Demystifying Infrastructure as Code IAC Scanning Enhancing DevOps Security
Demystifying infrastructure as code iac scanning enhancing security in devops – Demystifying Infrastructure as Code (IaC) scanning: enhancing security in DevOps is crucial in today’s complex development environments. IaC, the practice of managing and provisioning infrastructure through code, offers incredible efficiency and repeatability, but also introduces new security risks. This post dives into the world of IaC scanning, exploring how to identify and mitigate vulnerabilities before they impact your production systems, ultimately strengthening your DevOps pipeline and minimizing security breaches.
We’ll cover essential concepts, explore various IaC scanning tools, delve into common vulnerabilities, and Artikel best practices for integrating secure scanning into your CI/CD pipeline. From understanding static and dynamic analysis to leveraging AI for enhanced detection, we’ll equip you with the knowledge to confidently secure your IaC deployments.
Introduction to Infrastructure as Code (IaC) Scanning
Infrastructure as Code (IaC) has revolutionized how we manage and provision infrastructure. Instead of manually configuring servers and networks, IaC uses code to define and automate the entire process. This approach significantly improves efficiency, consistency, and repeatability in DevOps environments. IaC scanning takes this a step further by automatically analyzing that code for potential security vulnerabilities and compliance issues before deployment, acting as a crucial gatekeeper for security within the DevOps pipeline.IaC scanning plays a vital role in enhancing the security posture of DevOps workflows.
By automating the detection of misconfigurations and vulnerabilities early in the development lifecycle, it significantly reduces the risk of deploying insecure infrastructure. This proactive approach minimizes the attack surface, prevents costly remediation efforts later in the process, and accelerates the overall development lifecycle by catching problems before they reach production.
IaC and its Role in DevOps
IaC is a cornerstone of modern DevOps practices. It enables teams to treat infrastructure like software, allowing for version control, automated testing, and continuous integration/continuous delivery (CI/CD) pipelines. This approach promotes consistency across environments (development, testing, production), reduces human error, and speeds up deployment times. Using tools like Terraform or Ansible, developers can define infrastructure as code, enabling automated provisioning and management.
Changes are tracked, reviewed, and tested before deployment, ensuring reliability and reducing the risk of unintended consequences.
Benefits of Implementing IaC Scanning
Implementing IaC scanning within a DevOps pipeline offers numerous advantages. These include:* Early Detection of Vulnerabilities: Identifying security flaws early in the development cycle, before they reach production.
Reduced Risk of Deployment Errors
Preventing the deployment of misconfigured or insecure infrastructure.
Improved Compliance
Ensuring infrastructure configurations adhere to organizational policies and industry regulations.
Faster Remediation
Quickly addressing identified issues, minimizing downtime and reducing costs.
Enhanced Collaboration
Providing a centralized view of security risks for development and security teams.
Examples of Common IaC Tools and Their Functionalities
Several tools facilitate IaC scanning and management. Here are a few examples:* Chef InSpec: A compliance-as-code framework used to define and enforce security policies and compliance standards across infrastructure. It allows you to write tests to verify configurations and identify potential security weaknesses.* Pulumi: A modern IaC platform that supports multiple cloud providers and programming languages.
Its security features include policy-as-code capabilities, allowing for the enforcement of security rules throughout the infrastructure lifecycle.* Terraform: A popular IaC tool for defining and managing infrastructure in a declarative way. While not inherently a scanning tool, it integrates well with other security tools for scanning Terraform configurations.* Azure DevOps: Microsoft’s cloud-based DevOps platform includes built-in features for IaC scanning and security analysis, tightly integrating with Azure services.
Comparison of IaC Scanning Tools, Demystifying infrastructure as code iac scanning enhancing security in devops
The choice of IaC scanning tool depends on specific needs and existing infrastructure. The following table compares four popular options:
| Tool | Strengths | Weaknesses | Integration |
|---|---|---|---|
| Chef InSpec | Powerful compliance capabilities, supports various platforms | Steeper learning curve compared to some other tools | Integrates well with Chef Automate and other CI/CD pipelines |
| Checkov | Open-source, supports multiple IaC providers, easy to use | Limited advanced features compared to commercial options | Integrates with various CI/CD tools |
| Snyk | Comprehensive vulnerability scanning, supports multiple IaC languages | Can be expensive for large-scale deployments | Integrates with various CI/CD platforms and cloud providers |
| CloudSploit | Focuses on cloud security, provides detailed reports | Primarily cloud-focused, limited support for on-premise infrastructure | Integrates with various cloud platforms |
Security Vulnerabilities in IaC
Infrastructure as Code (IaC) offers incredible advantages in terms of speed, consistency, and automation, but it also introduces a new attack surface. Security vulnerabilities in IaC configurations can have devastating consequences, potentially leading to significant breaches and financial losses. Understanding these vulnerabilities and implementing robust security practices is crucial for any organization utilizing IaC.IaC configurations, essentially code defining your infrastructure, can contain flaws that expose your systems to various threats.
These vulnerabilities are often overlooked because they reside in the code itself, not within the running infrastructure. This makes them harder to detect through traditional security measures.
Common IaC Security Vulnerabilities
Several types of security vulnerabilities are commonly found in IaC. These range from simple misconfigurations to more sophisticated code injection attacks. Addressing these vulnerabilities proactively is critical for minimizing risk.
- Hardcoded Credentials: Embedding passwords, API keys, or other sensitive information directly into IaC code is a major security risk. This allows unauthorized access if the code is compromised.
- Insufficient Access Control: Improperly configured access control lists (ACLs) or insufficiently restrictive IAM roles can grant unauthorized users or services excessive permissions, leading to data breaches or system compromises.
- Unpatched Dependencies: Using outdated or unpatched libraries and modules in your IaC scripts can expose your infrastructure to known vulnerabilities. Regularly updating dependencies is essential.
- Misconfigured Security Groups: Incorrectly configured security groups in cloud environments can expose services to the internet or allow unwanted inbound/outbound traffic, making them vulnerable to attacks.
- Lack of Input Validation: Failing to validate user inputs in IaC scripts can lead to injection attacks, where malicious code is executed on your infrastructure.
- Open Ports and Services: Leaving unnecessary ports and services open on your infrastructure increases the attack surface. Only expose what is absolutely necessary.
Consequences of IaC Vulnerabilities in Production
The consequences of insecure IaC can be severe, ranging from minor disruptions to major security breaches.
- Data Breaches: Improperly configured access control can lead to unauthorized access to sensitive data, resulting in data theft or leakage.
- System Compromises: Vulnerabilities in IaC can allow attackers to gain control of your infrastructure, potentially leading to complete system takeover.
- Financial Losses: Security breaches can result in significant financial losses due to downtime, remediation costs, legal fees, and reputational damage.
- Compliance Violations: Failing to secure your infrastructure can lead to non-compliance with industry regulations, resulting in penalties and fines.
- Service Disruptions: Misconfigurations can lead to service outages or performance degradation, impacting business operations.
Real-World Examples of IaC Misconfigurations
While specific details of security breaches are often kept confidential, news reports frequently highlight the impact of IaC misconfigurations. For example, misconfigured cloud storage buckets exposing sensitive data or insecurely configured databases have resulted in significant data breaches across various industries. These incidents underscore the critical need for secure IaC practices.
Best Practices for Secure IaC Code
Writing secure IaC code requires a proactive approach, incorporating security considerations throughout the development lifecycle.
- Use Secrets Management: Never hardcode credentials. Utilize a secrets management system to securely store and manage sensitive information.
- Implement Least Privilege: Grant only the minimum necessary permissions to users and services.
- Regularly Update Dependencies: Keep all libraries and modules up-to-date to patch known vulnerabilities.
- Employ Static and Dynamic Analysis: Use security scanning tools to identify vulnerabilities in your IaC code.
- Validate User Inputs: Thoroughly validate all user inputs to prevent injection attacks.
- Follow the Principle of Least Exposure: Minimize the attack surface by only exposing necessary ports and services.
- Version Control and Code Reviews: Use version control for tracking changes and conduct thorough code reviews to catch security issues early.
- Infrastructure as Code Security Scanning: Integrate automated security scanning into your CI/CD pipeline.
Implementing IaC Scanning in the DevOps Pipeline: Demystifying Infrastructure As Code Iac Scanning Enhancing Security In Devops
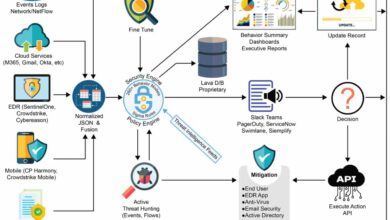
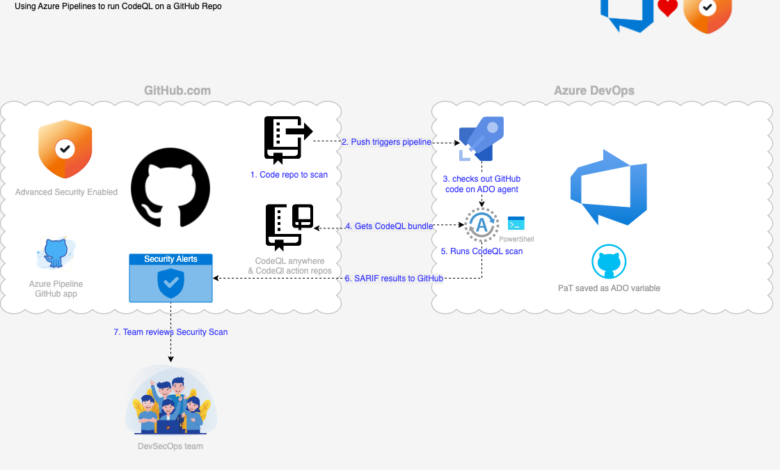
Integrating IaC scanning into your DevOps pipeline is crucial for proactively identifying and mitigating security risks before they reach production. This ensures a more secure and reliable infrastructure, minimizing vulnerabilities and potential breaches. By automating this process, you significantly reduce manual effort and improve the overall efficiency of your security posture.IaC scanning can be integrated at various points within the CI/CD pipeline, offering different levels of granularity and impact.
Strategic placement maximizes the benefits, allowing for early detection and resolution of issues. The optimal approach depends on your specific needs and the complexity of your infrastructure.
IaC Scanning Integration Points in the CI/CD Pipeline
The effectiveness of IaC scanning is directly related to where it’s placed in your CI/CD pipeline. Early integration allows for quicker identification and remediation of issues, minimizing downstream problems. Consider these common integration points:
- Pre-Commit/Pre-Merge: Scanning IaC code before it’s committed to the main branch allows for immediate feedback to developers. This prevents vulnerable code from entering the repository in the first place.
- Post-Commit/Merge: While less ideal than pre-commit, post-commit scanning provides a safety net, catching vulnerabilities that might have slipped through pre-commit checks. This stage can be integrated with your code review process.
- Build Stage: Integrating IaC scanning during the build stage can halt the pipeline if critical vulnerabilities are detected. This prevents deployment of insecure infrastructure.
- Deployment Stage: Scanning just before deployment offers a final check, though resolving issues at this stage might be more time-consuming and costly.
Automated IaC Scanning Configuration with Checkov
Checkov, an open-source IaC scanning tool, provides a robust and flexible solution for automating security checks. Let’s illustrate a basic configuration:First, you’ll need to install Checkov. This is typically done via pip: pip install checkov.Next, you can integrate Checkov into your CI/CD pipeline using your chosen tool (e.g., Jenkins, GitLab CI, GitHub Actions). A simple example using a shell script within a CI/CD pipeline might look like this: #!/bin/bashcheckov -d infra/terraform/ --skip-frameworkif [[ $? -ne 0 ]]; then echo "Checkov found vulnerabilities. Failing the pipeline." exit 1fiecho "Checkov scan completed successfully."This script scans the Terraform code in the `infra/terraform/` directory and fails the pipeline if vulnerabilities are found.
The `–skip-framework` flag skips framework checks which may not be relevant to every project. Remember to adjust the directory path to match your project structure.
Step-by-Step Guide to Secure IaC Scanning
Implementing a secure IaC scanning process involves several key steps:
- Choose an IaC scanning tool: Select a tool that supports your IaC frameworks (Terraform, CloudFormation, etc.) and integrates with your CI/CD pipeline.
- Configure the scanner: Set up the tool to scan your IaC code repositories and define the rules and policies for vulnerability detection.
- Integrate with CI/CD: Integrate the scanner into your pipeline at the appropriate stages (pre-commit, build, deployment, etc.).
- Establish thresholds: Define acceptable levels of risk and automatically fail the pipeline if the number of critical vulnerabilities exceeds a predefined limit.
- Regularly update the scanner: Keep the scanner and its rules updated to reflect the latest security threats and best practices.
- Monitor and review results: Regularly review the scan results to identify trends and improve your IaC security posture.
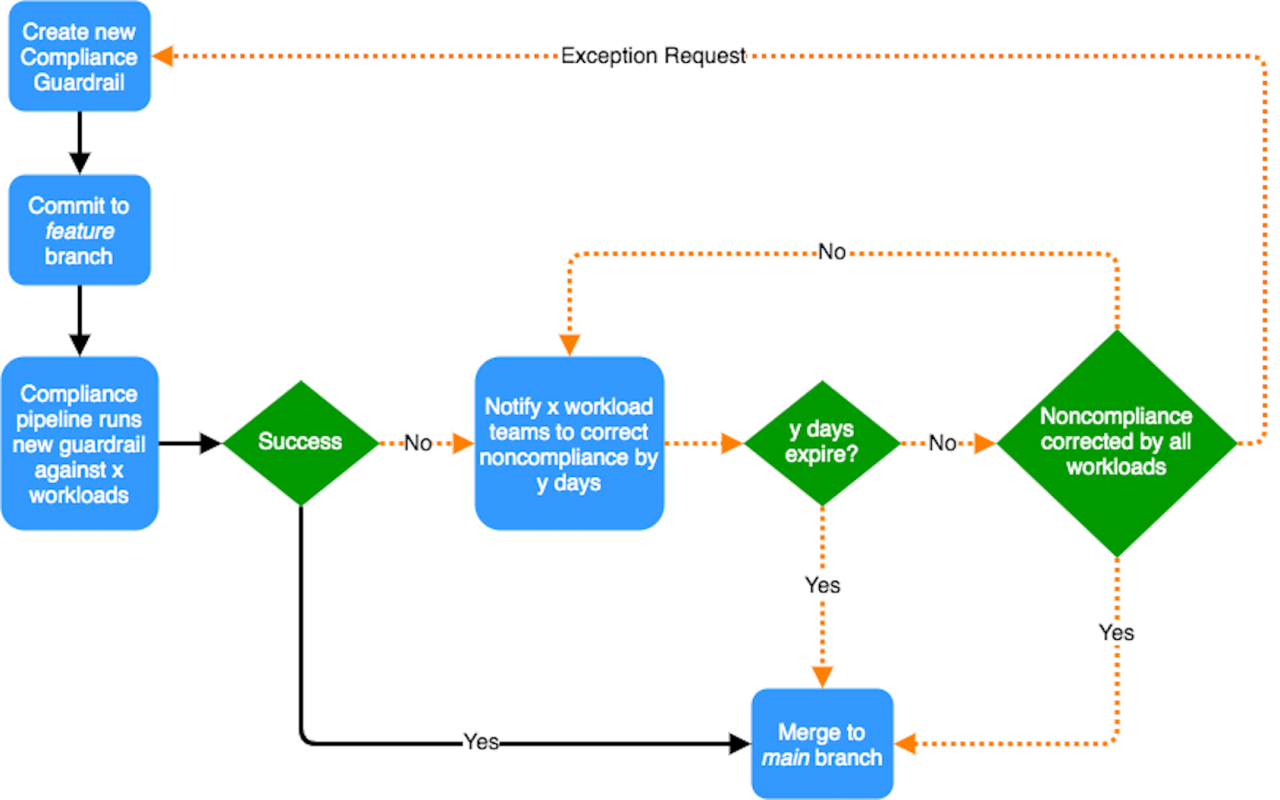
IaC Scanning Integration Flowchart
[Imagine a flowchart here. The flowchart would depict a typical CI/CD pipeline (Code -> Build -> Test -> Deploy). At each stage (or selected stages), a box representing the IaC scanner would be shown, with arrows indicating the flow of code and scan results. If vulnerabilities are found, an arrow would branch off to a “Remediation” box, and then back to the relevant stage for re-testing.
Upon successful scanning, the pipeline would continue to the next stage.]
Analyzing IaC Scan Results and Remediation
So, your IaC scan is complete. You’ve got a report – now what? This is where the real work begins: understanding the findings, prioritizing fixes, and implementing effective remediation strategies. Don’t worry, it’s not as daunting as it sounds. With a systematic approach, you can transform potential security vulnerabilities into strengthened infrastructure.Interpreting IaC scan reports requires careful attention to detail.
Reports typically categorize findings by severity (critical, high, medium, low), type of vulnerability (misconfigurations, insecure dependencies, secrets exposure), and location within your IaC code. Understanding the context of each vulnerability is key. For instance, a high-severity finding might indicate a misconfigured security group allowing unrestricted access to a database, while a low-severity finding might be a minor style guideline violation.
Prioritize based on risk; critical vulnerabilities impacting production systems demand immediate attention.
IaC Vulnerability Prioritization
Prioritization is crucial for efficient remediation. A common approach involves using a risk matrix that considers both the likelihood of exploitation and the potential impact of a successful attack. For example, a vulnerability with high likelihood and high impact (e.g., publicly exposed database credentials) should be prioritized over a vulnerability with low likelihood and low impact (e.g., a minor coding style issue).
Tools like risk management software can help automate this process, assigning scores based on predefined criteria. Regularly review your prioritization scheme; it should reflect your evolving risk tolerance and business context.
Remediation Strategies for Common IaC Vulnerabilities
Effective remediation strategies vary depending on the nature of the vulnerability.
| Vulnerability Type | Remediation Strategy | Example |
|---|---|---|
| Misconfigured Security Groups | Restrict inbound/outbound rules to only necessary ports and IP addresses. Implement principle of least privilege. | Instead of allowing all inbound traffic to an EC2 instance, only allow SSH from specific IP addresses and the necessary ports for application access. |
| Hardcoded Credentials | Use secrets management tools (e.g., AWS Secrets Manager, HashiCorp Vault) to store and manage sensitive information. Employ environment variables to inject credentials during deployment. | Instead of directly embedding database passwords in your Terraform configuration, store them securely in a secrets manager and reference them via environment variables. |
| Insecure Dependencies | Regularly update dependencies to the latest versions to patch known vulnerabilities. Use dependency scanning tools to identify outdated or vulnerable packages. | If your IaC uses a particular library or module with known vulnerabilities, update to the latest version which addresses the issue. |
| Lack of Input Validation | Implement robust input validation mechanisms to prevent injection attacks (e.g., SQL injection, cross-site scripting). | Sanitize all user inputs before using them in your IaC scripts or configurations. Validate data types and lengths. |
Managing and Tracking Remediation Efforts
Effective remediation requires a structured approach. Use a ticketing system (e.g., Jira, ServiceNow) to track each vulnerability, assign it to a responsible team member, set deadlines, and monitor progress. Regularly review the status of open tickets and escalate issues as needed. Maintain a central repository for all remediation documentation, including vulnerability details, remediation steps, and verification results. This ensures transparency and allows for efficient knowledge sharing.
Automate the process as much as possible, integrating your IaC scanning tool with your CI/CD pipeline to automatically trigger remediation actions or alerts when vulnerabilities are detected.
Advanced IaC Scanning Techniques
IaC scanning has evolved beyond basic syntax checks. Modern techniques leverage sophisticated analysis methods and integrate seamlessly with existing DevOps workflows to provide a more comprehensive security posture. This section delves into the advanced capabilities that elevate IaC scanning from a simple check to a crucial component of a robust security strategy.
Static and Dynamic Analysis in IaC Scanning
Static analysis examines the IaC code without executing it, identifying potential vulnerabilities through pattern matching, syntax analysis, and semantic analysis of the codebase. This approach is efficient and can be integrated early in the development pipeline. Dynamic analysis, conversely, involves executing the IaC code in a controlled environment (like a sandbox) to observe its runtime behavior and identify vulnerabilities that only manifest during execution.
Combining both methods offers a more comprehensive view of potential security risks. For example, static analysis might flag a hardcoded password in a configuration file, while dynamic analysis could reveal unintended network exposures resulting from misconfigured firewall rules.
Application of Security Policies and Compliance Standards in IaC Scanning
IaC scanning tools can be configured to enforce specific security policies and compliance standards. This allows organizations to ensure their infrastructure adheres to regulations like HIPAA, PCI DSS, or custom internal policies. These tools can automatically check for compliance violations, such as the use of deprecated cryptographic algorithms or the lack of proper access controls. For instance, a tool could be configured to flag any instances where storage buckets lack encryption or where database credentials are not managed securely via a secrets management system.
The integration of these policies directly into the scanning process automates compliance checks, reducing the risk of human error and improving overall security.
Comparison of IaC Scanning Methodologies
Various IaC scanning methodologies exist, each with strengths and weaknesses. Some tools focus solely on detecting known vulnerabilities based on predefined rules, while others employ machine learning to identify more subtle or novel threats. Open-source tools often offer flexibility and customization, but may require more manual configuration and maintenance compared to commercial solutions which typically provide a more streamlined user experience and comprehensive feature sets.
The choice of methodology depends on factors such as budget, technical expertise, and the specific security needs of the organization. A hybrid approach, combining multiple tools and methodologies, is often the most effective.
Challenges and Limitations of Current IaC Scanning Technologies
While IaC scanning has significantly improved security practices, challenges remain. The rapid evolution of IaC technologies and the emergence of new vulnerabilities constantly necessitate updates to scanning tools. Furthermore, accurately identifying and classifying vulnerabilities in complex IaC configurations can be difficult, leading to false positives or missed vulnerabilities. Another limitation is the ability to handle custom code and configurations that deviate from standard practices.
Finally, ensuring comprehensive coverage across all aspects of the infrastructure, including dependencies and third-party components, presents a significant ongoing challenge. For example, detecting vulnerabilities within custom Terraform modules or detecting misconfigurations in Kubernetes deployments can be challenging, requiring specialized expertise and potentially custom scanning rules.
Future Trends in IaC Scanning
The field of IaC scanning is rapidly evolving, driven by the increasing complexity of cloud-native architectures and the growing sophistication of cyber threats. New approaches are constantly emerging to address the challenges of securing increasingly intricate infrastructure deployments managed through code. This evolution promises more robust, efficient, and proactive security measures.The integration of advanced technologies like AI and machine learning is transforming IaC security, leading to more effective vulnerability detection and remediation.
Furthermore, the shift towards a more proactive, preventative approach to security is shaping the future of IaC scanning, moving beyond reactive patching to predictive risk management.
AI and Machine Learning in IaC Scanning
AI and machine learning are poised to revolutionize IaC scanning by automating and improving several key aspects. Machine learning algorithms can be trained on vast datasets of IaC code and known vulnerabilities to identify patterns and predict potential security risks with greater accuracy than traditional rule-based systems. This allows for the detection of subtle vulnerabilities that might be missed by human analysts or simpler scanners.
For example, an ML model could learn to recognize specific code patterns indicative of misconfigurations that lead to data breaches, even if those patterns haven’t been explicitly documented as vulnerabilities. This predictive capability allows for proactive remediation before vulnerabilities are exploited. Moreover, AI can automate the process of analyzing scan results, prioritizing critical vulnerabilities and suggesting appropriate remediation strategies, significantly reducing the workload on security teams.
Shift Towards Proactive Security
The future of IaC scanning is moving beyond simply identifying vulnerabilities after they exist. A proactive approach focuses on preventing vulnerabilities from ever being introduced into the codebase. This involves integrating IaC scanning tools early in the development lifecycle, performing continuous security checks during the coding process, and implementing automated security gates within the CI/CD pipeline. This shift requires a change in mindset, moving from a reactive “fix-it-when-broken” approach to a preventative “build-it-securely” approach.
Demystifying Infrastructure as Code (IaC) scanning is crucial for boosting DevOps security; it helps identify vulnerabilities early. Understanding cloud security posture management is equally important, and a great resource for learning more is this article on bitglass and the rise of cloud security posture management , which highlights how tools like Bitglass help manage cloud risks. Ultimately, combining strong IaC scanning with robust cloud security practices creates a significantly more secure DevOps pipeline.
Tools that incorporate static and dynamic analysis, combined with security best practice checks, will become increasingly important. For example, a system could automatically flag a developer’s code if it uses a deprecated library known to have security vulnerabilities, preventing the insecure code from ever reaching production.
Enhanced Contextual Awareness in Scanning
Current IaC scanning tools often lack sufficient contextual awareness. Future tools will be able to understand the broader context of the infrastructure being deployed, including dependencies, network configurations, and access controls. This contextual understanding will enable more accurate vulnerability assessments and more targeted remediation strategies. For example, a scanner could identify a misconfigured firewall rule that poses a significant risk only in the specific context of a particular application deployment.
Demystifying Infrastructure as Code (IaC) scanning is crucial for boosting DevOps security; it’s all about automating checks to prevent vulnerabilities. This proactive approach is especially important when considering the rapid development cycles often associated with platforms like Domino, as detailed in this insightful article on domino app dev the low code and pro code future. Ultimately, strengthening IaC scanning helps ensure the security of your entire application lifecycle, regardless of your development methodology.
Without this contextual understanding, the misconfiguration might be overlooked or flagged as a low-priority issue.
Increased Integration with DevOps Tools
Improved integration with existing DevOps tools and platforms is crucial for seamless IaC security. Future IaC scanners will be more tightly integrated with CI/CD pipelines, allowing for automated security checks at every stage of the software delivery lifecycle. This integration will reduce friction and ensure that security is not an afterthought but a core component of the development process.
For instance, a seamless integration could automatically halt the deployment pipeline if a critical vulnerability is detected during the build or testing phase, preventing insecure code from reaching production.
Outcome Summary
Securing your Infrastructure as Code is no longer optional; it’s a necessity. By implementing robust IaC scanning practices, you significantly reduce your attack surface and enhance the overall security posture of your DevOps workflow. This involves a multifaceted approach, from selecting the right scanning tools and integrating them effectively into your CI/CD pipeline to actively analyzing scan results and prioritizing remediation efforts.
Embrace continuous learning and adapt to evolving threats to ensure your IaC remains secure and your DevOps pipeline thrives.
FAQ Insights
What are the common types of IaC vulnerabilities?
Common vulnerabilities include misconfigurations (e.g., open ports, insecure credentials), insecure dependencies, and lack of proper access controls. These can lead to unauthorized access, data breaches, and system compromise.
How often should I run IaC scans?
The frequency depends on your development cycle. Ideally, integrate scans into every stage of your CI/CD pipeline – at least before deployments to staging and production.
What if my IaC scan reveals a critical vulnerability?
Prioritize critical vulnerabilities immediately. Implement a remediation plan, test thoroughly, and track the resolution. Consider rollback strategies if necessary.
Can IaC scanning tools detect all vulnerabilities?
No tool is perfect. Combine static and dynamic analysis techniques, and keep your tools updated to catch the latest vulnerabilities.