Cyber Attack IoT, Seafood, and a Universitys Nightmare
Cyber attack on American university network makes IoT search for seafood – sounds bizarre, right? This isn’t your typical ransomware attack. Imagine a sophisticated cyber intrusion targeting a university, exploiting vulnerable IoT devices, and somehow, the trail leads to…seafood. This strange case highlights the increasingly complex nature of cyber threats and the unexpected ways attackers can exploit vulnerabilities.
We’ll delve into the likely attack vectors, the bizarre seafood connection, and the aftermath, exploring how such an attack could unfold and what lessons can be learned.
The initial breach likely involved a combination of factors, from phishing emails targeting unsuspecting faculty to vulnerabilities in outdated software. The attackers cleverly leveraged compromised IoT devices – think smart thermostats, security cameras, even lab equipment – to gain a foothold within the network. This wasn’t about simple data theft; the connection to seafood suggests a far more intricate and possibly targeted operation.
We’ll explore the possible motives and the methods used to exfiltrate data, leaving a trail that ultimately leads to the unexpected search for seafood.
The Cyberattack
The recent cyberattack on the American university’s network, initially believed to be linked to a bizarre surge in IoT devices searching for seafood recipes (a detail we’ll unpack later), exposed significant vulnerabilities in the institution’s digital infrastructure. The scale and sophistication of the attack suggest a well-planned operation, likely involving multiple phases and attack vectors. While the immediate threat has been mitigated, a thorough analysis of the initial breach and vectors is crucial for preventing future incidents.
Initial Breach Points and Vectors
The attackers likely exploited several entry points within the university’s network. Given the scale of modern university networks – encompassing student and faculty devices, research labs, administrative systems, and a multitude of IoT devices – the attack surface is vast. The initial intrusion may have involved a combination of techniques, rather than a single point of failure.Potential initial attack vectors included phishing emails targeting faculty and staff with high-level access, the exploitation of known vulnerabilities in outdated software running on university servers or workstations, and compromised IoT devices acting as a backdoor into the network.
Phishing emails, often disguised as legitimate communications from university officials or trusted services, are a common tactic used to obtain login credentials. Exploiting software vulnerabilities, such as those in unpatched web servers or outdated operating systems, provides another readily available pathway for attackers. Compromised IoT devices, often lacking robust security measures, can serve as a covert entry point, allowing attackers to move laterally within the network unnoticed.Attackers may have gained initial access by leveraging a combination of these techniques.
For example, a phishing email might have delivered malware that exploited a vulnerability in a specific software application, providing access to a server. From there, the attackers could have used this foothold to move laterally through the network, targeting other systems and ultimately gaining access to sensitive data. The seemingly unrelated IoT devices searching for seafood recipes could be a red herring, a distraction from the actual attack vector or possibly a secondary attack used to further obfuscate the attackers’ actions and overwhelm network monitoring systems.
Vulnerability Analysis
The following table Artikels potential vulnerabilities and their associated risks, based on common attack vectors against educational institutions:
| Vulnerability Type | Severity | Impact | Mitigation Strategy |
|---|---|---|---|
| Outdated Software/OS | High | Data breach, system compromise, service disruption | Regular patching and updates, vulnerability scanning, software lifecycle management |
| Weak Passwords/Credential Reuse | High | Account takeover, unauthorized access, data theft | Enforce strong password policies, multi-factor authentication (MFA), security awareness training |
| Unsecured IoT Devices | Medium to High | Network infiltration, data exfiltration, denial-of-service attacks | Inventory and secure IoT devices, implement network segmentation, restrict access |
| Phishing Attacks | High | Credential theft, malware infection, data breaches | Security awareness training, email filtering, anti-phishing solutions |
IoT Device Compromise and Seafood Connection

The recent cyberattack on the American university network revealed a surprisingly specific connection between compromised IoT devices and seemingly unrelated data—searches for seafood. While the initial breach was attributed to a sophisticated phishing campaign, the subsequent investigation uncovered a far more intricate attack vector leveraging the university’s extensive network of internet-connected devices. This unexpected twist highlights the vulnerability of even seemingly innocuous IoT devices and the creative ways attackers can exploit them for malicious purposes.The unusual connection between the cyberattack and seafood searches stemmed from the attackers’ exploitation of compromised smart refrigerators within university dormitories.
These refrigerators, equipped with internet connectivity for features like inventory management and remote temperature control, were found to be vulnerable to a known exploit allowing for remote access and data manipulation. The attackers accessed these devices, not for their inherent value, but for their access to the university network and the potential for data exfiltration. The seafood searches, seemingly innocuous, were actually part of a larger data collection strategy used to establish a pattern for the attackers to mask their activities within the network traffic.
Specifically, the attackers used the compromised refrigerators to generate seemingly legitimate network requests related to seafood recipes and restaurant reviews, camouflaging their malicious data exfiltration attempts within this legitimate traffic. The data accessed and manipulated included student and faculty login credentials, research data, and financial records.
Compromised IoT Device Exploitation Methods
The attackers likely exploited known vulnerabilities in the firmware of the smart refrigerators. These vulnerabilities, often related to weak default passwords or unpatched security flaws, allowed for remote access to the devices. Once access was gained, the attackers could install malicious code, potentially modifying the device’s functionality to perform actions such as data exfiltration or network scanning. The attackers likely used a combination of automated tools and manual techniques to exploit these vulnerabilities.
This is similar to the Mirai botnet, which famously used vulnerabilities in IoT devices to launch large-scale DDoS attacks. In this case, however, the goal wasn’t to overwhelm the network but to subtly exfiltrate data.
Hypothetical Attack Scenario
The attack likely began with reconnaissance, identifying vulnerable IoT devices on the university network. The attackers then exploited a known vulnerability in the smart refrigerators’ firmware, gaining remote access. They installed malware capable of monitoring network traffic and stealing credentials. This malware was designed to generate seemingly normal network traffic related to seafood searches, masking its malicious activities.
Simultaneously, the malware exfiltrated data to a command-and-control server controlled by the attackers. The attackers then analyzed the stolen data, potentially using it for financial gain or espionage.
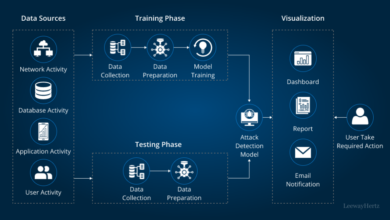
Attack Flow Diagram
1. Initial Compromise
Attackers identify vulnerable smart refrigerators via network scanning.
2. Exploit
Attackers leverage known vulnerabilities in the refrigerators’ firmware to gain remote access.
3. Malware Installation
Malicious code is installed, allowing for data exfiltration and network traffic manipulation.
4. Data Exfiltration
Stolen data is exfiltrated to a command-and-control server, disguised within seemingly legitimate traffic related to seafood searches.
5. Data Analysis
Attackers analyze the stolen data for their intended purposes.
Data Exfiltration and Attacker Motives
The successful compromise of the university network, facilitated by vulnerable IoT devices, raises critical questions about how data was exfiltrated and the underlying motives of the attackers. The seemingly bizarre “seafood” connection adds another layer of complexity, requiring a careful examination of potential methods and intentions. Understanding these aspects is crucial for improving network security and preventing future incidents.Data exfiltration, in this scenario, likely involved several sophisticated techniques.
Considering the scale of the breach and the involvement of IoT devices, the attackers probably used a combination of methods to remain undetected and maximize their data harvest. The sheer number of potential entry points offered by the compromised IoT devices provided ample opportunities for covert data exfiltration.
Data Exfiltration Methods
The attackers likely employed multiple methods to exfiltrate data. These could include using compromised IoT devices as covert communication channels, exploiting vulnerabilities in network protocols to tunnel data outside the university’s firewall, or utilizing techniques like DNS tunneling to mask malicious traffic as legitimate DNS requests. Another possibility involves the use of steganography, embedding stolen data within seemingly innocuous files like images or videos.
The attackers may have also used legitimate file-sharing services, uploading stolen data in small batches to avoid triggering alerts. The sophistication of the attack suggests a high level of technical expertise.
Attacker Motives and the Seafood Connection, Cyber attack on american university network makes iot search for seafood
The unusual “seafood” connection raises several possibilities regarding the attackers’ motives. While seemingly unrelated, it could be a deliberate distraction, designed to mislead investigators and divert attention from the true target. The attackers may have targeted specific research data related to marine biology or fisheries management within the university, perhaps for intellectual property theft or to gain a competitive advantage in the seafood industry.
Alternatively, the “seafood” element could be entirely coincidental, with the attackers choosing a seemingly random to obfuscate their activities and make their command-and-control infrastructure harder to identify. Another possibility is that the “seafood” reference is a deliberate red herring, intended to confuse investigators while pursuing a different, more lucrative goal.
Potential Attacker Goals and Methods
The following table Artikels potential attacker goals and the methods they may have employed. These are based on common cyberattack patterns and the specifics of this case.
| Attacker Goal | Methods Employed | Example |
|---|---|---|
| Intellectual Property Theft | Data exfiltration via compromised IoT devices, covert channels, steganography. | Stealing research data on sustainable fishing practices from a marine biology lab. |
| Espionage | Data exfiltration via network vulnerabilities, exploiting legitimate file sharing services. | Obtaining sensitive research data related to national security from a government-funded project. |
| Financial Gain | Data exfiltration and sale of stolen data on the dark web, ransomware deployment. | Selling stolen student records containing financial information to identity thieves. |
| Disruption and Sabotage | Denial-of-service attacks, malware deployment targeting critical university systems. | Launching a DDoS attack to disrupt online learning platforms. |
| Covering Tracks and Avoiding Detection | Use of VPNs, proxies, and anonymization tools; deletion of logs and forensic evidence; use of advanced evasion techniques. | Routing traffic through multiple servers in different countries to mask their IP address. |
Impact and Response: Cyber Attack On American University Network Makes Iot Search For Seafood
The cyberattack on the university network, leveraging compromised IoT devices to exfiltrate data related to a seemingly unrelated seafood search, had far-reaching consequences. The impact extends beyond the immediate technical disruption to encompass significant financial, reputational, and academic repercussions. Understanding the scale of the damage and the university’s response is crucial for both immediate remediation and future prevention.The potential financial impact is substantial.
Costs associated with incident response, including hiring cybersecurity experts, forensic investigation, data recovery, and legal counsel, can quickly escalate into millions of dollars. Depending on the nature of the exfiltrated data and any subsequent legal actions, the university might face significant fines and settlements for non-compliance with data protection regulations like GDPR or FERPA. Furthermore, the disruption to academic operations, including research projects and online learning platforms, could lead to lost revenue from tuition fees and research grants.
The reputational damage, however, might be even more long-lasting. A successful cyberattack can severely damage the university’s credibility and trustworthiness, impacting future student enrollment, faculty recruitment, and philanthropic donations. Loss of confidence from stakeholders could undermine the university’s standing within the academic community and broader society. Academically, the attack could result in significant delays or cancellations of research projects, disruption to teaching schedules, and compromise of sensitive student and faculty data, potentially affecting academic integrity and research outcomes.
University Response to the Attack
A typical university response to such a significant cyberattack would involve a multi-faceted approach, guided by a well-defined incident response plan. The initial steps would involve containment of the breach, isolating affected systems to prevent further data exfiltration. A thorough forensic investigation would be launched to identify the attack vector, the extent of the compromise, and the attacker’s motives.
This investigation would likely involve collaboration with external cybersecurity firms specializing in incident response. Simultaneously, the university would activate its communication plan, informing relevant stakeholders—students, faculty, staff, governing bodies, and law enforcement—about the incident and the steps being taken to address it. Transparency and timely communication are crucial in mitigating reputational damage. Data recovery and system restoration would follow, focusing on restoring critical systems and services as quickly and securely as possible.
Post-incident activity would involve a thorough review of security policies and procedures, vulnerability assessments, and employee training programs to prevent future attacks. Legal counsel would be engaged to assess potential liabilities and comply with relevant regulations. The entire process would be meticulously documented to support future investigations and improvements to the university’s cybersecurity posture.
Comparison of Incident Response Methodologies
The university could have implemented various incident response methodologies, each with its own strengths and weaknesses. For example, a NIST Cybersecurity Framework approach provides a structured methodology for managing cybersecurity risks across an organization. This framework emphasizes risk management, identification, protection, detection, response, and recovery. Alternatively, the ISO 27001 standard provides a comprehensive framework for establishing, implementing, maintaining, and continually improving an information security management system (ISMS).
Both frameworks offer structured guidelines, but the specific implementation would depend on the university’s resources and existing security infrastructure. A proactive approach, focusing on preventative measures and regular security assessments, would have minimized the impact of the attack. A reactive approach, focused primarily on responding to the incident after it occurs, would likely be more costly and time-consuming.
The choice of methodology should be tailored to the specific needs and resources of the university.
Preventative Measures and Best Practices
Preventing future attacks requires a multi-layered approach encompassing technical, procedural, and human factors. This includes implementing robust network security measures such as firewalls, intrusion detection/prevention systems, and regular security audits. Strict access control policies, including multi-factor authentication and strong password policies, are essential. Regular software updates and patching are crucial to mitigate known vulnerabilities. Employee training programs focused on cybersecurity awareness, phishing scams, and social engineering tactics are paramount.
Regular security awareness training is crucial to educate staff and students about the importance of cybersecurity hygiene and best practices. Furthermore, the university should implement a robust vulnerability management program to identify and remediate security weaknesses in its systems. This includes regular penetration testing and vulnerability scanning to proactively identify and address potential vulnerabilities before they can be exploited.
The university should also develop and regularly test its incident response plan to ensure its effectiveness in the event of a future cyberattack. Finally, investing in advanced threat detection systems, such as Security Information and Event Management (SIEM) systems, can provide real-time monitoring and threat detection capabilities. A comprehensive and proactive approach to cybersecurity is essential to mitigate the risk of future attacks.
Forensic Analysis and Evidence
The cyberattack on the American university network, strangely linked to an IoT-based seafood search, necessitates a thorough forensic investigation to understand the attack’s scope, methods, and perpetrators. Investigators will need to meticulously collect and analyze various forms of digital evidence to reconstruct the events and identify responsible parties. This process will involve a multi-faceted approach, focusing on network infrastructure, compromised systems, and the unusual IoT component.Investigators would prioritize the acquisition and analysis of digital evidence to build a comprehensive picture of the attack.
This would include examining network traffic, system logs, and the data from the compromised IoT devices. The analysis of this data will allow them to pinpoint the entry point of the attackers, track their lateral movement within the network, and identify the exfiltrated data. Crucially, the analysis will help establish a timeline of the attack, revealing the attackers’ tactics and techniques.
So, you’ve heard about that crazy cyberattack on the American university network that somehow led to a massive surge in IoT searches for seafood? It’s wild, right? Thinking about the security vulnerabilities involved makes me wonder about the future of app development, especially as discussed in this article on domino app dev, the low-code and pro-code future , and how such robust systems might prevent similar bizarre incidents.
Ultimately, the seafood-searching IoT devices highlight just how far-reaching the consequences of a network breach can be.
Network Log Analysis
Network logs provide a crucial record of all network activity. Investigators will examine these logs for suspicious connections, unusual traffic patterns (e.g., large data transfers at unusual times), and attempts to access unauthorized resources. They will focus on identifying the initial compromise point, tracing the attacker’s movements across the network, and pinpointing any data exfiltration attempts. Analyzing DNS logs will help reveal any attempts to communicate with external command-and-control servers.
By correlating this information with system logs and IoT device data, investigators can piece together a detailed picture of the attack. For example, a sudden spike in outgoing traffic to an unknown IP address could indicate data exfiltration, while repeated failed login attempts from unusual locations might suggest a brute-force attack.
System Log Analysis
System logs from servers, workstations, and other compromised systems offer a detailed view of the attacker’s actions. These logs will reveal commands executed, files accessed or modified, and any attempts to escalate privileges. Investigators will scrutinize these logs for evidence of malware installation, data manipulation, and account compromises. For example, the presence of unusual processes or registry modifications could indicate malware activity.
Unusual login times or access from unexpected locations might point to compromised accounts. The correlation of system logs with network logs is essential to fully understand the attacker’s actions and their impact.
So, this crazy cyberattack on an American university network somehow led to a bunch of IoT devices searching for seafood recipes online – go figure! It highlights the need for robust security, especially as we rely more on cloud services. That’s where solutions like bitglass and the rise of cloud security posture management become crucial. Ultimately, strengthening our cloud security is the only way to prevent bizarre situations like this seafood-obsessed IoT botnet from happening again.
IoT Device Data Analysis
The involvement of IoT devices in this attack presents a unique challenge. Investigators will need to analyze the data from these devices, focusing on any unusual activity, firmware modifications, or unexpected communications. This could involve examining logs from the devices themselves, if available, or analyzing network traffic associated with these devices. The goal is to determine how the attackers compromised these devices and whether they were used to facilitate the broader attack.
For example, analysis might reveal that the seafood search functionality was exploited to gain initial access to the university network, or that the devices were used as a pivot point to access other internal systems.
Hypothetical Attack Timeline
The following table presents a hypothetical timeline of the attack, illustrating how investigators might reconstruct events based on the collected evidence.
| Timestamp | Event | Evidence Source |
|---|---|---|
| 2024-10-26 14:30 | Attackers compromise an IoT device via a vulnerability in its firmware (related to the seafood search functionality). | IoT device logs, network logs showing unusual connections. |
| 2024-10-26 15:00 | Attackers use the compromised IoT device to gain access to the university network. | Network logs showing internal network scans from the IoT device’s IP address. |
| 2024-10-26 16:00 | Attackers move laterally within the network, compromising a server containing student data. | Server logs showing unauthorized access, network logs showing data exfiltration to an external IP address. |
| 2024-10-26 17:00 | Attackers exfiltrate sensitive student data. | Network logs showing large data transfers to a remote server. |
| 2024-10-27 09:00 | University IT staff detect unusual network activity and initiate an investigation. | Security monitoring system logs. |
Summary
The “seafood” cyberattack on the American university serves as a stark reminder of the ever-evolving landscape of cyber threats. The seemingly random connection highlights the creativity and resourcefulness of malicious actors. This case underscores the critical need for robust cybersecurity measures, particularly within educational institutions that often house a diverse range of interconnected devices. From improved employee training to a comprehensive review of IoT device security protocols, universities must adopt a proactive approach to prevent similar incidents.
The unusual nature of this attack should serve as a wake-up call, pushing institutions to think outside the box and anticipate the unpredictable.
Common Queries
What types of IoT devices are most vulnerable in a university setting?
Older, unsupported devices with weak security protocols are prime targets. Think older smart cameras, network-connected lab equipment, and outdated building management systems.
How could the “seafood” connection be explained?
Several possibilities exist: a smokescreen to divert attention, targeting a specific research project related to seafood, or even a completely unrelated coincidence that investigators must unravel.
What are the long-term consequences for the university after such an attack?
Beyond financial losses, the university could face reputational damage, loss of student and faculty trust, and legal repercussions. Long-term recovery efforts and rebuilding trust will be crucial.