
New Domino REST APIs Are Now Available
New Domino REST APIs are now available, and this is HUGE news for developers and administrators alike! Imagine the possibilities: seamless integration with your existing systems, streamlined data access, and the power to build innovative applications using a modern, flexible approach. This blog post dives deep into these exciting new APIs, exploring their features, benefits, and how you can start using them today.
We’ll cover authentication, common endpoints, best practices, and even a simple application example to get you going.
Forget wrestling with outdated methods! These REST APIs offer a clean, efficient way to interact with Domino, opening up a world of opportunities for automation, integration, and modern application development. Whether you’re a seasoned Domino pro or just starting your journey, this guide will equip you with the knowledge you need to harness the power of these new APIs.
Introduction to New Domino REST APIs: New Domino Rest Apis Are Now Available
The wait is over! We’re thrilled to announce the release of our new Domino REST APIs, offering a modern and efficient way to interact with your Domino applications. These APIs provide a significant upgrade over previous methods, streamlining development and improving integration with other systems. This post will delve into the key features, benefits, and target audience for these powerful new tools.These APIs leverage the power of RESTful architecture, providing a standardized and intuitive interface for developers.
This means simpler integration with a wide range of applications and programming languages, making it easier than ever to build custom solutions leveraging your existing Domino data and functionality. The improved performance and scalability offered by the RESTful approach also allow for the creation of more robust and responsive applications.
Key Features and Functionalities, New domino rest apis are now available
The new Domino REST APIs offer a comprehensive set of functionalities, including the ability to create, read, update, and delete (CRUD) Domino data, manage users and groups, and interact with various Domino services. Specific features include support for JSON data exchange, efficient handling of large datasets, and robust error handling. Developers can seamlessly integrate these APIs into their workflows, leveraging existing Domino resources within modern application architectures.
The APIs are designed to be flexible and adaptable, allowing for customization to fit diverse application needs.
Benefits Compared to Previous Methods
Previously, interacting with Domino often involved using more complex and less standardized methods. The new REST APIs offer several key advantages. First, they significantly simplify the development process, reducing the complexity and time required to build integrations. Second, the improved performance and scalability allow for handling larger volumes of data and a greater number of concurrent users.
Third, the use of standard RESTful principles enhances interoperability with other systems, making it easier to integrate Domino into a broader IT landscape. The clear, well-documented API specification ensures developers can easily understand and use the functionalities provided.
Target Audience
These APIs are primarily targeted at developers seeking to build custom applications that interact with Domino data and functionality. However, system administrators will also find them useful for automating tasks and managing the Domino environment. Anyone familiar with RESTful APIs and JSON will find the transition straightforward. The intuitive design and comprehensive documentation make these APIs accessible to a wide range of technical skill levels.
API Authentication and Authorization
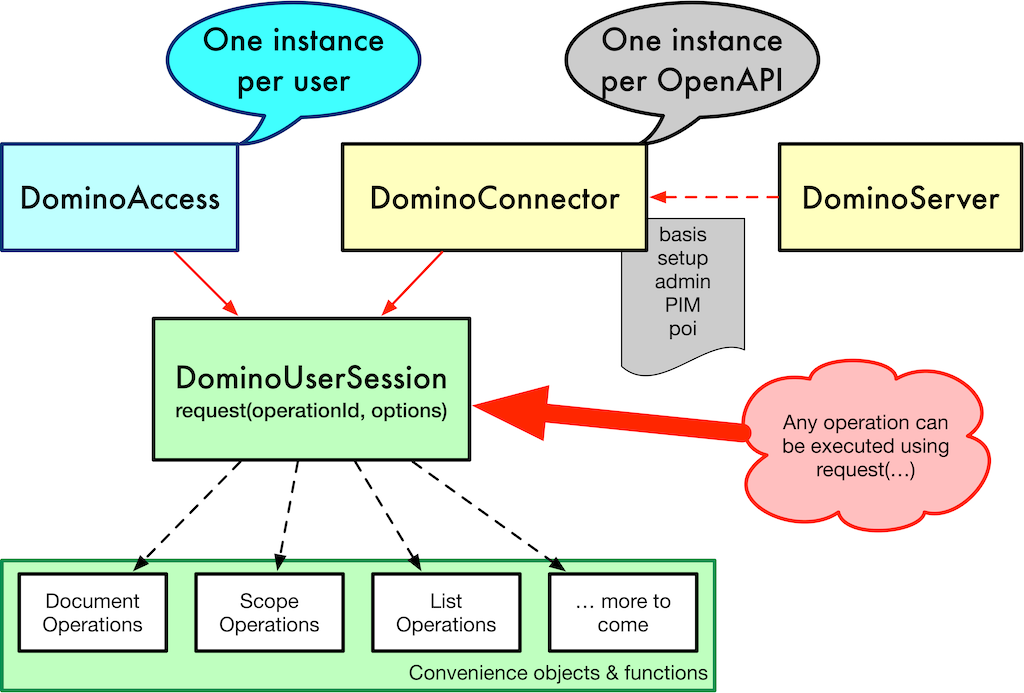
Securing your interactions with the new Domino REST APIs is paramount. This section details the authentication methods available and how authorization controls access to different API resources, ensuring only authorized users can perform specific actions. Understanding these mechanisms is crucial for building secure and robust applications that leverage the power of the Domino REST APIs.
Authentication Methods
The new Domino REST APIs support multiple authentication methods, allowing you to choose the approach best suited to your application’s security needs. These methods provide different levels of security and complexity, enabling flexibility in implementation.
Currently, the primary authentication method is API keys. An API key is a unique identifier that is assigned to your application. This key is included in the request header to authenticate your application to the Domino server. While relatively straightforward to implement, API keys should be treated with the same care as passwords, stored securely and never exposed directly in client-side code.
Consider using environment variables or secure configuration mechanisms to manage API keys.
Future releases may incorporate OAuth 2.0, a more robust and widely adopted authorization framework. OAuth 2.0 provides a more granular control over access, allowing you to grant specific permissions to your applications without sharing your user credentials directly. This enhances security and simplifies the management of application access.
Authorization Mechanisms
Authorization controls which API resources your application can access. This is typically achieved through roles and permissions assigned to users or applications. The Domino server verifies these permissions before granting access to a requested resource. Unauthorized attempts will result in an appropriate error response.
The level of access granted is determined by the assigned permission. For instance, a user with “Read” permission can only access resources that allow reading data, while a user with “Write” permission can read and modify data. A more fine-grained approach may be implemented in future versions to provide even more precise control over resource access.
| Permission Level | API Endpoint Examples |
|---|---|
| Read | /databases, /views, /documents (GET requests only) |
| Write | /databases/create, /documents (POST, PUT, DELETE requests), /views/update |
| Admin | /server/config, /security, /users (all requests) |
Common API Endpoints and Usage Examples
Now that we’ve covered the basics of authentication and authorization for the new Domino REST APIs, let’s dive into some practical examples. Understanding common endpoints is key to effectively leveraging these APIs for your applications. The following examples utilize curl for brevity and cross-platform compatibility, but the principles apply equally to other languages like Python. Remember to replace placeholders like `
Database Operations
These endpoints allow you to manage Domino databases, retrieving information and performing basic actions. Effective database management is crucial for any Domino application interacting with these APIs.
- Example 1: Retrieving a list of databases. This endpoint returns a JSON array containing information about all accessible databases.
curl -u <your_username>:<your_password> https://<your_server>/domino/api/databasesThe response will be a JSON array, each element representing a database with properties like its name, path, and creation date.
- Example 2: Getting information about a specific database. This endpoint retrieves detailed information about a single database.
curl -u <your_username>:<your_password> https://<your_server>/domino/api/databases/<database_name>The response provides comprehensive database details, including design elements, replica information, and more.
Document Management
These endpoints facilitate the creation, retrieval, updating, and deletion of documents within a specified database. Efficient document handling is essential for seamless data interaction.
- Example 3: Creating a new document. This example demonstrates creating a simple document with a few fields. The request body is a JSON object representing the document’s content.
curl -X POST -u <your_username>:<your_password> -H "Content-Type: application/json" -d '"Form": "MyForm", "Subject": "New Document", "Body": "This is a new document."' https://<your_server>/domino/api/databases/<database_name>/documentsThe response includes the newly created document’s UNID (Universal Note ID).
- Example 4: Updating an existing document. This endpoint modifies an existing document. The UNID identifies the target document, and the request body provides the updated data.
curl -X PUT -u <your_username>:<your_password> -H "Content-Type: application/json" -d '"Body": "This document has been updated."' https://<your_server>/domino/api/databases/<database_name>/documents/<unid>A successful response confirms the update.
- Example 5: Deleting a document. This endpoint removes a document from the database.
curl -X DELETE -u <your_username>:<your_password> https://<your_server>/domino/api/databases/<database_name>/documents/<unid>A successful response indicates successful deletion.
View Navigation
These endpoints allow interaction with Domino views, enabling querying and retrieving data based on view entries. Efficient view navigation is crucial for accessing and manipulating data organized within views.
- Example 6: Querying a view. This example retrieves entries from a specific view. Parameters can be added to refine the query (e.g., specifying a start and end key).
curl -u <your_username>:<your_password> https://<your_server>/domino/api/databases/<database_name>/views/<view_name>/entriesThe response will be a JSON array of view entries, each containing document UNIDs and other relevant information.
Error Handling and Best Practices
Successfully integrating the new Domino REST APIs into your applications requires a robust understanding of error handling and best practices for secure and efficient development. This section details common error codes, strategies for managing them, and guidelines for building reliable and secure applications.
Understanding how the APIs signal errors is crucial for building resilient applications. The APIs employ standard HTTP status codes to indicate success or failure. For instance, a 2xx status code signifies success, while 4xx codes indicate client-side errors (e.g., 400 Bad Request, 401 Unauthorized, 404 Not Found), and 5xx codes signal server-side errors (e.g., 500 Internal Server Error).
Each error response typically includes a JSON payload with details about the specific error, providing valuable context for debugging and user feedback.
Common Error Codes and Handling
The Domino REST APIs return various HTTP status codes to communicate the outcome of API requests. Effective error handling involves checking the status code of each response and acting accordingly. For example, a 401 Unauthorized response indicates authentication failure, requiring the application to re-prompt the user for credentials or handle the unauthorized access appropriately. A 404 Not Found response suggests the requested resource does not exist, and the application should inform the user of this issue.
Server-side errors (5xx codes) generally indicate problems with the API itself and might require contacting support or implementing retry mechanisms with exponential backoff. Detailed error messages within the JSON response body should be used for precise diagnostics.
Best Practices for Secure API Usage
Security is paramount when working with any API. These APIs employ various security mechanisms, including OAuth 2.0 for authentication and authorization. It is crucial to store and handle API keys and tokens securely, avoiding hardcoding them directly in the application code. Employing environment variables or secure configuration management tools is recommended. Always validate all user inputs received from API responses to prevent injection attacks (like SQL injection or cross-site scripting).
Rate limiting is another crucial consideration; implement logic to handle potential rate limits imposed by the API to prevent application disruptions. Regularly update your application to incorporate any security patches released for the APIs.
Best Practices for Efficient API Usage
Efficient API usage involves optimizing requests and responses to minimize latency and improve overall application performance. This includes using appropriate HTTP methods (GET for retrieval, POST for creation, PUT for updates, DELETE for removal), minimizing the number of requests, and using pagination for large datasets. Caching responses appropriately can reduce the load on the API and enhance the responsiveness of your application.
Consider using asynchronous requests where feasible to avoid blocking the user interface while waiting for API responses. Thorough testing under various load conditions is crucial to identify and address performance bottlenecks before deploying the application to production.
Structured List of Best Practices for API Usage
Effective use of the Domino REST APIs requires a structured approach. The following list summarizes key best practices:
- Always validate API responses for errors before processing the data.
- Implement proper error handling to gracefully manage various HTTP status codes.
- Securely store and manage API keys and authentication tokens.
- Validate all user inputs to prevent security vulnerabilities.
- Use appropriate HTTP methods for each operation.
- Employ pagination for large datasets to improve efficiency.
- Cache responses where appropriate to reduce API load.
- Consider asynchronous requests to enhance responsiveness.
- Implement rate limiting logic to prevent exceeding API limits.
- Conduct thorough testing under various load conditions.
Comparison with Other Domino APIs or Technologies
The introduction of Domino REST APIs represents a significant shift in how developers interact with the Domino platform. For years, developers relied primarily on Java APIs and LotusScript, each with its own strengths and weaknesses. This comparison highlights the key differences and helps developers choose the most appropriate approach for their specific needs. Understanding these distinctions is crucial for maximizing efficiency and leveraging the best features of the Domino ecosystem.
The following table provides a direct comparison of the new REST APIs against the older Java and LotusScript APIs. It focuses on ease of use, performance characteristics, and security considerations.
| Feature | REST API | Older Technologies (Java/LotusScript) |
|---|---|---|
| Ease of Use | REST APIs utilize standard HTTP methods (GET, POST, PUT, DELETE) and JSON or XML for data exchange, making them relatively easy to learn and use, especially for developers familiar with web technologies. The standardized approach simplifies integration with various client applications. | Java and LotusScript APIs require a deeper understanding of the Domino object model and specific API calls. Development often involves more complex code and a steeper learning curve, especially for developers new to the Domino platform. |
| Performance | Performance depends heavily on network latency and server load. However, REST APIs are generally efficient for data retrieval and manipulation, particularly when dealing with smaller datasets. | Java and LotusScript APIs can offer superior performance for complex tasks or large data processing, as they operate directly within the Domino server environment. However, poorly written code can negatively impact performance. The performance also depends on the specific implementation and optimization techniques employed. |
| Security | REST APIs benefit from standard HTTP security mechanisms like HTTPS, OAuth 2.0, and JWT for authentication and authorization. This allows for robust security controls and integration with existing security infrastructures. | Security in Java and LotusScript APIs relies on Domino’s built-in security features and proper access control within the code. While robust, it requires careful planning and implementation to ensure secure data handling. Misconfigurations can lead to vulnerabilities. |
| Platform Compatibility | REST APIs are inherently platform-agnostic. They can be accessed from any platform with HTTP capabilities, increasing flexibility and reducing dependencies on specific operating systems or development environments. | Java and LotusScript APIs are tightly coupled with the Domino environment. While Java offers some cross-platform capabilities, development and deployment are often restricted to the Domino server platform. |
| Scalability | REST APIs are generally more scalable due to their stateless nature and ability to handle concurrent requests effectively. Load balancing and caching strategies can further enhance scalability. | Scalability with Java and LotusScript APIs can be challenging, especially with complex applications. Careful design and resource management are essential for handling increased workloads. |
Advantages and Disadvantages Summary
Choosing between REST APIs and older technologies depends on the specific project requirements. REST APIs offer ease of use, broad platform compatibility, and improved scalability for many modern applications. However, older technologies might still be preferable for highly performance-critical tasks or applications requiring deep integration with existing Domino infrastructure where extensive legacy code already exists. A hybrid approach, leveraging the strengths of both, may be the optimal solution in certain scenarios.
Advanced API Usage and Capabilities

So far, we’ve covered the basics of using our new Domino REST APIs. Now let’s delve into some of the more advanced features that can significantly enhance your application’s capabilities and efficiency. These advanced features allow for real-time interactions and efficient handling of large datasets, moving beyond simple request-response cycles.The new APIs offer several advanced features, primarily focusing on enhanced real-time communication and efficient data handling.
This allows for the creation of more dynamic and responsive applications integrated with the Domino environment. We will explore WebSockets for real-time data streaming and efficient handling of large datasets.
WebSockets for Real-Time Data Streaming
WebSockets provide a persistent, bidirectional communication channel between the client and the server. This is a significant improvement over traditional RESTful approaches that rely on repeated polling for updates. Using WebSockets, the server can push updates to the client immediately, enabling real-time data synchronization and responsiveness.This technology is particularly useful in applications requiring immediate updates, such as dashboards displaying live data, collaborative editing tools, or chat applications integrated with Domino.
Consider a stock trading application needing immediate updates on price changes – WebSockets would be ideal for this scenario.Here’s a simplified code example (conceptual, language-agnostic) illustrating a WebSocket connection and data handling:“`//Establish WebSocket connectionwebsocket = new WebSocket(“ws://api.example.com/websocket”);//Handle messages from serverwebsocket.onmessage = function(event) let data = JSON.parse(event.data); //Process received data console.log(“Received data:”, data); updateDashboard(data); //Example function to update a dashboard;//Send data to the server (optional)websocket.send(JSON.stringify(“action”: “subscribe”, “topic”: “stock_prices”));“`This example shows a basic connection, message handling, and data sending.
Error handling and connection management are crucial aspects to be addressed in a production environment. Remember to consult the detailed API documentation for specific implementation details and security considerations.
Efficient Handling of Large Datasets
For applications dealing with extensive data, the APIs offer mechanisms to handle large datasets efficiently, avoiding overwhelming the client with single, massive responses. These mechanisms may involve pagination, streaming responses, or other optimized data transfer methods. This is crucial for applications that need to handle a large volume of data without compromising performance. Imagine an application needing to display thousands of documents from a Domino database; optimized data transfer methods are essential to avoid delays and improve user experience.
The specific implementation will depend on the API endpoint and its capabilities. Consult the API documentation for details on how to use these optimized methods.
Illustrative Scenario: Building a Simple Mobile App for Domino Data Access
This section details the creation of a simple mobile application leveraging the new Domino REST APIs. The app will allow users to view a list of names and associated phone numbers from a Domino view. This example focuses on core functionality and omits advanced features like offline capabilities or complex data manipulation.
Application Design and Architecture
The application will adopt a three-tier architecture: a client-side mobile interface (using a framework like React Native or Flutter), a REST API layer interacting with the Domino server, and the Domino server itself containing the data. The mobile app will make HTTP requests to the Domino REST API endpoints to retrieve and display the data. Error handling will be implemented to gracefully manage potential network issues or API failures.
API Calls and Data Retrieval
The core functionality revolves around a single API call to retrieve data from a specific Domino view. This call will utilize a GET request to a dedicated endpoint, likely structured as `/names_and_phones`, which returns a JSON representation of the view entries. The response will be parsed on the client-side to extract the name and phone number fields. For example, a successful response might look like this: `[“name”: “John Doe”, “phone”: “555-1212”, “name”: “Jane Smith”, “phone”: “555-3434”]`.
Authentication will be handled using API keys or OAuth 2.0, depending on the chosen security mechanism.
Data Processing and User Interface
The retrieved JSON data will be processed on the client-side to populate a user-friendly list view. Each list item will display a name and its corresponding phone number. The user interface will be designed for optimal readability and usability on mobile devices, with clear visual separation between items. The app will handle potential errors, such as empty responses or network connectivity problems, by displaying appropriate messages to the user.
For instance, if no data is returned, the app might show a message stating “No entries found”.
User Experience
The user experience will be straightforward. Upon launching the application, the user will see a list of names and phone numbers fetched from the Domino server. The list will be easily scrollable. No user input is required beyond launching the application. The app will be designed to be intuitive and easy to navigate, requiring minimal user interaction.
The focus is on providing a clean and efficient way to access the Domino data.
End of Discussion
The arrival of the new Domino REST APIs marks a significant leap forward in how we interact with Domino. By offering a modern, standardized approach to data access, these APIs unlock countless possibilities for developers and administrators. We’ve covered authentication, common endpoints, best practices, and even a glimpse into building a simple application. Now it’s your turn! Dive in, explore the possibilities, and build the next generation of Domino applications.
The future of Domino interaction is here, and it’s RESTful!
FAQ Corner
What is the difference between API keys and OAuth 2.0 for authentication?
API keys are simpler, offering a single key for authentication. OAuth 2.0 provides more granular control and security, especially useful for applications needing varying levels of access.
Are these APIs compatible with older versions of Domino?
Compatibility depends on the specific Domino server version. Check the official documentation for supported versions.
What kind of error codes can I expect?
You’ll likely encounter standard HTTP status codes (like 404 for not found or 500 for server errors), along with potentially Domino-specific error codes detailed in the API documentation.
Where can I find comprehensive documentation?
The official HCL Domino documentation will be your best resource. Look for the section dedicated to the REST APIs.
