Pentagons Zero Trust Office Details Inside
Details about pentagons zero trust office – Details about Pentagon’s zero trust office are finally coming to light, and it’s a fascinating peek into the future of cybersecurity. Forget the old perimeter-based security; we’re talking a completely different approach, one built on the principle of “never trust, always verify.” This means every user, every device, and every connection is constantly scrutinized, regardless of location. It’s a complex system, involving multiple layers of security and advanced technologies, but the goal is simple: to protect some of the most sensitive information in the world.
This post dives deep into the specifics of this groundbreaking initiative.
We’ll explore the core principles of the Pentagon’s Zero Trust architecture, examining the technologies employed and comparing it to traditional security methods. We’ll delve into data security and access control, network security infrastructure, and user/device management, highlighting the crucial role of risk management and compliance. Think of it as a behind-the-scenes look at how the Pentagon is safeguarding its digital assets in the face of ever-evolving cyber threats.
Pentagon’s Zero Trust Architecture
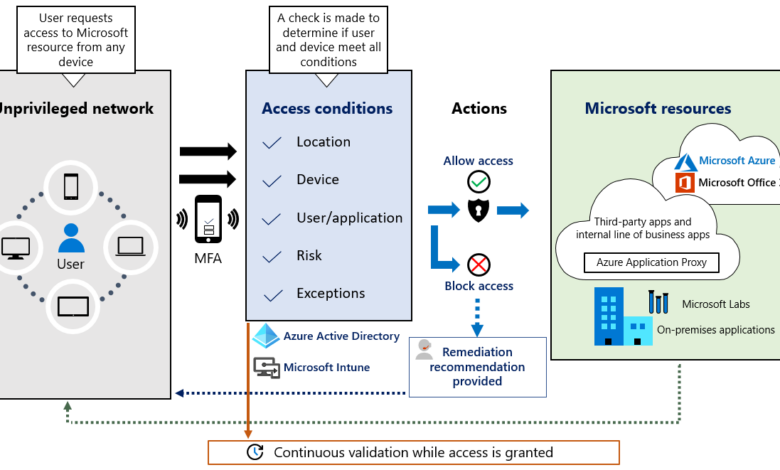
The Pentagon’s adoption of a Zero Trust security framework represents a significant shift in how the Department of Defense approaches cybersecurity. Moving away from traditional perimeter-based security, the Zero Trust model assumes no implicit trust and verifies every user and device before granting access to resources, regardless of location. This approach is crucial in mitigating the ever-increasing threat landscape faced by the DoD.
Core Principles of the Pentagon’s Zero Trust Framework
The Pentagon’s Zero Trust architecture is built upon several core principles. These include least privilege access, continuous authentication and authorization, micro-segmentation of networks, and robust data loss prevention (DLP) measures. The emphasis is on verifying identity and authorization at every access point, ensuring that only authorized users and devices can access specific resources and data. This granular control minimizes the impact of potential breaches, limiting the lateral movement of attackers within the network.
Technological Components of the Pentagon’s Zero Trust Implementation
Implementing Zero Trust within the vast and complex Pentagon network requires a sophisticated suite of technologies. These include multi-factor authentication (MFA) for all users and devices, robust identity and access management (IAM) systems, secure access service edge (SASE) solutions to secure remote access, and advanced endpoint detection and response (EDR) capabilities. Network segmentation using virtual local area networks (VLANs) and software-defined networking (SDN) is also critical in isolating sensitive data and applications.
Data encryption, both in transit and at rest, is another fundamental component of the Pentagon’s Zero Trust implementation.
Differences from Traditional Network Security Approaches
The Pentagon’s Zero Trust model significantly differs from traditional network security, which relies on a castle-and-moat approach. Traditional security focuses on securing the perimeter network, assuming that anything inside the perimeter is trusted. Zero Trust, in contrast, assumes no implicit trust, regardless of location (inside or outside the network). Every user, device, and application is continuously verified before access is granted, even within the internal network.
This proactive approach significantly reduces the attack surface and limits the damage from successful breaches.
Comparison with Zero Trust Initiatives in Other Government Agencies
While many government agencies are adopting Zero Trust principles, the Pentagon’s implementation is likely one of the most comprehensive and complex due to the scale and sensitivity of the data it handles. While other agencies might focus on specific aspects of Zero Trust, such as MFA or network segmentation, the Pentagon’s approach integrates these elements into a holistic, multi-layered security architecture.
The specifics of implementation vary based on agency needs and resources, but the underlying principle of “never trust, always verify” remains consistent across all initiatives.
Layers of Security in the Pentagon’s Zero Trust Architecture
| Layer | Description | Technologies | Purpose |
|---|---|---|---|
| Identity and Access Management (IAM) | Centralized management of user identities and access privileges. | MFA, SSO, RBAC | Verifies user identity and controls access to resources. |
| Network Segmentation | Dividing the network into smaller, isolated segments. | VLANs, SDN, micro-segmentation | Limits the impact of breaches and prevents lateral movement. |
| Endpoint Security | Protecting endpoints (computers, mobile devices) from threats. | EDR, antivirus, endpoint DLP | Ensures endpoint devices are secure and prevents data exfiltration. |
| Data Security | Protecting data in transit and at rest. | Encryption, data loss prevention (DLP), data masking | Ensures data confidentiality and integrity. |
Data Security and Access Control: Details About Pentagons Zero Trust Office

The Pentagon’s Zero Trust architecture necessitates robust data security and access control mechanisms to protect highly sensitive information. This goes beyond traditional perimeter security, focusing instead on verifying every access request regardless of location. The system employs a multi-layered approach, combining strong authentication, granular authorization, and advanced encryption techniques to ensure only authorized individuals can access specific data.
User Identity Verification and Access Privileges
The Pentagon’s system uses multi-factor authentication (MFA) as a cornerstone of its access control. This typically involves a combination of something the user knows (password), something the user has (smart card or token), and something the user is (biometrics). Once identity is verified, access privileges are granted based on a least privilege model. This means users are only given access to the specific data and systems necessary for their job functions.
Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) are likely employed to dynamically manage and adjust these privileges as roles and responsibilities change. Regular audits ensure that access remains appropriate and that no unnecessary privileges exist.
Data Encryption
Data encryption is paramount in the Pentagon’s Zero Trust model. Data in transit is protected using robust encryption protocols like TLS/SSL, ensuring that information exchanged between systems and users remains confidential. Data at rest, meaning data stored on servers and storage devices, is also encrypted using strong encryption algorithms like AES-256, making it unreadable even if the storage media is compromised.
Key management is a critical aspect, with strict protocols in place for generating, storing, and rotating encryption keys.
Preventing Data Breaches and Insider Threats, Details about pentagons zero trust office
The Pentagon’s Zero Trust architecture incorporates several strategies to mitigate data breaches and insider threats. Continuous monitoring and threat detection systems actively scan for suspicious activity, such as unauthorized access attempts or data exfiltration. Data loss prevention (DLP) tools monitor data movement to prevent sensitive information from leaving the network without authorization. Regular security awareness training for personnel helps to educate employees about potential threats and best practices for data security.
Furthermore, strict access controls, including mandatory vacations and separation of duties, minimize the risk posed by malicious or negligent insiders.
Data Security Best Practices within a Zero Trust Framework
Implementing the following best practices is crucial for maintaining a strong security posture within a Zero Trust environment:
- Implement strong authentication and authorization mechanisms: Utilize MFA and least privilege access models.
- Encrypt all data, both in transit and at rest: Employ strong encryption algorithms and robust key management practices.
- Regularly monitor and audit access logs: Identify and respond to suspicious activity promptly.
- Employ data loss prevention (DLP) tools: Prevent unauthorized data exfiltration.
- Conduct regular security awareness training: Educate personnel on security threats and best practices.
- Implement robust security information and event management (SIEM) systems: Correlate security events and identify threats.
- Regularly patch and update systems: Address vulnerabilities promptly to prevent exploitation.
- Employ robust intrusion detection and prevention systems: Detect and mitigate cyberattacks.
- Implement a comprehensive incident response plan: Prepare for and respond effectively to security incidents.
Network Security and Infrastructure
The Pentagon’s Zero Trust architecture extends far beyond user authentication and data protection; it fundamentally reshapes the network infrastructure itself. A robust and highly segmented network is crucial for mitigating the risks inherent in a large, complex organization handling sensitive national security information. This section delves into the intricate network security measures employed to achieve this level of protection.
Network Segmentation Techniques
The Pentagon’s network is meticulously segmented to isolate sensitive systems and data. This isn’t a simple division into a few broad segments; it involves a layered approach, creating numerous smaller, isolated networks. Each segment contains only the necessary systems and data, limiting the potential impact of a breach. Sophisticated firewalls and access control lists (ACLs) regulate traffic flow between segments, preventing unauthorized access.
This approach significantly reduces the attack surface and limits the lateral movement of potential threats within the network. For instance, a compromised system in one segment would have severely limited ability to access systems in another, more sensitive, segment. This granular control is paramount in protecting highly classified information.
The Role of Micro-segmentation
Micro-segmentation takes network segmentation to an even more granular level. Instead of segmenting at the network level, micro-segmentation isolates individual servers, applications, and even virtual machines. This fine-grained control allows for highly tailored security policies, further limiting the blast radius of a potential security incident. For example, a database server holding top-secret intelligence might be isolated not only from other segments but also from other servers within its own segment, further minimizing the risk of compromise.
This technique is crucial for mitigating the threats posed by advanced persistent threats (APTs) which often attempt to move laterally within a network.
Protection Against External Threats
Protecting against external threats like malware and phishing attacks requires a multi-layered defense. This includes robust intrusion detection and prevention systems (IDPS), regularly updated antivirus software, and rigorous employee security awareness training. Advanced email filtering techniques are used to identify and block phishing emails before they reach users’ inboxes. Sandboxing technologies are employed to analyze suspicious files and attachments in a controlled environment before they can execute on the network.
Regular security audits and vulnerability scans are conducted to identify and remediate weaknesses in the network infrastructure. The Pentagon likely utilizes advanced threat intelligence feeds to stay ahead of emerging threats and proactively mitigate potential vulnerabilities.
Advanced Threat Detection and Response Technologies
The Pentagon undoubtedly leverages advanced threat detection and response technologies, including security information and event management (SIEM) systems, to monitor network traffic for suspicious activity. These systems analyze vast amounts of data to identify anomalies and potential threats in real-time. Furthermore, technologies such as endpoint detection and response (EDR) provide visibility into the behavior of individual endpoints (computers, servers, and mobile devices) to detect and respond to malware infections.
Automated incident response systems are likely in place to automatically contain and remediate threats, minimizing the impact of successful attacks. This proactive approach to threat detection and response is crucial for maintaining the security of the Pentagon’s network.
Pentagon’s Zero Trust Network Infrastructure Diagram
Imagine a network depicted as a series of concentric circles. The innermost circle represents the most sensitive systems and data, perhaps containing classified intelligence databases and mission-critical applications. This core is heavily fortified with multiple layers of security, including advanced firewalls, intrusion detection systems, and strict access control. Each subsequent circle represents a less sensitive segment, with progressively fewer security controls.
The outermost circle represents the public internet, with a strong perimeter defense including firewalls, web application firewalls (WAFs), and DDoS mitigation systems. Between each concentric circle are multiple layers of micro-segmentation, creating thousands of isolated networks. Each system and application within these segments only has access to the resources absolutely necessary for its function. Connections between segments are tightly controlled and monitored, with all traffic subject to strict inspection and authorization.
This layered approach, combined with advanced threat detection and response capabilities, forms the foundation of the Pentagon’s Zero Trust network infrastructure.
User and Device Management
The Pentagon’s Zero Trust architecture necessitates a robust and highly secure system for managing users and devices. This goes beyond simple access controls; it involves continuous monitoring, rigorous authentication, and immediate responses to potential threats. The goal is to ensure only authorized individuals and devices with validated security postures can access sensitive information and systems.
Implementing Zero Trust requires a multifaceted approach to user and device management, encompassing stringent onboarding and offboarding processes, granular access control, and proactive security measures. This strategy minimizes the attack surface and limits the impact of potential breaches.
User Onboarding and Offboarding
The process of onboarding a new user begins with a comprehensive background check and security awareness training. Following this, a unique, strong password and multi-factor authentication (MFA) are mandatory. Device enrollment is strictly controlled, requiring compliance with pre-defined security profiles. Offboarding involves immediate revocation of access credentials, disabling accounts, and wiping all Pentagon-related data from the user’s devices.
This procedure adheres to strict timeframes to minimize any potential security risks.
User Access Rights and Privileges
Access rights are granted based on the principle of least privilege. This means users are only given the minimum access required to perform their job duties. Access is regularly reviewed and adjusted based on role changes or security assessments. The system utilizes role-based access control (RBAC) to streamline management and enforce consistent security policies across all users.
- Regular audits of user access rights are conducted to identify and rectify any inconsistencies or excessive permissions.
- Automated systems monitor user activity for suspicious patterns, immediately flagging any potential breaches.
- A comprehensive access request and approval process is in place, ensuring all access requests are vetted before being granted.
Device Security Policies and Compliance
All devices accessing Pentagon systems must meet stringent security requirements. This includes mandatory encryption, up-to-date anti-malware software, and regular security patching. Devices are continuously monitored for compliance, and non-compliant devices are blocked from accessing sensitive resources. Regular security assessments are conducted to identify and address any vulnerabilities.
- Mobile Device Management (MDM) solutions enforce security policies on mobile devices, including password complexity, remote wipe capabilities, and data encryption.
- Endpoint Detection and Response (EDR) systems monitor device activity for malicious behavior and provide real-time alerts.
- Regular vulnerability scans identify and address security weaknesses in both hardware and software.
Mobile Device and Remote Access Management
Mobile device access is carefully controlled through the use of MDM solutions and VPNs. All mobile devices must be enrolled in the MDM system, allowing for remote management and enforcement of security policies. VPNs encrypt all communications, ensuring data security even when accessing Pentagon systems remotely. Access is granted only after successful authentication and verification of device compliance.
Protection Against Compromised Devices and Accounts
The Pentagon employs a layered security approach to mitigate the risk of compromised devices and accounts. This includes multi-factor authentication, intrusion detection systems, and regular security awareness training. Suspicious activity triggers immediate alerts and investigations, leading to prompt remediation actions.
- Intrusion detection systems continuously monitor network traffic for malicious activity, providing real-time alerts and blocking suspicious connections.
- Security Information and Event Management (SIEM) systems collect and analyze security logs from various sources, providing a comprehensive view of security events and enabling faster incident response.
- Regular security awareness training educates users on best practices for protecting their accounts and devices, reducing the risk of phishing attacks and other social engineering tactics.
Risk Management and Compliance
Implementing a Zero Trust architecture within the Pentagon, a high-security environment handling sensitive national security information, presents unique and significant challenges. A robust risk management and compliance strategy is paramount to ensure the successful and secure deployment of this complex system. The potential for breaches, both internal and external, necessitates a proactive and multi-layered approach to mitigating risks and maintaining regulatory compliance.
Key Security Risks Associated with Zero Trust Implementation
The Pentagon’s Zero Trust initiative faces several key security risks. These include insider threats, where authorized personnel may unintentionally or maliciously compromise data; sophisticated external attacks targeting vulnerabilities in the system’s numerous interconnected components; data breaches resulting from compromised credentials or exploited software vulnerabilities; and the complexity of managing and monitoring a vast, distributed network under a Zero Trust model.
Furthermore, the sheer scale of the Pentagon’s operations and the diversity of its systems increase the attack surface and the difficulty of maintaining consistent security posture. The potential for human error, particularly in configuration and access management, also presents a substantial risk. Finally, maintaining the integrity and confidentiality of data in transit and at rest across a distributed environment requires robust encryption and data loss prevention (DLP) mechanisms.
Mitigation Strategies and Ensuring Framework Effectiveness
To mitigate these risks, the Pentagon employs a multi-pronged strategy. This includes robust security awareness training for all personnel, focusing on phishing, social engineering, and safe data handling practices. Regular security audits and penetration testing are conducted to identify and address vulnerabilities before they can be exploited. Multi-factor authentication (MFA) is mandated for all access points, reducing the likelihood of unauthorized access.
Data encryption, both in transit and at rest, is implemented using strong cryptographic algorithms. A comprehensive system of logging and monitoring tracks all network activity, enabling the rapid detection and response to security incidents. Furthermore, continuous monitoring and adaptation of the Zero Trust framework are crucial; the security landscape is constantly evolving, and the system must adapt to emerging threats and vulnerabilities.
The Pentagon likely uses advanced threat detection systems such as Security Information and Event Management (SIEM) solutions and intrusion detection/prevention systems (IDS/IPS). Finally, rigorous access control policies based on the principle of least privilege are enforced, limiting user access to only the resources necessary for their job function.
So, the Pentagon’s zero trust office is all about granular control, right? It’s fascinating to see how they’re managing such a massive, complex system. This need for tight security highlights the importance of robust cloud security solutions, and that’s where the rise of platforms like Bitglass comes into play; check out this great article on bitglass and the rise of cloud security posture management to understand the impact better.
Ultimately, these advanced security measures are crucial for protecting sensitive data, something vital for an organization like the Pentagon’s zero trust office.
Compliance Requirements and Alignment with Security Standards
The Pentagon’s Zero Trust initiative must adhere to a multitude of compliance requirements, including those mandated by federal regulations such as NIST Cybersecurity Framework, FISMA (Federal Information Security Management Act), and DoD instructions concerning information security. The framework’s design aligns with these standards through the implementation of strong authentication, authorization, and access control mechanisms. Continuous monitoring and logging capabilities enable compliance auditing and incident response.
Securing the Pentagon’s zero trust office requires robust, adaptable systems. Think about the complexities involved – managing access, data encryption, and constant threat monitoring. Building these solutions efficiently often hinges on modern development approaches, like those explored in this insightful article on domino app dev the low code and pro code future , which could inform better security architecture for sensitive government environments like the Pentagon’s.
Ultimately, the Pentagon’s zero trust initiative needs streamlined development to stay ahead of evolving threats.
The Pentagon’s adherence to these standards is regularly audited by both internal and external security teams to ensure ongoing compliance and effectiveness. This rigorous approach to compliance ensures that the Pentagon’s data and systems are protected to the highest standards, meeting both legal and operational requirements.
Key Performance Indicators (KPIs) for Zero Trust Implementation Success
The success of the Pentagon’s Zero Trust implementation is measured through several key performance indicators (KPIs). These KPIs provide quantifiable metrics to assess the effectiveness of the framework and identify areas for improvement.
| KPI | Metric | Target | Measurement Method |
|---|---|---|---|
| Mean Time To Detect (MTTD) | Average time to detect a security incident | < 24 hours | Security Information and Event Management (SIEM) system logs |
| Mean Time To Respond (MTTR) | Average time to respond to a security incident | < 4 hours | Incident response system logs and ticketing system |
| Number of successful breaches | Number of successful security breaches | 0 | Security incident reports and audits |
| Percentage of users with MFA enabled | Percentage of users utilizing multi-factor authentication | 100% | User authentication logs |
Closing Summary
The Pentagon’s Zero Trust implementation represents a significant leap forward in cybersecurity. By shifting from a perimeter-based model to a “never trust, always verify” approach, they’re significantly enhancing their security posture. While the specifics of their implementation remain somewhat classified, the key takeaways are clear: a multi-layered security approach, robust access control, and a strong focus on continuous monitoring are essential.
The challenges are immense, but the potential benefits—in terms of data protection and national security—are even greater. This is a model that other organizations, both public and private, would do well to study and adapt.
General Inquiries
What are the biggest challenges in implementing a Zero Trust architecture like the Pentagon’s?
The biggest challenges include the complexity of implementation, the need for significant infrastructure upgrades, the potential for disruption during the transition, and the ongoing need for skilled personnel to manage and maintain the system. Cost is also a significant factor.
How does the Pentagon’s Zero Trust approach handle remote workers?
Likely through strong multi-factor authentication, VPNs with strict access controls, and regular security updates and patches on all devices. Continuous monitoring of user activity and device integrity is also crucial.
What role does AI play in the Pentagon’s Zero Trust security?
AI likely plays a significant role in threat detection and response, analyzing vast amounts of data to identify anomalies and potential breaches in real-time. It can also automate tasks such as user authentication and access control.





