Culture Is Key for Security
Culture is key for security – it’s a phrase that’s gaining traction, and for good reason! We often focus on firewalls and passwords, but the real strength of any security system lies in the people using it. This post dives into how a company’s culture – its communication styles, risk tolerance, and overall approach – directly impacts its security posture.
We’ll explore how to cultivate a security-conscious culture, address cultural barriers, and even measure the effectiveness of our efforts. Get ready to rethink your approach to cybersecurity!
From designing culturally sensitive security awareness training to navigating incident response in diverse teams, we’ll unpack the complexities of integrating security into the very fabric of an organization. We’ll look at real-world examples, practical strategies, and actionable steps you can take to build a truly secure and resilient workplace. This isn’t just about policies; it’s about creating a shared understanding and commitment to security at every level.
Defining “Culture is Key for Security”
The statement “Culture is Key for Security” highlights the crucial role organizational culture plays in establishing and maintaining a robust security posture. A strong security culture isn’t simply about implementing technical controls; it’s about embedding security awareness and responsibility into the very fabric of how an organization operates. It’s a fundamental shift from viewing security as a separate function to integrating it seamlessly into daily workflows and decision-making processes.Organizational culture is multifaceted, encompassing shared values, beliefs, norms, and behaviors.
These elements significantly impact an organization’s security posture. A culture that prioritizes efficiency above all else might overlook security best practices in the pursuit of speed, while a culture that values collaboration might foster better incident response through effective teamwork. Conversely, a culture of secrecy or blame can hinder the reporting of security incidents, creating vulnerabilities. Different aspects of culture, such as communication styles, risk tolerance, and leadership commitment, directly influence how security practices are implemented and followed.
Communication Styles Influence Security Practices
Effective communication is paramount to a strong security culture. Open and transparent communication channels encourage employees to report security concerns without fear of reprisal. A culture that fosters open dialogue allows for the rapid identification and mitigation of threats. Conversely, a culture of silence or mistrust can lead to the concealment of vulnerabilities, allowing threats to fester.
For instance, an organization with a hierarchical communication structure might find it challenging to get security concerns from junior employees to senior management quickly, delaying critical responses. In contrast, a more flat organizational structure with open communication channels allows for faster feedback and response.
Risk Tolerance Shapes Security Approaches, Culture is key for security
An organization’s risk tolerance significantly influences its security investments and practices. Organizations with a high risk tolerance might prioritize cost-effectiveness over robust security measures, leading to potential vulnerabilities. Conversely, organizations with a low risk tolerance might overinvest in security, potentially hindering productivity and innovation. For example, a financial institution will likely have a much lower risk tolerance and invest heavily in security compared to a small non-profit organization with limited resources.
This difference in risk tolerance directly impacts their security strategies and resource allocation.
Leadership Commitment Drives Proactive Security
Strong leadership commitment is essential to fostering a proactive security mindset. Leaders who actively champion security initiatives, model secure behavior, and hold employees accountable for security practices create a culture where security is not an afterthought but a core value. Visible leadership support, including allocating sufficient resources and providing security awareness training, demonstrates the organization’s commitment to security and empowers employees to prioritize security in their daily tasks.
Conversely, a lack of visible leadership support can create a culture of complacency and weaken security efforts. A company CEO publicly endorsing a security awareness program, for instance, demonstrates a strong commitment that trickles down and motivates employees.
Cultural Impacts on Security Awareness Training: Culture Is Key For Security
Designing effective security awareness training isn’t just about delivering information; it’s about ensuring that information is understood, accepted, and acted upon. This requires a deep understanding of the cultural context of the audience, recognizing that different cultures have different communication styles, learning preferences, and approaches to risk perception. Ignoring these cultural nuances can lead to ineffective training and, ultimately, increased security vulnerabilities.Successful security awareness training must be culturally sensitive and tailored to resonate with the specific organizational culture.
A one-size-fits-all approach rarely works, especially in diverse workplaces. The effectiveness of the training hinges on how well it aligns with the values, beliefs, and communication norms of the employees.
Designing Culturally Tailored Security Awareness Training
Effective security awareness training programs must be meticulously designed to resonate with the specific cultural context of the organization. For example, a program designed for a hierarchical organization in a collectivist culture will differ significantly from one designed for a flat, individualistic organization. Consider a hypothetical example: a technology company with a predominantly young, tech-savvy workforce will respond well to interactive training modules and gamified challenges, unlike a more traditional, older workforce that might prefer in-person workshops and clear, concise instructions.
The training materials should also be presented in the employees’ preferred language and incorporate culturally relevant scenarios and examples to increase engagement and comprehension. This ensures that the information is not only accessible but also relatable and relevant to the employees’ daily lives.
Comparing and Contrasting Training Methods for Diverse Cultures
A multinational corporation, for instance, might employ a diverse workforce spanning various cultural backgrounds. While some cultures might readily accept direct feedback and assertive training styles, others might find these approaches confrontational and ineffective. For cultures valuing indirect communication, training should emphasize subtle cues and collaborative learning. For example, training for a collectivist culture might focus on the importance of teamwork and shared responsibility in maintaining security, whereas training for an individualistic culture might highlight personal accountability and the benefits of individual security practices.
Using diverse training methods—such as videos, interactive simulations, and role-playing exercises—can cater to different learning styles and preferences across various cultural groups. The key is to provide multiple avenues for information absorption and ensure that all employees feel comfortable participating.
Cultural Nuances Affecting Understanding and Retention of Security Information
Cultural norms significantly impact how individuals process and retain information. For instance, high-context cultures (where much of the communication is implicit) may require more nuanced and indirect training approaches than low-context cultures (where communication is direct and explicit). Similarly, differing levels of risk tolerance across cultures influence how seriously employees take security threats. A culture with a higher tolerance for risk might require more compelling and persuasive training materials to drive behavioral change compared to a risk-averse culture.
Furthermore, the preferred communication channels—email, face-to-face meetings, or online forums—also vary across cultures and should be considered when disseminating security information. Understanding these nuances is crucial for creating training that is not only effective but also respectful and inclusive of all employees.
Culture’s Role in Incident Response
Effective incident response isn’t just about technical proficiency; it’s deeply intertwined with an organization’s culture. How a company reacts to a security breach – from initial detection to post-incident analysis – is significantly shaped by its values, communication styles, and power structures. Ignoring cultural nuances can hinder response effectiveness, leading to delayed mitigation, increased damage, and reputational harm.
Understanding and adapting to these cultural factors is paramount for building a resilient security posture.Cultural differences impact every stage of incident response. For example, a hierarchical culture might prioritize reporting through formal channels, potentially delaying the identification of critical issues. Conversely, a more egalitarian culture may encourage quicker, informal communication, but this could lead to inconsistencies in information flow.
These differences necessitate a flexible and culturally sensitive approach to incident handling.
Best Practices for Incident Response Across Cultures
Organizations must tailor their incident response plans to reflect the specific cultural contexts within their workforce and stakeholder groups. This involves understanding communication preferences (direct vs. indirect, formal vs. informal), decision-making processes (centralized vs. decentralized), and levels of risk tolerance.
For instance, a plan might include multiple communication channels (email, instant messaging, phone calls) to accommodate diverse preferences. Furthermore, training materials should be translated and adapted to ensure accessibility and understanding across different linguistic and cultural backgrounds. Regular cultural sensitivity training for incident response teams is crucial. This training should cover topics like cross-cultural communication, conflict resolution, and ethical considerations in a global context.
The Importance of Open Communication and Trust in Incident Handling
Open communication and trust are the cornerstones of effective incident response, regardless of cultural background. However, building and maintaining this trust requires a deliberate effort. In high-context cultures (where meaning is often implicit), clear and concise communication is vital to avoid misunderstandings. In low-context cultures (where meaning is explicitly stated), building trust may require more time and effort to establish rapport.
Transparency is key; stakeholders, regardless of their cultural background, need to be kept informed about the incident, the response efforts, and the ongoing investigation. This transparency fosters trust and minimizes the spread of misinformation and rumors. Establishing clear reporting procedures and providing regular updates, tailored to different audiences and communication styles, is essential.
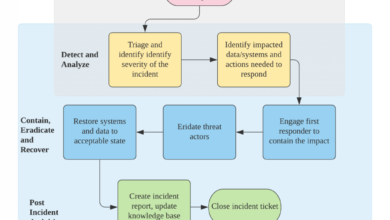
A Step-by-Step Guide for Handling Security Incidents Considering Cultural Sensitivities
A culturally sensitive incident response process requires a structured approach. Here’s a possible framework:
- Preparation: Develop a comprehensive incident response plan that incorporates cultural considerations. This includes identifying key stakeholders from diverse backgrounds, defining communication protocols for each group, and establishing clear escalation paths. Consider translating key documents and training materials into relevant languages.
- Detection and Analysis: Ensure that detection systems are sensitive to potential cultural biases that might impact threat identification. For example, certain types of attacks might be more prevalent in specific regions or cultures.
- Containment and Eradication: Implement containment and eradication strategies that minimize disruption and consider the unique needs of different user groups. This might involve providing customized support or resources to affected individuals.
- Recovery and Remediation: The recovery process should be tailored to the cultural context. This includes providing appropriate communication and support to affected individuals and ensuring that systems are restored in a way that respects cultural norms and values.
- Post-Incident Activity: Conduct a thorough post-incident review that analyzes the effectiveness of the response and identifies areas for improvement. This review should include feedback from stakeholders across different cultural backgrounds.
Building a Security-Conscious Culture
Building a security-conscious culture isn’t a quick fix; it’s a long-term investment requiring consistent effort and commitment from all levels of an organization. It’s about shifting the mindset from security as an afterthought to an integral part of daily operations, a shared responsibility woven into the fabric of the company. This requires a fundamental change in how people perceive and interact with security protocols.A strong security posture is built on a foundation of shared understanding and proactive engagement.
It’s not enough to simply implement technical controls; employees must understandwhy* these controls are in place and how they contribute to the overall security of the organization. This shared understanding fosters a sense of collective responsibility and empowers individuals to actively participate in maintaining a secure environment.
Key Cultural Elements Contributing to Strong Security
Several key cultural elements contribute significantly to a robust security posture. These elements work synergistically, reinforcing each other to create a truly security-conscious environment. A lack in any one area can significantly weaken the overall effectiveness of the security program.
- Open Communication: A culture of open communication encourages employees to report security incidents and concerns without fear of retribution. This transparency is crucial for early detection and response to threats.
- Accountability: Clearly defined roles and responsibilities, coupled with a system of accountability, ensure that everyone understands their contribution to security and the consequences of neglecting their duties. This fosters a sense of ownership and responsibility.
- Continuous Learning: Regular security awareness training and ongoing education keep employees informed about the latest threats and best practices. This ensures that security knowledge remains current and relevant, preventing complacency.
- Trust and Respect: A culture of trust and respect is essential for fostering collaboration and open communication. Employees are more likely to report issues and participate in security initiatives when they feel valued and heard.
- Positive Reinforcement: Recognizing and rewarding employees for their contributions to security strengthens positive behaviors and encourages others to follow suit. This can be as simple as public acknowledgment or more formal reward programs.
Framework for Cultivating a Security-Conscious Culture
Cultivating a security-conscious culture is a multifaceted process that requires a structured approach. A successful framework should address key areas, starting with leadership commitment and extending to employee engagement and continuous improvement.
- Leadership Buy-in: Executive sponsorship is paramount. Leaders must actively champion security initiatives, setting the tone from the top and allocating the necessary resources. Their visible commitment sends a clear message that security is a priority.
- Risk Assessment and Prioritization: A thorough risk assessment helps identify the most critical vulnerabilities and prioritize security efforts accordingly. This ensures that resources are allocated effectively to address the most significant threats.
- Security Awareness Training: Regular, engaging, and tailored security awareness training is crucial. This training should not only educate employees on security policies and procedures but also foster a sense of personal responsibility.
- Incident Response Plan: A well-defined and regularly tested incident response plan is essential for mitigating the impact of security breaches. This plan should Artikel clear procedures for identifying, containing, and recovering from incidents.
- Continuous Monitoring and Improvement: Security is an ongoing process, not a one-time event. Regular monitoring, evaluation, and adjustments are crucial to ensure the effectiveness of security measures and adapt to evolving threats.
Leadership Commitment’s Influence on Security Best Practices Adoption
Leadership commitment significantly influences the adoption of security best practices. When leaders visibly prioritize security, it creates a ripple effect throughout the organization. For example, if the CEO publicly champions a new security initiative, it sends a clear message to all employees that security is a top priority, encouraging greater participation and adherence to security policies. Conversely, a lack of leadership support can lead to apathy and a diminished commitment to security best practices.
This can be seen in organizations where security is viewed as a cost center rather than a strategic investment, leading to inadequate resources and a weaker security posture. Real-world examples include companies like Google, known for their robust security culture fostered by strong leadership commitment, contrasted with smaller organizations where security often takes a backseat due to limited resources and a lack of executive prioritization.
Cultural Differences in Security Policies and Procedures
Security policies and procedures, while crucial for protecting organizational assets, aren’t universally effective. Their success hinges significantly on how well they align with the prevailing organizational culture. A policy perceived as overly restrictive or irrelevant in one culture might be readily accepted and followed in another. Understanding these cultural nuances is paramount for building a truly robust security posture.Cultural factors significantly influence the effectiveness of security policies and procedures.
For example, a highly hierarchical culture might readily accept top-down security directives, while a more egalitarian culture might require a more collaborative and participatory approach to policy implementation. Similarly, a culture that values individual autonomy might resist stringent access controls, while a culture emphasizing collective responsibility might find such controls less intrusive. Ignoring these cultural differences can lead to widespread non-compliance, rendering even the most sophisticated security measures ineffective.
Adapting Security Policies to Different Cultural Contexts
Adapting security policies requires a deep understanding of the specific cultural values and norms within an organization. This involves more than simply translating documents; it requires a thoughtful consideration of how policies are communicated, enforced, and perceived by employees from diverse backgrounds. Effective adaptation often involves using culturally sensitive language, providing training materials in multiple languages, and incorporating cultural feedback into the policy development process.
For example, a policy requiring regular password changes might be better received if accompanied by clear explanations of the rationale and practical guidance on creating strong, memorable passwords, tailored to the specific technological literacy of the workforce. Similarly, a policy emphasizing data privacy might be more impactful if framed within the context of existing cultural values related to trust and confidentiality.
Examples of Culturally Adapted Security Policies
The following table illustrates how security policies and procedures might differ across three hypothetical company cultures: a highly hierarchical Japanese corporation, a collaborative Scandinavian startup, and a results-oriented American corporation. These are generalizations, and actual practices will vary within each cultural group.
| Company Culture | Policy | Procedure | Effectiveness |
|---|---|---|---|
| Highly Hierarchical Japanese Corporation | Strict access controls, top-down enforcement of security protocols. Emphasis on confidentiality and adherence to rules. | Regular security audits conducted by senior management. Clear chain of command for reporting security incidents. Formal training sessions with mandatory attendance. | Generally high, due to strong emphasis on authority and compliance. However, potential for suppressed reporting of issues due to fear of repercussions. |
| Collaborative Scandinavian Startup | Emphasis on employee empowerment and shared responsibility for security. Focus on education and awareness rather than strict rules. | Informal security training integrated into daily workflows. Open communication channels for reporting security incidents. Collaborative problem-solving approach to security breaches. | High, due to employee buy-in and proactive approach. However, may require more consistent reinforcement and clear escalation paths for serious incidents. |
| Results-Oriented American Corporation | Clear metrics for security performance, emphasis on efficiency and risk mitigation. Focus on accountability and consequences for non-compliance. | Regular security awareness training with measurable outcomes. Incentivized reporting of security incidents. Use of technology to automate security processes. | High, driven by accountability and clear expectations. However, may lead to a culture of risk aversion that stifles innovation if not properly managed. |
Measuring the Effectiveness of Security Culture
Gauging the success of security culture initiatives isn’t simply about ticking boxes; it’s about understanding if your efforts are truly translating into a more secure organization. Effective measurement requires a multi-faceted approach, combining quantitative data with qualitative insights to paint a complete picture of your security posture.Effective measurement requires a multifaceted approach, combining quantitative data with qualitative insights to build a comprehensive understanding of your security posture.
This involves tracking key metrics, conducting regular assessments, and actively seeking employee feedback. By combining these methods, organizations can gain a realistic view of their security culture’s effectiveness and identify areas for improvement.
Metrics for Evaluating Security Culture Initiatives
Several key performance indicators (KPIs) can be used to assess the effectiveness of security culture initiatives. These metrics provide quantifiable data to demonstrate progress and identify areas needing attention. For example, a decrease in phishing email click rates signifies improved user awareness and training effectiveness. Similarly, a reduction in the number of reported security incidents suggests a stronger security culture is taking root.
Conversely, a high number of reported vulnerabilities indicates potential weaknesses in the culture or processes. The selection of metrics should align with the specific goals and objectives of the security culture program.
Assessing Employee Understanding and Adherence to Security Policies
Understanding employee comprehension and adherence to security policies is crucial for evaluating the effectiveness of security culture programs. This can be achieved through various methods. Regular security awareness training assessments, including quizzes and simulations, provide a direct measure of employee knowledge. Furthermore, analyzing incident reports can reveal patterns of policy violations and pinpoint areas where further training or reinforcement is needed.
Employee surveys and focus groups can offer valuable qualitative insights into employees’ perceptions of security policies, their understanding of the rationale behind them, and any challenges they face in adhering to them. Combining quantitative data from assessments with qualitative feedback from surveys and focus groups provides a more holistic picture of employee understanding and compliance.
Visual Representation of Strong Security Culture and Reduced Security Incidents
Imagine a graph with two lines. The x-axis represents time, and the y-axis represents the number of security incidents. One line, labeled “Security Incidents,” shows a consistently high number of incidents initially, gradually decreasing over time as a strong security culture is implemented. The other line, labeled “Security Culture Strength,” shows a corresponding increase, mirroring the decrease in security incidents.
The two lines demonstrate an inverse relationship; as the strength of the security culture increases, the number of security incidents decreases. The graph could also include data points representing specific initiatives, such as new training programs or policy updates, showing their impact on both lines. This visual representation clearly illustrates the positive correlation between a robust security culture and a reduction in security breaches.
The downward trend of the “Security Incidents” line, coupled with the upward trend of the “Security Culture Strength” line, visually emphasizes the effectiveness of a strong security culture in mitigating security risks.
Addressing Cultural Barriers to Security
Implementing effective security measures across diverse organizations requires understanding and overcoming cultural barriers. These barriers often stem from ingrained beliefs, communication styles, and established work practices that can inadvertently undermine security initiatives. Ignoring these cultural nuances can lead to low adoption rates of security protocols, increased vulnerabilities, and ultimately, higher security risks.Successfully integrating security into a company’s culture requires acknowledging and actively addressing these challenges.
This involves a multi-faceted approach focusing on tailored communication strategies, targeted training programs, and the implementation of culturally sensitive security policies.
Common Cultural Barriers to Security Implementation
Several common cultural factors can hinder the effectiveness of security measures. These include a lack of awareness about security threats, resistance to change, a perception of security measures as overly burdensome or inconvenient, and a lack of trust in security initiatives. In some cultures, a hierarchical structure might hinder open communication about security incidents, while in others, a more informal work environment could lead to inconsistent adherence to security protocols.
Furthermore, language barriers and differing levels of digital literacy can significantly impact the success of security awareness training.
Strategies for Overcoming Cultural Barriers Through Communication and Training
Effective communication is paramount in overcoming cultural barriers to security. This involves tailoring communication materials to resonate with specific cultural groups, utilizing multiple communication channels (e.g., posters, emails, videos, and in-person sessions), and ensuring materials are accessible in multiple languages. Training programs should be interactive, engaging, and culturally relevant, utilizing scenarios and examples that resonate with the target audience.
For instance, training for a primarily visual culture might benefit from more visual aids, while a culture that values storytelling might benefit from narrative-based training modules. Gamification and rewards systems can also incentivize participation and engagement. Furthermore, fostering open communication channels and creating a safe space for reporting security incidents without fear of retribution is crucial for building trust and encouraging proactive security behavior.
Examples of Successful Initiatives Addressing Cultural Challenges in Security
One example of a successful initiative is a multinational corporation that implemented a phased rollout of its security awareness training. Recognizing the diverse cultural backgrounds of its employees, the company tailored the training modules to specific language groups and incorporated culturally relevant scenarios and examples. The phased rollout allowed the company to gather feedback and make adjustments based on employee responses.
This iterative approach ensured that the training was effective and well-received across different cultural groups. Another example involves a financial institution that implemented a security awareness campaign that emphasized the importance of protecting customer data, focusing on the potential reputational and financial consequences of a data breach. By framing security in terms of protecting the company’s reputation and its employees’ jobs, the campaign resonated strongly with employees across various cultural backgrounds.
These examples highlight the importance of adapting security initiatives to the specific cultural context and utilizing strategies that promote engagement and buy-in.
Last Point
Ultimately, building a strong security culture isn’t a one-time project; it’s an ongoing journey that requires consistent effort and adaptation. By understanding the nuances of culture and its impact on security, we can move beyond simply implementing technical solutions to fostering a proactive and resilient security mindset throughout our organizations. Remember, a security-conscious culture isn’t just about preventing breaches; it’s about building a workplace where everyone feels empowered to contribute to a safer environment.
Let’s start building that culture today!
FAQ Explained
What if my company has a very hierarchical culture? How can I promote security awareness?
In hierarchical cultures, communication needs to flow clearly from the top down. Leadership buy-in is crucial. Start with executive sponsorship and cascade security training and messaging through the management chain. Use clear, concise communication and emphasize the importance of security for the organization’s success.
How do I measure the effectiveness of my security culture initiatives?
Track metrics like the number of security incidents, employee participation in training, and the number of security policy violations. Surveys and feedback sessions can also gauge employee understanding and commitment to security practices. Look for a reduction in phishing attempts and improved reporting of suspicious activity.
My employees are resistant to new security measures. What can I do?
Address concerns directly through open communication and feedback sessions. Explain the “why” behind the measures, emphasizing the benefits for both the individual and the organization. Pilot programs and phased rollouts can ease the transition and address concerns proactively. Focus on training and education to build understanding and acceptance.