Cyber Attacks The Next State-Level Weapon
Cyber attacks now being targeted as the next state level weapons – Cyber attacks now being targeted as the next state-level weapons is no longer a futuristic fantasy; it’s chilling reality. We’re witnessing a dramatic escalation in cyber warfare, moving far beyond simple hacking sprees. Sophisticated state-sponsored attacks are targeting critical infrastructure, manipulating elections, and even disrupting entire economies. This isn’t just about stealing data anymore; it’s about wielding digital destruction as a tool of geopolitical power.
This post dives deep into the evolving landscape of state-sponsored cyberattacks, exploring their motivations, methods, and the crucial steps we need to take to defend ourselves.
The evolution of cyberattacks is a fascinating, and terrifying, story. From isolated incidents, we’ve progressed to coordinated campaigns orchestrated by nation-states, employing increasingly sophisticated tools and techniques. We’ll examine specific examples of these attacks, exploring the motivations behind them and the devastating consequences they can unleash. We’ll also look at how different countries are leveraging cyber warfare to achieve their strategic objectives, creating a complex and ever-shifting global landscape.
The Escalation of Cyber Warfare
The digital realm, once a relatively peaceful frontier, has become a new battleground for nation-states. What began as isolated incidents of hacking and data breaches has evolved into a sophisticated and increasingly dangerous form of warfare, with cyberattacks now considered a key component of modern military strategy. The stakes are higher than ever, as the potential for widespread disruption and even physical damage continues to grow.The evolution of cyberattacks mirrors the development of conventional weaponry.
Early attacks were relatively simple, often targeting individual systems or networks for espionage or vandalism. However, over time, nation-states have invested heavily in developing sophisticated cyber weapons, capable of causing widespread and devastating damage. This includes the development of highly advanced malware, capable of self-propagation and evasion of security measures, and the creation of dedicated cyber warfare units within military and intelligence organizations.
These units possess advanced technical expertise and the resources to plan and execute large-scale attacks.
The Sophistication of Cyber Weapons and Their Destructive Potential
Modern cyber weapons are far more sophisticated than their predecessors. They are designed not just to steal data or disrupt services, but to inflict significant damage on critical infrastructure. This includes the potential to disable power grids, disrupt financial systems, and even control industrial processes. The Stuxnet worm, for example, demonstrated the ability to physically damage industrial centrifuges used in Iran’s nuclear program, showcasing the potential for cyberattacks to have real-world, physical consequences.
The development of artificial intelligence and machine learning is further enhancing the capabilities of cyber weapons, allowing for more autonomous and adaptive attacks that are harder to detect and defend against. The destructive potential is immense, extending beyond simple data theft to encompass widespread societal disruption.
Cyber Warfare Capabilities of Nation-States
The capabilities of different nation-states in cyber warfare vary significantly. Countries like the United States, China, Russia, and Israel are generally considered to possess the most advanced cyber warfare capabilities. These nations have dedicated cyber commands within their militaries, significant investments in research and development, and highly skilled personnel. Other countries are also developing their cyber warfare capabilities, although they may lag behind in terms of sophistication and resources.
The asymmetry in capabilities creates a complex and potentially unstable global security environment. Smaller nations might rely on state-sponsored actors or even private mercenary groups to conduct cyber operations, blurring the lines of attribution and accountability.
Examples of Recent High-Profile Cyberattacks Attributed to State Actors, Cyber attacks now being targeted as the next state level weapons
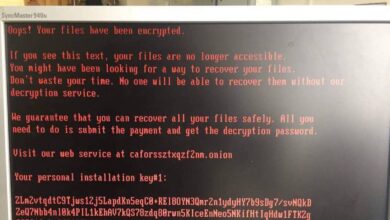
The NotPetya ransomware attack of 2017, widely attributed to Russia, caused billions of dollars in damage globally by crippling businesses and disrupting critical infrastructure. The SolarWinds attack of 2020, attributed to Russia’s foreign intelligence service, compromised numerous US government agencies and private sector companies, demonstrating the potential for large-scale espionage and data theft. The ongoing cyberattacks against Ukraine, attributed to various state-sponsored actors, highlight the use of cyber warfare as a tool in hybrid warfare scenarios, combining cyberattacks with conventional military actions.
These examples demonstrate the increasing frequency and severity of state-sponsored cyberattacks, and the potential for significant geopolitical consequences.
Types of State-Sponsored Cyberattacks: Cyber Attacks Now Being Targeted As The Next State Level Weapons

State-sponsored cyberattacks represent a significant threat to global security, transcending traditional warfare and targeting critical infrastructure, economic stability, and even the democratic process. These attacks are often sophisticated, well-resourced, and designed to achieve specific geopolitical objectives, making attribution challenging and response difficult. Understanding the various types of these attacks is crucial for developing effective defense strategies.
Nation-state actors employ a diverse range of cyberattack techniques, each designed to achieve specific goals. These attacks can be broadly categorized into espionage, sabotage, and disinformation campaigns, although there is often overlap between these categories.
Espionage
Espionage through cyber means involves the clandestine acquisition of sensitive information from government agencies, corporations, and other organizations. Techniques include exploiting vulnerabilities in software, using malware to steal data, and employing phishing attacks to gain access to credentials. Sophisticated tools like custom-built malware and advanced persistent threats (APTs) are frequently used to maintain persistent access and evade detection.
The stolen information can range from military secrets and intellectual property to personal data and financial records.
| Attack Type | Target | Perpetrator (if known) | Outcome |
|---|---|---|---|
| Data Breach via APT | US Office of Personnel Management | Likely Chinese government | Millions of personnel records compromised, significant damage to US national security |
| Network Intrusion | Various European energy companies | Likely Russian government | Industrial espionage, potential for sabotage, disruption of energy supply |
The impact of state-sponsored espionage on national security is profound. The theft of sensitive information can compromise national defense capabilities, undermine economic competitiveness, and erode public trust.
Sabotage
Cyber sabotage focuses on disrupting or destroying critical infrastructure and systems. This can involve disabling power grids, disrupting transportation networks, or compromising financial institutions. Techniques include deploying destructive malware (like Stuxnet), exploiting vulnerabilities to cause system failures, and launching distributed denial-of-service (DDoS) attacks to overwhelm systems.
| Attack Type | Target | Perpetrator (if known) | Outcome |
|---|---|---|---|
| Industrial Control System Compromise | Ukrainian power grid | Likely Russian government | Widespread power outages, disruption of essential services |
| Destructive Malware | Iranian nuclear facilities | US and Israeli intelligence (attributed) | Setback in Iranian nuclear program |
The impact of cyber sabotage on critical infrastructure can be devastating, leading to widespread power outages, transportation disruptions, and economic losses. Such attacks can also have significant consequences for national security, potentially undermining a nation’s ability to respond to emergencies.
With cyber attacks increasingly viewed as the next generation of state-sponsored weaponry, robust security is paramount. Understanding and mitigating vulnerabilities is crucial, and that’s where solutions like cloud security posture management become essential. Check out this insightful article on bitglass and the rise of cloud security posture management to learn how to better protect your systems against these sophisticated, state-level threats.
The fight against these attacks is an ongoing one, demanding constant vigilance and adaptation.
Disinformation
State-sponsored disinformation campaigns utilize cyberattacks to spread false or misleading information to manipulate public opinion, undermine trust in institutions, and sow discord. Techniques include creating and disseminating fake news articles, using social media bots to amplify propaganda, and hacking into news websites or social media accounts to spread false narratives.
| Attack Type | Target | Perpetrator (if known) | Outcome |
|---|---|---|---|
| Social Media Manipulation | US 2016 Presidential Election | Russian Internet Research Agency (IRA) | Spread of disinformation, influence on election outcome, erosion of public trust |
| Hacking and Leaks | Various political organizations and individuals | Various nation-states | Release of sensitive information, damage to reputation, political instability |
The impact of disinformation campaigns on national security is far-reaching. The erosion of public trust in institutions, the spread of misinformation, and the manipulation of public opinion can destabilize governments, fuel social unrest, and undermine democratic processes.
Motivations Behind State-Sponsored Cyberattacks
State-sponsored cyberattacks are rarely random acts. They are meticulously planned and executed operations driven by a complex interplay of geopolitical interests, economic ambitions, and military strategies. Understanding these motivations is crucial to comprehending the escalating threat of cyber warfare and developing effective countermeasures. The actors involved aren’t just rogue hackers; they are often highly trained professionals working within the framework of national intelligence agencies and military structures.The primary drivers behind these attacks are often deeply rooted in a nation’s foreign policy objectives and its perception of its own national security.
These actions are frequently designed to achieve specific goals, whether it be gaining a strategic advantage, undermining a rival, or protecting national interests. The methods employed are sophisticated and constantly evolving, reflecting the increasing sophistication of technology and the determination of state actors to use cyberspace as a battleground.
Geopolitical Motivations
Geopolitical rivalries are a significant catalyst for state-sponsored cyberattacks. Nations may launch attacks to destabilize their adversaries, influence political outcomes in other countries, or even directly interfere in elections. For example, the alleged Russian interference in the 2016 US presidential election exemplifies the use of cyberattacks to achieve political objectives – specifically, to sow discord and influence the outcome in favor of a preferred candidate.
Similarly, accusations of Chinese cyber espionage targeting intellectual property demonstrate the economic dimension of these attacks, aimed at gaining a technological and economic edge. The motivations can be subtle, like using disinformation campaigns to erode public trust, or overt, such as launching crippling attacks on critical infrastructure.
Economic Objectives
Cyberattacks are increasingly employed to achieve economic goals, ranging from corporate espionage to outright theft. State-sponsored actors often target businesses and government agencies to steal intellectual property, trade secrets, or financial information. This can provide a significant economic advantage to the attacker, enabling them to develop new technologies, gain a competitive edge in the marketplace, or even cripple a competitor’s operations.
The theft of intellectual property from companies in various sectors, including aerospace and pharmaceuticals, has been widely attributed to state-sponsored actors seeking to gain a technological advantage without the cost of research and development.
Military Objectives
Military objectives often overlap with geopolitical and economic ones. Cyberattacks can be used to disrupt military operations, disable critical infrastructure, or gather intelligence on an adversary’s capabilities. This can involve targeting military command and control systems, communication networks, or even weapon systems themselves. The Stuxnet worm, a sophisticated piece of malware believed to have been jointly developed by the US and Israel, is a prime example of a cyberattack targeting a specific industrial process – in this case, Iran’s nuclear enrichment program – for military purposes.
These attacks aim to inflict damage or disruption without resorting to traditional kinetic warfare, providing a deniable and potentially more cost-effective means of achieving military goals.
The Role of Intelligence Agencies and Military Units
Intelligence agencies and military units play a central role in planning and executing state-sponsored cyberattacks. These organizations possess the resources, expertise, and legal authority to conduct such operations. They are responsible for identifying targets, developing attack strategies, deploying malware, and managing the aftermath of an attack. These actors often operate in secrecy, making attribution difficult and adding to the complexity of addressing the issue.
The level of sophistication and resources employed often points to state-level actors rather than individual hackers or criminal groups. This underscores the organized and coordinated nature of these cyber operations.
Defending Against State-Sponsored Cyberattacks
The rise of state-sponsored cyberattacks necessitates a robust and multi-faceted approach to national cybersecurity. No single nation can effectively defend against these sophisticated threats alone; a collaborative, globally coordinated strategy is crucial. This requires a blend of technological advancements, proactive policy changes, and a well-educated populace capable of recognizing and responding to cyber threats.A National Cybersecurity Strategy Framework must be built on several key pillars.
A National Cybersecurity Strategy Framework
A comprehensive national cybersecurity strategy should incorporate a layered defense approach, combining preventative measures with robust detection and response capabilities. This framework should prioritize the protection of critical infrastructure, such as power grids, financial institutions, and government agencies, while also safeguarding the privacy and security of citizens’ data. Regular vulnerability assessments and penetration testing are essential, alongside the development and implementation of incident response plans.
These plans should Artikel clear procedures for containing and mitigating the impact of successful attacks, including effective communication strategies to inform the public and relevant authorities. Furthermore, robust data backup and recovery systems are vital to ensure business continuity in the event of a successful attack. The framework must also address the legal and regulatory aspects of cybersecurity, ensuring that appropriate laws and regulations are in place to deter malicious actors and provide a clear legal framework for responding to incidents.
Finally, the strategy must be adaptable and continuously evolving to address the ever-changing nature of cyber threats.
International Cooperation in Addressing Cyber Threats
Effective international cooperation is paramount in combating state-sponsored cyberattacks. Sharing threat intelligence, coordinating responses to large-scale attacks, and establishing common standards for cybersecurity practices are crucial steps. Existing international organizations, such as the UN and Interpol, can play a vital role in facilitating this cooperation. However, the challenge lies in building trust and establishing clear norms of behavior in cyberspace, given the varying geopolitical interests and levels of technological capability among nations.
Agreements on attribution of attacks and mechanisms for resolving cyber disputes are necessary to deter future aggression. Examples of successful collaborations, while limited, include information sharing agreements between intelligence agencies of allied nations and joint cybersecurity exercises aimed at improving incident response capabilities. These initiatives demonstrate the potential for effective international cooperation, but much more is needed to create a truly global cybersecurity ecosystem.
The Importance of Cybersecurity Education and Awareness
Cybersecurity education and awareness are vital components of any effective defense strategy. Individuals, businesses, and government agencies must be equipped with the knowledge and skills to identify and mitigate cyber threats. This includes educating the public on safe online practices, such as strong password management, phishing awareness, and the importance of software updates. Furthermore, training programs for cybersecurity professionals are essential to address the growing skills gap in the field.
Investing in educational initiatives at all levels, from primary schools to universities, is crucial to build a cybersecurity-aware populace capable of contributing to a safer digital environment. Public awareness campaigns can highlight the risks of cyberattacks and empower individuals to take proactive steps to protect themselves and their data. The success of these campaigns hinges on clear, concise messaging and the use of diverse communication channels to reach a broad audience.
Effective Defensive Measures
Effective defensive measures involve a combination of technological solutions and policy recommendations. Technological solutions include advanced threat detection systems, intrusion prevention systems, and security information and event management (SIEM) tools. These systems leverage machine learning and artificial intelligence to identify and respond to sophisticated cyber threats. Policy recommendations include implementing robust access control policies, enforcing strong authentication measures (such as multi-factor authentication), and regularly conducting security audits and vulnerability assessments.
With cyber attacks increasingly becoming the new battlefield for nation-states, robust and secure application development is paramount. This is where understanding the advancements in application building, like those discussed in this insightful article on domino app dev the low code and pro code future , becomes crucial. Strengthening our digital defenses requires a focus on secure coding practices and resilient application architectures to counter these sophisticated, state-sponsored threats.
Furthermore, the development and implementation of incident response plans is crucial to minimize the impact of successful attacks. Investing in cybersecurity research and development is also essential to stay ahead of evolving threats. Examples of effective defensive measures include the use of endpoint detection and response (EDR) solutions to monitor and protect individual computers and servers, and the implementation of zero-trust security models that limit access to sensitive data based on continuous verification of user identity and device security.
The adoption of these measures, coupled with strong policy frameworks, can significantly enhance the resilience of national infrastructure and minimize the impact of state-sponsored cyberattacks.
The Future of Cyber Warfare
The landscape of cyber warfare is rapidly evolving, driven by advancements in artificial intelligence, automation, and the increasing interconnectedness of our digital world. Predicting the future with certainty is impossible, but by examining current trends and technological advancements, we can anticipate a future where cyberattacks become more sophisticated, pervasive, and devastating. The lines between physical and cyber conflict will continue to blur, necessitating a proactive and adaptable approach to defense.The increasing sophistication of cyberattacks will be fueled by AI and automation.
This means faster, more targeted attacks, capable of adapting and learning in real-time. The human element will remain crucial, but AI will amplify both offensive and defensive capabilities dramatically.
AI and Automation in State-Sponsored Cyberattacks
AI’s impact on cyber warfare is multifaceted. On the offensive side, AI can automate the identification of vulnerabilities, the creation of malware, and the execution of attacks at scale. Imagine a scenario where AI autonomously scans millions of devices for weaknesses, deploys custom-made malware tailored to each victim, and then evades detection by constantly adapting its tactics. This level of automation allows for attacks to be launched simultaneously against numerous targets, overwhelming defensive capabilities.
Defensively, AI can analyze vast amounts of data to identify patterns indicative of malicious activity, predict future attacks, and automatically respond to threats in real-time. However, a crucial consideration is that AI can be used by both sides, creating an escalating arms race in cyber capabilities.
Escalation and Large-Scale Cyber Conflicts
The risk of large-scale cyber conflicts is substantial. A successful attack on critical infrastructure, such as power grids or financial systems, could have cascading effects across entire nations. The interconnected nature of global systems means that a cyberattack in one country could quickly destabilize others. The potential for miscalculation and accidental escalation is high, particularly if AI systems are involved in automated responses to attacks.
The lack of clear rules of engagement in cyberspace further exacerbates the risk. Consider the Stuxnet worm, a sophisticated cyberweapon believed to have been jointly developed by the US and Israel to disrupt Iranian nuclear facilities. While not a full-scale conflict, it demonstrated the potential for devastating cyberattacks against critical infrastructure, setting a precedent for future actions.
A Potential Future Cyberattack Scenario
Imagine a coordinated cyberattack targeting multiple nations’ financial institutions simultaneously. AI-powered malware, capable of self-propagation and adaptation, exploits vulnerabilities in legacy systems and rapidly compromises networks. The attack causes widespread disruption, freezing transactions, wiping out accounts, and triggering a global financial crisis. The perpetrators remain anonymous, leveraging sophisticated techniques to mask their origins and evade detection. Governments struggle to respond effectively, highlighting the limitations of existing cybersecurity infrastructure and international cooperation.
The ensuing economic chaos and political instability could escalate into a wider conflict, demonstrating the potential for cyber warfare to trigger significant geopolitical consequences.
Technological Advancements and Their Impact
Advancements in quantum computing pose both threats and opportunities. Quantum computers could break current encryption methods, rendering many cybersecurity measures obsolete. However, they also offer the potential for developing new, more secure cryptographic techniques. Similarly, the development of more powerful AI systems will lead to more sophisticated attacks, but also more effective defenses. The development of blockchain technology could offer increased security and transparency in financial transactions, mitigating the risk of some types of cyberattacks.
The race between offensive and defensive capabilities will continue to be a defining feature of cyber warfare, with each side constantly seeking to gain an advantage.
Illustrative Examples of Cyberattacks as Weapons
Cyberattacks are no longer just the domain of criminal actors; they’ve become sophisticated tools wielded by nation-states to achieve geopolitical objectives. These attacks, often meticulously planned and executed, can cripple critical infrastructure, steal sensitive information, and even influence elections. Understanding these attacks requires examining specific examples, delving into their technical aspects, and analyzing their broader impact on the global stage.
Stuxnet Worm
Stuxnet, discovered in 2010, is widely considered a landmark example of a state-sponsored cyberattack. Its sophistication and impact established a new benchmark for the destructive potential of cyber weaponry.
- Target: Iranian nuclear enrichment facilities at Natanz.
- Method: A highly sophisticated worm that infiltrated the industrial control systems (ICS) managing the centrifuges used in uranium enrichment. It subtly manipulated the centrifuges, causing them to malfunction and self-destruct, while masking its presence to avoid immediate detection.
- Outcome: Significant damage to Iran’s nuclear program, delaying its progress by several years. The attack demonstrated the vulnerability of critical infrastructure to cyberattacks and set a precedent for future state-sponsored operations.
Stuxnet leveraged several advanced techniques. It used zero-day exploits, vulnerabilities unknown to the software vendors, to gain initial access. It then spread laterally through the network, targeting specific systems. The worm used a combination of rootkit technology to hide its presence and sophisticated logic to manipulate the centrifuge control systems. The complexity of the attack highlighted the need for robust ICS security measures.
The geopolitical context involved the international community’s concerns about Iran’s nuclear ambitions. The attack, widely attributed to a collaboration between the US and Israel, intensified tensions in the region and sparked a global debate about the ethics and legality of offensive cyber operations.
NotPetya
NotPetya, unleashed in 2017, was a devastating ransomware attack that spread globally, causing billions of dollars in damage. While initially appearing as a simple ransomware attack, evidence points to its use as a weapon, likely by the Russian government.
- Target: Ukrainian businesses and government entities, with global spillover effects.
- Method: The attack leveraged a vulnerability in the Ukrainian accounting software M.E.Doc, which was widely used in the country. Once inside the network, the malware spread rapidly, encrypting files and crippling systems. Unlike typical ransomware, NotPetya’s primary goal wasn’t financial gain; it was disruption and destruction.
- Outcome: Massive disruption to businesses worldwide, particularly in Ukraine and several other countries. The attack highlighted the interconnectedness of global systems and the potential for cyberattacks to have far-reaching economic consequences. The scale of damage and the lack of a clear path to recovery underscored the severity of sophisticated cyberattacks as weapons.
NotPetya’s technical aspects involved a highly effective wiper function that permanently deleted data, making recovery extremely difficult. It exploited a known vulnerability in M.E.Doc but also used several other techniques to propagate rapidly, including EternalBlue, an exploit leaked from the NSA. The geopolitical context involved ongoing tensions between Russia and Ukraine. The attack, although denied by Russia, was widely seen as an act of aggression, escalating cyber tensions between nation-states.
SolarWinds Supply Chain Attack
The SolarWinds supply chain attack, discovered in late 2020, represents a new level of sophistication in state-sponsored cyber espionage. This attack highlighted the vulnerability of software supply chains and the potential for widespread compromise.
- Target: Numerous US government agencies and private sector organizations via compromised SolarWinds Orion software.
- Method: The attackers infiltrated SolarWinds’ software update process, inserting malicious code into the Orion platform. This allowed them to gain access to the networks of thousands of SolarWinds customers who subsequently updated their software.
- Outcome: Significant compromise of sensitive information from various US government agencies and private companies. The attack exposed vulnerabilities in the software supply chain and raised serious concerns about national security.
The technical aspects involved a highly sophisticated and stealthy approach. The malicious code, known as Sunburst, was designed to remain undetected for extended periods. The attackers used a combination of techniques to maintain persistence and access, demonstrating a high level of skill and resources. The geopolitical context is linked to the ongoing strategic competition between the US and Russia.
The attack, widely attributed to Russian intelligence agencies, further strained relations and intensified the debate about cybersecurity and national security.
Final Summary

The rise of cyberattacks as state-level weapons marks a profound shift in global power dynamics. The future of warfare is increasingly digital, and understanding the intricacies of this new battleground is paramount. While the challenges are immense, so too is the potential for collaboration and innovation in cybersecurity. By strengthening international cooperation, investing in robust defenses, and fostering a global culture of cyber awareness, we can hope to mitigate the risks and build a more secure digital future.
But let’s be clear – the fight for online security is far from over, and vigilance is key.
Essential Questionnaire
What are some common targets of state-sponsored cyberattacks?
Critical infrastructure (power grids, water systems), financial institutions, government agencies, and private companies holding sensitive data are frequent targets.
How can individuals protect themselves from state-sponsored cyberattacks?
Practice good cybersecurity hygiene: strong passwords, up-to-date software, caution with phishing emails, and using reputable antivirus software are crucial.
What role does international cooperation play in countering state-sponsored cyberattacks?
International cooperation is vital for sharing threat intelligence, developing common standards, and establishing frameworks for attribution and response to attacks.
What is the role of AI in future cyber warfare?
AI could significantly enhance both offensive and defensive capabilities, leading to more autonomous and sophisticated attacks and defenses.