Defending Against Business Email Compromise A Comprehensive Guide
Defending against business email compromise a comprehensive guide – Defending against business email compromise: a comprehensive guide. That’s a mouthful, isn’t it? But it’s a crucial topic for any business, big or small. We’re talking about sophisticated scams that can drain your bank account and damage your reputation faster than you can say “phishing.” This guide isn’t just another dry security manual; it’s your survival kit in the wild west of online threats.
We’ll dissect the various types of attacks, explore practical defense strategies, and even walk you through building a rock-solid incident response plan. Get ready to upgrade your cybersecurity game!
From understanding the psychology behind these attacks to implementing robust technical safeguards, we’ll cover everything you need to know to protect your business from BEC. We’ll explore email authentication protocols like SPF, DKIM, and DMARC, delve into the importance of employee training, and discuss advanced threat protection measures. We’ll also show you how to navigate the often-confusing world of incident response and working with law enforcement.
Think of this as your go-to resource for staying ahead of the curve and keeping your business safe.
Understanding Business Email Compromise (BEC)
Business Email Compromise (BEC) attacks are sophisticated phishing scams targeting organizations to trick employees into transferring money or sensitive data. These attacks exploit trust and leverage legitimate-looking emails to deceive victims. Understanding the various types, tactics, and motivations behind BEC is crucial for effective prevention.
Types of BEC Attacks and Common Tactics
BEC attacks manifest in several forms, each employing different tactics to achieve the same goal: financial gain or data theft. A common tactic involves compromising legitimate email accounts, impersonating executives or vendors to request wire transfers or sensitive information. Another tactic involves creating convincing fake email addresses that closely resemble legitimate ones. The attacker might also use spoofed domain names to further enhance the legitimacy of their communication.
These attacks often rely on a sense of urgency to pressure the victim into acting quickly without verifying the request.
Motivations Behind BEC Attacks
The primary motivation behind BEC attacks is financial gain. Attackers seek to exploit vulnerabilities in organizational processes to steal money directly or gain access to valuable assets. Data breaches, facilitated through BEC, can also lead to secondary financial losses through identity theft, reputational damage, and regulatory fines. The relative ease of execution, combined with the potential for substantial financial returns, makes BEC an attractive avenue for cybercriminals.
So you’re looking for a comprehensive guide on defending against business email compromise? That’s smart! A key aspect of that defense involves strong cloud security, which is why understanding tools like Bitglass is crucial. Check out this great article on bitglass and the rise of cloud security posture management to see how it fits into a robust BEC defense strategy.
Ultimately, a multi-layered approach, including strong cloud security, is the best way to protect your business from these sophisticated attacks.
Real-World BEC Incidents and Their Impact
Numerous high-profile BEC incidents have resulted in significant financial losses for organizations worldwide. For example, a well-documented case involved a manufacturing company that lost millions of dollars after an attacker impersonated the CEO, requesting an urgent wire transfer to a fraudulent account. The impact of such attacks extends beyond monetary losses; they can severely damage an organization’s reputation, erode trust with stakeholders, and disrupt business operations.
The legal and regulatory consequences can also be substantial, leading to investigations and penalties.
BEC Attack Vectors
The following table summarizes different vectors used in BEC attacks:
| Attack Vector | Description | Example | Mitigation |
|---|---|---|---|
| Account Takeover | Attackers gain access to a legitimate email account to send fraudulent requests. | Compromising a finance manager’s email to request a wire transfer. | Multi-factor authentication (MFA), strong passwords, regular security awareness training. |
| Email Spoofing | Attackers create emails that appear to come from a legitimate sender (e.g., CEO, vendor). | Sending an email that mimics the CEO’s email address to request payment. | Email authentication protocols (SPF, DKIM, DMARC), careful email verification. |
| Domain Spoofing | Attackers register a domain name that closely resembles a legitimate one. | Registering a domain like “googIe.com” (with an “l” instead of a “g”) to create fake invoices. | Careful examination of email addresses and domain names, DNSSEC. |
| Phishing | Attackers use deceptive emails to trick employees into revealing credentials or sensitive information. | Sending an email with a malicious link that redirects to a fake login page. | Security awareness training, robust phishing detection systems. |
Implementing Strong Email Authentication: Defending Against Business Email Compromise A Comprehensive Guide
Email authentication is your first line of defense against Business Email Compromise (BEC) attacks. Without robust authentication, malicious actors can easily spoof your legitimate email addresses, making it incredibly difficult for recipients to distinguish genuine communications from fraudulent ones. Implementing strong email authentication protocols is crucial for building trust and protecting your organization from BEC attacks and other email-borne threats.
SPF (Sender Policy Framework) Record Implementation
SPF is a DNS-based mechanism that allows you to specify which mail servers are permitted to send emails on behalf of your domain. By publishing an SPF record, you tell receiving mail servers which IP addresses or domains are authorized to send email using your domain name. This helps prevent email spoofing by blocking emails that appear to come from your domain but are actually sent from unauthorized servers.
A properly configured SPF record significantly reduces the risk of BEC attacks that leverage spoofed sender addresses.To implement SPF, you need to create a TXT record in your DNS settings. This record contains a list of authorized sending servers, typically expressed as IP addresses or domain names. For example: v=spf1 ip4:192.0.2.1 ip4:10.0.0.1 include:mail.example.com ~all. This record specifies that only emails from the IP addresses 192.0.2.1 and 10.0.0.1, and emails sent from servers within the mail.example.com domain, are authorized to send emails on behalf of your domain.
The `~all` mechanism indicates that emails from other sources should be treated as soft failures (meaning they might be delivered, but with a warning). Using `-all` instead would result in a hard fail for unauthorized senders. Careful consideration should be given to the specific needs of your email infrastructure when choosing between `~all` and `-all`.
So, you’re looking for ways to beef up your defenses against business email compromise? A comprehensive guide is definitely needed, covering everything from multi-factor authentication to employee training. But strong security also means leveraging modern tech, like the innovative approaches discussed in this article on domino app dev the low code and pro code future , which can help streamline processes and reduce vulnerabilities.
Ultimately, a layered approach to security, combined with efficient workflows, is your best bet against BEC attacks.
DKIM (DomainKeys Identified Mail) Record Implementation
DKIM uses public-key cryptography to verify the authenticity of emails sent from your domain. It adds a digital signature to your outgoing emails, allowing receiving mail servers to verify that the email hasn’t been tampered with during transit. This is crucial because BEC attacks often involve modifying the content of legitimate emails to deceive recipients. DKIM helps prevent these modifications from going undetected.Implementing DKIM involves generating a public and private key pair.
The public key is published in a DNS TXT record, while the private key is kept secret on your mail server. Your mail server uses the private key to sign outgoing emails, and receiving mail servers use the public key to verify the signature. The exact steps for generating and configuring DKIM keys vary depending on your email provider and server software.
Most email providers offer tools and documentation to simplify this process. A typical DKIM record might look like this: v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQ... (Note: the `p=` value would contain a long string of characters representing the public key).
DMARC (Domain-based Message Authentication, Reporting & Conformance) Record Implementation
DMARC builds upon SPF and DKIM by providing a policy for how receiving mail servers should handle emails that fail SPF and/or DKIM checks. It allows you to specify whether to quarantine or reject emails that don’t pass authentication. This is essential for actively protecting your organization from spoofing attempts. DMARC empowers you to define your policy (reject, quarantine, or none), enabling a strong defense against BEC and phishing attacks.To implement DMARC, you create a TXT record in your DNS settings.
This record specifies your policy (e.g., `p=reject`), as well as the email address where you want to receive authentication reports (`rua=` and `ruf=`). The reports provide valuable insights into email authentication failures, allowing you to identify and address potential vulnerabilities. A sample DMARC record: v=DMARC1; p=quarantine; rua=mailto:[email protected];. Starting with `p=quarantine` is generally recommended to allow time to analyze reports before implementing a `p=reject` policy.
Managing Email Authentication Across Multiple Domains
Managing email authentication across multiple domains requires careful coordination and a consistent approach. You’ll need to implement SPF, DKIM, and DMARC for each domain, ensuring that the records are properly configured and aligned. Centralized management tools can significantly simplify this process, particularly for larger organizations with numerous domains. Consider using a DNS management platform that allows for bulk updates and consistent policy application across all your domains.
Regular monitoring of authentication reports is also crucial to ensure the effectiveness of your email security measures and identify any emerging issues.
Employee Training and Awareness
Protecting your business from BEC attacks requires more than just technical safeguards; it demands a vigilant and well-trained workforce. Employees are often the first line of defense, and their awareness and ability to identify suspicious emails are crucial in preventing successful attacks. A comprehensive training program is essential to equip your staff with the knowledge and skills necessary to combat BEC threats.
Effective employee training goes beyond simply sending out a single email. It should be an ongoing process, incorporating regular updates, refresher courses, and interactive exercises to maintain a high level of awareness and alertness. This multifaceted approach ensures that employees remain vigilant against the ever-evolving tactics used in BEC attacks.
BEC Attack Red Flags
A robust training module should highlight the common red flags associated with BEC attacks. These red flags can help employees quickly identify suspicious emails and avoid becoming victims. Training should emphasize the importance of verifying requests, even those that appear to come from trusted sources.
The following are some key indicators of a potential BEC attack:
- Urgent requests: Emails demanding immediate action, often with threats of consequences if the request isn’t fulfilled promptly.
- Unusual tone or language: A change in the usual communication style of a known sender, such as unexpected informality or grammatical errors.
- Suspicious email addresses: Slight variations in the sender’s email address, often involving extra characters or a different domain name.
- Requests for wire transfers or other urgent payments: Unexpected requests for large sums of money, especially to unfamiliar accounts.
- Unverified requests for personal information: Emails requesting sensitive data like passwords, social security numbers, or banking details.
- Unexpected attachments: Attachments that are not expected or that seem unusual for the sender.
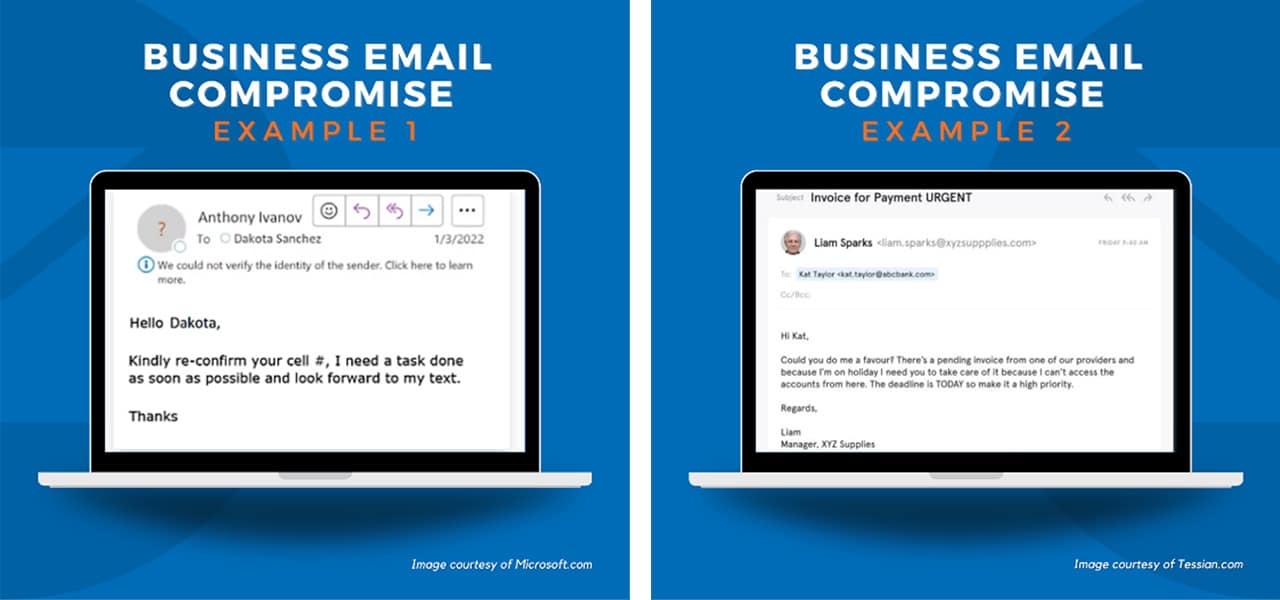
Examples of Phishing Emails
Practical examples are key to effective training. Employees should be shown real-world examples of phishing emails used in BEC attacks, highlighting the subtle differences that can indicate a fraudulent message.
Here are two examples:
Example 1: An email seemingly from the CEO, requesting an urgent wire transfer to a new vendor account. The email might contain slight misspellings or grammatical errors, and the sender’s email address may have a minor variation, such as a misplaced letter or number. The urgency of the request is designed to bypass normal verification processes.
Example 2: An email from a seemingly legitimate business partner, requesting a change in payment details. The email might contain a slightly altered link to a fake website, designed to steal login credentials or other sensitive information. The email might also include a sense of urgency to pressure the recipient into acting quickly.
Role-Playing Scenario: Handling Suspicious Emails
Role-playing exercises provide a safe environment for employees to practice their response to suspicious emails. These exercises should simulate real-life scenarios and allow employees to develop confidence in their ability to handle such situations.
Scenario: An employee receives an email that appears to be from their manager, requesting a large wire transfer to an unfamiliar account. The email is urgent and threatens disciplinary action if the request is not fulfilled immediately. The employee should practice verifying the request through multiple channels, such as calling the manager directly using a known phone number, before taking any action.
Best Practices for Handling Emails Requesting Sensitive Information
Employees need clear guidelines on how to handle emails requesting sensitive information. These guidelines should emphasize the importance of verification and caution.
The following are some best practices:
- Verify the sender: Always verify the sender’s identity through an independent channel, such as a phone call or a separate email.
- Never provide sensitive information via email: Sensitive data should never be shared via email, especially passwords, financial information, or social security numbers.
- Check the email address carefully: Examine the sender’s email address for any inconsistencies or unusual characters.
- Report suspicious emails: Report any suspicious emails to the IT department immediately.
- Do not click on links or open attachments from unknown sources: This is crucial to avoid malware infections and phishing attacks.
Securing Internal Systems and Processes
Protecting your internal systems and processes is crucial in preventing BEC attacks. A successful BEC attack often relies on exploiting weaknesses within an organization’s internal infrastructure, not just its email security. Strengthening these internal defenses significantly reduces the likelihood of a successful compromise.Internal vulnerabilities can act as entry points for BEC attackers, even if your email security is robust.
These vulnerabilities can range from weak password policies to inadequate access controls and a lack of verification procedures for financial transactions. Addressing these weaknesses is paramount to a comprehensive BEC defense strategy.
Vulnerability Identification in Internal Systems
Identifying vulnerabilities requires a proactive approach. This involves regular security audits and penetration testing to simulate real-world attacks and pinpoint weaknesses. A thorough assessment should cover all aspects of your internal network, including servers, workstations, and applications used for financial transactions. Regular software updates and patching are also critical to mitigate known vulnerabilities exploited by BEC attackers. For example, outdated accounting software might contain security flaws that allow attackers to manipulate financial data or initiate fraudulent wire transfers.
Furthermore, a lack of network segmentation can allow attackers to move laterally within the network after initially compromising a single system.
Multi-Factor Authentication (MFA) Implementation, Defending against business email compromise a comprehensive guide
Multi-factor authentication (MFA) adds an extra layer of security to all accounts, significantly reducing the risk of unauthorized access. Even if an attacker obtains a username and password, they will still need access to a second factor, such as a one-time code from an authentication app or a physical security key. Implementing MFA across all accounts, including email, financial systems, and cloud services, is a vital step in mitigating BEC threats.
For example, requiring MFA for access to the company’s accounting software would significantly hinder an attacker’s ability to initiate fraudulent transactions even if they’ve compromised an employee’s email account.
Strong Password Policies and Regular Password Changes
Strong password policies are essential. These policies should mandate the use of complex passwords with a minimum length, a mix of uppercase and lowercase letters, numbers, and symbols, and should prohibit the reuse of passwords across different accounts. Regular password changes, enforced by the system, further reduce the risk of compromised credentials. For instance, a policy requiring password changes every 90 days, coupled with password complexity requirements, makes it much harder for attackers to use brute-force or credential stuffing techniques.
Verification Procedures for Financial Transactions
Establishing robust verification procedures for wire transfers and other financial transactions is crucial. These procedures should include multiple levels of authorization, independent verification of payment instructions, and potentially the use of dedicated secure communication channels for sensitive financial information. For example, requiring two authorized personnel to approve all wire transfers above a certain threshold, and verifying the recipient’s bank details through an independent source before initiating the transfer, can significantly reduce the risk of BEC-related financial losses.
Implementing a dual-control system, where two individuals must approve each transaction, is another effective measure.
Incident Response Planning
A robust incident response plan is crucial for minimizing the damage caused by a Business Email Compromise (BEC) attack. Without a pre-defined plan, organizations often react haphazardly, potentially exacerbating the situation and increasing financial losses. A well-structured plan ensures a coordinated and efficient response, enabling faster recovery and improved security posture.Having a documented incident response plan is not merely a best practice; it’s a necessity in today’s threat landscape.
The cost of a successful BEC attack can be devastating, impacting not only finances but also reputation and customer trust. A proactive approach, involving clear procedures and designated personnel, can significantly mitigate these risks.
Incident Response Plan Steps
The following steps Artikel a comprehensive incident response plan for suspected BEC attacks. This plan should be regularly reviewed and updated to reflect evolving threats and organizational changes. Remember, speed and decisiveness are paramount in containing the damage.
- Detection and Initial Response: Upon suspicion of a BEC attack (e.g., an unusual wire transfer request, a phishing email mimicking a senior executive), immediately isolate the compromised account and prevent further unauthorized access. This might involve changing passwords, disabling the account, and notifying the IT security team.
- Containment: The primary goal is to prevent further financial losses and data breaches. This involves freezing any affected accounts, contacting financial institutions to halt any suspicious transactions, and assessing the extent of the compromise. This may include examining email logs, network traffic, and system activity logs.
- Eradication: Once the immediate threat is contained, the next step is to remove the malware or malicious code that facilitated the attack. This may involve reinstalling operating systems, scanning for malware, and patching vulnerabilities. A thorough forensic analysis might be necessary to identify the root cause of the breach.
- Recovery: This involves restoring affected systems and data from backups, ensuring business continuity, and implementing security measures to prevent future attacks. This stage also involves communicating with affected parties, such as customers or business partners.
- Post-Incident Activity: This involves analyzing the incident to identify vulnerabilities, improve security controls, and update the incident response plan. This step is crucial for preventing similar incidents in the future. It also includes documenting the incident thoroughly for future reference and reporting to relevant authorities.
Containing Damage and Investigating the Incident
Containing the damage involves swift action to limit the financial and reputational impact. This includes immediately contacting financial institutions to stop any fraudulent transactions, reviewing all recent financial transactions for suspicious activity, and securing all affected accounts. The investigation should focus on determining the attack vector, the extent of the compromise, and the identity of the perpetrators. This often involves analyzing email logs, network traffic, and system logs to reconstruct the attack timeline and identify any compromised credentials.
Forensic analysis may be required to identify malware or other malicious code.
Reporting BEC Incidents to Law Enforcement
Reporting BEC incidents to law enforcement is crucial for assisting in investigations and potentially recovering lost funds. Gather all relevant information, including email headers, transaction details, and any other evidence related to the attack. Contact your local FBI field office or the Internet Crime Complaint Center (IC3) to file a report. Provide detailed information about the incident, including the date, time, and method of the attack, as well as any financial losses incurred.
Cooperation with law enforcement is essential in combating BEC attacks.
Post-Incident Review Checklist
A post-incident review is critical for improving security measures and preventing future incidents. This checklist provides a framework for conducting a thorough review:
- Review incident timeline: Analyze the sequence of events to identify vulnerabilities and areas for improvement.
- Assess damage: Quantify the financial and reputational losses incurred.
- Identify root cause: Determine the vulnerabilities that allowed the attack to occur.
- Implement corrective actions: Develop and implement measures to address identified vulnerabilities.
- Update incident response plan: Revise the plan to reflect lessons learned from the incident.
- Employee training: Conduct refresher training on phishing awareness and security best practices.
- System updates: Ensure all systems are up-to-date with the latest security patches.
- Document findings: Create a detailed report summarizing the incident, its impact, and the corrective actions taken.
Advanced Threat Protection Measures
Business Email Compromise (BEC) attacks are sophisticated and constantly evolving, demanding more than basic email security. Advanced threat protection goes beyond simple spam filters and requires a multi-layered approach incorporating robust technologies and proactive strategies to effectively neutralize these threats. This section explores the crucial role of advanced technologies in preventing BEC attacks.Email security solutions are the first line of defense against BEC attacks.
They act as a gatekeeper, analyzing incoming and outgoing emails for malicious content and suspicious activity. A robust solution isn’t just about blocking spam; it’s about actively identifying and neutralizing sophisticated threats designed to bypass traditional security measures. The effectiveness of these solutions hinges on their ability to adapt to the ever-changing tactics used in BEC attacks.
Email Security Technologies: Sandboxing and Anti-Phishing
Sandboxing technology operates by isolating potentially malicious emails in a virtual environment before they reach the user’s inbox. This allows the system to analyze the email’s behavior and attachments without exposing the organization’s network to potential harm. In contrast, anti-phishing solutions focus on identifying and blocking emails that employ deceptive tactics, such as impersonating legitimate organizations or individuals.
While both technologies are crucial, sandboxing offers a more comprehensive approach by analyzing the dynamic behavior of the email, while anti-phishing primarily relies on static analysis and pattern recognition. Effective BEC defense often necessitates a combination of both, providing a layered approach to security.
Advanced Threat Intelligence Feeds
Advanced threat intelligence feeds provide real-time information about emerging threats, including known malicious email addresses, URLs, and file hashes associated with BEC attacks. These feeds are invaluable for proactively identifying and blocking malicious emails before they even reach the organization’s network. By integrating threat intelligence feeds into email security solutions, organizations can significantly enhance their ability to detect and prevent BEC attacks, staying ahead of the curve in the ever-evolving landscape of cyber threats.
For example, a feed might alert the system to block emails originating from a server known to be used in recent BEC campaigns targeting similar businesses.
Security Tools and Technologies for BEC Defense
The effectiveness of defending against BEC attacks relies on a comprehensive suite of tools. Implementing just one or two solutions is insufficient; a multi-layered approach is crucial.
- Email Security Gateway (ESG): Acts as the first line of defense, filtering spam, malware, and phishing attempts.
- Sandboxing: Isolates suspicious emails and attachments in a virtual environment for safe analysis.
- Anti-phishing Solutions: Identifies and blocks emails using deceptive tactics, including URL analysis and header inspection.
- Advanced Threat Protection (ATP): Uses machine learning and behavioral analysis to detect sophisticated threats.
- Security Information and Event Management (SIEM): Collects and analyzes security logs from various sources to detect anomalies and security breaches.
- Data Loss Prevention (DLP): Prevents sensitive data from leaving the organization’s network via email.
- Multi-Factor Authentication (MFA): Adds an extra layer of security to email accounts, making it more difficult for attackers to gain unauthorized access.
- Threat Intelligence Platforms: Provide real-time information on emerging threats and allow for proactive threat hunting.
Regular Security Audits and Assessments
Regular security audits and assessments are crucial for maintaining a robust defense against Business Email Compromise (BEC) and other cyber threats. They provide a systematic way to identify vulnerabilities, assess risks, and ensure your security measures are effective. Without them, your organization is essentially flying blind, leaving itself open to exploitation.Proactive identification of weaknesses is far more cost-effective than reacting to a breach.
A well-structured audit program allows for the continuous improvement of your security posture, minimizing the impact of potential attacks.
The Security Audit Process
A comprehensive security audit typically involves several phases. First, a scoping phase defines the specific systems, applications, and processes to be reviewed. This is followed by data collection, where information is gathered through various methods such as interviews, document reviews, and vulnerability scans. Next, the collected data is analyzed to identify vulnerabilities and risks. Finally, a report is generated detailing the findings, including recommendations for remediation.
The entire process should be documented meticulously, providing a clear audit trail.
Key Areas to Focus On During Audits
During security audits related to BEC prevention, several key areas require particular attention. These include email authentication protocols (SPF, DKIM, DMARC), the security of email servers and gateways, employee access controls, and the effectiveness of security awareness training programs. The audit should also assess the organization’s incident response plan and its ability to handle a BEC attack. Furthermore, the review should extend to the security of internal systems and processes that handle financial transactions, ensuring strong access controls and regular monitoring for suspicious activity.
Finally, the review of third-party vendors and their security practices is essential, as they can represent a significant point of vulnerability.
Using Audit Results to Improve Security Posture
The results of a security audit should be treated as a roadmap for improvement. Each identified vulnerability should be prioritized based on its potential impact and likelihood of exploitation. A remediation plan should be developed and implemented, addressing the most critical vulnerabilities first. This plan should include timelines, responsibilities, and a mechanism for tracking progress. Regular follow-up audits are essential to verify the effectiveness of the implemented remediation measures and to identify any new vulnerabilities that may have emerged.
Examples of Security Audit Reports and Key Findings
While specific audit reports are confidential and vary depending on the organization, common findings often include weaknesses in email authentication, outdated security software, insufficient employee training, and inadequate incident response planning. For example, a report might highlight a lack of DMARC implementation, making the organization vulnerable to spoofing attacks. Another might reveal that employees are still clicking on phishing links, indicating a need for improved security awareness training.
A third might point to a lack of multi-factor authentication (MFA) for critical accounts, increasing the risk of unauthorized access. These findings would then be used to create specific remediation plans, such as implementing DMARC, improving training materials, and enforcing MFA. A well-structured report will clearly Artikel the severity of each finding, its potential impact, and recommended remediation steps.
Working with Law Enforcement
Reporting a Business Email Compromise (BEC) incident to law enforcement is a crucial step in mitigating losses and potentially recovering stolen funds. The sooner you report, the better the chances of a successful investigation and recovery. Remember, law enforcement agencies are equipped to handle these complex cybercrimes and can provide valuable support throughout the process.The process of reporting a BEC incident typically involves contacting your local FBI field office or the Internet Crime Complaint Center (IC3).
You’ll need to provide comprehensive information to help them build a case and potentially trace the perpetrators. While procedures may vary slightly depending on your location, the core elements remain consistent. Prompt action is key; delays can hinder investigations.
Information Required by Law Enforcement
Law enforcement agencies will require detailed information about the BEC incident to initiate an investigation. This includes specifics about the fraudulent emails, the financial transactions involved, and any supporting documentation. Thorough documentation significantly improves the chances of recovery.
- Details of the fraudulent emails: This includes the email headers, sender information, subject lines, body content, and any attachments. Saving these emails in their original format, without altering them, is crucial.
- Financial transaction details: This involves providing information about the wire transfers, payment details, account numbers, and any supporting documentation such as bank statements or transaction records. Specific details on the amount lost and the recipient accounts are vital.
- Information about the compromised accounts: This includes the email addresses, usernames, and passwords associated with the compromised accounts. It’s also helpful to provide details about any security measures in place at the time of the compromise.
- Information about the victim: This includes the name, address, contact information, and any other relevant details about the organization or individual who was targeted by the BEC attack.
Recovering Lost Funds
Recovering lost funds after a BEC attack is challenging but not impossible. The success rate depends on several factors, including the speed of reporting, the cooperation of financial institutions, and the effectiveness of law enforcement investigations. However, a prompt response and detailed documentation significantly increase the chances of recovery.The process often involves working closely with law enforcement and your financial institution.
Law enforcement may issue subpoenas to financial institutions to trace the flow of funds and identify the perpetrators. Some financial institutions have specialized fraud departments that can assist in the recovery process. However, there are no guarantees, and the recovery process can be lengthy and complex. Patience and persistence are vital.
Resources Available for Victims of BEC Attacks
Several resources are available to assist victims of BEC attacks. These resources provide support, guidance, and information to help navigate the recovery process.
- The Internet Crime Complaint Center (IC3): This is the FBI’s online portal for reporting internet-related crimes, including BEC attacks. The IC3 provides a centralized platform for reporting and tracking these incidents.
- Your local FBI field office: Directly contacting your local FBI field office allows for a more personalized approach and potentially faster response times.
- Financial institutions: Many financial institutions have specialized fraud departments that can assist with recovering lost funds. It’s crucial to report the incident to your bank immediately.
- Cybersecurity professionals: Engaging a cybersecurity professional can provide valuable assistance in investigating the attack, improving security measures, and preventing future incidents.
Illustrating Common BEC Tactics

Understanding the tactics employed in Business Email Compromise attacks is crucial for effective prevention. BEC attacks rely on deception and exploiting human trust, often targeting specific individuals within an organization. Let’s examine three common scenarios to illustrate these tactics.
CEO Fraud Attack
Imagine this: Sarah, the accounts payable manager at a mid-sized manufacturing company, receives an email seemingly from her CEO, John Smith. The email is addressed from a slightly altered email address – [email protected] instead of the usual [email protected]. The email is urgent, requesting an immediate wire transfer of $50,000 to a foreign account for an “urgent acquisition.” The email includes details mimicking John’s typical communication style, even referencing an ongoing project they discussed last week.
The attacker’s method relies on the urgency and authority implied by the CEO’s name, bypassing normal approval processes. The subtle email address alteration is easily overlooked under pressure. Sarah, believing the email to be legitimate, processes the wire transfer, only to discover later that the CEO never sent the email and the money is lost.
Compromised Account Attack
In this scenario, David, a sales manager, has his company email account compromised through a phishing attack. The attacker gains access by tricking David into clicking a malicious link in an email that appeared to be from his bank. This link downloads malware onto his computer, granting the attacker access to his email account. The attacker then monitors David’s email communications for several days, learning about upcoming transactions and business relationships.
Once they identify a suitable opportunity, they send an email to a client, impersonating David, requesting a change in payment details. The email appears authentic, utilizing David’s signature and communication style, successfully redirecting a payment of $10,000 to the attacker’s account. The fraud goes undetected until the client contacts David directly, questioning the altered payment instructions.
Fake Invoice Attack
This scenario involves a fake invoice scam targeting the finance department. The attacker sends an email to the accounts payable department with an attached invoice for goods or services supposedly provided to the company. The invoice appears legitimate, mimicking the branding and formatting of a genuine supplier. However, the bank details on the invoice are altered, directing the payment to the attacker’s account.
The email content might include a subtle sense of urgency, perhaps mentioning a late payment fee or a discount for prompt payment. The attacker’s social engineering tactic relies on the recipient’s familiarity with regular supplier invoices and their tendency to process them quickly without detailed scrutiny. The finance department, seeing the invoice as seemingly authentic, processes the payment, unaware that they are transferring funds to a fraudulent account.
Closing Notes
So, there you have it – a comprehensive look at defending against business email compromise. It’s not a one-size-fits-all solution, but by implementing the strategies Artikeld here – from strengthening your email authentication to empowering your employees with the knowledge to spot suspicious emails – you’ll significantly reduce your vulnerability. Remember, staying vigilant and proactively adapting your security measures is key to surviving in today’s ever-evolving threat landscape.
Don’t wait until it’s too late; start protecting your business today!
FAQ
What is the average cost of a BEC attack?
The average cost varies greatly depending on the size of the business and the scale of the attack, but it can range from thousands to millions of dollars in losses.
Can insurance cover BEC losses?
Some insurance policies cover losses from BEC attacks, but coverage can vary significantly. It’s crucial to review your policy carefully.
How long does it typically take to recover from a BEC attack?
Recovery time depends on the severity of the attack and the resources available. It can range from weeks to months, involving legal, financial, and IT recovery efforts.
Are there any free tools to help detect BEC attempts?
While comprehensive solutions often require paid subscriptions, many free email security plugins and browser extensions offer basic anti-phishing features that can help.