Cring Ransomware Spreading Fortinet Vulnerability Exploited
Cring ransomware spreading because of fortinet vulnerability – Cring ransomware spreading because of a Fortinet vulnerability is a serious threat impacting organizations globally. This isn’t just another ransomware story; it highlights a critical flaw in widely used network security infrastructure, leaving countless systems vulnerable. We’ll dive into the specifics of this vulnerability, the tactics used by the attackers, and what you can do to protect yourself.
The scale of this attack is alarming, and understanding its intricacies is crucial for bolstering your own cybersecurity defenses.
The Fortinet vulnerability, once exploited, allowed Cring ransomware to spread rapidly. Attackers leveraged this weakness to gain initial access, encrypting sensitive data and demanding ransoms. The impact extends beyond the immediate financial losses; the long-term consequences, including reputational damage and operational disruptions, are significant. This incident serves as a stark reminder of the importance of proactive security measures and timely patching.
Fortinet Vulnerability Details
The recent Cring ransomware attacks highlight a critical vulnerability in Fortinet’s FortiGate and FortiOS systems. This vulnerability allowed attackers to gain unauthorized access and deploy ransomware, impacting numerous organizations globally. Understanding the technical specifics of this vulnerability is crucial for effective mitigation and prevention of future attacks.The specific vulnerability exploited by Cring ransomware is a critical remote code execution (RCE) flaw.
While the exact techniques used by the attackers are still being fully analyzed and refined, the exploitation leverages a weakness in the handling of specific network requests. This allowed attackers to execute arbitrary code on vulnerable Fortinet devices, giving them complete control over the system. The vulnerability, assigned CVE-2023-27997, is characterized by its severity and the potential for widespread damage.
Technical Aspects of CVE-2023-27997
CVE-2023-27997 is a vulnerability in the FortiOS SSL VPN web portal. Attackers could exploit this vulnerability by sending a specially crafted HTTP request to the vulnerable device. This request triggers a buffer overflow within the FortiOS system, allowing malicious code to be injected and executed. The impact of successful exploitation is significant, enabling attackers to take complete control of the affected device, potentially leading to data breaches, ransomware deployment, and disruption of services.
The vulnerability affects multiple versions of FortiOS, highlighting the need for prompt patching across a wide range of Fortinet products. The attackers likely leveraged automated scanning tools to identify vulnerable systems and then deployed their exploit payload. This payload then established a foothold, enabling lateral movement within the network to further compromise systems and deploy the Cring ransomware.
Attacker Methods
Attackers likely employed a multi-stage approach. First, they scanned the internet for vulnerable Fortinet devices using automated tools. Upon identifying a vulnerable system, they sent the crafted HTTP request, exploiting the buffer overflow to gain initial access. Following successful exploitation, the attackers likely established persistence, installed additional tools, and moved laterally within the network to identify high-value targets.
Finally, they deployed the Cring ransomware, encrypting sensitive data and demanding a ransom for its release. This methodical approach underscores the sophistication of the attackers and the potential for significant damage.
Vulnerability Summary
| Severity | Affected Products | Remediation Steps | CVE |
|---|---|---|---|
| Critical | FortiGate, FortiOS (various versions) | Apply the latest security patches and updates provided by Fortinet. Implement robust network segmentation and access controls. Regularly monitor system logs for suspicious activity. | CVE-2023-27997 |
Cring Ransomware Tactics and Techniques
Cring ransomware, leveraging the Fortinet vulnerability, demonstrates a concerning trend in sophisticated cyberattacks. Its success hinges on a combination of effective initial access, robust encryption, and a calculated approach to ransom demands. Understanding these tactics is crucial for effective prevention and mitigation strategies.
Infection Vector and Initial Access
Cring ransomware primarily spreads through exploitation of the Fortinet vulnerability. This vulnerability allows attackers to gain initial access to a network, often through compromised FortiGate devices. Once inside, the malware can then laterally move to other systems within the network, potentially infecting numerous machines. The attackers likely utilize automated tools and scripts to scan for vulnerable devices and deploy the ransomware payload.
This method avoids the need for user interaction, increasing the likelihood of successful infection.
Encryption Techniques and System Impact
Cring ransomware employs strong encryption algorithms, making decryption without the decryption key extremely difficult. The specific algorithm used is often kept secret by the attackers, further complicating recovery efforts. The ransomware typically targets critical files, including documents, databases, and backups, rendering affected systems unusable. The encryption process can be extremely fast, impacting a large number of files in a short timeframe.
This rapid encryption significantly increases the pressure on victims to pay the ransom.
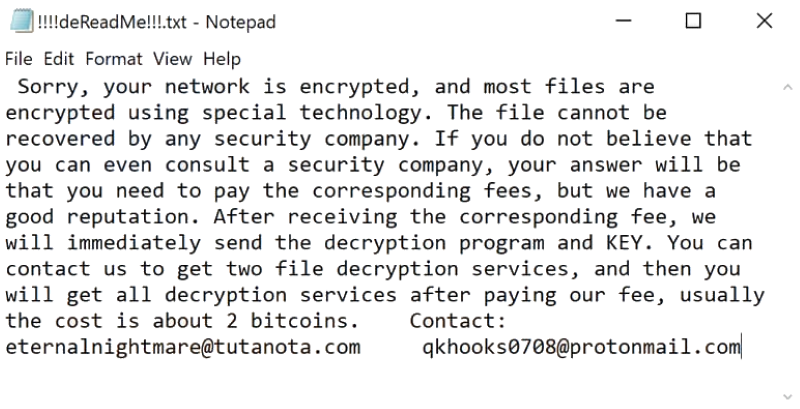
Ransom Demands and Payment Methods
The ransom demands associated with Cring ransomware vary depending on factors such as the size and sensitivity of the compromised data. Attackers often communicate their demands through ransom notes left on infected systems. These notes usually include instructions on how to pay the ransom, typically using cryptocurrency like Bitcoin or Monero, to maintain anonymity and hinder tracing. The ransom amounts can range from a few thousand dollars to significantly more, depending on the perceived value of the data to the victim.
The attackers might offer a reduced ransom if payment is made within a specific timeframe.
Command-and-Control Infrastructure
Cring ransomware relies on a command-and-control (C2) infrastructure to communicate with the attackers. This infrastructure might involve a network of compromised servers or cloud-based services used to receive commands, exfiltrate data, and potentially deliver updates to the malware. The C2 infrastructure is crucial for the attackers’ operational control and persistence. Securing and disrupting this infrastructure is a key element in neutralizing the threat.
Identifying and taking down the C2 servers is often a crucial step in disrupting the ransomware operation and preventing further attacks.
Impact and Spread of the Attack
The Cring ransomware attack, leveraging a Fortinet vulnerability, had a significant global impact, affecting a diverse range of organizations across various sectors. The speed and scale of the spread underscore the critical need for robust cybersecurity practices and timely patching. Understanding the geographical reach, affected industries, and resulting consequences is crucial for mitigating future risks and developing effective response strategies.
Geographical Distribution of the Attack
Imagine a world map. The most heavily affected regions appeared to be concentrated in North America, particularly the United States, and Western Europe, with notable clusters in the United Kingdom, Germany, and France. A less dense, but still significant, spread was observed across parts of Asia, particularly in regions with a high concentration of technology companies and financial institutions.
While precise numbers of affected systems in each location remain difficult to obtain due to the secretive nature of ransomware attacks, the observable pattern suggests a focus on areas with higher concentrations of potential targets offering substantial financial gain for the attackers. Less affected regions included those with weaker internet penetration or those where organizations already possessed stronger cybersecurity infrastructure.
Industries and Organizations Most Affected
The Cring ransomware attack disproportionately impacted several key sectors. This is largely due to the vulnerability exploited being prevalent in network infrastructure frequently used by these sectors.
- Healthcare: Hospitals and clinics faced significant disruption, potentially delaying critical care and impacting patient data security.
- Manufacturing: Production lines were halted in several instances, resulting in lost revenue and potential supply chain disruptions.
- Financial Services: Banks and other financial institutions were targeted, risking customer data breaches and financial losses.
- Education: Schools and universities experienced data breaches, disrupting academic operations and student records.
- Government: Several government agencies were affected, potentially impacting public services and sensitive information.
Financial and Operational Consequences for Victims, Cring ransomware spreading because of fortinet vulnerability
The financial and operational consequences for victims of the Cring ransomware attack were severe and varied widely depending on the size and resilience of the organization. Many organizations faced significant direct costs associated with:
- Ransom payments: While many victims choose not to pay, some succumbed to pressure and paid substantial sums to regain access to their data.
- Data recovery and restoration: The process of recovering encrypted data and restoring systems can be lengthy and expensive, requiring specialized expertise and resources.
- Legal and regulatory compliance: Victims faced legal costs and potential fines for non-compliance with data protection regulations, such as GDPR.
- Business interruption: The disruption to business operations resulted in lost revenue, reduced productivity, and damage to reputation.
Beyond the direct financial costs, the attack caused significant operational disruption, including lost productivity, damaged reputation, and strained relationships with clients and partners. The disruption caused by the attack cascaded through supply chains, impacting numerous other organizations not directly targeted.
Long-Term Impact on Data Security and Business Operations
The long-term impact of the Cring ransomware attack extends beyond the immediate financial and operational consequences. Organizations faced lasting challenges in:
- Enhanced cybersecurity investments: Many organizations were forced to significantly increase their cybersecurity budgets to improve their defenses and prevent future attacks.
- Improved incident response planning: The attack highlighted the need for robust incident response plans and regular security audits.
- Strengthened data backup and recovery strategies: Organizations had to review and strengthen their data backup and recovery strategies to ensure business continuity in case of future attacks.
- Employee training and awareness: The attack emphasized the importance of employee training and awareness in preventing phishing attacks and other social engineering techniques.
The Cring ransomware attack serves as a stark reminder of the evolving threat landscape and the importance of proactive cybersecurity measures. The long-term impact on data security and business operations underscores the need for continuous improvement and adaptation in the face of increasingly sophisticated cyber threats.
The Cring ransomware’s spread, fueled by the Fortinet vulnerability, highlights the urgent need for robust security. Building secure applications is crucial, and that’s where understanding the evolving landscape of application development comes in; check out this great article on domino app dev the low code and pro code future for insights. Ultimately, strong security practices, from the application level up, are our best defense against threats like Cring.
Mitigation and Prevention Strategies
The Cring ransomware attack, exploiting a Fortinet vulnerability, highlights the critical need for robust security measures. Preventing future incidents requires a multi-layered approach encompassing proactive patching, network segmentation, and employee training, coupled with a well-defined incident response plan. Ignoring these steps leaves organizations vulnerable to significant financial and reputational damage.Effective security measures to prevent exploitation of the Fortinet vulnerability begin with prompt patching.
This involves regularly updating all Fortinet devices with the latest security patches released by the vendor. Failing to apply these patches leaves systems exposed to known vulnerabilities, making them easy targets for attackers. Beyond patching, implementing strong access control mechanisms, including multi-factor authentication (MFA) and regular password rotations, significantly reduces the risk of unauthorized access. Network segmentation further limits the impact of a breach by isolating critical systems from less secure parts of the network.
This prevents a compromised system from easily spreading ransomware throughout the entire organization.
Patch Management and Vulnerability Scanning
Regularly scanning for vulnerabilities using automated tools is crucial. These scans identify potential weaknesses in systems and applications, allowing for timely patching and mitigation before exploitation. A comprehensive vulnerability management program should integrate automated patching processes, prioritized based on risk level, ensuring critical vulnerabilities are addressed first. This process should include not only Fortinet devices but also all other network components and applications.
Furthermore, regular penetration testing simulates real-world attacks to identify additional vulnerabilities that automated scanners might miss. This proactive approach helps organizations stay ahead of potential threats.
Network Segmentation and Access Control
Network segmentation divides a network into smaller, isolated segments. This limits the impact of a successful attack, preventing ransomware from spreading laterally across the entire network. For example, separating the corporate network from the guest Wi-Fi network and isolating sensitive data servers from less critical systems significantly reduces the potential damage. Access control mechanisms, such as role-based access control (RBAC) and least privilege principles, should be strictly enforced.
This limits the access rights of users and applications to only what is necessary for their function, minimizing the potential damage from a compromised account. Implementing strong multi-factor authentication (MFA) for all users, particularly those with administrative privileges, adds an additional layer of security.
Employee Security Awareness Training
Regular security awareness training is vital in mitigating ransomware attacks. Employees should be educated about phishing scams, malicious attachments, and suspicious links. Training should include practical examples of real-world attacks and best practices for identifying and reporting suspicious activity. Simulations, such as phishing tests, can help assess employee awareness and identify areas needing improvement. Furthermore, clear policies on acceptable use of company resources should be established and communicated to all employees.
This includes guidance on safe browsing habits, appropriate use of external storage devices, and reporting procedures for suspected security incidents.
Incident Response and Data Recovery
A comprehensive incident response plan is crucial for effectively managing a ransomware attack. This plan should Artikel clear procedures for identifying, containing, eradicating, recovering from, and learning from a ransomware infection. It should include steps for isolating infected systems, preventing further spread, and securing backups. Regular backups of critical data should be performed and stored offline or in a geographically separate location.
This ensures data recovery is possible even if the primary systems are compromised. The plan should also specify roles and responsibilities for each team member involved in the incident response process. Finally, regular testing and updates to the incident response plan are crucial to ensure its effectiveness.
Security Solutions Comparison
Various security solutions offer varying levels of protection against Cring ransomware. Next-generation firewalls (NGFWs) provide advanced threat protection, including intrusion prevention and malware detection. Endpoint detection and response (EDR) solutions monitor endpoint devices for malicious activity and can detect and respond to ransomware attacks in real-time. Security information and event management (SIEM) systems aggregate security logs from various sources, providing a centralized view of security events and facilitating threat detection and incident response.
The choice of security solutions depends on the specific needs and resources of an organization. A layered security approach combining multiple solutions provides the most comprehensive protection. For instance, an organization might utilize an NGFW for network protection, EDR for endpoint security, and SIEM for centralized monitoring and incident response. This layered approach increases resilience and reduces the likelihood of a successful ransomware attack.
Analysis of Attacker Motives and Operations: Cring Ransomware Spreading Because Of Fortinet Vulnerability
The Cring ransomware attack, leveraging a Fortinet vulnerability, reveals a sophisticated operation driven by financial gain and potentially a desire for notoriety within the cybercriminal underworld. Understanding the attackers’ motives and operational capabilities is crucial for developing effective countermeasures and preventing future incidents. This analysis delves into the likely motivations, infrastructure, and potential connections to other malicious actors.The primary motive behind the Cring ransomware attacks is almost certainly financial.
Ransomware operators profit directly from the extortion of victims, demanding payments in cryptocurrency to decrypt their data. The scale of the Fortinet vulnerability exploitation suggests a high potential for widespread infection and thus, significant financial returns for the attackers. Beyond direct financial gain, the successful exploitation of a widely used product like Fortinet’s could enhance the attackers’ reputation, attracting potential recruits or collaborators.
This reputation building within the dark web community can lead to future lucrative opportunities and collaborations on larger scale attacks.
Attacker Operational Capabilities and Infrastructure
The successful exploitation of the Fortinet vulnerability demonstrates a high level of technical expertise. The attackers likely possessed advanced knowledge of network security, exploit development, and ransomware deployment techniques. Their infrastructure likely includes command-and-control (C2) servers for managing infected systems, data exfiltration servers for stealing sensitive information, and cryptocurrency wallets for receiving ransom payments. The use of a widely exploited vulnerability suggests access to either a sophisticated exploit kit or the ability to rapidly adapt to newly discovered vulnerabilities, indicating a well-resourced operation.
Their ability to deploy the ransomware widely and efficiently suggests a level of automation in their operations, likely involving custom-built tools and scripts for automating various stages of the attack.
Potential Links to Other Cybercriminal Activities
Determining definitive links between the Cring ransomware operation and other cybercriminal activities requires extensive investigation and intelligence gathering. However, several indicators suggest potential connections. The use of similar tactics, techniques, and procedures (TTPs) to other ransomware groups could indicate a shared infrastructure, personnel, or affiliates. Analysis of the ransomware code itself, including its obfuscation techniques and unique identifiers, can reveal potential links to other known malware families.
Furthermore, the investigation might reveal the use of similar infrastructure or cryptocurrency wallets used in other cybercriminal activities, potentially linking this attack to other ransomware campaigns or data theft operations. Tracing the flow of cryptocurrency payments can provide valuable clues in uncovering potential connections.
Timeline of Key Events
The following timeline summarizes the key events of the Cring ransomware attack, based on currently available information. Note that the exact dates and times may vary depending on the sources and ongoing investigations.
- Discovery of Fortinet Vulnerability: [Insert Date – This date needs to be filled in with the actual date the vulnerability was discovered or disclosed.]
- Development and Deployment of Cring Ransomware: [Insert Date Range – This range represents the time when the attackers developed the ransomware and began deploying it, exploiting the Fortinet vulnerability.]
- Initial Reports of Infections: [Insert Date – This date reflects when the first reports of infections emerged, either from affected users or security researchers.]
- Public Disclosure of the Vulnerability and Attack: [Insert Date – This date marks the public awareness of both the Fortinet vulnerability and the Cring ransomware attacks.]
- Ongoing Investigations and Response Efforts: [Insert Date – This indicates the ongoing period of investigations by security researchers, law enforcement, and affected organizations.]
Conclusive Thoughts

The Cring ransomware outbreak, fueled by a critical Fortinet vulnerability, underscores the ever-evolving nature of cyber threats. While the immediate crisis might seem contained, the underlying vulnerabilities remain. Understanding the attack’s mechanics, from the initial exploit to the ransomware’s encryption techniques, is key to building robust defenses. Proactive patching, robust security protocols, and regular security audits are no longer optional—they’re essential for survival in today’s digital landscape.
Don’t wait for the next attack; take control of your security now.
FAQ Compilation
What specific Fortinet products are affected?
The exact affected Fortinet products vary depending on the specific vulnerability exploited. Check Fortinet’s official security advisories for the most up-to-date list.
How can I tell if my system is infected with Cring ransomware?
Look for encrypted files with a specific extension added by the ransomware (this can vary). You’ll also likely see a ransom note demanding payment.
Should I pay the ransom?
Generally, paying the ransom is not recommended. There’s no guarantee you’ll get your data back, and you’ll be encouraging further attacks.
What is the CVE number associated with this vulnerability?
You’ll need to consult Fortinet’s security advisories to find the relevant CVE numbers as they are often multiple and updated.