Cyber Threat to Pentagon Coronavirus Telecommuting
Cyber threat to pentagon coronovirus telecommuting – Cyber threat to Pentagon coronavirus telecommuting: The shift to remote work during the pandemic dramatically altered the Pentagon’s security landscape. Suddenly, a vast network of home computers and personal devices became part of the nation’s most sensitive defense systems. This massive expansion of the attack surface exposed the Pentagon to new and amplified cyber threats, demanding a reassessment of security protocols and a scramble to adapt to the rapidly evolving digital battlefield.
This post dives deep into the vulnerabilities, threats, and consequences of this unprecedented shift. We’ll explore the specific challenges faced, the effectiveness of mitigation strategies, and the long-term implications for the Pentagon’s cybersecurity posture. Prepare for a fascinating (and slightly unnerving) look behind the scenes.
Increased Vulnerability During Telecommuting
The Pentagon’s rapid shift to widespread telecommuting in response to the Coronavirus pandemic dramatically altered its cybersecurity landscape. While necessary for public health, this transition exposed the organization to new and significant vulnerabilities, demanding a reassessment of its security protocols and infrastructure. The pre-existing robust on-site security measures were simply not designed to handle the complexities and risks associated with a largely remote workforce.The security protocols in place before the pandemic relied heavily on physical security measures – secure facilities, access control systems, and strict on-site network controls.
Data was largely contained within the Pentagon’s internal network, minimizing exposure to external threats. After the shift to remote work, the perimeter expanded exponentially. The Pentagon’s network now extended to countless individual home networks, each with its own varying levels of security and potential vulnerabilities. This created a significantly larger attack surface, making the entire system far more susceptible to compromise.
Impact of Remote Access Technologies on Pentagon Security
The reliance on remote access technologies, such as VPNs and virtual desktops, introduced a new set of challenges. While these technologies are essential for secure remote access, their implementation and management can be complex and prone to errors. Improperly configured VPNs, for instance, could expose sensitive data to unauthorized access. Furthermore, the sheer volume of remote connections increased the load on the Pentagon’s network infrastructure, potentially creating vulnerabilities that could be exploited by attackers.
The inherent trust placed in employees to maintain secure home working environments also represented a significant departure from the tightly controlled on-site environment. This introduced a human element of risk, increasing the potential for accidental or malicious data breaches.
Hypothetical Cyberattack Scenario
Imagine a scenario where a malicious actor gains access to a Pentagon employee’s home network through a phishing email containing malware. This malware, designed to bypass the employee’s antivirus software and exploit a vulnerability in their operating system, could then establish a foothold on their computer. Because the employee is connected to the Pentagon’s network via a VPN, the attacker could leverage this access to laterally move within the network, potentially gaining access to sensitive data or critical systems.
The attacker might exploit a known vulnerability in the VPN software itself, or use the compromised employee’s credentials to access other systems. The lack of robust monitoring and detection capabilities in the expanded remote work environment could allow the attacker to remain undetected for an extended period, causing significant damage before being discovered. This scenario highlights the increased complexity and difficulty of securing a distributed workforce compared to a centralized, physically secured environment.
Types of Cyber Threats Faced
The shift to widespread telecommuting within the Pentagon during the COVID-19 pandemic dramatically increased its attack surface, exposing the department to a wider range of cyber threats than previously encountered. This wasn’t simply a matter of more people working remotely; it involved a significant alteration in security protocols and network access, creating vulnerabilities exploited by sophisticated adversaries. The threats weren’t just more numerous, but also more diverse and challenging to mitigate.The increased reliance on VPNs, personal devices, and cloud services, coupled with the inherent security challenges of remote work, amplified the risk.
This period saw a significant surge in various attack vectors, demanding a rapid and adaptive response from the Pentagon’s cybersecurity teams.
Specific Threat Types and Their Impact
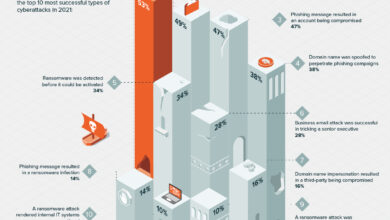
The Pentagon faced a multifaceted cyber threat landscape during the height of the pandemic-related telecommuting period. The most prevalent threats included phishing attacks, malware infections, and denial-of-service (DoS) attacks, each posing unique challenges and requiring different mitigation strategies. While precise figures on frequency and severity are classified for national security reasons, we can analyze the general trends and the types of incidents that occurred.
| Threat Type | Frequency | Severity | Mitigation Strategy |
|---|---|---|---|
| Phishing Attacks | High | Medium to High (depending on success) | Enhanced security awareness training, multi-factor authentication (MFA), email filtering and anti-spoofing techniques. |
| Malware Infections | High | High (potential for data breaches, system compromise) | Robust endpoint protection, regular software updates, network segmentation, and incident response planning. |
| Denial-of-Service (DoS) Attacks | Moderate | Medium to High (depending on duration and impact) | Distributed denial-of-service (DDoS) mitigation services, network infrastructure upgrades, and robust monitoring systems. |
| Supply Chain Attacks | Low | Extremely High (potential for widespread compromise) | Strict vendor vetting, secure software development lifecycle (SDLC), and regular security audits of third-party systems. |
While specific incidents and near misses remain undisclosed for security reasons, it’s widely understood that numerous phishing attempts targeting Pentagon personnel were recorded. These attacks often used sophisticated techniques, leveraging the urgency and uncertainty surrounding the pandemic to increase their effectiveness. Similarly, malware infections, potentially delivered through malicious attachments or compromised websites, posed a constant threat to sensitive data and operational systems.
The increased network traffic associated with remote work also made the Pentagon more susceptible to DoS attacks, aiming to disrupt essential services. The potential for supply chain attacks, compromising software or hardware from external vendors, also represented a significant, albeit less frequent, threat. The severity of such an attack could be catastrophic, leading to widespread system compromise and data breaches.
Impact of the Coronavirus Pandemic on Cybersecurity Resources: Cyber Threat To Pentagon Coronovirus Telecommuting
The COVID-19 pandemic dramatically reshaped the Pentagon’s operational landscape, forcing a rapid shift to widespread telecommuting. This transition, while necessary to maintain essential functions, significantly impacted the Department’s cybersecurity resources and workforce, creating new vulnerabilities and challenges. The sudden and massive shift to remote work exposed existing weaknesses and placed unprecedented strain on already stretched cybersecurity teams.The pandemic’s impact on the Pentagon’s cybersecurity capabilities went beyond simply increasing the attack surface.
Staffing shortages, budget reallocations, and the disruption of training and collaboration initiatives all contributed to a weakened security posture. The unexpected nature of the crisis made it difficult to implement adequate security measures quickly enough to counter the escalating threats. Furthermore, the increased reliance on remote access technologies introduced new vulnerabilities that malicious actors were quick to exploit.
Pentagon Cybersecurity Workforce Shortages and Budgetary Constraints
The pandemic exacerbated existing staffing challenges within the Pentagon’s cybersecurity workforce. Many cybersecurity professionals were tasked with supporting the rapid transition to remote work, diverting resources from proactive security measures to immediate crisis management. Simultaneously, recruitment and training programs were disrupted, hindering the ability to fill critical vacancies and build up necessary expertise. Budgetary constraints, resulting from pandemic-related economic downturns and the need to redirect funding towards immediate health and economic relief efforts, further limited the Pentagon’s ability to invest in advanced cybersecurity technologies and personnel.
For example, planned upgrades to network infrastructure and security systems may have been delayed or scaled back, leaving critical systems vulnerable. This budgetary pressure, coupled with the increased workload, contributed to burnout and attrition within the existing workforce, creating a vicious cycle of resource depletion.
Impact of Resource Limitations on Cyber Threat Response
The resource limitations stemming from the pandemic directly affected the Pentagon’s capacity to effectively respond to cyber threats. Delayed incident response, compromised situational awareness, and reduced capacity for proactive threat hunting were some of the key consequences. The increased volume of cyberattacks, combined with a diminished cybersecurity workforce, resulted in longer response times to incidents, potentially allowing attackers more time to exfiltrate sensitive data or disrupt critical operations.
The inability to adequately monitor and analyze network traffic also hampered the Pentagon’s ability to identify and mitigate threats in a timely manner. For instance, a delayed response to a ransomware attack could lead to significant data loss and operational disruption, costing the Pentagon valuable time and resources to recover. Furthermore, a shortage of skilled analysts meant fewer resources for proactive threat hunting, increasing the likelihood of successful attacks going undetected.
Potential Consequences of Resource Limitations on Cybersecurity Preparedness
The consequences of these resource limitations extend beyond immediate incident response. A weakened cybersecurity posture leaves the Pentagon more vulnerable to future attacks, potentially resulting in significant damage to national security. The following list illustrates some potential consequences:
- Increased risk of successful cyberattacks leading to data breaches and espionage.
- Disruption of critical military operations and infrastructure.
- Erosion of public trust in the Pentagon’s ability to protect sensitive information.
- Increased costs associated with remediation and recovery efforts following cyber incidents.
- Weakening of national security due to compromised intelligence and operational capabilities.
Effectiveness of Mitigation Strategies

The Pentagon’s response to the increased cyber threats during the coronavirus-induced telecommuting period involved a multi-pronged approach encompassing technological upgrades, enhanced security protocols, and employee training. Assessing the effectiveness of these strategies requires a nuanced understanding of their individual contributions and limitations. While some measures proved highly successful, others highlighted areas needing improvement for future remote work scenarios.The effectiveness of the Pentagon’s mitigation strategies varied significantly depending on the specific threat and the implemented countermeasure.
For example, the rapid deployment of multi-factor authentication (MFA) across all systems significantly reduced the success rate of phishing attacks targeting employee credentials. Conversely, while the implementation of Virtual Private Networks (VPNs) improved network security for remote workers, some challenges remained in ensuring consistent and secure VPN access across diverse employee locations and devices. This resulted in instances where employees bypassed VPNs, increasing vulnerability to attacks.
Multi-Factor Authentication Implementation, Cyber threat to pentagon coronovirus telecommuting
The widespread adoption of MFA across Pentagon systems proved a highly effective mitigation strategy. By requiring multiple forms of authentication (such as password and a one-time code), MFA significantly increased the difficulty for attackers to gain unauthorized access. Data from the Department of Defense (though not publicly released in detail due to security concerns) suggests a substantial decrease in successful credential theft attempts following the implementation of MFA.
This success can be attributed to the relative simplicity of implementation and widespread adoption across all systems. The high success rate of MFA underscores its importance as a cornerstone of future security strategies.
Virtual Private Network (VPN) Deployment and Usage
While VPN deployment was crucial in securing remote worker connections, its effectiveness was hampered by inconsistent usage and challenges in maintaining seamless access. Anecdotal evidence suggests that some employees experienced difficulty connecting to the VPN, leading to them bypassing the security measure. This is a crucial area for improvement, requiring a more user-friendly and robust VPN infrastructure. Furthermore, future strategies should incorporate regular VPN usage audits and training to ensure compliance.
The success rate of the VPN deployment was therefore partially undermined by practical limitations.
The Pentagon’s increased reliance on telecommuting during the coronavirus pandemic dramatically amplified its vulnerability to cyber threats. Secure, rapidly deployable applications are crucial, and that’s where the advancements in application development, like those discussed in this article on domino app dev the low code and pro code future , become incredibly important. Faster development cycles mean quicker patching of security holes, a vital need given the ever-evolving landscape of cyberattacks targeting remote workforces.
Employee Cybersecurity Training and Awareness Programs
The effectiveness of employee training programs in mitigating cyber threats during telecommuting is difficult to quantify directly. However, improved reporting of suspicious emails and phishing attempts indicates an increase in employee awareness. The Pentagon’s investment in regular training sessions focusing on phishing scams, malware detection, and secure remote working practices likely contributed to a reduction in successful social engineering attacks.
Future improvements could focus on personalized training modules tailored to specific roles and responsibilities, supplemented with regular simulated phishing exercises to maintain vigilance. The success of these programs is ultimately measured in the reduction of successful social engineering attacks.
Improved Incident Response Procedures
The Pentagon’s response to actual cyber incidents during the period of increased telecommuting revealed areas for improvement in incident response procedures. Faster detection and response times are crucial. Investing in advanced threat detection tools and streamlining the incident response process would be beneficial. This includes establishing clearer communication channels and protocols for reporting and addressing security incidents. The improved response procedures would reduce the impact of successful attacks, minimizing data breaches and system downtime.
This would enhance the overall effectiveness of the mitigation strategy.
The Role of Third-Party Vendors
The Pentagon, like any large organization, relies heavily on third-party vendors for a wide range of services, from IT infrastructure and cybersecurity solutions to specialized software and even building maintenance. This reliance, while often necessary for efficiency and cost-effectiveness, introduces significant cybersecurity risks. The interconnected nature of modern systems means a breach in a vendor’s security can easily cascade into the Pentagon’s own network, potentially compromising sensitive national security information.The risks associated with third-party vendors are multifaceted.
The Pentagon’s shift to telecommuting during the coronavirus pandemic dramatically increased its vulnerability to cyber threats. This highlights the urgent need for robust cloud security, and solutions like those offered by Bitglass, as detailed in this insightful article on bitglass and the rise of cloud security posture management , are crucial. Without strong cloud security posture management, remote workforces become easy targets, making comprehensive security solutions essential for national security.
Vendors may have weaker security practices than the Pentagon itself, lacking the resources or expertise to adequately protect sensitive data. Furthermore, the sheer number of vendors involved creates a complex web of access points, making comprehensive security monitoring and control extremely challenging. A lack of transparency in vendor security practices can also hinder the Pentagon’s ability to effectively assess and manage risks.
For example, a vendor might use outdated software or have insufficient employee training, leaving them vulnerable to common attacks like phishing or malware. Data breaches involving third-party vendors have historically had significant consequences for organizations, and the Pentagon is no exception, considering the highly sensitive nature of the data they handle.
Risks Associated with Third-Party Vendor Reliance
The potential for data breaches is a primary concern. A compromised vendor could expose classified information, intellectual property, or personal data of Pentagon employees and contractors. This could lead to significant reputational damage, financial losses, and legal repercussions. Furthermore, disruption of services provided by a compromised vendor could cripple critical operations, impacting national security. Another significant risk is the lack of visibility into the vendor’s security posture.
Without proper oversight and stringent security audits, the Pentagon might be unaware of vulnerabilities within the vendor’s systems until it’s too late. This lack of visibility makes it difficult to proactively mitigate potential threats. Finally, the contractual agreements with vendors often lack sufficient clauses addressing cybersecurity responsibilities and liabilities, leaving the Pentagon vulnerable in case of a breach.
For example, a poorly drafted contract might not clearly define the vendor’s obligations regarding data protection and incident response.
Best Practices for Managing Cybersecurity Risks Associated with Third-Party Vendors
It is crucial to establish robust processes for managing the risks associated with third-party vendors. This requires a multi-faceted approach.
The following best practices should be implemented:
- Thorough Due Diligence: Before engaging a vendor, conduct a comprehensive assessment of their security practices. This should include reviewing their security certifications, conducting background checks on key personnel, and performing penetration testing of their systems.
- Strict Contractual Agreements: Contracts should clearly define cybersecurity responsibilities, including data protection obligations, incident response procedures, and liability clauses. Regular security audits should be mandated and included as part of the contract.
- Continuous Monitoring: Implement continuous monitoring of vendor systems to detect and respond to security incidents promptly. This can involve using security information and event management (SIEM) systems and regularly reviewing vendor security reports.
- Security Awareness Training: Ensure that Pentagon personnel who interact with third-party vendors are adequately trained on cybersecurity best practices, including recognizing and avoiding phishing attempts and other social engineering attacks.
- Regular Security Audits of Vendors: Conduct regular, independent security audits of third-party vendors to assess their compliance with security requirements and identify potential vulnerabilities.
- Incident Response Planning: Develop a comprehensive incident response plan that addresses potential security breaches involving third-party vendors. This plan should Artikel procedures for containment, eradication, recovery, and post-incident analysis.
- Regularly Review and Update Vendor Relationships: Regularly reassess the need for each vendor relationship, and terminate relationships with vendors who fail to meet security standards or pose an unacceptable risk.
Long-Term Implications for Cybersecurity

The surge in cyber threats during the pandemic, exacerbated by the Pentagon’s rapid shift to telecommuting, has profound and lasting implications for its cybersecurity strategy. The vulnerabilities exposed necessitate a significant overhaul of infrastructure, protocols, and personnel training to ensure future resilience against increasingly sophisticated attacks. This isn’t simply a matter of returning to pre-pandemic practices; it requires a proactive, adaptable approach capable of weathering future unforeseen circumstances.The reliance on remote access, while initially crucial, highlighted weaknesses in the Pentagon’s network security perimeter and exposed a significant attack surface.
The increased volume of cyberattacks targeting remote workers, coupled with the potential for compromised personal devices accessing sensitive data, necessitates a complete reassessment of security architectures and risk mitigation strategies. The long-term consequences extend beyond immediate damage control and encompass the need for substantial investment in advanced security technologies and a highly skilled workforce capable of managing them.
Adapting Cybersecurity Infrastructure and Practices
The Pentagon must adopt a zero-trust security model, moving away from the traditional perimeter-based approach. This means verifying every user and device attempting to access the network, regardless of location. Multi-factor authentication (MFA) should be mandatory for all users, supplemented by robust endpoint detection and response (EDR) solutions to monitor and protect individual devices. Regular security awareness training for all personnel, encompassing best practices for remote work, phishing awareness, and password management, is crucial.
Investment in advanced threat detection systems, including AI-powered tools capable of identifying and responding to sophisticated attacks in real-time, is paramount. This includes strengthening incident response capabilities to effectively manage and mitigate the impact of successful breaches. The Pentagon should also establish a comprehensive vulnerability management program, regularly scanning for and patching security flaws across its entire IT infrastructure.
A Future-Proof Cybersecurity Model for the Pentagon
A future-proof cybersecurity model for the Pentagon would incorporate several key elements. First, a robust and scalable cloud infrastructure would allow for greater flexibility and agility in responding to changing threats. This cloud environment would need to be highly secure, leveraging advanced encryption and access controls. Second, a comprehensive data loss prevention (DLP) system would monitor and protect sensitive data both within the network and in transit.
Third, continuous monitoring and threat intelligence would provide real-time insights into emerging threats, allowing for proactive mitigation strategies. Imagine a system where AI algorithms analyze network traffic and user behavior, identifying anomalies and potential threats before they can cause significant damage. This system would be integrated with automated response mechanisms, allowing for rapid containment of incidents. Fourth, robust partnerships with cybersecurity firms and government agencies would provide access to cutting-edge technologies and threat intelligence.
Finally, a culture of cybersecurity awareness and responsibility would be ingrained throughout the organization, with regular training and awareness campaigns reinforcing best practices. This model, inspired by successful strategies employed by leading private sector organizations and drawing on lessons learned from the pandemic, represents a holistic and adaptive approach to cybersecurity that prioritizes proactive defense and rapid response.
Wrap-Up

The pandemic-induced shift to telecommuting at the Pentagon exposed critical vulnerabilities and highlighted the urgent need for adaptable cybersecurity strategies. While the Pentagon implemented various mitigation measures, the experience underscores the complex challenges inherent in securing a distributed workforce. Moving forward, a multi-faceted approach encompassing robust remote access technologies, enhanced employee training, and proactive threat hunting will be crucial in safeguarding national security in the face of ever-evolving cyber threats.
The lessons learned from this period are vital for building a more resilient and secure future.
Popular Questions
What specific remote access technologies were used by the Pentagon during the shift to telecommuting?
The exact technologies remain classified, but it likely involved a mix of VPNs, secure remote desktop protocols, and cloud-based solutions. The specifics are likely highly customized for different branches and levels of security clearance.
How did the Pentagon’s employee training change to address the increased cyber risks associated with telecommuting?
The training likely expanded to cover topics such as phishing awareness, secure remote work practices, and handling classified information remotely. The frequency and intensity of these training sessions likely increased significantly.
What were the biggest challenges in securing third-party vendors providing services to the Pentagon during the pandemic?
Ensuring the same high security standards were met by external vendors, especially with remote access and data handling, presented a major challenge. Verifying their security protocols and monitoring their activity became significantly more complex.