Cyber Attack on Deloitte Leaks Blue Chip Info
Cyber attack on Deloitte leaks blue chip info – the headline alone sends shivers down your spine, doesn’t it? Imagine the fallout: sensitive client data, potentially including financial records, strategic plans, and confidential communications, exposed to the wrong hands. This wasn’t just a minor breach; this was a significant blow to one of the world’s largest consulting firms, and the repercussions are far-reaching, impacting not only Deloitte’s reputation but also the trust placed in the entire industry.
We’ll delve into the specifics of the attack, exploring the vulnerabilities exploited, the damage inflicted, and the lessons learned – both for Deloitte and for all of us in the digital age.
This post will dissect the incident, examining Deloitte’s security posture before the attack, the nature of the cyberattack itself, the type of data breached, the response and mitigation efforts, and finally, the critical lessons learned and their implications for the future of cybersecurity. We’ll explore potential weaknesses in Deloitte’s security architecture, the attackers’ methods, and the potential legal and financial ramifications for both Deloitte and its clients.
Prepare for a deep dive into a story that highlights the ever-evolving and crucial battle against cyber threats.
Deloitte’s Security Posture Before the Attack

Deloitte, a global leader in professional services, maintains a sophisticated cybersecurity infrastructure, but like any large organization, it faces inherent vulnerabilities. Understanding their security posture before the recent data breach requires examining their known protocols, potential weaknesses, and comparing them to industry best practices. The specifics of their internal security architecture are, understandably, confidential, but public information and industry knowledge provide a framework for analysis.Deloitte’s security likely involved a multi-layered approach, incorporating various technologies and processes designed to detect and prevent cyber threats.
The complexity of their systems, however, presents a significant challenge in maintaining complete security. A single point of vulnerability, even a seemingly minor one, can compromise the entire system.
Deloitte’s Reported Security Measures
Reports suggest Deloitte employed a range of standard security measures, including firewalls to control network access, intrusion detection and prevention systems (IDS/IPS) to monitor network traffic for malicious activity, and data loss prevention (DLP) tools to prevent sensitive data from leaving the network without authorization. They also likely had robust access control mechanisms, such as multi-factor authentication (MFA), to restrict access to sensitive systems and data.
Regular security audits and penetration testing are also standard practice for organizations of their size and reputation. However, the effectiveness of these measures depends on their implementation, maintenance, and ongoing adaptation to evolving threats.
Potential Weaknesses in Deloitte’s Security Architecture
While Deloitte’s security infrastructure was likely extensive, potential weaknesses could have existed. One possibility is insufficient segmentation of networks. If different parts of their network were not adequately isolated, a breach in one area could have allowed attackers to move laterally to access more sensitive data. Another potential weakness could lie in the management of third-party access.
Deloitte works with numerous clients and vendors, and managing the security risks associated with these external connections is a significant challenge. Furthermore, human error remains a constant threat. Phishing attacks, social engineering, or even unintentional mistakes by employees can create vulnerabilities that attackers can exploit. Finally, the sheer volume and complexity of data Deloitte handles presents a challenge for effective monitoring and control.
A lack of sufficient real-time monitoring and analysis capabilities could have allowed a breach to go undetected for a significant period.
Comparison to Industry Best Practices
Compared to other large professional services firms, Deloitte’s security practices were likely in line with, or even exceeding, industry standards. However, the ever-evolving threat landscape necessitates constant vigilance and adaptation. Even the most sophisticated security measures can be circumvented by determined and resourceful attackers. The incident highlights the inherent challenges of balancing security with operational efficiency and the importance of continuous improvement and proactive threat intelligence.
The industry benchmark is always moving, and maintaining a leading-edge security posture requires significant investment and ongoing commitment.
The recent Deloitte cyberattack, exposing sensitive blue-chip data, highlights the urgent need for robust security solutions. Building secure, scalable applications is crucial, and that’s where understanding the future of app development comes in. Check out this article on domino app dev, the low-code and pro-code future , to see how innovative approaches can help prevent similar breaches. Ultimately, strengthening our digital defenses against attacks like the one on Deloitte requires a multi-faceted approach, including secure application development practices.
Nature of the Cyberattack
The precise nature of the cyberattack on Deloitte that leaked blue-chip client information remains shrouded in some secrecy, as details are often withheld for security and legal reasons. However, based on the scale and sophistication of the breach, we can reasonably infer several key aspects of the attack vector, techniques, and timeline. The lack of complete public information necessitates some educated speculation, but by drawing parallels to similar high-profile incidents, a plausible picture can be constructed.The attackers likely employed a multi-stage attack leveraging a combination of techniques.
It’s improbable that a single vulnerability or a simple phishing email was the sole entry point for such a significant data breach. Instead, the attackers probably used a sophisticated, multi-faceted approach.
Attack Vector and Techniques
The most probable attack vector involved a combination of spear-phishing emails targeting high-value employees within Deloitte, coupled with the exploitation of zero-day vulnerabilities or previously unknown weaknesses in Deloitte’s systems. Spear-phishing emails are highly targeted and personalized, making them far more effective than generic phishing attempts. These emails could have contained malicious attachments or links leading to malware downloads, granting initial access to the network.
Once inside, lateral movement techniques would have been employed to navigate the internal network, escalating privileges to access sensitive data repositories. This could have involved the use of tools like Mimikatz to harvest credentials or exploiting further vulnerabilities within the network infrastructure. The attackers may also have leveraged compromised accounts or insider threats to further facilitate their access.
The sophisticated nature of the attack suggests a significant level of planning and technical expertise.
Attack Sophistication and Resources
The attack clearly demonstrates a high level of sophistication. The ability to successfully penetrate Deloitte’s security perimeter, move laterally within the network undetected, and exfiltrate large volumes of sensitive data points to a well-resourced and highly skilled adversary. Such operations require significant technical expertise in areas such as network penetration testing, malware development, and data exfiltration techniques. The attackers likely possessed specialized tools and resources, including custom malware designed to bypass security controls and remain undetected for an extended period.
This is consistent with state-sponsored actors or advanced persistent threat (APT) groups known for their ability to conduct long-term, stealthy attacks against high-value targets. The resources required for such an operation would be substantial, including specialized personnel, advanced tools, and significant financial backing.
Timeline of Events
Precise timing is unavailable publicly. However, a likely scenario would involve:
- Initial Compromise: The attackers gain initial access, potentially through a spear-phishing email or exploitation of a zero-day vulnerability. This phase could have lasted for days or weeks, allowing the attackers to establish a foothold without detection.
- Lateral Movement: The attackers move through the network, gaining access to increasingly sensitive systems. This phase could involve credential harvesting, exploiting internal vulnerabilities, and using various techniques to evade detection by security systems.
- Data Exfiltration: The attackers locate and exfiltrate the targeted data, potentially using techniques like command-and-control servers or data encryption to conceal their actions. This phase could have been spread out over time to avoid detection.
- Discovery and Response: Deloitte discovers the breach and initiates an incident response process. This may involve notifying affected clients, conducting a forensic investigation, and implementing security measures to prevent future attacks.
Data Breached and its Impact
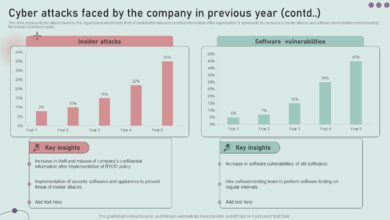
The cyberattack on Deloitte resulted in a significant data breach, exposing sensitive information belonging to both Deloitte and its high-profile clients. The scale and severity of the breach are still unfolding, but initial reports paint a concerning picture of the potential financial and reputational damage. Understanding the nature of the compromised data and its potential impact is crucial to assessing the long-term consequences of this incident.
The leaked data encompasses a range of sensitive information, impacting Deloitte’s operations and the trust placed in it by its clients. The consequences extend beyond financial losses; they include potential legal battles, regulatory scrutiny, and a significant blow to Deloitte’s reputation as a trusted advisor to major corporations.
Types of Data Breached and Potential Impact
| Data Type | Sensitivity Level | Number of Records Affected (Estimate) | Potential Impact |
|---|---|---|---|
| Financial Data (client & internal) | High | Unknown, potentially thousands | Identity theft, financial fraud, market manipulation, loss of investor confidence. This could lead to significant financial losses for both Deloitte and its clients, potentially triggering lawsuits and regulatory investigations. Examples include unauthorized access to bank accounts, investment portfolios, and confidential financial statements. |
| Strategic Plans & Business Documents (client) | High | Unknown, potentially hundreds | Competitive disadvantage for clients, loss of market share, compromised business opportunities. Competitors could exploit leaked information to gain an unfair advantage, impacting clients’ profitability and long-term viability. For example, leaked merger and acquisition plans could significantly affect market valuations. |
| Client Lists & Contact Information | Medium | Potentially tens of thousands | Spam, phishing attacks, targeted marketing campaigns, loss of client trust. Clients could face increased exposure to phishing and other cyberattacks, leading to further data breaches and financial losses. This could also damage client relationships and lead to the loss of future business. |
| Internal Deloitte Documents | High | Unknown | Compromised internal security, operational disruptions, reputational damage. Leaked internal documents could expose vulnerabilities within Deloitte’s security infrastructure, leading to further attacks and operational disruptions. This could also damage Deloitte’s reputation and erode client trust. Examples include security protocols, internal communication, and employee data. |
Financial and Reputational Consequences, Cyber attack on deloitte leaks blue chip info
The financial consequences for Deloitte could be substantial, including costs associated with incident response, legal fees, regulatory fines, and potential compensation to affected clients. Reputational damage could lead to the loss of clients, decreased profitability, and difficulty attracting and retaining top talent. Similar breaches in the past have resulted in billions of dollars in losses for affected companies, including costs associated with legal settlements and remediation efforts.
The reputational damage could be even more long-lasting, potentially impacting Deloitte’s ability to secure new contracts and maintain its position as a leading professional services firm.
Legal Ramifications for Deloitte
Deloitte faces potential legal ramifications under various data privacy regulations, including GDPR (in Europe) and CCPA (in California). Clients and individuals whose data was compromised may file lawsuits against Deloitte for negligence, breach of contract, and violation of data privacy laws. Regulatory bodies could also impose significant fines and penalties for failing to adequately protect sensitive information. The outcome of these legal battles will depend on the specifics of the breach, Deloitte’s security practices before and after the attack, and the extent of the damages suffered by affected parties.
The recent Deloitte cyberattack, exposing sensitive blue-chip information, highlights the urgent need for robust security measures. This incident underscores the importance of proactive cloud security, which is why I’ve been researching solutions like those offered by Bitglass, as detailed in this insightful article on bitglass and the rise of cloud security posture management. Ultimately, strengthening cloud security postures is crucial to preventing future breaches similar to the Deloitte incident and safeguarding valuable data.
Cases like the Equifax breach, which resulted in substantial fines and settlements, serve as a cautionary example of the potential legal consequences of data breaches.
Response and Mitigation
Deloitte’s response to the cyberattack was multifaceted and involved a rapid mobilization of its internal security teams and external experts. The immediate priority was to contain the breach, preventing further data exfiltration and limiting the damage to its clients and reputation. This involved a complex interplay of technical and communication strategies, demanding a coordinated effort across various departments.The initial response focused on isolating affected systems, shutting down vulnerable networks, and initiating a comprehensive forensic investigation to understand the attack’s scope and origin.
This involved analyzing logs, network traffic, and compromised systems to identify the attackers’ methods, their objectives, and the extent of the data breach. Simultaneously, Deloitte implemented emergency measures to secure remaining systems and prevent further exploitation.
Deloitte’s Actions to Contain the Breach and Investigate its Cause
The investigation involved a deep dive into system logs, network activity, and endpoint devices to trace the attackers’ actions. This included analyzing malware samples, reconstructing the attack timeline, and identifying any vulnerabilities exploited. Deloitte engaged leading cybersecurity firms specializing in incident response to provide expertise and support in this complex investigation. They also collaborated with law enforcement agencies to potentially identify and prosecute the perpetrators.
The goal was not just to understand what happened but to identify weaknesses in their security posture and implement preventative measures.
Mitigation Measures Implemented by Deloitte
Deloitte implemented several crucial measures to mitigate the damage and protect its remaining systems. These actions were designed to prevent further attacks and limit the potential impact of the breach.
- Enhanced Security Monitoring: Implementing advanced threat detection and response systems to proactively identify and neutralize future attacks. This involved upgrading existing security information and event management (SIEM) systems and deploying new security tools with advanced analytics capabilities.
- Vulnerability Remediation: Conducting a comprehensive vulnerability assessment and penetration testing to identify and patch any security weaknesses exploited in the attack. This included addressing both known and unknown vulnerabilities to strengthen their overall security posture.
- Improved Access Control: Strengthening access control measures to restrict access to sensitive data and systems. This involved implementing multi-factor authentication (MFA) across all systems, implementing the principle of least privilege, and regularly reviewing user access permissions.
- Employee Security Training: Providing enhanced security awareness training to employees to educate them about phishing scams, malware, and other social engineering techniques. This training aimed to reduce the likelihood of future attacks through human error.
- Data Backup and Recovery: Ensuring robust data backup and recovery procedures to minimize data loss in the event of future incidents. This involved regularly backing up critical data to secure offsite locations and testing the restoration process to ensure its effectiveness.
Deloitte’s Communication Strategy with Affected Clients and Stakeholders
Transparency and open communication were central to Deloitte’s response. They promptly notified affected clients and stakeholders about the breach, providing detailed information about the nature of the attack, the types of data potentially compromised, and the steps taken to mitigate the impact. They established dedicated communication channels to address client concerns and provide regular updates on the investigation and remediation efforts.
This proactive communication aimed to build trust and mitigate reputational damage. Deloitte likely offered credit monitoring and identity theft protection services to affected individuals. This demonstrated their commitment to supporting those impacted by the breach.
Effectiveness of Deloitte’s Response
The effectiveness of Deloitte’s response will be judged over time. While the immediate actions contained the breach and prevented further data loss, the long-term success will depend on the sustained implementation of the mitigation measures and the restoration of client trust. The thoroughness of the investigation, the transparency of their communication, and the effectiveness of their preventative measures will be key factors in determining the long-term impact of the incident.
A successful outcome would involve no further significant breaches and a reinforcement of Deloitte’s reputation as a trusted advisor. Failure to adequately address vulnerabilities or maintain transparency could lead to a loss of clients and significant reputational damage.
Lessons Learned and Future Implications
The Deloitte cyberattack serves as a stark reminder that even the most sophisticated organizations are vulnerable to increasingly sophisticated cyber threats. This incident highlights critical weaknesses in current cybersecurity practices and underscores the urgent need for a more proactive and robust approach to data protection. The lessons learned extend far beyond Deloitte, impacting the entire cybersecurity landscape and demanding a reassessment of trust in consulting firms and their ability to safeguard sensitive client information.The attack exposed significant vulnerabilities in Deloitte’s security posture, revealing the limitations of relying solely on technical solutions.
A multi-faceted approach, encompassing strong technical defenses, rigorous employee training, and a proactive security culture, is crucial for effective mitigation. This incident also underscores the importance of robust incident response planning and execution, demonstrating the need for organizations to regularly test and refine their response capabilities.
Improved Cybersecurity Measures
The insights gained from the Deloitte breach suggest several crucial improvements to cybersecurity measures. First, a significant investment in advanced threat detection and response capabilities is essential. This includes implementing robust intrusion detection and prevention systems, employing advanced endpoint detection and response (EDR) solutions, and proactively hunting for threats within the network. Second, regular security audits and penetration testing are vital to identify vulnerabilities before malicious actors can exploit them.
These assessments should not only focus on technical infrastructure but also incorporate social engineering simulations to test employee awareness and resilience to phishing and other attacks. Finally, robust data loss prevention (DLP) measures are crucial, including strict access control policies, data encryption both in transit and at rest, and regular data backups. Implementing a zero-trust security model, where every user and device is verified before access is granted, regardless of location, should also be considered.
Preventing and Mitigating Future Attacks
The Deloitte breach could have been mitigated more effectively through a combination of proactive measures. Strengthening multi-factor authentication (MFA) across all systems and accounts would significantly enhance security. Implementing robust security awareness training for employees, emphasizing the importance of recognizing and reporting phishing attempts and suspicious activity, is crucial. Furthermore, rigorous access control policies, based on the principle of least privilege, would limit the potential damage caused by a compromised account.
Regular vulnerability scanning and patching of software and systems are paramount to prevent exploitation of known vulnerabilities. Finally, a well-defined incident response plan, regularly tested and updated, is essential to ensure a swift and effective response in the event of a breach. This plan should include clear communication protocols, data recovery procedures, and collaboration with law enforcement and cybersecurity experts.
Broader Implications for the Cybersecurity Landscape
The Deloitte attack has significant implications for the cybersecurity landscape and the trust placed in consulting firms. It highlights the potential for breaches within organizations responsible for advising others on security best practices. This undermines public confidence and raises concerns about the effectiveness of current security frameworks. The incident underscores the need for greater transparency and accountability within the consulting industry regarding security incidents.
This includes proactively disclosing breaches, providing clear and concise information to affected clients, and demonstrating a commitment to continuous improvement in security practices. The attack also serves as a catalyst for further development and adoption of advanced cybersecurity technologies and strategies, pushing the industry to enhance its collective defenses against increasingly sophisticated threats. The long-term impact will likely include stricter regulations and increased scrutiny of cybersecurity practices across all industries, but particularly within the consulting sector.
The incident serves as a high-profile example of the need for continuous vigilance and adaptation in the face of evolving cyber threats.
Closing Summary

The Deloitte data breach serves as a stark reminder of the ever-present threat of sophisticated cyberattacks and the critical need for robust cybersecurity measures. While Deloitte’s response was swift, the incident underscores the importance of proactive security strategies, continuous monitoring, and a multi-layered approach to data protection. The lessons learned from this breach extend far beyond Deloitte, affecting every organization that handles sensitive information.
It’s a wake-up call to prioritize cybersecurity not just as a cost, but as a fundamental investment in trust and business continuity. The future of cybersecurity depends on our collective ability to learn from past mistakes and adapt to the ever-changing landscape of digital threats. Stay vigilant, stay informed, and stay secure.
FAQ Summary: Cyber Attack On Deloitte Leaks Blue Chip Info
What type of malware was used in the Deloitte attack?
The specific type of malware used hasn’t been publicly disclosed. Investigations often keep such details confidential to avoid aiding future attacks.
How many clients were affected by the Deloitte data breach?
The exact number of affected clients remains undisclosed. Deloitte likely contacted affected parties directly.
What legal actions are being taken against Deloitte?
While specifics are not publicly available, Deloitte likely faces various legal actions, including potential lawsuits from affected clients and regulatory investigations.
Did Deloitte’s insurance cover the losses from this breach?
Whether insurance covered the losses is unknown and likely confidential information.