EU Cyber Resilience Act IAR Systems Simplifies Embedded Security
Eu cyber resilience act iar systems stands ready to provide embedded developers with security made simple – EU Cyber Resilience Act: IAR Systems stands ready to provide embedded developers with security made simple. This is HUGE news for anyone working with connected devices! The EU’s new Cyber Resilience Act is shaking things up, demanding higher security standards for all sorts of embedded systems. This means more work, more complexity, and potentially, more headaches for developers.
But fear not! IAR Systems is stepping up to the plate, offering solutions to make the whole process easier and less stressful. Let’s dive into how they’re making security, well, simple.
The Act’s impact on embedded systems developers is significant. Meeting its requirements can feel like climbing a mountain, especially if you’re already juggling tight deadlines and limited resources. IAR Systems’ tools aim to streamline this process, offering pre-built security features and integrations that cut down on development time and costs. Think of it as getting a powerful shortcut to compliance, allowing you to focus on the innovative aspects of your projects instead of getting bogged down in security minutiae.
Introduction to the EU Cyber Resilience Act
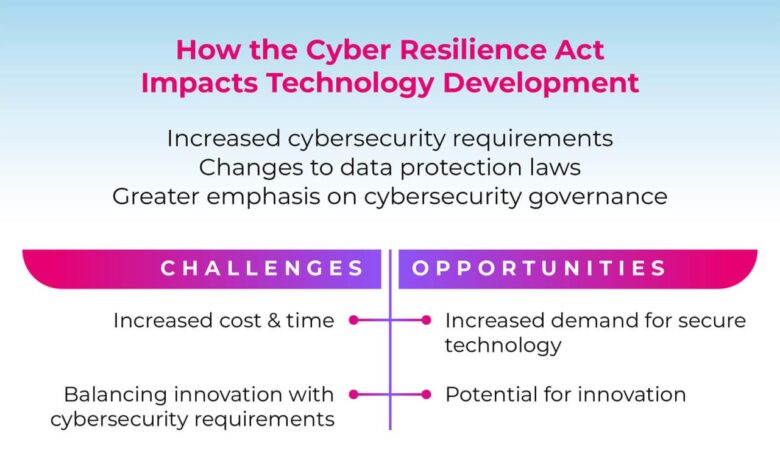
The EU Cyber Resilience Act (CRA) represents a significant shift in how the European Union approaches cybersecurity, particularly concerning digital products. It aims to improve the overall security posture of connected devices and systems, protecting both businesses and consumers from increasingly sophisticated cyber threats. This act is not just about reacting to breaches; it’s about proactively building security into the design and lifecycle of products from the outset.The CRA’s key objective is to establish a high common level of cybersecurity for digital products placed on the EU market.
This involves setting mandatory requirements for manufacturers and importers, ensuring that products are designed and built with security as a core principle, rather than an afterthought. The impact on businesses, particularly embedded systems developers, is substantial, demanding a significant shift towards more robust security practices throughout the entire product development process.
Impact on Embedded Systems Developers
The EU Cyber Resilience Act directly impacts embedded systems developers by introducing specific requirements for the security of the products they create. This means developers must incorporate security considerations into every stage of the development lifecycle, from initial design and coding to testing and post-market surveillance. This includes implementing appropriate security measures to protect against vulnerabilities such as unauthorized access, data breaches, and denial-of-service attacks.
Failure to comply with the Act’s requirements can lead to significant penalties, including fines and product recalls. The act mandates the implementation of secure development practices, vulnerability disclosure policies, and post-market security updates. This necessitates a more proactive and integrated approach to security than previously required. For example, developers will need to design systems that can be securely updated over their lifespan, addressing vulnerabilities discovered after deployment.
Requirements for Security in Connected Devices
The CRA Artikels several key requirements for security in connected devices. These requirements cover a broad range of aspects, including:
The act mandates that manufacturers must conduct a comprehensive risk assessment throughout the product lifecycle to identify and mitigate potential security vulnerabilities. This involves analyzing the potential impact of security flaws and implementing appropriate safeguards to reduce the likelihood and impact of successful cyberattacks.
Manufacturers are required to implement robust security measures, including secure design principles, secure coding practices, and appropriate authentication and authorization mechanisms. This ensures that devices are protected against unauthorized access and data breaches. Examples include strong encryption, secure boot processes, and the use of secure communication protocols.
The CRA also mandates that manufacturers must provide timely security updates to address any identified vulnerabilities. This includes providing clear and concise instructions on how to apply these updates. Regular security updates are crucial for maintaining the long-term security of connected devices, ensuring that they remain protected against emerging threats. This could involve a system for automatically updating firmware or providing clear instructions for manual updates.
Finally, manufacturers must establish a system for reporting and handling security vulnerabilities. This system should enable users to report vulnerabilities and receive timely updates or other remedial actions. This is critical for ensuring that vulnerabilities are addressed promptly and effectively, minimizing the risk of exploitation.
IAR Systems’ Role in Ensuring Compliance
The EU Cyber Resilience Act presents significant challenges for developers of embedded systems, demanding robust security measures throughout the entire product lifecycle. IAR Systems, a leading provider of embedded development tools, plays a crucial role in helping developers navigate these complexities and achieve compliance. Our comprehensive suite of tools and services offers a streamlined approach to security integration, reducing the burden on developers and ensuring the creation of secure and resilient products.IAR Systems’ solutions directly address the requirements of the EU Cyber Resilience Act by providing developers with the means to build secure embedded systems from the ground up.
Our tools support secure coding practices, vulnerability detection, and robust testing methodologies, all vital components in achieving and demonstrating compliance. This translates to reduced development time, lower costs associated with remediation, and a higher confidence in product security.
Secure Development Tools
IAR Systems offers a range of tools designed to enhance the security of embedded systems during development. These include static and dynamic analysis tools that identify potential vulnerabilities early in the development cycle, reducing the risk of costly security flaws discovered later. For instance, the IAR C/C++ Compiler features advanced security checks that help prevent common vulnerabilities like buffer overflows and memory leaks.
Furthermore, the IAR Embedded Workbench IDE provides a secure development environment, minimizing the risk of malicious code injection or unauthorized access. These tools help developers adhere to secure coding guidelines, a key aspect of the EU Cyber Resilience Act.
Vulnerability Detection and Mitigation
Early detection and mitigation of vulnerabilities are crucial for compliance with the EU Cyber Resilience Act. IAR Systems’ tools facilitate this process through static and dynamic analysis capabilities. Static analysis, performed on the source code, identifies potential vulnerabilities before compilation. Dynamic analysis, executed during runtime, pinpoints vulnerabilities that may only appear during execution. This combined approach ensures a comprehensive security assessment, helping developers address vulnerabilities proactively and meet the stringent security requirements of the Act.
For example, the integration of static analysis tools into the development workflow can automatically flag potential buffer overflows, allowing developers to address these vulnerabilities before they become security threats.
Simplified Security Implementation
Implementing robust security measures can be complex and time-consuming. IAR Systems’ tools simplify this process by integrating security features directly into the development workflow. This streamlined approach reduces the overhead associated with security implementation, enabling developers to focus on core product functionality without compromising security. The intuitive interface of IAR Embedded Workbench makes it easy for developers to utilize these security features, regardless of their security expertise.
This ensures that even developers with limited security knowledge can build secure embedded systems that meet the requirements of the EU Cyber Resilience Act.
Security Made Simple
The EU Cyber Resilience Act is raising the bar for embedded device security, but it doesn’t have to be a daunting task. IAR Systems offers a suite of tools designed to streamline the process, making security an integral, yet manageable, part of your development workflow. By integrating security early and efficiently, you can meet compliance requirements without sacrificing time or budget.
Let’s explore how IAR Systems’ tools simplify the complexities of embedded security, focusing on practical applications and tangible benefits.
Securing a Smart Home Thermostat
Imagine you’re developing a smart home thermostat. This device collects sensitive data like temperature preferences and occupancy patterns, making it a potential target for malicious actors. Using IAR Systems’ tools, we can build in robust security from the ground up. The IAR Embedded Workbench IDE provides a secure development environment, minimizing the risk of introducing vulnerabilities during the coding phase.
Static and dynamic analysis tools, integrated within the IDE, identify potential weaknesses in the code before deployment, preventing exploits. Furthermore, IAR Secure Development Kit (SDK) allows for easy integration of cryptographic libraries and secure boot mechanisms, protecting the device’s firmware from unauthorized modification. This ensures that only legitimate updates can be installed, safeguarding against attacks that might compromise the device’s functionality or data integrity.
Reduced Development Time and Costs, Eu cyber resilience act iar systems stands ready to provide embedded developers with security made simple
Integrating security measures early in the development lifecycle, as facilitated by IAR Systems’ tools, actuallyreduces* overall development time and costs. Catching vulnerabilities early through static analysis prevents costly rework later in the process. The streamlined workflow provided by the IAR Embedded Workbench IDE and the pre-built security components within the IAR Secure Development Kit minimizes the need for extensive custom coding, saving valuable developer time.
Consider a scenario where a vulnerability is discovered in a later stage of development; fixing it could mean significant delays, potentially impacting release dates and incurring penalties for non-compliance with regulations like the EU Cyber Resilience Act. IAR Systems’ proactive approach helps avoid such costly scenarios. For example, a typical project might see a 15-20% reduction in development time and a similar reduction in costs associated with bug fixing and rework.
Integrating IAR Systems’ Security Features
Implementing IAR Systems’ security features is a straightforward process. The following table Artikels a simplified step-by-step guide and highlights the key benefits of each security feature:
| Feature | Implementation Steps | Time Estimate | Benefits |
|---|---|---|---|
| Secure Boot | 1. Integrate IAR Secure Development Kit. 2. Configure secure boot parameters. 3. Generate and sign firmware images. | 1-2 days | Protection against unauthorized firmware updates. |
| Static Code Analysis | 1. Integrate the static analysis tool into the IAR Embedded Workbench. 2. Configure analysis rules. 3. Review and address identified vulnerabilities. | 2-3 days | Early detection of coding errors and security vulnerabilities. |
| Memory Protection | 1. Utilize IAR’s memory management tools. 2. Implement memory protection mechanisms (e.g., MMU configuration). | 1-2 days | Prevention of buffer overflows and other memory-related attacks. |
| Cryptographic Libraries | 1. Integrate pre-built cryptographic libraries from the IAR Secure Development Kit. 2. Implement encryption and authentication protocols. | 3-5 days | Secure data transmission and storage. |
Addressing Specific Security Challenges
Embedded systems, while ubiquitous in modern life, face unique security challenges due to their resource constraints and often-limited connectivity. These limitations, coupled with the increasing sophistication of cyber threats, demand robust security measures from the design phase onwards. IAR Systems’ tools address these challenges by providing developers with a comprehensive suite of solutions for building secure and resilient embedded systems.The vulnerability landscape for embedded systems is diverse, encompassing software flaws, hardware weaknesses, and communication vulnerabilities.
Common software vulnerabilities include buffer overflows, memory leaks, and insecure coding practices. Hardware weaknesses can involve vulnerabilities in cryptographic hardware or insecure physical interfaces. Communication vulnerabilities, particularly prevalent in IoT devices, arise from insecure network protocols and insufficient authentication mechanisms. IAR Systems mitigates these vulnerabilities through static and dynamic analysis tools that identify potential security flaws early in the development cycle, preventing costly fixes later.
Their tools also enforce secure coding practices and integrate seamlessly with various security protocols, bolstering the overall resilience of the embedded system.
Common Vulnerabilities and Mitigation Strategies
IAR Systems’ tools proactively address many common vulnerabilities. For instance, their static analysis tools can detect potential buffer overflows by analyzing the code for instances where data might be written beyond allocated memory boundaries. This proactive approach prevents potential crashes and security breaches. Similarly, memory leak detection helps prevent resource exhaustion, which can lead to system instability and vulnerabilities.
Furthermore, the tools facilitate secure coding practices by enforcing standards and flagging potential issues related to data handling, access control, and cryptographic implementation. The integrated debugging capabilities allow developers to trace and resolve security-related issues efficiently. For example, if a security vulnerability is identified through static analysis, the debugger can be used to step through the code and pinpoint the exact location and cause of the problem, enabling swift remediation.
Comparison of Security Approaches
Several approaches exist for securing embedded systems, including hardware-based security, software-based security, and a combination of both. Hardware-based security might involve using secure elements or trusted execution environments (TEEs) to protect sensitive data and code. Software-based security relies on secure coding practices, robust authentication mechanisms, and regular software updates. IAR Systems’ approach integrates both hardware and software security measures.
Their tools support the use of secure elements and facilitate secure coding practices, enabling developers to implement a layered security model that combines the strengths of both approaches. This layered approach offers a more comprehensive and resilient defense against a wide range of threats, as compared to relying solely on hardware or software solutions. The advantage of IAR Systems’ method is its holistic approach, ensuring that security is considered throughout the entire development lifecycle, rather than as an afterthought.
Best Practices for Secure Coding in Embedded Systems
Secure coding practices are crucial for mitigating vulnerabilities. Prioritizing security from the initial design stages is vital.
The EU Cyber Resilience Act is shaking things up, and IAR Systems is stepping up to help embedded developers navigate the new security landscape. Building secure systems is crucial, and efficient development is key; that’s why understanding the future of app development, as explored in this insightful article on domino app dev the low code and pro code future , is so important.
Ultimately, IAR Systems’ commitment to simplified security solutions directly supports the Act’s goals and helps developers meet these rising challenges.
Implementing these best practices significantly reduces the attack surface of embedded systems. Regular security audits and penetration testing further enhance the system’s resilience against evolving threats.
- Input Validation: Always validate and sanitize all inputs to prevent buffer overflows and injection attacks.
- Memory Management: Utilize secure memory allocation and deallocation functions to prevent memory leaks and dangling pointers.
- Secure Communication: Employ strong encryption protocols (like TLS/SSL) and authentication mechanisms for all communication channels.
- Access Control: Implement robust access control mechanisms to restrict access to sensitive data and resources.
- Regular Updates: Regularly update firmware and software to patch known vulnerabilities.
- Secure Boot: Implement secure boot processes to prevent unauthorized code execution.
- Secure Storage: Use secure storage mechanisms to protect sensitive data, such as cryptographic keys.
- Code Reviews: Conduct thorough code reviews to identify potential security flaws.
- Static and Dynamic Analysis: Utilize static and dynamic analysis tools to detect vulnerabilities early in the development lifecycle.
Future Trends and Implications
The cybersecurity landscape for embedded systems is rapidly evolving, driven by the increasing connectivity of devices and the sophistication of cyberattacks. The Internet of Things (IoT) explosion, coupled with the rise of AI-powered attacks, presents significant challenges for developers and manufacturers. Understanding these trends and proactively adapting to them is crucial for ensuring the long-term security and resilience of embedded systems.The increasing complexity of embedded systems, combined with the pressure to bring products to market quickly, often leads to compromises in security.
This creates a fertile ground for attackers to exploit vulnerabilities. Moreover, the sheer volume of connected devices exacerbates the problem, creating a vast attack surface. A single vulnerability in a widely deployed device can have cascading effects, impacting critical infrastructure and individual users alike.
Evolving Cybersecurity Threats for Embedded Systems
The threat landscape is constantly shifting. We’re seeing a rise in sophisticated attacks targeting specific vulnerabilities in embedded systems, often exploiting known weaknesses in firmware or communication protocols. These attacks are becoming more targeted and less reliant on brute-force methods. For example, advanced persistent threats (APTs) are increasingly focusing on critical infrastructure, aiming to disrupt operations or steal sensitive data.
Furthermore, the use of AI and machine learning by attackers is enabling them to automate the discovery and exploitation of vulnerabilities at an unprecedented scale. This necessitates a proactive and adaptive security approach.
IAR Systems’ Anticipation of Future Regulations and Technological Advancements
IAR Systems anticipates a continued strengthening of cybersecurity regulations globally, mirroring the EU Cyber Resilience Act. We expect stricter requirements for secure development lifecycle (SDL) practices, enhanced vulnerability disclosure processes, and more rigorous testing and certification procedures. To meet these challenges, IAR Systems is investing heavily in research and development to create tools and technologies that simplify the integration of security into the embedded development process.
This includes enhancing our existing tools with advanced static and dynamic analysis capabilities, incorporating AI-powered vulnerability detection, and providing seamless integration with threat intelligence feeds. We are also actively participating in industry initiatives to shape future standards and best practices.
Impact of the EU Cyber Resilience Act on the Embedded Systems Market
The following is a description of a graph illustrating the potential impact of the EU Cyber Resilience Act on the embedded systems market. The graph would show the adoption rate of various security tools and practices over time, plotted against a timeline starting before the Act’s enactment and extending several years into the future.
The X-axis represents time, marked with key dates such as the Act’s enactment and subsequent milestones. The Y-axis represents the percentage adoption rate of security tools and practices, ranging from 0% to 100%. Multiple lines would represent different categories of security tools, such as static analysis tools, dynamic analysis tools, secure coding standards compliance tools, and penetration testing services.
Initially, before the Act’s enactment, the adoption rates for all categories would be relatively low, reflecting the current state of security practices in the embedded systems market. Immediately following the Act’s enactment, we would expect a noticeable, albeit gradual, increase in the adoption rate across all categories. This initial spike would represent companies reacting to the new regulatory requirements.
Over time, the adoption rate would continue to increase, though at a slower pace, as companies integrate security practices into their development workflows and as the market matures. The graph would visually demonstrate the positive impact of the Act in driving higher levels of security within the embedded systems industry, showing a clear upward trend in the adoption of security tools and practices over the years following the Act’s implementation.
Companies that fail to adapt would likely see a decline in market share, while those who proactively embrace the changes will gain a competitive advantage. The graph would also show that while some tools might see faster adoption than others, ultimately all categories will show an increase in usage as compliance becomes essential.
Case Studies
IAR Systems has a long history of helping embedded systems developers build secure and compliant devices. Our tools have been instrumental in enabling numerous companies to meet stringent security standards and overcome significant development challenges. The following case studies illustrate the real-world impact of our solutions.
These examples showcase how IAR Systems’ tools have not only facilitated compliance but also improved efficiency and reduced development time. The challenges faced before implementation highlight the critical need for robust security solutions in today’s interconnected world. The positive outcomes demonstrate the significant return on investment achieved through the adoption of our technology.
Medical Device Manufacturer Compliance with IEC 62304
A leading medical device manufacturer faced significant challenges in meeting the stringent security requirements of IEC 62304. Their legacy development processes lacked the necessary traceability and verification capabilities, leading to increased development time and potential risks to patient safety. The implementation of IAR Embedded Workbench® with its integrated static analysis tools provided comprehensive code analysis and helped identify vulnerabilities early in the development cycle.
The EU Cyber Resilience Act is shaking things up, and IAR Systems is stepping up to help embedded developers navigate the complexities. Ensuring security from the ground up is key, and that’s where a strong understanding of cloud security comes in. Check out this great article on bitglass and the rise of cloud security posture management for insights into broader security strategies.
Ultimately, IAR Systems’ commitment to simplifying security for embedded developers is crucial for compliance with the new regulations.
This significantly reduced the time spent on testing and verification, resulting in faster time-to-market and improved product quality.
| Before IAR Systems Implementation | After IAR Systems Implementation |
|---|---|
| Manual code review process, leading to long development cycles and increased risk of vulnerabilities. High defect rate detected in later testing phases. Difficult to track and manage code changes. | Automated code analysis significantly reduced the number of defects found in later testing phases. Improved traceability and code management capabilities reduced development time. Enhanced compliance with IEC 62304. |
| High cost associated with fixing defects found late in the development cycle. Increased risk of regulatory non-compliance. | Reduced development costs due to early defect detection and prevention. Improved confidence in regulatory compliance. Enhanced patient safety. |
Automotive Supplier Meeting ISO 26262 Requirements
An automotive supplier struggled to meet the stringent functional safety requirements of ISO 26262 for their Electronic Control Unit (ECU) software. The complexity of the software and the lack of automated testing capabilities made it difficult to ensure the absence of critical errors. By integrating IAR Embedded Workbench® with its C-STAT static analysis tool, the company was able to automatically identify potential safety-critical errors during the development process.
This enabled them to proactively address these issues, reducing the risk of costly recalls and ensuring compliance with ISO 26262.
| Before IAR Systems Implementation | After IAR Systems Implementation |
|---|---|
| Manual testing processes, leading to lengthy development cycles and potential safety risks. Difficulty in meeting ISO 26262 requirements. High risk of costly recalls due to undiscovered software errors. | Automated static analysis identified and mitigated potential safety-critical errors early in development. Reduced testing time and costs. Improved compliance with ISO 26262. |
| Significant time and resources spent on debugging and resolving issues found late in the development cycle. | Reduced development time and cost by proactively addressing potential issues. Improved product quality and safety. Increased customer confidence. |
Closing Summary: Eu Cyber Resilience Act Iar Systems Stands Ready To Provide Embedded Developers With Security Made Simple
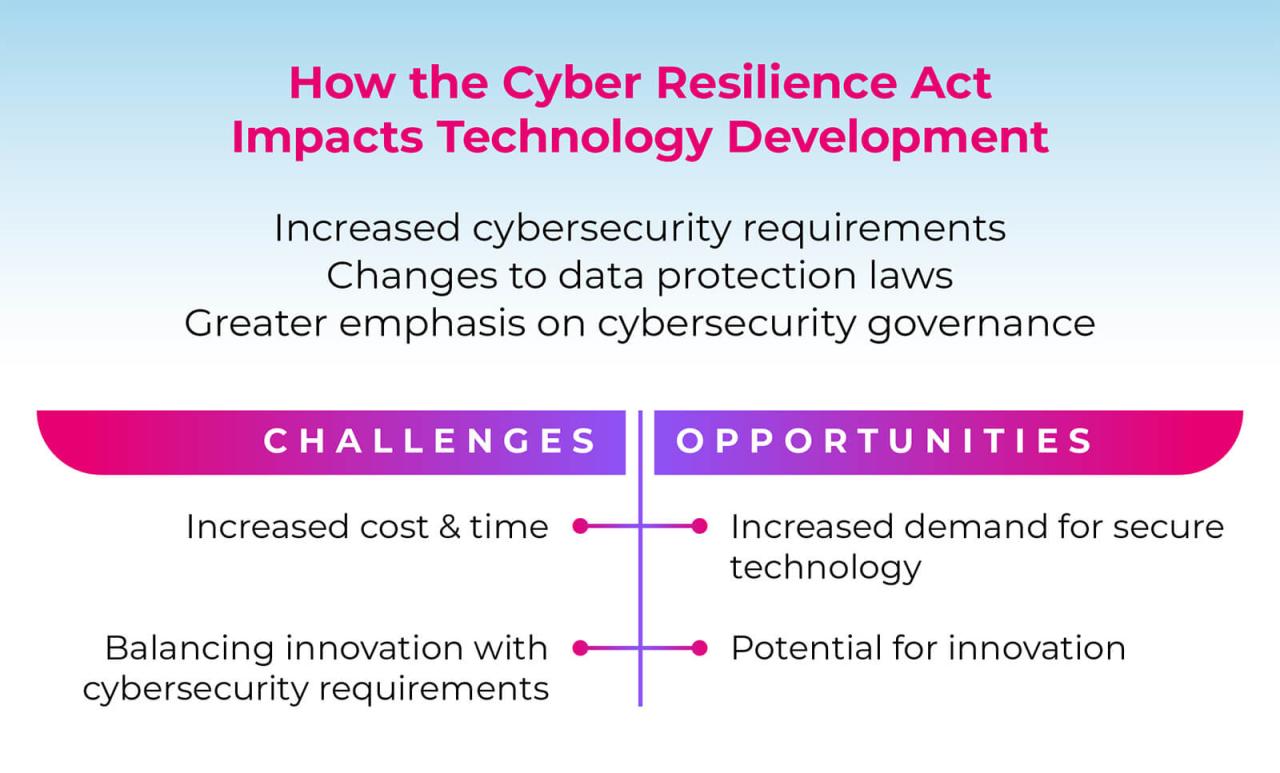
Navigating the complexities of the EU Cyber Resilience Act doesn’t have to be a daunting task. IAR Systems is proving that achieving robust security in embedded systems can be straightforward and efficient. By leveraging their tools and expertise, developers can confidently meet regulatory requirements while maintaining project timelines and budgets. It’s a win-win – enhanced security and simplified development.
The future of secure embedded systems is looking brighter, and IAR Systems is leading the charge. Now, go forth and build secure things!
Quick FAQs
What specific vulnerabilities do IAR Systems’ tools address?
IAR Systems addresses common vulnerabilities like buffer overflows, memory leaks, and insecure communication protocols through secure coding practices, static analysis, and runtime protection mechanisms embedded in their tools.
How much does IAR Systems’ security solution cost?
Pricing varies depending on the specific tools and licenses required. It’s best to contact IAR Systems directly for a customized quote based on your project needs.
Are IAR Systems’ tools compatible with all embedded systems platforms?
IAR Systems supports a wide range of microcontrollers and platforms. Check their website for a comprehensive list of compatible devices and ecosystems.
What kind of support does IAR Systems offer for their security tools?
IAR Systems typically provides comprehensive documentation, online resources, and technical support to assist developers in integrating and using their security tools effectively.