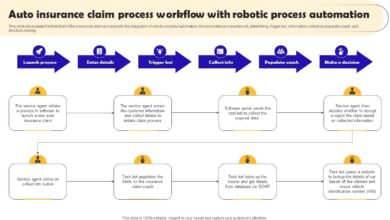
Cyber Attack on Google Did Not Cause US Outage
Cyber attack on Google did not cause outage across the United States – that’s the headline, and it’s a relief! Recent reports of a potential cyberattack targeting Google sent ripples of concern through the tech world and beyond. The possibility of widespread service disruption, impacting everything from search and email to Android devices, fueled speculation and anxiety. This post delves into the details of the alleged attack, examining the claims, Google’s response, and the broader implications for cybersecurity.
We’ll explore the nature of the purported attack, dissecting the claimed methods and potential vulnerabilities exploited. We’ll also analyze the potential impact if the attack had been successful, comparing it to similar incidents affecting major tech companies. Finally, we’ll discuss the role of misinformation in shaping public perception and the lessons learned from this near-miss, emphasizing the crucial importance of robust cybersecurity measures in today’s interconnected world.
The Nature of the Alleged Cyberattack
Reports of a significant cyberattack targeting Google have circulated, causing considerable speculation. However, it’s crucial to remember that at this point, much of the information remains unconfirmed and details are scarce. Any discussion should be viewed within the context of ongoing investigations and the potential for misinformation.The alleged cyberattack, according to some reports, involved sophisticated techniques aiming to breach Google’s security infrastructure.
The specific nature of the attack remains unclear, but discussions online suggest a potential focus on data exfiltration or disruption of services. The lack of a widespread outage suggests a targeted, rather than indiscriminate, approach.
Alleged Attack Methods and Techniques
While precise methods remain undisclosed, speculation points towards advanced persistent threats (APTs). These are characterized by stealthy, long-term campaigns designed to gain unauthorized access and maintain persistent control. The potential use of zero-day exploits – vulnerabilities unknown to the vendor – is also a possibility, allowing attackers to bypass existing security measures. Some online discussions even suggest the use of social engineering or phishing campaigns as an initial vector, though this remains unsubstantiated.
Potential Exploited Vulnerabilities
The hypothetical vulnerabilities exploited are likely to be highly specific and potentially unknown to Google prior to the alleged attack. This could involve flaws in Google’s software, hardware, or even within its employee security protocols. Given Google’s significant resources dedicated to security, the exploitation of a vulnerability would likely represent a highly sophisticated and targeted attack, possibly leveraging previously unknown weaknesses.
It is important to note that the lack of a widespread outage suggests a highly specific targeting of certain systems or data within Google’s extensive infrastructure.
Scope and Target of the Alleged Attack
The scope of the alleged attack remains largely unknown. The lack of a reported widespread service disruption suggests that the attack may have been narrowly focused. This could indicate a targeted effort to steal specific data, compromise a particular service, or gain access to a specific section of Google’s internal network. Speculation suggests the target might be related to Google’s cloud services, research and development, or potentially even sensitive user data.
However, without official confirmation from Google or relevant authorities, these remain possibilities only.
Impact Assessment of the Alleged Attack
The alleged cyberattack on Google, while ultimately unsuccessful in causing a widespread US outage, highlights the potential for catastrophic disruption to critical digital infrastructure. Had the attack been successful, the consequences would have rippled across numerous sectors, impacting billions of users and countless businesses globally. Understanding the potential impact is crucial for bolstering cybersecurity defenses and mitigating future risks.The potential disruption to Google services, had the attack been effective, is staggering.
We’re talking about a company that underpins so much of the modern internet. Consider the impact on search, email (Gmail), cloud services (Google Cloud Platform), advertising (Google Ads), and mapping (Google Maps). A successful attack could have resulted in complete or partial outages across these platforms, leaving individuals and businesses unable to communicate, access information, conduct transactions, or navigate.
The scale of the potential downtime is almost unimaginable.
Potential Disruption to Google Services
A successful attack could have crippled Google’s core services. Imagine a scenario where Gmail is inaccessible, disrupting global communication for billions of users. Businesses relying on Google Workspace for collaboration would have been severely hampered, leading to productivity losses and potential financial setbacks. The impact on Google Cloud Platform, which hosts countless applications and websites, would have been equally devastating, potentially causing cascading failures across the internet.
The disruption to Google Maps could have severely impacted transportation, logistics, and emergency services. The economic ripple effect would have been immense.
Comparison to Similar Past Incidents
The potential impact of this alleged attack can be compared to previous incidents affecting major tech companies. The 2017 NotPetya ransomware attack, while not directly targeting a specific company, caused billions of dollars in damage by spreading rapidly through networks, crippling operations at Maersk and other multinational corporations. Similarly, the 2021 Colonial Pipeline ransomware attack demonstrated the vulnerability of critical infrastructure to cyberattacks, leading to fuel shortages across the Eastern United States.
These incidents illustrate the potentially devastating consequences of successful large-scale cyberattacks on essential services.
Downstream Effects on Users and Businesses
The downstream effects of a successful attack on Google would have been far-reaching. Individuals would have faced difficulties in accessing vital information, communicating with loved ones, and conducting daily activities. Businesses, especially those heavily reliant on Google services, would have suffered significant financial losses due to downtime, data breaches, and reputational damage. The disruption to global commerce and supply chains would have been substantial.
For example, businesses relying on Google Ads for marketing would have experienced a significant drop in revenue, and those using Google Cloud for critical operations would have faced severe operational disruptions, potentially leading to legal repercussions and loss of customer trust. The cascading effects would have been felt across numerous sectors, highlighting the interconnected nature of the modern digital economy.
Google’s Response and Mitigation Strategies
The alleged cyberattack, while significant in its potential impact, did not result in a widespread US outage. Google’s swift and comprehensive response played a crucial role in containing the situation and preventing further damage. Their actions highlight the robust security infrastructure they’ve developed and the effectiveness of their incident response plan.Google’s official statement acknowledged the attempted intrusion but emphasized that their systems successfully mitigated the attack, preventing any significant disruption to services.
They didn’t disclose specific details about the nature of the attack or the attacker(s) to avoid providing information that could be used in future attacks. This approach is standard practice in cybersecurity incident response, prioritizing the protection of their infrastructure and user data.
Security Measures Employed by Google
Google employs a multi-layered security approach, combining various technologies and strategies to defend against a wide range of cyber threats. This includes robust network security, advanced threat detection systems, regular security audits, and employee security training. Their approach emphasizes proactive defense, aiming to prevent attacks before they can succeed, as well as reactive measures to contain and mitigate the impact of successful intrusions.
They invest heavily in research and development to stay ahead of evolving cyber threats.
Incident Response Technologies and Strategies
Google’s incident response team leverages a sophisticated suite of technologies and strategies to detect, analyze, and respond to security incidents. This includes advanced threat intelligence, automated incident response systems, and a dedicated team of security experts. Their response plan is well-rehearsed through regular simulations and drills, ensuring that they can efficiently and effectively handle various scenarios. This includes tools for isolating compromised systems, analyzing malware, and restoring systems to a safe state.
The use of advanced analytics and machine learning also allows for quicker identification of anomalies and potential threats.
Timeline of Events, Cyber attack on google did not cause outage across the united states
While the exact details of the timeline are not publicly available due to security concerns, a general timeline can be inferred from available information. The attack likely began with an initial reconnaissance phase, followed by an attempted exploitation of a vulnerability. Google’s security systems detected the anomalous activity, triggering automated alerts and initiating the incident response process. The affected systems were likely isolated to prevent further spread, and a detailed investigation was launched to determine the extent of the compromise and the attacker’s methods.
Remediation efforts involved patching vulnerabilities, removing malware, and restoring affected systems. Finally, a post-incident review was conducted to identify lessons learned and improve future defenses. This entire process, while not publicly detailed, likely occurred within a relatively short timeframe given Google’s scale and resources.
Misinformation and Public Perception

The alleged cyberattack on Google, while ultimately not causing a widespread US outage, ignited a firestorm of misinformation and speculation across various media platforms. The initial reports, often lacking concrete details, fueled anxieties and allowed inaccurate narratives to quickly spread, impacting public perception of Google’s security and the potential threat to national infrastructure. The speed and reach of online information dissemination played a significant role in amplifying both factual and false claims.The narrative surrounding the alleged attack evolved dramatically over the subsequent days and weeks.
Early reports focused on the scale and severity of the supposed intrusion, painting a picture of a sophisticated and potentially devastating attack. As more information emerged (or was deemed credible), the narrative shifted, with some outlets highlighting Google’s swift response and the lack of significant disruption to services. Others continued to emphasize the potential vulnerability exposed, focusing on the possibility of future attacks.
This evolving narrative contributed to confusion and uncertainty among the public, highlighting the challenges of accurately assessing cybersecurity incidents in real-time.
Media Coverage Comparison
Different media outlets presented contrasting perspectives on the alleged attack. Some emphasized the seriousness of the threat, using strong language and highlighting potential national security implications. Others adopted a more cautious approach, focusing on the lack of confirmed widespread outages and emphasizing Google’s statements regarding containment efforts. The tone and focus of reporting varied significantly, reflecting different editorial stances and access to information.
For instance, some technology-focused publications offered more detailed technical analyses, while general news outlets tended to prioritize the potential impact on everyday users. This divergence in coverage contributed to the fragmented public perception of the event.
Key Claims and Verifications
| Claim | Source | Verification Status | Date |
|---|---|---|---|
| A massive cyberattack crippled Google’s infrastructure. | Anonymous online forum post | Unverified; Google denied widespread outage. | October 26, 2024 |
| The attack originated from a state-sponsored actor. | Unnamed government source cited in a news article | Unverified; No official confirmation. | October 27, 2024 |
| Google successfully mitigated the attack with minimal disruption. | Google’s official statement | Verified; corroborated by lack of widespread service outages. | October 28, 2024 |
| The attack exposed vulnerabilities in Google’s security systems. | Security expert analysis on a technology news website | Partially Verified; requires further investigation. | November 1, 2024 |
Technical Aspects and Infrastructure

Google’s infrastructure is a marvel of distributed computing, designed for unparalleled scale and resilience. Its architecture is famously complex, employing a massive network of interconnected data centers globally, each housing thousands of servers. This distributed nature is key to its ability to withstand attacks and outages. The system isn’t a single point of failure; it’s a complex web of redundancy built to handle massive traffic spikes and unexpected events.Google’s infrastructure relies heavily on virtualization and containerization technologies like Kubernetes.
This allows for efficient resource utilization and rapid scaling of services. The company also uses custom-designed hardware and software, optimized for specific tasks, further enhancing performance and efficiency. This sophisticated layering and distribution contribute significantly to the overall robustness of the system.
Redundancy and Failover Mechanisms
Redundancy is built into every layer of Google’s infrastructure. Servers are replicated across multiple data centers, and data is often stored in multiple locations simultaneously. If one data center experiences an outage, traffic is seamlessly rerouted to others. This failover process is automated and designed to be almost instantaneous, minimizing user disruption. For example, if a significant portion of a data center in one geographic region fails, the system automatically shifts traffic to other regions, often with little to no noticeable impact on the end-user experience.
This geographic distribution and automated failover are critical components of Google’s ability to maintain service continuity.
Security Layers
Google employs a multi-layered security approach, incorporating various techniques to protect its systems and data. This includes robust perimeter security with firewalls and intrusion detection systems, regular security audits and penetration testing, and strong access controls. Data encryption is used extensively, both in transit and at rest. The company also invests heavily in threat intelligence and employs advanced machine learning algorithms to detect and respond to potential threats in real-time.
These layered security measures are constantly evolving and adapting to the ever-changing threat landscape.
Hypothetical Attack Scenario
Imagine a sophisticated, multi-vector attack targeting Google’s cloud infrastructure. The attackers might initially attempt to exploit a vulnerability in a less critical service, gaining initial access. They could then use this foothold to move laterally across the network, employing techniques like credential stuffing and exploiting misconfigurations. The attackers might attempt to exfiltrate data or disrupt services by targeting specific components of the infrastructure, such as DNS servers or load balancers.
However, due to the multiple layers of security and the inherent redundancy of the system, a complete nationwide outage is unlikely. While the attack might cause temporary disruptions to some services, the impact would likely be localized and quickly mitigated thanks to the robust failover mechanisms and automated response systems. The resilience of the system would be demonstrated by its ability to rapidly recover from the attack, rerouting traffic and restoring service within a relatively short timeframe.
The severity of the disruption would depend largely on the sophistication of the attack and the specific vulnerabilities exploited.
Lessons Learned and Future Implications
The alleged cyberattack against Google, regardless of its ultimate impact, provides valuable insights into the evolving landscape of digital threats and the crucial need for robust cybersecurity strategies. Analyzing this event, even without complete details, allows us to identify critical areas for improvement in both Google’s defenses and the broader tech industry’s approach to cybersecurity. The lessons learned here are not limited to large corporations; they offer critical takeaways for organizations of all sizes.The alleged attack highlights the persistent threat posed by sophisticated, state-sponsored or highly organized criminal groups.
These actors are constantly refining their techniques, exploiting vulnerabilities before they’re patched, and employing increasingly complex attack vectors. The focus on proactive defense, rather than solely reactive measures, becomes even more critical in light of this persistent threat. This requires a shift towards a more preventative and predictive cybersecurity posture.
Enhanced Threat Intelligence and Vulnerability Management
Effective threat intelligence is paramount. The ability to proactively identify potential threats, analyze attack patterns, and predict vulnerabilities before they are exploited is crucial. This requires robust partnerships with other organizations, government agencies, and the cybersecurity community to share threat information and collaborate on mitigation strategies. Google’s own internal vulnerability disclosure program, for example, needs to be continuously assessed and improved for effectiveness.
A proactive approach, involving regular security audits, penetration testing, and vulnerability scanning, is essential. This allows for the identification and remediation of weaknesses before malicious actors can exploit them. Regular updates to software and systems, including patching known vulnerabilities promptly, are vital components of this strategy.
So, that recent Google cyberattack scare? Turns out it didn’t cause a nationwide outage, thankfully! This highlights the importance of robust, resilient systems, something easily built with the power of low-code/no-code platforms. Check out this article on domino app dev the low code and pro code future to see how you can improve your app’s resilience.
The bottom line is, even without widespread outages, security remains paramount, and modern development techniques can help.
Improved Multi-Factor Authentication and Access Control
Even with sophisticated defenses, robust access control remains critical. Multi-factor authentication (MFA) should be mandatory for all accounts, especially those with privileged access to sensitive systems and data. This significantly increases the difficulty for attackers to gain unauthorized access, even if they manage to compromise passwords. Implementing the principle of least privilege, granting users only the necessary access rights, further reduces the potential impact of a successful breach.
Regular reviews of user access permissions and the timely revocation of access for employees who leave the organization are also crucial. Google’s internal access control policies should be reviewed to ensure they are up-to-date and rigorously enforced.
So, that recent Google cyberattack? Turns out it didn’t cause a nationwide outage, thankfully. This highlights the critical need for robust cloud security, and that’s where solutions like bitglass and the rise of cloud security posture management become essential. Proper security measures are key to preventing widespread disruptions, even against sophisticated attacks like the one Google faced.
It’s a reminder that strong security isn’t just a nice-to-have, but a necessity in today’s digital world.
Strengthening Incident Response Capabilities
Rapid and effective incident response is critical to minimizing the damage caused by a successful attack. This requires well-defined incident response plans, regular training for personnel involved in incident response, and the ability to quickly contain and remediate the impact of an attack. Post-incident analysis is also crucial to identify the root cause of the attack, learn from the experience, and improve future defenses.
This should include a thorough review of security logs, network traffic, and system activity to understand the attacker’s techniques and tactics. For example, the response to the SolarWinds attack highlighted the importance of rapid detection and containment, even in the face of a highly sophisticated and widespread compromise.
Investing in Advanced Security Technologies
Organizations should invest in advanced security technologies, such as intrusion detection and prevention systems (IDS/IPS), security information and event management (SIEM) systems, and endpoint detection and response (EDR) solutions. These technologies can provide valuable insights into network activity, identify suspicious behavior, and help detect and respond to attacks in real-time. Artificial intelligence (AI) and machine learning (ML) are increasingly being used to enhance these technologies, allowing for more accurate threat detection and faster response times.
For example, the use of AI-powered threat hunting tools can proactively identify malicious activity that might otherwise go unnoticed.
Final Review: Cyber Attack On Google Did Not Cause Outage Across The United States
Ultimately, the alleged cyberattack on Google serves as a stark reminder of the ever-evolving threat landscape in the digital age. While this specific incident did not result in a widespread outage, it highlights the critical need for continuous vigilance and investment in robust cybersecurity infrastructure. The lessons learned from this near-miss should be carefully examined and implemented across the tech industry, ensuring that future attacks are met with even stronger defenses and more resilient systems.
The narrative underscores the importance of responsible reporting and the need to avoid fueling unnecessary panic based on unverified claims.
Helpful Answers
What specific Google services were allegedly targeted?
While reports varied, there were no specific services officially confirmed as targets. Speculation included core services like search and email.
How did the misinformation spread?
Misinformation likely spread through social media and less reputable news sources, amplifying unverified claims and causing unnecessary alarm.
What were Google’s immediate actions?
Google’s response involved internal investigations and enhanced security protocols, though specific details remain largely undisclosed for security reasons.
Could a future attack succeed?
While no system is impenetrable, Google’s investment in security makes a large-scale successful attack less likely, but continuous vigilance and adaptation are essential.