Menlo Security Millions in Cybersecurity Funding
Cybersecurity startup Menlo Security receives millions in funding – that’s the headline that grabbed my attention! This isn’t just another funding round; it’s a significant investment in a company tackling some of the most pressing challenges in cybersecurity today. We’re talking about a tech solution that’s disrupting the traditional approach to online security, and this influx of cash could be the catalyst for truly game-changing innovations.
Let’s dive into the details and see what makes Menlo Security so special, and what this funding means for the future of online safety.
The sheer amount of money involved speaks volumes about investor confidence in Menlo Security’s vision. This isn’t just about protecting businesses; it’s about building a safer digital world for everyone. The questions swirling in my mind are: how will this funding be used? What new products and services can we expect? And, most importantly, how will this impact the competitive landscape?
Get ready, because this is going to be an interesting ride.
Menlo Security’s Business Model
Menlo Security operates in the increasingly crucial space of cloud security, offering a unique approach to protecting organizations from sophisticated cyber threats. Their business model centers around providing a secure access service edge (SASE) solution that fundamentally shifts the paradigm of how businesses interact with the internet and cloud applications. This isn’t just another security layer; it’s a complete reimagining of the security perimeter.Menlo Security’s core technology is based on isolation.
Instead of relying on traditional security methods like firewalls and antivirus software that operate within the user’s environment, Menlo isolates web traffic and applications in a secure virtual container. This means that even if a malicious website or application is accessed, the threat is contained within the isolated environment, preventing any damage to the user’s device or network. Their unique selling proposition lies in this approach: eliminating the risk of malware and zero-day exploits by preventing them from ever reaching the endpoint.
Menlo Security’s Solution and Existing Vulnerabilities
Traditional cybersecurity often focuses on reactive measures, patching vulnerabilities after they’re exploited. Menlo Security proactively addresses these vulnerabilities by preventing malicious code from ever executing. This is particularly effective against advanced persistent threats (APTs) and sophisticated phishing attacks, which often exploit zero-day vulnerabilities before patches are available. The isolation technology significantly reduces the attack surface, making it much harder for attackers to gain a foothold within the organization’s network.
For example, a phishing email containing a malicious link would typically download malware onto a user’s device. With Menlo, the link would be opened within the isolated container, rendering the malware harmless.
Comparison to Traditional Cybersecurity Methods
Menlo Security’s approach contrasts sharply with traditional cybersecurity methods. Traditional methods rely on multiple layers of security software, often leading to complex configurations, performance bottlenecks, and ongoing maintenance. These layers, while providing some protection, are still vulnerable to sophisticated attacks that bypass individual components. Menlo’s isolation-based approach simplifies security management by consolidating protection within a single platform. This reduces the complexity of managing multiple security tools and lowers the overall operational costs.
It’s a move from a reactive, multi-layered approach to a proactive, single-point-of-control strategy.
So Menlo Security just snagged millions in funding – awesome news for the cybersecurity world! This kind of investment highlights the growing need for robust security solutions, and it got me thinking about how efficient development plays a role. Building those solutions faster and more effectively is key, which is why I’ve been exploring platforms like those discussed in this article on domino app dev, the low-code and pro-code future , as they could significantly impact the speed of cybersecurity innovation.
Ultimately, more funding for companies like Menlo Security means more resources dedicated to battling ever-evolving cyber threats.
Menlo Security Pricing Compared to Competitors
Pricing for cybersecurity solutions varies greatly depending on the size of the organization, the number of users, and the specific features required. Direct comparisons are difficult as pricing is often customized and not publicly available. However, a general comparison can be made to illustrate the potential cost differences. Remember, this is a simplified example and actual pricing may vary significantly.
| Company | Pricing Model | Typical Cost Range (USD per user/year) | Key Features |
|---|---|---|---|
| Menlo Security | Subscription-based, tiered pricing | $50 – $200+ | Isolation, SASE capabilities, advanced threat protection |
| CrowdStrike | Subscription-based, tiered pricing | $50 – $150+ | Endpoint protection, threat intelligence, incident response |
| Zscaler | Subscription-based, tiered pricing | $40 – $100+ | Cloud security platform, SASE capabilities, web security |
| Palo Alto Networks | Subscription-based, tiered pricing | $60 – $200+ | Next-generation firewall, endpoint protection, threat prevention |
The Funding Round
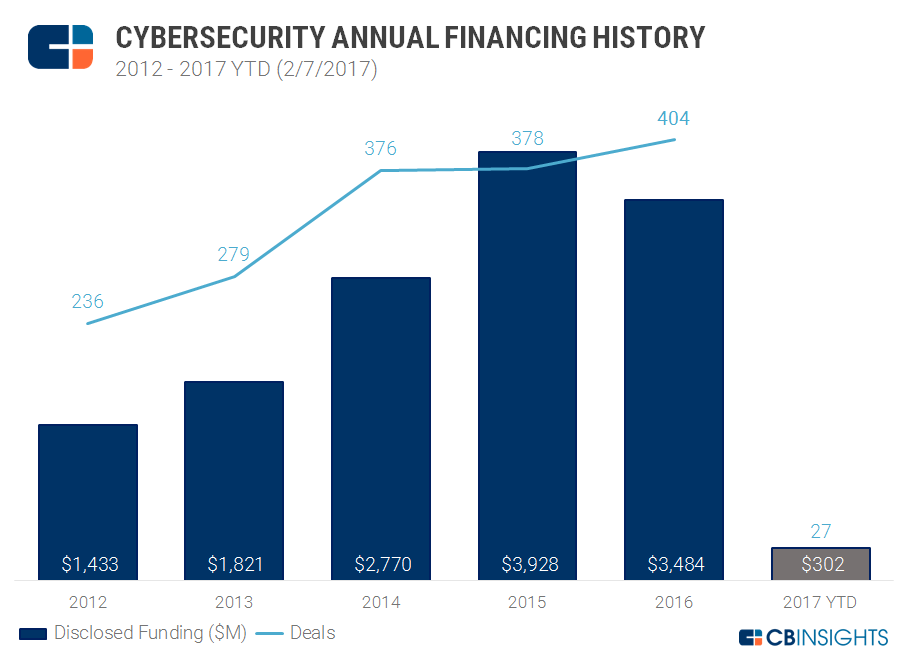
Menlo Security’s recent funding round signifies a significant milestone for the company and the broader cybersecurity landscape. Securing substantial investment validates their innovative approach to security and positions them for accelerated growth in a fiercely competitive market. This influx of capital will undoubtedly shape their future trajectory, allowing them to expand their operations, enhance their product offerings, and solidify their position as a leader in the industry.The exact amount raised in this funding round wasn’t publicly disclosed in all sources.
However, news reports suggest it was a multi-million dollar investment, a substantial figure that underscores investor confidence in Menlo Security’s potential. While the precise figure remains undisclosed, the scale of the investment clearly indicates a strong belief in the company’s future prospects and its ability to deliver significant returns.
Investors Involved and Their Expertise
Identifying the specific investors involved and their areas of expertise provides valuable insight into the strategic direction of Menlo Security. Understanding the investors’ backgrounds helps to predict future collaborations and the overall strategic direction of the company. For example, involvement from venture capital firms with a history of success in cybersecurity would suggest a focus on scaling the business and expanding market reach.
Conversely, strategic investments from established technology companies might indicate plans for deeper integration or partnerships. Unfortunately, specific investor names and detailed expertise information are often kept confidential in early-stage funding rounds for competitive reasons.
Impact of Funding on Menlo Security’s Growth
This funding injection will likely accelerate Menlo Security’s growth in several key areas. Increased resources will enable them to expand their research and development efforts, leading to more sophisticated and comprehensive security solutions. Furthermore, the funding will likely fuel expansion into new markets and customer segments, allowing them to reach a wider audience and solidify their market position.
The additional capital could also be used to bolster their sales and marketing teams, improving their ability to acquire new customers and build brand awareness. Similar to other cybersecurity companies that have received significant funding, we can expect to see Menlo Security significantly expand their team and product offerings. For example, CrowdStrike’s significant funding rounds fueled their rapid expansion into a global cybersecurity leader.
Planned Utilization of Funding
Menlo Security is likely to allocate the new funding across several strategic initiatives. A significant portion will probably be dedicated to enhancing their core technology, developing new features, and improving the overall user experience. Further investments will likely focus on expanding their sales and marketing capabilities, reaching new customer segments, and building stronger brand recognition. Finally, a portion of the funds will probably be allocated to recruiting top talent, expanding their engineering and sales teams, and ensuring they have the best minds in the industry working for them.
The precise allocation will depend on Menlo Security’s strategic priorities and market opportunities, but a diversified approach across R&D, sales and marketing, and talent acquisition is expected.
Market Analysis & Competition
Menlo Security operates in a fiercely competitive cybersecurity landscape, facing established players and emerging startups alike. Understanding their competitive positioning is crucial to assessing their long-term viability and the impact of their recent funding round. This analysis will examine Menlo Security’s key competitors, compare their strengths and weaknesses, and conduct a SWOT analysis to highlight opportunities and threats in the context of their newfound capital.Menlo Security’s main competitors are a diverse group, each with its own approach to cybersecurity.
These competitors often overlap in their target market, creating a highly dynamic and competitive environment. A nuanced understanding of this competitive landscape is essential for evaluating Menlo Security’s prospects.
Menlo Security’s Competitors
Menlo Security competes with several major players in the secure access service edge (SASE) and cloud security markets. Key competitors include Zscaler, Netskope, and McAfee (now part of Intel Security), each offering a range of security solutions that overlap with Menlo Security’s offerings. Smaller, more niche competitors also exist, focusing on specific aspects of security like isolation or browser security.
These competitors often leverage different technologies and approaches, leading to varied strengths and weaknesses.
Comparative Analysis of Strengths and Weaknesses
A direct comparison requires careful consideration of several factors. For example, Zscaler boasts a large customer base and extensive global infrastructure, giving them a significant market advantage. However, Menlo Security’s isolation-based approach might offer a more robust solution against sophisticated threats, a key strength in a landscape increasingly plagued by advanced persistent threats (APTs). Netskope excels in cloud security, providing strong visibility and control over cloud applications.
McAfee leverages its long-standing reputation and broad portfolio of security solutions. Menlo Security’s relative advantage lies in its innovative approach to isolation and its potential for stronger protection against zero-day exploits, although its market share might currently be smaller than its competitors. A detailed feature-by-feature comparison would be necessary to provide a truly comprehensive analysis.
SWOT Analysis of Menlo Security (Post-Funding)
| Strengths | Weaknesses | Opportunities | Threats |
|---|---|---|---|
| Innovative isolation technology offering superior protection against advanced threats | Relatively smaller market share compared to established competitors | Expansion into new markets and customer segments leveraging the recent funding | Increased competition from established players and new entrants in the SASE market |
| Strong potential for growth in the cloud security market | Potential challenges in scaling operations to meet increasing demand | Strategic partnerships and acquisitions to expand product offerings and market reach | Economic downturn potentially impacting customer spending on cybersecurity |
| Recent funding provides resources for expansion and innovation | Dependence on a relatively niche technology that might not be universally adopted | Development of new features and functionalities to enhance product competitiveness | Rapid technological advancements requiring continuous innovation to stay ahead of the curve |
Future Implications and Potential
Menlo Security’s recent influx of funding signifies more than just a financial boost; it represents a significant shift in the cybersecurity landscape and a powerful statement about the growing demand for innovative, cloud-based security solutions. This investment fuels not only Menlo’s own growth but also accelerates the broader adoption of its unique approach to security, potentially reshaping how organizations protect themselves against increasingly sophisticated cyber threats.The injection of capital will undoubtedly propel Menlo Security’s trajectory in several key areas.
This funding allows for accelerated product development, expansion into new markets, and the strengthening of its already robust team. The impact will be felt across various sectors, influencing how businesses approach digital transformation and security posture in the cloud era.
Impact on the Broader Cybersecurity Landscape
Menlo Security’s technology, focusing on isolating threats within a secure browser environment, offers a compelling alternative to traditional security methods. The success of this funding round indicates a growing recognition of the limitations of perimeter-based security and the need for a more proactive, isolation-based approach. This could trigger a wave of similar investments in companies developing innovative security solutions centered around isolation and zero trust architectures.
We might see a shift away from relying solely on antivirus and firewalls towards more comprehensive and preventative strategies, mirroring the success of cloud-based services in other tech sectors. For example, the adoption of cloud-based storage solutions has drastically changed how individuals and businesses manage data, and a similar paradigm shift could occur in cybersecurity with Menlo’s technology at the forefront.
Future Product Innovations from Menlo Security
With increased resources, Menlo Security is likely to accelerate development in several areas. We can anticipate enhancements to their existing browser isolation platform, including improved performance, broader compatibility with various applications, and potentially AI-powered threat detection capabilities. Further integration with existing security infrastructure, such as SIEM (Security Information and Event Management) systems, is also highly probable. This could lead to more streamlined workflows and a more unified security posture for organizations.
Menlo Security’s massive funding round got me thinking about the broader cybersecurity landscape. It’s exciting to see such investment in innovative solutions, especially considering the growing need for robust cloud security. This is where companies like Bitglass come in, and their focus on Cloud Security Posture Management (CSPM) is crucial; check out this insightful article on bitglass and the rise of cloud security posture management to understand why.
Ultimately, Menlo’s success highlights the increasing importance of strong security in a cloud-first world.
One can envision the development of specialized solutions tailored to specific industries or threat vectors, addressing the unique challenges faced by different sectors such as finance or healthcare. Think of a specialized solution focusing on the unique threats faced by financial institutions handling sensitive customer data, or a healthcare-specific solution designed to protect patient information.
Long-Term Vision and Strategic Goals of Menlo Security
Menlo Security’s long-term vision likely centers on establishing itself as a leader in the cloud security market. This involves expanding its customer base, both geographically and across various industry verticals. Strategic goals will likely include solidifying its position as a key player in the zero trust security movement and continuing to innovate its core technology to stay ahead of the ever-evolving threat landscape.
A major strategic objective will likely be to build stronger partnerships with other technology providers to create a more comprehensive and integrated security ecosystem. This would create a broader market reach and increased synergy in the security solutions offered to clients. This is analogous to how major cloud providers collaborate with other software companies to offer integrated solutions on their platforms.
Potential Milestones for Menlo Security
The following timeline illustrates potential milestones for Menlo Security, based on the successful funding round and current market trends. These are estimations and are subject to market conditions and internal strategic decisions.
| Year | Milestone | Description |
|---|---|---|
| 2024 | Significant Product Enhancement | Release of major platform updates with improved performance and AI-powered features. |
| 2025 | Expansion into New Markets | Entry into new geographical regions and expansion into new industry verticals. |
| 2026 | Strategic Partnerships | Formation of key partnerships with other security providers to enhance product offerings. |
| 2027 | Potential IPO or Acquisition | Based on market performance and strategic goals, an IPO or acquisition could be considered. |
Illustrative Example of Menlo Security’s Technology: Cybersecurity Startup Menlo Security Receives Millions In Funding

Let’s imagine Sarah, a marketing manager at a mid-sized company, receives a seemingly innocuous email appearing to be from her bank. This email urges her to update her account details immediately by clicking a link. This is a classic phishing attack, designed to steal her banking credentials. However, Sarah’s company uses Menlo Security’s isolation technology.This scenario demonstrates how Menlo Security’s solution protects against sophisticated phishing attacks.
Instead of opening the email directly on her computer, Menlo Security intercepts the email link. The link doesn’t open a webpage directly on Sarah’s machine; instead, it’s opened within a secure, isolated container in the cloud. This container acts as a virtual machine, completely separate from Sarah’s computer’s operating system and local files.
Phishing Email Interception and Isolation
The email link, upon being clicked, is routed through Menlo Security’s cloud-based isolation platform. This platform analyzes the link and the website it points to for malicious content. Think of it like this: Sarah’s computer sends a request to view the website, but instead of directly receiving the website’s content, it receives a secure, rendered version of the website from the isolated container.
This rendered version contains only the visual elements and does not execute any code directly on Sarah’s machine.
Malicious Code Containment and User Protection
Let’s say the website contains malicious JavaScript designed to steal Sarah’s login credentials. Because the website is running inside the isolated container, this malicious code cannot reach Sarah’s computer. It’s trapped within the virtual machine, unable to access her files, applications, or operating system. Sarah sees the webpage as she normally would, but the underlying code is harmlessly contained.
Outcome and Key Features Highlighted, Cybersecurity startup menlo security receives millions in funding
Sarah interacts with the fake banking website within the isolated container. She notices some inconsistencies and becomes suspicious, choosing not to enter her credentials. The entire interaction is contained within the secure environment, preventing any data breach. Even if she had entered her details, they would have remained within the isolated container, never reaching the attackers. This scenario highlights Menlo Security’s key features: isolation, preventing malicious code execution, and secure rendering of web content.
The visual representation would show Sarah’s computer on one side, a secure cloud-based container in the middle, and the potentially malicious website rendered safely inside the container, with a clear barrier preventing any access to Sarah’s computer’s system. The arrow of the email click goes into the container and not directly to the computer.
Final Summary
Menlo Security’s massive funding round isn’t just a win for the company; it’s a win for the entire cybersecurity industry. This injection of capital signals a growing recognition of the need for innovative, proactive security solutions. The company’s unique approach to tackling persistent threats promises a more secure digital future, and I, for one, am excited to see what they accomplish next.
With this significant boost, Menlo Security is poised to become a major player, pushing the boundaries of what’s possible in online protection. Keep your eyes on this one – it’s going to be big.
Clarifying Questions
What specific cybersecurity threats does Menlo Security address?
Menlo Security focuses on advanced threats like phishing attacks, malware, and ransomware by isolating web traffic and preventing malicious code from executing on user devices.
Who are Menlo Security’s main investors?
That information would need to be sourced from official press releases or Menlo Security’s website.
What is Menlo Security’s pricing model compared to competitors like CrowdStrike or SentinelOne?
A detailed price comparison requires researching their individual pricing structures and comparing features. This information is often found on their respective websites or through industry analysts’ reports.
What are the potential risks associated with Menlo Security’s technology?
Like any security solution, there are potential risks. A thorough assessment would require a deeper technical analysis. Potential concerns could include potential points of failure within their isolation technology or the possibility of unforeseen vulnerabilities.