Cyber Attack on APAC Companies $10.7M Loss Risk
Cyber attack on large companies operating in the asia pacific could fetch 10 7 m loss – Cyber attack on large companies operating in the Asia Pacific could fetch a staggering $10.7 million loss – that’s the chilling reality facing many businesses in the region. This isn’t just a headline; it’s a potential crisis waiting to happen, impacting everything from employee livelihoods to investor confidence and customer trust. We’re diving deep into the vulnerabilities, the attack vectors, and what companies can do to protect themselves from this devastating financial blow.
The sheer scale of potential damage is alarming. Imagine the domino effect: layoffs, plummeting stock prices, damaged reputations, and the potential loss of valuable customer data. This isn’t a problem confined to a single industry; from finance to healthcare, almost every sector in the Asia-Pacific region is at risk. Understanding the threats and implementing robust security measures is no longer optional; it’s a matter of survival.
Financial Impact of Cyberattacks in Asia-Pacific: Cyber Attack On Large Companies Operating In The Asia Pacific Could Fetch 10 7 M Loss
A $10.7 million loss from a cyberattack on a large Asia-Pacific company represents a significant blow, highlighting the escalating financial risks businesses face in the region. This figure doesn’t just represent a monetary loss; it signifies a cascade of negative consequences impacting various stakeholders and potentially triggering long-term instability.
Economic Consequences of a $10.7 Million Loss
A $10.7 million loss from a cyberattack can have far-reaching economic consequences. This sum could represent a substantial portion of a company’s annual profits, potentially leading to decreased shareholder value, reduced investment opportunities, and difficulty in meeting financial obligations. The cost extends beyond the immediate financial loss and includes expenses related to incident response, data recovery, legal fees, regulatory fines, and reputational damage repair.
For smaller companies, a loss of this magnitude could lead to bankruptcy. Even for large corporations, it can severely impact short-term financial performance and long-term strategic planning. The ripple effects could also extend to the broader economy, affecting employment and investor confidence.
Impact on Stakeholders
The impact of a $10.7 million cyberattack loss ripples through a company’s ecosystem of stakeholders. Employees may face job losses or salary reductions as the company struggles to recover. Investors will likely see a decrease in their return on investment, potentially leading to decreased stock prices and loss of confidence in the company’s management. Customers may experience disruptions in service, data breaches, or loss of trust, leading to decreased sales and brand loyalty.
The company’s reputation suffers, impacting its ability to attract future investments and customers.
Industries Most Vulnerable to Significant Financial Losses
Several industries in the Asia-Pacific region are particularly vulnerable to significant financial losses from cyberattacks due to the nature of their data and operations. The financial services sector, with its sensitive customer data and complex financial transactions, is highly susceptible. Similarly, the healthcare industry, with its protected health information (PHI), faces substantial risks and potential penalties for data breaches.
The technology sector, responsible for developing and maintaining critical infrastructure, is also a prime target. Finally, the retail sector, with its extensive customer databases and online transactions, is increasingly vulnerable to data breaches and financial losses.
Industry Vulnerability to Cyberattacks
| Industry | Average Loss (USD) | Recovery Time (Months) | Impact on Stock Price (%) |
|---|---|---|---|
| Financial Services | 5,000,000 – 15,000,000 | 6-12 | -5% to -20% |
| Healthcare | 2,000,000 – 8,000,000 | 3-9 | -3% to -15% |
| Technology | 3,000,000 – 12,000,000 | 4-10 | -4% to -18% |
| Retail | 1,000,000 – 5,000,000 | 2-6 | -2% to -10% |
Note: These figures are estimates based on industry reports and may vary depending on the scale and nature of the attack. The impact on stock price is an approximation and can fluctuate based on various market factors.
Types of Cyberattacks Targeting Large APAC Companies
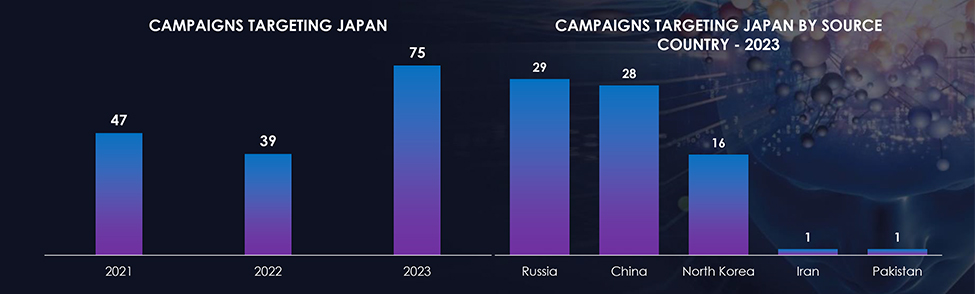
A $10.7 million loss from a cyberattack highlights the severe financial consequences facing large companies in the Asia-Pacific region. Understanding the types of attacks most likely to inflict such damage is crucial for effective cybersecurity strategies. This section details the common attack vectors, their methods, and real-world examples from the APAC region.
Ransomware Attacks
Ransomware attacks remain a significant threat, crippling operations and demanding substantial ransoms for data recovery. These attacks typically involve malicious software that encrypts a victim’s data, rendering it inaccessible. The attackers then demand a ransom payment, often in cryptocurrency, in exchange for a decryption key. Sophisticated ransomware strains often employ techniques like double extortion, where attackers not only encrypt data but also threaten to leak sensitive information publicly if the ransom isn’t paid.
The methods used include phishing emails containing malicious attachments or links, exploiting software vulnerabilities to gain initial access, and leveraging lateral movement techniques to spread the ransomware throughout the network. A notable example is the 2021 ransomware attack on Acer, which resulted in a reported multi-million dollar ransom payment. While the exact figure wasn’t publicly disclosed, it illustrates the significant financial impact such attacks can have on large organizations.
Data Breaches
Data breaches, often facilitated by phishing attacks, SQL injection, or exploiting vulnerabilities in web applications, lead to the theft of sensitive customer data, intellectual property, or financial information. The financial impact stems from the costs associated with investigations, regulatory fines, legal fees, credit monitoring services for affected customers, and reputational damage. Methods include exploiting known vulnerabilities in web applications, using credential stuffing to access accounts, or gaining access through compromised employee accounts.
The 2017 Equifax data breach, though not strictly within APAC, serves as a powerful example. It impacted millions globally and resulted in billions of dollars in fines, legal costs, and reputational damage – illustrating the scale of potential financial losses from data breaches.
Supply Chain Attacks
Supply chain attacks target vulnerabilities within a company’s network of suppliers, partners, and third-party vendors. Attackers compromise a less secure entity in the supply chain to gain access to the larger target. The methods involved often include phishing attacks, exploiting software vulnerabilities in third-party software, or compromising legitimate software updates. The 2020 SolarWinds attack, although global in reach, highlighted the devastating impact of supply chain attacks.
While not directly targeting APAC companies exclusively, it showed how a compromised software update could provide access to numerous organizations, including those in the region, potentially leading to significant financial losses from data theft, disruption, and remediation.
Phishing and Social Engineering Attacks
These attacks leverage human psychology to trick employees into revealing sensitive information or downloading malware. Methods involve sending deceptive emails, SMS messages, or making phone calls that appear legitimate, but actually lead to credential theft or malware installation. Successful phishing attacks can lead to data breaches, ransomware infections, or other costly security incidents. The frequency and sophistication of these attacks are constantly increasing, making them a persistent threat to organizations of all sizes in the APAC region.
Many instances of smaller-scale phishing attacks leading to significant internal damage and financial losses exist, although the precise financial impact is often not publicly reported.
Denial-of-Service (DoS) Attacks
DoS attacks flood a target’s servers with traffic, making them unavailable to legitimate users. Distributed Denial-of-Service (DDoS) attacks amplify the effect by using a network of compromised devices (botnets) to launch the attack. The financial impact stems from lost revenue due to business disruption, reputational damage, and the costs of mitigation and recovery. While the immediate financial impact might not reach tens of millions in a single instance, prolonged or well-orchestrated DDoS attacks can significantly cripple a business’s operations, leading to substantial long-term financial losses.
Examples are numerous, but often the specifics of the financial losses are not publicly disclosed due to competitive reasons.
Vulnerabilities of Large APAC Companies
The staggering potential losses from cyberattacks on large Asia-Pacific companies—reaching tens of millions of dollars—underscore the critical need to understand the underlying vulnerabilities. These attacks aren’t random; they exploit known weaknesses in systems and security practices, often amplified by regional specifics. Examining these vulnerabilities is crucial for developing effective mitigation strategies.The common thread weaving through many successful attacks against large APAC companies is a combination of outdated security practices and a lack of robust, proactive security measures.
This isn’t solely a technological issue; it often stems from insufficient investment in cybersecurity, inadequate employee training, and a lack of a comprehensive risk management framework. The consequences are severe, leading to significant financial losses, reputational damage, and legal repercussions.
Outdated Software and Patching Deficiencies
Many large APAC companies struggle with timely software updates and patching. This leaves their systems vulnerable to known exploits, often publicly available for attackers to leverage. For example, a delay in patching a known vulnerability in a widely used enterprise resource planning (ERP) system could allow attackers to gain unauthorized access, potentially leading to data breaches and ransomware attacks.
The sheer size and complexity of these organizations often mean that a comprehensive patching strategy isn’t easily implemented, creating significant vulnerabilities. This is further exacerbated by a reliance on legacy systems that may lack the security features of more modern counterparts.
Insufficient Employee Security Awareness Training
Human error remains a significant factor in many cyberattacks. Phishing campaigns, spear-phishing attacks, and social engineering tactics are highly effective, particularly against employees lacking adequate security awareness training. A well-crafted phishing email, impersonating a senior executive or a trusted vendor, can easily trick an unsuspecting employee into revealing sensitive credentials or downloading malicious software. The consequences can range from data breaches to full-scale network compromises.
Companies often underestimate the value of investing in regular and comprehensive security awareness training, leaving their workforce susceptible to these attacks.
Inadequate Network Security and Access Control
Weak network security controls, such as inadequate firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS), can significantly increase the risk of successful attacks. Similarly, lax access control policies, allowing excessive privileges to employees or lacking multi-factor authentication (MFA), can provide attackers with easy entry points into sensitive systems. For instance, an attacker who gains access to a single employee account with excessive privileges might be able to move laterally across the network, gaining access to sensitive data or critical systems.
The lack of robust network segmentation further exacerbates this vulnerability, allowing a single breach to have far-reaching consequences.
Industry-Specific Vulnerabilities in APAC
Vulnerabilities vary across industries within the APAC region. For example, the financial services sector faces a higher risk of sophisticated attacks targeting sensitive customer data and financial transactions, while the healthcare sector is vulnerable to attacks targeting patient records and medical devices. Manufacturing companies, with their extensive supply chains and interconnected systems, are particularly susceptible to disruptions caused by ransomware attacks.
The unique regulatory environments and technological landscapes of different APAC countries also contribute to varying levels of vulnerability across industries.
Hypothetical Security Plan: Key Improvements
A comprehensive security plan should include several key improvements. This would begin with a thorough risk assessment to identify vulnerabilities specific to the organization. This assessment should be followed by a robust security awareness training program for all employees, covering topics such as phishing recognition, password security, and safe internet practices. Furthermore, the organization needs to implement a strong access control policy with mandatory multi-factor authentication for all sensitive systems and accounts.
Regular security audits and penetration testing should be conducted to identify and address vulnerabilities proactively. Finally, investment in modern security technologies, such as advanced firewalls, intrusion detection/prevention systems, and security information and event management (SIEM) tools, is crucial for effective threat detection and response. The plan should also incorporate a robust incident response plan to minimize the impact of successful attacks.
Cybersecurity Measures and Mitigation Strategies
The potential for a cyberattack to inflict a $10.7 million loss on a large Asia-Pacific company underscores the critical need for robust cybersecurity measures. A multi-layered approach, combining preventative, detective, and responsive strategies, is essential to minimize vulnerabilities and mitigate the impact of successful attacks. This involves a proactive stance, investing in advanced technologies and skilled personnel, alongside comprehensive incident response planning.
Implementing effective cybersecurity measures requires a holistic strategy that addresses people, processes, and technology. This goes beyond simply installing antivirus software; it demands a cultural shift within the organization, prioritizing cybersecurity awareness and training at all levels. Investing in advanced security technologies is crucial, but equally important is the development of clear incident response plans and regular security audits to identify and address weaknesses before they can be exploited.
Multi-Layered Security Approach
A multi-layered security approach utilizes a combination of security controls to create a defense-in-depth strategy. This approach assumes that a single security control may fail, so multiple layers are necessary to provide redundancy and resilience. For large APAC companies, this could involve implementing firewalls at the network perimeter, intrusion detection/prevention systems (IDS/IPS) to monitor network traffic for malicious activity, endpoint detection and response (EDR) solutions on individual devices, data loss prevention (DLP) tools to prevent sensitive data from leaving the network, and a robust security information and event management (SIEM) system to collect and analyze security logs from various sources.
Regular security awareness training for employees is also a critical layer, educating them about phishing scams, social engineering, and other common attack vectors. For example, a company might implement multi-factor authentication (MFA) across all systems, requiring users to provide multiple forms of authentication before accessing sensitive data. This adds a significant layer of security beyond simple passwords.
Incident Response and Recovery Best Practices
Effective incident response and recovery are crucial to minimizing the impact of a successful cyberattack. A well-defined incident response plan should be in place, outlining roles, responsibilities, and procedures to follow in the event of a security incident. This plan should include steps for containment, eradication, recovery, and post-incident activity. Regular testing and training exercises are vital to ensure that the plan is effective and that personnel are familiar with their roles and responsibilities.
Furthermore, establishing strong relationships with law enforcement and cybersecurity experts can provide valuable support during an incident. Consider, for instance, a scenario where a ransomware attack encrypts critical data. A well-rehearsed incident response plan would allow the company to quickly isolate affected systems, prevent further spread of the malware, and initiate data recovery from backups. Post-incident analysis is also critical to identify the root cause of the attack and implement measures to prevent similar incidents in the future.
Incident Response and Recovery Flowchart
The following describes a flowchart illustrating the steps involved in incident response and recovery. Imagine a visual representation, starting with the “Incident Detection” box, which branches to “Confirmation/Investigation” leading to “Containment” and “Eradication”. “Containment” focuses on isolating affected systems, while “Eradication” involves removing the malware. These then converge to “Recovery,” which involves restoring systems and data from backups.
Finally, “Post-Incident Activity” includes analysis, reporting, and implementing preventative measures. Each stage has detailed sub-steps and decision points, ensuring a systematic approach to addressing the incident. The flowchart visualizes this process clearly, allowing for quick reference and efficient execution during a crisis. This structured approach minimizes downtime and damage.
Geopolitical and Regulatory Considerations
The Asia-Pacific region’s complex geopolitical landscape significantly influences the frequency and severity of cyberattacks against large companies. Rising tensions between nations, evolving trade relationships, and differing levels of cybersecurity infrastructure contribute to a dynamic threat environment. Understanding these factors and the corresponding regulatory frameworks is crucial for effective risk mitigation.Geopolitical factors such as territorial disputes and trade wars can exacerbate cyber threats.
For instance, increased tensions between nations may lead to state-sponsored cyberattacks targeting companies associated with rival countries. Similarly, economic sanctions or trade disputes can create incentives for cybercriminals to exploit vulnerabilities in companies affected by these actions, aiming for financial gain or disruption. The varying levels of cybersecurity infrastructure and expertise across the region also play a role, creating opportunities for attacks targeting less secure entities.
Cybersecurity Regulations and Compliance Standards in the Asia-Pacific Region
The Asia-Pacific region boasts a diverse regulatory landscape concerning cybersecurity. Several countries have implemented comprehensive data protection laws and cybersecurity frameworks, while others are still developing their regulatory infrastructure. These regulations often focus on data privacy, critical infrastructure protection, and incident reporting requirements. Compliance with these regulations is vital for minimizing legal and financial repercussions following a cyberattack.
For example, failure to comply with data breach notification laws can result in significant fines and reputational damage.
Comparative Analysis of Cybersecurity Regulations Across APAC Countries
Significant differences exist in the regulatory approaches adopted by various Asia-Pacific nations. Countries like Singapore and Australia have established robust cybersecurity frameworks and regulations, emphasizing proactive risk management and incident response. These frameworks often include mandatory breach notification requirements, data protection standards, and guidelines for critical infrastructure protection. In contrast, some other countries in the region are still in the process of developing comprehensive cybersecurity laws, leading to a less standardized and potentially less effective regulatory environment.
This disparity creates challenges for multinational companies operating across the region, requiring them to navigate a patchwork of different legal and regulatory requirements.
Regulatory Compliance and Mitigation of Financial Losses
Adherence to relevant cybersecurity regulations and standards plays a crucial role in mitigating financial losses from cyberattacks. Compliance often necessitates the implementation of robust security controls, such as data encryption, access control measures, and regular security audits. These measures can significantly reduce the likelihood and impact of successful attacks. For example, implementing strong data encryption can limit the damage from a data breach, preventing sensitive information from falling into the wrong hands.
Furthermore, robust incident response plans, mandated by many regulations, enable organizations to quickly contain and recover from cyberattacks, minimizing business disruption and financial losses. The cost of compliance is often significantly less than the potential cost of a major cyberattack and subsequent legal ramifications. Consider the example of a company fined millions for non-compliance with data breach notification laws; proactive regulatory compliance would have prevented this significant financial loss.
The Role of Insurance and Risk Management
The escalating costs of cyberattacks in the Asia-Pacific region underscore the critical need for robust insurance and proactive risk management strategies. For large companies, the potential financial losses are staggering, making comprehensive cyber insurance a crucial element of a holistic security approach. Effective risk management, coupled with appropriate insurance coverage, can significantly reduce the impact of a successful attack and enable faster recovery.Cyber insurance plays a vital role in mitigating the financial losses stemming from cyberattacks.
With cyber attacks on large Asia-Pacific companies potentially costing $107 million, robust security is crucial. That’s why understanding solutions like cloud security posture management is vital, and I found a great resource on bitglass and the rise of cloud security posture management that sheds light on this. Ultimately, preventing these massive financial losses requires a proactive approach to cybersecurity, leveraging the best available technology.
It acts as a financial safety net, covering expenses related to incident response, legal fees, regulatory fines, and business interruption. By transferring some of the financial risk to an insurer, companies can focus on restoring operations and maintaining business continuity after an incident. The level of protection offered, however, depends on the specific policy purchased and the diligence of the insured in implementing security measures.
Types of Cyber Insurance Policies Available to Large APAC Companies
Several types of cyber insurance policies cater to the diverse needs of large APAC companies. These policies can be tailored to cover specific risks and can include coverage for data breaches, ransomware attacks, system failures, and business interruption. Common types include first-party coverage (covering the insured company’s direct losses), third-party coverage (covering losses incurred by others due to the insured company’s actions), and regulatory liability coverage (covering fines and penalties imposed by regulatory bodies).
Some policies also offer crisis management and public relations support to help manage the reputational damage following a cyberattack. The specific coverage offered varies significantly between insurers and policy types.
Importance of Proactive Risk Management Strategies
Proactive risk management is paramount in reducing cyberattack vulnerabilities and minimizing insurance premiums. This involves conducting regular security assessments, implementing robust security controls, developing incident response plans, and providing comprehensive employee cybersecurity training. Companies that demonstrate a strong security posture through these proactive measures are typically viewed as lower risk by insurers, leading to more favorable premiums and broader coverage options.
Regular penetration testing, vulnerability scanning, and security awareness training are all key components of a comprehensive risk management program. For example, a company that invests in multi-factor authentication and regular employee phishing simulations will likely be considered a lower risk than a company that relies solely on password-based authentication.
Comparison of Cyber Insurance Providers, Cyber attack on large companies operating in the asia pacific could fetch 10 7 m loss
The following table compares hypothetical cyber insurance providers, illustrating the variation in coverage and premiums. Note that these are illustrative examples and actual offerings will vary depending on the specific needs of the company and the insurer’s risk assessment. Actual premiums and coverage will depend on factors such as company size, industry, existing security measures, and claims history.
The potential $10.7 million loss from cyberattacks on large Asia-Pacific companies is a sobering statistic. Building robust, secure applications is crucial, and that’s where learning about domino app dev, the low-code and pro-code future , becomes incredibly relevant. Investing in secure development practices, regardless of the coding approach, is the best defense against such devastating financial consequences.
| Provider | Coverage (Illustrative) | Annual Premium (Illustrative) |
|---|---|---|
| CyberSecure Global | Data breach response, ransomware coverage, business interruption, regulatory fines (up to $5 million) | $50,000 |
| Asia Pacific Insurance Co. | Data breach response, ransomware coverage, business interruption (up to $3 million), legal expenses | $30,000 |
| Global Risk Solutions | Data breach response, regulatory fines, crisis management, public relations support (up to $10 million) | $75,000 |
Wrap-Up

The threat of crippling cyberattacks in the Asia-Pacific region is undeniable. A $10.7 million loss is more than just a number; it represents a potential catastrophe for affected companies and the wider economy. While the challenges are significant, proactive security measures, robust risk management strategies, and collaboration across industries offer a path towards mitigation. By understanding the vulnerabilities and implementing the right safeguards, businesses can significantly reduce their exposure to these devastating attacks and protect their future.
Top FAQs
What types of cyber insurance are available to large APAC companies?
Several types exist, including first-party coverage (for the company’s own losses), third-party coverage (for losses incurred by others due to the company’s breach), and incident response insurance (covering the costs of investigating and resolving a breach).
How can geopolitical factors influence cyberattacks in the APAC region?
Geopolitical tensions can increase the likelihood of state-sponsored attacks or attacks targeting specific industries tied to national interests. Regional instability can also create opportunities for criminal cyber actors.
What are some examples of inadequate security measures that lead to significant losses?
Outdated software, lack of employee training on cybersecurity best practices, insufficient network segmentation, and failure to implement multi-factor authentication are common culprits.
What is the role of regulatory compliance in mitigating financial losses?
Compliance with data protection regulations like GDPR (in applicable regions) and local equivalents can help companies avoid hefty fines and reputational damage, indirectly reducing financial losses from breaches.