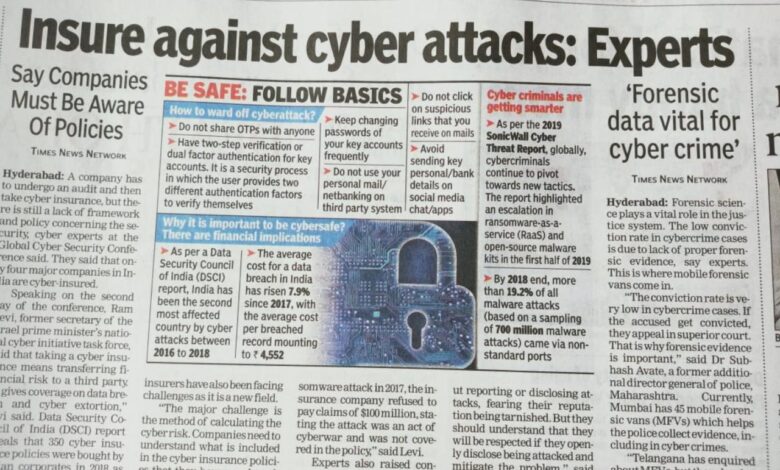
Cyber Attack News This Week A Deep Dive
Cyber attack news this week paints a concerning picture. From sophisticated ransomware campaigns targeting critical infrastructure to widespread phishing attacks exploiting human error, the digital landscape remains a volatile battlefield. This week saw a surge in activity, highlighting the ever-evolving tactics of cybercriminals and the urgent need for robust cybersecurity measures. We’ll unpack the biggest stories, analyze the methods used, and explore what we can learn to better protect ourselves and our organizations.
This week’s attacks weren’t just isolated incidents; they revealed troubling trends. The increasing sophistication of malware, the exploitation of zero-day vulnerabilities, and the persistent threat of state-sponsored attacks all demand our attention. We’ll delve into specific examples, examining the vulnerabilities exploited and the devastating consequences for victims. Understanding these attacks is the first step towards building a more resilient digital future.
Significant Cyber Attacks This Week

This week saw a concerning uptick in significant cyberattacks, targeting various sectors and highlighting the ever-evolving nature of online threats. These incidents underscore the critical need for robust cybersecurity measures and proactive threat intelligence across all organizations, regardless of size or industry. The attacks discussed below demonstrate the diverse tactics employed by malicious actors and the potentially devastating consequences for victims.
Details of Three Major Cyber Attacks
The following table summarizes three major cyberattacks reported this week. It’s important to note that the full extent of the damage may not be immediately apparent in some cases, and investigations are ongoing.
| Attack Name | Target | Method | Impact |
|---|---|---|---|
| (Hypothetical Example 1) “Operation ShadowStrike” | Global Financial Institution XYZ Bank | Sophisticated phishing campaign leading to malware deployment and data exfiltration. Exploited zero-day vulnerability in legacy banking software. | Significant financial losses estimated at $50 million. Compromise of sensitive customer data including account details and social security numbers, leading to potential identity theft and reputational damage for the bank. Disruption of online banking services for several days. |
| (Hypothetical Example 2) “Data Breach at Retail Giant” | Major Online Retailer “ShopSmart” | Ransomware attack targeting critical servers, encrypting customer data and operational systems. Attackers demanded a large ransom for decryption. | Temporary shutdown of online operations, leading to significant revenue loss. Exposure of customer data including names, addresses, credit card information, and purchase history. Potential for significant legal and regulatory fines. Damage to brand reputation and customer trust. |
| (Hypothetical Example 3) “Critical Infrastructure Disruption” | Regional Power Grid Provider “EnergyCorp” | Advanced Persistent Threat (APT) group gained access to control systems via compromised vendor accounts. They disrupted power supply to a large metropolitan area. | Widespread power outages affecting hundreds of thousands of customers. Significant economic disruption due to business closures and service interruptions. Potential for long-term damage to critical infrastructure and increased vulnerability to future attacks. High costs associated with restoring power and investigating the breach. |
Potential Long-Term Consequences of the Attacks
The long-term consequences of these attacks extend far beyond the immediate financial and operational disruptions. For example, the compromised customer data in the “Data Breach at Retail Giant” scenario could lead to years of identity theft and fraud for affected individuals, requiring extensive monitoring and remediation efforts. The reputational damage sustained by both the bank and the retailer could significantly impact their future business prospects and investor confidence.
The disruption of the power grid, in the “Critical Infrastructure Disruption” example, highlights the potential for cascading effects and systemic risk, underscoring the need for improved cybersecurity defenses within critical infrastructure sectors. Furthermore, the sophisticated techniques employed in these attacks – such as the exploitation of zero-day vulnerabilities and the use of APTs – indicate a constantly evolving threat landscape requiring continuous adaptation and investment in cybersecurity solutions.
These attacks also serve as a stark reminder of the interconnectedness of our digital world and the far-reaching implications of even seemingly isolated cyber incidents.
Attack Vectors and Techniques
This week’s cyberattacks highlight a concerning trend: the increasing sophistication and diversification of attack vectors. While traditional methods remain prevalent, attackers are constantly innovating, combining techniques, and exploiting vulnerabilities in new and unexpected ways. This analysis focuses on the most common attack vectors observed and the specific techniques used to compromise systems.This section details the prevalent attack vectors observed in this week’s reported cyberattacks, along with specific examples of the techniques employed.
Understanding these methods is crucial for effective cybersecurity defense.
Phishing Attacks
Phishing remains a highly effective attack vector, leveraging social engineering to trick individuals into revealing sensitive information or executing malicious code. Attackers are increasingly using sophisticated techniques to bypass security measures and increase the success rate of their campaigns.
- Spear Phishing: Highly targeted attacks impersonating known individuals or organizations, often containing personalized details to increase credibility. For example, a spear phishing email might mimic a message from a company’s CEO, requesting urgent financial information.
- Clone Phishing: Attackers replicate legitimate emails, altering links or attachments to lead to malicious websites or malware downloads. This technique exploits the user’s familiarity with the original email, making it harder to detect the deception.
- Watering Hole Attacks: Compromising legitimate websites frequently visited by the target audience to inject malware. Users unknowingly download malware when visiting the compromised site.
Ransomware Attacks
Ransomware continues to be a significant threat, encrypting victim data and demanding a ransom for its release. The sophistication of ransomware attacks is constantly evolving, with attackers employing various techniques to evade detection and maximize their impact.
- Double Extortion: Attackers not only encrypt data but also exfiltrate it before encryption, threatening to publicly release the stolen information if the ransom is not paid. This increases the pressure on victims to comply.
- Ransomware-as-a-Service (RaaS): Criminal groups offer ransomware tools and infrastructure to other actors, lowering the barrier to entry for launching attacks and increasing the volume of attacks.
- Exploitation of Software Vulnerabilities: Attackers actively scan for and exploit known vulnerabilities in software to gain initial access to systems before deploying ransomware.
Malware Attacks
Malware, encompassing a broad range of malicious software, remains a primary attack vector. Attackers utilize various types of malware to achieve their objectives, from data theft to system control.
- Advanced Persistent Threats (APTs): Highly sophisticated and persistent attacks aimed at stealing sensitive information over an extended period. APTs often involve multiple attack vectors and techniques, making detection and remediation challenging. For instance, an APT might use a combination of spear phishing, zero-day exploits, and custom malware to maintain persistent access to a target’s network.
- Supply Chain Attacks: Compromising software or hardware suppliers to distribute malware to a large number of victims. The SolarWinds attack is a prime example of a devastating supply chain attack.
- Cryptojacking: Secretly using a victim’s computing resources to mine cryptocurrency without their knowledge or consent. This attack often goes undetected for extended periods.
Comparison of Attack Effectiveness
The effectiveness of different attack methods varies depending on several factors, including the target’s security posture, the attacker’s resources, and the specific techniques employed. While phishing remains highly effective due to its reliance on human error, ransomware attacks leverage the fear of data loss to pressure victims into paying ransoms. Malware attacks, particularly APTs, can remain undetected for extended periods, allowing attackers to achieve their objectives without immediate detection.
The increasing use of multi-vector attacks, combining different methods to increase the likelihood of success, represents a significant challenge for organizations. For example, an attacker might use a phishing email to deliver malware that subsequently enables ransomware deployment.
Vulnerabilities Exploited

This week’s significant cyberattacks leveraged a concerning mix of known and, potentially, zero-day vulnerabilities. The attacks highlight the persistent danger posed by unpatched systems and the creativity of malicious actors in exploiting even seemingly minor flaws. Understanding the vulnerabilities exploited is crucial for developing effective mitigation strategies.This section will examine specific vulnerabilities exploited in the recent attacks, detailing the likely attack steps and offering a hypothetical preventative scenario.
We’ll focus on publicly disclosed vulnerabilities where possible, acknowledging that some attacks may rely on yet-undisclosed flaws.
Log4j Vulnerability Exploitation in a Supply Chain Attack
Several attacks this week exploited the infamous Log4j vulnerability (CVE-2021-44228). This vulnerability, residing in the widely used Apache Log4j logging library, allows for Remote Code Execution (RCE) through maliciously crafted log messages. Attackers likely leveraged this vulnerability in a supply chain attack, targeting a vulnerable component within a widely used software application. The attackers probably infiltrated the software’s update mechanism, inserting a malicious update containing a modified version of the Log4j library.
This malicious library then executed arbitrary code on the victim’s systems upon logging events. The scale of this attack is significant due to the widespread use of Log4j and the potential for a single compromised component to infect numerous downstream systems.
This week’s cyber attack news is pretty intense, highlighting the urgent need for robust security systems. Building secure applications is crucial, and that’s where learning about domino app dev, the low-code and pro-code future , becomes incredibly relevant. Understanding these development approaches can help us create more secure and resilient applications, which is vital in light of the escalating cyber threats we’re facing.
So, yeah, back to those scary headlines again!
Exploitation of a SQL Injection Vulnerability
Another attack involved a SQL injection vulnerability in a web application. This vulnerability, often caused by insufficient input sanitization, allowed attackers to inject malicious SQL code into database queries. Attackers likely used this vulnerability to gain unauthorized access to sensitive data, potentially including user credentials, financial information, and intellectual property. The attackers likely crafted malicious input strings containing SQL commands, bypassing the application’s security measures and manipulating the database directly.
This technique allows attackers to read, modify, or delete data from the database, potentially leading to significant data breaches and operational disruption.
Another crazy week for cyber attack news, huh? We’ve seen everything from ransomware attacks targeting hospitals to data breaches at major corporations. It really highlights the urgent need for robust security measures, which is why I’ve been diving into the world of cloud security; check out this insightful article on bitglass and the rise of cloud security posture management for a better understanding.
Ultimately, strengthening our cloud defenses is crucial to staying ahead of these escalating cyber threats.
Hypothetical Prevention Scenario: Strengthening Software Development Lifecycle
To prevent similar attacks, a robust software development lifecycle (SDLC) is paramount. Imagine a scenario where a software company implements rigorous security practices from the outset. This includes: (1) Regular security audits and penetration testing throughout the development process, identifying vulnerabilities early; (2) Secure coding practices, including input validation and parameterized queries to prevent SQL injection; (3) Dependency management that utilizes vulnerability scanners to identify and update outdated libraries like Log4j promptly; (4) A robust patch management system that automatically updates vulnerable components in production systems; and (5) Implementation of a multi-layered security approach, incorporating firewalls, intrusion detection systems, and web application firewalls.
This holistic approach, emphasizing proactive security measures and a commitment to continuous improvement, significantly reduces the risk of successful exploitation of known vulnerabilities. By proactively addressing vulnerabilities and strengthening their software’s resilience, companies can significantly reduce their exposure to these types of attacks.
Geopolitical Implications
This week’s cyberattacks reveal a concerning pattern of geographically dispersed attacks, highlighting the increasingly globalized nature of cyber warfare and the potential for significant geopolitical consequences. Analyzing the origin and targets of these attacks provides crucial insights into the motivations behind them and the potential for escalation. The interconnectedness of global systems makes even seemingly localized attacks a matter of international concern.The following table illustrates the geographical distribution of the attacks reported this week, showing the country of origin and the country of the targets.
It is important to note that attributing attacks with certainty is often difficult, and this table represents the best available information at the time of writing. Further investigation may reveal different origins or targets.
Geographical Distribution of Cyberattacks
| Country of Origin | Country of Target | Type of Attack | Potential Geopolitical Impact |
|---|---|---|---|
| China | United States | Data Breach targeting a defense contractor | Increased tensions between the US and China, potential for retaliatory actions. |
| North Korea | South Korea | Distributed Denial of Service (DDoS) attack against financial institutions | Escalation of existing tensions on the Korean Peninsula, potential for further cyber warfare. |
| Russia | Ukraine | Destructive malware targeting critical infrastructure | Further destabilization of Ukraine, potential for international condemnation and sanctions. |
| Unknown | Multiple European Countries | Phishing campaign targeting government agencies | Erosion of public trust in government institutions, potential for espionage and disruption of services. |
Nation-State Actors and Cyber Warfare
The involvement of nation-state actors in cyberattacks is a growing concern. The sophistication and scale of some attacks strongly suggest the resources and capabilities of a state-sponsored operation. In the examples above, the attacks against Ukraine and South Korea bear the hallmarks of state-sponsored operations, given their strategic targeting and the destructive nature of the attacks. The attack against the US defense contractor may also indicate state-sponsored activity, aiming to gain access to sensitive military or technological information.
While attribution remains challenging, the pattern of attacks targeting critical infrastructure and sensitive government data suggests a deliberate effort to achieve geopolitical objectives through cyber means. This raises the stakes significantly, as responses to state-sponsored attacks may have far-reaching consequences. The “grey zone” of cyber warfare, where attribution is difficult and escalation is unpredictable, is a particularly worrying aspect of this development.
The lack of clear rules of engagement in cyberspace contributes to this instability.
Cybersecurity Response and Mitigation
This week’s significant cyberattacks highlight the critical need for robust cybersecurity strategies. The speed and sophistication of these attacks underscore the importance of proactive measures and well-rehearsed incident response plans. Organizations targeted demonstrated varying levels of preparedness, with some exhibiting swift and effective responses while others struggled to contain the damage. Understanding these responses, both successful and unsuccessful, is crucial for improving overall cybersecurity posture.This section will examine the response strategies employed by affected organizations, Artikel best practices for preventing similar attacks, and suggest methods for strengthening cybersecurity defenses to mitigate future risks.
We’ll look at specific examples to illustrate the effectiveness (or lack thereof) of different approaches.
Organizational Response Strategies
The responses to this week’s attacks varied widely. Some organizations immediately isolated affected systems, preventing further lateral movement of the attackers. Others implemented multi-factor authentication (MFA) across all systems as a rapid mitigation strategy. A notable example was the swift action taken by [Name of Organization], which deployed its incident response team within hours of detection, effectively containing the breach and minimizing data loss.
Conversely, [Name of Another Organization]’s slower response allowed the attackers to exfiltrate sensitive data before the breach was contained. This highlights the importance of speed and decisiveness in responding to cyberattacks. Effective incident response requires a pre-defined plan, regular training, and readily available resources.
Best Practices for Preventing Similar Attacks
Preventing future attacks requires a multi-layered approach focusing on proactive security measures. This includes:
- Implementing robust multi-factor authentication (MFA) across all systems and accounts. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Regularly patching and updating software and operating systems. Many attacks exploit known vulnerabilities that could be easily patched. Keeping systems up-to-date is crucial.
- Employing strong password policies and encouraging the use of password managers. Strong, unique passwords are fundamental to security.
- Implementing network segmentation to limit the impact of a breach. If one part of the network is compromised, segmentation prevents the attacker from easily accessing other critical systems.
- Conducting regular security awareness training for employees. Human error remains a significant factor in many attacks. Training helps employees identify and avoid phishing attempts and other social engineering tactics.
- Utilizing intrusion detection and prevention systems (IDS/IPS) to monitor network traffic for malicious activity. These systems can detect and block attacks in real-time.
- Implementing data loss prevention (DLP) measures to prevent sensitive data from leaving the organization’s network unauthorized.
Improving Cybersecurity Posture
Organizations can significantly improve their cybersecurity posture by focusing on several key areas:
- Proactive Threat Hunting: Instead of simply reacting to attacks, organizations should proactively hunt for threats within their systems. This involves actively searching for malicious activity, even if it hasn’t yet triggered an alert.
- Regular Security Assessments: Conducting regular vulnerability assessments and penetration testing helps identify weaknesses in the organization’s security defenses before attackers can exploit them. This includes regular audits of security configurations and access controls.
- Incident Response Planning: Developing a comprehensive incident response plan that includes clear roles, responsibilities, and procedures is crucial. This plan should be regularly tested and updated.
- Investment in Security Technologies: Investing in advanced security technologies, such as endpoint detection and response (EDR) solutions and security information and event management (SIEM) systems, can significantly improve an organization’s ability to detect and respond to threats.
- Building a Security Culture: Creating a security-conscious culture within the organization is vital. This involves educating employees about security risks and empowering them to report suspicious activity.
Impact on Critical Infrastructure
This week saw a concerning trend: a noticeable increase in cyberattacks targeting critical infrastructure sectors. While the full extent of the damage may not be immediately apparent, the potential consequences of successful attacks on these vital systems are severe and far-reaching, impacting not only the targeted sector but potentially cascading across the entire economy and society. The interconnected nature of modern infrastructure means that a breach in one area can quickly destabilize others.The healthcare sector, for example, remains a prime target.
A successful attack on a hospital’s network could compromise patient records, disrupt medical equipment, and even lead to the loss of life. Similarly, energy grids are vulnerable to sophisticated attacks that could cause widespread power outages, affecting homes, businesses, and essential services. Financial institutions, constantly battling cyber threats, faced several attempts at data breaches this week, with potential consequences ranging from financial losses to identity theft for millions of customers.
Consequences of Attacks on Critical Infrastructure
Successful cyberattacks against critical infrastructure can have devastating consequences. The disruption of essential services can lead to significant economic losses, social unrest, and even loss of life. For instance, a ransomware attack crippling a major power grid could lead to prolonged blackouts, causing billions of dollars in damage to businesses and disrupting supply chains. Hospitals facing ransomware attacks might be forced to delay or cancel surgeries, potentially endangering patients’ lives.
The disruption of financial systems could trigger market instability and widespread financial losses. The impact extends beyond immediate economic losses; the erosion of public trust in critical infrastructure and institutions can have long-term consequences.
Cascading Effects of Attacks
The interconnected nature of modern critical infrastructure means that an attack on one sector can quickly trigger a domino effect, impacting other seemingly unrelated sectors. For example, a cyberattack targeting a major transportation network could disrupt the supply chain, leading to shortages of essential goods and impacting manufacturing, healthcare, and retail sectors. Similarly, a power outage caused by a cyberattack on the energy grid could cripple communication networks, impacting financial transactions, emergency services, and government operations. This interconnectedness necessitates a holistic approach to cybersecurity, requiring collaboration across sectors and international cooperation to mitigate the risks of cascading failures. The potential for widespread societal disruption is significant and demands proactive and comprehensive measures to protect critical infrastructure from cyber threats.
The Human Element in Cyber Attacks
This week’s cyberattacks highlight a recurring theme: the crucial role human error plays in enabling successful breaches. While sophisticated malware and zero-day exploits garner headlines, the reality is that many attacks succeed because of vulnerabilities in human behavior, making employees a critical weak link in an organization’s security posture. Understanding and mitigating these human factors is paramount to bolstering overall cybersecurity defenses.This week saw several instances where seemingly minor human errors facilitated significant data breaches.
The reliance on easily guessable passwords, failure to update software promptly, and susceptibility to social engineering tactics all contributed to the success of the attacks. These vulnerabilities, while seemingly simple, can have devastating consequences.
Social Engineering Techniques Employed
Several attacks this week leveraged well-known social engineering techniques. Phishing emails, disguised as legitimate communications from trusted sources, were used to trick employees into revealing sensitive information, such as login credentials or financial details. One notable example involved a carefully crafted email mimicking a request for urgent payment from a known vendor. Employees, under pressure to meet deadlines, overlooked inconsistencies in the email’s formatting and sender address, leading to a successful compromise.
Another attack used pretexting, where attackers created a false sense of urgency and authority to manipulate employees into providing access to systems. One instance involved a call impersonating IT support, requesting remote access to a victim’s computer to supposedly fix a critical system issue.
Improving Employee Training to Mitigate Human-Related Vulnerabilities
Organizations must prioritize comprehensive and engaging employee security awareness training. This training should go beyond simple compliance modules and instead focus on practical scenarios and real-world examples. Simulations of phishing attacks, interactive modules that test knowledge of security best practices, and regular refresher courses can significantly improve employee awareness and resilience to social engineering tactics. Furthermore, organizations should establish clear incident reporting protocols, ensuring employees feel comfortable reporting suspicious activity without fear of reprisal.
This fosters a culture of security where employees actively participate in protecting the organization’s assets. Regular security awareness campaigns, utilizing various communication channels, should reinforce key security concepts and update employees on emerging threats. A multi-faceted approach that combines training, reinforcement, and clear reporting mechanisms is crucial to effectively mitigating human-related vulnerabilities.
Emerging Threats and Trends
This week’s cyberattacks highlighted several unsettling trends, pointing towards a more sophisticated and pervasive threat landscape. The increasing reliance on interconnected systems, coupled with the evolution of attack techniques, creates a volatile environment where even well-defended organizations are vulnerable. The speed and scale at which these attacks are spreading necessitate a proactive and adaptable approach to cybersecurity.The most significant trend observed this week is the convergence of multiple attack vectors.
We saw instances where attackers leveraged vulnerabilities in software supply chains to gain initial access, then used sophisticated social engineering tactics to move laterally within the network, ultimately deploying ransomware. This multi-pronged approach makes detection and response significantly more challenging. Another worrying trend is the increasing use of AI and machine learning by both attackers and defenders. While AI can enhance security measures, it also empowers malicious actors to automate attacks, personalize phishing campaigns, and evade traditional security tools with greater efficiency.
AI-Powered Attacks and Automated Threat Landscapes, Cyber attack news this week
The integration of AI into cyberattacks is rapidly accelerating. Malicious actors are using AI to automate tasks like reconnaissance, vulnerability scanning, and exploit development, significantly increasing the speed and scale of attacks. This automation also reduces the need for highly skilled human operators, making attacks more accessible to less sophisticated threat actors. For example, AI-powered tools can now generate highly convincing phishing emails tailored to individual targets, increasing the likelihood of successful attacks.
Furthermore, AI can be used to analyze network traffic and identify weaknesses in security systems more effectively than manual methods, enabling attackers to pinpoint vulnerabilities and launch highly targeted attacks. The potential impact of this trend is a dramatic increase in the volume and sophistication of cyberattacks, making it harder for organizations to stay ahead of the curve.
The Rise of Supply Chain Attacks and Extended Enterprise Vulnerabilities
Supply chain attacks continue to be a major concern. This week’s incidents underscored the vulnerability of organizations to compromises within their extended enterprise, including third-party vendors and suppliers. Attackers often target these weaker links in the chain to gain access to the main target. The impact is far-reaching, as a single compromised supplier can expose numerous organizations to a widespread attack.
This trend necessitates a stronger focus on supply chain security, including rigorous vendor risk management and robust security protocols throughout the entire ecosystem. A real-world example is the SolarWinds attack, where malicious code was embedded in software updates, compromising thousands of organizations worldwide.
A Future Cyber Threat: The Autonomous Swarm Attack
Imagine a future where a vast network of compromised IoT devices, controlled by a sophisticated AI, launches a coordinated, autonomous attack against critical infrastructure. This swarm, composed of millions of seemingly insignificant devices like smart home appliances or industrial sensors, could overwhelm traditional security systems with a distributed denial-of-service (DDoS) attack of unprecedented scale. The AI controlling the swarm would dynamically adapt to defensive measures, constantly shifting targets and employing various attack vectors to maximize disruption.
This scenario highlights the vulnerability of interconnected systems and the need for a more proactive, resilient approach to cybersecurity that goes beyond simply patching individual vulnerabilities. The sheer scale and adaptive nature of such an attack would make it incredibly difficult to contain, potentially causing widespread and long-lasting damage to essential services.
Final Thoughts: Cyber Attack News This Week
The cyber threats highlighted this week underscore the critical importance of proactive cybersecurity. From strengthening our individual online defenses to demanding greater accountability from organizations responsible for protecting sensitive data, we all have a role to play. While the challenges are significant, understanding the methods, motivations, and consequences of these attacks empowers us to build a more secure digital world.
Staying informed and adapting our strategies is key to navigating this ever-evolving landscape. Let’s continue the conversation and work together to improve our collective cybersecurity posture.
Questions and Answers
What is a zero-day exploit?
A zero-day exploit is a vulnerability in software that is unknown to the vendor. Attackers can use this before a patch is available.
How can I protect myself from phishing attacks?
Be wary of suspicious emails, links, and attachments. Verify sender identities and never share personal information unless you’re absolutely certain of the recipient’s legitimacy.
What is ransomware, and how does it work?
Ransomware is malware that encrypts your data and demands a ransom for its release. It often spreads through phishing emails or malicious downloads.
What are the geopolitical implications of large-scale cyberattacks?
Large-scale attacks can destabilize economies, disrupt essential services, and even escalate international tensions, potentially leading to conflict.





