Digital Diagnosis Why Healthcare Email Breaches Escalate
Digital diagnosis why are email security breaches escalating in healthcare – Digital Diagnosis: Why are email security breaches escalating in healthcare? It’s a question haunting the healthcare industry, a chilling reality fueled by increasingly sophisticated attacks and vulnerabilities within our digital infrastructure. We’re seeing a dramatic rise in breaches, impacting everything from small clinics struggling to stay afloat to large hospitals facing crippling financial and reputational damage. This isn’t just about numbers; it’s about the sensitive patient data at risk – the very heart of the doctor-patient relationship.
This alarming trend isn’t simply a matter of bad luck; it’s a complex problem stemming from outdated systems, insufficient employee training, and the inherent challenges of balancing security with the need for seamless data access. We’ll delve into the specifics – from the types of attacks prevalent in the healthcare sector to the legal and regulatory consequences of failing to protect patient information.
We’ll also explore emerging technologies offering potential solutions to this critical issue, ultimately aiming to provide a clearer picture of how we can better protect ourselves in this increasingly digital world.
The Rising Tide of Healthcare Email Breaches
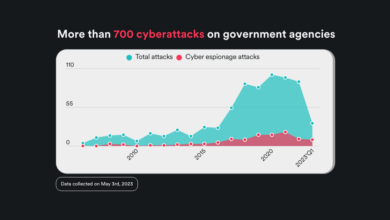
The healthcare industry, already grappling with complex regulations and increasing cybersecurity threats, faces a particularly acute challenge: the escalating number of email-based security breaches. Over the past five years, we’ve witnessed a dramatic rise in these incidents, impacting patient data, operational efficiency, and the overall trust placed in healthcare providers. This surge isn’t simply a matter of increasing cybercrime; it’s also driven by the unique vulnerabilities inherent in the healthcare sector’s data-rich environment and often outdated security infrastructure.The significant increase in healthcare email breaches over the past five years is undeniable.
While precise figures are difficult to obtain due to underreporting, numerous studies and news reports point to a consistent upward trend. For example, the Identity Theft Resource Center (ITRC) reports a substantial increase in data breaches across all sectors, with healthcare consistently ranking among the most heavily impacted. While specific percentage increases vary depending on the source and reporting methodology, a conservative estimate suggests a doubling or tripling of reported breaches compared to five years ago.
This underreporting, however, means the actual numbers are likely significantly higher.
Types of Email-Based Attacks Targeting Healthcare Organizations
Healthcare organizations are prime targets for various email-based attacks due to the sensitive nature of the data they hold. Phishing attacks, which involve deceptive emails attempting to trick recipients into revealing sensitive information, are extremely common. These emails often mimic legitimate communications from trusted sources, such as insurance companies or colleagues, to lure unsuspecting employees into clicking malicious links or downloading infected attachments.
Spear phishing attacks represent a more sophisticated variant, where attackers meticulously research their targets to personalize the phishing attempt, increasing the likelihood of success. Malware, including ransomware and spyware, is frequently delivered via email attachments or links, allowing attackers to gain unauthorized access to systems and data, potentially encrypting files and demanding ransom payments.
Impact of Breaches on Different Sized Healthcare Organizations
The impact of email security breaches varies considerably depending on the size of the healthcare organization. Smaller clinics, often lacking dedicated cybersecurity teams and robust security infrastructure, are particularly vulnerable. A single successful phishing attack could compromise a significant portion of their patient data, potentially leading to substantial financial losses, regulatory penalties, and reputational damage. Large hospitals, while possessing more resources for cybersecurity, face proportionally larger consequences due to the sheer volume of data they handle.
A breach affecting a large hospital could result in the exposure of millions of patient records, triggering widespread legal action and significant reputational harm. The cost of remediation and recovery efforts is also significantly higher for larger organizations. Furthermore, the potential for disruption to critical services is much greater in larger facilities.
Vulnerabilities in Healthcare Email Infrastructure: Digital Diagnosis Why Are Email Security Breaches Escalating In Healthcare
The healthcare industry faces a unique challenge in securing its email systems. The sensitive nature of patient data, combined with the often complex and outdated infrastructure, creates a fertile ground for breaches. Understanding the vulnerabilities within these systems is crucial for effective mitigation strategies. This section will explore the key weaknesses and their implications.
Healthcare email systems are vulnerable to a range of attacks, many stemming from a combination of factors. These vulnerabilities aren’t always obvious, and they often interact to create larger security risks. Addressing these issues requires a multi-faceted approach, encompassing technology upgrades, robust security protocols, and comprehensive employee training.
Outdated Software and Insufficient Security Patches, Digital diagnosis why are email security breaches escalating in healthcare
Outdated software represents a significant vulnerability. Many healthcare organizations still rely on legacy email systems that lack the security features of modern platforms. These older systems often lack crucial security patches, leaving them exposed to known exploits. For example, a system running an outdated version of Microsoft Exchange Server might be vulnerable to ransomware attacks or data exfiltration attempts that have already been patched in newer versions.
The delay in updating software, often due to budgetary constraints, integration challenges, or a lack of IT resources, directly increases the risk of a breach.
Phishing and Social Engineering Attacks
Phishing attacks, which exploit human error to gain access to sensitive information, are highly effective against healthcare email systems. Employees are often targeted with emails that appear to be legitimate communications from trusted sources, such as colleagues, insurance companies, or patients. These emails may contain malicious links or attachments that download malware onto the employee’s computer, providing attackers with access to the entire email system.
Insufficient employee training on recognizing and reporting phishing attempts significantly amplifies this risk. The lack of awareness, combined with pressure to respond quickly to emails, makes healthcare workers particularly susceptible.
Lack of Multi-Factor Authentication (MFA)
Many healthcare organizations still fail to implement multi-factor authentication (MFA), a critical security measure that adds an extra layer of protection beyond just passwords. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their phone, before granting access to the email system. Without MFA, attackers who obtain an employee’s password through phishing or other means can easily gain access to the email account and its contents.
The failure to implement MFA dramatically increases the likelihood of successful breaches.
Inadequate Employee Training
Inadequate employee training on cybersecurity best practices significantly contributes to email breaches. Healthcare employees may not be aware of the risks associated with opening suspicious emails, clicking on malicious links, or falling for social engineering tactics. Insufficient training on password security, phishing awareness, and secure email practices leaves organizations vulnerable to attacks that could easily be prevented with proper education and awareness programs.
Regular security awareness training should be mandatory for all employees and should cover relevant topics such as phishing, malware, and social engineering tactics.
Healthcare’s reliance on email for sensitive patient data makes it a prime target for cyberattacks, leading to the escalating breaches we see. Building robust, secure systems is crucial, and that’s where advancements like those discussed in this article on domino app dev the low code and pro code future become incredibly important. These new development methods could help healthcare organizations create more secure, efficient, and HIPAA-compliant applications to combat these threats and protect patient information.
Balancing Security, Accessibility, and Usability
Balancing security with accessibility and usability presents a significant challenge for healthcare email systems. Implementing overly restrictive security measures can hinder productivity and workflow, making it difficult for employees to access the information they need to perform their jobs. For example, excessively complex authentication procedures can frustrate users and lead to workarounds that weaken security. Finding the right balance requires careful consideration of the specific needs of the healthcare organization and its employees, incorporating user-friendly security solutions without compromising overall protection.
Comparison of Email Security Solutions
| Solution Name | Key Features | Cost | Security Rating |
|---|---|---|---|
| Proofpoint | Advanced threat protection, email encryption, data loss prevention | Varies based on features and users | High |
| Microsoft 365 E5 | Advanced threat protection, data loss prevention, MFA, email encryption | Subscription-based, varies based on users | High |
| Mimecast | Email security, archiving, continuity, and compliance | Varies based on features and users | High |
| Barracuda Essentials | Spam and virus filtering, email archiving, data loss prevention | Subscription-based, relatively affordable | Medium |
The Human Factor

Let’s face it: the weakest link in any cybersecurity system is often the human element. In healthcare, where sensitive patient data is constantly being handled via email, this weakness is amplified, leading to a significant portion of email-based breaches. Understanding and mitigating the risks associated with employee behavior is crucial for strengthening overall email security. This involves a multi-pronged approach encompassing education, policy, and robust security protocols.Employees, often unaware of the subtle tactics used in phishing and other email-based attacks, can inadvertently compromise the entire system.
A seemingly harmless email can contain malicious links or attachments, granting hackers access to valuable data. The consequences of such breaches can be devastating, leading to financial losses, reputational damage, and, most importantly, the potential exposure of patient Protected Health Information (PHI).
Common Employee Behaviors Increasing Email Security Risks
A lack of awareness regarding email security threats contributes significantly to successful attacks. For instance, employees might click on links in emails from unknown senders, download attachments from suspicious sources, or reuse passwords across multiple platforms. These actions, often performed out of haste or a lack of understanding, can have severe repercussions. Consider the scenario where an employee clicks a link in a phishing email disguised as an official communication from the hospital administration.
This single click could grant hackers access to the entire network, potentially exposing thousands of patient records. Another example could be an employee opening an attachment from an unknown sender, inadvertently installing malware onto their computer, thereby providing a backdoor for hackers to access sensitive data. Finally, reusing passwords across personal and work accounts creates a significant vulnerability; if one account is compromised, the attacker might gain access to multiple systems.
Designing an Effective Email Security Training Program
A comprehensive training program is essential to address the human factor. This program should go beyond simple awareness training and focus on practical skills and knowledge. The training should include interactive modules, real-life examples of phishing attempts, and simulated phishing exercises to test employee understanding. Regular refresher courses are also vital to reinforce key concepts and address emerging threats.
The program should be tailored to the specific roles and responsibilities of employees, acknowledging that different roles have different levels of email interaction and associated risks. For example, administrative staff who handle billing and patient information require more intensive training compared to those in less sensitive roles. Effective training should also emphasize the importance of reporting suspicious emails immediately and the consequences of failing to adhere to security protocols.
Best Practices for Secure Email Policies and Procedures
Healthcare organizations must establish clear and comprehensive email security policies and procedures. These policies should explicitly Artikel acceptable email usage, including guidelines for handling attachments, responding to suspicious emails, and password management. They should also detail the consequences of violating these policies. Regular audits and reviews of these policies are necessary to ensure they remain relevant and effective in the face of evolving threats.
For example, the policy should prohibit the opening of attachments from unknown senders and mandate the use of strong, unique passwords for all work-related accounts. Regular security awareness training should be mandatory for all employees, and the organization should provide clear reporting mechanisms for suspicious activity. Furthermore, implementing multi-factor authentication (MFA) adds an extra layer of security, making it significantly more difficult for unauthorized individuals to access accounts even if their passwords are compromised.
Regular security assessments and penetration testing can identify vulnerabilities in the email infrastructure and help organizations proactively address potential weaknesses. Finally, a robust incident response plan is essential to mitigate the impact of a successful breach and to ensure a swift and effective response.
The Role of Digital Diagnosis and Data Transmission
The increasing reliance on digital tools in healthcare, while offering significant benefits in terms of efficiency and patient care, has inadvertently created new vulnerabilities in email security. The widespread adoption of digital diagnostic tools and electronic health record (EHR) systems, coupled with the frequent use of email for communication, has dramatically increased the volume of sensitive patient data transmitted electronically, making healthcare organizations a prime target for cyberattacks.
This section explores the specific risks associated with this reliance on digital technologies and Artikels crucial security measures to mitigate these threats.The transmission of sensitive patient data, including medical images, test results, diagnoses, and treatment plans, via email presents a significant security risk. Email, by its nature, is not inherently secure. Unless properly secured, emails are easily intercepted by malicious actors using various methods, such as phishing attacks, malware, or exploiting vulnerabilities in email servers.
A single compromised email containing patient data can lead to a massive breach, exposing Protected Health Information (PHI) to unauthorized access, potentially resulting in identity theft, financial fraud, and reputational damage for both the healthcare provider and the patients involved. The consequences can be severe, including hefty fines from regulatory bodies like HIPAA in the US. For example, a recent breach involving a healthcare clinic that transmitted patient data via unencrypted email resulted in a settlement of several million dollars.
Email Encryption and Secure Transmission Protocols
Implementing robust security protocols is paramount to safeguarding patient data transmitted via email. This involves more than just relying on standard email security measures. Strong encryption is critical. Encrypting emails ensures that only the intended recipient, possessing the decryption key, can access the content. Several encryption methods are available, including TLS/SSL (Transport Layer Security/Secure Sockets Layer) for secure email transmission and PGP (Pretty Good Privacy) for end-to-end encryption.
Additionally, using a Virtual Private Network (VPN) for all email access adds an extra layer of security by encrypting internet traffic. A multi-layered approach combining these methods is highly recommended.
Data Minimization and Access Control
Limiting the amount of patient data transmitted via email is another crucial strategy. Only essential information should be included in emails. Healthcare providers should leverage secure file transfer protocols (SFTP) or dedicated patient portals for the transmission of large files or highly sensitive data. Implementing strict access control measures, ensuring that only authorized personnel can access and transmit patient data via email, is equally vital.
This includes strong password policies, multi-factor authentication (MFA), and regular security awareness training for all staff.
Regular Security Audits and Updates
Regular security audits and penetration testing of email systems and related infrastructure are essential to identify and address potential vulnerabilities. Keeping email software and antivirus programs updated with the latest security patches helps to protect against known exploits. Promptly addressing any security incidents and implementing corrective actions are also crucial. A proactive approach to security, involving continuous monitoring and improvement, is far more effective than a reactive one.
Regulatory Compliance and Legal Ramifications

Healthcare email breaches don’t just result in data loss; they trigger significant legal and financial repercussions. Strict regulations exist to protect patient health information, and violating these rules can lead to substantial penalties and damage to an organization’s reputation. Understanding these regulations and their potential consequences is crucial for healthcare providers.The legal landscape surrounding the protection of patient data in email communication is complex and varies depending on jurisdiction.
However, some key regulations consistently apply and carry substantial weight. Non-compliance can result in severe financial penalties, legal battles, and irreparable damage to public trust.
HIPAA Compliance and Penalties
The Health Insurance Portability and Accountability Act (HIPAA) in the United States is a cornerstone of patient data protection. It sets stringent standards for the privacy and security of Protected Health Information (PHI), which includes information transmitted via email. Breaches of HIPAA regulations can result in significant financial penalties, ranging from hundreds of thousands to millions of dollars, depending on the severity and nature of the breach.
For example, a hospital experiencing a large-scale data breach affecting thousands of patients could face penalties in the millions, alongside potential lawsuits from affected individuals. Beyond financial penalties, HIPAA violations can also lead to reputational damage, loss of patient trust, and even criminal charges in certain circumstances. The Office for Civil Rights (OCR) within the U.S. Department of Health and Human Services enforces HIPAA compliance and investigates reported breaches.
GDPR and Data Protection in Europe
The General Data Protection Regulation (GDPR) in the European Union sets a high bar for data protection, extending to all organizations processing personal data of EU residents, regardless of their location. Similar to HIPAA, GDPR mandates strict security measures to protect personal data, including email communication. Non-compliance can lead to substantial fines, up to €20 million or 4% of annual global turnover, whichever is higher.
The GDPR also grants individuals significant rights regarding their data, including the right to access, rectification, and erasure of their data. A healthcare provider in Europe failing to adequately secure patient email communications and resulting in a data breach could face these hefty fines, along with potential legal action from affected individuals and regulatory bodies.
Healthcare’s reliance on email for sensitive patient data makes it a prime target for breaches. The increasing use of cloud services exacerbates this, highlighting the need for robust security measures. Understanding how to effectively manage this risk is crucial, and learning more about solutions like bitglass and the rise of cloud security posture management can help.
Ultimately, stronger cloud security is essential to combatting the escalating email security breaches plaguing the healthcare industry.
International Variations in Data Protection Laws
Data protection laws vary across different jurisdictions, each with its own set of penalties for non-compliance. While HIPAA and GDPR are prominent examples, many other countries have their own regulations with varying levels of stringency. For instance, Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) provides a framework for protecting personal information, including health information. Australia’s Privacy Act 1988 also sets out requirements for handling personal information.
The penalties for non-compliance differ significantly across these jurisdictions, highlighting the need for healthcare organizations to understand the specific legal requirements in each region where they operate. Failure to comply with these international regulations can result in a range of sanctions, from warnings and fines to legal action and reputational damage. A multinational healthcare organization, for instance, needs a robust, globally compliant data protection strategy to avoid significant legal and financial risks.
Emerging Technologies and Future Solutions
The escalating tide of healthcare email breaches necessitates a proactive shift towards advanced security measures. Emerging technologies offer a powerful arsenal to combat these threats, moving beyond traditional approaches and implementing sophisticated, multi-layered defenses. This section explores some of the most promising advancements in email security for the healthcare sector.The potential of these technologies to mitigate risk is substantial, offering a significant upgrade in both preventative and reactive capabilities.
By leveraging AI and advanced encryption, healthcare providers can significantly reduce their vulnerability to sophisticated phishing attacks, malware infections, and data breaches. This proactive approach helps safeguard sensitive patient data and maintain compliance with stringent regulations.
AI-Powered Threat Detection
AI-powered threat detection systems analyze email content and metadata in real-time, identifying patterns and anomalies indicative of malicious activity. Unlike traditional rule-based systems, AI can adapt to evolving threats, learning from past attacks to improve its accuracy and effectiveness. For example, an AI system might detect a phishing email by identifying subtle inconsistencies in the sender’s email address, the language used, or the links included, even if those inconsistencies are too subtle for a human to notice.
This proactive identification allows for immediate blocking or quarantining of suspicious emails before they reach the intended recipient. Furthermore, AI can analyze user behavior to identify unusual patterns, such as unexpected login attempts or unusual email forwarding activity, potentially indicating a compromised account.
Advanced Encryption Techniques
Advanced encryption methods, such as end-to-end encryption and homomorphic encryption, offer robust protection for sensitive email content. End-to-end encryption ensures that only the sender and recipient can decrypt the message, protecting it from interception even if the email server is compromised. Homomorphic encryption, while still under development for widespread use, allows computations to be performed on encrypted data without decryption, potentially revolutionizing secure data sharing and collaboration.
This technology is particularly relevant for the exchange of sensitive medical images or patient records.
Comparative Effectiveness of Email Security Solutions
Imagine a table visualizing the effectiveness of different email security solutions against various attack types. The rows represent different security solutions (e.g., traditional spam filters, AI-powered threat detection, multi-factor authentication, end-to-end encryption). The columns represent different attack types (e.g., phishing, malware, ransomware, spoofing). Each cell in the table would show a rating (e.g., low, medium, high) indicating the effectiveness of a particular solution against a specific attack type.
For example, traditional spam filters would show high effectiveness against simple spam emails but low effectiveness against sophisticated phishing attacks, while AI-powered threat detection would show higher effectiveness across a wider range of attacks. Multi-factor authentication would be highly effective against unauthorized access attempts, and end-to-end encryption would offer strong protection against data breaches during transit. This visual representation would clearly demonstrate the strengths and weaknesses of different solutions and highlight the need for a multi-layered approach.
Final Wrap-Up
The escalating number of email security breaches in healthcare isn’t just a technical problem; it’s a systemic one, demanding a multi-pronged approach. Strengthening email security requires a combination of robust technological solutions, comprehensive employee training, and a fundamental shift in how we think about data protection. By understanding the vulnerabilities, addressing the human factor, and embracing emerging technologies, we can begin to mitigate the risks and safeguard the sensitive information entrusted to our care.
The future of healthcare security depends on our collective commitment to proactive and comprehensive solutions.
FAQs
What are the most common types of email attacks targeting healthcare?
Phishing, spear phishing, malware, and ransomware are common threats. Phishing attempts to trick users into revealing sensitive information, while spear phishing targets specific individuals. Malware infects systems, and ransomware encrypts data and demands payment for its release.
How can healthcare organizations improve employee training on email security?
Regular training sessions, phishing simulations, and clear guidelines on handling suspicious emails are crucial. Training should cover recognizing phishing attempts, avoiding suspicious links and attachments, and reporting suspicious activity.
What are the financial penalties for HIPAA violations related to email breaches?
Penalties vary depending on the severity and nature of the violation, ranging from thousands to millions of dollars in fines, along with potential legal action.
Are there any free or low-cost email security solutions available for small clinics?
Yes, several providers offer tiered pricing or free plans with basic features. Open-source solutions are also available but may require technical expertise to implement and maintain.