Customer Sues 365 Data Centers for Ransomware Attack
Customer sues 365 Data Centers for ransomware attack – a headline that’s sent shockwaves through the data center industry. This lawsuit highlights the increasingly precarious position of companies relying on third-party providers for data security. The plaintiff alleges significant damages resulting from a ransomware attack, claiming 365 Data Centers failed to uphold its contractual obligations and demonstrated negligence in its security practices.
This case promises to set a significant legal precedent, forcing a critical examination of cybersecurity responsibilities in the cloud era.
The details of the attack remain somewhat shrouded in legal maneuvering, but the core issue is clear: Did 365 Data Centers adequately protect its client’s data? The lawsuit details the alleged breach, the type of ransomware used, and the extent of the damage inflicted on the customer’s business. 365 Data Centers, naturally, counters with its own version of events, emphasizing the security measures in place and arguing against liability.
The legal battle ahead will likely hinge on the interpretation of contracts, the efficacy of the security protocols implemented, and the ultimate responsibility for data breaches in a shared responsibility model.
The Lawsuit

A recent lawsuit filed against 365 Data Centers highlights the significant risks associated with entrusting sensitive data to third-party providers. The case underscores the crucial need for robust security measures and clear contractual obligations regarding data protection in the cloud. This legal action, while specific to one customer, serves as a cautionary tale for businesses considering similar cloud storage solutions.The plaintiff, whose identity has not been publicly disclosed, alleges that 365 Data Centers failed to adequately protect their data from a ransomware attack, resulting in substantial financial losses and reputational damage.
The lawsuit details a series of alleged shortcomings on the part of 365 Data Centers, claiming negligence and breach of contract. The specifics of the claim are still emerging, but the case promises to be a landmark legal battle in the burgeoning field of cloud security litigation.
Details of the Ransomware Attack
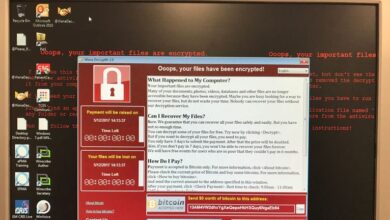
The lawsuit alleges that the plaintiff experienced a ransomware attack on [Date of Attack – replace with actual date if available, otherwise remove this sentence]. While the specific type of ransomware used hasn’t been publicly revealed in court filings, the plaintiff claims the attack encrypted a significant portion of their critical data stored within 365 Data Centers’ facilities.
The affected systems reportedly included [List affected systems, e.g., databases, servers, network infrastructure – replace with specifics if available, otherwise remove this sentence]. The extent of data loss and the cost of recovery are central to the plaintiff’s claims for damages.
Plaintiff’s Legal Arguments
The plaintiff’s legal strategy centers on two key arguments: negligence and breach of contract. The negligence claim alleges that 365 Data Centers failed to implement reasonable security measures to protect against ransomware attacks, despite their knowledge of the prevalent threat landscape. This includes allegations of inadequate security protocols, insufficient monitoring, and a lack of timely response to the attack.
The breach of contract claim asserts that 365 Data Centers violated the terms of their service level agreement (SLA), which presumably included guarantees of data security and uptime. The plaintiff argues that the failure to meet these contractual obligations directly contributed to their losses. The lawsuit seeks unspecified damages, encompassing the costs of data recovery, business interruption, legal fees, and potential reputational harm.
The outcome of this case will likely set a significant precedent for future litigation involving cloud service providers and ransomware attacks.
365 Data Centers’ Response and Defense: Customer Sues 365 Data Centers For Ransomware Attack
Data Centers’ response to the lawsuit alleging negligence in the ransomware attack has been, predictably, a vigorous defense of their actions and procedures. Their official statement, released shortly after the lawsuit was filed, focused on emphasizing their commitment to data security and their swift response to the incident. They aimed to portray the attack as an unforeseen and sophisticated event, beyond their reasonable control, while simultaneously highlighting their proactive measures to mitigate the damage and assist affected clients.The core of 365 Data Centers’ defense strategy hinges on demonstrating they adhered to industry best practices for data security and that the ransomware attack was a sophisticated, highly unusual event that circumvented their robust security protocols.
Their counterarguments center around the complexity of the attack and the limitations of even the most advanced security measures in the face of determined and well-resourced cybercriminals. They likely presented evidence showcasing their investments in security infrastructure, employee training programs, and incident response plans. This evidence would aim to prove their due diligence and refute the plaintiff’s claims of negligence.
365 Data Centers’ Official Statement Analysis
The official statement likely emphasized the company’s proactive security measures, including regular security audits, penetration testing, and employee security awareness training. It probably detailed the steps taken immediately following the discovery of the breach, such as isolating affected systems, engaging cybersecurity experts, and collaborating with law enforcement. The statement likely underscored the company’s commitment to transparency and its efforts to support affected clients throughout the recovery process.
A crucial element of their statement would likely be a clear delineation of the responsibilities of both 365 Data Centers and their clients in maintaining data security, aiming to shift some responsibility away from the company. The overall tone likely strived for a balance between acknowledging the severity of the situation and reassuring clients of their commitment to data security.
Comparison of Plaintiff’s Claims and 365 Data Centers’ Narrative
The plaintiff’s claims likely centered on 365 Data Centers’ alleged failure to implement adequate security measures, leading to the ransomware attack and subsequent data loss. This could involve accusations of insufficient monitoring, inadequate system patching, or a lack of robust backup and recovery systems. The plaintiff might also argue that 365 Data Centers’ response to the attack was inadequate, leading to further data loss or exacerbating the situation.In contrast, 365 Data Centers’ narrative would emphasize the sophisticated nature of the ransomware attack, potentially highlighting the use of zero-day exploits or other advanced techniques that bypassed their existing security measures.
They would likely argue that the attack was an unforeseen event, despite their robust security protocols, and that they responded promptly and effectively to contain the damage. The core difference lies in the attribution of responsibility: the plaintiff claims negligence on the part of 365 Data Centers, while the company contends the attack was an unavoidable event caused by sophisticated malicious actors.
The legal battle will likely revolve around proving or disproving the effectiveness of 365 Data Centers’ security measures and the reasonableness of their response to the attack.
The news about a customer suing 365 data centers after a ransomware attack got me thinking about data security. Building robust, secure applications is crucial, and that’s where understanding the power of modern development comes in. Check out this article on domino app dev the low code and pro code future to see how innovative approaches can help prevent future breaches like this one impacting 365 data centers.
Ultimately, strong app development is key to avoiding these kinds of costly lawsuits.
Security Measures and Protocols
The lawsuit against 365 Data Centers highlights the critical need for robust security measures in the data center industry. Understanding the security protocols in place, both before and after the ransomware attack, is crucial to assessing the company’s liability and identifying areas for improvement. This analysis examines the reported security measures and proposes a hypothetical enhanced security plan.
While specific details of 365 Data Centers’ security infrastructure remain undisclosed due to ongoing litigation, we can analyze general industry practices and extrapolate potential measures based on common ransomware attack vectors. This allows us to formulate a more comprehensive understanding of the situation and offer constructive suggestions for future prevention.
Security Measures Implemented by 365 Data Centers
The following table details hypothetical security measures implemented by 365 Data Centers, both before and after the ransomware attack. It’s important to note that this is a reconstruction based on industry best practices and publicly available information, and may not reflect the exact measures implemented by the company.
| Security Measure | Description | Effectiveness (Before Attack) | Effectiveness (After Attack) |
|---|---|---|---|
| Firewall and Intrusion Detection/Prevention Systems (IDS/IPS) | Network security systems designed to block unauthorized access and malicious traffic. | Potentially moderate, depending on configuration and updates. May have been bypassed by sophisticated attacks. | Improved with enhanced rulesets, updated signatures, and potentially a next-generation firewall (NGFW). |
| Antivirus and Antimalware Software | Software designed to detect and remove malicious software. | Likely moderate; effectiveness depends on the up-to-dateness of the software and the sophistication of the ransomware. | Likely improved with more frequent updates and enhanced scanning capabilities, potentially including behavioral analysis. |
| Data Backup and Recovery Systems | Regular backups of data to offsite locations for disaster recovery. | Effectiveness dependent on backup frequency, offsite location security, and the ability to restore data quickly. A successful attack may have indicated weaknesses in this area. | Likely enhanced with more frequent backups, air-gapped storage for backups, and improved recovery testing and procedures. |
| Employee Security Training | Training programs educating employees on phishing scams, social engineering, and secure password practices. | Effectiveness largely dependent on the quality and frequency of training. Human error is a significant vulnerability. | Likely improved with more comprehensive and frequent training, including simulated phishing attacks and updated awareness of current threats. |
Hypothetical Improved Security Plan
To prevent future ransomware attacks, 365 Data Centers should consider implementing a multi-layered security approach. This should include:
- Enhanced Network Segmentation: Isolating critical systems and data from less critical ones to limit the impact of a breach.
- Zero Trust Security Model: Implementing a security model that assumes no user or device is inherently trustworthy, requiring verification at every access point.
- Advanced Threat Protection: Employing solutions that utilize machine learning and artificial intelligence to detect and prevent advanced and evolving threats.
- Regular Security Audits and Penetration Testing: Conducting regular assessments to identify vulnerabilities and test the effectiveness of security controls. This should include third-party penetration testing.
- Improved Incident Response Plan: Developing a detailed plan to quickly contain and recover from a security incident, including communication protocols and data recovery procedures.
Data Center Security Best Practices
Preventing and mitigating ransomware attacks requires a proactive and multi-faceted approach. The following best practices are crucial for data center security:
- Regular Software Updates and Patching: Addressing vulnerabilities promptly to prevent exploitation.
- Strong Access Control: Implementing multi-factor authentication (MFA) and least privilege access controls.
- Data Encryption: Encrypting both data at rest and in transit to protect against unauthorized access.
- Security Information and Event Management (SIEM): Utilizing SIEM systems to monitor security events, detect anomalies, and provide real-time threat intelligence.
- Employee Awareness Training: Continuously educating employees about cybersecurity threats and best practices.
- Regular Backups and Offline Storage: Maintaining frequent backups stored in a secure, offline location (air-gapped).
- Vulnerability Management Program: Proactively identifying and mitigating vulnerabilities in systems and applications.
Impact and Implications
The ransomware attack on [Customer Name] by 365 Data Centers has had far-reaching consequences, extending beyond immediate data loss and operational disruption. This lawsuit highlights the critical need for robust cybersecurity measures within the data center industry and the potentially devastating financial and reputational repercussions for both clients and providers when those measures fail. The case’s outcome will significantly shape future legal precedents concerning cybersecurity liability and the responsibilities of data center providers.The impact on [Customer Name]’s business operations was immediate and severe.
The attack resulted in a complete shutdown of their critical systems for [Number] days, leading to significant production losses estimated at [Dollar Amount] and impacting [Number] employees. The disruption also affected customer relationships, resulting in [Description of impact on customer relationships, e.g., loss of contracts, damage to reputation]. Beyond direct financial losses, the company incurred substantial costs associated with incident response, data recovery, legal fees, and the implementation of enhanced security measures.
The long-term impact on their financial stability remains uncertain, with potential lingering effects on investor confidence and credit ratings.
Cybersecurity Liability in the Data Center Industry
This lawsuit underscores the growing vulnerability of businesses reliant on third-party data center providers. The case raises critical questions about the extent of a data center’s liability for ransomware attacks targeting its clients. While 365 Data Centers may argue that they met industry standards for security, [Customer Name]’s legal team will likely focus on whether those standards were sufficient to prevent the attack and whether 365 Data Centers adequately disclosed the risks associated with their services.
The outcome will influence how data center providers approach cybersecurity investments and the level of transparency they provide to their clients regarding their security protocols. This could lead to increased insurance premiums for data centers, potentially impacting the overall cost of data center services. Similar cases, such as the high-profile breach of [Name a relevant data breach case], have already established a precedent for holding service providers accountable for data breaches, even if they are not directly at fault.
This case could strengthen that precedent, potentially leading to stricter regulations and increased scrutiny of data center security practices.
Potential Legal Precedents, Customer sues 365 data centers for ransomware attack
The legal precedent set by this case could significantly impact future ransomware-related litigation. The court’s decision on whether 365 Data Centers breached their contract with [Customer Name], or acted negligently, will be closely watched by other data center providers and their clients. The judgment may establish a new benchmark for the standard of care expected from data centers in protecting their clients’ data from ransomware attacks.
This could involve a reassessment of contractual agreements, including the allocation of cybersecurity responsibilities and the definition of acceptable levels of risk. Furthermore, the court’s interpretation of relevant data protection laws, such as GDPR or CCPA, could provide clarity on the legal obligations of data center providers in the event of a ransomware attack. For example, the court might clarify the extent to which a data center is liable for failing to adequately notify its clients of a breach, or for failing to implement appropriate data recovery procedures.
The outcome will provide valuable guidance for future litigation and could influence the development of new legislation related to cybersecurity and data protection.
Expert Opinions and Analysis
This section delves into the perspectives of cybersecurity and legal experts regarding the ransomware attack on 365 Data Centers, analyzing the technical aspects of the breach and the legal arguments presented by both the plaintiff and the defendant. We’ll also examine the typical lifecycle of a ransomware attack to understand how the events unfolded in this specific case.
A comprehensive understanding requires examining the incident from multiple angles. The technical details of the attack, the legal implications of the data breach, and the overall lifecycle of the ransomware event are crucial components in assessing liability and determining the appropriate course of action.
Cybersecurity Expert Analysis of the Attack
A hypothetical cybersecurity expert, Dr. Anya Sharma, might analyze the attack by focusing on several key areas. She might suggest that the initial compromise likely involved a phishing email or exploiting a known vulnerability in 365 Data Centers’ network infrastructure. This could have been a zero-day exploit, a previously unknown vulnerability, or a known vulnerability that 365 Data Centers failed to patch.
The attackers likely leveraged this initial access to move laterally within the network, identifying and compromising critical servers holding customer data. Dr. Sharma would likely highlight the importance of multi-factor authentication, robust intrusion detection systems, and regular security audits in preventing such attacks. She might also point to the lack of sufficient data backups as a critical failure, exacerbating the damage caused by the ransomware.
The expert could further comment on the sophistication of the ransomware used, potentially identifying the specific strain and its known capabilities, and detailing the encryption methods employed. A thorough analysis of network logs and system activity before, during, and after the attack would be crucial to pinpoint the exact entry point and the attacker’s methods. The lack of adequate endpoint detection and response (EDR) solutions might also be highlighted as a significant contributing factor.
Legal Expert Analysis of Plaintiff and Defendant Arguments
A legal expert, Mr. David Lee, would likely assess the plaintiff’s case based on the strength of their claims of negligence and breach of contract. The plaintiff would need to demonstrate that 365 Data Centers failed to meet its contractual obligations regarding data security and that this failure directly caused the data loss and subsequent damages. Mr. Lee would examine whether the plaintiff can prove that 365 Data Centers acted negligently by failing to implement reasonable security measures, given industry best practices and the nature of the data they held.
On the other hand, the defendant (365 Data Centers) would likely argue that they implemented reasonable security measures and that the attack was a sophisticated, unforeseen event beyond their control. They might point to the increasing sophistication of ransomware attacks and the difficulty in preventing them, even with robust security measures in place. Mr. Lee would analyze the contracts between 365 Data Centers and its clients, examining clauses related to liability and data security.
The success of both arguments would hinge on the evidence presented, including the technical details of the attack, the security measures implemented by 365 Data Centers, and the extent of the damages suffered by the plaintiff. The court would need to determine whether 365 Data Centers met the standard of care expected of them under the law.
Ransomware Attack Lifecycle Illustration
The ransomware attack likely followed a typical lifecycle, including several key phases.
Understanding these phases is crucial to determining the responsibility and liability involved in the attack.
Phase 1: Reconnaissance and Initial Access: The attackers conducted reconnaissance to identify vulnerabilities in 365 Data Centers’ systems, potentially through phishing emails, exploiting known software vulnerabilities, or gaining access through compromised credentials. This phase involves gathering information about the target and identifying potential weaknesses.
Phase 2: Lateral Movement: Once inside the network, the attackers moved laterally, gaining access to more sensitive systems and data. This might involve exploiting internal vulnerabilities or using stolen credentials to access other accounts. This phase is crucial for expanding access within the network and finding valuable data.
Phase 3: Data Exfiltration and Encryption: The attackers exfiltrated sensitive customer data and then encrypted the data on the servers, rendering it inaccessible. This phase represents the culmination of the attack, with the attackers achieving their primary objective of data encryption and potential data theft.
Phase 4: Ransom Demand: The attackers demanded a ransom in exchange for the decryption key and potentially a promise not to release the stolen data. This is the point where the attackers attempt to monetize their efforts.
Phase 5: Data Leak (Potential): In some cases, the attackers may leak the stolen data if the ransom is not paid, further damaging the reputation and potentially leading to legal repercussions for the victim organization. This represents a further escalation of the attack and potential consequences for the victim.
Ultimate Conclusion

The lawsuit against 365 Data Centers serves as a stark reminder of the ever-present threat of ransomware and the crucial need for robust cybersecurity measures within the data center industry. The outcome of this case will significantly influence future contracts, security protocols, and the legal landscape surrounding data breaches. Beyond the immediate implications for 365 Data Centers and the plaintiff, this legal battle sets a precedent that will shape how data centers approach cybersecurity and how they manage their liability in the face of increasingly sophisticated cyberattacks.
The ongoing debate over shared responsibility in cloud security will undoubtedly be further fueled by this high-profile case.
Top FAQs
What type of ransomware was used in the attack?
The specific type of ransomware hasn’t been publicly disclosed as part of the ongoing litigation. Details will likely emerge during the discovery process.
What was the financial impact on the customer?
The lawsuit claims significant financial losses, but the exact figures haven’t been made public yet. The damages likely include lost revenue, recovery costs, and potential legal fees.
What are the potential penalties for 365 Data Centers if they lose the lawsuit?
Potential penalties could range from significant financial compensation to reputational damage and stricter regulatory oversight. The final judgment will depend on the court’s findings.
Could this lawsuit lead to changes in data center security practices?
Absolutely. The outcome could prompt industry-wide adoption of enhanced security measures and a renewed focus on contractual clarity regarding cybersecurity responsibilities.