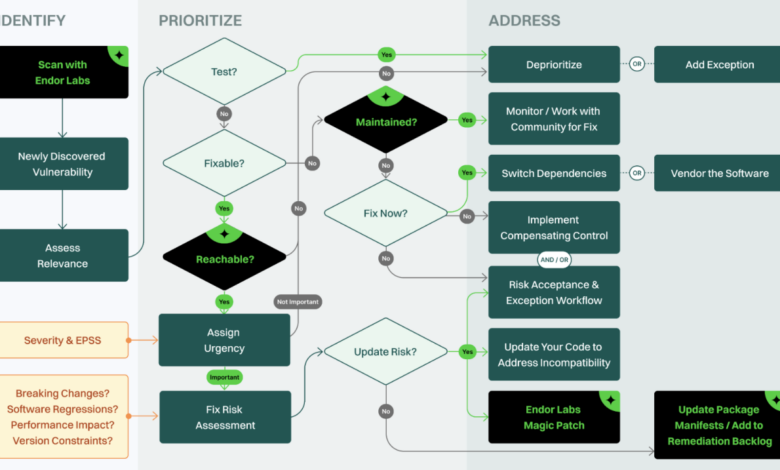
Lightspeed Remediation Integrated Risk Prioritization
Integrated risk prioritization for lightspeed remediation is crucial for navigating the complexities of fast-paced risk mitigation. This approach allows organizations to effectively identify, assess, and address critical risks, enabling swift and targeted remediation efforts. By prioritizing risks based on severity, probability, and potential impact, companies can allocate resources effectively and minimize disruptions to operations.
This detailed exploration dives into the core principles, methodologies, and practical applications of integrated risk prioritization. We’ll examine the specific needs of lightspeed remediation, how to link risk assessment to remediation plans, and explore various tools and techniques that can streamline the entire process. Ultimately, this guide aims to equip you with the knowledge and strategies to effectively manage risk and achieve swift remediation.
Defining Integrated Risk Prioritization
Integrated risk prioritization is a crucial element in any effective remediation strategy, particularly in fast-paced environments like Lightspeed remediation. It moves beyond simply identifying risks to actively managing them based on their potential impact and likelihood. This approach enables organizations to focus resources on the most critical vulnerabilities, minimizing downtime and maximizing efficiency. Prioritization is not just about ranking; it’s about making informed decisions that align with overall business objectives.A robust integrated risk prioritization framework is essential for effectively managing risk in a dynamic environment.
It involves a systematic approach to identifying, assessing, and prioritizing risks. Key components include a clear risk definition process, standardized assessment criteria, and consistent scoring methodologies. The framework should also accommodate the evolving nature of risk landscapes, allowing for continuous improvement and adaptation.
Key Components of a Robust Integrated Risk Prioritization Framework
A robust framework incorporates several key elements. First, a comprehensive risk register is vital. This register acts as a central repository for all identified risks, providing a clear picture of the current risk profile. Second, standardized assessment criteria are crucial for consistency and accuracy. These criteria should be tailored to the specific context of the organization, considering factors like industry regulations, business objectives, and technical infrastructure.
Third, consistent scoring methodologies are necessary to ensure that risks are evaluated objectively and compared fairly. Finally, the framework must be adaptable to evolving threats and changing circumstances.
Different Approaches to Risk Prioritization
Several approaches to risk prioritization exist. One common approach is qualitative risk analysis, which uses subjective judgment to assess risk factors. Another approach is quantitative risk analysis, which utilizes statistical data and mathematical models to estimate the likelihood and impact of risks. A hybrid approach combines elements of both qualitative and quantitative methods to provide a more comprehensive view of risk.
Comparison of Risk Prioritization Methodologies
Qualitative methods are generally faster and less resource-intensive, making them suitable for initial risk assessments. Quantitative methods, on the other hand, provide a more precise evaluation of risk, especially when dealing with complex systems. However, quantitative methods require more data and resources. A hybrid approach often provides the best balance, leveraging the strengths of both qualitative and quantitative methods.
Benefits of Integrating Risk Prioritization into a Lightspeed Remediation Strategy
Integrating risk prioritization into a Lightspeed remediation strategy provides several key benefits. It allows for a focused approach to remediation efforts, enabling teams to concentrate on the most critical vulnerabilities first. This ensures that resources are deployed effectively, minimizing disruption to operations. Furthermore, it helps to identify potential cascading effects of remediation activities, reducing the risk of unintended consequences.
Risk Prioritization Table
| Risk Type | Severity | Probability | Impact | Prioritization Score |
|---|---|---|---|---|
| Application Vulnerability | High | Medium | Medium | 6 |
| Network Outage | Critical | High | High | 9 |
| Data Breach | Critical | Low | Extreme | 8 |
| System Failure | High | Low | High | 6 |
| Configuration Error | Medium | Medium | Medium | 6 |
Understanding Lightspeed Remediation
Lightspeed remediation, a critical component of modern risk management, demands swift and decisive action to mitigate threats. This approach recognizes that certain risks, if left unaddressed, can escalate rapidly, impacting operations and potentially jeopardizing the entire system. This requires a deep understanding of the process and a robust prioritization system.
Defining Lightspeed Remediation
Lightspeed remediation is a risk management strategy characterized by its rapid response to high-priority vulnerabilities. It focuses on immediate actions to mitigate threats that pose imminent danger to systems, data, or operations. The goal is to minimize the impact of a threat and restore stability as quickly as possible. This is not simply a faster version of standard remediation; it requires a different mindset and a structured approach.
Key Characteristics of a Lightspeed Remediation Approach
A lightspeed remediation approach is distinguished by several key characteristics. These include a pre-defined framework for identifying and prioritizing critical vulnerabilities, streamlined communication channels, and a highly-trained team ready to execute tasks swiftly. It leverages automation wherever possible to accelerate the remediation process. The team is equipped with the necessary tools and resources to act decisively.
Time-Sensitive Nature and Implications for Risk Prioritization
The time-sensitive nature of lightspeed remediation necessitates a robust risk prioritization framework. Identifying risks based on their potential impact and the speed at which they can escalate is paramount. This prioritization ensures that the most critical threats receive immediate attention, minimizing disruption and preventing wider damage. For example, a vulnerability in a critical financial transaction system would be prioritized higher than a minor security flaw in a non-critical application.
Challenges Associated with Lightspeed Remediation
Implementing lightspeed remediation presents unique challenges. These include maintaining accuracy in the face of rapidly evolving threats, ensuring the quality of the remediation process, and coordinating diverse teams and resources. Risk prioritization is crucial in navigating these challenges, as it provides a structured approach for decision-making under pressure. It allows for a clear understanding of the impact of a potential failure and the cost of remediation.
Quick remediation of vulnerabilities is crucial, especially when dealing with high-risk issues. Integrated risk prioritization for lightspeed remediation is vital, and understanding specific vulnerabilities like those detailed in Azure Cosmos DB Vulnerability Details is key. Knowing these specifics helps prioritize remediation efforts effectively, ensuring a robust and secure system.
Key Performance Indicators (KPIs) for Effectiveness
The effectiveness of lightspeed remediation is measured by several key performance indicators (KPIs). These include the speed of remediation, the reduction in the impact of the incident, the number of successful mitigations, and the time taken to restore normal operations. A critical metric is the reduction in potential downtime or service disruption.
Lightspeed Remediation Process
| Task | Timeline | Resources | Responsibilities |
|---|---|---|---|
| Identify critical vulnerabilities | Within 24 hours of discovery | Security team, vulnerability scanners | Security team lead |
| Prioritize vulnerabilities based on risk | Within 48 hours of identification | Risk assessment team, security team | Risk management team, security analysts |
| Develop and execute remediation plan | Within 72 hours of prioritization | Development team, security team, incident response team | Development lead, security team lead, incident response lead |
| Verify successful remediation | Within 48 hours of execution | Testing team, security team | Testing lead, security analysts |
| Document the remediation process | Within 7 days of verification | Documentation team, security team | Documentation lead, security team lead |
Linking Risk Prioritization to Remediation: Integrated Risk Prioritization For Lightspeed Remediation

Integrating risk prioritization into lightspeed remediation is crucial for efficient and effective vulnerability management. By understanding the severity and likelihood of risks, organizations can focus their limited resources on the most impactful threats, preventing costly downtime and reputational damage. This targeted approach ensures a proactive and streamlined remediation process, reducing the time and expense associated with patching and fixing vulnerabilities.Risk prioritization isn’t just about identifying the problems; it’s about strategically addressing them.
A well-defined process helps allocate resources effectively, ensuring that critical vulnerabilities are patched quickly, while less critical ones are addressed in a timely but less urgent manner. This approach not only minimizes disruption but also enhances overall security posture.
Risk Matrices and Remediation Alignment
Risk matrices provide a structured framework for aligning remediation efforts with risk priorities. These matrices visually represent the potential impact and likelihood of a risk, enabling organizations to categorize vulnerabilities based on their severity. By mapping vulnerabilities to their corresponding risk levels on the matrix, teams can quickly identify those requiring immediate attention. For example, a high-impact, high-likelihood vulnerability would be prioritized for lightspeed remediation, while a low-impact, low-likelihood vulnerability might be scheduled for a later, less urgent remediation cycle.
Integrated risk prioritization for lightspeed remediation is crucial, but it’s not enough to just identify vulnerabilities. We need tools like those discussed in Deploying AI Code Safety Goggles Needed to proactively address code safety issues. This helps us focus on the most critical risks first, ensuring faster remediation and a more secure system overall.
Impact of Risk Levels on Remediation Speed and Scope
Different risk levels necessitate varying approaches to remediation. The table below demonstrates how risk levels influence the speed and scope of remediation activities:
| Risk Level | Impact | Likelihood | Remediation Speed | Remediation Scope |
|---|---|---|---|---|
| High | Significant | High | Immediate (within 24 hours) | Comprehensive; involve multiple teams if necessary |
| Medium | Moderate | Medium | Within 7 days | Focused on critical components; involve relevant stakeholders |
| Low | Minimal | Low | Within 30 days | Address as part of regular maintenance schedule |
This table highlights the critical need for a flexible approach. Organizations must adapt their remediation strategies based on the specific risk levels.
Stakeholder Communication in Lightspeed Remediation
Effective stakeholder communication is vital for successful lightspeed remediation. Clear and concise communication keeps stakeholders informed about the risks, the remediation process, and the expected timeline. This transparency builds trust and minimizes potential disruptions. Regular updates, progress reports, and open channels for questions and concerns are essential for maintaining stakeholder confidence and ensuring that remediation efforts align with business objectives.
Integrated risk prioritization for lightspeed remediation is crucial, especially when considering recent developments like the Department of Justice’s new safe harbor policy for Massachusetts transactions. This policy could significantly impact how we approach risk assessment and mitigation strategies, forcing a re-evaluation of our existing protocols for lightspeed remediation. Ultimately, this all means a more robust and adaptable approach to integrated risk prioritization is needed.
Escalation Process for High-Priority Risks
An escalation process is essential for managing high-priority risks that require immediate attention. This process should clearly define criteria for escalation, roles and responsibilities, and communication channels. For example, a high-severity vulnerability impacting a critical system might trigger an escalation to senior management, ensuring that resources and expertise are allocated accordingly. The escalation process should also specify the required level of detail in reporting and the frequency of updates.
Tools and Technologies for Integrated Risk Prioritization
Choosing the right tools is crucial for effectively prioritizing risks and enabling lightspeed remediation. Selecting software that seamlessly integrates with existing systems, facilitates clear visualization of risk data, and streamlines automation is paramount. This allows for faster identification of critical vulnerabilities and quicker response times. The right tools will translate risk assessment data into actionable remediation steps, driving a culture of proactive security.The selection of risk prioritization tools should be driven by factors like scalability, ease of use, and the ability to adapt to evolving business needs.
Furthermore, the tool should provide robust reporting capabilities, allowing for transparent communication of risk statuses and remediation progress to stakeholders. This ultimately helps build trust and confidence in the security posture of the organization.
Software Tools for Risk Prioritization
Various software solutions cater to integrated risk prioritization. These tools provide a comprehensive platform for identifying, analyzing, and mitigating risks. They often include features for visualizing risk data, automating tasks, and enabling lightspeed remediation.
- Risk Management Platforms: These platforms offer a centralized repository for managing risks, vulnerabilities, and compliance requirements. They typically incorporate risk assessment methodologies, allowing for the prioritization of risks based on factors like likelihood and impact. Risk management platforms can automate the tracking of remediation efforts, enabling a clear view of progress and outstanding tasks.
- Security Information and Event Management (SIEM) Systems: SIEM systems collect and analyze security logs from various sources. By correlating events and identifying patterns, SIEMs can help identify potential risks and vulnerabilities. Advanced SIEM solutions integrate with risk prioritization tools, enabling a holistic view of security posture and facilitating faster remediation efforts. Their dashboards often provide insightful visualizations of security incidents, helping analysts quickly identify and address high-priority risks.
- Vulnerability Management Tools: These tools scan systems for known vulnerabilities and provide prioritized remediation recommendations. They often integrate with asset management systems to provide context for the identified vulnerabilities. Integration with risk prioritization platforms allows for a complete risk assessment framework. This ensures vulnerabilities are linked to specific risks and prioritized accordingly, facilitating rapid remediation.
Features Enabling Lightspeed Remediation
Key features enabling lightspeed remediation in these tools include:
- Automated Risk Scoring: Automated risk scoring algorithms can quickly evaluate the impact and likelihood of a risk. This prioritizes high-risk vulnerabilities, enabling a focused remediation effort.
- Automated Remediation Tasks: Some tools automate the assignment of remediation tasks, creating a workflow that moves risks through different stages. This reduces manual intervention and accelerates the overall remediation process.
- Integration with Incident Response Tools: Integration with incident response platforms allows for a seamless flow of information, enabling a rapid response to security incidents. This minimizes the time to contain and remediate a threat.
Data Visualization for Risk Analysis
Data visualization plays a critical role in risk analysis. Clear visualizations of risk data facilitate understanding and improve decision-making. Tools often employ charts, graphs, and dashboards to represent risk scores, trends, and remediation progress. Examples include heat maps showing the correlation between vulnerabilities and business impact, or interactive dashboards providing a real-time overview of the organization’s risk profile.
Automation in Risk Prioritization
Automation is a critical component of integrated risk prioritization. Automating tasks like risk scoring, vulnerability scanning, and remediation tracking reduces manual effort and improves efficiency. This allows security teams to focus on more complex issues, and increases the speed and accuracy of risk management.
Comparison of Tools
| Tool | Features | Cost | Ease of Use |
|---|---|---|---|
| Risk Management Platform A | Comprehensive risk assessment, reporting, and automation | High | Medium |
| SIEM B | Advanced threat detection, correlation, and visualization | Medium | Medium |
| Vulnerability Management C | Automated vulnerability scanning, prioritization, and remediation | Medium | High |
Illustrative Examples of Integrated Risk Prioritization for Lightspeed Remediation
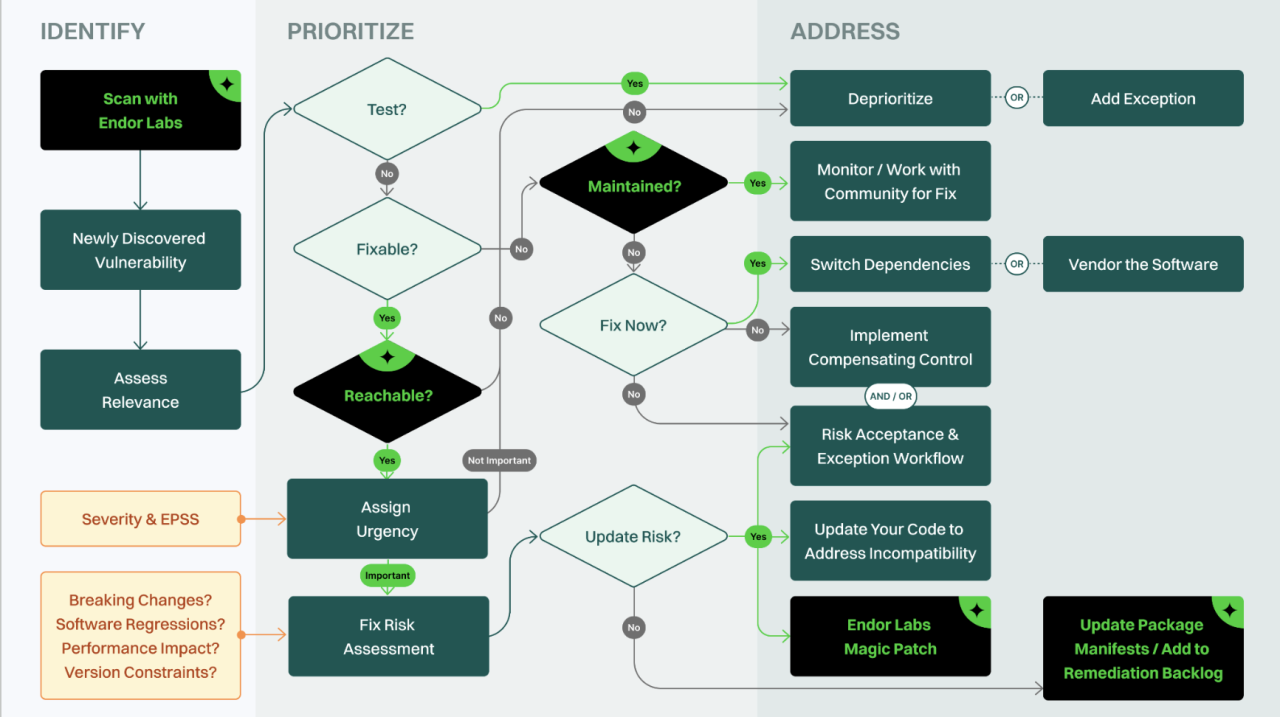
Integrating risk prioritization with lightspeed remediation is crucial for effective incident response. By focusing on the most critical vulnerabilities first, organizations can minimize disruption and maintain operational efficiency. This approach requires a structured methodology to evaluate risks, determine their impact, and establish a remediation timeline.
A Specific Risk Prioritization Example, Integrated risk prioritization for lightspeed remediation
A retail company experienced a significant data breach affecting customer credit card information. The risk was identified as high due to the potential financial loss, reputational damage, and regulatory penalties. The company implemented a multi-faceted approach to risk assessment, considering the likelihood of the breach occurring, the potential impact on customers, and the potential legal ramifications.
Steps in Prioritizing the Risk
- Data Collection and Analysis: Detailed information on the breach, including the number of affected customers, the type of data compromised, and the potential financial implications, was collected. This involved consulting with security teams, legal counsel, and customer service representatives. Analysis of historical data on similar incidents further informed the assessment.
- Risk Scoring and Ranking: Each risk factor was assigned a score based on a predefined scale, considering its likelihood and potential impact. The scoring system factored in the likelihood of the data breach occurring again, the number of compromised accounts, the financial losses estimated, and the possible fines or legal repercussions.
- Remediation Planning: Based on the risk score, a remediation plan was developed, which included strengthening the security infrastructure, implementing a comprehensive incident response plan, conducting regular security audits, and offering financial compensation to affected customers.
How the Risk Was Remediated
The remediation plan was implemented in phases. First, the company implemented enhanced security measures to prevent similar incidents. This involved upgrading firewalls, implementing multi-factor authentication, and conducting regular security audits. Second, they worked with legal counsel to develop a strategy for dealing with potential regulatory actions. Finally, they provided affected customers with comprehensive support and financial compensation.
The prioritization process ensured the most critical vulnerabilities were addressed first, minimizing the overall impact of the breach.
Effectiveness of the Prioritization Process
The integrated risk prioritization process was instrumental in streamlining the remediation efforts. By focusing on the most critical aspects of the breach, the company was able to mitigate the risk of further damage and effectively respond to the incident. The approach minimized the negative impact on operations, maintained customer trust, and enabled the company to avoid significant financial losses and legal issues.
Initial Risk Assessment and Final Remediation Plan
| Risk Factor | Initial Assessment Score (1-10) | Remediation Plan |
|---|---|---|
| Data Breach Likelihood | 9 | Implement multi-factor authentication, enhance firewall security |
| Number of Compromised Accounts | 8 | Provide comprehensive support to affected customers |
| Financial Losses | 10 | Offer financial compensation to affected customers |
| Regulatory Penalties | 9 | Consult with legal counsel, prepare for potential fines |
Case Study: A Successful Lightspeed Remediation Effort
A large financial institution successfully used integrated risk prioritization for a lightspeed remediation effort following a denial-of-service attack. By prioritizing the restoration of critical services, the institution minimized downtime and prevented significant financial losses. The rapid response, guided by a well-defined risk prioritization methodology, was instrumental in restoring service quickly and maintaining customer confidence. The organization utilized a robust risk scoring model, considering factors like service availability, financial impact, and regulatory compliance.
This led to a rapid and effective remediation strategy, demonstrating the value of a proactive approach to security incidents.
Best Practices and Considerations
Implementing integrated risk prioritization for lightspeed remediation requires a structured approach that considers various factors. This involves not only identifying and assessing risks but also aligning them with the specific remediation actions, ensuring a swift and effective response to vulnerabilities. A robust framework must be adaptable to changing threat landscapes and evolving technologies.Effective integration necessitates a clear understanding of the interplay between risk assessment, remediation timelines, and resource allocation.
This understanding will ensure the remediation efforts are prioritized strategically, focusing on the highest-impact vulnerabilities first.
Best Practices for Implementation
Prioritizing risk effectively for lightspeed remediation demands a comprehensive strategy. This includes establishing clear communication channels between security teams, development teams, and other stakeholders. Regular meetings and progress updates are crucial for maintaining alignment and addressing any roadblocks promptly. Documentation of the entire process, from risk identification to remediation completion, is essential for future reference and improvement. Furthermore, using standardized reporting formats enhances the visibility and analysis of risk data.
Common Pitfalls to Avoid
One common pitfall is neglecting the human element. Effective communication and collaboration are critical. Failure to involve all relevant stakeholders in the risk prioritization process can lead to resistance and difficulties in implementation. Another pitfall is using static risk assessment models. Threats evolve rapidly, so the risk prioritization framework must be dynamic and updated regularly.
Importance of Regular Review and Update
The threat landscape is constantly shifting. Security vulnerabilities are discovered daily, and new attack vectors emerge. Regular reviews of the risk prioritization framework are essential for maintaining its relevance and accuracy. Regular updates ensure the framework adapts to new threats and vulnerabilities, preventing complacency and maintaining a proactive approach to security. These reviews should incorporate feedback from previous incidents and security audits.
A schedule for periodic reviews (e.g., quarterly or annually) is crucial for continuous improvement.
Checklist for Evaluating Effectiveness
Evaluating the effectiveness of an integrated risk prioritization process is critical for continuous improvement. A checklist should include key performance indicators (KPIs) that assess the timeliness of remediation, the reduction in vulnerabilities, and the cost-effectiveness of the process. Quantifiable metrics for successful remediation are essential. These KPIs should be monitored and reported on regularly to track progress and identify areas needing improvement.
- Timeliness of Remediation: Track the average time taken to remediate prioritized risks. Compare this to established targets.
- Vulnerability Reduction: Measure the reduction in identified vulnerabilities after remediation efforts. Compare this to pre-implementation figures.
- Cost-Effectiveness: Analyze the cost of remediation against the potential financial impact of a successful attack. Assess if resources were allocated efficiently.
- Stakeholder Satisfaction: Gather feedback from all stakeholders involved in the process. Address any concerns and seek improvements.
Selecting a Risk Prioritization Methodology
Several methodologies exist for risk prioritization. Choosing the right methodology depends on the specific context of the organization and the nature of the risks being assessed. Factors to consider include the organization’s size, its technical infrastructure, and the resources available for remediation. Some methods might focus on quantitative metrics, while others emphasize qualitative assessments. A hybrid approach that combines both quantitative and qualitative factors might be optimal for lightspeed remediation.
Key Factors to Consider
The key factors for selecting a risk prioritization methodology for lightspeed remediation include the ability to adapt to rapid changes, the potential for automation, and the alignment with the organization’s overall security strategy. The selected methodology should be easily integrated with existing security tools and platforms to minimize disruption and maximize efficiency. Integration with existing IT infrastructure is essential for smooth implementation.
End of Discussion
In conclusion, integrated risk prioritization for lightspeed remediation provides a structured framework for proactively managing and mitigating risks. By understanding the unique challenges and opportunities presented by fast-paced remediation, organizations can develop efficient processes and deploy effective strategies. This comprehensive approach ensures resources are allocated strategically, enabling rapid responses to critical issues and maintaining operational stability.
FAQs
What are the key performance indicators (KPIs) for measuring lightspeed remediation effectiveness?
KPIs for measuring lightspeed remediation effectiveness often include the speed of remediation, the cost of remediation, the reduction in risk exposure, and the level of stakeholder satisfaction.
How does stakeholder communication play a role in integrated risk prioritization?
Clear and consistent communication with stakeholders is vital. It ensures everyone understands the risks, prioritization methodologies, and the remediation plan. Open communication fosters collaboration and helps manage expectations throughout the process.
What are common pitfalls to avoid when integrating risk prioritization with lightspeed remediation?
Some common pitfalls include neglecting to involve key stakeholders, failing to update risk assessments regularly, and not adapting the prioritization framework to evolving circumstances. Also, neglecting the human element of communication and collaboration is often overlooked.
How can automation streamline the risk prioritization process?
Automation tools can automate tasks like data collection, analysis, and reporting, allowing risk managers to focus on higher-level strategic decisions. This frees up time for more complex assessments and ensures consistency in the process.





