Demystifying Network Isolation and Micro-segmentation 2
Demystifying network isolation and micro segmentation 2 – Demystifying Network Isolation and Micro-segmentation 2: Dive deep into the world of enhanced network security! This isn’t your grandpa’s network security; we’re talking about isolating threats before they can even sniff around, creating tiny, secure pockets of data within your network. Think of it as building a Swiss cheese network, but instead of holes, you have impenetrable walls protecting your most valuable data.
We’ll explore various approaches, tools, and the future of this increasingly crucial technology. Get ready to level up your network security game!
This post breaks down the complexities of network isolation and micro-segmentation, exploring different approaches, practical implementations, and the future of this vital security strategy. We’ll cover everything from the core principles and benefits to tackling real-world challenges and emerging trends. Whether you’re a seasoned security pro or just starting to understand the importance of robust network protection, this guide is designed to provide clear, concise, and actionable insights.
Introduction to Network Isolation and Micro-segmentation
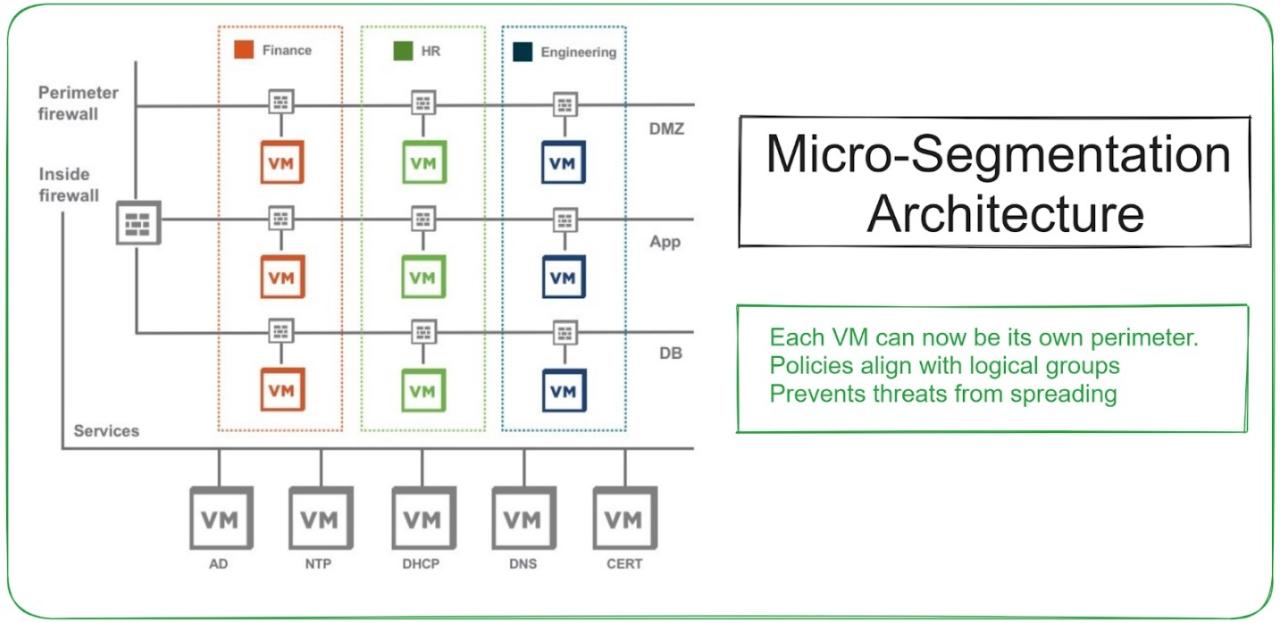
Network security is constantly evolving, and traditional perimeter-based defenses are proving insufficient against increasingly sophisticated threats. This necessitates a shift towards more granular and adaptive security strategies, with network isolation and micro-segmentation playing crucial roles. These approaches focus on limiting the lateral movement of attackers within a network, even if the perimeter is compromised.
Core Principles of Network Isolation
Network isolation involves segmenting a network into smaller, isolated zones to limit the impact of a security breach. The core principle is to restrict communication between these segments, preventing malware or unauthorized access from spreading beyond its initial point of entry. This can be achieved through various methods, including VLANs (Virtual LANs), firewalls, and dedicated network segments. The goal is to create a “defense in depth” strategy, where multiple layers of security work together to protect valuable assets.
Effective isolation requires careful planning and a deep understanding of network traffic flows to minimize disruption to legitimate communication while maximizing security.
Benefits of Implementing Micro-segmentation, Demystifying network isolation and micro segmentation 2
Micro-segmentation takes network isolation a step further by segmenting the network at a much finer granularity. Instead of isolating entire network segments, micro-segmentation focuses on isolating individual workloads, applications, or even virtual machines (VMs). This significantly reduces the attack surface and limits the blast radius of a successful breach. The benefits include improved security posture, reduced risk of lateral movement, enhanced compliance, and simplified incident response.
By isolating sensitive data and critical applications, organizations can minimize the potential impact of a security incident.
Traditional Network Security vs. Micro-segmentation
Traditional network security relies heavily on perimeter defenses, such as firewalls and intrusion detection systems (IDS), to protect the entire network. This approach is becoming increasingly ineffective against advanced threats that can bypass perimeter defenses and move laterally within the network. Micro-segmentation, on the other hand, focuses on internal security, segmenting the network at a much finer level to limit the impact of a breach.
It’s a more granular and adaptive approach that provides stronger protection against lateral movement and reduces the attack surface. Essentially, micro-segmentation complements traditional perimeter security, offering an additional layer of defense.
Real-World Scenarios Where Micro-segmentation is Beneficial
Micro-segmentation is particularly beneficial in environments with sensitive data, such as financial institutions, healthcare providers, and government agencies. For example, a hospital could isolate patient data from administrative systems, preventing unauthorized access to sensitive medical information even if the administrative network is compromised. Similarly, a financial institution could isolate trading systems from other applications, limiting the impact of a breach on critical financial operations.
In cloud environments, micro-segmentation helps protect individual VMs and containers, preventing attackers from moving laterally between them.
Comparison of Micro-segmentation Techniques
The following table compares different micro-segmentation techniques:
| Technique | Mechanism | Implementation Complexity | Scalability |
|---|---|---|---|
| VLANs | Network-level segmentation using VLAN tags | Relatively low | Good |
| Firewalls (Next-Generation Firewalls – NGFWs) | Packet filtering and inspection based on policies | Medium | Good |
| Software-Defined Networking (SDN) | Programmable network control plane for dynamic segmentation | High | Excellent |
| Container-level Security | Isolation at the container level using tools like Kubernetes Network Policies | Medium to High | Excellent |
Understanding Different Micro-segmentation Approaches

Micro-segmentation, as we’ve explored, is crucial for enhancing network security. But the “how” is where things get interesting. There isn’t a one-size-fits-all solution; various approaches exist, each with its strengths, weaknesses, and suitability for different scenarios. Understanding these nuances is key to implementing effective micro-segmentation.
Network Virtualization for Micro-segmentation
Network virtualization techniques, like virtual LANs (VLANs) and virtual private clouds (VPCs), offer a foundational layer for micro-segmentation. VLANs partition a physical network into multiple logical networks, isolating traffic based on VLAN tags. VPCs, commonly used in cloud environments, provide similar isolation but within a virtualized infrastructure. VLANs are simpler to implement in existing networks but can be less flexible and scalable compared to VPCs.
VPCs offer greater control and scalability, especially in dynamic cloud environments, but require more sophisticated management. A weakness of both approaches is the potential for misconfiguration leading to unintended security breaches if VLANs or VPCs are not carefully planned and managed. Scalability depends heavily on the underlying network infrastructure and management tools. For example, a small business might find VLANs sufficient, while a large enterprise might need the scalability of a VPC-based approach integrated with a robust network management system.
Policy-Based Micro-segmentation
Policy-based micro-segmentation uses software-defined networking (SDN) and security policies to control traffic flow. This approach offers granular control, allowing administrators to define precise rules based on various factors like application, user, and device. Examples include defining rules that allow only specific applications to communicate with each other or restricting access to sensitive data based on user roles. Strengths include fine-grained control and adaptability to changing network needs.
Weaknesses include the complexity of policy management, the potential for policy conflicts, and the need for robust monitoring to detect and mitigate policy-related issues. Scalability depends on the chosen SDN platform and its ability to handle a large number of policies and network elements. A well-designed policy-based system can scale to handle very large networks; however, poor policy design can lead to performance bottlenecks.
Host-Based Micro-segmentation
Host-based micro-segmentation relies on software agents deployed on individual servers or endpoints to enforce security policies. These agents monitor network traffic and enforce rules based on pre-defined policies. This approach provides granular control at the individual host level, allowing for very precise isolation of applications and services. The strengths lie in its granular control and ability to isolate applications even within a single host.
However, managing a large number of agents can be challenging and requires robust management tools. Scalability is generally good, provided the agent software is lightweight and efficient. A large-scale deployment may still require considerable administrative overhead.
Choosing a Micro-segmentation Solution: Key Considerations
Selecting the right micro-segmentation approach requires careful consideration of several factors. These include the size and complexity of the network, the existing infrastructure, the level of security required, the budget, and the available expertise. For example, a small business with a simple network might opt for a VLAN-based approach, while a large enterprise with complex applications and sensitive data might require a more sophisticated policy-based or host-based solution.
The cost of implementation and ongoing management should also be factored in.
Hypothetical Micro-segmented Network Architecture for a Small Business
Consider a small business with a network consisting of a server, a few workstations, and a guest Wi-Fi network. A suitable micro-segmentation strategy would involve using VLANs to isolate the server network from the workstation network and the guest Wi-Fi network. The server network would have strict access control policies, while the workstation network would have more relaxed policies, but still segmented from the guest Wi-Fi.
This provides a basic level of isolation while remaining relatively simple to manage. Adding a firewall between VLANs would further enhance security. This approach balances security with ease of management, suitable for a small business’s limited resources and technical expertise.
Implementing Micro-segmentation

Implementing micro-segmentation requires careful planning and the right tools. It’s not a simple “plug-and-play” solution, but rather a strategic shift in how you approach network security. Success hinges on choosing the appropriate technologies, integrating them effectively with your existing infrastructure, and establishing robust monitoring practices.
Software-Defined Networking (SDN) Tools for Micro-segmentation
Software-Defined Networking (SDN) offers powerful capabilities for implementing micro-segmentation. SDN controllers provide centralized management and policy enforcement across the network, allowing for granular control over traffic flow. Several vendors offer SDN solutions tailored for micro-segmentation. For example, VMware NSX leverages its virtual networking capabilities to create isolated segments, defining policies based on application, workload, or other criteria. Cisco ACI (Application Centric Infrastructure) similarly uses a policy-based approach to manage network traffic and enforce micro-segmentation rules.
These platforms offer sophisticated features like automated policy creation and enforcement, providing significant advantages over traditional methods. Open source SDN controllers, such as OpenDaylight, can also be used, though they may require more extensive configuration and integration effort.
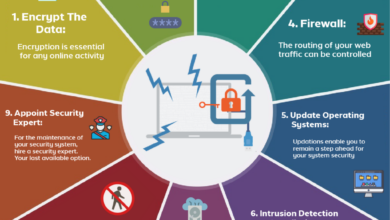
The Role of Firewalls and Intrusion Detection/Prevention Systems
Traditional firewalls and Intrusion Detection/Prevention Systems (IDPS) remain vital components in a micro-segmented environment. While micro-segmentation reduces the blast radius of a security breach, firewalls at the perimeter and between micro-segments provide an additional layer of defense. They act as gatekeepers, controlling traffic flow based on pre-defined rules. IDPS systems monitor network traffic for malicious activity within each micro-segment, offering early detection and prevention capabilities.
The integration of these technologies with the SDN controller allows for a unified security posture, where firewall rules and IDPS signatures are dynamically adjusted based on the micro-segmentation policies.
Network Monitoring and Visibility in a Micro-segmented Environment
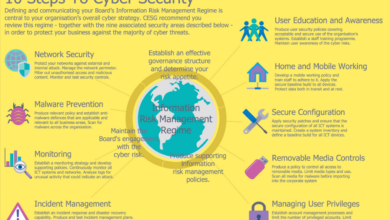
Maintaining comprehensive network visibility is crucial in a micro-segmented environment. The increased complexity introduced by micro-segmentation requires robust monitoring tools to track traffic flow, identify anomalies, and ensure the effectiveness of the security policies. Network monitoring tools should provide detailed insights into traffic patterns within each micro-segment, allowing security teams to quickly detect and respond to suspicious activity.
Centralized logging and analytics platforms are essential for correlating data from various sources, including firewalls, IDPS, and the SDN controller, to provide a holistic view of the network’s security posture. Real-time dashboards visualizing key metrics can help administrators proactively identify potential issues and ensure the smooth operation of the micro-segmented network.
Integrating Micro-segmentation with Existing Security Infrastructure
Integrating micro-segmentation with existing security infrastructure requires a phased approach. The initial step involves assessing the current infrastructure and identifying potential conflicts or gaps. This includes evaluating the compatibility of existing security tools with the chosen micro-segmentation platform. The integration process may involve updating existing firewalls, IDPS, and other security tools to work seamlessly with the new micro-segmentation architecture.
A gradual rollout, starting with less critical segments, is recommended to minimize disruption and allow for thorough testing and validation. Regular audits and security assessments are necessary to ensure the effectiveness of the integrated security solution.
Best Practices for Implementing Micro-segmentation
Implementing micro-segmentation effectively requires careful planning and execution. Here are some best practices:
- Start small and iterate: Begin with a pilot project focusing on a limited number of critical applications or workloads. This allows for testing and refinement before expanding to the entire network.
- Define clear segmentation criteria: Establish criteria for segmenting the network based on factors such as application, workload, sensitivity of data, or user roles.
- Automate policy management: Utilize automated tools to manage and enforce micro-segmentation policies, reducing the risk of human error and improving efficiency.
- Implement robust monitoring and alerting: Establish comprehensive monitoring and alerting mechanisms to detect anomalies and security breaches within micro-segments.
- Regularly review and update policies: Micro-segmentation policies should be regularly reviewed and updated to adapt to changes in the network environment and security threats.
Addressing Challenges in Micro-segmentation
Implementing micro-segmentation offers significant security benefits, but it’s not without its hurdles. Successfully deploying and managing a micro-segmented network requires careful planning, robust tooling, and a dedicated operational approach. Ignoring these challenges can lead to decreased performance, increased complexity, and ultimately, a less secure environment.
Micro-segmentation Policy Management Complexity
Managing micro-segmentation policies can be incredibly complex. As the number of segments and applications grows, so does the complexity of defining and maintaining the rules that govern communication between them. This complexity stems from the granular level of control required. Each policy must be meticulously crafted to allow necessary communication while strictly limiting unnecessary access. A single misconfiguration can create security vulnerabilities or disrupt critical business operations.
For example, mistakenly blocking communication between a database server and its application tier can lead to application outages. Effective management requires robust automation tools and a well-defined policy management process, including rigorous testing and version control. Furthermore, changes to the application architecture or network infrastructure necessitate corresponding updates to the micro-segmentation policies, adding to the ongoing management overhead.
Impact of Micro-segmentation on Network Performance
The introduction of micro-segmentation can impact network performance if not implemented carefully. Each segment adds an extra layer of network traversal, potentially increasing latency and reducing throughput. This is especially true if the chosen micro-segmentation solution relies on deep packet inspection or other computationally intensive techniques. For instance, a poorly configured solution might lead to noticeable delays in application response times, impacting user experience.
Continuing our deep dive into demystifying network isolation and micro-segmentation, a key consideration is application architecture. For instance, the robust security offered by micro-segmentation becomes even more powerful when paired with modern application development strategies, like those explored in this insightful article on domino app dev: the low-code and pro-code future. Understanding how applications are built directly impacts how effectively we can isolate and protect them, bringing us back to the core principles of effective network segmentation.
To mitigate this, it’s crucial to select a high-performance solution and optimize the micro-segmentation policies to minimize unnecessary network hops. Careful consideration should be given to the placement of security controls and the use of optimized routing protocols.
Troubleshooting Micro-segmented Environments
Troubleshooting in a micro-segmented environment differs significantly from traditional network troubleshooting. The granular nature of segmentation makes it more challenging to isolate issues. Traditional tools may not provide the necessary visibility into inter-segment communication. Effective troubleshooting requires specialized tools capable of monitoring traffic flows within and between segments. For instance, identifying the source of a communication failure might involve analyzing logs from multiple security controls and network devices to pinpoint the specific policy or infrastructure component causing the problem.
This often necessitates a deeper understanding of the micro-segmentation architecture and the policies in place. A systematic approach, utilizing network monitoring tools and detailed logs, is crucial for effective troubleshooting.
Incident Response in a Micro-segmented Network
A well-defined incident response process is essential for a micro-segmented network. The containment phase of incident response benefits greatly from micro-segmentation’s inherent isolation capabilities. However, the investigation phase can be more complex due to the numerous segments and the need to trace communication flows across them. The following flowchart illustrates a typical incident response process in a micro-segmented environment:
Incident Response Flowchart
(Imagine a flowchart here. The flowchart would begin with “Incident Detected,” branching to “Initial Containment (Isolate affected segment),” then “Investigation (Analyze logs, network traffic, etc.),” followed by “Remediation (Fix vulnerability, restore services),” and finally “Post-Incident Activity (Review, improve policies, etc.).” Each stage would have associated actions and considerations relevant to a micro-segmented environment, such as specific tools used for analysis and the need for careful coordination across different segments.)
Future Trends in Network Isolation and Micro-segmentation
The landscape of network security is constantly evolving, driven by the increasing sophistication of cyber threats and the adoption of cloud-native architectures. Micro-segmentation, already a cornerstone of modern security, is poised for significant advancements, fueled by emerging technologies and shifting security paradigms. The future of network isolation and micro-segmentation promises more intelligent, automated, and adaptable solutions.
Artificial Intelligence and Machine Learning in Micro-segmentation
AI and ML are revolutionizing micro-segmentation by enabling more dynamic and responsive security policies. Instead of relying on static rules, AI-powered systems can analyze network traffic patterns, user behavior, and threat intelligence to automatically identify and isolate compromised devices or applications in real-time. For instance, an AI system could detect anomalous network activity from a specific server, automatically isolating it from the rest of the network before a full-blown attack can occur.
This proactive approach minimizes the impact of breaches and improves overall security posture. Machine learning algorithms can also be used to predict potential vulnerabilities and proactively adjust micro-segmentation policies to mitigate risks. This predictive capability moves beyond reactive security measures, anticipating threats before they materialize.
Predictions for the Future Evolution of Micro-segmentation Technologies
We can expect to see a continued shift towards more granular and context-aware micro-segmentation. This means moving beyond simple network segmentation based on IP addresses or VLANs towards segmentation based on application behavior, user roles, and data sensitivity. Future micro-segmentation technologies will likely incorporate advanced analytics and automation capabilities, minimizing the need for manual configuration and management. For example, we can anticipate self-learning micro-segmentation systems that adapt to changing network conditions and threat landscapes without human intervention.
The integration of micro-segmentation with other security tools, such as intrusion detection systems and security information and event management (SIEM) systems, will also become more seamless and sophisticated, creating a more holistic security approach. Imagine a future where micro-segmentation automatically adjusts its policies based on real-time threat intelligence feeds from a SIEM system, dynamically adapting to emerging threats.
The Impact of Zero-Trust Security Models on Micro-segmentation
Zero-trust security models, which assume no implicit trust within the network, are perfectly aligned with the principles of micro-segmentation. Micro-segmentation inherently embodies the zero-trust philosophy by verifying and controlling access to every resource within the network, regardless of its location or user identity. The adoption of zero-trust will further drive the demand for more granular and context-aware micro-segmentation, as organizations strive to enforce least privilege access and minimize the blast radius of potential security breaches.
A successful implementation of zero trust heavily relies on effective micro-segmentation to enforce granular access control and prevent lateral movement within the network. For example, a zero-trust implementation might use micro-segmentation to isolate sensitive databases, ensuring that only authorized users and applications can access them, even if other parts of the network are compromised.
Innovative Approaches to Network Isolation
Beyond traditional micro-segmentation techniques, we’re seeing the emergence of innovative approaches to network isolation. Software-defined networking (SDN) is playing a crucial role, enabling dynamic and flexible network segmentation that can be easily adapted to changing requirements. Furthermore, technologies like containerization and serverless computing are driving the need for micro-segmentation at the application level, isolating individual containers or serverless functions from each other.
This granular approach to isolation provides better protection against vulnerabilities and limits the impact of breaches. For instance, a microservices architecture, where applications are broken down into smaller, independent services, benefits greatly from micro-segmentation, allowing for independent isolation and management of each service.
Implications of Cloud-Native Micro-segmentation
As more organizations migrate to cloud-native architectures, the demand for effective micro-segmentation in the cloud is increasing. Cloud-native micro-segmentation requires solutions that can seamlessly integrate with cloud platforms and leverage their native capabilities for security. This includes utilizing cloud-based security tools and services for automated policy enforcement and threat detection. For example, cloud providers often offer micro-segmentation services that leverage their infrastructure for efficient and scalable isolation.
These services can dynamically adjust security policies based on cloud resource usage and activity, ensuring consistent security across hybrid and multi-cloud environments. Effective cloud-native micro-segmentation is crucial for protecting applications and data in dynamic and distributed cloud environments.
Case Studies
Let’s delve into some real-world examples showcasing the power and effectiveness of micro-segmentation. These case studies highlight successful implementations across various industries and demonstrate how micro-segmentation can significantly enhance security and operational efficiency. We’ll examine both the benefits and the challenges encountered during implementation.
Micro-segmentation in a Large Financial Institution
A major global bank implemented micro-segmentation to protect its core banking systems. Facing increasing threats of sophisticated cyberattacks, they segmented their network into smaller, isolated zones based on application and data sensitivity. Critical systems like transaction processing and customer data management were placed in highly restricted zones, with strict access control policies enforced at each segment boundary. This granular control prevented lateral movement of attackers, even if an initial breach occurred.
The implementation involved a phased approach, starting with high-value assets and gradually expanding to other parts of the network. This minimized disruption to ongoing operations and allowed for thorough testing and validation at each stage. The result was a significant reduction in the attack surface and a demonstrable improvement in the bank’s overall security posture. Incident response times also improved dramatically, as the scope of potential damage was greatly reduced by the isolation of compromised segments.
Micro-segmentation Benefits in the Healthcare Industry
A large healthcare provider implemented micro-segmentation to protect patient data under HIPAA regulations. By segmenting their network based on data sensitivity and user roles, they were able to enforce stricter access controls, ensuring that only authorized personnel could access sensitive patient information. This approach significantly reduced the risk of data breaches and HIPAA violations. Moreover, the improved network visibility provided by micro-segmentation allowed the IT team to more effectively monitor network traffic and identify potential security threats in real-time.
This proactive approach to security resulted in fewer incidents and faster response times when issues did arise. The cost savings from avoided fines and legal battles were substantial, offsetting the initial investment in the micro-segmentation solution.
Mitigating Ransomware with Micro-segmentation
A manufacturing company successfully used micro-segmentation to mitigate a ransomware attack. While a phishing email initially compromised a workstation in the marketing department, the micro-segmentation prevented the ransomware from spreading to other parts of the network, including the critical production systems. The isolated segment containing the compromised workstation was quickly quarantined, limiting the damage to a small, manageable area.
The company was able to recover from the attack much faster and with significantly less disruption than they would have experienced without micro-segmentation. This rapid containment significantly reduced the financial and operational impact of the attack. The incident underscored the importance of micro-segmentation as a critical component of a robust cybersecurity strategy.
Picking up where we left off with demystifying network isolation and micro-segmentation, effective security hinges on a robust understanding of your entire attack surface. This is where cloud security posture management (CSPM) becomes crucial, and understanding tools like Bitglass is key; check out this great article on bitglass and the rise of cloud security posture management for more insights.
Ultimately, strong CSPM practices complement and enhance the benefits of micro-segmentation, creating a layered defense strategy.
| Case Study | Industry | Key Benefits | Security Threat Addressed |
|---|---|---|---|
| Large Financial Institution | Finance | Reduced attack surface, improved incident response, enhanced security posture | Sophisticated cyberattacks |
| Large Healthcare Provider | Healthcare | Reduced data breach risk, improved HIPAA compliance, enhanced network visibility | Data breaches, HIPAA violations |
| Manufacturing Company | Manufacturing | Contained ransomware spread, minimized operational disruption, reduced financial impact | Ransomware attack |
Outcome Summary: Demystifying Network Isolation And Micro Segmentation 2
So, there you have it – a deep dive into demystifying network isolation and micro-segmentation. We’ve explored the various techniques, tools, and challenges involved in implementing this powerful security strategy. Remember, effective network security is an ongoing process, and staying informed about the latest trends and technologies is critical. By understanding and implementing micro-segmentation, you can significantly reduce your attack surface and protect your valuable data.
Let’s continue the conversation – what are your biggest challenges when it comes to network security?
Answers to Common Questions
What’s the difference between network isolation and micro-segmentation?
Network isolation is a broad term referring to separating different parts of a network. Micro-segmentation takes this further by isolating individual applications, workloads, or even virtual machines, offering a much finer-grained level of control.
Is micro-segmentation suitable for all organizations?
While beneficial for many, the complexity and resource requirements might make it less suitable for very small organizations. Larger organizations with complex networks and sensitive data often benefit the most.
How does micro-segmentation impact network performance?
Properly implemented micro-segmentation shouldn’t significantly impact performance. However, poorly planned or overly granular segmentation can introduce latency. Careful planning and choosing the right tools are crucial.
What are the key metrics for measuring the success of micro-segmentation?
Key metrics include reduced attack surface, faster incident response times, improved compliance posture, and minimized lateral movement of threats.