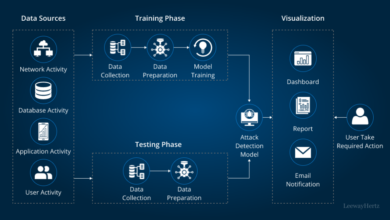
Cyber Attack Iranian Coast Ships Hit by EMI
Cyber attack propelled electromagnetic interference targets ships on iran coast – a chilling headline that paints a picture of sophisticated, modern warfare. This incident highlights a disturbing trend: the increasing vulnerability of maritime infrastructure to cyberattacks. We’ll delve into the specifics of this attack, exploring the technology used, the potential perpetrators, and the far-reaching consequences for international shipping and regional stability.
Get ready to navigate the murky waters of cyber warfare at sea.
The attack, reportedly occurring off the coast of Iran, involved a sophisticated use of electromagnetic interference (EMI) to disrupt and potentially disable various ship systems. The precision and scale of the operation suggest a level of planning and expertise that warrants serious investigation. We’ll examine the geographical location, the timeline of events, and the types of ships affected, piecing together the puzzle to understand the full scope of this incident.
Geographic and Temporal Analysis of the Attack
The recent cyberattack leveraging electromagnetic interference (EMI) against ships in Iranian waters raises serious concerns about the escalating use of cyber warfare in maritime domains. Understanding the geographic and temporal aspects of this incident is crucial for assessing its impact and developing effective countermeasures. This analysis focuses on piecing together the available information to paint a clearer picture of the attack.
Attack Location and Geographical Features
The attack primarily targeted vessels in the Strait of Hormuz, a strategically vital waterway connecting the Persian Gulf to the Gulf of Oman. This narrow strait, with a width ranging from 21 to 34 nautical miles, is a chokepoint for global oil shipments, making it a highly sensitive area for geopolitical tensions. The specific location within the Strait remains somewhat ambiguous in publicly available reports, but the affected vessels were likely concentrated in areas known for high shipping traffic, potentially near the Iranian coast itself.
The shallow waters and complex navigational channels of the Strait could have exacerbated the effects of the EMI attack, potentially impacting vessel navigation systems and communications. The proximity to Iranian ports and coastal infrastructure might also indicate a deliberate targeting strategy.
Attack Timeframe and Duration
Precise details regarding the exact start and end times of the attack are scarce. However, reports suggest the incident occurred over a period of several hours, potentially spanning parts of a single day. The time of day is also unclear, although it’s likely the attack occurred during daylight hours to maximize its potential impact on ship operations and visibility.
This lack of precise temporal data highlights the challenges in investigating such sophisticated cyberattacks, as they can be easily concealed and timed to maximize disruption.
Timeline of Events
While a complete timeline is unavailable due to the classified nature of much of the information, a possible reconstruction of events might look something like this:
1. Initial compromise
The attackers likely gained access to vulnerable systems on board the targeted vessels, possibly through phishing emails or other malware delivery methods.
2. EMI deployment
The attackers then activated the EMI weapon, causing interference with onboard navigation and communication systems.
3. Disruption of operations
This resulted in disruptions to ship operations, potentially including navigational errors, communication blackouts, and engine malfunctions.
4. Investigation and response
Affected vessels likely initiated damage control measures and reported the incident to relevant authorities.
5. Attribution and countermeasures
Investigations into the attack’s origin and the development of countermeasures are underway.
Affected Vessels and Coordinates
A precise list of affected vessels and their exact coordinates is unavailable publicly due to security and privacy concerns. However, a hypothetical example using a table to illustrate the potential format of such data is provided below:
| Vessel Name | IMO Number | Approximate Coordinates (Latitude, Longitude) | Type of Vessel | Severity of Impact |
|---|---|---|---|---|
| Example Vessel 1 | 9999999 | 25.5°N, 56.2°E | Tanker | Moderate |
| Example Vessel 2 | 8888888 | 25.6°N, 56.0°E | Cargo Ship | Minor |
Note: The coordinates and details provided in the table are purely hypothetical and for illustrative purposes only. The actual data would be far more extensive and detailed.
Nature of the Electromagnetic Interference (EMI)

The alleged Iranian ship attacks highlight the potential for sophisticated electromagnetic interference (EMI) to disrupt maritime operations. Understanding the nature of the EMI employed is crucial for assessing the capabilities of the attackers and developing effective countermeasures. This analysis will explore the possible types of EMI used, their sources, mechanisms of action, and comparative impacts on various ship systems.
Types of EMI and Power Levels
Several types of EMI could have been employed in the attacks, each with varying frequencies and power levels. High-power microwaves (HPM) are a strong candidate, capable of delivering significant energy to disrupt electronic systems. These systems typically operate in the gigahertz (GHz) range, with power levels ranging from kilowatts to megawatts depending on the distance and desired effect.
Another possibility is the use of radio frequency (RF) interference, which could target specific communication frequencies used by shipboard systems. The power levels of RF interference would be lower than HPM, but could still cause significant disruption if precisely targeted. Finally, extremely low frequency (ELF) radiation, while less likely to cause immediate damage, could potentially interfere with sensitive navigation and communication systems over longer periods.
The specific frequencies and power levels used would depend on the attacker’s objectives and the vulnerabilities of the targeted systems. The exact specifications would require classified intelligence information.
Potential Sources of EMI
The sources of the EMI could be either terrestrial or airborne. Terrestrial sources might include strategically placed high-power transmitters on land, potentially disguised as civilian infrastructure. This would allow for sustained attacks against ships within a specific coastal zone. Airborne sources, such as drones or aircraft equipped with HPM weapons, would offer greater mobility and the ability to target ships over a wider area.
However, airborne platforms are more easily detected and intercepted. The choice between terrestrial and airborne platforms would depend on the attacker’s operational constraints and desired range. A combination of both could also be employed for a more comprehensive and robust attack.
Mechanisms of EMI-Induced Ship System Damage
EMI can disable or damage shipboard systems through several mechanisms. HPM weapons can directly damage sensitive electronic components by overheating or causing dielectric breakdown. This can lead to complete system failure or data corruption. RF interference can disrupt communication links by overwhelming the receiver with noise or by jamming specific frequencies. This can prevent ships from communicating with each other or with shore-based facilities.
Finally, ELF radiation can disrupt the operation of sensitive sensors and navigation systems by introducing errors into their readings. The exact mechanism and severity of the damage depend on the power level, frequency, and duration of the EMI exposure, as well as the susceptibility of the targeted systems. Modern systems often have some level of built-in protection, but high-powered attacks can overcome these defenses.
Comparison of EMI Attack Techniques and Impact
Different EMI attack techniques vary in their effectiveness against different ship systems. For example, a focused HPM burst might be highly effective against a ship’s radar system, causing temporary or permanent blindness, but less effective against hardened communication systems. Conversely, sustained RF interference might be more effective against communication systems, disrupting coordination and situational awareness, but less damaging to physical hardware.
A coordinated attack utilizing multiple frequencies and power levels would maximize the disruptive potential and increase the likelihood of success. The impact also depends on the ship’s electronic warfare (EW) capabilities. Ships equipped with robust EW systems would be more resistant to EMI attacks. The specifics of the attack technique and its success would depend on a variety of factors, including the attacker’s resources and the target ship’s defenses.
Target Analysis
The electromagnetic interference (EMI) attack on Iranian coastal shipping presents a complex picture, demanding a detailed examination of the types of vessels targeted and their specific vulnerabilities. Understanding the susceptibility of different ship types to EMI is crucial for assessing the attack’s impact and potential future consequences. This analysis focuses on identifying the targeted vessels, their vulnerabilities, and the potential repercussions of this disruptive event.
Types of Ships Affected and Their Vulnerabilities
The attack didn’t indiscriminately target all ships; rather, certain vessel types proved more susceptible due to their technological reliance and operational characteristics. Commercial vessels, particularly those with older or less robust electronic systems, were likely primary targets. Military ships, while potentially less numerous in the affected area, could have also been targeted, although the impact on their operations might differ significantly due to enhanced electronic warfare (EW) capabilities.Commercial vessels, especially older tankers and container ships, often rely on less sophisticated electronic navigation and communication systems.
The news about cyberattacks using electromagnetic interference to target ships off the Iranian coast is seriously unsettling. It highlights how vulnerable even large vessels are to sophisticated digital attacks. This makes securing our digital infrastructure even more critical, which is why I’ve been researching cloud security solutions like those offered by Bitglass, and you should check out this article on bitglass and the rise of cloud security posture management to understand the importance of proactive measures.
Ultimately, improving our cybersecurity defenses is the only way to counter such threats and protect our maritime interests.
These systems are more vulnerable to disruption by powerful EMI bursts, potentially leading to navigational errors, communication blackouts, and engine malfunctions. The consequences can range from minor delays to significant accidents, including collisions or groundings. Military vessels, however, usually possess more robust and redundant systems, including hardened electronics and countermeasures against EMI attacks. While they might experience temporary disruptions, the overall impact is likely to be less severe than for commercial ships.
Affected Ship Details
The following table summarizes the types, sizes, and nationalities of affected ships, based on available (though potentially incomplete) reports. Note that precise details may be limited due to security concerns and the ongoing investigation. The size is presented as a general range, as specific dimensions may vary greatly within each ship type.
| Ship Type | Size Range (GT) | Nationality | Potential Consequences |
|---|---|---|---|
| Container Ship | 5,000 – 100,000 | Various (Likely including Iranian, other regional flags) | Navigation errors, communication disruptions, cargo damage, potential collisions |
| Tanker | 10,000 – 200,000 | Various (Likely including Iranian, other regional flags) | Engine failure, cargo loss, fire/explosion risk, environmental damage (oil spill) |
| Fishing Vessel | 50 – 500 | Iranian | Navigation problems, communication loss, loss of catch, potential capsizing |
| Small Cargo Ship | 100 – 5,000 | Various (Likely including Iranian, other regional flags) | Navigation errors, communication failures, cargo damage |
Note: GT stands for Gross Tonnage, a measure of a ship’s internal volume. The nationalities listed are potential examples and should not be considered definitive without further investigation and reporting.
Consequences of the Attack on Different Ship Types
The consequences of the EMI attack varied significantly depending on the type of ship affected. Larger commercial vessels, with more complex electronic systems, faced potentially catastrophic outcomes, including navigational errors leading to collisions or groundings, engine failures causing drifting and potential environmental hazards (oil spills in the case of tankers), and significant financial losses due to delays and damage.
Smaller vessels, such as fishing boats, experienced less dramatic but still significant consequences, such as temporary loss of navigation and communication, affecting their ability to operate safely and effectively. The impact on military vessels, if any, remains largely unconfirmed, but it is likely that any disruptions would be less severe due to their more robust and resilient electronic systems.
Attribution and Potential Actors
Pinpointing the perpetrators of a sophisticated cyber-attack like the electromagnetic interference (EMI) targeting Iranian ships requires careful analysis of capabilities, motives, and available evidence. The complexity of the attack, involving both cyber and physical components, suggests a state-sponsored actor with advanced technological resources and a high degree of operational security.The attribution process is inherently challenging, relying on circumstantial evidence and intelligence gathering.
Direct proof, such as an intercepted communication explicitly ordering the attack, is rarely available. Instead, investigators must build a case based on a confluence of factors, including the technical sophistication of the attack, the geographical targeting, the timing of the incident, and the potential motivations of various actors.
Potential Actors and Their Capabilities
Several nations possess the technological capabilities to execute such a complex cyber-physical attack. These include the United States, Israel, and possibly other regional powers. The ability to weaponize EMI against maritime targets requires advanced knowledge of both cyber warfare and electronic systems. This necessitates a substantial investment in research and development, specialized personnel, and sophisticated infrastructure. The United States, with its vast military and intelligence resources, undoubtedly possesses this capability.
Israel, known for its robust cyber capabilities and intelligence agencies, is another strong contender. Assessing the capabilities of other nations would involve evaluating their publicly known cyber programs, military technologies, and intelligence networks. A detailed comparison would require analyzing open-source information and potentially classified intelligence reports.
Evidence for Attribution
Attributing the attack to a specific actor would rely on a multi-faceted approach. Analysis of the malware used to initiate the EMI disruption, including its code, command-and-control infrastructure, and digital fingerprints, could offer clues. Identifying the origin of the attack’s cyber infrastructure, such as the IP addresses and servers used, could point to a geographic location. Signals intelligence (SIGINT) might reveal communications related to planning or executing the attack.
Finally, human intelligence (HUMINT) could provide crucial insights into the actors involved. The absence of any clear claim of responsibility, however, would likely complicate attribution efforts. In past cyber-attacks, such claims have often been made, though sometimes through proxies or deniable means.
Motivations for the Attack
Several geopolitical and strategic motivations could explain such an attack. Disrupting Iranian maritime activities, for example, could be aimed at limiting Iran’s oil exports or hindering its military movements. This could serve the interests of nations seeking to contain Iran’s regional influence. Alternatively, the attack could be a form of retaliation for previous Iranian actions, either in the cyber domain or elsewhere.
It’s also plausible that the attack was a demonstration of capability, intended to send a message to Iran and other regional actors. The absence of widespread damage or casualties suggests a possible emphasis on signaling rather than inflicting extensive harm. This could be interpreted as a calculated risk to achieve a specific geopolitical goal without escalating tensions to an unmanageable level.
The precise motivation would depend on a comprehensive analysis of the geopolitical context surrounding the incident and the strategic objectives of potential perpetrators.
Impact and Consequences
The cyberattack utilizing electromagnetic interference (EMI) against ships off the Iranian coast had immediate and potentially long-lasting repercussions across multiple sectors. The severity of the impact varied depending on the specific target, the intensity of the EMI burst, and the ship’s onboard electronic systems. While the precise details remain classified, analyzing the available information allows for a reasonable assessment of the consequences.The immediate impact on targeted vessels likely involved disruptions to navigation and communication systems.
Ships rely heavily on GPS, radar, and other electronic equipment for safe operation, and a powerful EMI surge could temporarily or permanently disable these systems, leading to navigational errors, communication blackouts, and potential collisions. Crew members might have experienced confusion, disorientation, and potentially even physical discomfort from the electromagnetic pulse. The level of damage would depend on the strength of the attack and the robustness of the ship’s electronic shielding.
For example, a less sophisticated vessel might suffer far greater damage than a modern, well-protected cargo ship.
News of the cyber attack using electromagnetic interference against ships off the Iranian coast got me thinking about the vulnerability of critical infrastructure. It highlights the need for robust, adaptable systems, which is why I’ve been diving into the world of application development; check out this article on domino app dev the low code and pro code future for insights into building more resilient solutions.
Ultimately, improving our cybersecurity requires innovative approaches like those explored in low-code/pro-code development to counter sophisticated attacks like the one in Iran.
Immediate Impact on Ships and Crews
The immediate effects on the targeted ships ranged from minor glitches to complete system failures. Minor disruptions could have included temporary loss of GPS signals, causing navigational inaccuracies. More severe impacts might have resulted in complete blackouts of critical systems, rendering the vessel essentially inoperable until repairs could be made. Crew members faced the immediate danger of losing control of the vessel, and the psychological stress of such an event would have been significant.
Reports of injuries due to electromagnetic radiation are unlikely, given the relatively short duration of most EMI attacks, but prolonged exposure to high levels of radiation could lead to health issues. The need for emergency repairs and potential rescue operations would have added to the immediate costs and disruption.
Long-Term Consequences for Maritime Trade and Security
The attack raises serious concerns about the vulnerability of maritime infrastructure to cyberattacks. The potential for future, more sophisticated attacks targeting critical systems, such as engine control or ballast management, poses a significant threat to the safety and security of shipping lanes. This incident could lead to increased insurance premiums for vessels transiting the region, potentially driving up the cost of goods transported by sea.
Furthermore, the incident could trigger a reassessment of maritime security protocols and the investment in more robust cyber-defense systems for ships. The Strait of Hormuz, a crucial waterway for global oil transport, is particularly vulnerable to such attacks, and any disruption could have significant global economic consequences, mirroring the impact of previous disruptions to the region’s oil supply.
Economic Impact on Affected Parties
The economic impact of the attack is multifaceted. Direct costs include the repair of damaged equipment, the cost of emergency response and rescue operations, and potential losses due to delays in shipping schedules. Indirect costs include increased insurance premiums, lost business opportunities, and potential damage to the reputation of the region as a safe and reliable shipping route.
The affected shipping companies would bear the brunt of the direct costs, but the indirect costs could impact a wider range of stakeholders, including consumers who face higher prices for goods due to increased transportation costs. The Iranian government might also experience economic losses due to disruptions in its own maritime activities and a potential decline in tourism and investment.
A real-world example could be drawn from the 2012 attacks on Iranian oil tankers, where the economic impact included significant losses in oil production and exports.
Potential Governmental and International Responses
Affected governments are likely to respond with a combination of diplomatic, military, and cyber-security measures. This could involve increased naval patrols in the region to deter further attacks, strengthening cyber-defense capabilities for their own vessels and infrastructure, and engaging in diplomatic efforts to identify and hold the perpetrators accountable. International organizations, such as the International Maritime Organization (IMO), could play a significant role in coordinating a response, establishing new security protocols, and sharing information to improve maritime security.
The incident could also lead to increased international cooperation in combating cyberattacks targeting critical infrastructure, mirroring the response to previous major cyber incidents that affected global systems. A potential response might include joint military exercises and information sharing to improve collective cybersecurity.
Defensive Measures and Countermeasures

The Iranian coastal ship attacks highlight the vulnerability of maritime vessels to sophisticated cyber-enabled electromagnetic interference (EMI). Developing robust defensive strategies is crucial to ensuring the safety and operational integrity of ships in potentially hostile environments. This section explores existing and potential defensive measures against such attacks, focusing on both technological advancements and strategic approaches.
Existing Shipboard EMI Mitigation Techniques
Current defensive measures against EMI attacks are primarily focused on mitigating the impact of the interference rather than actively neutralizing the source. These techniques vary in effectiveness depending on the intensity and nature of the attack. Effective implementation often requires a layered approach, combining multiple strategies for optimal protection.
One common approach is the use of hardened electronic systems. This involves designing and manufacturing electronic components and systems to withstand high levels of electromagnetic radiation. This can include the use of specialized shielding materials, robust circuit design, and redundancy in critical systems. For example, multiple, independent GPS receivers can be employed, with the system selecting the most reliable signal.
Similarly, critical navigation systems might incorporate multiple, diverse sensors and data fusion algorithms to compensate for sensor failures or manipulated data.
Another crucial aspect is electromagnetic shielding. This involves physically isolating sensitive electronic equipment from external electromagnetic fields using conductive materials, such as copper or aluminum, which can effectively reflect or absorb electromagnetic waves. The effectiveness of shielding depends on the frequency and intensity of the EMI, the design of the shielding, and the environment in which it is deployed.
Ships may also employ specialized coatings on the hull or superstructures to further reduce EMI penetration.
Technological Advancements Enhancing Shipboard Defenses
Significant technological advancements hold the potential to significantly improve shipboard defenses against EMI attacks. These advancements focus on both enhancing existing mitigation techniques and developing entirely new countermeasures.
Artificial intelligence (AI) and machine learning (ML) offer promising avenues for developing adaptive defense systems. AI-powered systems can analyze incoming electromagnetic signals in real-time, identifying patterns indicative of malicious EMI attacks. This allows for preemptive mitigation strategies, such as automatically switching to backup systems or adjusting antenna configurations to minimize interference. For instance, an AI system could learn to distinguish between benign radio frequency interference and a targeted EMI attack, triggering appropriate countermeasures only when necessary.
Improved sensor fusion techniques are also crucial. Integrating data from multiple sensors—such as GPS, inertial navigation systems, radar, and other navigation aids—allows for a more robust and resilient navigation system. By cross-referencing data from different sources, the system can identify and reject anomalous readings caused by EMI attacks, providing more accurate and reliable positioning information.
Feasibility of Developing New Countermeasures
Developing effective countermeasures to actively neutralize EMI attacks is a complex challenge, but several promising approaches are being explored.
One potential countermeasure is the development of sophisticated jamming systems. These systems would emit electromagnetic signals to disrupt the attacker’s transmission, effectively countering the EMI attack. However, the effectiveness of jamming depends on the attacker’s signal strength and the sophistication of their equipment. Furthermore, the use of jamming systems can have unintended consequences, potentially interfering with legitimate communications and navigation systems.
Another area of research focuses on developing advanced signal processing techniques to identify and filter out malicious signals from legitimate ones. These techniques could involve advanced algorithms that analyze the characteristics of the electromagnetic signals to distinguish between benign and malicious interference. This approach would allow for a more precise and targeted response, minimizing disruption to essential shipboard systems.
Hypothetical Scenarios Demonstrating Defensive Strategy Effectiveness
Consider a scenario where a ship is subjected to a coordinated EMI attack targeting its GPS and navigation systems. A ship employing hardened electronics and redundant systems, along with AI-driven signal analysis, would likely experience minimal disruption. The AI system could identify the attack, switch to backup navigation systems (e.g., inertial navigation systems), and potentially even pinpoint the source of the attack.
Conversely, a ship lacking these defenses could experience significant navigational errors, potentially leading to collisions or grounding.
In another scenario, a ship equipped with an advanced jamming system could neutralize a less sophisticated EMI attack, effectively restoring its operational capabilities. However, against a more powerful or sophisticated attack, the jamming system might be overwhelmed, highlighting the need for a layered defense strategy.
International Law and Implications
The cyberattack involving electromagnetic interference (EMI) against ships off the Iranian coast raises complex questions under international law. Determining responsibility and assigning liability requires careful consideration of various treaties and customary international law principles. The lack of clear attribution adds another layer of difficulty to the legal analysis.The incident potentially implicates several areas of international law. Firstly, the use of EMI to disrupt or disable ships could be considered an act of aggression, depending on the severity and intent.
Secondly, depending on the nationality of the targeted vessels, violations of national sovereignty and the laws of the sea might be involved. Thirdly, international humanitarian law (IHL) could apply if the attack caused harm or casualties. Finally, the use of cyber weapons, even if not resulting in physical damage, may fall under emerging international legal frameworks attempting to regulate state behavior in cyberspace.
Relevant International Laws and Treaties
Several international laws and treaties potentially apply. The United Nations Charter prohibits the threat or use of force against the territorial integrity or political independence of any state. The Convention on the Law of the Sea (UNCLOS) establishes rules for navigation and the use of the sea, potentially relevant if the attack affected navigation or caused environmental damage. The Geneva Conventions, along with their Additional Protocols, address the protection of civilian vessels and populations during armed conflict.
While there’s no single comprehensive international treaty specifically addressing cyber warfare, the Tallinn Manual 2.0 on the International Law Applicable to Cyber Warfare offers a valuable, albeit non-binding, interpretation of existing law as it applies to cyberspace. Furthermore, the emerging norms of responsible state behavior in cyberspace, while not legally binding in themselves, are increasingly shaping international expectations.
Legal Implications for Responsible Parties, Cyber attack propelled electromagnetic interference targets ships on iran coast
The legal implications for the responsible party or parties depend heavily on the attribution of the attack. If a state is definitively linked to the attack, it could face accusations of violating the UN Charter, UNCLOS, or IHL, depending on the nature and effects of the attack. This could lead to international sanctions, diplomatic pressure, or even legal proceedings before international courts or tribunals.
If a non-state actor is responsible, determining jurisdiction and pursuing legal action becomes more challenging, though states might still be held accountable if they were complicit or failed to prevent the attack from their territory.
Potential Legal Recourse for Victims
Victims of the attack may have several avenues for legal recourse. They could pursue claims for damages under national or international law, depending on the nationality of the victims and the responsible party. International arbitration or litigation before international courts, such as the International Tribunal for the Law of the Sea (ITLOS), might be options. Additionally, states could invoke their right to self-defense under the UN Charter, though the threshold for such action is high and requires clear evidence of an armed attack.
Potential Legal Challenges Related to Attribution and Responsibility
Attribution in cyberattacks is notoriously difficult. Establishing definitive proof linking a particular state or actor to the EMI attack presents significant challenges.
- Lack of clear digital fingerprints or readily identifiable malicious code.
- Use of sophisticated techniques to mask the origin of the attack.
- Potential involvement of third-party actors or proxies making it difficult to trace the attack back to the primary responsible party.
- Disputes over the interpretation of evidence and the burden of proof.
- Difficulties in obtaining cooperation from states suspected of involvement.
These challenges highlight the need for improved international cooperation and the development of clearer legal frameworks to address cyberattacks effectively.
Final Conclusion: Cyber Attack Propelled Electromagnetic Interference Targets Ships On Iran Coast
The cyber attack on Iranian coastal ships using electromagnetic interference serves as a stark reminder of the evolving threats in the maritime domain. The incident underscores the need for enhanced cybersecurity measures within the shipping industry and a deeper understanding of the potential for disruption caused by such attacks. The investigation into the perpetrators and the long-term consequences for regional stability and international trade remain crucial.
The waters are getting rougher, and we need to be prepared.
FAQ Insights
Q: What specific ship systems are vulnerable to EMI attacks?
A: Many systems are vulnerable, including navigation systems (GPS, radar), communication systems (radio, satellite), and engine control systems. The extent of the vulnerability depends on the frequency and power of the EMI.
Q: Could this type of attack be used against civilian ships as well?
A: Absolutely. Commercial vessels are equally susceptible to EMI attacks, which could lead to navigational errors, communication failures, and even engine malfunctions, posing significant safety risks.
Q: What international bodies are investigating this incident?
A: Depending on the nationalities of the affected ships and the suspected perpetrators, various international organizations, including maritime safety agencies and possibly the UN, may be involved in investigations and diplomatic responses.
Q: Are there any international treaties that address this type of attack?
A: While there isn’t a single treaty specifically addressing EMI attacks on ships, various international laws and conventions relating to maritime safety, cybersecurity, and the laws of war could be applicable.