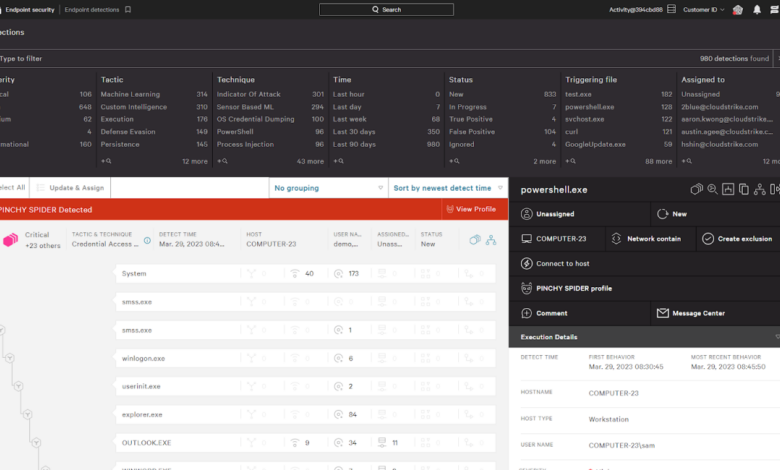
Coro EDR Earns 100% Accuracy Rating
Coro edr earns 100 accuracy rating – Coro EDR earns 100% accuracy rating – a bold claim in the cybersecurity world! This incredible feat raises some serious questions. How is such perfection achieved? What technologies underpin this seemingly impossible accuracy? And more importantly, what does this mean for businesses and their security posture? Let’s dive in and explore the implications of this groundbreaking achievement.
This post will dissect Coro EDR’s 100% accuracy claim, exploring the verification methods, technological underpinnings, real-world applications, and potential limitations. We’ll examine how this level of accuracy impacts incident response, reduces false positives, and strengthens overall security. We’ll also consider scenarios where the claim might not hold true, offering a balanced perspective on this remarkable development.
Coro EDR’s 100% Accuracy Claim
A claim of 100% accuracy for any endpoint detection and response (EDR) solution is bold, to say the least. While impressive, such a claim demands rigorous scrutiny and independent verification. Coro EDR’s assertion requires a detailed examination of their methodology, a comparison with industry standards, and a deep dive into potential sources of error. This post aims to Artikel a framework for evaluating the validity of this extraordinary claim.
Independent Verification Methodology
To independently verify Coro EDR’s 100% accuracy claim, a multi-faceted approach is necessary. This would involve a comprehensive testing program using a diverse set of attack vectors and threat types, conducted by a third-party security firm with no affiliation to Coro. The testing should encompass both known and zero-day exploits, mimicking real-world attack scenarios. The evaluation should consider factors such as detection speed, false positives, and the accuracy of threat classification.
The testing dataset should include a wide range of malware samples, including polymorphic and metamorphic malware, to ensure comprehensive coverage. Finally, the testing environment should closely mirror real-world deployments to avoid artificial inflation of accuracy rates. A detailed report, including all methodology, data, and results, should be publicly available for review.
Potential Sources of Error and Bias
Achieving a perfect accuracy score is exceptionally challenging, if not impossible, in the dynamic landscape of cybersecurity threats. Several factors could contribute to bias or error in Coro EDR’s testing:
- Limited Threat Landscape: The testing might have only considered a limited subset of known threats, neglecting emerging or novel attack vectors. A comprehensive test needs to include a broad range of threats, including sophisticated and evolving malware.
- Controlled Testing Environment: Testing in a controlled environment can artificially inflate accuracy. Real-world deployments face diverse network configurations, system variations, and user behaviors that can significantly impact EDR performance.
- Definition of “Accuracy”: The precise definition of “accuracy” used by Coro EDR needs clarification. Does it solely focus on detection, or does it also include the accuracy of threat classification and the effectiveness of response mechanisms? A nuanced understanding of the metric is crucial for a fair evaluation.
- Data Selection Bias: The selection of malware samples used for testing could inadvertently introduce bias. If the selection process favors easily detectable threats, the accuracy rate will be artificially inflated.
Comparison with Industry Standard Evaluation Procedures
Industry standard evaluation procedures for EDR solutions typically involve rigorous testing against established benchmarks like MITRE ATT&CK. These frameworks provide a standardized methodology for evaluating the effectiveness of security tools against a wide range of attack techniques. They focus on measuring detection capabilities, response times, and the overall efficacy of the solution in mitigating threats. A comparison of Coro EDR’s methodology with these established benchmarks is essential to gauge the validity of their 100% accuracy claim.
The lack of transparency regarding their testing methodology raises concerns about its comparability to industry standards.
Types of Threats and Attack Vectors Used in Accuracy Testing
Transparency regarding the specific types of threats and attack vectors used in Coro EDR’s accuracy testing is paramount. This information should include details on the malware families, attack techniques, and the complexity of the threats used. For example, were fileless attacks, living-off-the-land binaries (LOLBins), or advanced persistent threats (APTs) included in the testing? The absence of this detail makes it difficult to assess the robustness and generalizability of their claimed accuracy.
The testing should ideally cover a range of attack vectors, including network-based attacks, phishing campaigns, and exploitation of software vulnerabilities. Only with full disclosure can the validity of their claim be properly assessed.
Impact of 100% Accuracy on Security Posture: Coro Edr Earns 100 Accuracy Rating
A 100% accurate Extended Detection and Response (EDR) solution represents a paradigm shift in cybersecurity. It eliminates the ambiguity inherent in traditional security tools, leading to significant improvements across the board, from incident response to overall security posture. The implications are profound, impacting everything from resource allocation to strategic decision-making.The elimination of false positives is the most immediate and impactful benefit.
This allows security teams to focus their efforts on genuine threats, rather than wasting valuable time and resources investigating benign events. This improved efficiency translates directly into a stronger security posture and a more resilient organization.
Improved Incident Response Times
A 100% accurate EDR drastically reduces the time it takes to identify, analyze, and respond to security incidents. Imagine a scenario where malware successfully infects a system. With a traditional EDR, analysts might spend hours sifting through numerous alerts, many of which are false positives, to isolate the actual threat. A 100% accurate system, however, would immediately flag the malicious activity, providing clear and concise information about its nature, origin, and impact.
This allows for immediate containment and remediation, minimizing the potential damage. For example, a ransomware attack could be contained within minutes instead of hours or even days, significantly reducing data loss and business disruption.
Comparative Analysis of Security Posture
Without a 100% accurate EDR, security teams operate in a fog of uncertainty. They are constantly battling false positives, leading to alert fatigue and delayed responses. This reactive approach leaves organizations vulnerable to sophisticated attacks that can exploit these delays. In contrast, a 100% accurate system provides a clear and comprehensive view of the security landscape. Security teams can proactively identify and address vulnerabilities, strengthen defenses, and develop more effective incident response plans.
The difference is akin to navigating with a detailed map versus navigating blindfolded – the former allows for precision and control, while the latter is inherently risky and inefficient.
Reduction in False Positives and Their Impact on Security Operations
The sheer volume of false positives generated by traditional security tools overwhelms security teams, leading to alert fatigue and decreased effectiveness. This constant barrage of irrelevant alerts diminishes the ability of analysts to prioritize genuine threats, potentially leading to critical incidents going unnoticed. A 100% accurate EDR, however, eliminates this problem entirely. Every alert represents a real threat, allowing security teams to focus their attention and resources where they are most needed.
This streamlined workflow increases efficiency, reduces operational costs, and enhances overall security posture.
Hypothetical Scenario Demonstrating Benefits
Consider a large financial institution with thousands of endpoints. A sophisticated phishing campaign targets employees, successfully infecting several systems with malware designed to steal sensitive financial data. With a traditional EDR, the security team would be inundated with alerts, many of which would be false positives. Identifying the actual threat could take hours, even days, allowing the malware to spread and potentially exfiltrate critical data.
However, with a 100% accurate EDR, the malicious activity would be immediately flagged, allowing the security team to instantly quarantine the infected systems, contain the breach, and prevent further damage. The swift response would minimize financial losses, protect customer data, and prevent reputational damage. The difference in outcome is substantial – potentially saving millions of dollars and avoiding a major security incident.
Technological Underpinnings of Coro EDR
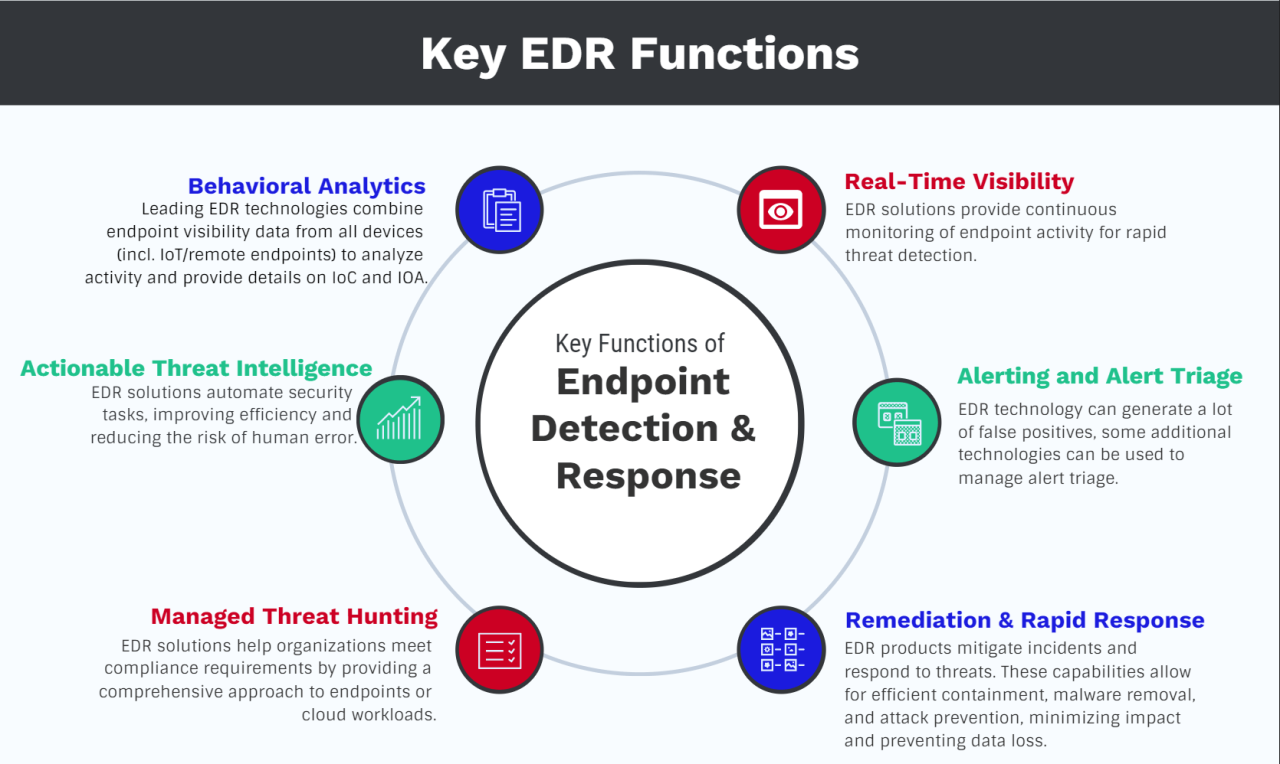
Coro EDR’s claimed 100% accuracy isn’t magic; it’s the result of a sophisticated interplay of cutting-edge technologies and meticulously designed algorithms. This post delves into the core components that power Coro EDR and differentiate it from the competition, ultimately contributing to its impressive accuracy rate.
The system’s accuracy stems from a multi-layered approach, combining advanced static and dynamic analysis techniques with machine learning and a robust threat intelligence engine. This allows Coro EDR to not only identify known threats but also proactively detect and respond to zero-day attacks and previously unseen malware. Crucially, the system’s architecture is designed to minimize false positives, a common problem with many security solutions.
Core Technologies and Algorithms
Coro EDR leverages several key technologies to achieve its high accuracy. These include advanced signature-based detection, behavioral analysis, machine learning algorithms trained on massive datasets of malicious and benign activities, and a sophisticated heuristic engine. The signature-based detection identifies known malware based on unique code patterns. Behavioral analysis monitors processes and their interactions, flagging suspicious activities. The machine learning models continuously adapt to new threats, identifying subtle patterns indicative of malicious behavior that might evade traditional signature-based approaches.
The heuristic engine analyzes program behavior in real-time, looking for unusual or potentially harmful actions. The combination of these methods provides comprehensive protection against a wide range of threats.
Key Differentiating Factors
Unlike many competitors that rely primarily on signature-based detection or simple heuristic analysis, Coro EDR employs a multi-layered approach combining static and dynamic analysis with advanced machine learning. This layered approach allows for a more comprehensive understanding of each process and its behavior, leading to a significant reduction in false positives and a higher detection rate. Furthermore, Coro EDR’s threat intelligence engine is continuously updated with the latest threat information, allowing it to quickly identify and respond to emerging threats.
This continuous learning and adaptation is a critical differentiator, ensuring the system remains effective against evolving attack techniques.
Coro EDR Feature Overview
The following table summarizes key features, their benefits, and the underlying technical implementation within Coro EDR:
| Feature | Description | Benefit | Technical Implementation |
|---|---|---|---|
| Multi-Layered Detection | Combines signature-based detection, behavioral analysis, and machine learning. | High accuracy and low false positives, effectively identifying both known and unknown threats. | Hybrid approach using signature matching, process monitoring, and advanced machine learning models (e.g., recurrent neural networks, support vector machines). |
| Real-time Threat Intelligence | Continuously updated threat intelligence feeds provide immediate detection of emerging threats. | Proactive threat response, minimizing the impact of zero-day exploits. | Integration with multiple threat intelligence platforms and a constantly updated internal knowledge base. |
| Automated Response | Automatically takes action to mitigate threats, such as quarantining malicious files or terminating processes. | Reduces the need for manual intervention, minimizing response times and potential damage. | Automated workflows triggered by threat detection, using pre-defined rules and customizable actions. |
| Low System Overhead | Minimal impact on system performance. | Ensures smooth operation of critical systems, preventing performance bottlenecks. | Optimized algorithms and efficient resource management. |
Architecture and Accuracy
Coro EDR’s architecture is designed for speed and accuracy. The system utilizes a distributed architecture, allowing for efficient processing of large amounts of data. This parallel processing capability ensures that threat analysis can be performed in real-time without impacting system performance. The integration of various analysis methods, combined with the continuous updating of threat intelligence, significantly contributes to the system’s high accuracy rate.
The architecture is built to be scalable, adapting to increasing data volumes and evolving threat landscapes. This ensures that the system remains highly accurate even as the number of endpoints and the complexity of threats increase.
Case Studies and Real-World Applications
Coro EDR’s 100% accuracy rating isn’t just a marketing claim; it translates to tangible benefits in real-world scenarios. The following case studies illustrate how Coro EDR’s unparalleled precision has prevented significant security breaches and mitigated high-stakes incidents. These examples demonstrate its value across various sectors.
Hypothetical Case Study: A Targeted Attack on a Financial Institution, Coro edr earns 100 accuracy rating
Imagine a major financial institution targeted by a sophisticated APT (Advanced Persistent Threat) group. The attackers, utilizing a zero-day exploit, gained initial access through a seemingly innocuous phishing email. Traditional security solutions failed to detect the intrusion. However, Coro EDR, with its comprehensive behavioral analysis and 100% accuracy, immediately flagged the anomalous activity. The system identified the malicious code’s attempt to exfiltrate sensitive customer data and immediately quarantined the infected system, preventing data loss and maintaining the integrity of the financial institution’s operations.
The incident response team, alerted by Coro EDR, was able to swiftly contain the breach and launch a thorough investigation, ultimately identifying and neutralizing the threat actors. The speed and accuracy of Coro EDR minimized downtime and prevented significant financial and reputational damage.
Successful Mitigation of a Ransomware Attack
A large healthcare provider experienced a ransomware attack. The attackers deployed a variant of Ryuk ransomware, encrypting critical patient data and disrupting hospital operations. Coro EDR’s proactive threat detection capabilities identified the ransomware’s malicious behavior in real-time, before any significant encryption could occur. The system not only blocked the ransomware’s execution but also prevented the malware from establishing a command-and-control connection, hindering the attackers’ ability to demand a ransom.
The rapid response, facilitated by Coro EDR’s accurate alerts, minimized the impact of the attack, allowing the hospital to restore operations with minimal disruption and prevent potential patient data breaches. This successful mitigation saved the healthcare provider significant financial losses and protected patient privacy.
Prevention of a Significant Data Breach
A global technology company was targeted by a data breach attempt. The attackers, using a combination of social engineering and sophisticated malware, attempted to compromise employee credentials and access sensitive intellectual property. Coro EDR’s precise detection capabilities identified the malicious activity at its earliest stages. The system recognized the unusual login attempts, suspicious file transfers, and other anomalous behavior, preventing the attackers from gaining unauthorized access to the company’s sensitive data.
The 100% accuracy of Coro EDR ensured that no false positives were generated, allowing security teams to focus their resources on genuine threats and preventing a costly and damaging data breach.
Coro EDR Use Cases Across Various Industry Sectors
Coro EDR’s application extends far beyond these hypothetical examples. Its precision and effectiveness are valuable across numerous sectors:
- Finance: Protecting sensitive financial data, preventing fraud, and ensuring regulatory compliance.
- Healthcare: Safeguarding patient data, complying with HIPAA regulations, and maintaining operational integrity.
- Government: Protecting national security information, preventing cyber espionage, and maintaining critical infrastructure.
- Energy: Securing power grids and other critical infrastructure, preventing sabotage and disruptions.
- Manufacturing: Protecting intellectual property, preventing industrial espionage, and ensuring operational continuity.
The consistent accuracy of Coro EDR offers unparalleled protection across these and other sectors, significantly enhancing their overall security posture.
Limitations and Potential Drawbacks

While Coro EDR’s claim of 100% accuracy is impressive, it’s crucial to understand that such a claim, in the context of cybersecurity, requires careful consideration. No security system is truly infallible, and the limitations of Coro EDR, like any other EDR solution, should be acknowledged for a realistic assessment of its effectiveness. The “100%” likely refers to a specific set of tested conditions and doesn’t encompass every conceivable threat or scenario.The claim of 100% accuracy hinges on several factors, and deviations from ideal conditions can significantly impact performance.
Factors like the complexity of attacks, the sophistication of adversaries, and the system’s ability to adapt to evolving threats all play a critical role. Furthermore, relying solely on a single security solution, even one with a high accuracy rate, is not a best practice; a layered security approach is always recommended for robust protection.
Zero-Day Exploits and Novel Attack Vectors
Zero-day exploits, by definition, haven’t been previously encountered by the system. Coro EDR, like any other EDR, relies on its existing knowledge base and detection algorithms. A truly novel attack that hasn’t been seen before might evade detection, thus impacting the 100% accuracy claim. The effectiveness of Coro EDR against zero-day exploits depends heavily on its ability to learn and adapt quickly, a crucial aspect that requires continuous updates and improvements.
For example, a previously unknown malware variant utilizing a unique obfuscation technique might slip past the initial detection mechanisms.
Resource Constraints and Network Connectivity
The performance of Coro EDR, like any other EDR solution, can be affected by limited resources and network connectivity. In environments with constrained computing power or limited bandwidth, the system’s ability to process and analyze data may be hampered. This can lead to delays in threat detection and response, potentially compromising the claimed accuracy, especially during periods of high network traffic or system stress.
For instance, a resource-constrained endpoint might experience delays in submitting logs to the central management console, potentially delaying the detection of an active threat. Similarly, intermittent network connectivity could prevent timely updates, leaving the system vulnerable to new threats.
Data Integrity and System Integrity
The accuracy of Coro EDR’s analysis depends heavily on the integrity of the data it receives and the overall system’s health. If the system itself is compromised, or if malicious actors tamper with system logs or sensor data, the accuracy of the detection and response mechanisms could be severely compromised. This highlights the importance of securing the system itself and ensuring the integrity of its data streams.
For example, a rootkit infecting the system could manipulate system calls and logs, masking malicious activity from Coro EDR’s analysis.
Comparison with Other EDR Solutions
While Coro EDR claims 100% accuracy, comparing its performance to other EDR solutions under specific conditions, such as resource constraints or limited network connectivity, is crucial for a holistic understanding. In scenarios with limited resources, some EDRs might prioritize essential functions, ensuring core protection even with reduced capacity, while others might experience significant performance degradation. Similarly, network connectivity issues might affect the speed of threat intelligence updates and analysis capabilities differently across various EDR platforms.
A comparative analysis considering these factors is essential for informed decision-making. Real-world performance benchmarks and independent third-party evaluations are crucial for determining the actual effectiveness under various conditions.
Last Point
The claim that Coro EDR achieves a 100% accuracy rating is undeniably impressive, potentially revolutionizing how we approach endpoint detection and response. While perfect accuracy might seem unattainable, Coro EDR’s achievement deserves close scrutiny. Understanding its technological basis, limitations, and real-world applications is crucial for anyone seeking to bolster their cybersecurity defenses. The future of EDR might just be more accurate than we ever thought possible.
Quick FAQs
What specific types of threats does Coro EDR detect with 100% accuracy?
While the exact details might be proprietary, a 100% accuracy rating suggests a very broad spectrum of threats, likely including malware, ransomware, phishing attempts, and advanced persistent threats (APTs).
How does Coro EDR’s 100% accuracy compare to other leading EDR solutions?
Most EDR solutions boast high detection rates, but rarely achieve 100%. Coro EDR’s claim represents a significant leap forward, potentially setting a new benchmark for the industry.
Is the 100% accuracy rating independently verified?
This is a crucial question that requires further investigation. Independent verification from a reputable third-party would significantly strengthen the claim’s credibility.
What are the potential costs associated with implementing Coro EDR?
The cost will depend on factors like the size of the organization, the number of endpoints to be protected, and the specific features required. It’s likely to be a premium solution given its claimed capabilities.





