Cost-Effective Ransomware Mitigation in Healthcare
Cost effective steps the healthcare industry can take to mitigate damaging ransomware attacks – Cost-effective steps the healthcare industry can take to mitigate damaging ransomware attacks are crucial in today’s digital landscape. Healthcare providers, constantly juggling patient data and sensitive information, are prime targets for ransomware criminals. The financial and reputational damage from a successful attack can be catastrophic, leading to lost revenue, legal battles, and eroded public trust. This post explores practical, budget-friendly strategies to bolster your cybersecurity defenses and minimize the risk of ransomware disruption.
We’ll delve into strengthening cybersecurity infrastructure through cost-effective measures like enhanced firewalls and multi-factor authentication. We’ll also examine the importance of employee training, robust data backup and recovery plans, and proactive incident response strategies. By understanding and implementing these steps, healthcare organizations can significantly reduce their vulnerability to ransomware attacks without breaking the bank.
Strengthening Cybersecurity Infrastructure
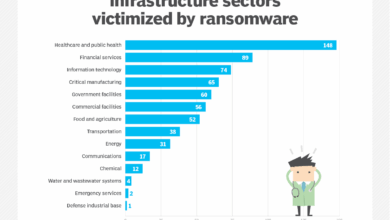
Ransomware attacks are a significant threat to the healthcare industry, causing disruptions to patient care, financial losses, and reputational damage. Strengthening cybersecurity infrastructure is paramount to mitigating these risks, and thankfully, many cost-effective strategies exist. Focusing on proactive measures is key to preventing attacks rather than solely reacting to them.
A robust cybersecurity infrastructure requires a multi-pronged approach, combining technological solutions with robust security policies and employee training. Prioritizing cost-effective solutions doesn’t mean compromising security; rather, it involves strategic planning and the selection of appropriate tools based on risk assessment and organizational needs.
Network Security Enhancements
Improving network security is foundational to ransomware prevention. This involves implementing and maintaining strong firewalls and intrusion detection systems (IDS). Cost-effective firewall enhancements include regularly updating firewall rules to block known malicious traffic and implementing deep packet inspection (DPI) to analyze network traffic for suspicious activity. For IDS, consider open-source solutions or cloud-based services that offer scalable and cost-effective monitoring capabilities.
These systems can alert administrators to potential intrusions, allowing for timely intervention. Regularly reviewing and updating firewall rules and IDS signatures is crucial for maintaining effectiveness. For example, a small clinic might opt for a cloud-based firewall service with basic DPI, while a larger hospital might require a more sophisticated on-premise solution with advanced threat intelligence feeds.
Multi-Factor Authentication Implementation
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication before accessing systems. This significantly reduces the risk of unauthorized access, even if credentials are compromised. Cost-effective MFA implementation can involve leveraging existing systems. For instance, many email providers offer built-in MFA, and many cloud-based services provide MFA as a standard feature.
For on-premise systems, implementing a cost-effective MFA solution might involve using hardware tokens or time-based one-time passwords (TOTP) applications. A phased rollout of MFA, prioritizing high-risk systems and sensitive data first, can be a cost-effective strategy. For example, a hospital could start by implementing MFA for administrative accounts and gradually expand to all clinical staff.
Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are critical for identifying and addressing security weaknesses before they can be exploited. Cost-effective strategies include using automated vulnerability scanners to identify common vulnerabilities and misconfigurations. Penetration testing, while more expensive, can be performed periodically to simulate real-world attacks and identify vulnerabilities that automated scanners might miss. Prioritizing critical systems and high-value data during assessments allows for a focused and cost-effective approach.
For instance, a healthcare provider might prioritize assessing their electronic health record (EHR) system and patient data storage systems more frequently than less critical systems. The frequency of audits and assessments should be tailored to the organization’s risk profile and resources.
Cost-Benefit Analysis of Cybersecurity Solutions
The following table compares the costs and benefits of different cybersecurity solutions. Remember that costs can vary widely depending on the size of the organization, the complexity of its systems, and the chosen vendor.
| Solution | Cost | Benefits | Implementation Time |
|---|---|---|---|
| Cloud-based Firewall | $500 – $5,000+/year | Enhanced network security, ease of management, scalability | 1-4 weeks |
| On-premise Firewall | $1,000 – $10,000+ initial cost, ongoing maintenance | High level of customization and control | 4-8 weeks |
| Open-source IDS | Low initial cost, ongoing maintenance required | Cost-effective intrusion detection | 2-6 weeks |
| Cloud-based MFA | $1 – $10+/user/year | Stronger authentication, reduced risk of unauthorized access | 1-2 weeks |
| Automated Vulnerability Scanner | $500 – $5,000+/year | Regular vulnerability identification | 1-2 weeks |
Employee Training and Awareness: Cost Effective Steps The Healthcare Industry Can Take To Mitigate Damaging Ransomware Attacks

Ransomware attacks are often successful because of human error. A strong employee training program is the most cost-effective way to significantly reduce your organization’s vulnerability. Investing in comprehensive training is far cheaper than dealing with the aftermath of a ransomware attack, including data recovery, system restoration, and potential legal and financial repercussions. This proactive approach shifts the focus from reactive damage control to preventative security measures.Regular and engaging training is key to maintaining a high level of awareness.
Employees need to understand not only the threat of ransomware but also how to identify and respond to it effectively. This goes beyond simply reading a manual; it requires interactive sessions, practical exercises, and consistent reinforcement.
Phishing Simulations and Their Effectiveness
Phishing simulations are incredibly valuable tools for assessing employee vulnerability and reinforcing safe practices. These simulated attacks mimic real-world phishing attempts, exposing employees to realistic scenarios without the risk of actual infection. For example, a simulation might involve sending an email that appears to be from a trusted source, such as the IT department or a bank, requesting login credentials or containing a malicious link.
Tracking employee responses allows you to identify individuals who are susceptible to phishing attacks and tailor further training to their specific needs. The effectiveness of these simulations can be measured by tracking the click-through rate (the percentage of employees who clicked on the malicious link) and the overall success rate of the simulation in identifying vulnerable employees. A successful program will show a decrease in the click-through rate over time, demonstrating improved employee awareness and response.
Safe Email Practices and Malicious Link Recognition, Cost effective steps the healthcare industry can take to mitigate damaging ransomware attacks
Educating employees about safe email practices is crucial. This includes teaching them how to identify suspicious emails, such as those with unusual sender addresses, grammatical errors, or urgent requests for personal information. Employees should be trained to carefully examine email headers and links before clicking on them. Hovering over a link to see the actual URL before clicking is a simple but effective technique.
Furthermore, training should cover how to recognize common types of malicious links, such as those shortened using URL shorteners or those that contain unusual characters. Employees should be instructed to never click on links from unknown senders or links that appear suspicious.
Best Practices for Handling Suspicious Emails and Attachments
A clear protocol for handling suspicious emails and attachments should be established and communicated to all employees. This protocol should emphasize the importance of reporting any suspicious activity to the IT department immediately. Employees should be instructed to never open attachments from unknown senders or attachments that appear suspicious. They should also be cautioned against clicking on links in emails that they are unsure about.
If an employee receives an email that they suspect is a phishing attempt, they should forward it to the IT department for analysis before taking any action. This proactive approach minimizes the risk of infection and allows the IT department to take appropriate measures to prevent further attacks. A well-defined reporting system ensures swift action and reduces the potential impact of a successful attack.
Regular reminders and reinforcement of these best practices through newsletters, emails, or short training videos will help keep employees vigilant and informed.
Data Backup and Recovery
Ransomware attacks can cripple a healthcare organization, leading to significant financial losses, reputational damage, and, critically, disruption of patient care. A robust data backup and recovery strategy is therefore not just a good idea—it’s a necessity. This strategy needs to be comprehensive, regularly tested, and cost-effective to ensure business continuity and minimize the impact of a successful attack.A well-designed backup and recovery plan should include multiple layers of protection, incorporating both on-site and off-site storage, diverse backup methods, and rigorous testing procedures.
The goal is to ensure rapid and complete data restoration with minimal downtime, even in the face of a sophisticated ransomware attack that encrypts or deletes critical data.
Offsite Data Storage and Redundancy
Offsite storage is crucial for protecting against physical disasters (fire, flood) and ransomware attacks that compromise on-site systems. This could involve using a cloud-based service, replicating data to a geographically separate data center, or using external hard drives stored in a secure, off-site location. The choice will depend on budget, security requirements, and the amount of data needing protection.
For example, a smaller clinic might opt for a cloud-based solution with regular offsite backups to an external hard drive, while a large hospital system may utilize a more complex multi-site replication strategy. Redundancy is key – having multiple backups in different locations significantly reduces the risk of complete data loss.
Regular Backups and Restoration Testing
Regular backups are essential. The frequency depends on the rate of data change. Critically important data, such as patient records, may require hourly or daily backups, while less frequently updated data can be backed up less often. However, regular backups are only useful if the restoration process is tested. Regularly restoring data from backups ensures that the backups are functional and that the recovery process is efficient and reliable.
Simulating a ransomware attack scenario – restoring data from backups to a separate test environment – allows the organization to identify and address any weaknesses in the process before a real attack occurs. For example, a weekly test restoration of critical patient data ensures the process is streamlined and minimizes downtime during a real emergency.
Diverse Backup Methods: Cloud, On-site, and Hybrid Approaches
Employing multiple backup methods enhances resilience. Cloud-based backup offers scalability, accessibility, and offsite protection. On-site backups, using tape or disk, provide quick access to data for immediate recovery. A hybrid approach, combining both, offers the best of both worlds. The specific mix of methods depends on the organization’s size, budget, and risk tolerance.
A small practice might rely on a cloud-based solution for simplicity, while a larger hospital system might use a combination of cloud, on-site disk arrays, and tape backups for redundancy and disaster recovery. Each method offers distinct advantages and disadvantages that should be carefully weighed against specific needs.
Minimizing Downtime During a Ransomware Attack
The speed of recovery is paramount. A well-defined incident response plan, including pre-defined recovery procedures, is crucial. This plan should detail the steps to be taken when a ransomware attack occurs, including isolating infected systems, initiating the recovery process from backups, and communicating with staff and patients. Having a dedicated recovery team trained to execute this plan swiftly minimizes downtime.
The use of a secondary, isolated system with regularly updated backups allows for a rapid shift to the backup system, minimizing the impact on patient care and other essential services. The faster the recovery, the less the overall disruption and cost.
Incident Response Planning
A robust incident response plan is crucial for minimizing the damage caused by a ransomware attack. It’s not enough to simply have security measures in place; you need a well-defined process to follow when an attack occurs. A proactive approach, including regular testing and updates, is key to its effectiveness. This plan should be a living document, regularly reviewed and updated to reflect changes in technology and threats.A comprehensive incident response plan Artikels the steps to be taken from the initial detection of a ransomware attack to the eventual recovery and remediation.
It should be specific to the organization’s size, infrastructure, and the types of data it handles. The speed and efficiency of the response directly impact the extent of the damage and the cost of recovery.
Key Personnel and Roles
Defining roles and responsibilities beforehand is critical. This ensures a coordinated and efficient response. Key personnel should include a designated incident response team leader, IT security specialists, legal counsel, public relations personnel, and representatives from affected departments. Each person should have a clearly defined role and contact information readily available. For example, the IT security specialist might be responsible for isolating infected systems, while the legal counsel handles communication with law enforcement and regulatory bodies.
The PR representative manages communication with the public and stakeholders.
Isolating Infected Systems and Preventing Further Spread
The immediate priority upon detecting a ransomware attack is to contain the threat. This involves isolating infected systems from the network to prevent the ransomware from spreading. This might involve disconnecting the affected system from the network, disabling network shares, and implementing network segmentation. Additionally, disabling unnecessary services and applications on affected systems can help limit the ransomware’s impact.
A critical step is the immediate disabling of any shared drives or network file shares. Imagine a scenario where an employee’s computer is infected – immediately disconnecting it prevents the spread to the company’s entire shared document drive.
Communicating with Stakeholders During a Ransomware Attack
Effective communication is essential during a ransomware attack. A pre-defined communication plan Artikels who needs to be informed, what information needs to be shared, and the channels for communication. This includes internal stakeholders (employees, management) and external stakeholders (clients, partners, regulatory bodies, law enforcement). The plan should address the type of messaging to use, avoiding panic-inducing language while remaining transparent about the situation and the steps being taken to resolve it.
For instance, a template email could be prepared in advance to notify employees about the attack and the actions they should take. A similar template could be used for external communications, though the details shared might differ. Regular updates should be provided to keep stakeholders informed of the progress.
Vendor Risk Management
In today’s interconnected healthcare landscape, reliance on third-party vendors for services like data storage, software applications, and IT support is unavoidable. However, this reliance introduces significant cybersecurity risks. Effective vendor risk management is crucial for mitigating these risks and protecting sensitive patient data. Failing to properly vet and manage vendors can leave your organization vulnerable to breaches, hefty fines, and reputational damage.Managing cybersecurity risks associated with third-party vendors requires a proactive and multi-faceted approach.
This involves establishing clear security requirements, conducting thorough due diligence, negotiating strong contractual agreements, and implementing ongoing monitoring and assessment procedures. A robust vendor risk management program is not a one-time task; it’s an ongoing process that requires consistent attention and adaptation.
Due Diligence in Vendor Selection
Selecting vendors solely based on cost or functionality is a recipe for disaster. A comprehensive due diligence process should be implemented to assess a vendor’s security posture before any contract is signed. This involves reviewing their security certifications (e.g., ISO 27001, SOC 2), conducting security questionnaires, and potentially performing penetration testing or vulnerability assessments. Understanding a vendor’s incident response plan and their track record in handling security incidents is also critical.
For instance, a vendor with a history of data breaches should raise significant red flags. Consider their physical security measures, employee background checks, and data encryption practices. A well-structured due diligence process should identify potential weaknesses before they become vulnerabilities within your own systems.
Contractual Clauses Addressing Cybersecurity Responsibilities
Contracts with vendors should explicitly Artikel cybersecurity responsibilities. These clauses should clearly define each party’s obligations regarding data security, incident response, and compliance with relevant regulations (like HIPAA). For example, the contract should specify the vendor’s responsibility for data encryption both in transit and at rest, their obligation to report security incidents promptly, and their commitment to maintaining specific security controls.
A strong contract will also detail the consequences of non-compliance, including potential financial penalties and termination of the agreement. Consider including clauses that mandate regular security audits and assessments of the vendor’s infrastructure. Example clause: “Vendor shall implement and maintain industry-standard security controls, including but not limited to, encryption, intrusion detection systems, and regular security vulnerability assessments, to protect Customer Data from unauthorized access, use, disclosure, alteration, or destruction.”
Vendor Cybersecurity Posture Evaluation Checklist
A structured checklist can help streamline the vendor evaluation process. This checklist should encompass several key areas:
- Security Policies and Procedures: Does the vendor have documented security policies and procedures that align with industry best practices and relevant regulations?
- Security Certifications and Audits: Does the vendor hold any relevant security certifications (e.g., ISO 27001, SOC 2, HIPAA)? Have they undergone independent security audits?
- Data Security Controls: What data security controls does the vendor have in place (e.g., encryption, access controls, data loss prevention)?
- Incident Response Plan: Does the vendor have a documented incident response plan? What is their process for reporting security incidents?
- Employee Security Training: Does the vendor provide regular security awareness training to its employees?
- Physical Security: What physical security measures does the vendor have in place to protect its facilities and data?
- Third-Party Risk Management: Does the vendor have a process for managing the cybersecurity risks associated with its own third-party vendors?
- Business Continuity and Disaster Recovery: Does the vendor have a business continuity and disaster recovery plan?
Using a checklist ensures consistency and thoroughness in the evaluation of each vendor, minimizing the risk of overlooking critical security considerations. Regular review and updates of this checklist are essential to adapt to evolving threats and best practices.
Leveraging Technology for Prevention

Ransomware attacks are a significant threat to healthcare organizations, demanding a multi-pronged approach to mitigation. While employee training and robust data backups are crucial, leveraging advanced technologies forms a critical layer of defense, offering cost-effective ways to prevent and respond to attacks. Investing in the right tools can significantly reduce the financial and reputational damage caused by ransomware.Advanced threat protection tools, endpoint detection and response (EDR) solutions, and security information and event management (SIEM) systems represent key technological advancements in bolstering cybersecurity.
Choosing the right combination of these technologies, based on an organization’s specific needs and budget, is key to maximizing their effectiveness and minimizing costs.
Advanced Threat Protection Tools and Cost-Effectiveness
Advanced threat protection (ATP) tools go beyond traditional antivirus software by employing machine learning and behavioral analysis to identify and neutralize sophisticated threats, including ransomware. These tools proactively monitor network traffic and endpoint activity, detecting anomalies indicative of malicious behavior before they can cause significant damage. While the initial investment in ATP solutions can be higher than basic antivirus, the long-term cost savings from preventing successful ransomware attacks – including downtime, data recovery costs, and potential fines – often outweigh the initial expense.
For example, a hospital that avoids a ransomware attack costing millions in recovery and lost revenue would quickly recoup the cost of an ATP solution. The cost-effectiveness is further enhanced by reduced IT support staff time spent dealing with security incidents.
Endpoint Detection and Response (EDR) Solutions
Endpoint Detection and Response (EDR) solutions provide real-time visibility into endpoint activity, enabling rapid detection and response to ransomware attacks. EDR tools monitor processes, file activity, and network connections on individual devices, identifying suspicious behavior that might indicate a ransomware infection. Early detection through EDR allows for quicker containment, minimizing the impact of the attack. The cost of an EDR solution varies depending on the number of endpoints and the features included, but the reduced downtime and data recovery costs often justify the investment.
A small clinic could significantly reduce their operational disruption by using EDR to swiftly identify and isolate a compromised machine before the ransomware spreads.
Strengthening cybersecurity in healthcare is crucial, and thankfully, there are cost-effective solutions. Investing in robust data backups and employee training is a great start. But to streamline these processes and build more secure systems, exploring modern development approaches like those detailed in this article on domino app dev the low code and pro code future could be incredibly beneficial.
This allows for faster development of security tools and applications, ultimately helping healthcare providers better protect patient data from ransomware threats.
Security Information and Event Management (SIEM) Systems
Security Information and Event Management (SIEM) systems collect and analyze security logs from various sources across an organization’s network. This centralized view provides a comprehensive understanding of security events, allowing for quicker identification of ransomware attacks and other threats. SIEM systems can correlate events, detect patterns indicative of malicious activity, and generate alerts to security personnel. While SIEM implementation requires upfront investment in hardware, software, and skilled personnel, the improved threat detection and response capabilities significantly reduce the risk of costly ransomware attacks.
Large hospital systems benefit significantly from SIEM’s ability to monitor vast amounts of data from diverse sources, allowing for faster detection and more effective incident response.
Comparison of Security Technologies and Associated Costs
The choice of security technologies depends heavily on the organization’s size, budget, and risk tolerance. A cost-benefit analysis is crucial.
Strengthening cybersecurity in healthcare is crucial, and cost-effective measures are key. Investing in robust employee training and multi-factor authentication are great starting points. However, managing the ever-growing cloud footprint is equally vital, which is where understanding tools like those discussed in this article on bitglass and the rise of cloud security posture management becomes essential.
This helps healthcare providers proactively identify and address vulnerabilities before they become ransomware attack vectors, ultimately saving money in the long run.
- Basic Antivirus: Low initial cost, but limited protection against sophisticated ransomware. High risk of successful attack.
- Advanced Threat Protection (ATP): Moderate to high initial cost, but significantly improved protection against advanced threats. Lower risk of successful attack, reduced recovery costs.
- Endpoint Detection and Response (EDR): Moderate to high initial cost, but provides real-time visibility and rapid response capabilities. Minimizes the impact of successful attacks.
- Security Information and Event Management (SIEM): High initial cost, requiring significant investment in hardware, software, and personnel. Provides comprehensive security monitoring and threat detection. Significantly reduces the risk of large-scale breaches.
Choosing the right combination of these technologies, tailored to the specific needs and resources of the healthcare organization, is key to achieving cost-effective ransomware mitigation. A phased approach, starting with essential protections and gradually adding more advanced layers as resources allow, can be a practical strategy.
Insurance and Mitigation Strategies
Ransomware attacks can cripple a healthcare organization, leading to significant financial losses and reputational damage. A multi-pronged approach, including robust cybersecurity measures and a well-defined insurance strategy, is crucial for effective mitigation. This section explores the role of cyber insurance and other financial strategies to minimize the impact of a ransomware incident.Cyber insurance offers a financial safety net in the event of a ransomware attack, covering costs associated with data recovery, legal fees, and business interruption.
However, it’s not a silver bullet. Careful consideration of policy terms, coverage limits, and exclusions is essential.
Cyber Insurance Benefits and Drawbacks
Cyber insurance policies can reimburse organizations for expenses related to ransomware attacks, such as ransom payments (though often with stipulations), data recovery, legal counsel, public relations, and notification costs. However, obtaining adequate coverage can be expensive, and policies often have deductibles and exclusions that limit the actual payout. Furthermore, the process of filing a claim and receiving reimbursement can be lengthy and complex.
Some insurers may also require organizations to meet specific cybersecurity standards to qualify for coverage, creating an incentive for improved security practices. The cost of premiums can also be significant, requiring a careful cost-benefit analysis.
Strategies for Reducing Financial Impact Beyond Insurance
Minimizing the financial impact of a ransomware attack extends beyond simply purchasing insurance. A proactive approach involving robust security measures, incident response planning, and business continuity strategies significantly reduces the potential for substantial losses. Investing in advanced threat detection systems, regular security audits, and employee training programs can significantly lower the likelihood of an attack. Moreover, developing a comprehensive incident response plan with clearly defined roles and responsibilities enables a swift and efficient response, limiting downtime and data loss.
Contingency Plans for Maintaining Operations During an Attack
A robust contingency plan is paramount for maintaining critical operations during a ransomware attack. This includes establishing offline backups of critical data, implementing a disaster recovery site, and having a clear communication plan for stakeholders. For example, a hospital might establish a temporary data center to handle patient records and essential medical functions while its primary systems are offline.
This requires significant upfront investment but can prevent catastrophic service disruptions and save lives. Another example is a clinic using a paper-based system as a temporary fallback, although this is less efficient.
Return on Investment (ROI) Calculation for Mitigation Strategies
Calculating the ROI for different mitigation strategies requires a careful assessment of costs and benefits. For example, the cost of implementing a robust backup and recovery system needs to be weighed against the potential cost of data loss and recovery in the event of an attack. The formula for calculating ROI is:
ROI = (Net Benefit – Total Cost) / Total Cost
The net benefit includes the cost avoided by preventing an attack or mitigating its impact. For instance, the cost of a ransomware attack might be estimated based on factors such as downtime, data recovery costs, legal fees, and reputational damage. By comparing the cost of implementing a particular security measure (e.g., employee training) to the potential cost savings from avoiding an attack, organizations can determine if the investment is worthwhile.
This analysis needs to be tailored to the specific risks and vulnerabilities of each organization. For example, a large hospital system will have different ROI calculations compared to a small private clinic.
Epilogue
Protecting patient data and maintaining operational continuity are paramount for the healthcare industry. While completely eliminating the risk of ransomware is impossible, implementing a multi-faceted approach combining strong cybersecurity infrastructure, employee training, data backup, and incident response planning is essential. By prioritizing cost-effective strategies, healthcare organizations can significantly improve their resilience against ransomware attacks, minimizing disruption and protecting their valuable assets – both tangible and intangible.
Remember, proactive security is far cheaper than reactive recovery.
Top FAQs
What is the single most important step to take?
While all steps are important, employee training is arguably the most critical. Human error is often the weakest link in cybersecurity, so educating staff about phishing scams and safe email practices is paramount.
How often should we test our backup and recovery systems?
Regular testing is crucial. Aim for at least a monthly test of your recovery process to ensure it’s functioning correctly and you can restore data quickly in an emergency.
What if we can’t afford all the recommended security solutions?
Prioritize based on risk. Focus on implementing multi-factor authentication, strong firewalls, and employee training first. Then, gradually implement other solutions as your budget allows.
How do I choose a reputable cybersecurity vendor?
Thoroughly research potential vendors, check their certifications and track record, and request references. Don’t hesitate to ask detailed questions about their security practices and incident response capabilities.