Criminal IP Unveils Innovative Fraud Detection Data Products
Criminal IP unveils innovative fraud detection data products on Snowflake Marketplace, revolutionizing how businesses combat fraud. This isn’t just another data product; it’s a game-changer, leveraging cutting-edge technology to provide unparalleled accuracy and efficiency in identifying and preventing fraudulent activities. Imagine a world where financial crime is significantly reduced, and businesses can operate with greater confidence – that’s the promise Criminal IP delivers.
This blog post dives deep into their new offerings, exploring their functionality, innovation, and impact on the industry.
From the diverse data sources they utilize to the sophisticated machine learning algorithms powering their models, Criminal IP offers a comprehensive solution. Their products integrate seamlessly with the Snowflake platform, making them accessible and user-friendly for businesses of all sizes. We’ll explore the key features of their data products, comparing their capabilities and highlighting the innovative technologies that set them apart.
We’ll also address crucial security and privacy considerations, ensuring you understand the robust measures in place to protect sensitive information.
Criminal IP’s Data Products on Snowflake Marketplace

Criminal IP has significantly enhanced its fraud detection capabilities by bringing its powerful data products to the Snowflake Marketplace. This move allows businesses to seamlessly integrate high-quality threat intelligence directly into their existing Snowflake data warehouses, streamlining workflows and improving the efficiency of fraud prevention strategies. The availability on Snowflake Marketplace simplifies deployment and reduces the technical overhead involved in implementing these critical security solutions.Criminal IP’s fraud detection data products provide comprehensive insights into malicious online activity, empowering organizations to identify and mitigate risks more effectively.
The integration with Snowflake leverages the platform’s scalability and performance, ensuring that businesses can analyze vast amounts of data quickly and accurately to identify fraudulent patterns and prevent financial losses.
Criminal IP Data Product Functionality
Criminal IP’s data products offer a range of functionalities designed to detect and prevent fraud. These include IP address reputation scoring, identifying known malicious actors, and flagging suspicious transactions based on behavioral patterns. The data is enriched with contextual information, such as geographic location, associated domains, and observed malicious activities, providing a comprehensive view of potential threats. This rich data allows for more accurate risk assessments and proactive fraud prevention measures.
Snowflake Integration Details
The Criminal IP data products are designed for seamless integration with Snowflake’s data platform. Users can access the data through Snowflake’s secure and scalable environment, allowing for easy querying and analysis within their existing data workflows. This integration eliminates the need for complex data transfers or separate data management systems. The data is delivered in a structured format, making it easily compatible with Snowflake’s querying capabilities and readily usable within existing business intelligence dashboards and security information and event management (SIEM) systems.
Target Audience
Criminal IP’s data products are targeted towards a broad range of industries and company sizes that face significant risks from online fraud. This includes financial institutions, e-commerce businesses, payment processors, and gaming companies. The products are scalable, making them suitable for both small businesses seeking to improve their security posture and large enterprises needing to manage massive volumes of transactional data.
Even organizations with existing fraud detection systems can benefit from the enhanced intelligence and contextual data provided by Criminal IP’s offerings.
Comparison of Key Data Products
The following table compares three of Criminal IP’s key data products, highlighting their features and benefits:
| Product Name | Key Features | Benefits | Target Use Case |
|---|---|---|---|
| IP Reputation Score | Real-time IP address risk scoring, historical threat data, geolocation data. | Improved accuracy in identifying malicious IPs, reduced false positives, proactive threat detection. | Transaction monitoring, access control, security incident response. |
| Fraudulent Actor Database | List of known malicious actors, associated IP addresses, domains, and email addresses. | Faster identification of known bad actors, prevention of account takeover, reduction in fraudulent transactions. | Account security, fraud investigation, risk assessment. |
| Behavioral Analytics | Detection of suspicious patterns in user behavior, anomaly detection, machine learning-based models. | Improved detection of sophisticated fraud schemes, reduced false positives, real-time alerts. | Real-time transaction monitoring, fraud investigation, risk management. |
Innovative Aspects of Criminal IP’s Fraud Detection Technology
Criminal IP’s fraud detection technology leverages a unique combination of data sources and advanced analytical techniques to provide a significantly more accurate and efficient solution compared to traditional methods. This allows businesses to proactively identify and mitigate fraudulent activities, minimizing financial losses and protecting their reputation. The innovative approach focuses on speed, accuracy, and scalability, addressing the ever-evolving tactics of fraudsters.
The core strength of Criminal IP’s technology lies in its ability to correlate and analyze vast quantities of data from diverse sources, identifying subtle patterns and anomalies that traditional rule-based systems often miss. This multi-layered approach, combined with machine learning algorithms, enables a proactive, rather than reactive, approach to fraud prevention.
Criminal IP’s new fraud detection tools on the Snowflake Marketplace are a game-changer, offering granular insights into suspicious activity. This kind of advanced threat detection is crucial, especially considering the increasing complexity of cloud environments; for a deeper dive into securing those environments, check out this article on bitglass and the rise of cloud security posture management , which highlights the importance of proactive security measures.
Ultimately, both Criminal IP’s data products and robust cloud security solutions like Bitglass are essential for a comprehensive fraud prevention strategy.
Real-time Risk Scoring and Predictive Modeling
Criminal IP’s real-time risk scoring system assigns a dynamic risk score to each transaction or user based on a comprehensive analysis of various data points. This includes information from their proprietary database of known fraudulent actors and activities, combined with behavioral biometrics and transactional data. This allows for immediate identification of high-risk transactions, enabling businesses to take preventative action in real-time, rather than reacting after a fraudulent event has occurred.
This significantly improves efficiency by reducing the time spent investigating potentially fraudulent activities. For example, a flagged high-risk transaction involving an unusual purchase amount from a newly registered user with a suspicious IP address would trigger an immediate alert, allowing for manual review or automated blocking. This contrasts with traditional methods that often rely on post-event analysis, resulting in significant financial losses and reputational damage.
Advanced Behavioral Biometrics and Anomaly Detection
Beyond traditional data points, Criminal IP’s technology incorporates advanced behavioral biometrics to identify subtle deviations in user behavior that might indicate fraudulent activity. This includes analyzing mouse movements, typing patterns, and scrolling behavior, providing a more holistic view of user authenticity. Combined with sophisticated anomaly detection algorithms, the system can identify unusual patterns and deviations from established baselines, even in the absence of explicit fraudulent indicators.
This is particularly effective in detecting sophisticated fraud schemes that attempt to mimic legitimate behavior. For instance, a sudden change in a user’s login location, combined with unusual purchasing patterns, could trigger an alert even if the user’s credentials are legitimate. Traditional methods relying solely on static data points would likely miss such nuanced indicators.
Global Threat Intelligence Network and Continuous Learning
Criminal IP’s fraud detection technology benefits from a constantly evolving global threat intelligence network. This network aggregates data from various sources, including law enforcement agencies, financial institutions, and other partners, providing a constantly updated view of emerging fraud trends and tactics. This intelligence feeds directly into the system’s machine learning algorithms, enabling continuous learning and adaptation to new and evolving fraud schemes.
This contrasts sharply with traditional methods, which often rely on static rule sets that become quickly outdated as fraudsters develop new techniques. The continuous learning aspect ensures that the system remains effective against sophisticated, evolving fraud tactics, protecting against both known and unknown threats. For example, the system could quickly adapt to a newly discovered phishing campaign by identifying common patterns in the URLs, email content, and user behavior associated with the campaign.
Data Sources and Processing Techniques
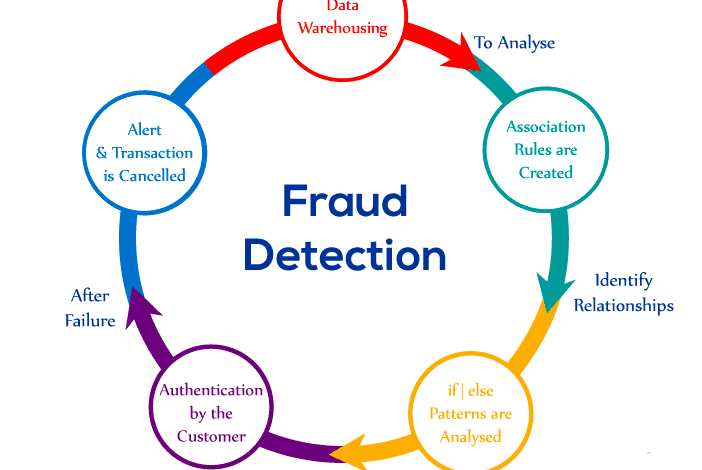
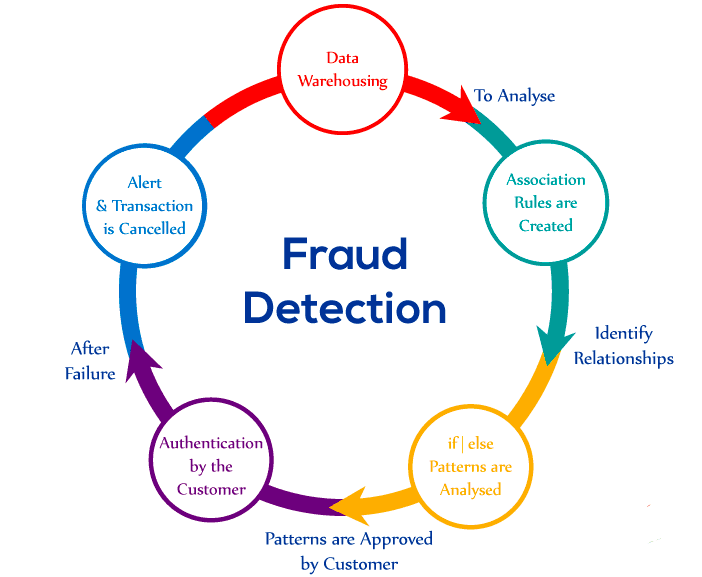
Criminal IP’s powerful fraud detection capabilities are built upon a robust foundation of diverse data sources and sophisticated processing techniques. Our models leverage a wealth of information to identify and prevent fraudulent activities, offering clients a comprehensive and highly accurate solution. This intricate process involves meticulous data cleaning, transformation, enrichment, and the application of advanced machine learning algorithms.The accuracy and effectiveness of our fraud detection models are directly tied to the quality and breadth of our data sources.
We employ a multi-layered approach, combining various data types to create a holistic view of potential fraudulent behavior. This allows us to identify patterns and anomalies that might be missed by using a single data source. The process of transforming this raw data into actionable insights involves several crucial steps, each contributing to the overall accuracy and efficiency of our system.
Criminal IP’s new fraud detection tools on the Snowflake Marketplace are seriously impressive; they’re changing the game in real-time data analysis. Think about how much easier building those kinds of applications would be with the low-code/pro-code flexibility described in this article on domino app dev the low code and pro code future , and you can see how these technologies complement each other.
Ultimately, Criminal IP’s focus on rapid deployment benefits from streamlined development processes.
Data Sources
Criminal IP utilizes a wide array of data sources to fuel its fraud detection engine. These sources are carefully selected for their relevance, accuracy, and coverage. Key sources include transactional data from various industries (e.g., e-commerce, finance, gaming), network data providing insights into IP addresses and their associated activities, publicly available information such as known malicious IP addresses and blacklists, and proprietary data sets built through years of research and analysis of fraud patterns.
The integration of these diverse data sources allows for a more comprehensive understanding of fraudulent activities and improved model performance. For example, combining transactional data with network data allows us to identify suspicious patterns in both transaction details and the origin of the transactions.
Data Processing Techniques
The raw data ingested from these diverse sources is far from perfect. It often contains inconsistencies, errors, and missing values. To address these issues, we employ a series of rigorous data processing techniques. Data cleaning involves identifying and correcting or removing inaccurate, incomplete, or irrelevant data points. Data transformation involves converting data into a format suitable for analysis and model building, including normalization, standardization, and feature engineering.
Data enrichment involves adding relevant contextual information to enhance the analytical value of the data. This might include adding geolocation data to IP addresses or linking transactions to known fraudulent actors.
Model Building Methodologies, Criminal ip unveils innovative fraud detection data products on snowflake marketplace
Criminal IP employs a range of advanced machine learning algorithms to build its fraud detection models. These algorithms are selected based on the specific characteristics of the data and the nature of the fraud being detected. Commonly used algorithms include logistic regression, random forests, gradient boosting machines, and neural networks. The choice of algorithm is crucial, as different algorithms excel in different scenarios.
For example, random forests are effective in handling high-dimensional data, while neural networks can identify complex, non-linear relationships. Model performance is continuously monitored and refined through rigorous testing and validation. This ensures that our models remain accurate and effective in detecting evolving fraud tactics.
Data Pipeline Steps
The following steps Artikel Criminal IP’s data pipeline:
- Data Ingestion: Real-time and batch ingestion of data from various sources using secure and reliable methods.
- Data Cleaning: Identification and handling of missing values, outliers, and inconsistencies.
- Data Transformation: Conversion of data into a suitable format for model training, including feature scaling and encoding.
- Data Enrichment: Augmentation of data with external sources to improve model accuracy and insights.
- Feature Engineering: Creation of new features from existing data to enhance model predictive power.
- Model Training: Training machine learning models using selected algorithms and training data.
- Model Evaluation: Assessment of model performance using appropriate metrics such as precision, recall, and F1-score.
- Model Deployment: Deployment of trained models into a production environment for real-time fraud detection.
- Model Monitoring: Continuous monitoring of model performance and retraining as needed to adapt to evolving fraud patterns.
Security and Privacy Considerations: Criminal Ip Unveils Innovative Fraud Detection Data Products On Snowflake Marketplace
Protecting sensitive data and respecting user privacy are paramount at Criminal IP. Our fraud detection data products are built with a multi-layered security architecture and are designed to comply with stringent data privacy regulations. We understand the critical nature of the information we handle and have implemented robust measures to ensure its confidentiality, integrity, and availability.Our commitment to data security extends beyond technical measures.
We maintain a rigorous internal security policy, encompassing employee training, regular security audits, and penetration testing to proactively identify and address potential vulnerabilities. This holistic approach ensures that our security practices are constantly evolving to meet emerging threats.
Data Encryption and Access Control
All data within our systems, both in transit and at rest, is encrypted using industry-standard encryption algorithms. Access to sensitive data is strictly controlled through role-based access control (RBAC), ensuring that only authorized personnel with a legitimate need to access specific data can do so. This granular control minimizes the risk of unauthorized access or data breaches. Regular security audits verify the effectiveness of our access controls and identify any potential weaknesses.
Privacy Policy and Compliance
Criminal IP’s privacy policy clearly Artikels how we collect, use, and protect personal information. We are committed to complying with all applicable data privacy regulations, including the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in California. We employ data minimization principles, collecting only the necessary personal information for fraud detection purposes and securely deleting it when no longer required.
Individuals have the right to access, correct, or delete their personal information as Artikeld in our privacy policy and in accordance with relevant legislation.
Compliance Standards
Our data products undergo regular audits to ensure compliance with industry best practices and relevant regulations. We actively monitor changes in legislation and adapt our practices to maintain compliance. Specific compliance certifications and attestations are actively pursued and maintained, reflecting our dedication to data security and user privacy. For example, our internal processes are aligned with the ISO 27001 standard for information security management systems.
Hypothetical Security Breach and Mitigation
Let’s imagine a scenario where a malicious actor gains unauthorized access to a portion of our database through a sophisticated phishing attack targeting an employee. Criminal IP’s response would be swift and multi-faceted. First, we would immediately isolate the affected system to prevent further compromise. A comprehensive forensic investigation would be launched to determine the extent of the breach and identify the attacker’s methods.
We would then notify affected individuals and relevant authorities, as required by law, and cooperate fully with any investigations. Finally, we would implement corrective measures, including strengthening security protocols, enhancing employee training, and potentially upgrading our security infrastructure to prevent similar incidents from occurring in the future. This would involve a review of our phishing detection and response mechanisms, along with enhanced multi-factor authentication processes.
Lessons learned would be incorporated into our ongoing security improvement program.
Market Positioning and Competitive Analysis
Criminal IP’s entry into the Snowflake Marketplace positions it strategically within a rapidly expanding market for fraud detection solutions. Understanding our competitive landscape and highlighting our unique advantages is crucial for successful market penetration and growth. This analysis compares Criminal IP’s offerings to key competitors, identifies our strengths, and projects potential market expansion.
Comparison with Major Competitors
To effectively position Criminal IP, we’ll compare our offerings against two prominent players in the fraud detection market: MaxMind and ThreatMetrix. MaxMind provides comprehensive IP address intelligence, including geolocation and threat scoring, while ThreatMetrix focuses on device and user behavior analytics for fraud prevention. Criminal IP differentiates itself by offering a highly granular, continuously updated dataset of known malicious IP addresses specifically optimized for Snowflake’s data warehouse environment.
This allows for seamless integration and real-time fraud detection within existing data pipelines, a significant advantage over competitors whose solutions might require more complex integrations or data transformations. Unlike MaxMind’s broader focus, Criminal IP concentrates solely on malicious IP identification, delivering a specialized and highly accurate solution. Compared to ThreatMetrix’s behavioral analytics, Criminal IP’s IP-centric approach provides a complementary layer of security, enhancing existing fraud detection systems.
Criminal IP’s Competitive Advantages
Criminal IP’s competitive advantages stem from several key factors. First, our hyper-focused dataset on malicious IP addresses provides unmatched accuracy and precision. Second, the seamless integration with Snowflake enables near real-time fraud detection, crucial for minimizing financial losses. Third, our data is continuously updated, reflecting the ever-evolving landscape of online fraud. This dynamic approach ensures our clients benefit from the latest threat intelligence.
Finally, the ease of use and readily available documentation within the Snowflake Marketplace simplifies implementation and reduces onboarding time for our customers. These combined advantages position Criminal IP as a powerful and efficient solution for organizations seeking robust fraud protection.
Potential Market Growth
The market for fraud detection solutions is experiencing exponential growth, driven by the increasing sophistication of online fraud and the rising volume of digital transactions. The global market size is projected to reach [Insert credible market research data and source here, e.g., “$XX billion by 2028, according to a report by [Market Research Firm]”]. Criminal IP is well-positioned to capture a significant share of this growth.
Our strategic partnership with Snowflake provides access to a vast network of potential customers, many of whom are already leveraging Snowflake’s data warehouse capabilities. Furthermore, the increasing demand for real-time fraud detection and the need for seamless integration with existing data infrastructure create a strong market pull for our product. For example, the recent surge in e-commerce transactions during the pandemic significantly increased the demand for robust fraud prevention measures, highlighting the critical need for solutions like Criminal IP’s.
Visual Representation of Competitive Landscape
Imagine a two-dimensional graph. The X-axis represents the “Breadth of Data Coverage” (ranging from narrow to broad), and the Y-axis represents “Integration Ease with Snowflake” (ranging from difficult to seamless). MaxMind would be positioned towards the broad end of the X-axis and somewhere in the middle on the Y-axis, reflecting its comprehensive data but potentially more complex integration. ThreatMetrix would be placed in a similar position on the X-axis, focusing on behavioral data, but also closer to the middle on the Y-axis, representing a moderate level of integration complexity.
Criminal IP would be plotted near the “narrow” end of the X-axis (due to the specialized focus) and at the “seamless” end of the Y-axis, showcasing its superior integration with Snowflake. This visual representation clearly illustrates Criminal IP’s unique position within the market, highlighting its competitive advantage in terms of both data specificity and ease of implementation.
Conclusion
Criminal IP’s launch of innovative fraud detection data products on the Snowflake Marketplace marks a significant step forward in the fight against financial crime. Their commitment to cutting-edge technology, robust security measures, and user-friendly integration makes their offering a compelling solution for businesses seeking to strengthen their fraud prevention strategies. The potential impact on the industry is undeniable, promising a future where fraud is detected and prevented more effectively than ever before.
It’s clear that Criminal IP is not just reacting to the evolving threat landscape; they’re shaping it, leading the charge towards a more secure digital future.
FAQ
What types of fraud do Criminal IP’s products detect?
Their products are designed to detect a wide range of fraud, including financial fraud (e.g., credit card fraud, account takeover), identity theft, and insurance fraud.
How much does it cost to use Criminal IP’s data products?
Pricing varies depending on the specific product and usage. It’s best to contact Criminal IP directly for detailed pricing information.
What kind of customer support do they offer?
Criminal IP typically provides comprehensive customer support, including documentation, tutorials, and direct contact with their support team. The specifics should be Artikeld on their website.
What is the data retention policy for Criminal IP’s data?
Their data retention policy should be clearly defined in their terms of service or privacy policy. Check their website for details.