial data. Their cyber insurance policy might cover:
- The costs of a forensic investigation to determine the source and extent of the breach.
- Expenses related to notifying affected customers and complying with data breach notification laws.
- The cost of restoring data from backups or purchasing new hardware and software.
- Legal fees associated with regulatory investigations or lawsuits.
- Expenses for crisis communication and public relations.
A larger enterprise might experience a more extensive attack, leading to a broader range of covered expenses, potentially including business interruption insurance to cover lost revenue during downtime.
Limitations of Insurance Coverage in Ransomware Incidents
While cyber insurance offers significant support, it’s essential to understand its limitations. Many policies exclude certain types of attacks, such as those resulting from negligence or failure to maintain adequate security practices. Some policies may have sub-limits on specific expenses, such as ransom payments or legal fees. The claims process can also be complex and time-consuming, requiring thorough documentation and cooperation with the insurer.
Moreover, the insurance industry is still evolving its understanding and response to ransomware, leading to inconsistencies in coverage and claims handling across different providers. Finally, the rising frequency and sophistication of ransomware attacks have led some insurers to increase premiums or tighten coverage terms, making insurance more expensive and potentially less comprehensive.
Ransomware Response Process and Insurance Company Involvement
Imagine a flowchart. The first stage, “Attack Detection,” shows the insured discovering the ransomware attack. This flows into “Incident Response Initiation,” where the insured contacts their insurer and the insurer’s incident response team is deployed. The next stage, “Containment and Investigation,” shows the team working to contain the attack and investigate its extent, with the insurer covering costs for this.
This leads to “Data Recovery and System Restoration,” where the insurer covers the costs of restoring data and systems. The final stage, “Post-Incident Activities,” includes legal and regulatory compliance, rebuilding trust with customers, and implementing improved security measures; the insurer may contribute financially to these as well. The flowchart clearly illustrates the insurer’s active participation throughout the entire process, providing both financial and technical assistance.
It’s a crazy world out there; even companies with cyber insurance are prime targets for ransomware. Ironically, robust security systems, perhaps built using the innovative approaches detailed in this article on domino app dev the low code and pro code future , might be the best defense. Ultimately, no insurance policy can completely eliminate the risk, highlighting the constant need for proactive security measures.
The Future of Cyber Insurance and Ransomware

The relationship between cyber insurance and ransomware is rapidly evolving, driven by the increasing sophistication and frequency of ransomware attacks. The current model, while offering crucial financial protection, is facing significant challenges that necessitate adaptation and innovation. The future will see a shift towards more proactive, preventative measures integrated into insurance policies, alongside a greater emphasis on technological solutions to mitigate risk.The landscape of cyber insurance is undergoing a significant transformation in response to the ever-growing threat of ransomware.
The sheer volume and cost of ransomware attacks are forcing insurers to re-evaluate their risk assessments, pricing models, and policy coverage. This is leading to a more nuanced approach, moving away from simply reacting to breaches towards a more proactive, preventative model.
Changes in Cyber Insurance Policies and Coverage
Insurers are increasingly demanding higher security standards from their clients before offering coverage. This includes implementing multi-factor authentication, robust endpoint detection and response (EDR) systems, and regular security audits. Policies are likely to include clauses that explicitly address ransomware, potentially including specific coverage for ransom payments (though this remains controversial), incident response costs, and business interruption losses. We are also seeing a rise in policies that offer coverage for extortion beyond ransom demands, encompassing data theft and reputational damage.
For example, a policy might now cover not only the ransom payment itself but also the costs associated with notifying affected customers, legal fees, and credit monitoring services for those whose data was compromised. This broader coverage reflects the evolving nature of ransomware attacks, which often go beyond simple data encryption.
Emerging Technologies and Strategies for Ransomware Mitigation
Several emerging technologies are poised to play a crucial role in mitigating ransomware risks and improving insurance coverage. Advanced threat detection systems utilizing artificial intelligence (AI) and machine learning (ML) are becoming increasingly sophisticated in identifying and preventing ransomware attacks before they can occur. Blockchain technology is also being explored for its potential to enhance data security and improve the traceability of ransom payments.
Furthermore, robust data backup and recovery solutions, including immutable backups stored offline, are becoming essential for minimizing the impact of a successful ransomware attack. The use of zero-trust security models, which limit access to sensitive data based on strict verification, also represents a significant advancement in mitigating the risks. Companies investing in these technologies can expect to secure more favorable insurance premiums and broader coverage.
For example, a company implementing an AI-powered threat detection system and robust offline backups would likely receive a lower premium and broader coverage than a company relying solely on traditional antivirus software.
The Future Relationship Between Cyber Insurance and Ransomware
The future relationship between cyber insurance and ransomware is likely to be characterized by a closer partnership between insurers and their clients. Insurers will play a more active role in guiding clients towards better security practices, offering risk assessments and consulting services to help them reduce their vulnerability to attacks. This proactive approach will be essential in managing the rising costs associated with ransomware incidents.
We can anticipate a continued rise in the demand for cyber insurance, particularly as ransomware attacks become more frequent and sophisticated. However, the cost of premiums is likely to remain high, reflecting the inherent risks involved. This will incentivize companies to invest heavily in preventative security measures, leading to a more secure digital landscape overall. The future may see the development of innovative insurance products, such as parametric insurance, which provides payouts based on pre-defined triggers, such as the volume of encrypted data, rather than the actual cost of the incident.
This approach could streamline the claims process and provide faster payouts to businesses affected by ransomware attacks.
Last Point: Companies Taking Cyber Insurance Are Vulnerable To Ransomware Attacks
The relationship between cyber insurance and ransomware attacks is a complex and evolving one. While cyber insurance is a crucial tool for mitigating financial losses from cyberattacks, it’s not a silver bullet. Understanding how attackers leverage the existence of insurance to their advantage is vital. By focusing on robust cybersecurity practices, proactive threat intelligence, and a comprehensive understanding of insurance policy terms, companies can significantly reduce their vulnerability and navigate this challenging landscape.
The future of cyber insurance will likely involve more sophisticated risk assessments and policies that incentivize strong security postures, ultimately creating a more balanced equation between protection and risk.
Query Resolution
What types of data breaches are most likely to trigger a ransomware attack on an insured company?
Breaches revealing sensitive financial data, customer Personally Identifiable Information (PII), or intellectual property are prime targets, as these hold the most value for extortion.
Does my cyber insurance policy cover the cost of negotiating with ransomware attackers?
This varies greatly by policy. Some policies explicitly cover negotiation costs, while others may exclude it or have specific limitations. Review your policy carefully.
How can I improve my company’s cybersecurity posture to reduce the likelihood of a ransomware attack, regardless of insurance coverage?
Implement multi-factor authentication, regularly update software, conduct employee security awareness training, and maintain robust backups are crucial steps.
If I have cyber insurance, do I still need to report a ransomware attack to law enforcement?
Yes, absolutely. Reporting is crucial for investigations, identifying attack vectors, and contributing to broader cybersecurity efforts. Your insurance company may also require it.