Venn Redefines Remote Work Security with BYOPC
Venn redefines remote work security with innovative byo pc solution – Venn redefines remote work security with its innovative BYOPC (Bring Your Own PC) solution. This isn’t your grandpappy’s VPN; we’re talking about a whole new approach to securing remote workforces. Forget the headaches of managing company-owned devices – Venn’s solution empowers employees to use their personal computers while maintaining robust security. This post dives deep into how Venn achieves this, exploring its security features, impact on employee experience, and overall cost-effectiveness.
Get ready to rethink remote work security!
Imagine a world where employees are happier because they use their preferred devices, and IT teams sleep soundly knowing their data is secure. That’s the promise of Venn’s BYOPC solution. We’ll unpack the details of its architecture, explore its advantages over traditional VPNs, and discuss how it addresses common vulnerabilities. We’ll also tackle the inevitable challenges of a BYOPC strategy and show how Venn proactively mitigates them.
Prepare to be amazed by the possibilities!
Venn’s BYOPC Solution
Venn’s Bring Your Own PC (BYOPC) solution represents a significant shift in how organizations approach remote work security. Instead of mandating specific company-owned hardware, Venn empowers employees to use their personal devices while maintaining a robust security posture. This approach offers advantages in terms of employee satisfaction and cost-effectiveness, while simultaneously addressing critical security challenges inherent in traditional remote work setups.
This deep dive will explore the key features and benefits of Venn’s innovative solution.
Venn’s BYOPC solution is a game-changer for remote work security, addressing the challenges of managing diverse personal devices. But securing the data accessed on those devices requires robust application development, which is where the power of low-code and pro-code approaches comes in, as detailed in this insightful article on domino app dev the low code and pro code future.
Ultimately, combining Venn’s security focus with efficient app development creates a truly secure and productive remote workforce.
Core Components of Venn’s BYOPC Solution
Venn’s BYOPC solution is built upon a multi-layered security architecture. At its core is a secure, client-side agent that integrates seamlessly with the employee’s personal computer. This agent enforces security policies, monitors system activity, and provides a secure connection to the company network. It leverages micro-segmentation and zero-trust principles to isolate sensitive corporate data and applications. The solution also includes a centralized management console that allows IT administrators to monitor the security posture of all connected devices, deploy updates, and enforce policies consistently across the entire remote workforce.
Finally, robust authentication mechanisms, including multi-factor authentication (MFA), ensure only authorized users can access corporate resources.
Security Features Compared to Traditional VPNs
Traditional VPNs, while offering some level of security, often fall short in addressing the complexities of modern remote work environments. Venn’s BYOPC solution goes beyond the basic encryption provided by VPNs. It offers granular control over access to corporate resources, employing zero-trust principles to verify every user and device before granting access. Unlike VPNs that often rely on a single point of entry, Venn’s solution uses micro-segmentation to isolate sensitive data and applications, preventing lateral movement even if one device is compromised.
Furthermore, Venn’s solution incorporates advanced threat detection and response capabilities, automatically identifying and mitigating potential threats before they can cause damage. This proactive approach contrasts with the reactive nature of many VPN solutions.
Addressing Common Remote Work Security Vulnerabilities
Venn’s BYOPC solution directly addresses several common remote work security vulnerabilities. For example, it mitigates the risk of malware infections by employing endpoint detection and response (EDR) technologies that constantly monitor for malicious activity. It also protects against phishing attacks and other social engineering techniques through strong authentication mechanisms and security awareness training integrated within the platform. The solution’s ability to enforce device posture requirements ensures that only compliant devices can access corporate resources, preventing access from compromised or outdated systems.
By providing a secure and controlled environment for accessing corporate data and applications, Venn significantly reduces the attack surface for remote workers.
Comparison with Competitor Offerings
The following table compares Venn’s BYOPC solution with three hypothetical competitor offerings (Competitor A, B, and C). Note that specific pricing and features may vary depending on the chosen plan and specific needs.
| Feature | Venn | Competitor A | Competitor B | Competitor C |
|---|---|---|---|---|
| Zero Trust Architecture | Yes | No | Partial | Yes |
| Micro-segmentation | Yes | No | No | Partial |
| Endpoint Detection & Response (EDR) | Yes | No | Yes | Yes |
| Multi-Factor Authentication (MFA) | Yes | Yes | Yes | Yes |
| Pricing (per user/month) | $25 | $15 | $30 | $20 |
Impact on Employee Experience

Venn’s BYOPC (Bring Your Own PC) solution has the potential to significantly reshape the employee experience, impacting everything from daily productivity to overall job satisfaction. The success, however, hinges on careful planning and execution, addressing both the opportunities and challenges inherent in such a model. A well-implemented BYOPC program can foster a more personalized and empowering work environment, while a poorly managed one can lead to frustration and decreased efficiency.The core of this impact lies in the shift of control and responsibility.
Employees gain more agency over their work tools, potentially leading to increased comfort and productivity. However, this also introduces complexities in maintaining consistent security and support across a diverse range of devices.
Productivity and Satisfaction
Allowing employees to use their preferred hardware can boost productivity and job satisfaction. Many employees are already familiar and comfortable with their personal devices, leading to quicker onboarding and a more seamless transition into their work tasks. The ability to customize their workspace—choosing specific software, keyboard layouts, or even monitor setups—can contribute to a more personalized and engaging work experience, reducing frustration and increasing efficiency.
For example, a graphic designer might experience a significant boost in productivity using their high-resolution personal monitor and preferred design software, compared to a standardized company-provided setup. This personalized approach can also foster a sense of ownership and responsibility, leading to increased job satisfaction.
Onboarding and Training Processes
Venn’s BYOPC solution can both improve and hinder onboarding and training, depending on the implementation. A streamlined onboarding process, incorporating clear guidelines on acceptable hardware specifications and security protocols, can facilitate a smooth transition. Pre-configured software packages and remote support options can minimize the time spent setting up work environments. However, if not carefully managed, variations in hardware and software configurations can complicate training efforts.
Providing standardized training materials that adapt to various device configurations and operating systems is crucial. For instance, a comprehensive onboarding checklist outlining necessary software installations and security configurations for various operating systems (Windows, macOS, Linux) will minimize confusion and ensure consistent security practices. Failure to do so could lead to inconsistent training experiences and potential security vulnerabilities.
Device Compliance and Updates
Managing device compliance and updates across a diverse range of employee-owned hardware presents a significant challenge. Venn’s solution likely addresses this through a combination of robust remote management tools, automated update mechanisms, and clear security policies. This includes implementing mandatory security software, regular security audits, and automated updates for critical system components. For example, the system might leverage Mobile Device Management (MDM) software to enforce security policies, push updates, and remotely wipe devices if necessary.
This ensures that despite the variety of devices, a consistent level of security is maintained across the entire workforce. The effectiveness of this approach relies on the adoption of these tools by employees and the enforcement of policies.
Challenges and Mitigation Strategies
Implementing a BYOPC strategy presents several challenges, but effective mitigation strategies can minimize their impact.
- Challenge: Ensuring consistent security across diverse hardware and software configurations.
- Mitigation: Implementing robust MDM solutions, enforcing strong password policies, and providing regular security training.
- Challenge: Providing adequate technical support for a wide range of devices.
- Mitigation: Offering comprehensive online documentation, remote support options, and a dedicated help desk.
- Challenge: Managing data loss and recovery across employee-owned devices.
- Mitigation: Implementing data encryption, regular backups, and clear data recovery procedures.
- Challenge: Maintaining compliance with industry regulations and internal policies.
- Mitigation: Developing comprehensive policies and procedures, conducting regular audits, and providing regular training on compliance requirements.
Security Architecture and Implementation: Venn Redefines Remote Work Security With Innovative Byo Pc Solution
Venn’s BYOPC (Bring Your Own PC) solution prioritizes a robust security architecture designed to protect company data while respecting employee autonomy. This architecture leverages a multi-layered approach encompassing data encryption, granular access controls, and rigorous device onboarding procedures. The system is built to minimize risks inherent in allowing personal devices onto a corporate network.
The core of Venn’s security lies in its combination of hardware and software security measures. Data encryption, both in transit and at rest, is implemented using industry-standard AES-256 encryption. This ensures that even if a device is compromised, the data remains inaccessible without the correct decryption keys. Access control is managed through a sophisticated role-based access control (RBAC) system, granting users only the permissions necessary for their roles, limiting the potential damage from a compromised account.
Furthermore, the system incorporates continuous monitoring and threat detection capabilities, proactively identifying and responding to potential security breaches.
Employee Onboarding and Device Security
The onboarding process for new employees using their personal devices involves several key steps. First, employees must agree to a comprehensive Acceptable Use Policy (AUP) outlining security responsibilities and acceptable behavior. Next, their devices undergo a security assessment, checking for malware, outdated software, and other vulnerabilities. This assessment uses a combination of automated scanning tools and manual review by IT personnel.
Once the device passes the assessment, a secure VPN connection is established, creating a secure tunnel for all corporate data traffic. Finally, the employee receives necessary access credentials and undergoes security awareness training.
Potential Security Risks and Mitigation Strategies
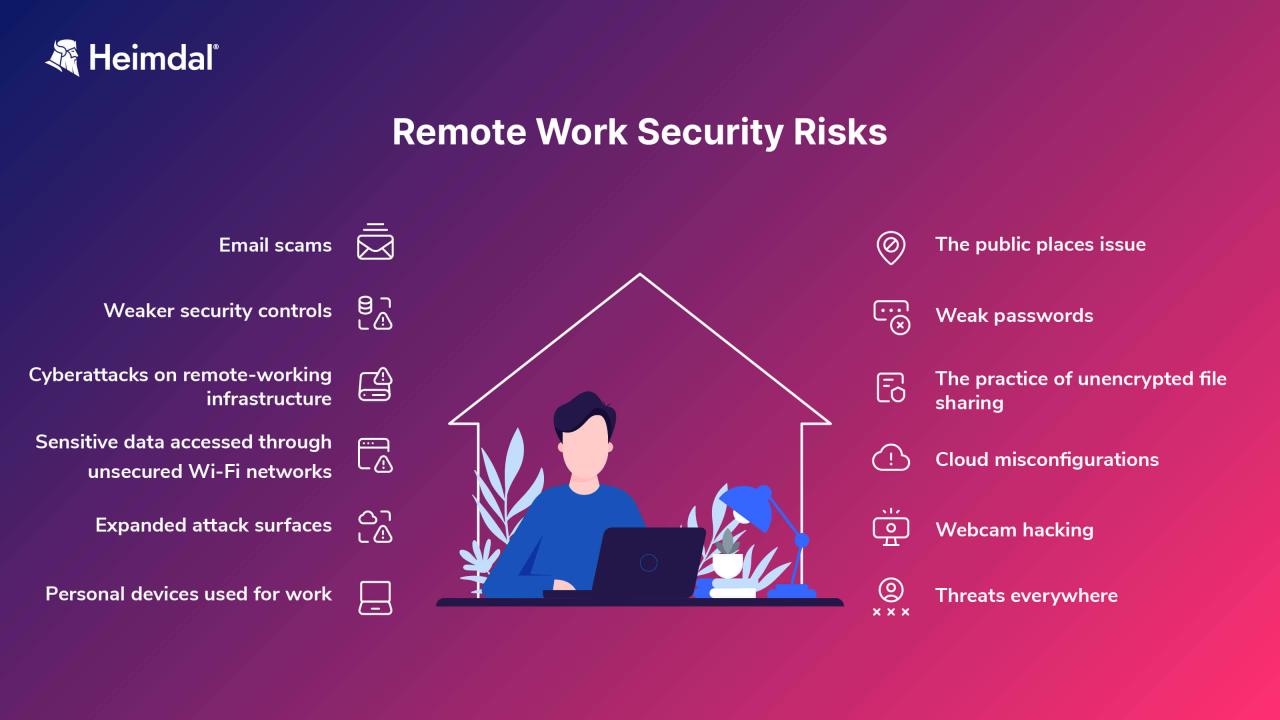
While BYOPC offers significant benefits, it also introduces potential risks. For instance, a lost or stolen device could expose company data. Venn mitigates this risk through strong password policies, multi-factor authentication (MFA), and device tracking capabilities. Another concern is the potential for malware infection on personal devices. Venn addresses this through mandatory security software installation, regular software updates, and proactive threat detection.
Finally, the risk of employee negligence or malicious intent is addressed through robust security awareness training, clear AUP guidelines, and ongoing monitoring of user activity.
BYOPC Solution Deployment and Management
Deploying and managing Venn’s BYOPC solution requires a systematic approach for IT administrators.
- Assessment and Planning: Begin by assessing the existing IT infrastructure and identifying any necessary upgrades or changes to accommodate BYOPC. This includes evaluating network bandwidth, security protocols, and existing security tools. A detailed implementation plan should be created outlining timelines, responsibilities, and potential challenges.
- Software Installation and Configuration: Install and configure the Venn BYOPC software on the company server and any necessary client-side components. This includes setting up the VPN gateway, configuring access control policies, and integrating with existing directory services.
- Employee Onboarding and Training: Implement the employee onboarding process as described above. Provide comprehensive training to both IT staff and employees on the security policies and procedures related to BYOPC.
- Ongoing Monitoring and Maintenance: Regularly monitor the system for security threats and vulnerabilities. Conduct regular security audits and update security software and policies as needed. This also includes monitoring user activity for any suspicious behavior.
- Incident Response: Develop and test an incident response plan to handle security breaches or data loss. This plan should Artikel steps to contain the breach, investigate the cause, and recover from the incident.
Cost-Effectiveness and ROI
Venn’s BYOPC (Bring Your Own PC) solution offers a compelling alternative to traditional remote work security models, promising significant cost savings and a rapid return on investment. By shifting the burden of hardware procurement from the company to the employee, and leveraging a robust, cloud-based security architecture, Venn’s solution streamlines IT operations and reduces overall expenditure. This approach allows organizations to focus resources on strategic initiatives rather than managing a vast and complex array of company-owned devices.The total cost of ownership (TCO) for traditional remote work setups often includes significant expenses related to purchasing and maintaining company-owned laptops, desktops, and associated software licenses.
These costs are compounded by the need for regular hardware upgrades, IT support for troubleshooting individual devices, and the ongoing management of software updates and security patches. In contrast, Venn’s BYOPC model significantly reduces these expenses by leveraging employee-owned devices, thereby minimizing capital expenditure and ongoing maintenance costs.
Total Cost of Ownership Comparison
A direct comparison of Venn’s BYOPC solution with a traditional model reveals substantial cost differences. Consider a company with 100 remote employees. A traditional approach might involve purchasing high-end laptops at $1500 each, totaling $150,000 upfront. Annual maintenance, including software licenses and IT support, could easily reach $50,000. Over three years, this totals $300,000.
With Venn’s BYOPC, the initial hardware cost is eliminated. While there will be ongoing costs associated with the security software and support, these are significantly lower, potentially reducing the three-year cost to $75,000 – a saving of $225,000. This savings assumes a modest annual cost of $25,000 for Venn’s security solution and support.
Reduction in IT Support Costs
Venn’s BYOPC solution contributes to a dramatic reduction in IT support costs. With a centralized security platform managing employee devices, troubleshooting and support become significantly more streamlined. Instead of dealing with a multitude of hardware and software issues across diverse devices, IT support can focus on the security platform itself, addressing common issues efficiently. This reduces the time spent on individual device support, freeing up IT staff for more strategic projects.
Return on Investment Measurement
Organizations can measure the ROI of Venn’s BYOPC solution by tracking key metrics such as: (1) the reduction in hardware procurement costs; (2) the decrease in IT support tickets and resolution time; (3) the improvement in employee productivity due to reduced technical issues; (4) the decreased risk of security breaches; and (5) the overall cost savings compared to traditional models.
By comparing the total cost of ownership over a defined period (e.g., three years) for both approaches, organizations can quantify the financial benefits of adopting Venn’s solution. For example, a company could calculate the difference in total IT expenditure between the traditional and BYOPC models and express this as a percentage return on the investment in Venn’s security platform.
Cost Savings and Efficiency Gains Visualization
A bar chart would effectively illustrate the cost savings. The X-axis would represent the three-year period (Year 1, Year 2, Year 3). The Y-axis would represent the total cost in dollars. Two bars would be displayed for each year: one representing the total cost under the traditional model (including hardware, software, and support) and the other representing the total cost under Venn’s BYOPC solution (including the cost of Venn’s security platform and support).
The difference in height between the bars for each year would visually demonstrate the cost savings achieved with Venn’s solution. A line graph could be overlaid to show the cumulative cost savings over the three-year period, further emphasizing the long-term ROI. The chart’s title would be “Cost Comparison: Traditional vs. Venn BYOPC (3-Year Projection).” A legend would clearly identify each bar and the line.
Future Trends and Innovation
Venn’s BYOPC solution represents a significant leap forward in remote work security, but the landscape of technology is constantly evolving. To maintain its leading edge, Venn must proactively anticipate and adapt to emerging trends, integrating new technologies and refining its approach to meet future challenges. This requires a forward-thinking strategy that embraces innovation and continuous improvement.The future of Venn’s BYOPC solution hinges on its ability to seamlessly integrate with the ever-changing technological landscape.
This involves anticipating future threats and developing robust countermeasures, as well as embracing new opportunities to enhance user experience and streamline security management.
AI-Powered Threat Detection and Response
Integrating advanced AI and machine learning capabilities into the BYOPC platform will be crucial for proactive threat detection and response. This could involve real-time analysis of device behavior, identifying anomalies indicative of malware or unauthorized access attempts. The system could automatically quarantine infected devices, preventing widespread breaches, and even learn from past incidents to improve its predictive capabilities.
For example, by analyzing network traffic patterns and device usage data, the AI could predict potential vulnerabilities and proactively mitigate risks before they materialize. This proactive approach would significantly enhance the overall security posture of the BYOPC system.
Enhanced Zero Trust Architecture
The core of Venn’s BYOPC solution already relies on a zero-trust model, but future enhancements could involve more granular access controls and continuous authentication. This might include integrating behavioral biometrics, analyzing user activity patterns to identify suspicious behavior. The system could also dynamically adjust access permissions based on real-time risk assessments, ensuring that only authorized users have access to sensitive data, regardless of their location or device.
For instance, access to certain applications or files could be temporarily revoked if unusual activity is detected, further strengthening the security posture.
Seamless Integration with Existing Security Tools, Venn redefines remote work security with innovative byo pc solution
Future iterations of the BYOPC solution should prioritize seamless integration with other widely used security tools and platforms. This could include integration with existing endpoint detection and response (EDR) solutions, security information and event management (SIEM) systems, and cloud-based security platforms. This interoperability will provide a more holistic security view, enabling better threat detection, incident response, and overall risk management.
Imagine a scenario where a threat is detected by the EDR system; this information is automatically relayed to the BYOPC platform, triggering an immediate response such as device isolation or password reset.
Predictive Analytics for Risk Mitigation
By leveraging data analytics and predictive modeling, Venn can enhance the BYOPC solution’s ability to anticipate and mitigate potential risks. This could involve analyzing historical data on security breaches, user behavior, and emerging threats to identify patterns and predict future vulnerabilities. The system could then proactively suggest security enhancements or recommend changes in user policies to minimize risk exposure.
For example, if a specific type of malware is detected in a particular geographic region, the system could automatically implement enhanced security measures for users in that region.
Long-Term Impact on the Remote Work Landscape
BYOPC solutions, like Venn’s, are poised to fundamentally reshape the remote work landscape. The ability to provide secure access to corporate resources from personally owned devices will empower a more flexible and productive workforce. This will lead to increased employee satisfaction, reduced IT costs, and a more agile and competitive business environment. We can expect to see a wider adoption of BYOPC models across various industries, driving innovation and fostering a more inclusive and geographically diverse workforce.
The success stories of companies that have successfully implemented BYOPC strategies, demonstrating improved productivity and reduced security incidents, will further fuel this adoption. This shift will necessitate a continued focus on robust security measures and user education to mitigate potential risks associated with BYOPC deployments.
Conclusive Thoughts

Venn’s BYOPC solution isn’t just a security upgrade; it’s a paradigm shift in how we approach remote work. By combining robust security with employee empowerment, Venn offers a compelling alternative to traditional remote access models. The potential cost savings, increased employee satisfaction, and enhanced security posture make it a compelling option for businesses of all sizes. Ready to ditch the corporate-issued laptops and embrace the future of secure remote work?
Then it’s time to learn more about Venn!
FAQs
What happens if an employee’s personal computer is lost or stolen?
Venn’s solution incorporates data encryption and remote wipe capabilities to protect company data in case of device loss or theft. The specific procedures would be Artikeld in the employee onboarding process and company security policy.
How does Venn ensure compliance with company security policies on personal devices?
Venn likely employs a combination of software agents, regular security audits, and policy enforcement tools to maintain compliance. This might include mandatory software updates, security scans, and restrictions on certain applications or activities.
Does Venn support all operating systems and hardware configurations?
While Venn likely aims for broad compatibility, there will be limitations. It’s best to check their official documentation or contact their support team for a comprehensive list of supported systems and hardware.
What level of IT support is required to manage Venn’s BYOPC solution?
The level of IT support required will depend on the size of the organization and the complexity of its IT infrastructure. However, Venn’s solution is designed to simplify management compared to traditional methods, potentially reducing the overall burden on IT staff.