Cybersecurity vs Computer Science A Deep Dive
Cybersecurity vs computer science: At first glance, these two fields might seem intertwined, even interchangeable. But a closer look reveals distinct yet overlapping paths, each demanding a unique skillset and offering a diverse range of career opportunities. This post explores the key differences and fascinating connections between these crucial disciplines, revealing how they complement and enhance each other in the ever-evolving digital landscape.
Get ready to unravel the mysteries of protecting our digital world!
We’ll dissect the core principles of each field, comparing their educational routes and career trajectories. We’ll delve into the areas where they intersect, highlighting the crucial role computer science plays in building the very tools used to defend against cyber threats. From network security to ethical hacking, we’ll uncover the specific cybersecurity specializations that build upon a strong foundation in computer science.
Finally, we’ll explore the ethical dimensions and societal impacts of both fields, considering the future trends and emerging technologies that will shape their evolution.
Defining Cybersecurity and Computer Science
Computer science and cybersecurity are closely related yet distinct fields. While both deal with computers and information, their focuses and approaches differ significantly. Understanding these differences is crucial for anyone considering a career in either field.Computer science is a broad discipline encompassing the theoretical foundations of information and computation and their application in computer systems. Cybersecurity, on the other hand, is a specialized area focusing on protecting computer systems and networks from unauthorized access, use, disclosure, disruption, modification, or destruction.
Think of computer science as the blueprint for building a house, while cybersecurity is the security system protecting that house from intruders.
Core Principles Comparison
Computer science’s core principles revolve around algorithms, data structures, programming languages, and software engineering. It’s concerned with designing, developing, and implementing efficient and effective computational solutions to various problems. Cybersecurity, conversely, centers on risk management, threat modeling, vulnerability analysis, and incident response. Its primary goal is to safeguard digital assets and maintain data integrity and confidentiality. Both fields utilize mathematical and logical reasoning, but their applications differ significantly.
Computer science might use cryptography for efficient data compression, whereas cybersecurity leverages the same cryptography to secure sensitive data.
Educational Pathways and Career Trajectories
The educational pathways for computer science and cybersecurity diverge after foundational courses in mathematics and programming. Computer science curricula delve deeper into theoretical computer science, artificial intelligence, database management, and software engineering. Cybersecurity programs, while often building upon computer science fundamentals, emphasize specialized topics like network security, cryptography, ethical hacking, digital forensics, and security auditing. Consequently, career trajectories differ.
Computer scientists may find roles in software development, data science, or artificial intelligence, while cybersecurity professionals typically pursue careers as security analysts, penetration testers, security architects, or incident responders. For example, a computer scientist might design a new algorithm for image recognition, whereas a cybersecurity professional would analyze the security vulnerabilities of that same algorithm to prevent its misuse.
Essential Skills
The essential skills for each field also differ significantly. Computer scientists need strong programming skills across multiple languages, a deep understanding of data structures and algorithms, and proficiency in software development methodologies. They often need strong problem-solving skills and the ability to think abstractly. Cybersecurity professionals, in addition to strong programming skills, require expertise in network security protocols, vulnerability assessment tools, incident response procedures, and a thorough understanding of various attack vectors and threat actors.
They also need strong analytical and investigative skills, as well as a deep understanding of relevant security standards and regulations. A computer scientist might excel at developing a new encryption algorithm, while a cybersecurity professional would focus on implementing and maintaining that algorithm securely within a system.
Overlapping Areas of Expertise
Cybersecurity and computer science are deeply intertwined disciplines, sharing a significant amount of overlapping expertise. A strong foundation in computer science is crucial for anyone pursuing a career in cybersecurity, and conversely, many advancements in computer science directly benefit the field of cybersecurity. The relationship is symbiotic, with each field constantly informing and enhancing the other.Computer science provides the fundamental building blocks upon which many cybersecurity tools and techniques are built.
Without a deep understanding of computer architecture, networking protocols, operating systems, and programming languages, developing effective cybersecurity solutions would be nearly impossible.
The Role of Computer Science in Cybersecurity Tool Development
Computer science plays a vital role in the creation of various cybersecurity tools and techniques. For example, the development of intrusion detection systems (IDS) relies heavily on algorithms and data structures from computer science. These systems analyze network traffic and system logs, searching for patterns indicative of malicious activity. The efficiency and accuracy of these systems depend directly on the sophistication of the algorithms employed, which are a direct product of computer science research and development.
Similarly, the creation of firewalls, antivirus software, and encryption algorithms all require expertise in areas like cryptography, network security, and data structures, all core components of computer science. The design and implementation of these tools demand a rigorous understanding of how computers and networks function at a fundamental level.
Computer Science Principles Underpinning Cybersecurity Practices
Many cybersecurity practices are directly rooted in core computer science principles. For instance, the concept of secure coding practices is fundamentally about applying computer science principles to minimize vulnerabilities in software. This includes understanding how memory management, input validation, and error handling can be implemented securely to prevent exploits. Furthermore, the principles of cryptography, a significant branch of computer science, are central to securing data in transit and at rest.
Techniques like public-key cryptography and symmetric-key encryption rely on complex mathematical algorithms and theoretical foundations from computer science to guarantee data confidentiality and integrity. Network security, another critical area of cybersecurity, depends on a thorough understanding of networking protocols, routing algorithms, and network topologies – all areas of expertise within computer science. Understanding these principles is vital for designing secure networks and mitigating risks.
Cybersecurity Specializations within Computer Science
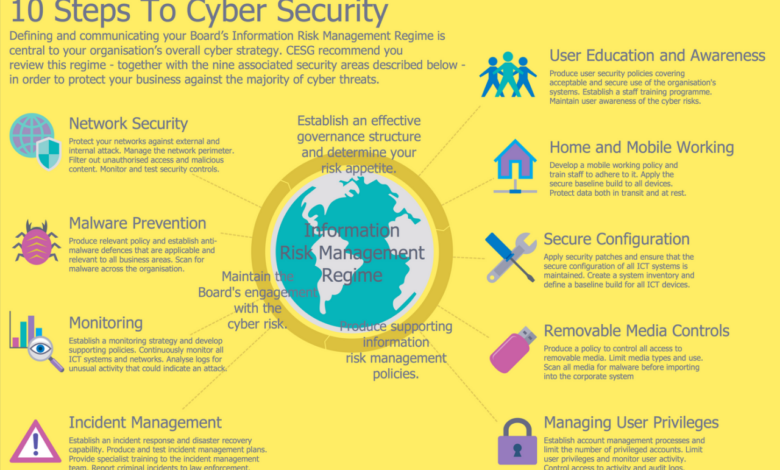
Cybersecurity is a vast field, and its intricacies are deeply intertwined with the foundational principles of computer science. A strong understanding of computer science provides the bedrock for expertise in various cybersecurity specializations. This section delves into some key areas, highlighting their core computer science components and potential career paths.
Cybersecurity Specializations and Their Relationship to Computer Science
The following table Artikels several popular cybersecurity specializations, illustrating their connection to core computer science concepts and the skills they require. These specializations represent just a fraction of the diverse opportunities available within cybersecurity, demonstrating the breadth of the field and its reliance on a robust computer science foundation.
| Specialization | Core Computer Science Concepts | Key Skills | Career Paths |
|---|---|---|---|
| Network Security | Networking protocols (TCP/IP, UDP), network architecture, operating systems, data structures and algorithms | Network monitoring, intrusion detection, firewall management, vulnerability assessment, incident response | Network Security Engineer, Security Analyst, Penetration Tester, Cybersecurity Architect |
| Cryptography | Number theory, algebra, discrete mathematics, algorithm design and analysis, data structures | Encryption/decryption techniques, key management, digital signatures, cryptographic protocol design, security auditing | Cryptographer, Security Architect, Blockchain Developer, Cryptographic Engineer |
| Ethical Hacking | Operating systems, networking, programming, databases, web application development | Vulnerability scanning, penetration testing, social engineering, malware analysis, incident response | Penetration Tester, Security Consultant, Security Analyst, Red Teamer |
| Cloud Security | Cloud computing architectures (IaaS, PaaS, SaaS), distributed systems, virtualization, databases | Cloud security architecture design, access control management, data encryption, security auditing, incident response in cloud environments | Cloud Security Engineer, Cloud Security Architect, DevOps Engineer (with security focus) |
Progression of a Computer Science Student Specializing in Cybersecurity
This flowchart visually represents a typical progression for a computer science student focusing on cybersecurity. The path isn’t linear; students might take electives in different orders or pursue internships early on. The key is building a strong foundation in computer science before diving deeper into cybersecurity specializations. The flowchart would start with a “Computer Science Fundamentals” box, branching into core courses like data structures, algorithms, and operating systems. From there, a path leads to “Cybersecurity Core Courses” such as network security, cryptography, and ethical hacking. Concurrent with these, students might pursue “Programming and Scripting” skills (Python, C++, etc.). A further branch would lead to “Specialization Electives,” where students could choose to focus on areas like cloud security, digital forensics, or security auditing. Finally, the flowchart culminates in “Internship/Job Search” and “Advanced Studies (Masters/PhD)”. Feedback loops could be included to show iterative learning and skill development. For example, practical experience from internships could inform elective choices, and further studies could lead to specialization in niche areas within cybersecurity.
Computer Science Fundamentals for Cybersecurity Professionals
A strong foundation in computer science is paramount for a successful cybersecurity career. While cybersecurity focuses on protecting systems, understanding how those systems work at a fundamental level is essential for effective defense. This requires a deep understanding of the underlying principles that govern software, hardware, and networks. This section will explore key computer science concepts crucial for cybersecurity professionals.
Essential Computer Science Courses for Cybersecurity
A solid cybersecurity education benefits greatly from a curriculum that includes core computer science principles. These courses provide the theoretical and practical knowledge needed to understand and counter evolving threats. Selecting courses that cover both theoretical concepts and practical applications is highly beneficial.
- Data Structures and Algorithms: Understanding how data is organized and manipulated is crucial for analyzing network traffic, identifying malicious code, and optimizing security tools.
- Operating Systems: In-depth knowledge of operating system internals, including processes, memory management, and file systems, is vital for understanding vulnerabilities and developing effective security measures.
- Computer Networks: A comprehensive understanding of network protocols, architectures, and security mechanisms is fundamental for network security professionals. This includes topics such as TCP/IP, routing, and firewalls.
- Cryptography: This course covers the principles and techniques of secure communication, including encryption, decryption, and digital signatures. It’s essential for understanding and implementing secure systems.
- Database Systems: Security professionals often need to work with databases, so understanding database design, security, and vulnerabilities is important for protecting sensitive data.
- Software Engineering: Understanding software development principles helps in analyzing code for vulnerabilities and building secure software applications.
- Discrete Mathematics: This provides the mathematical foundation for many cybersecurity concepts, including cryptography and algorithm analysis.
The Importance of Data Structures and Algorithms in Cybersecurity
Data structures and algorithms are the backbone of efficient and effective cybersecurity solutions. Understanding how data is organized and processed allows security professionals to develop optimized tools for tasks such as intrusion detection, malware analysis, and vulnerability assessment. For example, efficient search algorithms are crucial for quickly identifying malicious patterns in network traffic, while graph algorithms are useful for analyzing network topologies and identifying vulnerabilities.
The choice of data structure directly impacts the performance and scalability of security tools. Using the wrong data structure can lead to slow response times and a decreased ability to effectively handle large datasets. For instance, using a linear search on a large dataset would be significantly slower than using a hash table or a binary search tree.
Operating Systems Knowledge: A Crucial Security Asset, Cybersecurity vs computer science
Operating systems are the foundation of any computer system, and a deep understanding of their inner workings is critical for cybersecurity professionals. This knowledge enables security experts to identify and mitigate vulnerabilities, analyze malware behavior, and develop effective security solutions. For example, understanding process management allows a security professional to detect and respond to malicious processes. Knowledge of file system structures is essential for analyzing malware and recovering from attacks.
Furthermore, expertise in memory management is vital for identifying and mitigating memory-related vulnerabilities, such as buffer overflows. The ability to analyze system logs and identify suspicious activity is also heavily reliant on a solid understanding of the operating system’s logging mechanisms. Without this knowledge, a security professional would be significantly hampered in their ability to effectively protect systems and respond to security incidents.
Ethical Considerations and Societal Impact
The digital age, while offering unparalleled opportunities, has also introduced significant ethical challenges, particularly in the realms of cybersecurity and computer science. The interconnected nature of our world means that cybersecurity breaches aren’t just technical failures; they have profound societal implications, impacting individuals, businesses, and governments alike. Understanding these ethical dimensions is crucial for responsible innovation and the development of secure systems.The increasing reliance on technology across all aspects of life makes the ethical considerations of cybersecurity paramount.
Data breaches can lead to identity theft, financial losses, reputational damage, and even physical harm. Furthermore, the misuse of technology for malicious purposes, such as cyber warfare or the spread of disinformation, poses significant threats to societal stability and democratic processes. The development and deployment of AI-powered cybersecurity tools also raises complex ethical questions around bias, transparency, and accountability.
Cybersecurity Professionals’ Role in Mitigating Risks and Protecting Data Privacy
Cybersecurity professionals play a vital role in minimizing these risks. Their responsibilities extend beyond technical expertise to include a strong ethical compass. They are tasked with designing and implementing secure systems, responding to incidents effectively, and adhering to relevant regulations and best practices. This involves making difficult choices, such as balancing security measures with user convenience, and prioritizing data privacy while ensuring operational efficiency.
A key aspect of their role is educating users about cybersecurity threats and best practices, empowering individuals to protect themselves and contribute to a more secure digital environment. For example, a cybersecurity professional might design a system that prioritizes user privacy by implementing strong encryption and data anonymization techniques, even if it means slightly slower processing speeds. They might also develop security awareness training programs to help employees recognize and avoid phishing scams.
Ethical Responsibilities: Computer Scientists vs. Cybersecurity Specialists
While both computer scientists and cybersecurity specialists share a commitment to responsible technology development, their ethical responsibilities differ in focus and scope. Computer scientists often focus on broader issues of technological innovation and its impact on society, including potential biases embedded in algorithms or the societal implications of emerging technologies. Cybersecurity specialists, on the other hand, have a more immediate and focused responsibility – protecting systems and data from malicious actors.
This often requires them to grapple with ethical dilemmas related to surveillance, data retention, and the potential for misuse of their expertise.For instance, a computer scientist might be involved in developing an AI system for facial recognition, raising ethical concerns about privacy and potential bias in the algorithm. A cybersecurity specialist, however, might be tasked with securing that same system, focusing on protecting it from unauthorized access or manipulation.
Both roles require careful consideration of ethical implications, but their specific concerns and priorities often differ significantly. The overlap lies in the shared responsibility for ensuring that technology is developed and used responsibly, contributing to a safe and equitable digital society.
Future Trends and Emerging Technologies
The convergence of computer science and cybersecurity is rapidly evolving, driven by the relentless advancement of emerging technologies. Artificial intelligence (AI), the Internet of Things (IoT), and quantum computing are not just shaping the future of computing; they’re fundamentally reshaping the cybersecurity landscape, creating both unprecedented challenges and exciting opportunities. Understanding these trends is crucial for anyone navigating this dynamic field.The impact of these technologies is multifaceted.
AI, for instance, is being leveraged to automate security tasks, improving threat detection and response times. However, the same technology can also be weaponized by malicious actors to create more sophisticated and evasive attacks. Similarly, the proliferation of IoT devices, while offering unparalleled connectivity and convenience, exponentially expands the attack surface, creating vulnerabilities that need to be addressed proactively.
Quantum computing, while still in its nascent stages, poses a significant long-term threat to current cryptographic methods, necessitating the development of quantum-resistant algorithms.
AI’s Influence on Cybersecurity and Computer Science
AI is revolutionizing both fields. In computer science, AI is driving advancements in areas like natural language processing, computer vision, and robotics. In cybersecurity, AI powers advanced threat detection systems, anomaly detection algorithms, and automated incident response capabilities. For example, AI-powered security information and event management (SIEM) systems can analyze massive datasets of security logs to identify subtle patterns indicative of malicious activity far faster than human analysts could.
However, AI also presents challenges. Adversaries are using AI to create more sophisticated phishing attacks, develop advanced malware, and automate large-scale cyberattacks. The development of robust defenses against AI-powered attacks is a critical area of research and development.
The IoT and its Security Implications
The sheer number of connected devices in the IoT presents a massive challenge for cybersecurity. Each device, from smart home appliances to industrial control systems, represents a potential entry point for attackers. The diversity of operating systems, protocols, and security implementations across these devices makes securing the IoT a complex undertaking. However, the IoT also presents opportunities for innovation.
The development of secure IoT architectures, including robust authentication and encryption protocols, is essential to mitigating the risks associated with this technology. The potential for AI-powered security solutions to manage and monitor the vast number of IoT devices is a key area of research.
Challenges and Opportunities in Quantum Computing
Quantum computing’s potential to break current encryption methods presents a significant long-term challenge to cybersecurity. The development of post-quantum cryptography (PQC) is a critical area of research, focusing on algorithms that are resistant to attacks from quantum computers. This requires significant advancements in computer science, particularly in areas like number theory and cryptography. The opportunities lie in developing and implementing these new algorithms, ensuring the security of critical infrastructure and data in the quantum era.
The transition to PQC will be a gradual process, requiring careful planning and coordination across the industry.
Future Career Paths at the Intersection of Computer Science and Cybersecurity
The intersection of computer science and cybersecurity offers a wealth of career opportunities. The demand for skilled professionals in this area is expected to continue to grow exponentially.
- AI Security Engineer: Developing and deploying AI-powered security solutions.
- IoT Security Architect: Designing and implementing secure architectures for IoT devices and networks.
- Quantum Cryptographer: Researching and developing quantum-resistant cryptographic algorithms.
- Cybersecurity Analyst specializing in AI/ML: Focusing on detecting and responding to AI-powered attacks.
- Cloud Security Engineer specializing in serverless technologies: Securing cloud-based infrastructure and applications, particularly focusing on serverless architectures.
- Blockchain Security Specialist: Protecting blockchain networks and applications from various threats.
These are just a few examples, and the field is constantly evolving, creating new and exciting opportunities for skilled professionals.
Case Studies
Real-world cybersecurity incidents and successful defense strategies offer invaluable lessons. Analyzing these events reveals the interplay between computer science principles and the ever-evolving landscape of cyber threats. Understanding both the failures and successes illuminates best practices and highlights areas needing further improvement.
The Target Data Breach of 2013
The 2013 Target data breach is a prime example of a large-scale cyberattack exploiting technical weaknesses. Hackers gained access to Target’s network through a third-party vendor, accessing credentials and subsequently deploying malware. This malware stole customer data, including credit card information and personal details, impacting millions of individuals. The technical weakness exploited was a lack of robust security measures at the vendor level, coupled with insufficient network segmentation within Target’s infrastructure.
The attackers leveraged known vulnerabilities in outdated software to gain initial access and then moved laterally within the network. The resolution involved extensive forensic analysis to determine the extent of the breach, notification of affected customers, and significant investment in improving security infrastructure, including enhanced network segmentation, improved vulnerability management, and stronger access control measures. This incident underscores the importance of secure supply chain management and the need for a proactive approach to vulnerability identification and mitigation.
The Successful Defense Strategy of Estonia in 2007
Estonia’s successful defense against a large-scale DDoS attack in 2007 showcased the power of a well-planned and executed cybersecurity strategy. Facing a coordinated attack targeting government websites and infrastructure, Estonia leveraged its robust network infrastructure and international collaborations. Computer science principles, including distributed systems and network security protocols, played a crucial role. The defense involved mitigating the impact of the DDoS attacks through traffic filtering, rate limiting, and the use of distributed denial-of-service mitigation techniques.
International cooperation allowed Estonia to leverage resources and expertise from other countries to effectively combat the attack. This strategy highlighted the importance of proactive planning, robust infrastructure, international collaboration, and the ability to adapt to evolving attack vectors. The incident demonstrated that a well-designed and executed cybersecurity strategy, underpinned by strong computer science fundamentals, can effectively withstand sophisticated cyberattacks.
Final Wrap-Up
So, cybersecurity vs computer science? The answer isn’t a simple either/or. Instead, we see a powerful synergy. Computer science provides the foundational building blocks, while cybersecurity applies that knowledge to protect our digital lives. Understanding this relationship is crucial, whether you’re a budding student choosing a career path or a seasoned professional navigating the complexities of the digital age.
The future of both fields is bright, intertwined with emerging technologies and a constant need for innovation and ethical considerations. The journey to securing our digital future is a collaborative one, demanding the expertise of both computer scientists and cybersecurity specialists.
Answers to Common Questions: Cybersecurity Vs Computer Science
What’s the average salary for a cybersecurity professional vs. a computer scientist?
Salaries vary widely based on experience, location, and specialization. Generally, both fields offer competitive salaries, with cybersecurity often commanding slightly higher compensation due to the high demand for skilled professionals.
Is a computer science degree necessary for a cybersecurity career?
While not strictly mandatory, a computer science background (or a related field like information technology) is highly beneficial and often preferred for many cybersecurity roles. A strong understanding of computer systems and networks is essential.
Can I switch from computer science to cybersecurity?
Absolutely! Many computer scientists transition into cybersecurity roles. Your existing programming, networking, and problem-solving skills provide a strong foundation. You’ll likely need to supplement your knowledge with cybersecurity-specific training and certifications.
What are some entry-level cybersecurity jobs for someone with a computer science degree?
Entry-level positions might include Security Analyst, Systems Administrator, Penetration Tester (with further training), or Security Engineer. Internships are also a great way to gain experience.