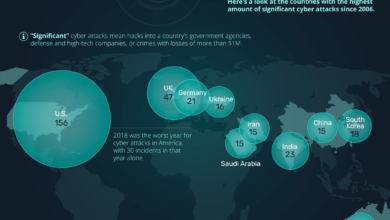
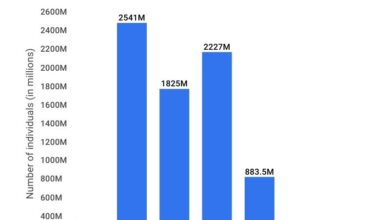
Cyber Attack Automation Turning Lethal
Cyber attack automation turning lethal: It’s a chilling reality. No longer are cyberattacks the domain of lone hackers; sophisticated, automated systems are now capable of unleashing devastating attacks at an unprecedented scale and speed. This isn’t just about annoying spam emails anymore; we’re talking about crippling infrastructure, stealing sensitive data, and causing widespread chaos. The evolution from simple scripts to AI-driven systems has transformed the cyber landscape, making the need for robust defenses more critical than ever.
This escalating threat requires a deeper understanding. We’ll explore the various techniques used in automated attacks, from botnets silently spreading malware to sophisticated phishing campaigns targeting individuals and organizations. We’ll delve into the specific ways automation increases the lethality of attacks, examining the impact on speed, scale, and the difficulty of detection. Finally, we’ll look at the defensive strategies needed to combat this growing menace, exploring the technologies and best practices that can help organizations protect themselves in this increasingly dangerous digital world.
The Rise of Automated Cyberattacks
The digital landscape has witnessed a dramatic shift in the nature of cyberattacks. No longer are attacks solely the domain of highly skilled, individual hackers. Instead, we’re facing a surge in automated attacks, leveraging sophisticated tools and techniques to achieve unprecedented scale and efficiency. This automation, driven by readily available tools and increasingly sophisticated artificial intelligence, presents a significant and evolving threat to individuals, businesses, and nations alike.The evolution of automated cyberattacks is a fascinating story of technological advancement and malicious intent.
It began with simple scripts automating repetitive tasks, such as sending spam emails. These early efforts were crude and easily detected. However, as technology progressed, so did the sophistication of these attacks. The development of botnets, allowing for coordinated attacks from thousands of compromised machines, marked a significant leap. Today, we see AI-driven systems capable of adapting and learning, making them far more difficult to defend against.
These systems can autonomously identify vulnerabilities, exploit them, and even evade detection mechanisms, representing a significant escalation in the threat landscape.
Automation Techniques in Modern Cyberattacks
The effectiveness of modern cyberattacks relies heavily on automation. Several techniques are commonly employed, each with its strengths and weaknesses.
| Technique | Description | Strengths | Weaknesses |
|---|---|---|---|
| Botnets | Networks of compromised computers controlled remotely by attackers. | High scalability, distributed denial-of-service (DDoS) attacks, malware propagation. | Vulnerable to takedown efforts, requires initial compromise of individual machines. |
| Malware Propagation | Automated spreading of malicious software through various methods, including email, phishing, and drive-by downloads. | Rapid infection rate, wide reach, can bypass security measures. | Relies on successful social engineering or exploitation of vulnerabilities, can be detected and blocked. |
| Exploit Kits | Collections of exploits targeting known vulnerabilities in software. | Efficient exploitation of multiple vulnerabilities, rapid compromise of systems. | Relies on outdated or unpatched software, easily countered by timely updates. |
| AI-powered Attacks | Utilizes artificial intelligence to autonomously identify and exploit vulnerabilities, adapt to defenses, and evade detection. | Highly adaptable, difficult to detect and defend against, can learn and improve over time. | Requires significant computational resources, development and maintenance are complex and expensive. |
High-Profile Examples of Automated Cyberattacks
The impact of automated attacks is evident in numerous high-profile incidents. The NotPetya ransomware attack of 2017, for example, caused billions of dollars in damage globally. Spread through a highly automated process, it rapidly infected thousands of systems, crippling businesses and critical infrastructure. Similarly, the Mirai botnet, responsible for several massive DDoS attacks, demonstrated the devastating power of automated attacks on internet services.
These attacks highlight the potential for widespread disruption and financial loss caused by automated cyberattacks. The scale and speed at which these attacks can spread make them particularly dangerous.
Lethality of Automated Attacks
The increasing sophistication and accessibility of automation tools have dramatically escalated the lethality of cyberattacks. No longer confined to the realm of nation-state actors or highly skilled individuals, automated attacks empower a wider range of adversaries, from financially motivated cybercriminals to politically driven groups, to inflict significant damage with far less effort. This amplified lethality stems from a potent combination of speed, scale, and the challenges they pose to detection and response.Automation fundamentally alters the dynamics of a cyberattack, transforming it from a painstaking, resource-intensive process into a highly efficient and scalable operation.
This shift has profound implications for the vulnerability of critical infrastructure and the overall security landscape.
Speed and Scale of Automated Attacks
The speed at which automated attacks can execute is a primary factor contributing to their lethality. Manual attacks, relying on human intervention at each stage, are inherently slow. Automation, however, allows for the simultaneous execution of thousands, even millions, of attacks across a vast network of targets. This massive scale overwhelms traditional security defenses designed for a more measured pace of attack.
Imagine a botnet launching a distributed denial-of-service (DDoS) attack: thousands of compromised devices flooding a target server with traffic simultaneously, rendering it inaccessible within minutes. This contrasts sharply with a manually executed attack, where a single attacker might only manage a few attempts per hour. The sheer volume and speed of automated attacks make them far more effective at disrupting services and causing widespread damage.
Difficulty of Detection and Response
Automated attacks are often designed to be stealthy and difficult to detect. They can leverage sophisticated techniques like polymorphic malware, which constantly changes its signature, evading traditional antivirus software. Furthermore, the scale of these attacks makes it challenging to identify the source and coordinate a timely response. By the time a security team identifies an attack, significant damage may already have been inflicted.
The automated nature of the attack also allows for rapid adaptation and adjustments based on the response of the target system, making it a constant and evolving threat.
Resource Requirements: Automated vs. Manual Attacks
The resources required to launch a successful cyberattack are drastically reduced through automation. A single individual with basic programming skills and access to readily available automation tools can now launch a highly effective attack that would previously have required a large team of experts and significant financial investment. This democratization of attack capabilities is a major concern. Manual attacks, on the other hand, necessitate extensive technical expertise, meticulous planning, and significant time investment.
The lower barrier to entry for automated attacks poses a significant threat to organizations of all sizes.
Hypothetical Scenario: Automated Attack on Critical Infrastructure
Consider a hypothetical scenario targeting a nation’s power grid. A sophisticated, automated malware campaign infects thousands of supervisory control and data acquisition (SCADA) systems across multiple power plants. The malware is designed to gradually increase the load on the generators, causing cascading failures throughout the grid. The automated nature of the attack allows for a slow, incremental approach, making detection difficult.
As the system begins to overload, the malware subtly adjusts its actions to avoid triggering immediate alarms. The resulting widespread power outage could cripple essential services, impacting hospitals, communication networks, and financial institutions, causing billions of dollars in damage and potentially widespread societal disruption. This scenario illustrates the catastrophic potential of large-scale, automated attacks against critical infrastructure. The speed, scale, and difficulty of detection make such attacks incredibly dangerous and highlight the urgent need for robust, proactive cybersecurity measures.
Types of Automated Attacks: Cyber Attack Automation Turning Lethal
The rise of automation in cyberattacks has dramatically shifted the landscape of online security. No longer are attacks solely the domain of highly skilled individuals; sophisticated, readily available tools empower less-skilled actors to launch devastating campaigns. Understanding the different types of automated attacks is crucial for developing effective defense strategies. This section will explore several common categories, outlining their methods, effectiveness, and impact.
Automated attacks leverage software and scripts to perform malicious actions at scale, increasing speed and efficiency compared to manual attacks. This allows attackers to target a larger number of victims simultaneously, maximizing their potential for damage and financial gain. The sheer volume and speed of these attacks often overwhelm traditional security measures, highlighting the urgent need for robust, adaptive defenses.
Ransomware Attacks
Ransomware attacks utilize malicious software to encrypt a victim’s data, rendering it inaccessible. Attackers then demand a ransom payment in exchange for the decryption key. The automation element comes into play through the use of sophisticated malware that can spread rapidly across networks, encrypting files autonomously and often employing techniques to evade detection.
Methods used in ransomware attacks include:
- Exploiting software vulnerabilities: Attackers leverage known vulnerabilities in software to gain initial access to systems.
- Phishing campaigns: Ransomware is often delivered through phishing emails containing malicious attachments or links.
- Malvertising: Compromised advertisements on legitimate websites can deliver ransomware payloads.
- Drive-by downloads: Visiting compromised websites can automatically download and install ransomware.
- Use of botnets: Large networks of compromised computers (botnets) are used to distribute ransomware widely and quickly.
The impact of a successful ransomware attack can be devastating, leading to significant financial losses, data loss, operational disruption, and reputational damage. The NotPetya ransomware attack in 2017, for example, caused billions of dollars in damage globally.
Phishing Attacks
Phishing attacks involve deceptive attempts to acquire sensitive information such as usernames, passwords, and credit card details. Automation enhances the effectiveness of phishing through the use of sophisticated tools that can generate personalized emails at scale, targeting specific individuals or organizations.
Methods employed in automated phishing attacks include:
- Spear phishing: Highly targeted attacks that use personalized information to increase the likelihood of success.
- Email spoofing: Making emails appear to come from legitimate sources to deceive recipients.
- Creating convincing websites: Building fake websites that mimic legitimate sites to steal login credentials.
- Using social engineering techniques: Employing psychological manipulation to trick victims into revealing sensitive information.
- Automated email generation and delivery: Software can generate and send thousands of phishing emails automatically.
The effectiveness of phishing attacks is amplified by automation, allowing attackers to cast a wide net and increase their chances of success. The resulting data breaches can lead to identity theft, financial fraud, and reputational harm.
Cyber attack automation is becoming scarily efficient, leaving even seasoned security experts scrambling. This increased sophistication highlights the urgent need for rapid application development, which is why I’ve been researching the advancements in domino app dev, the low-code and pro-code future , to see how it can help bolster defenses against these ever-evolving threats. Ultimately, faster development cycles are crucial in the arms race against increasingly lethal automated attacks.
Denial-of-Service (DoS) Attacks
DoS attacks aim to disrupt online services by flooding them with traffic, making them unavailable to legitimate users. Automation plays a crucial role in amplifying the scale and impact of these attacks, enabling attackers to launch massive distributed denial-of-service (DDoS) attacks using botnets.
Methods utilized in automated DoS attacks include:
- Using botnets: Large networks of compromised computers are used to generate massive amounts of traffic.
- Employing amplification techniques: Exploiting vulnerabilities in network protocols to magnify the attack’s impact.
- Using specialized DDoS tools: Software tools are readily available to automate the process of launching DDoS attacks.
- Targeting specific services: Attackers may focus on critical services like web servers, DNS servers, or gaming platforms.
The impact of a successful DDoS attack can range from minor inconvenience to significant financial losses and reputational damage, depending on the target and the attack’s duration and intensity.
Data Breaches
Data breaches involve the unauthorized access and exfiltration of sensitive data from an organization’s systems. Automation can significantly accelerate the speed and scale of data breaches, enabling attackers to compromise a large number of systems quickly and efficiently.
Methods used in automated data breaches include:
- Exploiting vulnerabilities: Attackers use automated tools to scan for and exploit vulnerabilities in systems.
- Credential stuffing: Using stolen credentials from other breaches to access accounts on different platforms.
- SQL injection: Injecting malicious SQL code into databases to gain unauthorized access.
- Automated data exfiltration: Using automated tools to transfer stolen data to remote servers.
The consequences of a data breach can be severe, leading to financial losses, legal penalties, reputational damage, and loss of customer trust. The Equifax data breach in 2017, for instance, exposed the personal information of millions of individuals, resulting in significant financial and reputational consequences for the company.
Defending Against Automated Attacks

The rise of automated cyberattacks necessitates a proactive and multi-layered defense strategy. Organizations can no longer rely on reactive measures alone; instead, a robust, preventative approach coupled with effective incident response planning is crucial for survival in this evolving threat landscape. This requires a deep understanding of attack vectors and the deployment of advanced technologies capable of detecting and mitigating automated threats in real-time.
Cyber attack automation is becoming terrifyingly efficient, leaving even seasoned security teams scrambling. To combat this, robust cloud security is crucial, and that’s where understanding solutions like bitglass and the rise of cloud security posture management becomes vital. Ultimately, strengthening our cloud defenses is the only way to stay ahead of these increasingly lethal automated attacks.
Effective defense against automated attacks hinges on a combination of technological solutions and best practices. Technological solutions provide the necessary tools for detection and response, while best practices ensure that these tools are used effectively and that the organization’s overall security posture is strengthened.
Intrusion Detection and Prevention Systems
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are fundamental components of any robust cybersecurity architecture. IDS passively monitors network traffic and system activity for suspicious patterns indicative of an attack, generating alerts when anomalies are detected. IPS, on the other hand, actively intervenes to block or mitigate threats identified by the IDS. These systems can be deployed at various points in the network, from perimeter firewalls to individual host machines, providing comprehensive coverage against automated attacks.
Sophisticated IDS/IPS solutions utilize machine learning algorithms to identify previously unseen attack patterns and adapt to evolving threats. For example, an IDS might detect a distributed denial-of-service (DDoS) attack by identifying a sudden surge in traffic from multiple IP addresses targeting a specific server. An IPS could then automatically block traffic from those identified malicious sources.
Security Information and Event Management (SIEM)
SIEM systems centralize and correlate security logs from various sources across the organization’s IT infrastructure. This aggregation allows security analysts to gain a comprehensive view of the security landscape, identify potential threats, and investigate security incidents more effectively. By correlating events from different sources, SIEM systems can detect complex attack patterns that might go unnoticed by individual security tools.
For instance, a SIEM system might detect a suspicious login attempt followed by unusual file access patterns, indicating a potential compromise. This capability is crucial in the context of automated attacks, which often involve multiple stages and techniques. The ability to correlate these events is key to timely detection and response.
Threat Intelligence Platforms
Threat intelligence platforms provide valuable insights into the latest threats and vulnerabilities. These platforms aggregate information from various sources, including security researchers, government agencies, and private sector organizations, providing actionable intelligence that can be used to proactively defend against attacks. This intelligence can be used to update security tools, prioritize patching efforts, and proactively hunt for threats within the organization’s network.
For example, a threat intelligence platform might alert an organization to a newly discovered vulnerability in a specific software application, allowing them to patch the vulnerability before it can be exploited by automated attack tools.
Best Practices for Enhancing Cybersecurity Posture
Effective defense against automated attacks requires a multi-faceted approach encompassing both preventative measures and incident response planning.
The following are crucial best practices:
- Regular Software Updates and Patching: Promptly patching known vulnerabilities minimizes the attack surface and prevents automated exploits.
- Strong Password Policies and Multi-Factor Authentication (MFA): Robust authentication mechanisms significantly impede automated brute-force attacks.
- Network Segmentation: Dividing the network into smaller, isolated segments limits the impact of a successful breach.
- Regular Security Audits and Penetration Testing: Proactive vulnerability assessments identify weaknesses before attackers can exploit them.
- Employee Security Awareness Training: Educating employees about phishing and social engineering techniques reduces the risk of human error leading to automated attacks.
- Incident Response Planning: A well-defined incident response plan ensures a coordinated and effective response to security incidents.
Layered Security Approach
A layered security approach is essential for effective defense against automated attacks. This involves implementing multiple security controls at different points in the network and system architecture, creating a defense-in-depth strategy.
Imagine a layered security model represented as concentric circles. The outermost layer represents the perimeter security, including firewalls, intrusion detection systems, and web application firewalls. These tools act as the first line of defense, filtering and inspecting traffic before it reaches internal systems. The next layer involves network segmentation, isolating critical systems and data from less sensitive areas.
The innermost layer focuses on endpoint security, including anti-malware software, data loss prevention (DLP) tools, and endpoint detection and response (EDR) solutions, protecting individual devices from threats. Each layer provides an additional level of protection, making it significantly harder for attackers to penetrate the organization’s defenses. If one layer fails, others are in place to mitigate the threat.
The Future of Automated Cyberattacks

The relentless march of technology continues to reshape the landscape of cybersecurity, pushing both offensive and defensive capabilities to unprecedented levels. The future of automated cyberattacks is inextricably linked to advancements in artificial intelligence, machine learning, and other emerging technologies, promising both heightened threats and more sophisticated defenses. This evolution will require a proactive and adaptive approach to cybersecurity, necessitating a constant reassessment of vulnerabilities and strategies.The increasing sophistication of automated attacks will be driven by several key factors.
AI and ML will enable attackers to develop more adaptive and evasive malware, capable of learning from past encounters and modifying its behavior to circumvent traditional security measures. This will lead to a rise in highly targeted and personalized attacks, tailored to exploit specific vulnerabilities within individual systems or networks. Furthermore, the growing accessibility of automation tools will empower less technically skilled individuals to launch complex attacks, democratizing malicious capabilities and significantly expanding the threat landscape.
AI-Driven Attack Strategies
AI’s impact on cyberattacks will extend beyond simple malware adaptation. We can anticipate the emergence of autonomous attack systems capable of independently identifying targets, exploiting vulnerabilities, and executing attacks without direct human intervention. These systems could analyze vast datasets of network traffic, identify weaknesses in security protocols, and autonomously deploy exploits, resulting in significantly faster and more effective attacks.
For example, imagine an AI system capable of identifying a zero-day vulnerability in a specific software application and then immediately deploying a customized exploit across thousands of vulnerable systems, all within a matter of minutes. This level of autonomous operation represents a substantial leap in the sophistication and lethality of automated cyberattacks.
Advancements in Defensive Technologies, Cyber attack automation turning lethal
The escalating threat of AI-driven attacks necessitates equally sophisticated defensive measures. The development of AI-powered security systems is crucial for detecting and responding to these advanced threats. These systems can leverage machine learning algorithms to analyze network traffic and system behavior, identifying anomalies and potential attacks with greater accuracy and speed than traditional signature-based methods. Furthermore, the use of AI in threat intelligence gathering and vulnerability management will allow organizations to proactively identify and mitigate potential risks before they can be exploited.
For example, AI can analyze large datasets of threat intelligence to predict potential attack vectors and proactively patch vulnerabilities, reducing the window of opportunity for attackers.
Ethical Implications of Autonomous Cyberattacks
The increasing autonomy of cyberattacks raises significant ethical concerns. The potential for unintended consequences and escalation is substantial. An autonomous system, operating without direct human oversight, could misinterpret data, leading to unintended collateral damage or escalation of a conflict. Establishing clear lines of accountability in the event of an autonomous attack is also a significant challenge. Furthermore, the potential for misuse of such technology by state-sponsored actors or malicious groups poses a severe threat to global security and stability.
The development and deployment of autonomous cyber weapons necessitates a robust ethical framework, encompassing international cooperation and stringent regulatory oversight to prevent the escalation of cyber warfare and mitigate the risks of unintended consequences. The lack of such a framework could lead to a dangerous arms race in autonomous cyber weaponry, with unpredictable and potentially devastating outcomes.
Final Thoughts

The automation of cyberattacks represents a significant and evolving threat. The speed, scale, and sophistication of these attacks are constantly increasing, demanding a proactive and adaptable approach to cybersecurity. While the technology behind these attacks is advancing, so too are the defensive measures. A layered security approach, combined with robust threat intelligence and proactive incident response planning, is crucial for mitigating the risks.
The future of cybersecurity hinges on our ability to stay ahead of the curve, continuously evolving our defenses to match the ever-changing landscape of automated cyber threats. The stakes are high, and the fight for digital security is far from over.
FAQ Resource
What are some common examples of automated attack tools?
Common tools include Metasploit (for exploiting vulnerabilities), various botnet command-and-control systems, and custom-built malware propagation scripts.
How can small businesses protect themselves from automated attacks?
Small businesses should prioritize basic security hygiene: strong passwords, multi-factor authentication, regular software updates, employee security awareness training, and basic firewall protection.
What role does AI play in both offensive and defensive cybersecurity?
AI powers both attack automation (creating more efficient and targeted attacks) and defensive measures (detecting anomalies and predicting threats).
Is it possible to completely prevent automated cyberattacks?
No, complete prevention is unlikely. The goal is to minimize the impact and likelihood of a successful attack through layered security and proactive measures.