Cyber Threats to Healthcare on the Rise 2
Cyber threats to healthcare on the rise 2 – it’s a headline that’s unfortunately becoming all too familiar. We’re seeing a dramatic increase in cyberattacks targeting hospitals, clinics, and pharmaceutical companies, and the consequences are devastating. From ransomware crippling vital systems to data breaches exposing sensitive patient information, the stakes are higher than ever. This isn’t just about numbers; it’s about real people, their health, and their trust.
Let’s dive into the growing threat landscape and explore what we can do to fight back.
The sheer volume of attacks is alarming. We’re witnessing sophisticated attacks leveraging vulnerabilities in legacy systems and exploiting the interconnected nature of modern healthcare technology. The value of patient data on the dark web fuels this relentless assault, making healthcare a prime target. This post will explore the different types of attacks, their impact on patient care and finances, and, crucially, the strategies we need to implement to strengthen our defenses.
The Increasing Prevalence of Cyberattacks Targeting Healthcare
The healthcare industry, already grappling with staffing shortages and rising costs, faces a growing threat: cyberattacks. Over the past two years, we’ve seen a dramatic increase in the frequency and severity of these attacks, impacting everything from patient care to research and development. This isn’t just a technological issue; it’s a significant threat to public health and safety.The rise in healthcare cyberattacks is a complex issue with multiple contributing factors.
The expanding attack surface, driven by the increasing reliance on interconnected medical devices, electronic health records (EHRs), and telehealth platforms, creates more vulnerabilities for attackers to exploit. Simultaneously, the immense value of healthcare data – including protected health information (PHI) – makes it a lucrative target for both financially motivated cybercriminals and state-sponsored actors. This data can be sold on the dark web, used for identity theft, or leveraged for blackmail and extortion.
Factors Contributing to the Increase in Healthcare Cyberattacks
The expanding attack surface, coupled with the high value of healthcare data, creates a perfect storm for cybercriminals. Hospitals and clinics are increasingly reliant on networked systems, including medical devices like insulin pumps and pacemakers, which can be vulnerable to hacking. The transition to cloud-based systems, while offering benefits, also introduces new security challenges. Furthermore, the human element plays a crucial role.
Phishing attacks, exploiting employee vulnerabilities, remain a highly effective method of gaining access to sensitive systems. The lack of robust cybersecurity infrastructure and insufficient training among healthcare professionals further exacerbates the problem.
Types of Healthcare Organizations Targeted and Impact of Attacks
While all healthcare organizations are vulnerable, hospitals and pharmaceutical companies are disproportionately targeted due to the volume and sensitivity of the data they hold. Clinics and smaller healthcare providers are also frequent targets, often lacking the resources to invest in robust cybersecurity defenses.
| Year | Type of Attack | Target Organization | Impact |
|---|---|---|---|
| 2022 | Ransomware | University of Vermont Health Network | Disruption of patient care, financial losses, reputational damage |
| 2022 | Data Breach | Medibank (Australian health insurer) | Exposure of sensitive patient data, including medical records and claims information |
| 2023 | Phishing | Several small clinics in the US | Access to patient records, potential for identity theft and fraud |
| 2023 | Ransomware | A large pharmaceutical company (unnamed for confidentiality reasons) | Disruption of research and development, significant financial losses, potential for drug supply chain disruption |
Types of Cyber Threats Facing Healthcare Providers
The healthcare industry, with its sensitive patient data and interconnected systems, faces a unique and ever-growing threat landscape. Cybercriminals are increasingly targeting hospitals, clinics, and other healthcare providers, exploiting vulnerabilities to steal data, disrupt operations, and extort money. Understanding the specific types of cyber threats and their potential consequences is crucial for effective mitigation and protection.
Ransomware Attacks
Ransomware attacks are among the most prevalent and damaging cyber threats facing healthcare. These attacks involve malicious software that encrypts a victim’s data, rendering it inaccessible until a ransom is paid. In the healthcare context, this can be devastating. Imagine a hospital’s electronic health records (EHRs) being locked, preventing doctors from accessing crucial patient information during emergencies.
The consequences could be catastrophic, delaying treatment, leading to misdiagnosis, and potentially even causing patient harm. The pressure to pay the ransom to restore access to critical systems is immense.
- Attackers often exploit vulnerabilities in outdated software or phishing emails to deploy ransomware.
- They may use sophisticated encryption techniques to make data recovery extremely difficult.
- Ransom demands can range from thousands to millions of dollars.
- Data breaches resulting from ransomware attacks can lead to significant financial losses, legal penalties, and reputational damage.
Phishing Attacks
Phishing is a social engineering technique where attackers attempt to trick individuals into revealing sensitive information, such as usernames, passwords, and credit card details. In healthcare, phishing attacks often target employees with emails that appear to be from legitimate sources, such as the hospital administration or a trusted vendor. These emails may contain malicious attachments or links that download malware onto the victim’s computer, granting attackers access to the network.
A successful phishing attack can lead to data breaches, ransomware infections, and account takeovers.
- Attackers often craft highly convincing emails that mimic legitimate communications.
- They may use spoofed email addresses or create fake websites that look identical to real ones.
- Phishing emails may contain malicious attachments or links that download malware.
- Successful phishing attacks can lead to data breaches, ransomware infections, and financial losses.
Denial-of-Service (DoS) Attacks
Denial-of-service attacks flood a network or server with traffic, making it unavailable to legitimate users. In healthcare, a DoS attack can disrupt critical services, such as online appointment scheduling, patient portals, and electronic health record systems. This can severely impact patient care, potentially leading to delays in treatment and increased wait times. The disruption of services can also cause significant financial losses and reputational damage.
- Attackers use various methods to generate large amounts of traffic, overwhelming the target system.
- DoS attacks can be launched from a single source or a distributed network of compromised computers (DDoS).
- The consequences of a DoS attack can include service disruptions, financial losses, and reputational damage.
Unique Vulnerabilities of Healthcare Systems
Healthcare systems are particularly vulnerable to cyberattacks due to their reliance on legacy systems, interconnected medical devices, and the sensitive nature of the data they handle. Many healthcare organizations still use outdated software and hardware, making them easy targets for attackers. The increasing connectivity of medical devices, such as insulin pumps and pacemakers, introduces new vulnerabilities, as these devices can be remotely accessed and compromised.
The sheer volume of sensitive patient data held by healthcare providers makes them attractive targets for data theft and extortion. For example, a breach of patient data could lead to identity theft, financial fraud, and reputational damage for the healthcare provider. The consequences can be far-reaching and costly.
The Impact of Cyberattacks on Patient Care and Healthcare Operations
Cyberattacks against healthcare providers aren’t just a technological problem; they have profound and far-reaching consequences for patients, staff, and the healthcare system as a whole. The disruption caused by these attacks extends beyond simple inconvenience, impacting patient safety, financial stability, and public trust. Understanding these impacts is crucial for developing effective preventative measures and response strategies.
Disruption of Patient Care
A successful cyberattack can cripple a healthcare organization’s ability to deliver timely and effective care. Ransomware attacks, for example, can lock down electronic health records (EHRs), preventing doctors from accessing crucial patient information needed for diagnosis and treatment. This can lead to delayed or cancelled surgeries, postponed appointments, and misdiagnosis due to the lack of readily available medical history.
Data breaches, exposing sensitive patient information, can also lead to a loss of confidence in the healthcare provider, causing patients to seek care elsewhere, potentially exacerbating existing healthcare access issues. The disruption extends beyond direct patient care to administrative functions, hindering appointment scheduling, billing, and medication management. For instance, the 2017 WannaCry ransomware attack affected hospitals worldwide, disrupting services and delaying patient treatment.
Cyber threats to healthcare are escalating, forcing organizations to rethink their security strategies. A crucial element of this is robust cloud security, and that’s where understanding solutions like bitglass and the rise of cloud security posture management becomes vital. Ultimately, strengthening cloud security is a key step in mitigating the growing risks facing the healthcare sector.
Financial Repercussions for Healthcare Organizations
The financial burden of a cyberattack on a healthcare organization can be devastating. Ransom payments, while often demanded, are only the tip of the iceberg. Organizations face significant costs associated with incident response, including hiring cybersecurity experts, forensic investigations, and legal counsel. Recovery efforts, such as rebuilding systems and restoring data, can take months and incur substantial expenses.
Furthermore, reputational damage following a breach can lead to decreased patient volume, loss of insurance contracts, and increased difficulty attracting and retaining skilled staff. The fines and penalties levied by regulatory bodies, like HIPAA in the United States, can add further financial strain. Consider the case of the University of Vermont Health Network, which faced millions of dollars in costs after a ransomware attack in 2020.
Impact on Patient Privacy and Data Security, Cyber threats to healthcare on the rise 2
Healthcare data is among the most sensitive and valuable information available, containing personal details, medical history, and financial information. Breaches can expose this data to malicious actors, leading to identity theft, medical fraud, and emotional distress for patients. The consequences can be long-lasting and far-reaching, impacting patients’ credit scores, insurance coverage, and overall sense of security. Beyond the individual impact, large-scale breaches can erode public trust in the healthcare system and damage the reputation of the affected organization.
The consequences can extend beyond the immediate victims, impacting public health by hindering disease surveillance and potentially delaying or disrupting crucial public health initiatives.
Short-Term and Long-Term Effects of a Major Cyberattack
| Effect | Short-Term (0-6 months) | Long-Term (6+ months) |
|---|---|---|
| Patient Care | Delayed or cancelled treatments, inaccurate diagnoses, reduced access to care, increased wait times. | Lingering effects on patient trust, potential for long-term health consequences due to delayed care, difficulty attracting and retaining patients. |
| Financial Impact | Ransom payments, costs of incident response, system recovery, loss of revenue due to service disruptions. | Reduced profitability, difficulty securing loans, increased insurance premiums, potential legal settlements. |
| Reputational Damage | Negative media coverage, loss of patient confidence, damage to brand image. | Long-term erosion of trust, difficulty attracting new patients and staff, potential loss of market share. |
| Regulatory Compliance | Potential for fines and penalties from regulatory bodies (e.g., HIPAA violations). | Ongoing monitoring and compliance costs, potential for future legal action. |
Strategies for Mitigating Cyber Threats in Healthcare
The healthcare industry faces a unique challenge in cybersecurity, balancing the need for robust data protection with the critical demands of patient care. Effective mitigation strategies require a multi-faceted approach, encompassing technological safeguards, robust employee training, and a commitment to ongoing security assessments. Failing to implement these strategies can lead to devastating consequences, including data breaches, financial losses, and irreparable damage to patient trust.
Implementing comprehensive cybersecurity measures is no longer optional; it’s a necessity for survival in today’s threat landscape. Healthcare providers must adopt a layered security approach, combining various technologies and practices to create a robust defense against increasingly sophisticated attacks. This involves investing in advanced security tools, educating staff on best practices, and regularly evaluating the effectiveness of security protocols.
Multi-Factor Authentication and Employee Training
Multi-factor authentication (MFA) significantly enhances security by requiring multiple forms of verification before granting access to systems and data. This can include something the user knows (password), something the user has (security token), and something the user is (biometrics). Combining these methods makes it exponentially more difficult for attackers to gain unauthorized access, even if they obtain a password.
Employee training is equally crucial. Regular cybersecurity awareness programs should educate staff on phishing scams, malware, and social engineering tactics, empowering them to identify and report suspicious activity. Realistic phishing simulations can effectively assess employee vulnerability and reinforce training. For example, a hospital could simulate a phishing email mimicking a request for patient data, allowing them to track who falls victim and provide targeted retraining.
Robust Security Protocols and Technologies
Firewalls act as the first line of defense, filtering network traffic and blocking malicious attempts to access internal systems. Intrusion detection systems (IDS) monitor network activity for suspicious patterns, alerting security personnel to potential threats in real-time. Data encryption protects sensitive patient information, both in transit and at rest, rendering it unreadable to unauthorized individuals. For instance, encrypting electronic health records (EHRs) ensures that even if a breach occurs, the data remains confidential.
Implementing robust access controls, limiting user privileges based on their roles and responsibilities, further strengthens security. This principle of least privilege ensures that even if an account is compromised, the attacker’s access is restricted.
Comparison of Security Solutions and Costs
The cost-effectiveness of different security solutions varies greatly. Basic antivirus software is relatively inexpensive but offers limited protection against sophisticated threats. Advanced threat detection systems, while more expensive, provide comprehensive monitoring and response capabilities. The decision of which security solutions to implement should be based on a thorough risk assessment, considering the organization’s size, budget, and the sensitivity of the data it handles.
Healthcare is facing a serious surge in cyberattacks, making robust security paramount. Building secure and efficient systems is crucial, and that’s where the advancements in application development come in; check out this article on domino app dev, the low-code and pro-code future , for insights into faster, potentially more secure development. Ultimately, these innovations could help healthcare providers better combat the escalating cyber threats they face.
A smaller clinic might prioritize basic MFA and employee training, while a large hospital system might invest in a more comprehensive suite of security tools, including SIEM (Security Information and Event Management) systems for centralized threat monitoring and response. The long-term cost of a data breach, including legal fees, reputational damage, and regulatory fines, far outweighs the cost of preventative measures.
Layered Security Approach
A layered security approach combines multiple security controls to create a robust defense-in-depth strategy. This approach recognizes that no single security measure is foolproof. By implementing multiple layers, organizations can significantly reduce their vulnerability to cyberattacks.
- Network Security: Firewalls, intrusion prevention systems (IPS), and network segmentation.
- Endpoint Security: Antivirus software, endpoint detection and response (EDR) solutions, and data loss prevention (DLP) tools.
- Application Security: Secure coding practices, vulnerability scanning, and penetration testing.
- Data Security: Data encryption, access controls, and data backups.
- User and Access Management: Multi-factor authentication (MFA), strong password policies, and regular security awareness training.
- Incident Response: Incident response plan, security information and event management (SIEM) system, and regular security audits.
The Role of Government and Industry Regulations in Cybersecurity for Healthcare

The healthcare industry faces a unique challenge in balancing patient privacy with the need for technological advancement. This delicate balance necessitates robust cybersecurity measures, and government regulations and industry standards play a crucial role in establishing and enforcing these measures. Without strong regulatory frameworks, the risks associated with cyberattacks on healthcare organizations would be significantly amplified.Government regulations and industry standards provide a framework for healthcare providers to build secure systems, protect patient data, and respond effectively to cyber incidents.
They also establish accountability and provide a basis for legal action in cases of non-compliance. However, the effective implementation and enforcement of these regulations presents significant ongoing challenges.
HIPAA and its Impact on Healthcare Cybersecurity
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a cornerstone of healthcare data privacy and security in the United States. While not solely focused on cybersecurity, HIPAA’s Privacy Rule and Security Rule establish significant requirements for protecting the confidentiality, integrity, and availability of electronic protected health information (ePHI). The Security Rule specifically Artikels administrative, physical, and technical safeguards that covered entities must implement.
These safeguards include risk assessments, security awareness training for staff, access controls, and data encryption. Failure to comply with HIPAA can result in significant civil and criminal penalties. For example, a hospital failing to properly secure patient data leading to a breach could face hefty fines and reputational damage. The penalties can be substantial, driving organizations to invest in better security practices.
The NIST Cybersecurity Framework and its Application to Healthcare
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is a voluntary framework that provides a comprehensive approach to managing cybersecurity risk. Unlike HIPAA, which focuses specifically on the protection of ePHI, the NIST framework offers a broader, more adaptable approach applicable across various sectors, including healthcare. It Artikels five core functions: Identify, Protect, Detect, Respond, and Recover.
Healthcare organizations can use the framework to assess their current cybersecurity posture, identify gaps, and develop a plan to improve their defenses. The framework’s flexibility allows organizations to tailor their implementation to their specific needs and resources, making it a valuable tool for organizations of all sizes. A successful implementation of the NIST framework allows for better risk management and preparedness in case of a cyberattack.
Regulatory Enforcement and Challenges in Implementation
Regulatory bodies like the Office for Civil Rights (OCR) within the U.S. Department of Health and Human Services (HHS) are responsible for enforcing HIPAA compliance. They conduct audits, investigate complaints, and impose penalties on organizations that fail to meet the requirements. Similarly, other national and international regulatory bodies play a vital role in enforcing compliance with various cybersecurity standards and guidelines.
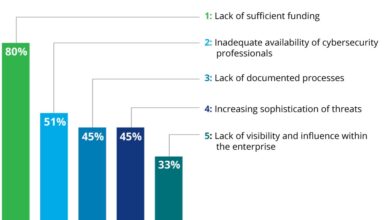
However, challenges remain in effectively enforcing these regulations. These challenges include the ever-evolving nature of cyber threats, the complexity of healthcare IT systems, and the resource constraints faced by many healthcare providers. Keeping up with the latest threats and implementing the necessary security measures can be expensive and time-consuming. Furthermore, the sheer volume of data involved in healthcare makes complete protection challenging, and the human element – such as phishing attacks targeting employees – remains a significant vulnerability.
Summary of Key Regulations and Standards
| Regulation/Standard | Scope | Enforcement Mechanism |
|---|---|---|
| HIPAA (Privacy & Security Rules) | Protection of ePHI | OCR audits, investigations, and penalties |
| NIST Cybersecurity Framework | Managing cybersecurity risk across all organizational functions | Voluntary adoption, but influences industry best practices and may be referenced in regulatory investigations |
The Future of Cybersecurity in Healthcare

The healthcare industry faces an increasingly complex and sophisticated cyber threat landscape. The sheer volume and variety of attacks, coupled with the sensitive nature of patient data, demand a proactive and innovative approach to cybersecurity. Looking ahead, we can anticipate a continued escalation of threats, necessitating the adoption of advanced technologies and collaborative strategies.The evolving landscape of cyber threats will likely see a rise in targeted attacks leveraging artificial intelligence (AI) to bypass traditional security measures.
Ransomware attacks will become more sophisticated, potentially targeting critical infrastructure and causing widespread disruption. Furthermore, the increasing reliance on interconnected medical devices and the Internet of Medical Things (IoMT) presents new vulnerabilities that malicious actors will undoubtedly exploit. We’ve already seen examples of ransomware attacks crippling hospitals, delaying critical care, and jeopardizing patient safety. The future will likely see more frequent and severe instances of this.
Emerging Technologies Enhancing Healthcare Cybersecurity
AI-powered threat detection systems are becoming increasingly crucial in identifying and responding to cyber threats in real-time. These systems can analyze vast amounts of data to identify anomalies and patterns indicative of malicious activity, far exceeding the capabilities of human analysts alone. For example, an AI system could detect unusual login attempts from a specific geographic location or identify subtle changes in network traffic that might signal a breach.
Blockchain technology offers potential for enhanced data security and integrity. By creating a tamper-proof record of patient data, blockchain can significantly reduce the risk of data breaches and unauthorized access. Imagine a system where patient medical records are stored on a decentralized blockchain, making it virtually impossible for a single point of failure to compromise the entire system.
Collaboration and Information Sharing in Healthcare Cybersecurity
Effective cybersecurity in healthcare requires a collaborative approach. Sharing threat intelligence and best practices among healthcare providers, cybersecurity experts, and government agencies is paramount. This collaborative approach can facilitate the rapid identification and mitigation of emerging threats. A hypothetical scenario illustrates this: If one hospital experiences a ransomware attack, sharing details of the attack vector and mitigation strategies with other hospitals can prevent similar attacks elsewhere.
A centralized, secure platform for sharing threat intelligence could greatly enhance the collective security posture of the entire healthcare sector.
Potential Future Threats and Their Impact
Several significant threats are anticipated to pose major challenges to healthcare cybersecurity in the coming years. These include the increasing sophistication of AI-powered attacks, the proliferation of IoT medical devices with inherent vulnerabilities, and the rise of targeted attacks against specific healthcare organizations holding valuable data. The impact of these threats could be devastating, ranging from data breaches leading to patient identity theft and financial losses to disruptions of critical healthcare services, potentially resulting in patient harm or even loss of life.
The potential for significant reputational damage to healthcare organizations should also not be underestimated. A high-profile data breach could severely impact patient trust and the financial stability of the affected institution.
Closing Notes: Cyber Threats To Healthcare On The Rise 2
The rise of cyber threats in healthcare isn’t just a trend; it’s a crisis demanding immediate attention. While the challenges are significant – from outdated systems to the sheer complexity of modern healthcare networks – the solutions are within reach. A multi-pronged approach combining robust security technologies, rigorous employee training, and proactive regulatory oversight is crucial. By fostering collaboration between healthcare providers, cybersecurity experts, and government agencies, we can create a more resilient and secure healthcare ecosystem.
The fight is far from over, but by working together, we can significantly reduce the risk and protect the invaluable data and lives entrusted to our care.
FAQ
What are the most common types of phishing attacks targeting healthcare professionals?
Common phishing attacks include emails pretending to be from trusted sources (like insurance companies or the CDC) requesting login details or containing malicious links. Spear phishing, targeting specific individuals with personalized messages, is also prevalent.
How can small clinics afford robust cybersecurity measures?
Small clinics can leverage cost-effective solutions like cloud-based security services, multi-factor authentication, and employee training programs. Focusing on basic security hygiene and regularly updating software can significantly reduce vulnerabilities.
What is the role of patients in protecting their health data?
Patients should be vigilant about suspicious emails and calls, avoid clicking on unknown links, and report any suspected breaches to their healthcare provider immediately. Understanding their rights regarding data privacy is also crucial.