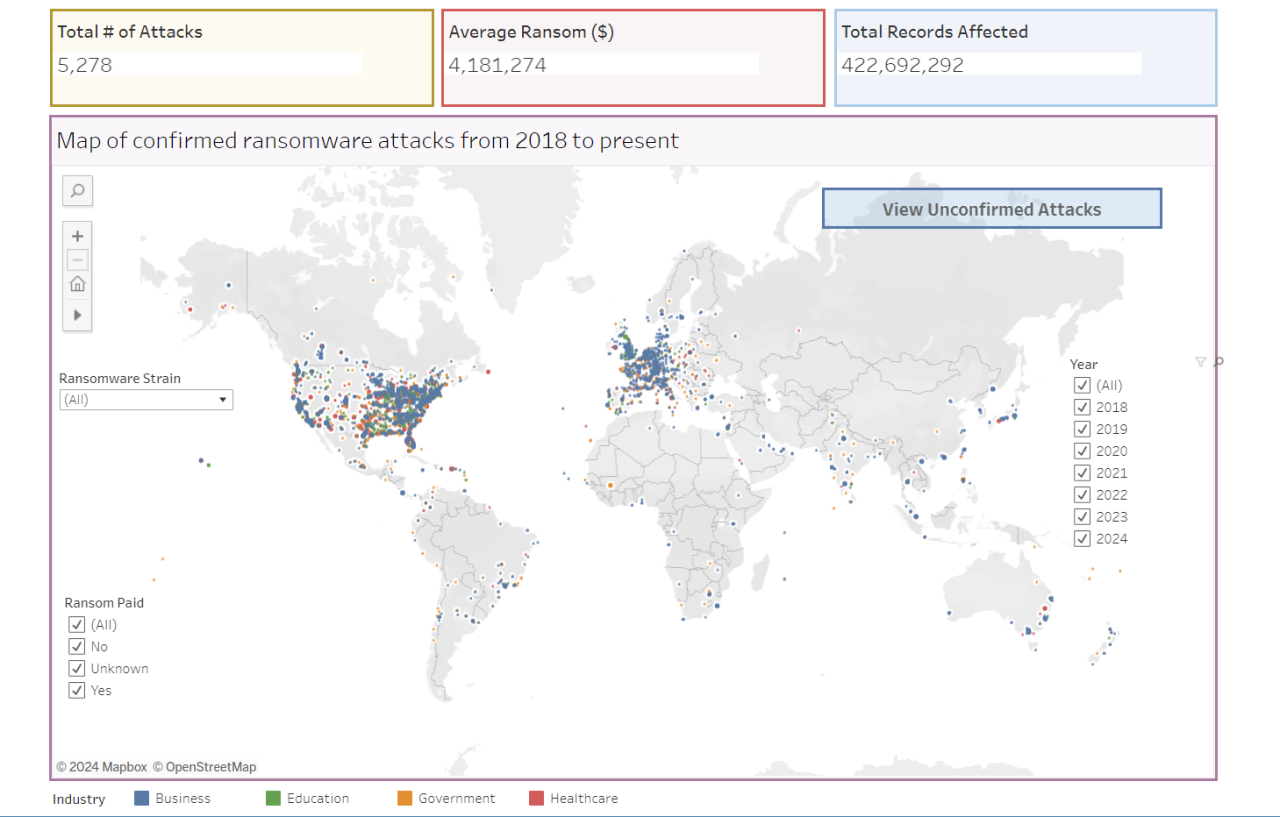
Data Centers Are Extremely Vulnerable to Ransomware Threats
Data centers are extremely vulnerable to ransomware threats. It’s a scary thought, isn’t it? These digital fortresses, housing the world’s most valuable data, are surprisingly susceptible to crippling attacks. We’re not just talking about lost files; we’re talking about massive financial losses, operational downtime, and reputational damage that can take years to recover from. This post dives deep into the vulnerabilities, the threats, and most importantly, how we can better protect these critical infrastructure hubs.
The sheer scale of the problem is staggering. Ransomware attacks are becoming more sophisticated, targeting not just individual computers but entire data center networks. The methods used are diverse, ranging from simple phishing emails to highly targeted exploits that leverage zero-day vulnerabilities. The consequences can be devastating, leading to business disruption, legal repercussions, and a significant erosion of customer trust.
Understanding these threats is the first step towards building a more resilient and secure digital future.
The Scope of the Problem
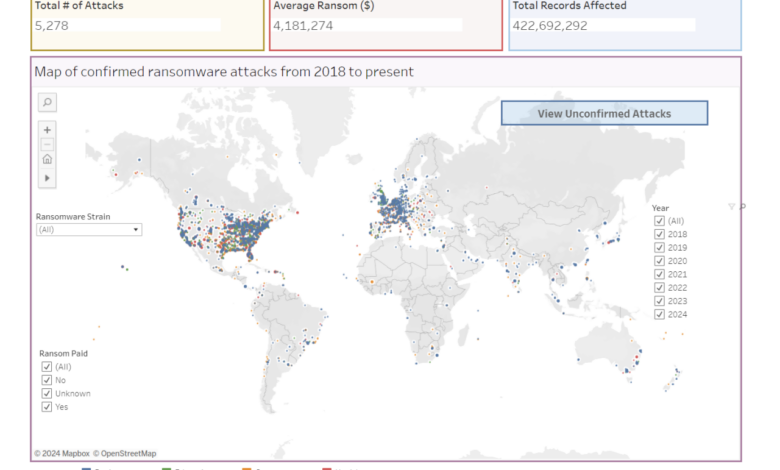
Data centers, the beating heart of the digital world, are facing an unprecedented threat: ransomware. These attacks are no longer isolated incidents; they’re a widespread, evolving problem with devastating consequences for businesses and organizations globally. The sheer volume and sophistication of these attacks are increasing, demanding a proactive and comprehensive approach to security.The vulnerability of data centers stems from their critical role in storing and processing sensitive information.
They are often targeted because a successful attack can cripple operations, expose valuable data, and extract significant ransoms. The interconnected nature of modern data centers, coupled with the ever-increasing reliance on digital infrastructure, makes them prime targets for cybercriminals. The potential impact extends far beyond financial losses, impacting reputation, customer trust, and even national security in certain cases.
Financial and Operational Consequences of Ransomware Attacks
Successful ransomware attacks on data centers can lead to crippling financial and operational losses. Direct costs include the ransom payment itself, which can reach millions of dollars depending on the size and criticality of the affected data center. Beyond the ransom, organizations face substantial costs associated with incident response, data recovery, system restoration, legal fees, and potential regulatory fines.
Operational disruptions can lead to lost revenue, decreased productivity, and damage to brand reputation. Downtime can range from days to weeks, even months, depending on the extent of the damage and the organization’s recovery capabilities. This downtime translates directly into lost business opportunities and potential long-term damage to the bottom line. Furthermore, the disruption of critical services can have cascading effects on dependent organizations and the wider economy.
Examples of High-Profile Ransomware Attacks
Several high-profile ransomware attacks have highlighted the vulnerability of data centers. While specific details are often kept confidential for security reasons, the impact is often publicly visible. For instance, a major healthcare provider experienced a ransomware attack that crippled its entire network, resulting in significant delays in patient care and millions of dollars in losses. Similarly, a large financial institution faced a ransomware attack that disrupted online banking services for several days, impacting millions of customers and resulting in substantial reputational damage.
These examples illustrate the severe consequences that ransomware attacks can have, regardless of an organization’s size or industry.
Types of Ransomware Attacks Targeting Data Centers and Their Methods
The following table compares different types of ransomware attacks targeting data centers and their methods.
| Ransomware Type | Target | Method | Impact |
|---|---|---|---|
| CryptoLocker | Data files | Encryption of files, demanding ransom for decryption key | Data loss, operational disruption |
| LockBit | Entire systems/networks | Encryption of critical systems and data, data exfiltration | Complete system shutdown, data loss, data leak |
| REvil (Sodinokibi) | Virtual machines, backups | Encryption of virtual machines and backups, data exfiltration | Significant downtime, data loss, reputational damage |
| Ryuk | Critical servers and applications | Encryption of critical systems and applications, potentially data exfiltration | Service disruption, financial losses, operational downtime |
Attack Vectors and Entry Points
Data centers, despite their robust security measures, remain vulnerable to ransomware attacks. Understanding the various attack vectors and entry points is crucial for effective defense. These attacks exploit weaknesses in infrastructure, applications, and human behavior, often converging to create a successful breach.
Ransomware actors employ a multifaceted approach, leveraging a combination of technical exploits and social engineering tactics to gain unauthorized access. The sophistication of these attacks is constantly evolving, requiring a proactive and layered security strategy to mitigate the risk.
Vulnerabilities in Network Infrastructure
Network infrastructure vulnerabilities represent a significant entry point for ransomware. Outdated or misconfigured firewalls, vulnerable network devices (routers, switches), and insecure remote access protocols (like RDP or SSH) all provide potential avenues for attackers. For instance, a failure to patch known vulnerabilities in network equipment can allow attackers to gain initial access, often through easily exploitable exploits publicly available on the dark web.
Once inside the network perimeter, lateral movement to critical systems becomes significantly easier. This often involves exploiting weak or default passwords on network devices and leveraging known vulnerabilities in network operating systems.
Vulnerabilities in Applications
Applications, both custom-built and commercial off-the-shelf (COTS), frequently contain vulnerabilities that can be exploited. Unpatched software, particularly database systems and web servers, are prime targets. Attackers often use automated tools to scan for known vulnerabilities, exploiting them to gain initial access or escalate privileges within the data center environment. For example, a SQL injection vulnerability in a poorly secured web application could allow an attacker to execute arbitrary commands, potentially leading to ransomware deployment.
Regular security audits and penetration testing are vital to identify and mitigate these risks.
Human Error and Social Engineering
Human error remains a significant factor in ransomware attacks. Phishing emails, cleverly disguised to appear legitimate, often trick employees into revealing credentials or downloading malicious attachments. Social engineering techniques, such as pretexting (creating a false sense of urgency or authority), can also be effective in manipulating individuals into compromising security protocols. A single compromised account can provide attackers with a foothold, enabling them to deploy ransomware across the entire data center.
The 2021 Colonial Pipeline attack serves as a stark reminder of the devastating impact of social engineering; a compromised VPN account allowed attackers to cripple the pipeline’s operations.
The Role of Phishing, Social Engineering, and Malware
Phishing and social engineering attacks are often the initial vectors for ransomware deployment. Malicious emails containing attachments or links that download malware are commonly used. This malware can range from simple trojans that provide remote access to sophisticated ransomware strains that encrypt data and demand payment for its release. Once malware is installed, it can spread laterally through the network, infecting servers and workstations, and eventually encrypting critical data.
The malware itself may also contain functionalities to disable security software or evade detection.
Stages of a Typical Ransomware Attack
Understanding the typical stages of a ransomware attack is crucial for developing effective preventative measures and incident response plans.
The following flowchart illustrates a typical attack sequence:
[Flowchart Description]: The flowchart begins with the Initial Access stage, depicting various entry points like phishing emails, exploited vulnerabilities, or compromised credentials. This leads to Reconnaissance, where attackers explore the network to identify valuable targets. Next is Lateral Movement, where the attackers move from the initial compromised system to other systems within the data center, gaining privileged access. The Data Exfiltration phase involves stealing sensitive data, often as a backup plan or to increase leverage for negotiation.
Finally, the Ransomware Deployment phase sees the encryption of critical data, followed by a ransom demand. The final stage depicts Post-Attack Activities, which could involve data destruction or continued extortion.
Data Center Security Measures and Their Effectiveness
Data centers, the beating heart of the digital world, are increasingly targeted by ransomware attacks. The sheer volume and sensitivity of data they house make them lucrative targets, demanding robust and multifaceted security strategies. This section delves into the effectiveness of existing security measures in mitigating these threats, exploring different approaches to bolstering data center resilience.
Existing security measures are designed to create layered defenses, aiming to prevent, detect, and respond to ransomware attacks. This layered approach acknowledges that no single solution is foolproof. A successful strategy relies on the integration of multiple techniques, working in concert to minimize vulnerabilities and maximize protection.
Firewall and Intrusion Detection/Prevention Systems
Firewalls act as the first line of defense, filtering network traffic based on predefined rules. They control inbound and outbound connections, blocking malicious traffic attempting to penetrate the data center network. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) monitor network activity for suspicious patterns indicative of attacks, such as unauthorized access attempts or malware behavior. While effective in blocking known threats, these systems are less effective against sophisticated, zero-day exploits that bypass traditional signature-based detection.
Their effectiveness is greatly enhanced by regular updates and integration with other security tools.
Data Backup and Recovery Strategies, Data centers are extremely vulnerable to ransomware threats
A robust backup and recovery strategy is crucial for ransomware resilience. This goes beyond simply backing up data; it involves implementing a multi-layered approach. The 3-2-1 rule is a common guideline: three copies of data, on two different media types, with one copy offsite. This ensures that even if one copy is compromised, others remain accessible. Different strategies exist, including full backups, incremental backups, and differential backups, each with its own advantages and disadvantages.
For example, while full backups are time-consuming, they offer a complete snapshot of data, while incremental backups are faster but require the base backup to restore data. Regular testing of the backup and recovery process is essential to ensure its effectiveness in a real-world scenario. The recovery process should be well-documented and readily available to minimize downtime.
Access Control and Authentication Mechanisms
Implementing robust access control and authentication mechanisms is paramount. This involves implementing strong password policies, multi-factor authentication (MFA), and role-based access control (RBAC). MFA adds an extra layer of security by requiring multiple forms of verification, such as passwords, one-time codes, or biometric authentication. RBAC limits user access to only the resources necessary for their role, minimizing the impact of a compromised account.
Regular audits of user access privileges and the implementation of least privilege access are critical to prevent unauthorized access. Zero trust security models, where no user or device is implicitly trusted, are gaining traction, enforcing strict verification at every access point.
Security Recommendations for Data Center Operators
Effective ransomware mitigation requires a proactive and multi-layered approach. Here are key recommendations:
Implementing these recommendations requires a significant investment of time, resources, and expertise. However, the potential cost of a successful ransomware attack far outweighs the cost of prevention.
- Implement a comprehensive security awareness training program for all personnel.
- Regularly patch and update all software and operating systems.
- Employ robust endpoint detection and response (EDR) solutions.
- Segment the network to limit the impact of a breach.
- Implement a robust incident response plan and regularly test it.
- Conduct regular security audits and penetration testing.
- Utilize network traffic analysis tools to detect anomalous behavior.
- Establish strong data governance policies and procedures.
- Maintain offline backups in a secure, geographically separate location.
- Invest in advanced threat protection solutions such as sandboxing and machine learning-based threat detection.
The Human Element
Let’s face it, even the most robust data center security infrastructure is only as strong as its weakest link – the human element. Ransomware attacks often exploit human error, leveraging social engineering tactics and exploiting vulnerabilities in employee knowledge and awareness. Investing in comprehensive training and awareness programs is therefore not just a good idea; it’s a critical necessity for safeguarding your data center.Employee training and awareness programs are paramount in preventing ransomware attacks.
Well-trained employees are less likely to fall victim to phishing scams, social engineering attempts, and other malicious activities that can compromise the security of your data center. Furthermore, a knowledgeable workforce can play a crucial role in identifying and reporting suspicious activities, helping to minimize the impact of a successful attack. Regular training reinforces best practices and keeps security protocols top-of-mind, reducing the risk of accidental breaches.
Methods for Educating Data Center Personnel
Effective education involves a multi-pronged approach. Training should cover a range of topics, including recognizing and avoiding phishing emails, understanding social engineering techniques, and implementing safe security practices. This can be achieved through various methods, such as interactive online modules, hands-on workshops, and regular security awareness campaigns. For example, employees can be taught to identify suspicious email attachments, links, and requests for personal information.
They should also be trained on how to report suspicious activity immediately to the appropriate security personnel. Role-playing scenarios can simulate real-world situations, allowing employees to practice their response skills in a safe environment.
Data centers are prime targets for ransomware attacks, holding sensitive information that can cripple businesses. Building robust, secure applications is crucial, and exploring modern development approaches like those discussed in this article on domino app dev the low code and pro code future could significantly improve security. Ultimately, mitigating ransomware risk requires a multifaceted strategy, including strong application development practices, to protect our increasingly vulnerable data centers.
Sample Employee Training Module: Ransomware Prevention and Response
This module should include several key components:
Module 1: Understanding Ransomware This section defines ransomware, explains how it works, and provides real-world examples of its impact. It should cover different types of ransomware and their delivery methods (e.g., email attachments, malicious websites, infected software). A case study showing the financial and reputational damage from a real ransomware attack on a similar organization would be impactful.
Module 2: Phishing and Social Engineering This section details common phishing techniques, including spear phishing and whaling attacks. It will provide practical examples of phishing emails and explain how to identify them. It should also cover social engineering tactics such as pretexting and baiting. Employees will learn to verify the legitimacy of emails and requests before taking any action.
Module 3: Safe Security Practices This section covers password security, secure browsing habits, the importance of regular software updates, and the proper handling of sensitive data. It emphasizes the need for strong, unique passwords and the use of multi-factor authentication wherever possible. It also highlights the risks of using public Wi-Fi and downloading files from untrusted sources.
Module 4: Incident Response This section Artikels the procedures to follow if a ransomware attack is suspected. It emphasizes the importance of immediate reporting to the security team and the steps to take to contain the infection. A clear, step-by-step guide with contact information is crucial.
Module 5: Post-Incident Activities This section explains the recovery process after a ransomware attack. It Artikels the steps involved in restoring data from backups and securing the system to prevent future attacks. It also emphasizes the importance of conducting a thorough post-incident review to identify vulnerabilities and improve security protocols.
Examples of Effective Security Awareness Campaigns
Regular security awareness campaigns are crucial to reinforce training and maintain a high level of vigilance. These campaigns can take many forms, such as:
Simulated phishing attacks: Sending controlled phishing emails to employees to test their awareness and response. This provides valuable data on the effectiveness of training and highlights areas needing improvement. The results should be analyzed and used to refine future training programs.
Interactive quizzes and games: Engaging employees with fun and interactive activities that reinforce key security concepts. Gamification can improve knowledge retention and make learning more enjoyable.
Regular security newsletters and emails: Sharing timely security updates, news, and best practices to keep employees informed about emerging threats. This helps to maintain a proactive security culture.
Posters and visual aids: Placing posters and other visual aids around the data center to remind employees of key security procedures. Simple visuals can effectively reinforce important messages.
Rewards and recognition programs: Acknowledging and rewarding employees who demonstrate excellent security practices. This fosters a culture of security and encourages others to follow suit. For example, recognizing employees who reported a suspicious email or identified a potential security risk.
Incident Response and Recovery Strategies
A robust incident response plan is crucial for minimizing the damage caused by a ransomware attack on a data center. Effective planning involves proactive measures, a well-defined response protocol, and a comprehensive recovery strategy. Failing to prepare adequately can lead to significant financial losses, reputational damage, and operational disruption.
Step-by-Step Incident Response Plan
A ransomware attack necessitates immediate and decisive action. The following steps Artikel a comprehensive incident response plan:
1. Detection and Confirmation
Identify the attack through monitoring systems, user reports, or unusual system behavior. Verify that it is indeed a ransomware attack by analyzing the encrypted files and ransom notes.
2. Containment
Isolate infected systems from the network to prevent lateral movement of the ransomware. This may involve disconnecting affected servers, shutting down network segments, or implementing network segmentation firewalls.
3. Eradication
Remove the ransomware from infected systems. This requires a thorough investigation, using antivirus software, and potentially deploying specialized tools for malware removal. System backups should be thoroughly checked for infection before restoring data.
4. Recovery
Restore data from clean backups. Prioritize critical systems and data based on business impact. Verify data integrity after restoration.
5. Post-Incident Activity
Analyze the attack to understand the attack vector, vulnerabilities exploited, and the extent of the damage. Implement security enhancements to prevent future attacks. This includes patching vulnerabilities, strengthening access controls, and enhancing security awareness training.
Containing and Eradicating Ransomware
Containment focuses on limiting the spread of the ransomware. This might involve disabling affected accounts, shutting down affected servers, and blocking malicious network traffic. Eradication involves removing the malware completely, which may necessitate reinstalling operating systems, reformatting hard drives, and using specialized malware removal tools. Thorough scanning and validation are crucial to ensure complete removal. The process needs to be meticulously documented for auditing and future analysis.
Data Recovery and Business Continuity Planning
Data recovery is paramount after a ransomware attack. Regular backups, preferably stored offline or in a geographically separate location, are vital. A well-defined data recovery plan should Artikel the procedures for restoring data, testing the recovery process regularly, and prioritizing critical data. Business continuity planning goes hand-in-hand with data recovery. It involves establishing alternative ways to continue operations during an outage, such as using a disaster recovery site or cloud-based solutions.
This ensures minimal disruption to business operations.
Data centers are prime targets for ransomware attacks, leaving businesses scrambling to recover vital information. The shift to cloud environments only amplifies this risk, which is why understanding solutions like those discussed in this article on bitglass and the rise of cloud security posture management is crucial. Ultimately, proactive security measures are essential to mitigate the ever-present threat of ransomware crippling your data center operations.
Roles and Responsibilities During a Ransomware Incident
Effective incident response requires clear roles and responsibilities. The following table Artikels the key teams and their responsibilities:
| Team | Responsibilities | Contact Person | Escalation Path |
|---|---|---|---|
| Security Team | Incident detection, containment, eradication, forensic analysis, vulnerability remediation. | Chief Security Officer (CSO) | IT Director, CEO |
| IT Operations Team | System restoration, network recovery, application support. | IT Manager | IT Director, CIO |
| Legal Team | Compliance, regulatory reporting, legal advice, communication with law enforcement. | General Counsel | CEO |
| Communications Team | Internal and external communication, media relations, crisis management. | Communications Manager | CEO |
Technological Advancements and Future Trends: Data Centers Are Extremely Vulnerable To Ransomware Threats
The vulnerability of data centers to ransomware necessitates a proactive approach leveraging cutting-edge technologies. The future of data center security hinges on the integration of advanced systems and strategies that go beyond traditional methods. This involves harnessing the power of artificial intelligence, embracing emerging security technologies, and anticipating evolving ransomware tactics.AI and machine learning are transforming the landscape of cybersecurity, offering powerful tools for both prevention and detection.
These technologies are capable of analyzing vast amounts of data to identify anomalous behavior indicative of a ransomware attack, far exceeding the capabilities of human analysts alone. Furthermore, AI can automate responses to threats, significantly reducing the time it takes to contain an attack and minimize damage.
Artificial Intelligence and Machine Learning in Ransomware Mitigation
AI-powered security information and event management (SIEM) systems can correlate events across multiple sources, identifying subtle patterns that might indicate an impending ransomware attack. Machine learning algorithms can be trained to recognize the signatures of known ransomware strains and even predict new variations. This proactive approach allows for the implementation of preventative measures before an attack can fully materialize.
For example, an AI system might detect unusual login attempts from unfamiliar IP addresses, flag suspicious file transfers, or identify unusual spikes in network activity – all potential indicators of a ransomware infection. Real-time threat analysis coupled with automated responses provides a significant advantage in minimizing the impact of an attack.
Emerging Technologies Enhancing Data Center Security
Beyond AI, several other technologies are enhancing data center security. Blockchain technology, for example, can be used to create immutable records of data, making it more difficult for ransomware to encrypt and hold data hostage. Zero Trust security architectures assume no implicit trust and verify every user and device before granting access, significantly reducing the attack surface. Advanced threat detection systems utilizing behavioral analytics can identify malicious activity based on deviations from established baselines, catching attacks that might evade traditional signature-based detection methods.
Microsegmentation of networks limits the impact of a successful attack by isolating compromised systems, preventing the spread of ransomware throughout the data center.
Future Trends in Ransomware Attacks Targeting Data Centers
We can expect to see increasingly sophisticated and targeted ransomware attacks. Attackers are likely to focus on exploiting vulnerabilities in cloud-based infrastructure and leveraging AI to automate and personalize their attacks. Ransomware-as-a-service (RaaS) models will continue to proliferate, making it easier for less technically skilled individuals to launch devastating attacks. We will also likely see an increase in attacks targeting critical infrastructure, with the potential for significant societal disruption.
The rise of IoT devices within data centers expands the attack surface, presenting new challenges in securing these often-overlooked endpoints.
Visual Representation of Future Data Center Security
Imagine a data center visualized as a highly secured fortress. Instead of traditional walls and gates, this fortress is protected by layers of intelligent security systems. AI acts as the vigilant guard, constantly monitoring the network for suspicious activity. Blockchain technology forms an impenetrable vault, safeguarding sensitive data from unauthorized access. Zero Trust security acts as a sophisticated drawbridge, only granting access to verified entities.
Microsegmentation creates inner walls, isolating different sections of the fortress to contain any breaches. Advanced threat detection systems are the fortress’s radar, constantly scanning for incoming threats and providing early warnings. This multi-layered approach, utilizing advanced technologies, represents a robust defense against the ever-evolving threat of ransomware.
End of Discussion
The vulnerability of data centers to ransomware is a serious and evolving threat. While the risks are significant, effective mitigation strategies exist. By combining robust security measures, comprehensive employee training, and proactive incident response planning, organizations can significantly reduce their exposure. Staying informed about the latest threats and emerging technologies is crucial in this ongoing battle to protect our digital assets.
Remember, it’s not a matter of
-if* an attack will happen, but
-when*. Proactive preparation is the key to surviving and thriving in this increasingly dangerous digital landscape.
FAQ
What is the average cost of a ransomware attack on a data center?
The cost varies wildly depending on factors like the size of the organization, the amount of data encrypted, and the downtime experienced. However, it can easily run into millions of dollars, including ransom payments, recovery costs, and lost revenue.
How long does it typically take to recover from a data center ransomware attack?
Recovery time depends on the extent of the damage and the organization’s preparedness. It can range from days to weeks, or even months, in severe cases. Having a robust backup and recovery plan is crucial for minimizing downtime.
Are all ransomware attacks on data centers successful?
No, not all attacks are successful. Strong security measures, including multi-factor authentication, intrusion detection systems, and regular security audits, can significantly reduce the likelihood of a successful attack.
What is the role of insurance in mitigating ransomware risks?
Cybersecurity insurance can help cover some of the costs associated with a ransomware attack, such as ransom payments (though this is often discouraged), legal fees, and recovery expenses. However, it’s crucial to have a comprehensive security plan in place, as insurance alone is not a sufficient safeguard.