Dell EMC Releases Cyber Attack Protection Software
Dell emc release cyber attack protection software for data centers – Dell EMC’s release of its new cyber attack protection software for data centers is HUGE news! In a world increasingly threatened by sophisticated cyberattacks, this launch signifies a significant step forward in bolstering the security of our digital infrastructure. This isn’t just another security update; it’s a comprehensive suite designed to address vulnerabilities previously left exposed, offering a much-needed layer of protection against the ever-evolving threat landscape.
We’ll dive into the specifics, exploring its features, functionality, and the impact it promises to have on data center security worldwide.
The software boasts impressive capabilities, from advanced threat detection and prevention to robust incident response mechanisms. It’s not just about reacting to attacks; it’s about proactively preventing them. Think of it as a highly-trained security guard, constantly monitoring for threats and ready to spring into action the moment something suspicious arises. We’ll explore real-world scenarios to illustrate its effectiveness and discuss how it stacks up against competing solutions.
Dell EMC’s Cyber Attack Protection Software Landscape
Dell EMC has a long-standing commitment to data center security, offering a robust portfolio of solutions before the release of their latest cyber attack protection software. This new software represents a significant advancement, building upon existing capabilities and addressing emerging threats in the evolving landscape of data center security.
Existing Dell EMC Data Center Security Solutions
Prior to this release, Dell EMC provided a range of security solutions for data centers, including network security appliances (firewalls, intrusion prevention systems), data security solutions (encryption, data loss prevention), and security information and event management (SIEM) tools. These solutions, while effective, often required complex integration and lacked comprehensive, automated threat response capabilities. Many relied on reactive measures rather than proactive threat hunting and prevention.
This often led to a fragmented security posture, making it difficult to gain a holistic view of security threats and respond effectively.
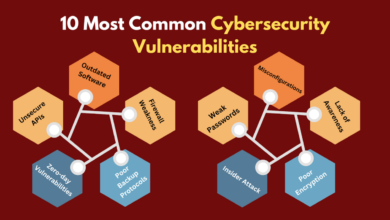
Vulnerabilities Addressed by the New Software
The new software directly tackles several key vulnerabilities. It focuses on addressing the increasing sophistication of ransomware attacks, supply chain compromises, and insider threats. Specifically, it aims to mitigate the risks associated with zero-day exploits, lateral movement within the data center network, and the exploitation of vulnerabilities in legacy systems. The software improves detection and response times to significantly reduce the impact of successful attacks.
For example, the software’s advanced threat detection capabilities can identify malicious activity even before it reaches critical systems, preventing data breaches before they happen.
Comparison with Competitor Offerings
While competitors offer similar data center security solutions, Dell EMC’s new software differentiates itself through its integrated approach. Many competitor offerings are point solutions, requiring extensive manual integration and configuration. In contrast, this new software seamlessly integrates with existing Dell EMC infrastructure, providing a unified security platform. Furthermore, its AI-powered threat detection capabilities are designed to be more accurate and less prone to false positives than some competitor solutions.
This reduces the burden on security teams and allows for quicker, more effective responses to actual threats. Specific competitor comparisons would require a detailed analysis of individual product features and pricing, which is beyond the scope of this overview.
Key Features of the New Software
The following table summarizes the key features of Dell EMC’s new cyber attack protection software:
| Feature Name | Description | Target Vulnerability | Benefit |
|---|---|---|---|
| AI-Powered Threat Detection | Utilizes machine learning to identify anomalous behavior and potential threats in real-time. | Zero-day exploits, advanced persistent threats (APTs) | Proactive threat identification and prevention, reduced response times. |
| Automated Response System | Automatically isolates infected systems and implements remediation actions to contain threats. | Ransomware attacks, lateral movement | Minimized downtime, reduced data loss. |
| Vulnerability Management | Continuously scans for and assesses vulnerabilities in the data center infrastructure. | Exploitable vulnerabilities in applications and operating systems | Improved security posture, reduced attack surface. |
| Integrated Security Orchestration | Provides a centralized platform for managing and coordinating all security functions. | Fragmented security infrastructure | Improved visibility and control over security posture, simplified management. |
Technical Specifications and Functionality
Dell EMC’s new Cyber Attack Protection software represents a significant advancement in data center security. This robust solution offers a multi-layered approach to threat detection, prevention, and response, leveraging advanced analytics and automation to minimize downtime and data loss. The following details provide a comprehensive overview of its technical specifications and core functionalities.
Software Architecture
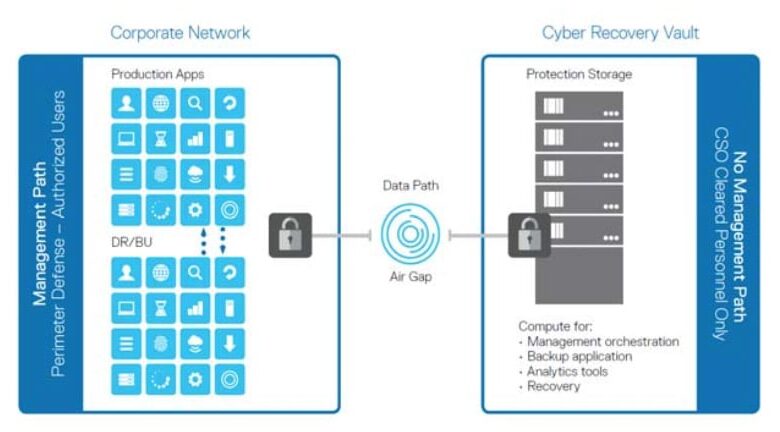
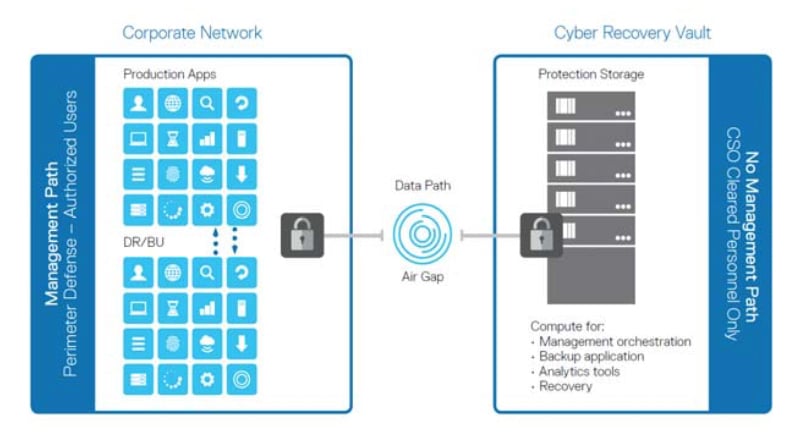
The software employs a distributed architecture, utilizing a combination of lightweight agents deployed on individual servers and a central management console. This allows for efficient monitoring and control across large and complex data center environments. The agents continuously collect telemetry data, analyzing network traffic, system logs, and application behavior for anomalies. This data is then transmitted to the central console for correlation and analysis using advanced machine learning algorithms.
The central console provides a unified view of the entire data center’s security posture, enabling proactive threat hunting and rapid response to incidents. The architecture is designed for scalability, allowing it to adapt to growing data center infrastructures. This scalability is achieved through horizontal scaling of the central console and the agents.
Deployment Methods and System Requirements
The software supports both physical and virtual deployments, offering flexibility to accommodate various data center configurations. Deployment is streamlined through a user-friendly installer, minimizing disruption to ongoing operations. System requirements vary depending on the scale of the deployment but generally include a minimum of 8GB of RAM and a multi-core processor for the central console. Agents have significantly lower requirements, enabling deployment on even resource-constrained servers.
The software supports a range of operating systems, including Windows Server, Linux, and VMware ESXi.
Threat Detection, Prevention, and Response Mechanisms
The software utilizes a multi-layered approach to threat detection, incorporating signature-based detection, anomaly detection, and behavioral analysis. Signature-based detection identifies known malware and exploits. Anomaly detection flags unusual activity patterns that deviate from established baselines. Behavioral analysis monitors the behavior of processes and applications, identifying malicious activities even from unknown threats. Prevention mechanisms include real-time blocking of malicious traffic, automated patching of vulnerabilities, and isolation of compromised systems.
Dell EMC’s new data center cyber attack protection software is a significant step forward, but the shift to cloud necessitates a broader approach. Understanding the complexities of cloud security is crucial, and that’s where resources like this article on bitglass and the rise of cloud security posture management become invaluable. Ultimately, combining robust on-premise solutions with a strong cloud security posture is key to comprehensive data protection.
The response mechanisms automate incident response procedures, including containment, eradication, and recovery, minimizing the impact of successful attacks. This automation drastically reduces the mean time to recovery (MTTR) following a cyber incident.
Ransomware Mitigation Scenario
Imagine a scenario where a sophisticated ransomware attack targets a data center. The software’s agents detect unusual encryption activity on several servers. The anomaly detection engine flags this activity as suspicious, triggering an alert on the central console. The software automatically isolates the affected servers, preventing the ransomware from spreading. Simultaneously, the software initiates a rollback to a known good state, restoring the affected systems from backups.
The central console provides a comprehensive report detailing the attack, including the source, impact, and remediation steps taken. This rapid response minimizes data loss and downtime, limiting the overall impact of the ransomware attack. This scenario showcases the software’s ability to proactively identify, prevent, and mitigate even advanced persistent threats.
User Access and Permissions
User access and permissions are managed through a role-based access control (RBAC) system. This ensures that only authorized personnel have access to sensitive data and functionalities. The following levels of access are defined:
- Administrator: Full access to all features and functionalities.
- Security Analyst: Access to monitoring and investigation tools, including dashboards, alerts, and logs.
- Operator: Limited access to specific tasks, such as running reports and managing alerts.
- Auditor: Read-only access to security logs and reports.
This granular control over access rights ensures data security and prevents unauthorized modifications or actions. Each role is assigned specific permissions, tailoring access to individual job responsibilities.
Dell EMC’s new cyber attack protection software is a game-changer for data center security, offering robust defenses against evolving threats. But even the strongest security needs efficient, adaptable applications, which is why understanding the future of app development, as explored in this insightful article on domino app dev the low code and pro code future , is crucial.
Ultimately, strong security and agile development work hand-in-hand to protect our increasingly digital world, making Dell EMC’s release even more significant in the context of modern app architecture.
Impact on Data Center Security: Dell Emc Release Cyber Attack Protection Software For Data Centers

Dell EMC’s new cyber attack protection software promises a significant shift in data center security, offering proactive defense and improved response capabilities. Its impact extends beyond simply adding another layer of protection; it fundamentally alters how organizations approach risk management and incident handling within their critical infrastructure. This software represents a move towards a more predictive and automated security posture.The software’s potential to improve the overall security posture of data centers is multifaceted.
By integrating advanced threat detection and response capabilities, it can significantly reduce the window of vulnerability, minimizing the time between an attack and its containment. This proactive approach, combined with automated remediation, helps prevent attacks from escalating and causing widespread damage. Furthermore, the software’s ability to analyze network traffic and identify malicious activity in real-time allows for quicker identification of threats, leading to faster incident response and reduced downtime.
Improved Incident Response Times and Reduced Attack Impact
The software’s impact on incident response times is demonstrably positive. For instance, imagine a scenario where a sophisticated ransomware attack targets a data center. Traditional security solutions might detect the attack after significant data encryption has already occurred. Dell EMC’s software, however, with its advanced threat intelligence and behavioral analysis, could identify the anomalous activity much earlier – perhaps even before the ransomware payload is fully deployed.
This early detection enables immediate containment, preventing widespread encryption and minimizing data loss. Furthermore, the automated response capabilities could isolate infected systems, preventing the lateral movement of the malware and reducing the overall impact of the attack. This translates directly to faster recovery times and reduced financial losses. A real-world example could be seen in a financial institution where rapid response prevents a significant disruption to online banking services, avoiding reputational damage and financial penalties.
Challenges and Limitations in Real-World Deployments
While the software offers significant advantages, real-world deployment presents certain challenges. Integration with existing security infrastructure can be complex, requiring careful planning and potentially significant upfront effort. Furthermore, the software’s effectiveness depends on accurate configuration and ongoing maintenance. False positives, while hopefully minimized, could lead to alert fatigue and a decrease in the effectiveness of the security team.
Finally, the software’s ability to adapt to new and evolving threats relies heavily on continuous updates and the timely integration of new threat intelligence. Any delay in updates could compromise the system’s effectiveness against emerging attack vectors.
Cost-Benefit Analysis of Software Implementation
Implementing the Dell EMC cyber attack protection software requires a careful cost-benefit analysis. The initial investment includes the software license, hardware upgrades (if necessary), and professional services for deployment and integration. Ongoing costs encompass maintenance contracts, software updates, and potentially the need for specialized personnel to manage and monitor the system. However, these costs must be weighed against the potential losses mitigated by the software.
Consider a scenario where a large enterprise experiences a major data breach resulting in regulatory fines, legal fees, reputational damage, and lost business. The cost of such a breach could easily exceed the cost of implementing and maintaining the software, making the investment a financially sound decision. The potential return on investment (ROI) is substantial, especially for organizations handling sensitive data and facing significant regulatory compliance requirements.
A quantitative analysis would require specific cost figures (which are unavailable without a specific Dell EMC product specification) and a detailed risk assessment for each organization. However, the qualitative benefits, in terms of improved security posture and reduced downtime, are clearly substantial.
User Experience and Adoption
Dell EMC’s new cyber attack protection software is designed with a user-friendly interface prioritizing ease of navigation and intuitive functionality. The goal is to empower security teams of all skill levels to effectively utilize the software’s robust capabilities without requiring extensive specialized training. This approach minimizes the learning curve and facilitates rapid adoption across data centers.The software features a clean, modern dashboard providing a clear overview of the system’s status, active threats, and overall security posture.
Key metrics and alerts are prominently displayed, enabling quick identification of potential issues. Detailed reports and visualizations aid in comprehensive threat analysis and incident response planning. The software also incorporates context-sensitive help features and integrated tutorials accessible directly within the interface, further enhancing usability.
Training and Support Resources
Dell EMC provides a comprehensive suite of training and support resources designed to ensure successful software implementation and ongoing user proficiency. These resources include online tutorials, interactive training modules, and detailed documentation covering all aspects of the software’s functionality. Furthermore, users have access to a dedicated support portal offering troubleshooting assistance, knowledge base articles, and direct contact with experienced technical support engineers.
On-site training sessions are available for organizations requiring more hands-on instruction. These resources cater to various learning styles and technical expertise levels, ensuring that all users can confidently leverage the software’s capabilities.
Best Practices for Implementation and Adoption
Successful implementation and adoption of the software hinges on a well-defined strategy that encompasses planning, training, and ongoing support. Prior to deployment, a thorough assessment of the data center’s security needs and infrastructure is crucial to tailor the software’s configuration to the specific environment. This includes identifying critical assets, defining security policies, and establishing clear incident response protocols.
A phased rollout approach, starting with a pilot program in a limited environment, allows for controlled testing and iterative improvements before full-scale deployment. Regular training sessions and ongoing communication with users are essential to maintain proficiency and address any challenges encountered during the adoption process. Finally, establishing a feedback mechanism allows for continuous improvement and refinement of the software and associated support resources.
Typical Workflow for Addressing a Security Incident, Dell emc release cyber attack protection software for data centers
The following flowchart illustrates the typical workflow for using the software to address a security incident:[Imagine a flowchart here. The flowchart would begin with “Security Incident Detected” and branch to “Initial Threat Assessment” using the software’s threat detection capabilities. This would lead to “Incident Isolation and Containment” using the software’s isolation tools. Next, “Root Cause Analysis” would be conducted using the software’s forensic tools, followed by “Remediation and Recovery” using the software’s automated remediation features.
Finally, the flowchart would conclude with “Post-Incident Review and Reporting,” documenting the entire process for future reference and improvement.] The software automates many steps, such as isolating infected systems and initiating remediation procedures, significantly reducing the time and effort required to contain and resolve security incidents. Detailed logs and reports are automatically generated throughout the process, providing a comprehensive record of the incident for auditing and analysis.
Future Developments and Integrations
The Dell EMC Cyber Attack Protection software is not a static product; it’s designed for continuous improvement and expansion to meet the ever-evolving threat landscape. Our roadmap focuses on enhancing existing capabilities, integrating with other security solutions, and proactively addressing emerging vulnerabilities. This ensures our clients benefit from the most advanced and comprehensive data center protection available.Our development strategy prioritizes user feedback and industry best practices.
We are committed to providing a solution that is not only effective but also intuitive and easy to manage, minimizing the burden on IT teams while maximizing security. This commitment extends to seamless integration with existing infrastructure, avoiding disruption and maximizing the return on investment.
Planned Software Updates and Enhancements
The next phase of development will focus on several key areas. We plan to significantly improve the software’s ability to detect and respond to zero-day exploits, leveraging advanced machine learning techniques to identify anomalous behavior in real-time. This will involve enhancing our threat intelligence feeds and integrating with external threat intelligence platforms. Further enhancements will include improved reporting and visualization tools, providing a clearer picture of security posture and enabling faster incident response.
Finally, we’re committed to streamlining the user interface, making it even more user-friendly and efficient.
Integration with Other Dell EMC Products and Third-Party Solutions
Seamless integration is paramount. Future versions will include enhanced compatibility with other Dell EMC security products, such as our advanced threat prevention solutions and data loss prevention tools. This integrated approach provides a unified security posture, reducing complexity and improving overall effectiveness. We are also exploring strategic partnerships with leading third-party security vendors to expand our ecosystem of compatible solutions.
For example, integration with leading SIEM (Security Information and Event Management) platforms will allow for centralized security monitoring and incident response across the entire IT infrastructure. This collaboration will extend the reach and capabilities of our Cyber Attack Protection software.
Potential Areas for Future Research and Improvement
Ongoing research will focus on several key areas to further enhance the software’s capabilities. One area of focus is the development of more sophisticated behavioral analytics, leveraging AI and machine learning to identify and mitigate advanced persistent threats (APTs). Another area involves exploring the use of blockchain technology to enhance data integrity and immutability, providing an additional layer of security against data breaches and ransomware attacks.
Finally, we will continue to investigate the application of automation to improve incident response times and reduce the reliance on manual intervention.
Prioritized Future Features
The following list Artikels potential future features categorized by priority:
- High Priority:
- Enhanced zero-day exploit detection using advanced machine learning.
- Integration with leading SIEM platforms.
- Improved automated incident response capabilities.
- Medium Priority:
- Enhanced reporting and visualization tools.
- Integration with Dell EMC data loss prevention solutions.
- Support for additional cloud platforms.
- Low Priority:
- Exploration of blockchain technology for enhanced data integrity.
- Development of a self-service portal for users.
- Improved user interface customization options.
Ending Remarks
In short, Dell EMC’s new cyber attack protection software represents a major advancement in data center security. Its comprehensive features, proactive approach, and user-friendly design make it a compelling solution for organizations seeking to fortify their defenses against the ever-growing threat of cyberattacks. While challenges and limitations always exist in the real world, the potential benefits – reduced downtime, mitigated financial losses, and enhanced peace of mind – are undeniable.
This isn’t just about technology; it’s about safeguarding critical data and ensuring business continuity in an increasingly volatile digital environment. The future of data center security looks brighter thanks to this significant release.
Q&A
What types of cyberattacks does this software protect against?
It’s designed to protect against a wide range of attacks, including ransomware, malware, denial-of-service attacks, and insider threats. The specific vulnerabilities addressed are detailed in the software’s documentation.
How much does the software cost?
Pricing varies depending on the size of your data center and the specific features you require. Contact Dell EMC for a customized quote.
What kind of training is provided for users?
Dell EMC offers comprehensive training resources, including online tutorials, documentation, and potentially on-site training depending on your needs.
Is the software compatible with other security solutions?
Yes, Dell EMC plans for integration with other Dell EMC products and third-party security solutions. Specific compatibility information should be available in the product documentation.