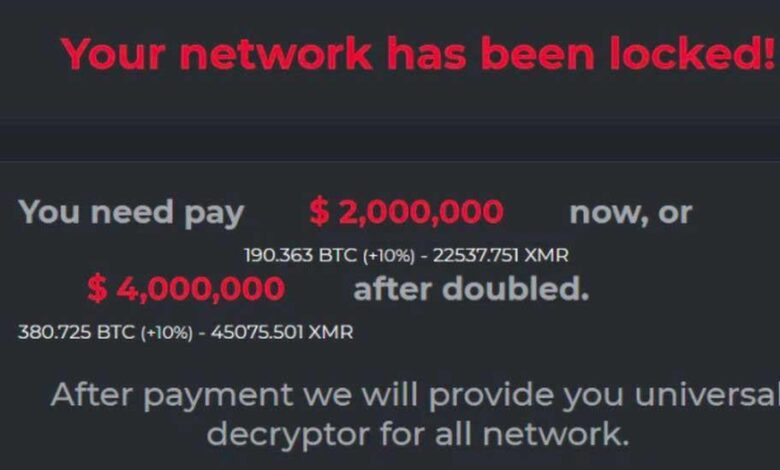
DarkSide Ransomware Demands $2,000,000
Darkside ransomware demands 2000000 – DarkSide ransomware demands $2,000,000 – a chilling headline that underscores the escalating threat of cybercrime. This isn’t just about money; it’s about the crippling impact on businesses, the fear instilled in victims, and the sophisticated tactics employed by these digital criminals. We’ll delve into the mechanics of this particular attack, exploring the methods used by DarkSide, the staggering ransom amount, and the lasting consequences for those caught in its web.
Prepare to be both informed and alarmed.
The sheer scale of the $2,000,000 demand highlights the increasing profitability of ransomware attacks. We’ll examine the factors contributing to this hefty sum, comparing it to demands from other notorious ransomware groups. We’ll also explore the intricate process of negotiation, the payment methods used, and the hidden infrastructure supporting these malicious operations. This isn’t just a story about money; it’s a case study in the evolution of cybercrime and its devastating impact.
DarkSide Ransomware’s Operational Methods
DarkSide, a notorious ransomware-as-a-service (RaaS) operation, employed sophisticated techniques to infiltrate networks, encrypt data, and extort victims. Understanding its operational methods is crucial for effective prevention and response. This analysis delves into the technical aspects of DarkSide’s attacks, providing a detailed overview of its tactics and procedures.
DarkSide’s Encryption Techniques
DarkSide utilized AES-256 encryption, a widely considered strong symmetric encryption algorithm, to encrypt victim files. This encryption method involves generating a unique encryption key for each victim, making decryption without the correct key computationally infeasible. The encryption process was designed to be fast and efficient, maximizing the disruption caused to the victim’s operations. Furthermore, DarkSide often employed a double-encryption scheme, layering an additional encryption layer for enhanced security.
This added layer significantly increased the difficulty of decryption, even for advanced forensic teams.
DarkSide’s Infiltration Vectors and Initial Access Methods
DarkSide’s initial access methods were diverse and sophisticated. Common vectors included exploiting vulnerabilities in exposed Remote Desktop Protocol (RDP) servers, phishing campaigns delivering malicious attachments or links, and the use of compromised credentials to gain unauthorized access. The ransomware operators often leveraged previously unknown or unpatched vulnerabilities (zero-day exploits) to bypass security measures. In addition, DarkSide’s operators frequently employed social engineering techniques to manipulate employees into granting access or revealing sensitive information.
DarkSide’s Data Exfiltration Process
Before encryption, DarkSide typically exfiltrated sensitive data from the victim’s network. This stolen data served as leverage, threatening to publicly release it if the ransom was not paid. Data exfiltration was achieved through various methods, including the use of command-and-control (C2) servers to transfer stolen data discreetly. The selection of data targeted for exfiltration was often strategic, focusing on highly sensitive information such as financial records, intellectual property, and customer data.
This exfiltration process often occurred prior to the encryption phase, maximizing the pressure on the victim to comply with the ransom demand.
A Typical DarkSide Attack: A Step-by-Step Breakdown
A typical DarkSide attack followed a structured approach. Initially, the attackers would gain initial access to the network, often through compromised credentials or exploited vulnerabilities. They would then move laterally within the network, identifying valuable data and systems. Subsequently, they would exfiltrate sensitive data before deploying the ransomware to encrypt critical files. Finally, a ransom note would be displayed, demanding payment in cryptocurrency for decryption and a promise to not release the exfiltrated data.
Stages of a DarkSide Attack
| Stage | Description | Tactics | Techniques |
|---|---|---|---|
| Initial Access | Gaining unauthorized access to the victim’s network. | Exploitation, Social Engineering | RDP brute-forcing, Phishing, Credential harvesting |
| Lateral Movement | Moving within the network to identify valuable assets. | Privilege Escalation, Discovery | Pass-the-hash, Active Directory enumeration, Network scanning |
| Data Exfiltration | Transferring sensitive data to the attacker’s servers. | Data Staged, Exfiltration | Data transfer via C2 servers, use of encrypted channels |
| Ransomware Deployment & Encryption | Encrypting the victim’s files and displaying a ransom note. | Execution, Defense Evasion | File encryption using AES-256, Ransom note delivery |
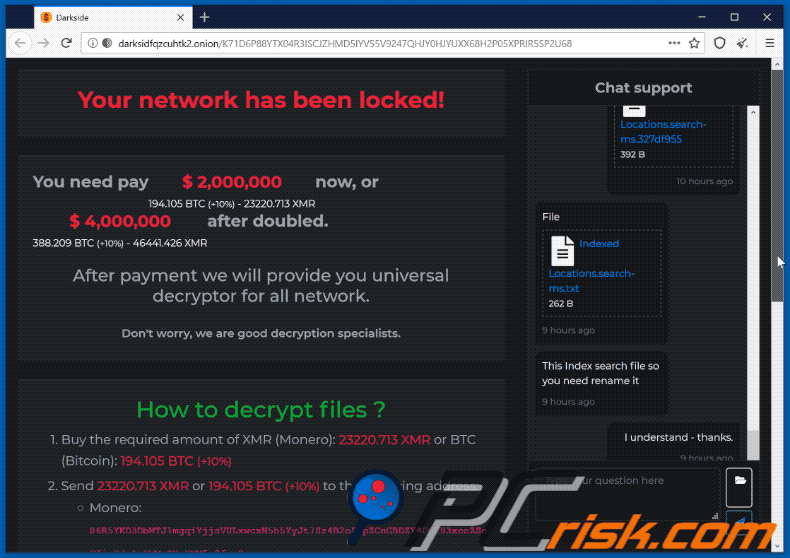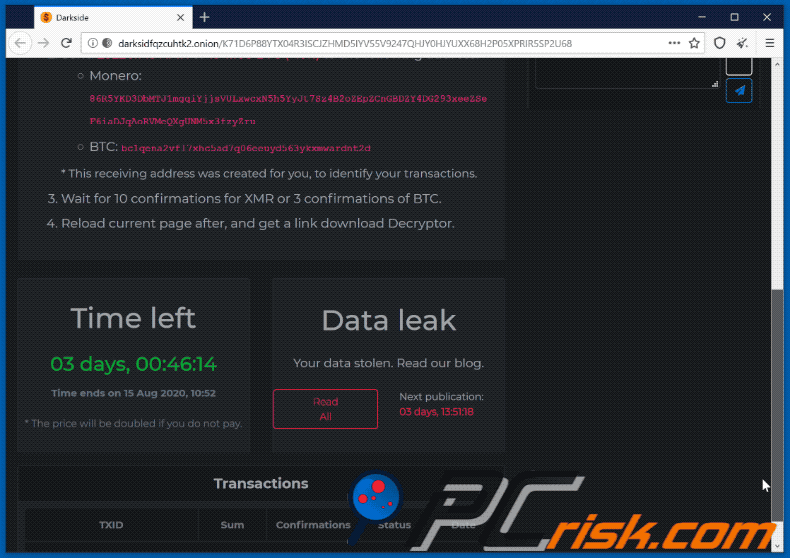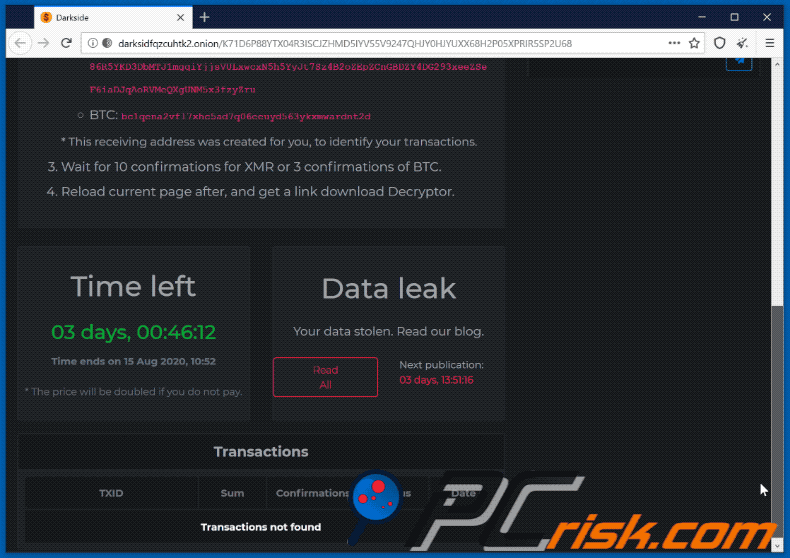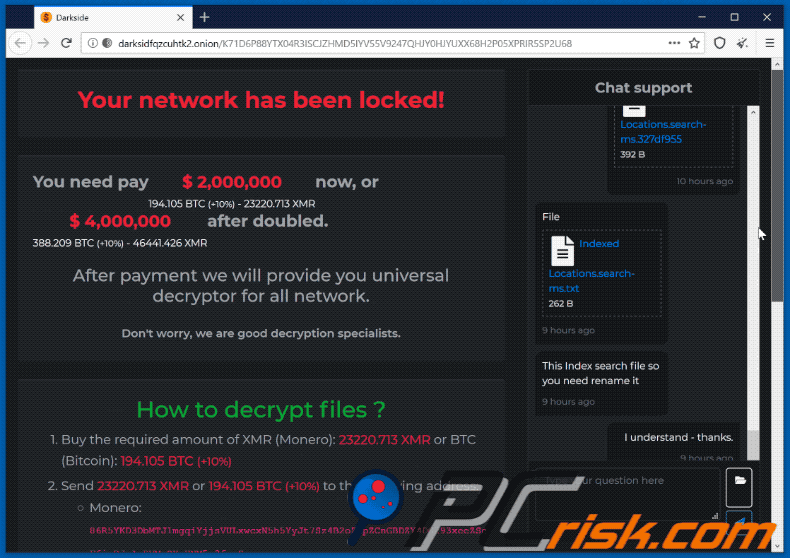
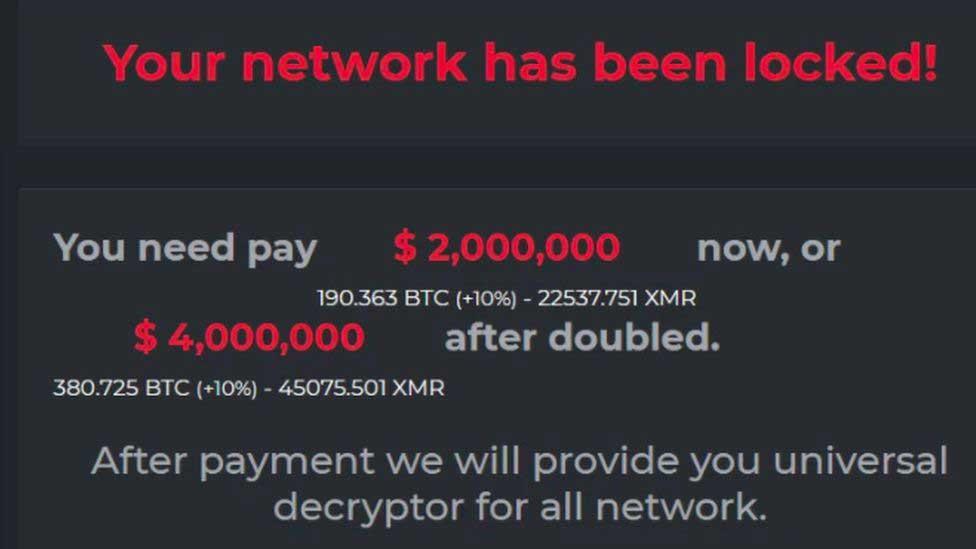
The $2,000,000 Ransom Demand
The sheer size of the $2,000,000 ransom demanded by DarkSide in some cases highlights the significant financial stakes involved in ransomware attacks. This figure wasn’t a standard across all victims; the amount was likely tailored to the perceived value of the compromised data and the victim’s ability to pay. Several factors contributed to the determination of this substantial sum.The factors influencing the size of the ransom demand are complex and multifaceted.
The size of the victim organization played a crucial role; larger corporations with more extensive data holdings and greater revenue streams were likely targeted for higher ransom demands. The sensitivity of the stolen data was another key factor. Confidential customer information, intellectual property, or sensitive financial records would justify a higher price than less critical data. The potential for reputational damage and legal ramifications following a data breach also contributed to the ransom negotiation.
DarkSide likely assessed the victim’s risk tolerance and willingness to pay to mitigate these potential consequences.
Factors Influencing Ransom Demand Size
The ransom amount wasn’t arbitrarily chosen. DarkSide, like other ransomware groups, engaged in a calculated assessment of the victim’s vulnerabilities and the potential impact of a data breach. They considered the victim’s financial resources, the value of the stolen data, and the potential for negative publicity. A large multinational corporation would likely face a much larger demand than a small local business.
The sensitivity of the data – for example, medical records versus marketing materials – also heavily influenced the amount demanded.
Comparison to Other Ransomware Groups
While DarkSide’s demands often reached into the millions, it wasn’t always the highest. Other ransomware groups like REvil (Sodinokibi) and Conti have been known to demand even larger sums, sometimes reaching tens of millions of dollars for high-profile targets. The variation in ransom demands reflects the differing strategies and targets of various ransomware groups. Some groups may focus on quantity, targeting numerous smaller businesses with lower ransom demands, while others prioritize quality, targeting a few high-value targets with significantly larger demands.
DarkSide’s Payment Methods
DarkSide primarily used cryptocurrency for ransom payments, specifically Bitcoin. This choice offered a degree of anonymity and untraceability, making it difficult for law enforcement to track the funds. The use of cryptocurrency is a common practice among ransomware groups due to its decentralized nature and relative ease of transferring funds across borders. The exact details of the payment process were likely communicated through encrypted channels during the ransom negotiation.
DarkSide’s Ransom Negotiation Infrastructure
DarkSide utilized encrypted communication channels, likely through anonymizing networks like Tor, to conduct ransom negotiations. This ensured a degree of secrecy and prevented easy monitoring by law enforcement or security researchers. They likely used dedicated servers or infrastructure to manage the negotiations and communication with victims, ensuring a degree of operational security. The use of a dedicated infrastructure helped them maintain plausible deniability and avoid direct association with the attacks.
DarkSide Ransom Negotiation Process Flowchart
The following describes a hypothetical flowchart illustrating the ransom negotiation process from DarkSide’s perspective. Note that this is a representation based on observed patterns and may not reflect the exact process in every instance.[Imagine a flowchart here. It would start with “Initial Compromise,” branching to “Data Exfiltration,” then “Victim Identification and Assessment” leading to “Ransom Demand Generation.” This would then branch to “Negotiation Initiation (via encrypted channels),” followed by “Payment Instructions Provided,” and finally, “Decryption Key Delivery (upon payment confirmation).” Failure at any stage would lead to a separate branch, such as “Data Leak” or “No Payment, No Decryption.”]
Victim Impact and Response

The DarkSide ransomware attacks, with their hefty ransom demands like the $2,000,000 case, inflict significant damage on victims, extending far beyond the immediate financial loss. The impact varies depending on the organization’s size, preparedness, and ultimately, their decision to pay the ransom. Understanding this impact is crucial for effective prevention and response.Organizations most vulnerable to DarkSide attacks typically share common characteristics.
Large enterprises with extensive networks and valuable data are prime targets, as are those in sectors with sensitive information, such as healthcare, finance, and manufacturing. Smaller businesses with less robust cybersecurity infrastructure are also at risk, often lacking the resources for advanced threat detection and response. The attackers strategically target organizations they believe are likely to pay the ransom due to the potential cost of downtime and data loss.
Immediate Consequences for Victims Who Pay the Ransom
Paying the ransom doesn’t guarantee data recovery or prevent future attacks. In fact, it often fuels further criminal activity. Victims face immediate financial losses from the ransom payment itself, plus the costs associated with incident response, including hiring cybersecurity experts, legal counsel, and potentially public relations to manage reputational damage. Even after payment, there’s no guarantee the attackers will decrypt the data; some victims have reported receiving unusable decryption keys or facing further extortion attempts.
The immediate disruption to operations can also lead to lost business, contracts, and customer trust. For example, a hospital forced to shut down its systems due to a DarkSide attack may face severe consequences, including patient care disruptions and potential legal liabilities.
Long-Term Repercussions for Victims Who Refuse to Pay
Refusing to pay the ransom carries its own set of challenges. The loss of sensitive data can result in significant financial losses, regulatory fines (particularly in heavily regulated industries like healthcare and finance), and legal repercussions. Reputational damage is also a significant long-term concern, potentially leading to decreased customer trust and difficulty attracting investors. The time and resources spent recovering data, rebuilding systems, and restoring operations can be substantial.
For instance, a manufacturing company might experience production delays, lost revenue, and damage to its supply chain if it cannot access critical operational data after a DarkSide attack. The long-term costs of recovery can far exceed the ransom demand in many cases.
Steps a Victim Should Take After a DarkSide Attack
Immediate action is crucial after a DarkSide attack. First, isolate infected systems from the network to prevent further spread of the ransomware. Second, thoroughly investigate the extent of the breach to determine what data has been compromised. Third, contact law enforcement and relevant regulatory bodies to report the incident. Fourth, engage with a reputable cybersecurity firm specializing in ransomware recovery.
Fifth, carefully consider the decision to pay the ransom, weighing the risks and potential consequences. Finally, implement robust security measures to prevent future attacks. This multi-faceted approach is essential to mitigate the damage and protect against future threats.
Best Practices for Ransomware Prevention and Incident Response
A proactive approach is the most effective defense against ransomware attacks.
- Regularly back up critical data to offline storage, ensuring backups are tested and readily accessible.
- Implement a robust patching and update schedule for all software and operating systems.
- Employ multi-factor authentication (MFA) to enhance account security.
- Educate employees about phishing and social engineering tactics to prevent initial infection.
- Restrict administrative privileges to minimize the impact of compromised accounts.
- Utilize endpoint detection and response (EDR) solutions to monitor for malicious activity.
- Develop and regularly test an incident response plan to ensure a coordinated and effective response.
- Segment networks to limit the impact of a breach.
- Conduct regular security awareness training for all employees.
- Consider cybersecurity insurance to mitigate financial losses.
Law Enforcement and DarkSide’s Demise
The takedown of DarkSide, a prolific ransomware-as-a-service (RaaS) operation, wasn’t a singular event but rather the culmination of a multi-pronged effort involving international law enforcement cooperation and sophisticated cyber investigative techniques. While the group’s activities caused significant damage, their ultimate demise highlights the increasing effectiveness of global collaboration in combating cybercrime.The role of law enforcement in disrupting DarkSide’s operations was crucial.
Agencies in multiple countries worked together, sharing intelligence and coordinating actions to identify and neutralize the group’s infrastructure. This included seizing servers, tracing financial flows, and ultimately identifying and arresting key members. This coordinated effort proved significantly more effective than isolated national investigations.
DarkSide’s Takedown and Related Prosecutions
While there haven’t been widely publicized, high-profile prosecutions directly tied to the core DarkSide leadership resulting in lengthy prison sentences (as of late 2023), the disruption of their infrastructure and subsequent shutdown effectively crippled their operations. The FBI and other agencies successfully seized infrastructure components, disrupting their ability to encrypt victims’ data and collect ransoms. This disruption, though not resulting in immediate high-profile convictions, significantly hampered their ability to operate and ultimately led to their demise.
The investigation continues, and future prosecutions are possible.
Factors Contributing to DarkSide’s Shutdown
Several factors contributed to DarkSide’s downfall. The coordinated international law enforcement response was paramount, leveraging intelligence sharing and joint operations. The group’s reliance on cryptocurrency for ransom payments, while initially providing anonymity, ultimately left a trail that investigators could follow. Additionally, pressure from the media, victims, and the cybersecurity community, along with the reputational damage from high-profile attacks, likely played a role in their decision to shut down.
The increased scrutiny and the rising cost of maintaining operational security likely made continuing operations unsustainable.
Comparison with Other Successful Ransomware Takedowns, Darkside ransomware demands 2000000
The DarkSide takedown shares similarities with other successful ransomware group disruptions, such as the takedown of REvil. In both cases, international cooperation, sophisticated cyber investigation techniques, and the tracing of cryptocurrency transactions were key. However, the level of public information and subsequent prosecutions has varied significantly between different operations. The success of these takedowns underscores the importance of proactive law enforcement and international collaboration in disrupting ransomware networks.
Unlike some ransomware groups who simply rebranded or fragmented after a takedown, DarkSide appears to have ceased operations altogether.
Impact of the DarkSide Takedown on the Ransomware Landscape
The impact of DarkSide’s shutdown was significant, though not immediately resulting in a complete eradication of ransomware attacks. It sent a clear message to other ransomware groups that law enforcement possesses the capability to disrupt their operations and bring them to justice.
The DarkSide ransomware attack demanding $2,000,000 highlights the urgent need for robust cybersecurity. This incident underscores the importance of proactive security measures, especially with the rise of cloud-based systems; understanding solutions like those discussed in this article on bitglass and the rise of cloud security posture management is crucial. Ultimately, preventing such devastating DarkSide ransomware attacks requires a multi-layered approach to security.
| Date | Event | Impact | Source |
|---|---|---|---|
| May 2021 | DarkSide ransomware attack on Colonial Pipeline | Significant disruption to fuel supply in the US; payment of a $4.4 million ransom. | News reports, Colonial Pipeline statement |
| July 2021 | DarkSide announces shutdown | Temporary reduction in DarkSide attacks; shift towards other ransomware groups. | DarkSide statement (reported by various news outlets) |
| Post-July 2021 | Rise of other ransomware groups | Other ransomware groups filled the void left by DarkSide, demonstrating the persistent nature of the threat. | Cybersecurity reports, news articles |
| Ongoing | Continued law enforcement efforts | Sustained pressure on ransomware groups; increased collaboration between law enforcement agencies. | Public statements from law enforcement agencies |
The DarkSide Ransomware’s Infrastructure
DarkSide’s success stemmed not only from its potent encryption but also from its sophisticated and well-hidden infrastructure. This network, designed for anonymity and resilience, allowed the operators to maintain control and evade detection for a considerable period. Understanding its components is crucial to grasping the scale of the operation and the challenges faced in dismantling it.DarkSide leveraged a multi-layered infrastructure to distribute its ransomware, manage its victims, and receive payments.
This wasn’t a single server; it was a network of interconnected systems designed to complicate tracing and disruption.
Server Architecture and Location
DarkSide employed a decentralized server architecture, likely distributed across multiple jurisdictions to hinder law enforcement efforts. They likely used virtual private servers (VPS) hosted by various providers, making it difficult to pinpoint a single location or provider responsible. This geographic dispersion also provided redundancy; the failure of one server wouldn’t cripple the entire operation. The servers themselves likely ran on common operating systems, possibly Linux distributions given their prevalence in server environments, and were hardened to resist intrusion.
They were carefully configured to minimize their digital footprint, potentially using anonymization techniques like VPNs and Tor.
Obfuscation and Anonymity Techniques
The operators implemented several layers of obfuscation to mask their true identities and the location of their servers. This included using anonymizing proxies and the Tor network for communication, which routes traffic through multiple relays, obscuring the origin and destination. They also likely employed techniques to encrypt their communications, making it extremely difficult to intercept and decipher their messages.
The use of cryptocurrency for ransom payments further enhanced their anonymity, as it removed the need for traditional banking channels that leave traceable records. Furthermore, the infrastructure may have included techniques like domain generation algorithms (DGAs) to generate new domains dynamically, making it harder for researchers to track their C&C servers.
Communication Channels
DarkSide operators likely communicated with victims and amongst themselves through encrypted channels. These channels could have included encrypted email, messaging applications with end-to-end encryption, or custom-built communication systems utilizing the Tor network. The use of secure communication methods was critical for maintaining operational security and preventing law enforcement from intercepting their communications. The choice of communication methods would have prioritized security and anonymity over speed or ease of use.
Tools and Technologies
DarkSide utilized a range of tools and technologies to support its operations. This included custom-built ransomware code, sophisticated encryption algorithms, command-and-control (C&C) servers for managing infected systems, and data exfiltration tools to steal sensitive information from victims. They also likely used penetration testing tools and exploit kits to initially compromise victim networks. Their toolkit was constantly evolving, incorporating new techniques and technologies to improve their effectiveness and evade detection.
The DarkSide ransomware attack demanding $2,000,000 highlights the vulnerability of even the most secure systems. Building robust, resilient applications is crucial, and that’s where understanding the advancements in application development comes in. Check out this article on domino app dev, the low-code and pro-code future , to see how modern approaches can help mitigate such risks. Ultimately, the DarkSide attack underscores the need for continuous improvement in application security and development practices.
The use of open-source tools, combined with custom-developed components, would have allowed for flexibility and adaptability.
Visual Representation of DarkSide’s Infrastructure
Imagine a network diagram. At the center are several C&C servers, each located in a different geographic location and masked by multiple layers of anonymization. These servers communicate with each other through encrypted channels. Around the C&C servers are multiple layers of proxies and VPNs, further obscuring their location. Connecting to these are numerous compromised victim machines, each sending data back to the C&C servers via encrypted channels.
The entire network is designed for resilience and redundancy, with multiple paths for communication and data transfer. This structure makes tracing the origins of attacks and identifying the perpetrators exceptionally difficult. The entire system is further reinforced by the use of cryptocurrency for payments and techniques such as DGAs to maintain a constantly shifting network.
Closing Summary: Darkside Ransomware Demands 2000000
The DarkSide ransomware saga, with its $2,000,000 ransom demand, serves as a stark reminder of the ever-evolving landscape of cyber threats. Understanding the methods, motivations, and impact of such attacks is crucial for both individuals and organizations. While DarkSide may be gone, the lessons learned from its reign of terror remain vital in bolstering our defenses against future attacks.
Proactive security measures, robust incident response plans, and a heightened awareness are our best weapons in this ongoing battle.
Question Bank
What encryption methods did DarkSide use?
Reports suggest DarkSide employed AES-256 encryption, known for its strength and difficulty to crack without the decryption key.
How did DarkSide infiltrate systems?
DarkSide used various methods, including exploiting software vulnerabilities, phishing emails, and compromised credentials.
What happens if a victim refuses to pay the ransom?
Refusal to pay often leads to data being leaked publicly, causing reputational damage and potential legal repercussions.
What are the long-term effects of a DarkSide attack?
Long-term effects can include financial losses, legal battles, damaged reputation, and operational disruptions.
Are there any successful prosecutions related to DarkSide?
While DarkSide’s infrastructure was taken down, information on specific prosecutions is limited and often confidential.