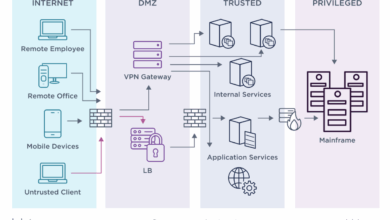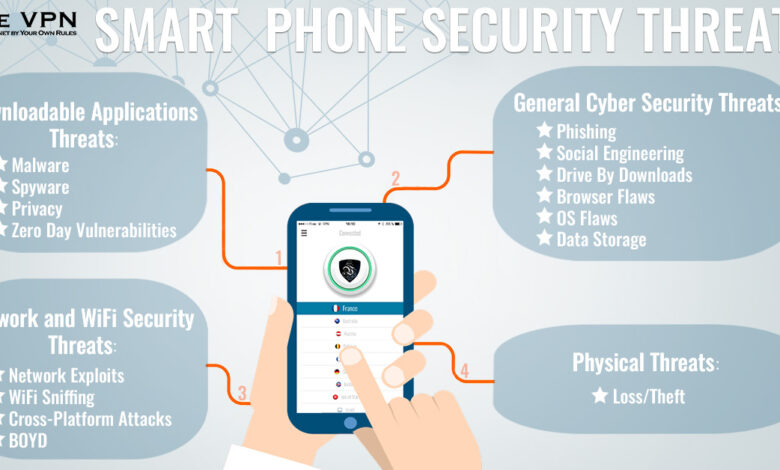
Cybersecurity Vulnerabilities in Millions of Smart Devices
Cybersecurity vulnerabilities in millions of smart connected devices are a growing concern. Our increasingly interconnected world, filled with smart homes, wearables, and even medical devices, creates a vast landscape ripe for exploitation. From simple password breaches to sophisticated malware attacks, the potential for damage is immense, affecting everything from personal privacy to critical infrastructure. This post delves into the heart of this issue, exploring the vulnerabilities, the risks, and what we can do to mitigate them.
We’ll examine common types of vulnerable devices, explore the methods hackers use to exploit weaknesses, and analyze the real-world consequences of successful attacks. We’ll also discuss practical steps individuals and organizations can take to improve their security posture, including best practices for securing devices, the importance of software updates, and the role of emerging technologies in both enhancing and compromising our safety.
Get ready to dive into the fascinating – and sometimes frightening – world of smart device security.
Types of Smart Connected Devices Vulnerable to Cybersecurity Threats: Cybersecurity Vulnerabilities In Millions Of Smart Connected Devices
The increasing interconnectedness of our world through smart devices presents a significant challenge in terms of cybersecurity. Millions of these devices, lacking robust security features, are vulnerable to a wide range of attacks, potentially compromising personal data, disrupting services, and even causing physical harm. Understanding the types of devices most at risk, their common vulnerabilities, and effective mitigation strategies is crucial for building a more secure digital environment.
Commonly Targeted Smart Devices and Their Vulnerabilities
Smart connected devices encompass a broad spectrum of technologies, each presenting its own unique security challenges. The following table Artikels five common types of devices frequently targeted by cyberattacks, highlighting their vulnerabilities and potential attack vectors. Effective mitigation strategies are also discussed.
| Device Type | Common Vulnerabilities | Attack Vectors | Mitigation Strategies |
|---|---|---|---|
| Smart TVs | Weak default passwords, lack of software updates, insecure Wi-Fi configurations. | Malware injection via malicious apps, network attacks exploiting vulnerabilities, phishing attacks targeting user credentials. | Change default passwords, enable automatic software updates, use strong Wi-Fi passwords, install reputable apps only. |
| Smart Home Assistants | Vulnerable APIs, insecure data storage, lack of encryption. | Man-in-the-middle attacks intercepting commands, unauthorized access to user data, exploitation of vulnerabilities in the device’s software. | Enable two-factor authentication, regularly update firmware, use strong passwords, limit device permissions. |
| Smart Security Systems | Unpatched vulnerabilities, weak authentication mechanisms, insecure cloud connectivity. | Brute-force attacks, unauthorized access via default credentials, denial-of-service attacks. | Use strong and unique passwords, regularly update firmware and software, enable multi-factor authentication, monitor network traffic. |
| Smart Baby Monitors | Lack of encryption, easily guessable default passwords, insecure network configurations. | Unauthorized access to live video feed, eavesdropping, denial-of-service attacks. | Change default passwords, use strong Wi-Fi passwords, enable encryption, regularly update firmware. |
| Wearable Fitness Trackers | Poor data encryption, vulnerabilities in mobile apps, insecure Bluetooth connections. | Data breaches exposing personal health information, Bluetooth hacking, malicious app installations. | Use strong passwords, enable two-factor authentication, keep apps updated, connect only to trusted Bluetooth devices. |
Unique Security Challenges of Internet of Medical Things (IoMT) Devices
IoMT devices, while offering significant benefits in healthcare, present unique security challenges compared to other smart devices. The potential consequences of a security breach in an IoMT device are far more severe, potentially impacting patient safety and privacy. For example, a compromised insulin pump could deliver incorrect dosages, while a compromised medical imaging system could lead to inaccurate diagnoses.
The sensitive nature of the data handled by these devices, coupled with the often limited security expertise within healthcare organizations, creates a particularly vulnerable landscape. The lack of standardization in security protocols and the reliance on legacy systems further exacerbates the problem. Robust security measures, including strong authentication, data encryption, and regular software updates, are crucial to mitigating these risks.
Vulnerability Exploitation Methods
Exploiting vulnerabilities in smart connected devices often involves a combination of technical skills and understanding of the device’s weaknesses. Attackers leverage various methods to gain unauthorized access, ranging from simple phishing scams to sophisticated malware infections. Understanding these methods is crucial for developing effective security measures.
Common Exploitation Methods
Three common methods used to exploit vulnerabilities in smart connected devices are phishing attacks, malware infections, and denial-of-service (DoS) attacks. Each method utilizes different techniques to compromise the device’s security and achieve the attacker’s goal, whether it’s data theft, system control, or disruption of service.
Phishing Attacks
Phishing attacks rely on social engineering to trick users into revealing sensitive information or installing malicious software. A common tactic involves sending seemingly legitimate emails or text messages that appear to be from a trusted source, such as a bank or service provider. These messages often contain links to fake websites that mimic the appearance of the legitimate site.
Once a user enters their credentials on the fake website, the attacker gains access to their account. Another approach involves attachments containing malware that is executed when opened. The effectiveness of a phishing attack depends heavily on the sophistication of the social engineering techniques used and the user’s level of security awareness. A well-crafted phishing email can easily bypass even cautious users, leading to successful exploitation.
Malware Infections
Malware infections involve the installation of malicious software onto the smart device. This can occur through various means, including drive-by downloads, infected attachments, or exploits of software vulnerabilities. Once installed, malware can perform various malicious activities, such as stealing data, controlling the device remotely, or creating a botnet for launching larger attacks. For instance, a smart thermostat might be infected with malware that allows an attacker to remotely control its temperature settings, potentially causing significant inconvenience or even physical damage.
The effectiveness of a malware infection hinges on the malware’s capabilities and the device’s security posture. A device with outdated firmware or weak security settings is much more susceptible to malware infections. The impact can range from minor data breaches to complete system compromise.
The sheer number of smart devices online means cybersecurity vulnerabilities are a massive, growing problem. Building secure applications is crucial, and that’s where exploring options like domino app dev the low code and pro code future becomes really important. Faster development cycles could help us patch those vulnerabilities quicker, ultimately protecting millions of devices from potential attacks.
Denial-of-Service Attacks
Denial-of-service (DoS) attacks aim to disrupt the availability of a service by overwhelming the target with traffic. In the context of smart connected devices, a DoS attack might target a network of devices, such as a network of smart home devices. The attacker floods the network with requests, preventing legitimate users from accessing the devices or services. This could be achieved by exploiting vulnerabilities in the devices’ firmware or by leveraging botnets of compromised devices.
The technical steps might involve identifying a vulnerability that allows for the amplification of attack traffic, such as a vulnerability in the device’s network protocol. The attacker then sends a series of crafted packets exploiting this vulnerability, resulting in a massive flood of traffic directed at the target network. The impact of a successful DoS attack on a network of smart home devices could be significant, rendering them unusable and disrupting essential services.
Phishing vs. Malware: A Comparison
Phishing attacks and malware infections are both effective methods for compromising smart devices, but they differ in their approach and impact. Phishing attacks rely on social engineering to trick users, while malware infections involve directly compromising the device’s software. Phishing is often a precursor to malware infection, where a successful phishing attack leads to the installation of malware. While phishing attacks might only lead to credential theft, malware infections can have far-reaching consequences, including data theft, remote control, and participation in botnets.
The effectiveness of each method depends on factors such as the user’s security awareness and the sophistication of the attack.
Hypothetical Denial-of-Service Attack Scenario
Imagine a scenario where an attacker launches a distributed denial-of-service (DDoS) attack against a neighborhood’s network of smart home devices. The attacker exploits a known vulnerability in the firmware of a specific smart lock model, which allows for the amplification of attack traffic. By sending a relatively small amount of crafted packets to a large number of these vulnerable smart locks, the attacker triggers a massive flood of traffic directed at the network infrastructure, overwhelming the router and causing a complete network outage.
This outage renders all smart home devices inaccessible, impacting security systems, lighting, thermostats, and other connected appliances. The consequences include disruption of daily life, potential security risks due to the unavailability of security systems, and financial losses due to repair costs and potential damage to appliances. The impact would be significant, highlighting the vulnerability of interconnected smart home ecosystems to coordinated attacks.
Impact of Vulnerabilities on Users and Infrastructure
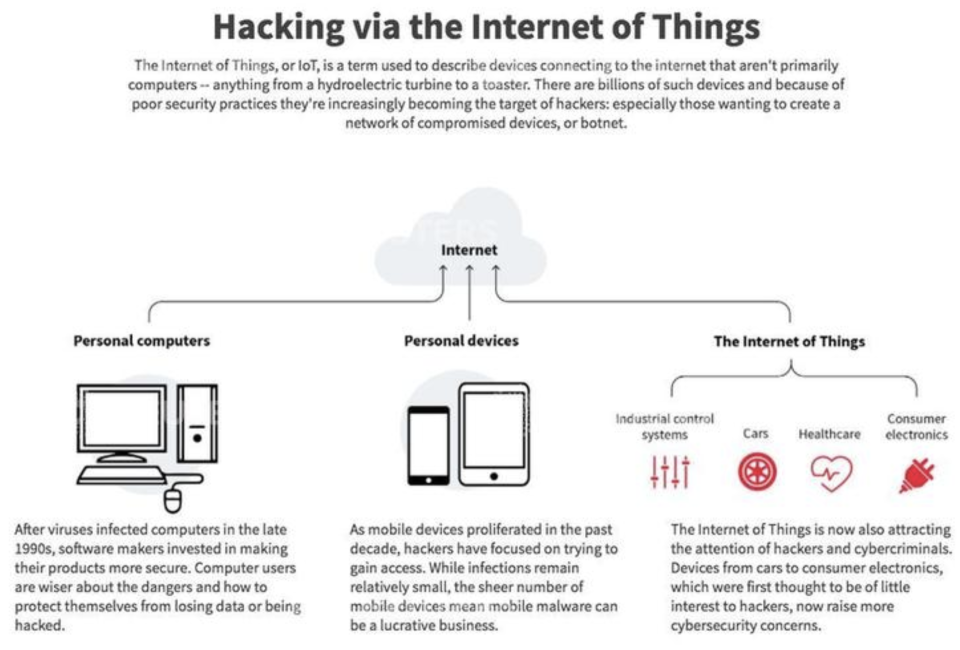
The proliferation of smart connected devices, while offering convenience and efficiency, has inadvertently created a vast attack surface for cybercriminals. The interconnected nature of these devices means that a vulnerability in one can trigger a cascade of failures across an entire system, impacting individuals, businesses, and critical infrastructure. Understanding the potential consequences is crucial for developing effective mitigation strategies.The impact of vulnerabilities in smart connected devices extends far beyond simple inconvenience.
Breaches can lead to significant financial losses, reputational damage, and even physical harm. Furthermore, the interconnectedness of these devices within smart cities and other critical infrastructure systems amplifies the potential for widespread disruption and chaos.
Real-World Examples of Large-Scale Cybersecurity Breaches
Several high-profile incidents highlight the devastating consequences of vulnerabilities in smart connected devices. The Mirai botnet, for example, leveraged vulnerabilities in poorly secured Internet of Things (IoT) devices like security cameras and routers to launch massive distributed denial-of-service (DDoS) attacks against major websites and online services in 2016. This resulted in widespread service outages, impacting millions of users and causing significant economic losses for affected businesses.
Another notable example is the 2015 attack on Ukraine’s power grid, where malicious actors exploited vulnerabilities in industrial control systems to disrupt power supply to hundreds of thousands of people. This demonstrates the potential for cyberattacks to directly impact critical infrastructure and cause significant physical disruption. Finally, the 2021 Colonial Pipeline ransomware attack, while not directly targeting smart devices, highlighted the vulnerability of critical infrastructure to cyberattacks.
The attack caused widespread fuel shortages and economic disruption across the southeastern United States. These incidents underscore the urgent need for improved security practices across all connected devices.
Potential Consequences of a Cyberattack on Smart City Infrastructure
A successful cyberattack on a smart city’s infrastructure could have far-reaching and devastating consequences across economic, social, and environmental domains.
With millions of smart devices constantly connecting to the cloud, cybersecurity vulnerabilities are a growing concern. The sheer volume makes traditional security methods struggle, which is why understanding solutions like cloud security posture management is crucial. For a deeper dive into effective strategies, check out this article on bitglass and the rise of cloud security posture management ; it really sheds light on how to better protect against threats targeting these vulnerable devices.
Ultimately, proactive management is key to mitigating the risks associated with this ever-expanding digital landscape.
- Economic Impacts: Disruption of essential services like transportation, energy, and water supply would lead to significant economic losses. Businesses would suffer from operational disruptions, decreased productivity, and potential financial losses. The cost of remediation and recovery efforts would also be substantial.
- Social Impacts: Disruption of emergency services, communication networks, and healthcare systems could put lives at risk. Loss of public trust in smart city technologies and governance could also result from a major breach. Widespread panic and social unrest are also possible outcomes.
- Environmental Impacts: Compromised environmental monitoring systems could lead to delayed responses to environmental emergencies. Disruptions to energy grids and waste management systems could also have negative environmental consequences.
Cascading Failures in Interconnected Smart Devices, Cybersecurity vulnerabilities in millions of smart connected devices
The interconnected nature of smart devices creates a significant risk of cascading failures. A single compromised device can act as a gateway for attackers to access and compromise other devices within the network. For example, consider a scenario where a smart home security system is compromised due to a known vulnerability.
- An attacker exploits a vulnerability in the smart home security system, gaining access to the network.
- The attacker uses this access to compromise the smart thermostat, adjusting the temperature to extreme levels, potentially causing damage to the home or significant energy waste.
- The compromised thermostat then provides access to the smart lighting system, allowing the attacker to manipulate lighting schedules, potentially disrupting daily routines or creating security risks.
- From the lighting system, the attacker moves to the smart appliances, such as refrigerators or washing machines, potentially causing damage or disrupting their functionality.
- Finally, the attacker might use the compromised smart home network to launch attacks against other devices on the local network or even beyond, creating a far wider disruption.
This illustrates how a single point of failure can quickly escalate into a widespread disruption, highlighting the importance of robust security measures throughout the entire network.
Mitigation and Prevention Strategies

Securing the vast landscape of smart connected devices requires a multi-faceted approach encompassing both proactive measures and reactive responses. The sheer number of devices, their diverse functionalities, and the often-fragmented nature of their security implementations present significant challenges. However, by focusing on robust security practices at the hardware, software, and network levels, we can significantly reduce the risk of exploitation.
Effective mitigation strategies hinge on a combination of strong security protocols, regular software updates, and user education. Addressing vulnerabilities before they are exploited is paramount, and this requires a proactive stance from manufacturers, service providers, and users alike. Furthermore, a robust incident response plan is crucial to minimize the impact of any successful attacks.
Best Practices for Securing Smart Connected Devices
Implementing strong security practices across hardware and software is essential for minimizing vulnerabilities. A layered security approach, incorporating multiple defense mechanisms, is far more effective than relying on a single point of protection.
- Strong and Unique Passwords/Authentication: Employ strong, unique passwords for each device and utilize multi-factor authentication (MFA) whenever possible. Avoid using default passwords provided by manufacturers. MFA adds an extra layer of security by requiring a second form of verification, such as a one-time code sent to a mobile phone, in addition to a password.
- Regular Software and Firmware Updates: Install all available security updates and firmware patches promptly. These updates often contain critical security fixes that address known vulnerabilities. Automatic update features should be enabled whenever possible.
- Secure Network Configuration: Use strong encryption protocols (like WPA3) for Wi-Fi networks and enable firewalls on both the devices and the network router. Regularly review network access controls to ensure only authorized devices can connect.
- Hardware Security Considerations: Choose devices from reputable manufacturers with a proven track record of security. Consider devices with hardware-based security features, such as secure boot and Trusted Platform Modules (TPMs), which offer additional protection against attacks.
- User Education and Awareness: Educate users about potential threats and best practices. This includes recognizing phishing attempts, understanding the importance of software updates, and knowing how to report suspicious activity.
Comparison of Security Protocols
Various security protocols are employed to protect data transmitted between smart devices and the cloud. Their effectiveness varies based on factors such as encryption strength, authentication mechanisms, and overall implementation.
| Protocol | Description | Strengths | Weaknesses |
|---|---|---|---|
| TLS/SSL | Transport Layer Security/Secure Sockets Layer; provides encrypted communication over a network. | Widely adopted, robust encryption. | Susceptible to vulnerabilities if not properly implemented or updated. Man-in-the-middle attacks remain a possibility. |
| HTTPS | Hypertext Transfer Protocol Secure; uses TLS/SSL to secure web communication. | Secure communication for web-based interactions with smart devices. | Relies on the underlying TLS/SSL implementation; vulnerabilities in TLS/SSL impact HTTPS. |
| MQTT (with TLS) | Message Queuing Telemetry Transport; lightweight messaging protocol often used in IoT. TLS adds encryption. | Suitable for resource-constrained devices. | Requires careful configuration to ensure security. Vulnerabilities in MQTT implementation can be exploited. |
Role of Firmware Updates and Patching
Firmware updates are critical for patching security vulnerabilities and improving the overall security posture of smart connected devices. These updates often address bugs and weaknesses that could be exploited by malicious actors. Prompt deployment of updates is essential to minimize the window of vulnerability.
Deploying updates across millions of devices presents significant challenges. These include:
- Device Heterogeneity: Millions of devices may have different hardware and software configurations, making it difficult to deploy updates universally.
- Connectivity Issues: Devices may be deployed in remote locations with limited or unreliable internet connectivity, hindering update deployment.
- User Engagement: Users may delay or fail to install updates, leaving their devices vulnerable.
- Update Management Complexity: Managing updates across a large number of devices requires robust infrastructure and sophisticated update management systems.
Future Trends and Challenges
The explosive growth of smart connected devices presents a rapidly evolving cybersecurity landscape. While we’ve made strides in understanding and mitigating existing vulnerabilities, new threats constantly emerge, demanding innovative solutions and proactive strategies. The interconnected nature of these devices exacerbates the problem, creating cascading effects from a single compromised device to entire networks. This section explores emerging threats, the role of AI, and key challenges facing the cybersecurity community.The increasing sophistication of cyberattacks targeting smart devices necessitates a deeper understanding of future trends and the challenges they pose.
The interconnectedness of these devices within the Internet of Things (IoT) creates a complex attack surface, making it crucial to anticipate and address emerging threats effectively.
Emerging Cybersecurity Threats Targeting Smart Connected Devices
Three significant emerging threats are particularly concerning: supply chain attacks targeting firmware, sophisticated malware exploiting vulnerabilities in device operating systems, and the use of compromised devices in large-scale botnet operations. Supply chain attacks, where malicious code is introduced during the manufacturing process, are difficult to detect and can affect millions of devices simultaneously. Advanced malware designed to exploit zero-day vulnerabilities in the underlying operating systems of these devices can allow attackers to gain complete control, leading to data breaches or device hijacking.
Finally, the use of compromised smart devices in botnets allows attackers to launch distributed denial-of-service (DDoS) attacks or participate in other malicious activities on a massive scale, impacting critical infrastructure. For instance, a recent attack on a major smart home manufacturer revealed that millions of devices were vulnerable to a single exploit that allowed remote control. This highlights the scale of the problem and the potential for widespread damage.
The Role of Artificial Intelligence in Exploiting and Mitigating Cybersecurity Vulnerabilities
AI plays a dual role – both as a weapon for attackers and a shield for defenders. Attackers leverage AI for automating vulnerability discovery, crafting sophisticated phishing attacks, and developing highly effective malware capable of evading traditional security measures. For example, AI-powered tools can rapidly analyze code for vulnerabilities, allowing attackers to identify and exploit weaknesses more efficiently.
On the other hand, AI-powered security systems can analyze massive datasets to detect anomalies, predict attacks, and automatically respond to threats in real-time. AI can improve threat detection by identifying patterns and behaviors that would be missed by traditional security tools, leading to faster response times and reduced impact. For example, AI-powered intrusion detection systems can analyze network traffic to identify malicious activity and automatically block or quarantine compromised devices.
Key Challenges Facing the Cybersecurity Community
The cybersecurity community faces numerous challenges in securing the ever-growing number of smart connected devices. These include:
- The sheer volume and diversity of devices: The vast number of devices from various manufacturers with different operating systems and security protocols makes comprehensive security management extremely difficult.
- The lack of standardized security protocols and updates: Inconsistent security practices across devices hinder the implementation of effective security measures and make it difficult to deploy patches and updates.
- The difficulty in detecting and responding to attacks: The distributed and heterogeneous nature of IoT devices makes it challenging to detect and respond to attacks effectively.
- The limited resources and expertise available: Many organizations lack the resources and expertise to implement and maintain robust security measures for their IoT devices.
- The increasing sophistication of cyberattacks: Attackers are constantly developing new and more sophisticated techniques to exploit vulnerabilities in IoT devices.
Final Thoughts
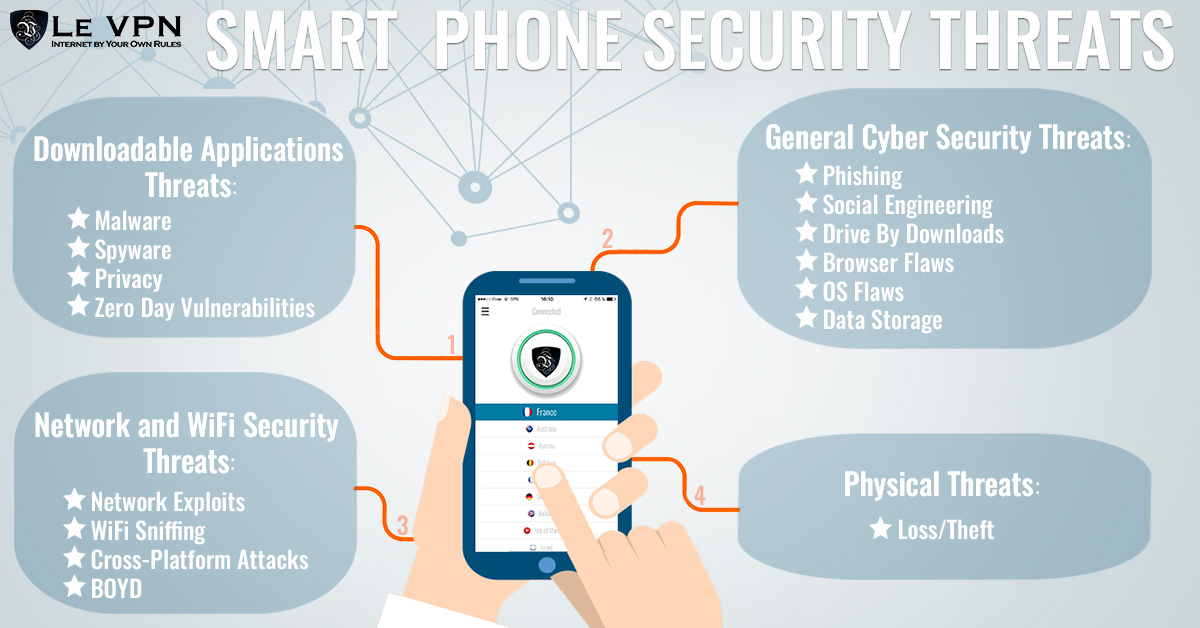
The pervasive nature of smart connected devices presents a significant challenge to cybersecurity. While the risks are real and substantial, the solutions are multifaceted and require a collaborative effort from manufacturers, developers, and users alike. By understanding the vulnerabilities, employing robust security practices, and staying informed about emerging threats, we can collectively work towards a safer and more secure connected future.
It’s not just about protecting our gadgets; it’s about protecting our data, our privacy, and ultimately, our way of life.
Question & Answer Hub
What are the most common entry points for hackers targeting smart devices?
Many attacks exploit default passwords, weak Wi-Fi security, or outdated firmware. Phishing scams and malware are also common entry points.
How can I tell if my smart devices are vulnerable?
Look for security alerts from manufacturers, check for available software updates, and be wary of unexpected behavior from your devices. Regularly change default passwords and enable strong authentication wherever possible.
What should I do if I suspect my smart device has been compromised?
Disconnect the device from your network immediately. Change all associated passwords. Run a malware scan. Contact the device manufacturer and your internet service provider.
Are all smart devices equally vulnerable?
No. The level of vulnerability varies depending on the device, its operating system, the security features implemented by the manufacturer, and the user’s security practices.