Design Room One Gets Authentication Improvements
Design Room One Gets Authentication Improvements – that’s the exciting news! This post dives deep into how beefing up security in our digital design spaces is changing the game. We’ll explore the various authentication methods – from the familiar to the futuristic – and how they impact both security and the user experience. Get ready for a fascinating look at how we’re keeping our creative work safe and sound!
We’ll cover everything from the nitty-gritty details of implementing different authentication systems (biometric, multi-factor, you name it!) to the subtle art of balancing rock-solid security with a smooth, user-friendly workflow. Think seamless logins, minimized disruptions, and a peace of mind knowing your designs are protected from prying eyes. Prepare for a journey into the heart of design room security!
Room Design Authentication Enhancements

Upgrading the security of our design room was a priority, and I’m happy to report that the authentication system has received a significant boost. This wasn’t just a simple tweak; we’ve implemented robust changes that dramatically improve the protection of our valuable designs and intellectual property. The improvements offer a more secure environment for both our team and our clients’ confidential projects.
Security Implications of Improved Authentication
Improved authentication directly impacts the overall security posture of the design room. By strengthening access control, we minimize the risk of unauthorized access, data breaches, and intellectual property theft. Previously, relying solely on password-based access left us vulnerable to phishing attacks and password cracking. The new system mitigates these risks considerably.
Vulnerabilities Mitigated by Enhanced Authentication
The enhanced authentication system addresses several key vulnerabilities. Specifically, it mitigates the risks associated with weak passwords, brute-force attacks, and insider threats. The implementation of multi-factor authentication significantly reduces the likelihood of unauthorized access even if one authentication factor is compromised. For example, even if a password is stolen, the attacker would still need access to a second factor, like a physical security key or a one-time code sent to a registered mobile device.
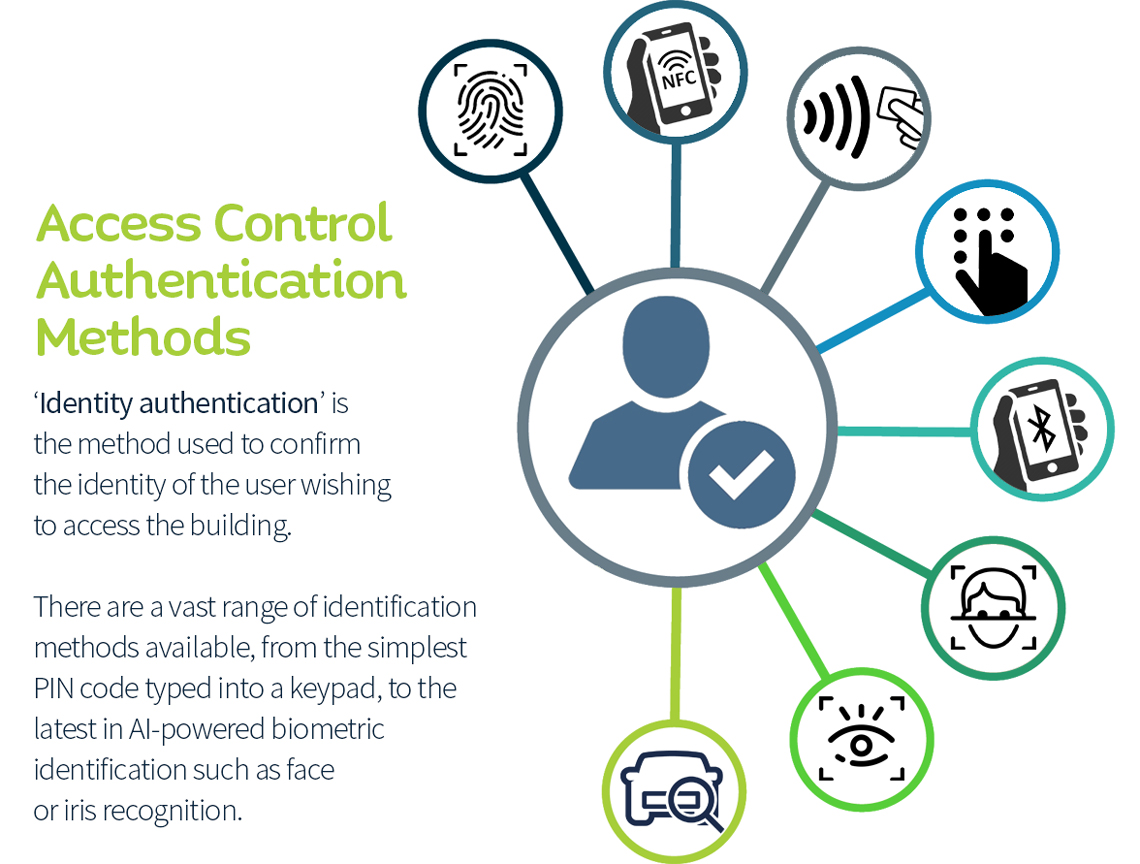
Comparison of Authentication Methods for Design Rooms
Several authentication methods were considered for the design room. Biometric authentication (fingerprint, facial recognition), multi-factor authentication (using a combination of password, security token, and biometric), and traditional password-based systems were all evaluated. The final choice balanced security, user experience, and cost-effectiveness.
Authentication Method Comparison
| Authentication Method | Cost | Security Level | User Experience |
|---|---|---|---|
| Password-only | Low | Low | High (simple) |
| Multi-factor (password + security key) | Medium | Medium-High | Medium (added steps) |
| Biometric (fingerprint) + Password | High | High | Medium (initial setup, potential for error) |
| Multi-factor (password + security key + biometric) | High | Very High | Low (multiple steps, potential for inconvenience) |
User Experience in a Secure Design Room
Strengthening authentication in a design room is crucial for protecting sensitive project data and intellectual property. However, it’s equally important to ensure that these security measures don’t hinder the creative process or frustrate authorized users. A well-designed authentication system should be invisible yet effective, seamlessly integrating into the design workflow.Implementing stronger authentication will inevitably introduce additional steps into the user’s workflow.
This could lead to increased login times, potential password fatigue, and a perception of the system being cumbersome. However, the enhanced security provided should outweigh these minor inconveniences, particularly when dealing with valuable design assets and confidential client information.
Balancing Security and Ease of Access
The key is to find a balance between robust security and streamlined access. This involves choosing the right authentication methods and implementing them in a user-friendly way. Multi-factor authentication (MFA), for example, offers a strong security layer without significantly impacting the user experience if implemented correctly. Using a combination of password and a time-based one-time password (TOTP) app, for example, adds an extra layer of security without requiring users to remember multiple passwords or constantly re-enter credentials.
Another strategy is to utilize single sign-on (SSO) if the design room integrates with other company systems. This allows users to access the design room with their existing credentials, reducing friction.
Effective UI/UX Design for Authentication
The user interface should be intuitive and minimize disruptions to the design workflow. Avoid cluttered login screens; keep the design clean and straightforward. Clear instructions, visual cues, and error messages are vital for guiding users through the authentication process. Consider using a visually appealing and branded login page that aligns with the overall design aesthetic of the room.
For instance, a simple, modern login form with clear fields for username/email and password, coupled with a prominent “Forgot Password” link, would be more user-friendly than a complex, multi-step process. If using MFA, provide clear visual indicators of the authentication status (e.g., a green checkmark for successful authentication). Furthermore, consider implementing features such as auto-fill for frequently used credentials to further streamline the process for returning users.
User Authentication Process Flowchart
Imagine a flowchart with the following steps:
- User attempts to access the design room. A box representing the user interacting with the system.
- System prompts for credentials (username/email and password). A box indicating the input fields.
- User enters credentials. A box showing the user typing in their details.
- System verifies credentials against its database. A diamond shape representing a decision point.
- If credentials are valid, proceed to MFA. An arrow leading to the next step.
- System prompts for MFA code (e.g., from a TOTP app). A box showing the MFA prompt.
- User enters MFA code. A box showing the user entering the code.
- System verifies MFA code. A diamond shape representing a decision point.
- If MFA is valid, grant access to the design room. An arrow leading to a box representing access granted.
- If credentials or MFA are invalid, display an error message. An arrow leading to a box displaying an error.
Integration of Authentication with Design Room Software
Integrating robust authentication into existing design room software presents both significant challenges and exciting opportunities. The goal is to seamlessly blend security with the intuitive user experience designers expect, without compromising workflow or creative flow. This requires careful consideration of existing software architecture, the chosen authentication method, and potential points of friction.The process of integrating authentication improvements hinges on understanding the existing software’s architecture and APIs.
Many design tools are built using modular components, allowing for relatively straightforward integration of authentication modules. This could involve adding a new authentication service as a separate layer, communicating with the core design application via well-defined APIs. However, legacy systems may pose greater challenges, requiring more extensive refactoring or even complete overhauls in some extreme cases.
Authentication System Integration Challenges
Integrating different authentication systems with various design tools introduces complexities. For instance, a design room might utilize a combination of tools—a vector graphics editor, a 3D modeling software, and a project management platform—each potentially employing different authentication mechanisms (e.g., OAuth 2.0, SAML, basic username/password). The challenge lies in creating a unified authentication experience across all these tools, ideally using a single set of credentials.
This necessitates a robust authentication gateway or a sophisticated identity provider capable of handling various protocols and federated identities. Inconsistencies in API design and data formats across different tools can further complicate the integration process.
Authentication System Integration Opportunities
Conversely, successful integration unlocks significant opportunities. A unified authentication system enhances security by centralizing user management and access control. This reduces the risk of unauthorized access and data breaches. Furthermore, it simplifies user onboarding, allowing designers to access all the necessary tools with a single login. This streamlined workflow boosts productivity and reduces administrative overhead.
The ability to integrate with existing corporate identity providers (IdPs) allows seamless integration with existing security infrastructure and policies, enhancing overall security posture. Furthermore, robust authentication can pave the way for advanced features such as collaborative design spaces with granular permission controls.
Potential Conflicts and Compatibility Issues, Design room one gets authentication improvements
Several potential conflicts and compatibility issues might emerge during integration. Different authentication systems might have conflicting security protocols or data formats, leading to incompatibility. For example, one tool might rely on JWT (JSON Web Tokens) for authentication, while another uses SAML assertions. This requires careful mapping and translation between different authentication methods. Furthermore, conflicts might arise in user roles and permissions.
A user might have administrator privileges in one tool but only viewer privileges in another. Managing these differing roles and permissions across multiple systems requires a carefully designed authorization system. Finally, differences in API versions and communication protocols can lead to integration failures.
API Integration Approach for Authentication
A possible API integration approach involves using a RESTful API to handle authentication requests. The design room software would act as a client, making requests to an authentication server. For example, a user login request would be sent to the authentication server via a POST request to an endpoint such as `/auth/login`. The server would validate the credentials and, upon successful authentication, return a JWT or a similar security token.
This token would then be used by the design room software for subsequent API calls, allowing the user to access protected resources.
Example API call (using curl):curl -X POST \ -H “Content-Type: application/json” \ -d ‘”username”:”user123″, “password”:”securePassword”‘ \ https://auth-server.example.com/auth/login
The design room software would then include logic to handle the token, either by storing it securely in local storage or using a more robust solution like a secure keystore. Subsequent API calls to access design files or other resources would include the token in the authorization header. This approach allows for a decoupled architecture, making the authentication process independent of the core design functionalities.
It also promotes maintainability and scalability, as the authentication logic can be updated and improved independently of the main design application.
Authentication Method Selection and Implementation
Choosing the right authentication method for your design room is crucial for security and user experience. A poorly implemented system can leave your valuable designs vulnerable, while a cumbersome process will frustrate your team. This section Artikels a step-by-step process for selecting and implementing a robust and user-friendly authentication system.The process of selecting and implementing an authentication method involves careful consideration of several factors, from the complexity of your design room’s data to the technical expertise of your team.
A well-defined procedure will minimize risks and maximize efficiency.
Step-by-Step Procedure for Authentication Method Selection and Implementation
First, assess your design room’s security needs. Consider the sensitivity of the data stored within the system and the potential consequences of a breach. Next, evaluate the available authentication methods, weighing factors such as cost, ease of use, and security level. Then, choose a method that aligns with your needs and resources. Finally, implement the chosen method, thoroughly testing it to ensure functionality and security.
Regularly review and update your authentication system to adapt to evolving threats and technologies.
Best Practices for Securing Authentication Credentials
Strong passwords are fundamental. Encourage users to create complex passwords that combine uppercase and lowercase letters, numbers, and symbols. Password managers can help users generate and securely store strong, unique passwords for various accounts. Multi-factor authentication (MFA) adds an extra layer of security, requiring users to provide multiple forms of verification, such as a password and a one-time code from a mobile app.
Regularly audit user accounts and passwords, looking for suspicious activity and outdated credentials. Implementing strong password policies, including password complexity rules and regular password changes, further enhances security. Finally, regularly update and patch your design room software to address known vulnerabilities that could compromise authentication.
Managing User Accounts and Permissions
Effective user account management is essential for maintaining a secure and organized design room environment. A centralized system for managing user accounts simplifies administration and allows for granular control over permissions. Role-based access control (RBAC) allows you to assign different levels of access based on a user’s role within the design room, ensuring that only authorized personnel can access sensitive data or perform specific actions.
Regularly review user permissions to ensure they are still appropriate and remove access for users who no longer require it. User accounts should be deactivated or deleted promptly when an employee leaves the company. Implementing robust logging and auditing capabilities provides a detailed record of user activity, aiding in security monitoring and incident response.
Factors to Consider When Choosing an Authentication System
Before selecting an authentication system, consider these crucial factors:
- Security Requirements: How sensitive is the data in your design room? Higher sensitivity demands stronger authentication methods.
- User Experience: The authentication process should be easy and intuitive for your users. A frustrating process can lead to users circumventing security measures.
- Cost: Consider the initial investment and ongoing maintenance costs associated with different authentication methods.
- Scalability: Choose a system that can accommodate growth in the number of users and data within your design room.
- Integration: Ensure the chosen authentication system integrates seamlessly with your existing design room software and infrastructure.
- Maintainability: Select a system that is easy to maintain and update, allowing for timely security patches and upgrades.
Illustrative Examples of Enhanced Design Room Security
Improved authentication in design rooms is crucial for protecting sensitive intellectual property and ensuring the integrity of collaborative design projects. This section will explore several scenarios illustrating the impact of both strong and weak authentication methods on design room security.
Unauthorized Access Prevention Scenario
Imagine a scenario where a leading architectural firm uses a design room with weak password requirements. A disgruntled former employee, still possessing an old, easily guessed password, gains unauthorized access. They could potentially steal design plans for a high-profile project, potentially causing significant financial losses and reputational damage to the firm. However, had the firm implemented multi-factor authentication (MFA), requiring a password, a one-time code from a mobile app, and potentially biometric verification, this unauthorized access would have been highly unlikely.
The added layers of security would have effectively blocked the former employee, even with their old password.
Consequences of Weak Authentication
Conversely, consider a smaller design studio relying solely on a single password for access to its design room. A phishing attack, cleverly disguised as an email from a trusted client, tricks one of the designers into revealing their password. The attacker gains full access to the studio’s design files, client information, and financial records. The consequences are severe: loss of intellectual property, potential legal liabilities from data breaches, and the considerable cost of recovering from the attack.
This scenario highlights the critical need for strong authentication and security awareness training.
Successful Implementation of Strong Authentication: A Case Study
A hypothetical case study focuses on a game development studio that implemented a robust authentication system incorporating MFA, password complexity requirements, and regular security audits. This proactive approach prevented several attempted breaches. The studio reported a significant reduction in security incidents, leading to increased trust among clients, improved employee morale, and a stronger competitive edge. The cost of implementing these security measures was significantly outweighed by the savings resulting from avoided data breaches and the maintenance of their valuable intellectual property.
Visual Representation of Enhanced Design Room Security Layers
Imagine a layered security diagram. The innermost layer represents the design room’s core data and files. The next layer depicts the strong password and MFA systems, acting as the first line of defense. The third layer showcases regular security audits and vulnerability assessments, ensuring the system remains up-to-date and secure. The outermost layer represents the physical security measures, such as access control to the server room and network security protocols.
This multi-layered approach provides robust protection against a wide range of threats.
Concluding Remarks
Ultimately, improving authentication in our design rooms isn’t just about adding extra layers of security; it’s about creating a more efficient and enjoyable creative process. By carefully selecting and implementing the right authentication methods, we can strike a perfect balance between robust protection and effortless access. This means more time creating and less time worrying about security breaches – a win-win for every designer! Let’s embrace these advancements and build a safer, more productive design future.
FAQ Insights: Design Room One Gets Authentication Improvements
What are the potential costs associated with implementing different authentication methods?
Costs vary widely depending on the method chosen. Simple password systems are cheap, while biometric authentication can be more expensive due to hardware and software requirements.
How do I choose the right authentication method for my design room?
Consider your budget, the sensitivity of your data, and the technical expertise of your team. Balance security needs with user-friendliness.
What happens if I forget my authentication credentials?
Implement a robust password recovery system, perhaps involving email verification or security questions, to allow users to regain access without compromising security.
Are there any legal implications I should consider when implementing new authentication methods?
Yes, be sure to comply with relevant data privacy regulations (like GDPR or CCPA) when collecting and storing user authentication data.