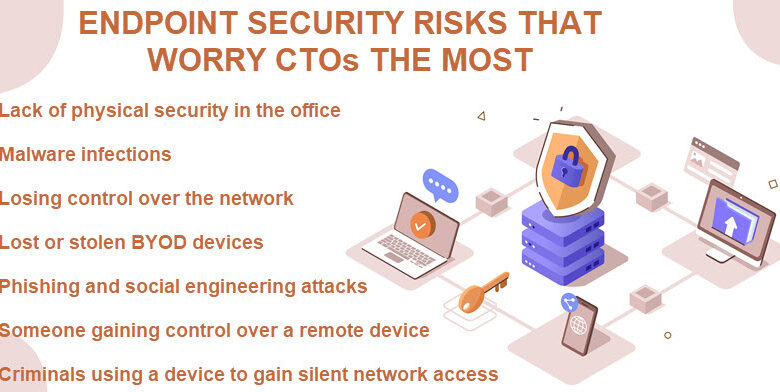
Are You Making Basic Endpoint Protection Mistakes?
Are you making some basic endpoint protection mistakes – Are You Making Basic Endpoint Protection Mistakes? This is a question every business owner, IT manager, and even tech-savvy individual should be asking themselves regularly. We all strive for airtight digital security, but sometimes, the simplest oversights create the biggest vulnerabilities. This post dives into common endpoint protection mistakes, offering practical advice and actionable steps to bolster your defenses.
Let’s face it, nobody wants to be the next headline in a cybersecurity breach story.
From misconfigured firewalls leaving gaping holes in your defenses to neglecting essential software updates and weak password policies, we’ll explore the most prevalent errors and provide clear, concise solutions. Think of this as a cybersecurity checkup—a chance to identify potential weaknesses before they’re exploited. We’ll cover everything from practical firewall rules and robust anti-malware strategies to the importance of user education and data loss prevention (DLP) measures.
Get ready to tighten up your security game!
Insufficient Firewall Configuration

Your endpoint firewall is your first line of defense against malicious network traffic. A poorly configured firewall, however, can leave your system wide open to attacks, rendering other security measures largely ineffective. Many organizations underestimate the importance of meticulous firewall rule management, leading to significant vulnerabilities.Insufficient firewall configuration often stems from a lack of understanding of the nuanced workings of firewall rules, and the implications of different rule ordering and configurations.
This can lead to accidental openings in your security posture, allowing unwanted traffic to access your system.
Common Firewall Misconfigurations, Are you making some basic endpoint protection mistakes
Several common misconfigurations significantly weaken endpoint firewall protection. These include overly permissive default rules, allowing all incoming or outgoing traffic unless explicitly blocked; incorrectly ordered rules, where a less restrictive rule overrides a more restrictive one; and failure to regularly update firewall rules to address emerging threats and vulnerabilities. Furthermore, neglecting to define specific ports and protocols for applications leaves systems vulnerable to unauthorized access.
Finally, a lack of logging and monitoring prevents the timely detection of suspicious activity.
Best Practices for Firewall Rule Configuration
Effective firewall configuration necessitates a multi-faceted approach. Firstly, adopt a “deny by default” policy, explicitly blocking all traffic unless specifically permitted. This minimizes the attack surface significantly. Secondly, prioritize rules carefully, placing more restrictive rules before less restrictive ones. Thirdly, be specific: instead of broad allowances, define rules that specify exact ports, protocols, and IP addresses.
This granularity significantly reduces the risk of unintended access. Regular updates to firewall rules are crucial to address newly discovered vulnerabilities and emerging threats. Finally, enable detailed logging and monitoring to detect and respond to suspicious activity promptly.
Sample Endpoint Firewall Rule Set
Consider this simplified example for a typical endpoint. Remember, this is a
sample* and needs customization based on your specific needs and applications.
| Rule Number | Action | Source IP | Destination IP | Port | Protocol | Description ||—|—|—|—|—|—|—|| 1 | Deny | Any | Any | Any | Any | Default Deny Rule || 2 | Allow | 192.168.1.0/24 | Any | Any | TCP | Internal Network Communication || 3 | Allow | Any | localhost | Any | Any | Local Loopback || 4 | Allow | Any | 8.8.8.8 | 53 | UDP | DNS Queries to Google Public DNS || 5 | Allow | Any | 8.8.4.4 | 53 | UDP | DNS Queries to Google Public DNS || 6 | Allow | Any | 10.0.0.1 | 443 | TCP | HTTPS to Web Server (Example)|| 7 | Allow | 10.0.0.2 | Any | 22 | TCP | SSH Access from Specific IP (Example) |Crucial considerations include: regularly reviewing and updating this table based on application needs and security advisories; using specific IP addresses instead of broad ranges where possible; and implementing strong authentication mechanisms alongside firewall rules.
Permissive vs. Restrictive Firewall Approaches
| Approach | Advantages | Disadvantages | Implementation Considerations |
|---|---|---|---|
| Permissive (Allow by default) | Easier initial configuration, potentially less restrictive for legitimate traffic. | Increased attack surface, harder to manage and audit, difficult to identify unauthorized access. | Requires careful monitoring and regular rule updates; unsuitable for security-sensitive environments. |
| Restrictive (Deny by default) | Reduced attack surface, improved security posture, easier to identify unauthorized access attempts. | More complex initial configuration, potential for blocking legitimate traffic if rules aren’t carefully defined. | Requires meticulous planning and comprehensive understanding of application needs; robust logging and monitoring are essential. |
Lack of Anti-Malware Protection or Outdated Definitions: Are You Making Some Basic Endpoint Protection Mistakes
Ignoring anti-malware protection or failing to keep its definitions updated is a critical oversight in endpoint security. Modern malware evolves rapidly, constantly adapting to bypass older detection methods. A robust and current anti-malware solution is your first line of defense against a wide range of threats, from simple viruses to sophisticated ransomware attacks. Neglecting this fundamental aspect leaves your systems vulnerable to compromise and data breaches.Effective anti-malware software is more than just a signature scanner; it’s a multi-layered defense system.
Choosing the right software and maintaining it properly are key to protecting your endpoints.
Essential Features of Effective Anti-Malware Software
A comprehensive anti-malware solution should incorporate several key features to provide robust protection. These features work in concert to identify and neutralize threats before they can cause damage.
- Real-time Protection: This continuously monitors system activity, blocking malicious code before it can execute. Think of it as a security guard constantly watching for suspicious behavior.
- Heuristic Analysis: This technique goes beyond simple signature matching. It analyzes the behavior of programs to identify malicious activity even if the specific code hasn’t been seen before. It’s like profiling suspects based on their actions rather than just their names.
- Sandboxing: Suspicious files are executed in an isolated environment to observe their behavior without risking the main system. This allows for safe analysis before deciding whether to block or quarantine the file. Imagine a controlled testing lab where potentially dangerous substances are examined before release.
- Web Protection: This feature blocks access to malicious websites and prevents the download of malware from untrusted sources. It acts as a filter, preventing you from entering dangerous online areas.
- Email Protection: Similar to web protection, this safeguards against malware embedded in emails, a common attack vector. It’s like having a spam filter, but for malicious attachments and links.
- Behavioral Monitoring: This observes system processes for unusual activity, such as unauthorized access attempts or data exfiltration. It’s like having an internal security team constantly monitoring the system’s activities.
Maintaining Up-to-Date Anti-Malware Definitions
Regular updates are crucial for maintaining the effectiveness of your anti-malware software. Outdated definitions leave significant gaps in protection, making your systems vulnerable to known threats.
Best practices include configuring automatic updates, checking for updates manually at least weekly, and ensuring the software is allowed to download and install updates without interference. This is like regularly updating a map application on your phone; without updates, you’re navigating with outdated information, increasing the risk of getting lost (or compromised).
Implications of Using Outdated Anti-Malware Definitions
Using outdated anti-malware definitions significantly increases the risk of infection. New malware variants are constantly emerging, and without the latest definitions, your software won’t be able to recognize and block these threats. This can lead to data breaches, system crashes, and significant financial losses. Consider the WannaCry ransomware attack in 2017; many victims were infected because their systems lacked updated security patches and anti-malware definitions.
Types of Malware and Their Mitigation
Effective anti-malware solutions address various malware types.
- Viruses: These self-replicating programs attach themselves to other files and spread rapidly. Anti-malware software detects and removes viruses through signature-based and behavioral analysis.
- Worms: These self-replicating programs spread across networks without needing to attach to other files. Anti-malware’s network monitoring and real-time protection capabilities effectively combat worms.
- Trojans: These disguise themselves as legitimate software to gain access to systems. Heuristic analysis and behavioral monitoring are crucial for detecting Trojans.
- Ransomware: This encrypts files and demands a ransom for their release. Real-time protection, sandboxing, and behavioral monitoring help prevent ransomware infections, while backups mitigate the impact of successful attacks.
- Spyware: This secretly monitors user activity and steals sensitive information. Anti-malware software detects and removes spyware through various techniques, including real-time protection and behavioral analysis.
Weak or Missing Password Policies

Let’s face it, passwords are the gatekeepers to our digital lives. A weak password policy is like leaving the front door unlocked – an open invitation for trouble. Even with robust firewall configurations and up-to-date anti-malware, a lax approach to password management can unravel all your security efforts. This section dives into the common pitfalls of weak password policies and how to build a robust system to protect your data.Weak password policies often stem from a lack of understanding of the real risks involved.
Many organizations and individuals rely on simple, easily guessable passwords, or enforce policies that are too lenient. This creates significant vulnerabilities, making systems susceptible to brute-force attacks, dictionary attacks, and even social engineering. The consequences can range from account breaches and data theft to complete system compromise. The cost of remediation, including financial losses, reputational damage, and regulatory fines, can be substantial.
Common Weaknesses in Password Policies
Common weaknesses include overly short password lengths (less than 12 characters), allowing easily guessable passwords (like names, birthdays, or common words), and lacking complexity requirements (a mix of uppercase and lowercase letters, numbers, and symbols). Many policies also fail to mandate regular password changes, leaving passwords vulnerable for extended periods. Another critical weakness is the lack of enforcement of unique passwords across different accounts.
Reusing the same password across multiple platforms dramatically increases the risk of a widespread breach if one account is compromised.
Best Practices for Creating Strong and Secure Password Policies
A strong password policy starts with understanding the principles of strong password creation. This includes enforcing minimum password length (at least 12 characters, ideally longer), requiring a mix of uppercase and lowercase letters, numbers, and symbols, and prohibiting the use of easily guessable information like personal details or dictionary words. Regular password changes (e.g., every 90 days) should be mandated, along with the requirement for unique passwords for each account.
Consider implementing password complexity scoring systems to provide users with immediate feedback on the strength of their chosen passwords. Furthermore, implementing multi-factor authentication (MFA) adds an extra layer of security, significantly reducing the risk of unauthorized access even if a password is compromised.
A Robust Password Policy Example
A robust password policy might include the following requirements:* Minimum length: 16 characters
Minimum character types
Uppercase letters, lowercase letters, numbers, and symbols Prohibition of dictionary words and personal information
-
Password expiration
Every 90 days
- Unique passwords for each account
- Mandatory use of a password manager
- Account lockout after three failed login attempts
Password Managers vs. Traditional Password Management
Choosing between a password manager and traditional methods significantly impacts security.
Here’s a comparison:
| Feature | Password Manager | Traditional Methods (e.g., written list, note in phone) |
|---|---|---|
| Security | High, if using a reputable manager with strong encryption and security features. | Very low, susceptible to theft or loss. |
| Convenience | High, automatic login and password generation. | Low, requires remembering many passwords. |
| Complexity | High, encourages complex and unique passwords. | Low, often results in simple and repetitive passwords. |
| Cost | May involve subscription fees, but often free options exist. | Typically free, but the cost of a breach can be far higher. |
Failure to Patch Operating Systems and Applications
Ignoring timely patching is a major security oversight. Unpatched systems are like open doors, inviting attackers to exploit vulnerabilities and compromise your entire network. Regular patching is crucial for maintaining a strong endpoint security posture and minimizing your attack surface. Failing to do so leaves your organization vulnerable to devastating consequences, including data breaches, financial losses, and reputational damage.Regular patching ensures that your systems are protected against the latest known vulnerabilities.
These vulnerabilities are constantly being discovered and exploited by malicious actors. By applying patches promptly, you effectively close these security gaps, making it much harder for attackers to gain unauthorized access. This proactive approach is far more effective and cost-efficient than reacting to a breach after it has already occurred.
Patching Schedule Creation and Maintenance
A well-defined patching schedule is essential for effective endpoint security. This schedule should Artikel which systems need patching, what patches need to be applied, and when the patching process will take place. Consider factors like system criticality, user impact, and the severity of the vulnerabilities being addressed when prioritizing patches. Thorough testing in a non-production environment before deploying patches to production systems is also vital to prevent unexpected downtime or functionality issues.
Regular review and updates to the schedule are necessary to adapt to evolving threats and new patch releases. Automated patching tools can significantly streamline this process, reducing manual effort and improving consistency.
Resources for Obtaining Security Patches
Several resources provide security patches for common operating systems and applications. Microsoft provides updates for Windows through Windows Update, while Apple offers updates for macOS and iOS through the App Store and system updates. Linux distributions like Ubuntu and Fedora have their own update mechanisms. Software vendors often release patches through their websites or dedicated update mechanisms.
So you’re worried about making basic endpoint protection mistakes? That’s smart! Securing your apps is crucial, especially with the rapid advancements in development, like what’s discussed in this great article on domino app dev the low code and pro code future. Understanding these new development approaches helps you anticipate potential vulnerabilities and strengthen your overall security strategy, reducing those endpoint risks.
After all, a robust app is only as strong as its weakest security link.
Staying subscribed to security advisories and newsletters from these vendors is a proactive way to stay informed about new vulnerabilities and available patches. It’s also important to utilize reputable patch management software to streamline the process of identifying, downloading, and deploying patches across your entire network.
Exploitation of Unpatched Systems
Imagine a scenario where a company fails to patch a critical vulnerability in its web server software. A malicious actor discovers this vulnerability and uses it to inject malicious code, gaining control of the server. From there, they can access sensitive customer data, install ransomware, or launch further attacks against the company’s internal network. The consequences could include significant financial losses, legal repercussions, and irreparable damage to the company’s reputation. This is a realistic scenario, and many similar attacks have occurred due to a lack of timely patching.
Neglecting User Education and Training
Your endpoint security is only as strong as its weakest link – your users. Even the most robust technical safeguards can be bypassed by a well-crafted phishing email or a socially engineered attack. Investing in comprehensive user education and training is crucial for building a strong security posture. Ignoring this aspect leaves your organization vulnerable to a wide range of threats.
Effective user training isn’t about overwhelming employees with technical jargon; it’s about empowering them to recognize and respond to threats intelligently. This requires a multi-faceted approach that combines interactive learning, real-world examples, and ongoing reinforcement.
Examples of Phishing Scams and Social Engineering Techniques
Phishing scams often mimic legitimate communications, aiming to trick users into revealing sensitive information like passwords, credit card details, or social security numbers. A common example is a seemingly urgent email from a bank or online retailer, requesting immediate action to verify account details or prevent account suspension. The email usually contains a link to a fake website designed to look authentic.
Social engineering, on the other hand, manipulates individuals into divulging confidential data or performing actions that compromise security. This might involve a phone call from someone pretending to be IT support, requesting remote access to a computer under the guise of troubleshooting a problem. Another example is pretexting, where an attacker creates a believable scenario to gain trust and information.
For instance, an attacker might pose as a potential client or vendor to obtain sensitive data.
Designing a Training Program to Address Common Endpoint Security Risks
A comprehensive training program should cover a range of topics relevant to endpoint security. This includes recognizing phishing emails and malicious links, understanding the importance of strong passwords and password management practices, identifying and reporting suspicious activity, and following safe browsing habits. The program should incorporate interactive modules, simulations, and real-world scenarios to engage users and enhance knowledge retention.
Regular refresher courses and simulated phishing attacks can help maintain awareness and improve response times. The training should be tailored to different roles and responsibilities within the organization, addressing specific security risks faced by each group. For example, employees handling financial transactions would require more intensive training on fraud prevention than those in less sensitive roles.
Training Methods, Effectiveness, and Cost
| Training Method | Effectiveness | Cost | Target Audience |
|---|---|---|---|
| Interactive Online Modules | High (engaging, self-paced) | Medium (development costs, platform fees) | All employees |
| In-Person Workshops | Medium-High (face-to-face interaction, Q&A) | High (instructor fees, venue costs, travel) | Small groups, specific roles |
| Simulated Phishing Attacks | High (real-world application, immediate feedback) | Low-Medium (software costs, email distribution) | All employees |
| Short Videos and Tutorials | Medium (easily digestible information) | Low (production costs, online hosting) | All employees |
| Gamified Training | High (engaging, memorable) | Medium-High (game development, platform costs) | All employees, particularly younger generations |
Absence of Data Loss Prevention (DLP) Measures
Data breaches are a constant threat to any organization, regardless of size. The loss of sensitive information can lead to significant financial penalties, reputational damage, and legal repercussions. While firewalls, anti-malware, and strong passwords are crucial, they’re only part of a comprehensive security strategy. A critical missing piece is often a robust Data Loss Prevention (DLP) system.
DLP goes beyond simply blocking threats; it actively monitors and prevents sensitive data from leaving your network, even if it’s done unintentionally.DLP is essential because it provides a proactive approach to data security. It doesn’t just react to attacks; it anticipates and prevents data breaches before they happen. This proactive approach is vital in today’s threat landscape, where sophisticated attackers are constantly seeking ways to exploit vulnerabilities.
A comprehensive DLP strategy can significantly reduce your organization’s risk profile and protect your most valuable asset: your data.
Data Loss Prevention Measures
Implementing effective DLP requires a multi-layered approach. This involves a combination of technical controls, policies, and employee training. A well-rounded strategy considers various vectors for data loss, including accidental disclosure, malicious insider threats, and external attacks.
Data Classification and Access Control
A robust DLP strategy begins with data classification. This involves identifying and categorizing all sensitive data within the organization. This might include customer Personally Identifiable Information (PII), financial records, intellectual property, and trade secrets. Once data is classified, access control measures are implemented to restrict access based on the sensitivity level. This might involve role-based access control (RBAC), where users only have access to the data necessary for their job functions.
Regular audits of access privileges should also be conducted to ensure they remain appropriate. For example, an employee who leaves the company should have their access revoked immediately. This principle of least privilege is paramount in preventing unauthorized data access.
DLP Technology Comparison
Several technologies can be used to implement DLP. The best choice depends on the specific needs and resources of the organization.
- Network-based DLP: This monitors network traffic for sensitive data being transmitted. Strengths include broad coverage and the ability to detect data exfiltration attempts. Weaknesses include potential performance impact and the inability to detect data loss through removable media or cloud services.
- Endpoint DLP: This monitors data on individual devices (computers, laptops, mobile phones). Strengths include granular control and the ability to detect data loss through various channels. Weaknesses include the need for agent deployment on each device and potential resource consumption.
- Cloud-based DLP: This monitors data stored in and transmitted through cloud services. Strengths include scalability and the ability to protect data in various cloud environments. Weaknesses include reliance on cloud service providers’ security measures and potential limitations in monitoring data outside the cloud.
- Database Activity Monitoring (DAM): This focuses on monitoring database activity to detect unauthorized access or data modification. Strengths include precise tracking of database changes and potential for real-time alerts. Weaknesses can include complexity of implementation and the need for specialized expertise.
Choosing the right combination of these technologies depends on factors such as budget, existing infrastructure, and the types of sensitive data being protected. A hybrid approach, combining multiple technologies, often provides the most comprehensive protection. For instance, a company might use network-based DLP to monitor outbound traffic, endpoint DLP to control data on employee devices, and cloud-based DLP to protect data stored in cloud services.
This layered approach helps to create a robust and resilient data security posture.
Inadequate Network Segmentation
Network segmentation is often overlooked in endpoint security strategies, yet it’s a powerful technique for minimizing the impact of breaches. By dividing your network into smaller, isolated segments, you create a layered defense that prevents a compromised device from easily accessing sensitive data or other critical systems. This approach significantly reduces the attack surface and limits the potential damage caused by malware or malicious actors.Network segmentation limits the impact of a successful attack by containing the breach within a specific segment.
Imagine a scenario where a single endpoint is infected with ransomware. If your network isn’t segmented, the malware could spread rapidly across your entire network, encrypting all your data. However, with proper segmentation, the infection would be confined to its own segment, preventing widespread damage. This allows for quicker containment and remediation, minimizing downtime and data loss.
Network Segmentation Strategy for a Typical Office Environment
A typical office environment can benefit from a multi-layered segmentation strategy. We can segment the network based on function and sensitivity of data. For example, a common approach would involve separating the following segments:
- Guest Network: This segment provides internet access for visitors, keeping them isolated from internal resources.
- Untrusted Zone: This segment houses devices like printers and other shared resources that are accessible from the internet. Strict access controls are implemented here.
- Demilitarized Zone (DMZ): This segment hosts publicly accessible servers, such as web servers or email servers, providing an additional layer of protection between the internet and the internal network.
- Internal Network: This segment contains all internal resources, including workstations, servers, and databases. Access to this segment is restricted to authorized personnel.
- Sensitive Data Segment: This highly secured segment houses critical data, such as financial records or customer information. Access is strictly controlled through advanced authentication and authorization mechanisms.
This layered approach allows for granular control over access and data flow, limiting the impact of a security breach. Each segment can have its own security policies, firewalls, and intrusion detection systems, enhancing the overall security posture.
Comparison of Network Segmentation Techniques
Several techniques can be employed for network segmentation. Each offers unique advantages and disadvantages, impacting implementation complexity.
| Technique | Advantages | Disadvantages | Implementation Complexity |
|---|---|---|---|
| VLANs (Virtual LANs) | Cost-effective, easy to implement on existing infrastructure, flexible. | Can be complex to manage in large networks, requires careful planning. | Medium |
| Firewalls | Granular control over network traffic, strong security capabilities. | Can be expensive, requires expertise to configure and manage. | High |
| Software-Defined Networking (SDN) | Highly flexible and scalable, centralized management. | Can be complex to implement and manage, requires specialized skills. | High |
| Micro-segmentation | Very granular control, isolates individual workloads or applications. | Can be complex to manage, requires significant investment in tools and expertise. | High |
The choice of technique depends on factors like budget, network size, and security requirements. Smaller organizations might opt for VLANs, while larger enterprises might prefer SDN or micro-segmentation for more granular control and scalability.
Closing Summary
Securing your endpoints isn’t a one-time fix; it’s an ongoing process requiring vigilance and proactive measures. By addressing the common mistakes Artikeld here – from properly configuring your firewall and maintaining up-to-date anti-malware to implementing strong password policies and investing in user training – you can significantly reduce your vulnerability to cyber threats. Remember, even small improvements in your endpoint security posture can make a huge difference in protecting your valuable data and reputation.
Stay informed, stay vigilant, and stay secure!
Question Bank
What is the difference between a firewall and anti-malware software?
A firewall controls network traffic, blocking or allowing connections based on pre-defined rules. Anti-malware software actively scans for and removes malicious software on your devices.
How often should I update my anti-malware definitions?
Ideally, your anti-malware software should update its definitions automatically and frequently, ideally several times a day. Check your software’s settings to ensure automatic updates are enabled.
What are some examples of social engineering techniques I should be aware of?
Phishing emails, pretexting (pretending to be someone else to gain information), baiting (offering something tempting to trick you), and quid pro quo (offering something in exchange for information) are common social engineering tactics.
What is the best way to choose a strong password?
Use a password manager, and ensure your passwords are long (at least 12 characters), complex (mix of uppercase, lowercase, numbers, and symbols), and unique to each account. Avoid using personal information.





