Cyber Threat Warning Issued to All Internet Connected UPS Devices
Cyber threat warning issued to all internet connected UPS devices! Seriously, folks, this isn’t a drill. Think about it – those unassuming boxes keeping your power stable are now potential entry points for hackers. This isn’t just about a flickering screen; we’re talking about potential disruptions to critical systems, data breaches, and even physical damage. This post dives into the specifics of this alarming threat, exploring the vulnerabilities, the impact, and most importantly, how to protect yourself.
The recent warning highlights a critical vulnerability in many internet-connected UPS (Uninterruptible Power Supply) devices. Attackers can exploit weaknesses in their firmware and network configurations to gain unauthorized access, potentially leading to data theft, system control, and even physical damage to the devices themselves. Industries relying on consistent power, such as healthcare and finance, are particularly at risk. The methods used range from exploiting known vulnerabilities to employing sophisticated malware designed specifically for these devices.
We’ll unpack all this and more, providing actionable steps to safeguard your systems.
The Nature of the Threat
The recent cyber threat targeting internet-connected uninterruptible power supply (UPS) devices highlights a growing vulnerability in critical infrastructure. These devices, often overlooked in traditional cybersecurity strategies, represent a significant entry point for attackers seeking to disrupt operations or gain access to larger networks. The potential consequences range from minor inconveniences to catastrophic failures, underscoring the urgent need for improved security measures.The vulnerabilities exploited in these attacks typically stem from several factors.
Many older UPS models lack robust security features, employing default or easily guessable passwords and lacking secure update mechanisms. Furthermore, the devices themselves often run on outdated firmware with known security flaws, making them easy targets for exploitation. The open nature of many internet-connected devices, combined with a lack of regular security audits, significantly increases the risk.
Methods of Attack
Attackers can employ various methods to compromise UPS systems. Common tactics include brute-force password attacks, exploiting known vulnerabilities in the device’s firmware (often through publicly available exploits), and using phishing techniques to trick administrators into providing credentials. Once access is gained, attackers can then use the compromised UPS as a foothold to penetrate other systems within the network.
They might install malware to monitor network traffic, disable the UPS, or even use it as a launching point for further attacks on more sensitive systems. In some cases, compromised UPS systems could be incorporated into botnets, contributing to larger-scale attacks like distributed denial-of-service (DDoS) assaults.
Potential Impact of a Successful Cyberattack
A successful cyberattack on a UPS system can have several devastating consequences. The most immediate impact is the potential loss of power to critical systems. This could lead to data loss, equipment damage, and significant downtime, resulting in substantial financial losses. Beyond the direct impact on the affected system, a compromised UPS can serve as a gateway to a wider network breach, potentially exposing sensitive data and intellectual property.
In industrial settings, this could lead to operational disruptions, impacting production and safety. The reputational damage from such an incident could also be significant, impacting customer trust and business relationships.
Seriously freaked out about that cyber threat warning for internet-connected UPS devices – it highlights how vulnerable even seemingly simple devices can be. Thinking about secure development practices makes me appreciate the potential of domino app dev the low code and pro code future for building robust and secure applications. Hopefully, future UPS firmware updates will address these vulnerabilities, preventing future widespread attacks.
Examples of Malware and Techniques
While specific malware used in attacks against UPS systems isn’t always publicly disclosed due to security reasons, the techniques employed often mirror those used against other IoT devices. Examples include Mirai-style botnets, which recruit vulnerable devices to participate in DDoS attacks, and custom-built malware designed to exploit specific vulnerabilities in the UPS firmware. The use of readily available exploit kits further reduces the technical barrier to entry for attackers.
These kits automate the process of identifying and exploiting vulnerabilities, making it easier for less-skilled individuals to carry out attacks.
Common Vulnerabilities and Their Consequences
| Vulnerability | Impact | Exploitation Method | Mitigation Strategy |
|---|---|---|---|
| Default/Weak Passwords | Unauthorized access, system compromise | Brute-force attack, credential stuffing | Change to strong, unique passwords; enable multi-factor authentication |
| Outdated Firmware | Exploitation of known vulnerabilities | Exploit kits, malicious code injection | Regular firmware updates; automated update mechanisms |
| Lack of Security Features | Increased vulnerability to attacks | Various methods (e.g., port scanning, SQL injection) | Implement strong access controls, firewalls, intrusion detection systems |
| Unsecured Network Connections | Exposure to external threats | Network scanning, man-in-the-middle attacks | Use VPNs, secure network segmentation, strong encryption |
Affected Devices and Users
This cyber threat targeting internet-connected UPS (Uninterruptible Power Supply) devices has the potential to impact a wide range of users and industries. The vulnerability isn’t limited to a specific brand or model, though some are demonstrably more susceptible than others. Understanding the potential impact requires examining the types of devices affected, the geographic reach of the threat, and the critical services that could be disrupted.The types of UPS devices most vulnerable are those with outdated firmware, weak default passwords, or inadequate security protocols.
This includes both consumer-grade UPS units found in homes and small offices, as well as industrial-grade UPS systems supporting critical infrastructure. Older models, lacking robust security features, represent a particularly high-risk category. The threat actors are likely targeting devices with exposed remote management interfaces, allowing for remote control and exploitation.
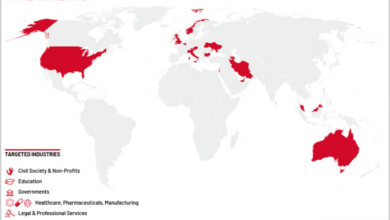
Geographic Locations and Industries Most Affected
While the threat is global in its potential reach, the impact will likely be felt most acutely in regions with high concentrations of critical infrastructure and advanced technology industries. Areas with dense data centers, manufacturing facilities, and healthcare institutions could experience significant disruptions. Industries particularly at risk include finance, healthcare, manufacturing, and telecommunications, where reliable power is essential for continued operations.
For example, a hospital reliant on a compromised UPS system could face a complete power failure during a critical procedure, leading to potentially life-threatening consequences. Similarly, a data center outage could result in significant financial losses and data breaches.
Potential Disruption to Critical Infrastructure or Services
The consequences of a successful attack could range from minor inconveniences to catastrophic failures. A widespread compromise of UPS systems could lead to cascading power outages, impacting not only individual users but also essential services. Imagine a scenario where multiple hospitals in a city simultaneously experience power failures due to compromised UPS units—the consequences would be devastating. Similarly, a large-scale attack on data centers could lead to widespread internet disruptions and data loss, crippling financial markets and other critical systems.
The ripple effect of such an event could be felt globally.
Hypothetical Scenario: Impact on a Small Business
Consider “Bob’s Bakery,” a small business reliant on a network of computers and refrigeration units. Their internet-connected UPS system is compromised, leading to a complete power outage during a crucial baking period. This results in spoiled goods, lost revenue, and potential damage to equipment. Furthermore, the attack could compromise their customer database, leading to further financial losses and reputational damage.
This scenario highlights the significant impact this threat can have even on smaller businesses.
Vulnerability Levels of Different UPS Manufacturers
The following table provides a hypothetical assessment of vulnerability levels based on reported vulnerabilities and security features of different manufacturers. Note that this is not an exhaustive list, and actual vulnerability levels may vary depending on the specific model and firmware version.
| Manufacturer | Model | Vulnerability Level (Low, Medium, High) | Mitigation Recommendation |
|---|---|---|---|
| APC | Smart-UPS SRT 1500VA | Medium | Update firmware, change default password, enable strong authentication. |
| CyberPower | CP1500PFCLCD | Low | Regular firmware updates and strong password practices are recommended. |
| Eaton | 5PX1500RT2U | High | Immediate firmware update, strong password, disable remote access if not needed. |
| Tripp Lite | OM600 | Medium | Regular security audits and firmware updates are advised. |
Mitigation and Prevention Strategies
Securing your internet-connected UPS devices is crucial to maintaining the integrity of your network and preventing potential disruptions. A multi-layered approach encompassing robust security practices, regular updates, and controlled network access is vital to mitigating the risks associated with these threats. This section Artikels practical steps you can take to bolster your UPS device security.
Effective security isn’t a one-time fix; it’s an ongoing process. The threat landscape is constantly evolving, demanding proactive measures to stay ahead of potential vulnerabilities.
Firmware Updates and Patching Vulnerabilities
Regularly updating your UPS device’s firmware is paramount. Firmware updates often include critical security patches that address known vulnerabilities, preventing attackers from exploiting weaknesses in the system’s software. Manufacturers release these updates to fix bugs and enhance security, so checking for updates should be a regular part of your maintenance routine. Ignoring updates leaves your device exposed to potentially devastating attacks.
For example, a known vulnerability in a specific UPS model allowed remote code execution, potentially leading to complete system compromise. Prompt patching prevented this in many cases.
Network Segmentation and Access Controls, Cyber threat warning issued to all internet connected ups devices
Implementing network segmentation isolates your UPS devices from other sensitive parts of your network. This limits the impact of a successful attack. If a compromised UPS were on the same network segment as your servers, the attacker could potentially access those servers as well. By segmenting your network, you create a barrier that prevents this lateral movement.
Furthermore, restricting access to your UPS devices using strong passwords and multi-factor authentication (MFA) further enhances security. Only authorized personnel should have access to manage the device’s settings.
Robust Security Protocols and Best Practices
Employing robust security protocols significantly reduces the risk of compromise. This includes using strong, unique passwords for all devices and enabling any available security features such as encryption and authentication protocols. Consider using protocols like HTTPS for any communication with the UPS device’s management interface. Implementing a firewall to control network traffic in and out of the device adds another layer of protection.
Regularly review and update your security policies to reflect the latest best practices and address emerging threats. Think of it as a layered defense, where each measure adds to the overall resilience of your system. For instance, a company that implemented MFA alongside network segmentation reported a significant decrease in successful cyberattacks targeting their UPS systems.
Steps to Protect Your Systems
Here’s a concise list of actionable steps to protect your internet-connected UPS devices:
- Change the default password immediately upon installation.
- Enable strong authentication methods like MFA wherever possible.
- Regularly check for and install firmware updates.
- Segment your network to isolate UPS devices from other critical systems.
- Use a firewall to control network access to the UPS.
- Monitor your UPS device for unusual activity.
- Keep detailed records of all configuration changes.
Incident Response and Recovery

A compromised UPS (Uninterruptible Power Supply) device, especially one connected to the internet, poses a significant risk, potentially disrupting operations and exposing sensitive data. Swift and effective incident response is crucial to minimize damage and ensure business continuity. This section Artikels the necessary steps to take should your UPS be compromised.
Identifying and Isolating Infected Devices
Identifying a compromised UPS requires vigilant monitoring and a proactive approach. Regular security audits, including vulnerability scans and penetration testing, are essential preventative measures. However, if suspicion arises, immediate action is necessary. Look for unusual network activity emanating from the UPS’s IP address, such as unexpected outbound connections or unusually high data transfer rates. Review system logs for suspicious entries, such as unauthorized access attempts or unusual configuration changes.
If suspicious activity is detected, immediately isolate the UPS from the network by disconnecting it from the internet and any other network connections. This prevents further damage and limits the potential spread of malware. Physical isolation, such as unplugging the device, is also recommended.
Data Recovery and System Restoration
Data recovery from a compromised UPS depends heavily on the extent of the compromise. If malware has encrypted data, specialized decryption tools or professional data recovery services may be necessary. Before attempting any data recovery, create a full image backup of the UPS’s storage media (if applicable) to preserve potential evidence for forensic analysis. If the compromise involved a firmware infection, a complete firmware reinstallation from a verified, trusted source is necessary.
This requires following the manufacturer’s instructions precisely. System restoration should involve wiping and reinstalling the operating system (if applicable), followed by thorough security hardening, including strong passwords and updated firmware. Remember to verify the integrity of all software and firmware after restoration.
Incident Reporting and Collaboration
Prompt and accurate incident reporting is vital for effective response and prevention of future incidents. Document all actions taken, including the timeline of events, the nature of the compromise, and the steps taken to contain and remediate the issue. This documentation is crucial for internal investigations and potential legal or regulatory requirements. Collaboration with cybersecurity experts, incident response teams, and potentially law enforcement (depending on the severity and nature of the breach) is essential.
Sharing information with other organizations that may be affected by similar threats facilitates collective learning and helps improve overall cybersecurity posture. Consider reporting the incident to relevant Computer Emergency Response Teams (CERTs) or similar organizations.
Incident Response Process Flowchart
The following flowchart illustrates the key steps in responding to a compromised UPS device:
- Detect Anomaly: Observe unusual network activity, system logs, or performance issues.
- Isolate Device: Immediately disconnect the UPS from the network and power source.
- Assess Damage: Determine the extent of the compromise (data breach, malware infection, etc.).
- Data Backup & Preservation: Create a forensic image of the UPS’s storage (if applicable).
- Data Recovery: Attempt data recovery using appropriate methods.
- System Restoration: Reinstall firmware/OS from trusted sources and apply security hardening.
- Incident Reporting: Document the incident and report to relevant authorities and stakeholders.
- Post-Incident Analysis: Review the incident to identify vulnerabilities and improve security measures.
Future Implications and Trends: Cyber Threat Warning Issued To All Internet Connected Ups Devices
The recent cyber threat targeting internet-connected UPS devices is just a glimpse into the rapidly evolving landscape of IoT security. The increasing interconnectedness of our world, while offering undeniable benefits, simultaneously expands the attack surface for malicious actors. This incident underscores the urgent need for a proactive and comprehensive approach to securing not only UPS systems but the entire IoT ecosystem.
Failing to address these vulnerabilities will lead to increasingly sophisticated and devastating attacks in the future.The interconnected nature of IoT devices means a breach in one system can easily cascade into others. This incident serves as a stark reminder that even seemingly simple devices, like UPS systems, can become critical entry points for larger, more destructive attacks. The implications extend far beyond simple power outages; compromised UPS systems could be used as stepping stones to access sensitive data within a network, potentially impacting critical infrastructure or sensitive business operations.
Evolving Cyber Threats Targeting IoT Devices
The sophistication of cyber threats targeting IoT devices is constantly increasing. We’re moving beyond simple denial-of-service attacks towards more targeted and complex attacks that exploit vulnerabilities in firmware, communication protocols, and device management systems. Malicious actors are becoming increasingly adept at using these devices as part of larger botnets, capable of launching massive distributed denial-of-service (DDoS) attacks or conducting espionage operations.
For example, the Mirai botnet, which famously targeted Dyn in 2016, leveraged vulnerabilities in a wide range of IoT devices, including routers and security cameras, highlighting the potential for widespread disruption. Future attacks could leverage artificial intelligence and machine learning to automate the discovery and exploitation of vulnerabilities, making them even more difficult to detect and defend against.
Potential Future Vulnerabilities in UPS Systems and Similar Devices
Future vulnerabilities in UPS systems and similar devices could arise from several sources. One key area of concern is the lack of robust authentication and authorization mechanisms. Many devices rely on default passwords or weak encryption, making them easy targets for brute-force attacks. Furthermore, the increasing reliance on cloud-based management platforms introduces new vulnerabilities, such as insecure APIs and data breaches in the cloud itself.
Another significant risk lies in the lack of regular firmware updates and patching. Outdated firmware often contains known vulnerabilities that malicious actors can exploit. Finally, the increasing integration of UPS systems with other IoT devices within a network expands the potential attack surface, creating more opportunities for lateral movement by attackers.
The Need for Enhanced Security Standards and Regulations
The current security standards and regulations for IoT devices are often insufficient to address the evolving threat landscape. There’s a need for more stringent requirements for device authentication, data encryption, and secure firmware updates. Mandatory security assessments before devices are released to the market could help identify and mitigate vulnerabilities early in the development process. Stronger regulatory frameworks are also necessary to hold manufacturers accountable for the security of their products and to establish clear penalties for failing to address vulnerabilities.
Examples of improved regulations could include mandatory security certifications for IoT devices, similar to those already in place for other types of electronic equipment. Furthermore, international collaboration is crucial to establish globally recognized security standards and enforcement mechanisms.
Recommendations for Manufacturers to Improve Product Security
Manufacturers must prioritize security from the design phase onwards, employing secure coding practices, robust authentication mechanisms, and end-to-end encryption. Regular security audits and penetration testing should be conducted to identify and address vulnerabilities before product release. A comprehensive firmware update mechanism is crucial to allow for timely patching of security flaws. Manufacturers should also invest in secure boot processes and provide clear and concise security documentation for their products.
Furthermore, manufacturers should establish robust incident response plans to address security incidents effectively and promptly. Open-source hardware and software can facilitate greater transparency and community-driven security improvements.
IoT Security Concerns Highlighted by This Threat
This UPS system cyber threat highlights the broader concerns surrounding IoT security. The sheer number of connected devices, their often limited processing power and memory, and the lack of standardized security practices create a significant challenge. The incident underscores the need for a holistic approach to IoT security that considers the entire ecosystem, from device manufacturers to end-users and network operators.
Collaborative efforts between industry stakeholders, researchers, and policymakers are essential to develop and implement effective security measures. This incident serves as a critical reminder that IoT security is not just a technical problem; it requires a multi-faceted approach that addresses technical, regulatory, and societal aspects.
Last Word
The cyber threat targeting internet-connected UPS devices underscores a broader issue: the expanding attack surface created by the Internet of Things (IoT). While these devices offer convenience and efficiency, their often-overlooked security vulnerabilities make them tempting targets. Taking proactive steps to secure these systems, including regular firmware updates, robust network security, and vigilant monitoring, is no longer optional – it’s essential.
Don’t wait for a disaster; take control of your digital security today. Stay informed, stay vigilant, and stay safe!
Essential Questionnaire
What specific types of malware are targeting UPS devices?
While specific malware names aren’t always publicly released due to ongoing investigations, attacks often involve variations of existing malware adapted to exploit vulnerabilities in UPS firmware or network protocols. Think of things like botnets, ransomware, and even custom-built tools designed for specific devices.
How can I tell if my UPS is vulnerable?
Check your UPS manufacturer’s website for security advisories and firmware updates. If your device is outdated or hasn’t received updates in a while, it’s likely vulnerable. You should also monitor your network for any unusual activity originating from your UPS’s IP address.
What if I don’t have internet connectivity to my UPS? Am I safe?
While not directly exposed to internet-borne threats, a locally connected UPS can still be vulnerable if it’s part of a larger network that’s compromised. Strong network security practices are crucial regardless of direct internet connectivity.