
DHS Issues Cyber Threat Alert Iran Suspected
DHS issues cyber threat alert for US government websites and suspects Iran. This alarming news highlights a significant escalation in cyber warfare, raising concerns about the vulnerability of critical government infrastructure and the potential for widespread disruption. The alert details a sophisticated attack, potentially leveraging previously unknown vulnerabilities, targeting a range of government websites. Understanding the scale of this threat, Iran’s known cyber capabilities, and the government’s response is crucial to mitigating future risks and ensuring the security of our digital landscape.
The Department of Homeland Security’s (DHS) alert focuses on the suspected involvement of Iranian state-sponsored actors in a series of cyberattacks targeting US government websites. The specifics of the vulnerabilities exploited remain under wraps for security reasons, but the potential impact is far-reaching. From data breaches to service disruptions, the consequences could be devastating. This incident underscores the ongoing need for robust cybersecurity measures and international cooperation to combat these increasingly sophisticated threats.
DHS Alert Overview
The Department of Homeland Security (DHS) recently issued a cyber threat alert warning of malicious cyber activity targeting US government websites, with strong indications pointing towards Iranian state-sponsored actors. This alert highlights a significant escalation in the ongoing cyber conflict between the US and Iran, underscoring the persistent threat posed by sophisticated state-sponsored attacks against critical infrastructure and government systems.
The alert urged immediate action from federal agencies to bolster their defenses and mitigate potential damage.The alert detailed a sophisticated campaign leveraging multiple vulnerabilities, exploiting known weaknesses and likely zero-day exploits. While specific vulnerabilities weren’t publicly disclosed in their entirety to prevent further exploitation, the alert highlighted techniques such as spear-phishing emails containing malicious attachments, exploitation of known software vulnerabilities in widely used applications, and the potential use of advanced persistent threats (APTs) to maintain long-term access to compromised systems.
The attackers aimed to gain unauthorized access to sensitive data, disrupt government operations, and potentially conduct espionage.
Vulnerabilities Exploited
The DHS alert, while not specifying every vulnerability, emphasized the multifaceted nature of the attack. The attackers likely employed a combination of known vulnerabilities in widely used software applications, such as outdated versions of operating systems and applications lacking security patches. They also likely utilized zero-day exploits – vulnerabilities unknown to the public and software vendors – providing them with an initial foothold in the targeted systems.
This combination of known and unknown vulnerabilities underscores the challenge of maintaining robust cybersecurity defenses against sophisticated adversaries. The use of spear-phishing emails, tailored to specific individuals within target organizations, demonstrated the attackers’ ability to leverage social engineering techniques to bypass technical security controls.
Timeline of Events
Precise details regarding the timeline are limited due to national security concerns. However, the alert suggests that the initial discovery of the malicious activity likely occurred through a combination of internal monitoring, threat intelligence sharing, and incident response efforts by various federal agencies. The identification and assessment of the threat likely took place over several days or weeks, allowing for investigation and analysis of the attack techniques and the extent of the compromise.
Following the internal assessment, the decision was made to issue a public alert to warn other government entities and the private sector of the ongoing threat and to encourage proactive mitigation measures. The public release of the alert followed the completion of this internal process and the coordination of messaging among relevant government agencies.
Iranian Cyber Capabilities
Iran’s state-sponsored cyber actors possess a range of sophisticated capabilities, posing a significant threat to US government websites and other critical infrastructure. Their operations are often characterized by a blend of advanced persistent threats (APTs), disruptive attacks, and information warfare campaigns. Understanding the nature and extent of these capabilities is crucial for effective cybersecurity defense.Iran’s cyberattacks against US targets have historically involved a variety of techniques and objectives.
These range from data breaches aimed at stealing sensitive information to disruptive attacks designed to cripple essential services. The sophistication and scale of these operations have increased over time, reflecting the growth of Iran’s cyber capabilities and its willingness to employ them against perceived adversaries.
Types of Cyberattacks Conducted by Iran
Iranian cyber operations against the US and its allies have demonstrated a diverse toolkit. These attacks frequently involve the exploitation of vulnerabilities in software and hardware, often coupled with social engineering techniques to gain initial access to systems. Data breaches, aimed at acquiring intellectual property, military secrets, and personal information, are a common tactic. Disruptive attacks, including denial-of-service (DoS) assaults and the infiltration of critical infrastructure systems, are also employed to cause widespread disruption and damage.
Furthermore, Iran has engaged in extensive information operations, spreading disinformation and propaganda through online platforms to influence public opinion and sow discord. Examples include the widespread dissemination of false narratives surrounding political events and the targeting of media outlets.
Comparison with Previous Iranian Cyber Operations
While the specifics of each incident vary, this recent DHS alert echoes patterns observed in previous Iranian cyber operations against US targets. Past attacks have often involved the use of custom-built malware and advanced persistent threats (APTs) to maintain long-term access to compromised systems. Similar to previous incidents, this attack likely involved a multi-stage intrusion, beginning with initial reconnaissance and exploitation of vulnerabilities, followed by lateral movement within the targeted network to achieve the attackers’ objectives.
The scale and sophistication of the attack, while still under investigation, suggest a level of planning and resources consistent with previous state-sponsored Iranian operations. The targeting of US government websites further reinforces the strategic nature of these attacks, indicating a clear intention to undermine US interests and capabilities. Past examples include attacks on the US banking system and attacks against Saudi Aramco, demonstrating Iran’s capacity for both large-scale disruption and targeted espionage.
Impact on US Government Websites
The potential impact of Iranian cyberattacks on US government websites is a serious concern, extending beyond simple website defacement. The consequences could be far-reaching, affecting critical government services and the security of sensitive citizen data. Understanding the potential targets and the resulting disruption is crucial for effective mitigation strategies.The types of websites targeted would likely vary based on the attackers’ goals.
High-value targets include those holding sensitive national security information, financial data, or citizen personal information. Websites related to defense, intelligence, diplomacy, and social security are prime candidates for sophisticated attacks. Less prominent but equally impactful targets could include state and local government websites responsible for crucial services like elections, healthcare, or infrastructure management. The potential for cascading effects across interconnected systems makes even seemingly minor targets significant vulnerabilities.
Consequences of a Successful Cyberattack
A successful attack could lead to several devastating consequences. Data breaches could expose sensitive personal information of millions of citizens, leading to identity theft, financial fraud, and reputational damage for the government. Disruption of government services, such as the inability to file taxes, access healthcare benefits, or receive social security payments, would cause widespread public inconvenience and economic hardship.
The compromise of national security information could have severe geopolitical implications, potentially impacting national defense and international relations. Furthermore, the loss of public trust in government institutions resulting from such attacks could be long-lasting and difficult to repair.
The DHS alert about Iranian cyberattacks targeting US government websites is a serious wake-up call. This highlights the critical need for robust security measures, especially as more government services move to the cloud. Understanding how to effectively manage this risk is crucial, and that’s where solutions like those discussed in this article on bitglass and the rise of cloud security posture management become invaluable.
Ultimately, strengthening our cloud security posture is vital to defending against these kinds of sophisticated threats.
Hypothetical Scenario: Disruption of Election-Related Services
Imagine a scenario where a sophisticated Iranian cyberattack targets state and local election websites during a critical election cycle. The attackers successfully infiltrate the systems, altering voter registration databases, disseminating misinformation through compromised websites, or even disrupting online voting systems. The immediate consequence would be widespread confusion and distrust in the election process. The integrity of the election results could be called into question, leading to potential social unrest and political instability.
Furthermore, the long-term impact on public trust in democratic institutions could be significant, undermining the legitimacy of future elections. The investigation and remediation efforts would be costly and time-consuming, diverting resources from other essential government functions. This scenario highlights the critical need for robust cybersecurity measures to protect election infrastructure and ensure the integrity of the democratic process.
The scale of such an event, even with partial success, could easily eclipse the impact of previous election interference attempts.
Government Response and Mitigation
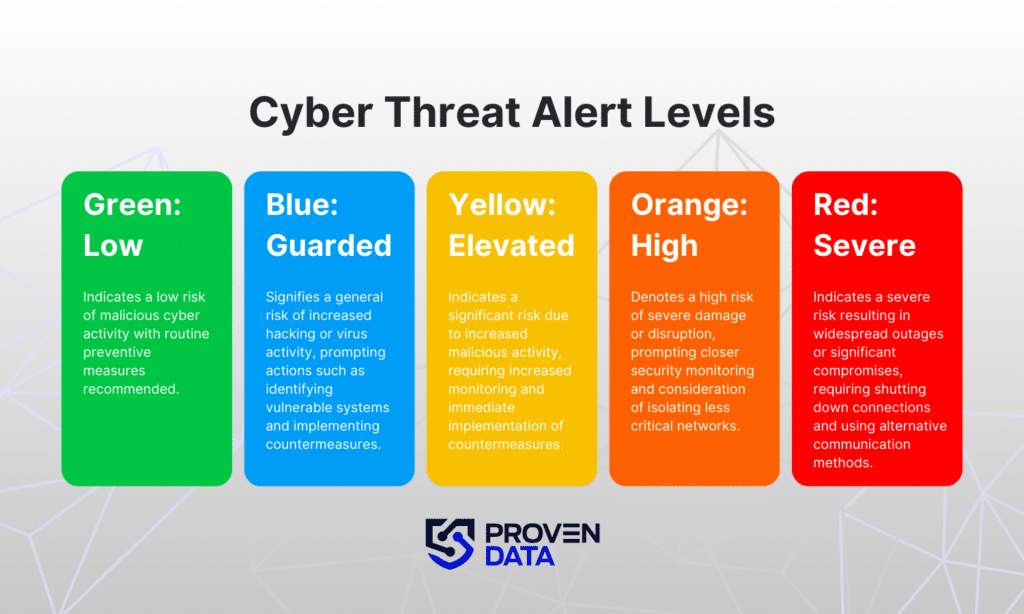
The US government’s response to the suspected Iranian cyberattacks on government websites has been multifaceted, involving immediate defensive actions, long-term strategic adjustments, and increased international cooperation. The gravity of the situation necessitates a robust and adaptable approach, encompassing both short-term damage control and long-term improvements to national cybersecurity infrastructure.The effectiveness of existing cybersecurity measures in protecting government websites is a complex issue.
While significant investments have been made in network security, firewalls, and intrusion detection systems, the sophistication of modern cyberattacks often outpaces these defenses. The recent incidents highlight vulnerabilities that require immediate attention and systemic improvements. The challenge lies not only in technological advancements but also in addressing human factors, such as phishing scams and insider threats, which often serve as entry points for malicious actors.
Government Actions to Mitigate the Threat, Dhs issues cyber threat alert for us government websites and suspects iran
The government’s response has included immediate steps to contain the damage from the attacks, such as isolating affected systems to prevent further spread of malware. Simultaneously, investigations are underway to identify the full extent of the breach and attribute responsibility. This involves close collaboration between various agencies, including the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA).
Beyond immediate response, the government is focusing on enhancing its cybersecurity capabilities through increased funding for research and development, improved employee training programs to enhance awareness of phishing and social engineering techniques, and the strengthening of existing security protocols across all government agencies. Furthermore, international partnerships are being leveraged to share threat intelligence and coordinate responses to similar attacks in the future.
For example, information sharing agreements with allies such as the UK and Israel have proven invaluable in identifying and mitigating threats.
Effectiveness of Current Cybersecurity Measures
Current cybersecurity measures, while significant, have proven insufficient to completely prevent sophisticated attacks like those attributed to Iran. The attacks highlight the limitations of relying solely on technological solutions. Many breaches exploit human error, such as employees clicking on malicious links in phishing emails. This underscores the need for comprehensive training programs and a cultural shift towards cybersecurity awareness within government agencies.
Additionally, the rapid evolution of cyberattack techniques necessitates continuous investment in research and development to stay ahead of emerging threats. Regular security audits and penetration testing are crucial to identify vulnerabilities before malicious actors can exploit them. The effectiveness of current measures is therefore best described as a work in progress, constantly adapting to the evolving landscape of cyber warfare.
Recommended Best Practices for Improving Cybersecurity Defenses
Strengthening cybersecurity defenses requires a multi-pronged approach. The following best practices are crucial for improving protection against similar attacks:
- Implement multi-factor authentication (MFA) across all government systems. MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even if they obtain usernames and passwords.
- Conduct regular security awareness training for all employees, focusing on phishing scams, social engineering techniques, and safe browsing practices. Regular training is vital to keep employees up-to-date on the latest threats and best practices.
- Invest in advanced threat detection and response systems, including intrusion detection and prevention systems (IDPS), security information and event management (SIEM) tools, and threat intelligence platforms. These systems can help identify and respond to attacks in real-time.
- Regularly patch and update software and systems to address known vulnerabilities. Prompt patching prevents attackers from exploiting known weaknesses.
- Implement robust data loss prevention (DLP) measures to protect sensitive government data. DLP measures help prevent sensitive information from leaving the network without authorization.
- Strengthen network segmentation to limit the impact of successful breaches. Segmenting the network restricts the lateral movement of attackers within the system.
- Develop and maintain comprehensive incident response plans to effectively manage and mitigate the impact of cyberattacks. A well-defined plan ensures a coordinated and efficient response in the event of an attack.
- Enhance collaboration and information sharing with other government agencies, private sector partners, and international allies. Collaboration is crucial for sharing threat intelligence and coordinating responses to large-scale attacks.
International Implications
The alleged Iranian cyberattack on US government websites carries significant geopolitical implications, extending far beyond the immediate technical damage. It highlights the growing sophistication and boldness of state-sponsored cyber warfare, potentially destabilizing international relations and prompting a reassessment of national cybersecurity strategies worldwide. The incident also underscores the challenges in attributing cyberattacks definitively and the difficulties in responding effectively without escalating tensions.The potential for escalation is a major concern.
A tit-for-tat response by the US could trigger a cycle of retaliatory cyberattacks, potentially expanding the conflict to other sectors or even involving kinetic military action. The lack of clear international norms and mechanisms for addressing state-sponsored cyberattacks exacerbates this risk. A miscalculation or an overreaction could have far-reaching consequences, affecting not only the US and Iran but also other nations caught in the crossfire.
Moreover, other nations might feel emboldened to engage in similar actions, leading to a more unstable and dangerous international environment.
International Responses to Similar Cyber Incidents
The international community has responded to state-sponsored cyberattacks in varying ways, reflecting differing national interests and capabilities. Some nations have opted for diplomatic solutions, while others have employed more assertive measures, including sanctions or counter-cyber operations. The effectiveness of these responses has been mixed, often depending on the specific circumstances of the incident and the willingness of involved nations to cooperate.
The timeline of response also varies significantly.
| Country | Response Type | Effectiveness | Timeline |
|---|---|---|---|
| United States | Sanctions, indictments, counter-cyber operations (alleged) | Varied; sanctions have had limited impact in some cases, while counter-cyber operations are often clandestine and their effectiveness difficult to assess. | Responses typically occur within weeks to months of an incident, but long-term consequences can take years to manifest. |
| United Kingdom | Diplomatic pressure, sanctions, law enforcement investigations | Effectiveness depends on the level of cooperation from the targeted nation and the nature of the attack. | Similar to the US, with a focus on swift diplomatic response and long-term legal action. |
| Israel | Alleged preemptive and retaliatory cyber operations, intelligence gathering | Difficult to assess publicly due to the clandestine nature of cyber warfare. | Responses often occur quickly, sometimes within days of an incident. |
| Russia | Denial, deflection, and potential counter-cyber operations | Often ineffective in deterring future attacks. | Responses are often delayed and focused on minimizing domestic repercussions. |
Future Cyber Threats

The recent wave of cyberattacks targeting US government websites, attributed to Iranian state-sponsored actors, serves as a stark reminder of the evolving and increasingly sophisticated nature of modern cyber warfare. This incident highlights critical vulnerabilities within the US cybersecurity infrastructure and foreshadows a future where such attacks become more frequent, intense, and devastating. The sophistication of these attacks, employing advanced techniques to evade detection and inflict maximum damage, underscores the need for a proactive and comprehensive approach to national cybersecurity.The Iranian cyber campaign, while significant, is only a glimpse into the potential future of state-sponsored cyberattacks.
The increasing accessibility of advanced cyber tools and techniques, coupled with the growing geopolitical tensions, creates a fertile ground for escalating cyber conflict. This incident demonstrates that even well-defended systems are susceptible to determined and well-resourced adversaries. The speed and scale of the attacks, along with the apparent ease with which sensitive information was potentially compromised, underscores the urgent need for significant improvements in both defensive and offensive cybersecurity capabilities.
Advanced Persistent Threats (APTs) and Evolving Tactics
The Iranian attack likely involved a sophisticated Advanced Persistent Threat (APT) campaign. APTs are characterized by their stealth, persistence, and ability to remain undetected within a system for extended periods, gathering intelligence and preparing for a larger-scale attack. Future threats will likely involve more sophisticated APTs, utilizing techniques like polymorphic malware (which changes its code to evade detection), zero-day exploits (exploiting previously unknown software vulnerabilities), and AI-powered tools to automate attacks and make them harder to trace.
For example, the NotPetya ransomware attack in 2017, though not directly attributed to Iran, demonstrated the devastating potential of a large-scale, sophisticated cyberattack that crippled global infrastructure. Future attacks could similarly target critical infrastructure like power grids, financial institutions, or even military command and control systems.
Exploitation of Software Vulnerabilities
The success of many cyberattacks hinges on exploiting vulnerabilities in software and systems. The Iranian attack likely leveraged previously unknown or poorly patched vulnerabilities to gain initial access. This highlights the ongoing challenge of maintaining up-to-date software and patching systems effectively across vast government networks. Future attacks will likely focus on exploiting zero-day vulnerabilities – vulnerabilities unknown to the software vendor and thus unpatched – and supply chain attacks, compromising software during its development or distribution to infect numerous downstream users.
So, the DHS just issued a cyber threat alert, blaming Iran for targeting US government websites. It makes you think about the security of our digital infrastructure, and how crucial robust development practices are. This is why I’ve been digging into the advancements in application development, particularly checking out what’s new in domino app dev the low code and pro code future , to see how these tools might help bolster defenses against these kinds of attacks.
Ultimately, strengthening our online systems is a battle we all need to fight, and innovative tech plays a key role.
The SolarWinds attack in 2020, which compromised thousands of organizations through a compromised software update, is a prime example of the devastating potential of such attacks. This underscores the need for greater vigilance in software supply chain security and more robust vulnerability management practices.
Increased Use of Artificial Intelligence and Machine Learning
The application of AI and machine learning in both offensive and defensive cybersecurity is rapidly expanding. State-sponsored actors like Iran are likely to leverage these technologies to automate attacks, enhance their effectiveness, and make them harder to detect. AI can be used to identify vulnerabilities, craft more effective phishing campaigns, and even automate the process of exploiting weaknesses in systems.
On the defensive side, AI can be used to detect anomalies and suspicious activity, but the arms race continues, requiring constant innovation to stay ahead of the curve. The potential for AI-powered attacks to overwhelm human defenders and escalate the speed and scale of cyber conflicts is a significant concern for the future. Real-world examples, although not directly attributable to Iran, include the increasing use of AI-powered malware and automated phishing campaigns already observed in various cybercrime operations.
Public Awareness and Education: Dhs Issues Cyber Threat Alert For Us Government Websites And Suspects Iran

The recent cyberattacks targeting US government websites underscore the critical need for enhanced public cybersecurity awareness. A well-informed populace is the first line of defense against sophisticated cyber threats, bolstering national security and protecting individual interests. Improved understanding of online risks and proactive measures can significantly reduce the vulnerability of both individuals and government systems.This section details a public service announcement, a proposed infographic design, and recommendations to better educate the public about cybersecurity threats and government responses.
Public Service Announcement: Cybersecurity Awareness
This public service announcement (PSA) would utilize a concise and impactful message to reach a broad audience. The PSA would open with a compelling statistic highlighting the increasing prevalence of cyberattacks and their potential consequences (e.g., “Cybercrime costs the US billions annually, impacting individuals and businesses alike”). The core message would emphasize the importance of practicing safe online habits, such as using strong passwords, regularly updating software, and being wary of phishing attempts.
The PSA would conclude with a call to action, encouraging viewers to visit a dedicated website for further resources and educational materials. The visual style would be clean and modern, employing bold colors and clear typography for maximum impact across various media platforms (television, radio, social media). A short, memorable tagline would be incorporated, such as “Stay Secure Online: It’s Your Responsibility.”
Infographic: Common Cyber Threats and Prevention
The infographic would be designed as a visually appealing and easily digestible guide to common cyber threats. It would employ a circular layout, with each segment representing a different threat. The central circle would feature the title: “Protect Yourself Online.”Each segment would depict a specific threat:* Phishing: This segment would show a visual representation of a phishing email, highlighting suspicious elements like poor grammar, unexpected requests, and unusual sender addresses.
Accompanying text would explain how to identify and avoid phishing scams.* Malware: This segment would use an icon depicting a virus or worm alongside a brief explanation of malware types (viruses, ransomware, spyware). It would emphasize the importance of using antivirus software and regularly updating it.* Weak Passwords: This segment would visually represent a cracked padlock, contrasting it with a strong, complex password.
It would provide examples of strong passwords and recommend using password managers.* Public Wi-Fi Risks: This segment would show a person using a laptop in a coffee shop, with a warning about the dangers of unsecured Wi-Fi networks. It would advise using a VPN for secure connections.* Social Engineering: This segment would depict a person being manipulated online, highlighting the tactics used in social engineering attacks.
It would emphasize the importance of verifying requests and information before acting.Data presented would include statistics on the frequency of each threat type, emphasizing their real-world impact. The infographic’s color scheme would use contrasting colors to highlight key information and maintain visual appeal.
Recommendations for Improving Public Understanding
Improving public understanding requires a multi-pronged approach. First, government agencies should collaborate with educational institutions to integrate cybersecurity education into school curricula, starting at a young age. Second, public awareness campaigns should be regularly updated to reflect emerging threats and technologies. These campaigns should use accessible language and multiple media channels to reach diverse audiences. Third, the government should invest in developing user-friendly cybersecurity tools and resources, making it easier for individuals to protect themselves online.
Finally, clear and concise government communication during and after cyber incidents is crucial for building public trust and confidence. Transparency and proactive information sharing will empower citizens to take appropriate precautions.
Conclusion
The DHS cyber threat alert serves as a stark reminder of the ever-evolving landscape of cyber warfare and the persistent threat posed by state-sponsored actors. While the full extent of the damage may not be known for some time, the incident highlights critical vulnerabilities in our national cybersecurity infrastructure. Proactive measures, improved cybersecurity practices, and increased international collaboration are essential to mitigate future threats and protect vital government systems and citizen data.
The ongoing investigation and the government’s response will be key in determining the long-term implications of this incident and shaping future cybersecurity strategies.
FAQ Section
What specific government websites were targeted?
The DHS alert hasn’t publicly disclosed the specific websites targeted to avoid aiding potential future attacks. The information is likely being kept confidential during the ongoing investigation.
What type of data might have been compromised?
The potential data breach could include sensitive government information, citizen data, or confidential documents depending on the websites targeted and the success of the attack.
What is the likelihood of future attacks?
The likelihood of future attacks is unfortunately high. State-sponsored cyberattacks are becoming increasingly common, and this incident highlights the ongoing need for robust cybersecurity measures.
How can I protect myself from similar attacks?
While this attack targets government systems, practicing good cybersecurity hygiene is always recommended. This includes using strong passwords, being wary of phishing scams, and keeping software updated.





