
Demystifying PBOM and SBOM Understanding Key Differences
Demystifying pbom and sbom understanding the key differences – Demystifying PBOM and SBOM: Understanding the key differences is crucial in today’s complex software and hardware landscape. Ever wondered what exactly these acronyms mean and why they matter? This post dives deep into the world of Product Bills of Materials (PBOMs) and Software Bills of Materials (SBOMs), exploring their core components, data formats, and the significant implications for security and supply chain management.
We’ll unravel the mysteries surrounding these essential documents and show you how understanding their differences can significantly improve your risk management strategies.
From comparing their structures and purposes to examining their roles in vulnerability management, we’ll cover a wide range of topics. We’ll also look at practical applications across various industries and discuss future trends shaping the landscape of PBOM and SBOM management. Get ready to become fluent in the language of PBOMs and SBOMs!
Introduction to PBOM and SBOM: Demystifying Pbom And Sbom Understanding The Key Differences
Understanding the components and relationships within a product, whether physical or software-based, is crucial for efficient management, security, and compliance. This involves utilizing two key documents: the Product Bill of Materials (PBOM) and the Software Bill of Materials (SBOM). While both serve to list components, their focus and application differ significantly.
A PBOM, or Product Bill of Materials, is a comprehensive list of all the physical components, parts, sub-assemblies, raw materials, and instructions needed to manufacture a product. It’s essentially a recipe for building something tangible, from a simple toy to a complex piece of machinery. An SBOM, or Software Bill of Materials, on the other hand, details the software components, libraries, and dependencies that make up a software application.
It’s a detailed inventory of the software building blocks.
PBOM Components
A PBOM typically includes detailed information about each component, such as part numbers, descriptions, quantities, manufacturers, suppliers, and specifications. It may also include cost information, weight, and other relevant data. For example, a PBOM for a bicycle would list the frame, wheels, handlebars, gears, brakes, and all the smaller parts, specifying their individual characteristics. This detailed information facilitates efficient manufacturing, inventory management, and cost tracking.
SBOM Components
An SBOM lists all the software components that constitute a software application. This includes libraries, frameworks, modules, dependencies, and even the version numbers of each. It also often includes metadata about the components, such as licensing information, security vulnerabilities, and checksums to verify integrity. For instance, an SBOM for a web application might include details about the specific versions of Node.js, React, and various other packages used in its development.
This granular level of detail is essential for software security and vulnerability management.
PBOM and SBOM Usage in Different Industries, Demystifying pbom and sbom understanding the key differences
PBOMs are widely used in manufacturing industries such as automotive, aerospace, electronics, and construction. They are critical for managing supply chains, ensuring product quality, and complying with regulatory requirements. For example, in the automotive industry, a PBOM is essential for tracking every part used in a vehicle, from the engine to the seatbelts.SBOMs are increasingly vital in software development, particularly in industries with stringent security and compliance needs like healthcare, finance, and government.
They are used to identify and mitigate security vulnerabilities, manage software licenses, and track compliance with regulations like the NIST Cybersecurity Framework and the EU’s Cybersecurity Act. For example, in the healthcare sector, an SBOM can help ensure that medical devices and software applications are free from known vulnerabilities that could compromise patient data or device functionality.
Comparison of PBOM and SBOM
| Feature | PBOM | SBOM |
|---|---|---|
| Focus | Physical components | Software components |
| Components | Parts, sub-assemblies, raw materials | Libraries, frameworks, dependencies |
| Data Included | Part numbers, quantities, specifications, cost | Version numbers, licenses, vulnerabilities, checksums |
| Primary Use | Manufacturing, supply chain management | Software security, vulnerability management, compliance |
Data Representation in PBOMs and SBOMs
Choosing the right data format for your PBOM (Product Bill Of Materials) and SBOM (Software Bill Of Materials) is crucial for efficient data management, analysis, and interoperability. The format you select will directly impact how easily you can share, process, and utilize this vital information throughout your product lifecycle. Different formats offer varying strengths and weaknesses, and understanding these nuances is key to making an informed decision.The selection of a data format significantly impacts how easily you can share, process, and utilize PBOM and SBOM data throughout the product lifecycle.
Different formats offer distinct advantages and disadvantages, and a thorough understanding of these factors is essential for informed decision-making.
Common Data Formats for PBOMs and SBOMs
Several data formats are commonly used for representing PBOM and SBOM information. The most prevalent include CSV, JSON, and XML. Each has its own strengths and weaknesses regarding readability, complexity, and suitability for different applications.
- CSV (Comma Separated Values): A simple, human-readable format ideal for basic data representation. Its simplicity makes it easy to generate and parse, but it lacks the structured capabilities of more complex formats, limiting its usefulness for intricate BOMs.
- JSON (JavaScript Object Notation): A lightweight, text-based format that uses a key-value pair structure. It’s widely used for data exchange on the web due to its readability and efficiency. JSON is better suited for representing complex hierarchical structures than CSV, making it more suitable for representing detailed BOM information.
- XML (Extensible Markup Language): A more complex, verbose format that uses tags to define data elements. XML offers extensive capabilities for defining custom structures and schemas, allowing for a highly detailed and structured representation of BOM information. However, its complexity can make it less efficient and more difficult to parse than JSON.
Advantages and Disadvantages of Different Data Formats
The choice between CSV, JSON, and XML often depends on the specific needs of the project.
| Format | Advantages | Disadvantages |
|---|---|---|
| CSV | Simple, human-readable, easily parsed. | Limited structure, not suitable for complex BOMs, lacks schema validation. |
| JSON | Lightweight, efficient, widely used, supports complex structures. | Can become less readable with deeply nested structures. |
| XML | Highly structured, allows for custom schemas, extensive validation capabilities. | Verbose, complex, can be difficult to parse and less efficient than JSON. |
The Importance of Standardized Data Formats for Interoperability
Standardized data formats are crucial for ensuring interoperability between different tools and systems used in the product lifecycle. Without standardization, exchanging BOM data between different platforms and applications becomes extremely difficult, leading to data silos and inefficiencies. Standardized formats facilitate seamless data sharing and integration, enabling better collaboration and automation. For example, the adoption of SPDX (Software Package Data Exchange) for SBOMs promotes interoperability by providing a common vocabulary and structure for representing software component information.
Example PBOM and SBOM in JSON Format
JSON’s flexibility and widespread adoption make it a suitable choice for representing both PBOM and SBOM data.
PBOM Example
"product": "Widget X", "components": [ "name": "Part A", "quantity": 2, "manufacturer": "Acme Corp" , "name": "Part B", "quantity": 1, "manufacturer": "Beta Inc" ]
SBOM Example
"spdxVersion": "SPDX-2.3", "name": "My Software", "components": [ "name": "Library Z", "version": "1.0", "license": "MIT" , "name": "Framework Y", "version": "2.2", "license": "GPLv3" ]
Key Differences between PBOM and SBOM
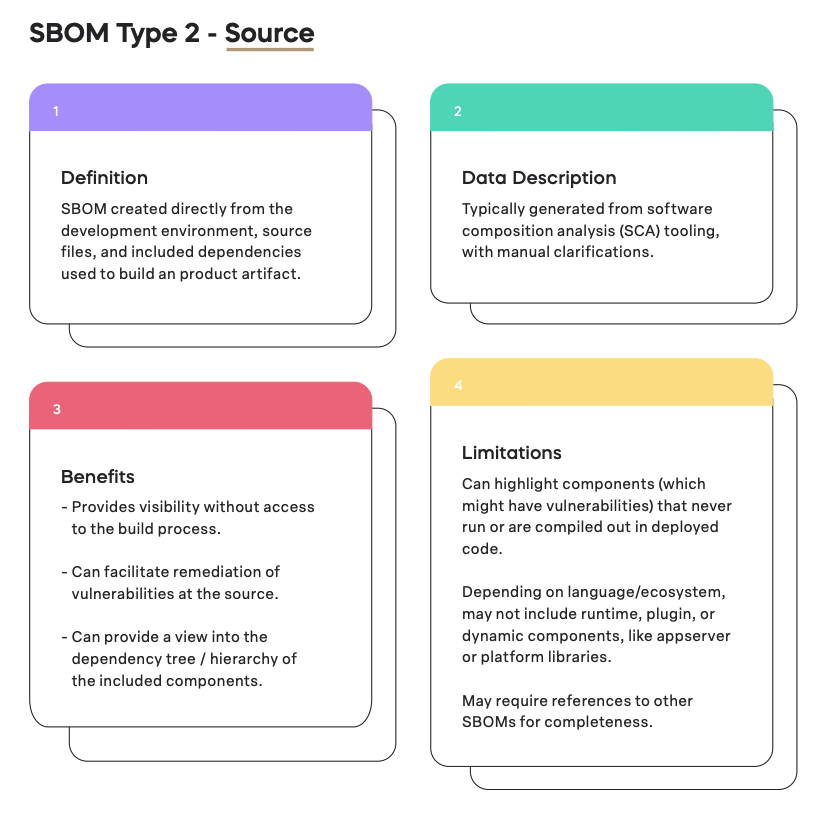
Understanding the distinctions between a Product Bill of Materials (PBOM) and a Software Bill of Materials (SBOM) is crucial for effective supply chain risk management. While both document the components of a product, their scope, content, and implications for security differ significantly. This leads to different approaches in risk assessment and mitigation.
The core difference lies in their focus: PBOMs detail the physical components of a product, while SBOMs focus on the software components within a product or system. This seemingly simple distinction has profound consequences for how we understand and manage vulnerabilities.
Scope and Content Differences
The scope of a PBOM is broad, encompassing all the physical parts, sub-assemblies, and raw materials necessary to manufacture a product. Think of the detailed list of parts in a car, from the engine block to the seatbelts. Conversely, an SBOM focuses specifically on the software components, including libraries, frameworks, and other software modules, used in a product.
This might include information about the specific versions of open-source packages used in a piece of software or an embedded system.
Security and Supply Chain Management Implications
These differences directly impact security and supply chain management. A PBOM helps manage physical supply chains, ensuring the availability of parts and tracking their origin. However, it doesn’t address the software vulnerabilities that can compromise a product’s security. The SBOM, on the other hand, is critical for identifying and mitigating software-related risks. It allows for vulnerability scanning and patching, providing a crucial layer of security in an increasingly software-defined world.
Examples Illustrating Risk Assessment and Mitigation
Consider a medical device. A PBOM might detail the various sensors, processors, and housings used in its construction. However, if a critical software library within the device contains a known vulnerability, this would only be revealed by an SBOM. This vulnerability could allow unauthorized access or malfunction, potentially endangering patients. A comprehensive SBOM allows for timely patching, reducing the risk.
Similarly, in automotive software, an SBOM enables identifying vulnerable components within the car’s infotainment system or autonomous driving software, allowing for prompt security updates to prevent hacking or malfunctions.
Comparison of PBOM and SBOM
The following bullet points highlight the key distinctions between PBOMs and SBOMs:
- Focus: PBOM – Physical components; SBOM – Software components
- Scope: PBOM – Encompasses all physical parts and materials; SBOM – Focuses on software libraries, frameworks, and modules.
- Data Type: PBOM – Primarily descriptive data about physical parts; SBOM – Includes descriptive data and version information, hashes, and license details.
- Security Implications: PBOM – Primarily relates to physical supply chain risks; SBOM – Directly addresses software vulnerabilities and security risks.
- Risk Assessment: PBOM – Helps assess risks related to part availability and quality; SBOM – Enables identification and assessment of software vulnerabilities and their potential impact.
- Mitigation Strategies: PBOM – Focuses on supply chain diversification and quality control; SBOM – Enables vulnerability patching, security audits, and software updates.
Security Implications and Vulnerability Management
SBOMs and PBOMs, while serving different purposes, both play crucial roles in managing the security risks associated with software and hardware components. Understanding their contribution to vulnerability identification and remediation is vital for building secure and resilient systems. This section delves into the security implications of both, highlighting their individual strengths and weaknesses in vulnerability management.SBOMs significantly enhance vulnerability identification and remediation.
By providing a comprehensive inventory of software components, including their versions and licenses, SBOMs allow organizations to quickly identify components with known vulnerabilities. This facilitates proactive patching and mitigation efforts, minimizing the system’s exposure to attacks. Automated tools can scan SBOMs against vulnerability databases, flagging potential risks and prioritizing remediation actions. This automated approach reduces the manual effort involved in vulnerability assessment and dramatically speeds up the response time to security threats.
SBOM Contribution to Vulnerability Management
SBOMs enable efficient vulnerability management through automated scanning and reporting. Tools can cross-reference the SBOM with publicly available vulnerability databases (like the National Vulnerability Database or CVE) to identify known vulnerabilities present in the system’s software components. This allows for proactive patching and mitigation, minimizing the window of vulnerability. For example, if an SBOM reveals the use of a specific version of a library known to have a critical vulnerability (e.g., a remote code execution flaw), the organization can immediately prioritize patching that library.
This rapid response reduces the likelihood of successful exploitation.
PBOM Role in Hardware Vulnerability Identification
While SBOMs focus on software, PBOMs provide a critical view of hardware components and their potential vulnerabilities. Knowing the precise hardware components used in a system allows for effective identification of potential hardware-related weaknesses. For instance, a PBOM could reveal the use of a specific chipset known to have a vulnerability to side-channel attacks. This knowledge allows for informed decisions on mitigation strategies, such as firmware updates or implementing countermeasures to protect against these attacks.
In cases of critical hardware vulnerabilities, PBOMs guide decisions on whether to replace or isolate affected hardware.
Security Risks of Incomplete or Inaccurate SBOMs and PBOMs
Incomplete or inaccurate SBOMs and PBOMs pose significant security risks. An incomplete SBOM might omit critical components, leaving vulnerabilities undetected. This can lead to successful attacks that exploit these overlooked vulnerabilities. Similarly, inaccurate information in an SBOM, such as incorrect component versions, can lead to ineffective patching and continued exposure to vulnerabilities. In the case of PBOMs, inaccurate information on hardware components could lead to inadequate security measures being implemented, leaving the system vulnerable to hardware-specific attacks.For example, imagine a system’s SBOM omits a third-party library used for authentication.
A known vulnerability in that library could go unnoticed, leaving the system susceptible to unauthorized access. Similarly, an inaccurate PBOM stating an older, less secure version of a CPU could result in the system being left vulnerable to exploits targeting that specific CPU model. The consequences can range from data breaches and system compromises to complete system failure.
Examples of Vulnerability Impact
Consider a medical device with an incomplete PBOM. If the PBOM doesn’t list a specific microcontroller, a critical vulnerability in that microcontroller’s firmware might remain unknown, potentially leading to device malfunction during a critical procedure. This could have serious consequences for patient safety. Similarly, an inaccurate SBOM in a financial system could lead to the failure to patch a known vulnerability in a crucial transaction processing component, leaving the system open to fraud and financial loss.
These examples highlight the importance of accurate and complete SBOMs and PBOMs in ensuring system security and reliability.
Practical Applications and Use Cases

PBOMs and SBOMs, while distinct, offer powerful capabilities when integrated into various stages of the software development lifecycle (SDLC) and across diverse industries. Their combined use significantly enhances transparency, security, and collaboration, ultimately leading to more robust and reliable software systems. Let’s explore some practical applications and real-world examples.
PBOM and SBOM Usage in Different SDLC Phases
PBOMs and SBOMs play crucial roles throughout the SDLC. During the design phase, PBOMs help define the complete hardware and software bill of materials, facilitating early identification of potential compatibility issues. In the development phase, SBOMs track software components, aiding in dependency management and vulnerability detection. Testing and deployment benefit from both, enabling efficient verification of system integrity and facilitating rapid response to discovered vulnerabilities.
Finally, maintenance and updates are streamlined with readily available component information provided by both PBOMs and SBOMs. This comprehensive approach minimizes risks and maximizes efficiency across the entire lifecycle.
Real-World Examples of Successful Implementations
Several industries are successfully leveraging PBOMs and SBOMs. In the automotive industry, PBOMs are essential for managing complex electronic systems in vehicles, ensuring compliance with safety standards and facilitating recalls if necessary. The aerospace industry utilizes both PBOMs and SBOMs for mission-critical systems, where component traceability and reliability are paramount. In the medical device sector, precise tracking of components through PBOMs and SBOMs is crucial for regulatory compliance and patient safety.
These examples highlight the versatility and importance of these tools in high-stakes environments.
Benefits of Integrating PBOM and SBOM Data into Existing Workflows
Integrating PBOM and SBOM data into existing workflows yields several benefits. Automated vulnerability scanning becomes significantly more efficient, reducing the time and resources needed to identify and remediate security risks. Compliance with industry regulations, such as those mandated by government agencies or specific industries, becomes simpler and more demonstrable. Improved supply chain visibility allows for quicker identification of problematic components and more proactive risk mitigation.
Ultimately, this leads to cost savings, reduced downtime, and enhanced reputation for producing secure and reliable products.
Hypothetical Scenario: Collaborative Project Utilizing PBOM and SBOM
Imagine a collaborative project developing a complex IoT device involving multiple teams: hardware designers, software developers, and security experts. The hardware team generates a detailed PBOM, outlining all physical components, including their manufacturers, versions, and certifications. Concurrently, the software team creates an SBOM, detailing all software libraries, dependencies, and their respective licenses. The security team uses both documents to perform vulnerability scans, identifying potential weaknesses early in the development process.
By integrating this information, the teams proactively address potential issues, ensuring a secure and compliant final product. This collaborative approach, facilitated by the clear and structured information provided by PBOMs and SBOMs, significantly reduces risks and improves overall project efficiency.
Future Trends and Considerations
The landscape of software supply chain security is rapidly evolving, driven by increasing reliance on open-source components and the growing sophistication of cyber threats. PBOMs and SBOMs are at the forefront of this evolution, and their future hinges on advancements in automation, standardization, and integration with other security tools. The coming years will see significant shifts in how these crucial documents are created, managed, and utilized.The widespread adoption of PBOMs and SBOMs faces several challenges and opportunities.
While the benefits of enhanced transparency and vulnerability management are clear, significant hurdles remain in terms of standardization, tool integration, and the sheer volume of data involved in managing complex software systems. However, these challenges also present opportunities for innovation and the development of new technologies and methodologies.
Automation and AI in PBOM and SBOM Management
Automation is key to overcoming the challenges of managing the large volumes of data associated with PBOMs and SBOMs. Tools are emerging that automatically generate these documents from build systems and software repositories. Artificial intelligence (AI) can further enhance this process by identifying potential vulnerabilities and inconsistencies within the data, flagging them for human review and remediation. For instance, AI could analyze an SBOM to identify components with known vulnerabilities and prioritize remediation efforts based on the severity of the risk.
This automated analysis allows for faster response times to security threats and reduces the manual effort required for vulnerability management.
Challenges and Opportunities in Widespread Adoption
One major challenge is the lack of consistent standards for PBOM and SBOM formats and content. While efforts are underway to standardize these formats (e.g., SPDX), achieving widespread adoption remains a significant hurdle. This lack of standardization hinders interoperability between different tools and systems, making it difficult to share and analyze SBOMs effectively across the software supply chain.
However, this also presents an opportunity for the development of robust, interoperable tools and platforms that can handle multiple SBOM formats and seamlessly integrate with existing security tools. The opportunity also lies in educating developers and organizations about the benefits of using PBOMs and SBOMs and providing clear guidelines on their implementation.
Evolution of Standards and Best Practices
The standardization of PBOM and SBOM formats is crucial for widespread adoption. Organizations like the SPDX (Software Package Data Exchange) are actively working to develop and refine standards for representing software component information. Best practices are also evolving, emphasizing the importance of incorporating SBOM generation into the software development lifecycle (SDLC) from the beginning. This includes integrating SBOM generation tools into CI/CD pipelines and establishing clear processes for reviewing and updating SBOMs as the software evolves.
This ongoing evolution will drive better integration and compatibility between tools, facilitating more efficient vulnerability management and improved software supply chain security.
Future Technological Advancements
Future technological advancements in areas like blockchain technology could revolutionize SBOM management. Blockchain’s immutable ledger could provide a secure and transparent way to track the provenance of software components, ensuring the authenticity and integrity of SBOMs. Furthermore, advancements in AI and machine learning will continue to improve the accuracy and efficiency of vulnerability detection and risk assessment within SBOMs.
Imagine a future where AI-powered tools can not only identify vulnerabilities but also automatically suggest remediation strategies and even generate patches. This would significantly enhance the speed and effectiveness of vulnerability management, enabling organizations to respond more quickly and efficiently to emerging threats. For example, a future system might automatically generate a patch for a vulnerable component identified in an SBOM, significantly reducing the time-to-remediation.
Final Conclusion
So, there you have it – a clearer picture of PBOMs and SBOMs and their distinct roles. While seemingly similar, understanding their key differences is critical for effective security and supply chain management. By embracing both PBOM and SBOM practices, organizations can proactively identify and mitigate risks, fostering greater transparency and resilience in their operations. Hopefully, this demystification empowers you to leverage these tools for improved security and efficiency in your projects.
Answers to Common Questions
What are the legal implications of not having an SBOM?
The legal landscape surrounding SBOMs is evolving. Increasingly, regulations mandate SBOM provision for certain software, especially in government contracts and critical infrastructure. Non-compliance can lead to penalties and legal challenges.
Can I generate an SBOM automatically?
Yes, many tools and platforms now automate SBOM generation. The specific method depends on your development environment and chosen SBOM format. Several open-source and commercial solutions are available.
How often should SBOMs be updated?
SBOMs should be updated whenever changes are made to the software’s components. This could be after each release, or even more frequently depending on the project’s complexity and security requirements. Continuous integration/continuous delivery (CI/CD) pipelines can automate this process.
What’s the difference between a CycloneDX and SPDX SBOM?
Both CycloneDX and SPDX are popular SBOM formats. CycloneDX is known for its ease of use and machine readability, while SPDX offers a more comprehensive and detailed representation of software components. The choice often depends on specific needs and tooling.





