Improve Software Quality with Application Governance
Improve software quality with application governance: It sounds serious, right? But think of it this way – it’s about building better software, faster, and with fewer headaches. This isn’t about stifling creativity; it’s about setting up a system that helps your team thrive. We’ll explore how a well-defined governance framework can be your secret weapon for delivering high-quality software that actually meets your users’ needs and keeps your business humming.
We’ll dive into the practical aspects, from defining application governance and its key principles to exploring the role of automation and tools. We’ll also cover risk management, compliance, and the crucial importance of collaboration and communication throughout the entire software development lifecycle. Get ready to level up your software development game!
Defining Application Governance for Software Quality
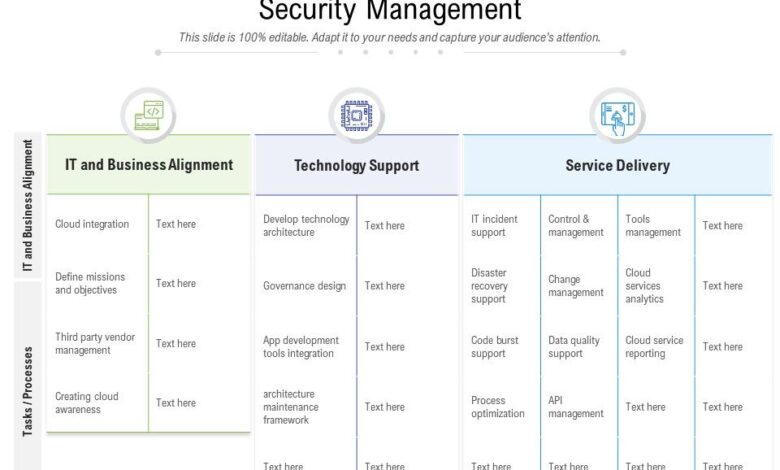
Application governance, in the context of software development, isn’t just about following rules; it’s a strategic approach to managing the entire lifecycle of applications to ensure they consistently meet quality standards, business needs, and risk tolerances. It acts as a bridge between business objectives and the technical execution of software projects, fostering a culture of quality and efficiency. Think of it as the conductor of an orchestra, ensuring all the different instruments (teams, processes, technologies) work together harmoniously to produce a beautiful piece of software.Application governance plays a vital role in improving software quality by providing a structured framework for decision-making, accountability, and continuous improvement.
It establishes clear guidelines and processes for everything from initial requirements gathering to deployment and maintenance, reducing the likelihood of errors, inconsistencies, and security vulnerabilities. By implementing a robust governance framework, organizations can significantly reduce development costs, improve time-to-market, and enhance customer satisfaction.
Key Principles of Effective Application Governance
Effective application governance hinges on several core principles. These principles act as guiding lights, ensuring that the governance framework remains relevant, adaptable, and effective throughout the software development lifecycle. Without these principles, the framework can become cumbersome and ultimately counterproductive.
- Clear Roles and Responsibilities: Defining who is responsible for what, from initial approval of projects to ongoing maintenance and support, is crucial. This avoids ambiguity and ensures accountability.
- Standardized Processes and Procedures: Consistent processes across all applications ensure predictability and reduce the risk of errors. This includes coding standards, testing methodologies, and deployment procedures.
- Risk Management and Mitigation: Identifying and addressing potential risks proactively is essential. This includes security vulnerabilities, performance bottlenecks, and compliance issues.
- Continuous Monitoring and Improvement: Regularly assessing the effectiveness of the governance framework and making adjustments based on feedback and performance data is key to ongoing success. This involves tracking key metrics and identifying areas for improvement.
- Communication and Collaboration: Effective communication and collaboration among all stakeholders (developers, testers, business users, etc.) is vital to ensure alignment and prevent misunderstandings.
Benefits of Implementing a Robust Application Governance Framework
The benefits of implementing a robust application governance framework extend beyond simply improving software quality. It fosters a more efficient and predictable development process, leading to significant improvements across the board.
- Improved Software Quality: Consistent adherence to standards and processes results in fewer defects, enhanced security, and improved performance.
- Reduced Development Costs: Proactive risk management and efficient processes minimize rework and delays, saving time and money.
- Faster Time-to-Market: Streamlined processes and reduced errors contribute to quicker deployment and release cycles.
- Enhanced Compliance: A well-defined governance framework ensures compliance with relevant regulations and industry standards.
- Increased Stakeholder Satisfaction: Meeting expectations and delivering high-quality software on time and within budget leads to increased satisfaction among all stakeholders.
A Simple Model Illustrating the Relationship Between Application Governance and Software Quality Improvement
Imagine a simple model represented as a Venn diagram. One circle represents “Effective Application Governance,” encompassing elements like defined processes, clear roles, risk management, and continuous improvement. The other circle represents “Software Quality Attributes,” including functionality, reliability, security, performance, and maintainability. The overlapping area of the two circles represents the significant improvement in software quality directly attributable to the implementation of effective application governance.
The larger the overlap, the greater the improvement in software quality. This model visually demonstrates the direct and positive correlation between strong application governance and the achievement of higher software quality.
Key Processes and Practices
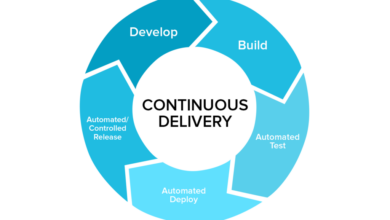
Building a robust application governance framework isn’t a one-time event; it’s an ongoing commitment to continuous improvement. This requires a blend of strategic planning, practical implementation, and consistent monitoring. Effective application governance directly translates to higher software quality, reduced risk, and improved operational efficiency.Establishing and maintaining a strong application governance framework requires a multi-faceted approach. It’s not enough to simply define policies; you need to embed them into the software development lifecycle (SDLC) and foster a culture of compliance.
This involves clear roles and responsibilities, well-defined processes, and the use of appropriate tools and technologies.
Best Practices for Establishing and Maintaining a Strong Application Governance Framework
A successful application governance framework hinges on several key practices. These practices ensure alignment between business needs, IT capabilities, and risk management objectives. Implementing these practices fosters a proactive, rather than reactive, approach to software quality.
- Clearly Defined Roles and Responsibilities: Establish a governance team with clearly defined roles and responsibilities, including application owners, architects, developers, security personnel, and compliance officers. Each role should have a defined scope of authority and accountability.
- Standardized Processes and Procedures: Develop and implement standardized processes for application development, deployment, and maintenance. This includes requirements gathering, design, coding, testing, and release management. Consistency ensures predictability and reduces errors.
- Regular Application Portfolio Reviews: Conduct regular reviews of the application portfolio to identify potential risks, inefficiencies, and opportunities for improvement. This allows for proactive risk mitigation and optimization of resources.
- Automated Tools and Technologies: Utilize automated tools for application monitoring, security scanning, and performance analysis. Automation streamlines processes, improves efficiency, and enhances accuracy.
- Continuous Monitoring and Improvement: Continuously monitor application performance, security, and compliance. Regularly review and update governance policies and procedures based on lessons learned and best practices.
Common Challenges in Implementing Application Governance and Mitigation Strategies
Implementing application governance often faces hurdles that can impede its effectiveness. Understanding these challenges and developing mitigation strategies is crucial for success.
- Resistance to Change: Introducing new processes and procedures can meet resistance from teams accustomed to established workflows. Mitigation: Engage stakeholders early, clearly communicate the benefits of application governance, and provide adequate training and support.
- Lack of Resources: Implementing and maintaining a robust governance framework requires resources, including personnel, tools, and budget. Mitigation: Develop a phased implementation plan, prioritize initiatives based on risk and impact, and secure buy-in from senior management.
- Data Silos and Lack of Visibility: Lack of integrated data and visibility across the application portfolio can hinder effective governance. Mitigation: Implement a centralized application inventory and reporting system to provide a comprehensive view of the application landscape.
- Inconsistent Enforcement: Without consistent enforcement of policies and procedures, application governance initiatives can become ineffective. Mitigation: Establish clear accountability mechanisms and regularly monitor compliance.
Comparison of Application Governance Models
Different organizations adopt varying approaches to application governance. The choice depends on factors such as organizational structure, size, and risk tolerance.
| Governance Model | Description | Effectiveness |
|---|---|---|
| Centralized | A single team manages all aspects of application governance. | Highly effective for smaller organizations or those with a limited number of applications. Can become cumbersome in larger organizations. |
| Decentralized | Responsibility for application governance is distributed across different teams or departments. | Suitable for larger organizations with diverse application portfolios. Requires strong communication and coordination across teams. |
| Hybrid | Combines elements of centralized and decentralized models. | Offers flexibility and scalability. Requires careful planning and coordination to avoid inconsistencies. |
Essential Elements for a Successful Application Governance Program
A checklist of essential elements ensures a comprehensive and effective program.
- Clearly Defined Objectives and Scope: Define the goals and scope of the application governance program, aligning with overall business objectives.
- Governance Structure and Roles: Establish a clear governance structure with defined roles and responsibilities.
- Policies and Procedures: Develop and implement comprehensive policies and procedures covering all aspects of the application lifecycle.
- Risk Management Framework: Integrate a risk management framework to identify, assess, and mitigate potential risks.
- Metrics and Reporting: Establish key performance indicators (KPIs) and regularly report on the effectiveness of the governance program.
- Continuous Improvement Process: Implement a continuous improvement process to adapt to changing business needs and technology advancements.
Role of Automation and Tools
Automating application governance processes is no longer a luxury; it’s a necessity for organizations aiming for high-quality software delivery at scale. Manual processes are prone to errors, inconsistencies, and bottlenecks, hindering efficiency and increasing the risk of defects slipping into production. Automation streamlines these processes, allowing teams to focus on higher-value activities and ultimately delivering better software faster.Automation significantly improves application governance by enhancing visibility, traceability, and control across the entire software development lifecycle (SDLC).
By automating repetitive tasks and enforcing consistent policies, organizations can reduce human error, improve compliance, and accelerate the feedback loop for faster issue resolution. This leads to a more robust and reliable application ecosystem.
Automation’s Impact on Key Governance Activities
Automating application governance isn’t about replacing human expertise; it’s about augmenting it. Automation handles the repetitive, time-consuming tasks, freeing up human resources to focus on strategic initiatives, such as risk assessment and continuous improvement. Specific areas where automation shines include automated policy enforcement, streamlined change management, and proactive risk identification. For instance, automated code analysis can detect vulnerabilities early in the development process, preventing security breaches and reducing the cost of remediation.
Automated deployment pipelines ensure consistent and reliable releases, minimizing the risk of human error during the deployment process.
Examples of Application Governance Tools
The following table showcases some tools commonly used to support application governance activities. The selection represents a range of functionalities and price points, highlighting the breadth of available options. Remember that the optimal toolset will depend on the specific needs and context of your organization.
| Tool Name | Function | Benefits | Limitations |
|---|---|---|---|
| GitHub/GitLab/Bitbucket | Version control, collaboration, code review | Improved collaboration, code traceability, easier rollback | Requires strong team adherence to workflows; managing large repositories can be challenging. |
| SonarQube | Static code analysis, vulnerability detection | Early detection of bugs and vulnerabilities, improved code quality | Can generate false positives; requires configuration and expertise to use effectively. |
| Jenkins/Azure DevOps/GitLab CI/CD | Continuous Integration/Continuous Delivery (CI/CD) | Automated builds, testing, and deployments; faster release cycles | Requires expertise in setting up and maintaining pipelines; complex integrations may be needed. |
| Splunk/Datadog/Prometheus | Application performance monitoring (APM) | Real-time monitoring of application performance, proactive issue detection | Can be complex to set up and manage; requires expertise in data analysis. |
| ServiceNow/Jira | Incident and change management | Streamlined incident resolution, improved change control processes | Can be expensive; requires careful configuration and integration with other systems. |
Automated Testing and Monitoring’s Contribution to Effective Application Governance
Automated testing is a cornerstone of effective application governance. Unit tests, integration tests, and end-to-end tests, when automated, provide continuous feedback on code quality, ensuring that new features and changes don’t introduce regressions. This reduces the risk of defects reaching production and improves overall software reliability. Automated monitoring tools provide real-time insights into application performance, security, and availability.
By detecting anomalies and potential issues proactively, organizations can respond quickly, minimizing downtime and ensuring a positive user experience. For example, automated alerts triggered by performance degradation can initiate immediate investigation and remediation, preventing major outages. This proactive approach is crucial for maintaining high levels of software quality and user satisfaction.
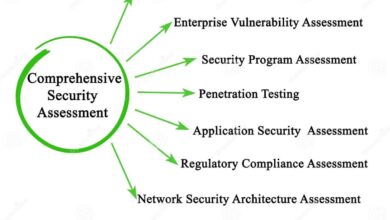
Risk Management and Compliance
Application governance plays a crucial role in mitigating risks and ensuring compliance throughout the software development lifecycle. By establishing clear processes, roles, and responsibilities, it provides a framework for proactively identifying, assessing, and managing potential issues before they escalate into major problems impacting quality, security, and regulatory adherence. This proactive approach leads to more stable, reliable, and compliant software applications.Application governance helps mitigate software development risks by providing a structured approach to managing the entire software development lifecycle.
This includes requirements gathering, design, development, testing, deployment, and maintenance. By implementing a robust governance framework, organizations can reduce the likelihood of errors, delays, and security vulnerabilities, ultimately leading to improved software quality and reduced costs. This structured approach allows for better tracking of progress, identification of potential bottlenecks, and early detection of risks.
Risk Identification and Assessment Process
A well-defined process is essential for identifying and assessing potential risks associated with software development and deployment. This process should be integrated into the application governance framework and involve various stakeholders across the organization. The process begins with brainstorming sessions to identify potential risks, followed by a detailed assessment of each risk’s likelihood and potential impact. A risk register, regularly updated, documents these findings.This risk identification and assessment process can be broken down into these steps:
- Risk Identification: This involves brainstorming sessions with developers, testers, security experts, and business stakeholders to identify potential risks across all phases of the software development lifecycle. Examples include technical risks (e.g., technology incompatibility, integration issues), business risks (e.g., changing requirements, market competition), and security risks (e.g., vulnerabilities, data breaches).
- Risk Analysis: Each identified risk is analyzed based on its likelihood and potential impact. Likelihood refers to the probability of the risk occurring, while impact assesses the severity of the consequences if the risk materializes. This can be quantified using a risk matrix, assigning scores to each risk based on likelihood and impact.
- Risk Prioritization: Based on the risk analysis, risks are prioritized based on their overall risk score (likelihood multiplied by impact). This allows resources to be focused on addressing the most critical risks first.
- Risk Response Planning: For each prioritized risk, a response plan is developed. This might involve mitigation strategies (e.g., implementing security controls, improving testing processes), acceptance (e.g., accepting the risk and its potential consequences), transference (e.g., outsourcing a risky task), or avoidance (e.g., changing requirements to eliminate the risk).
- Risk Monitoring and Review: The risk register is regularly reviewed and updated to reflect changes in the project or environment. This ensures that risks are continuously monitored and addressed throughout the software development lifecycle.
Ensuring Compliance with Industry Standards and Regulations
Application governance plays a vital role in ensuring compliance with various industry standards and regulations, such as HIPAA, GDPR, and PCI DSS. By establishing policies and procedures that align with these standards, organizations can minimize their risk of non-compliance and potential penalties. Regular audits and assessments help ensure ongoing compliance. This involves documenting processes, training employees, and implementing appropriate controls to safeguard sensitive data and adhere to regulatory requirements.
For instance, a financial institution developing a new mobile banking application must ensure compliance with PCI DSS to protect customer credit card information. Failure to do so can result in significant financial penalties and reputational damage.
Software Risk Management Flowchart
A flowchart visually represents the steps involved in managing software risks within an application governance framework.[Imagine a flowchart here. The flowchart would begin with “Risk Identification,” branching to “Risk Analysis,” then to “Risk Prioritization.” From prioritization, it would branch to “Risk Response Planning” (with sub-branches for Mitigation, Acceptance, Transference, and Avoidance). Finally, a loop would lead back to “Risk Monitoring and Review,” indicating the continuous nature of risk management.] The flowchart would clearly illustrate the iterative and cyclical nature of risk management, emphasizing the ongoing monitoring and adaptation required throughout the software development lifecycle.
Measuring and Improving Software Quality
Effective application governance isn’t just about setting rules; it’s about using data to understand and improve the quality of your software. By tracking key metrics and analyzing trends, we can identify weaknesses, prioritize improvements, and ultimately deliver higher-quality applications that meet business needs and stakeholder expectations. This section delves into the practical aspects of measuring and enhancing software quality within the framework of application governance.
Measuring software quality requires a multifaceted approach, encompassing various perspectives and utilizing a range of metrics. The specific metrics chosen will depend on the context of the application, the development methodology, and the overall goals of the organization. However, a focus on key areas consistently yields valuable insights.
Key Metrics for Software Quality Measurement, Improve software quality with application governance
The selection of appropriate metrics is crucial for effective software quality measurement. Focusing on a balanced set of metrics across different aspects of software development provides a holistic view of quality. These metrics should be regularly tracked and analyzed to gain actionable insights.
Effective tracking and analysis involve more than simply collecting numbers; it necessitates understanding the context of those numbers and using them to drive improvements. Let’s explore some key metrics and how to effectively analyze them.
Tracking and Analyzing Software Quality Metrics
Tracking and analyzing metrics requires a structured approach. By consistently monitoring these metrics, we can pinpoint areas needing attention and measure the effectiveness of improvement initiatives. The following examples illustrate how to use data to drive improvements.
- Defect Density: Track the number of defects found per thousand lines of code (KLOC) or per function point. A high defect density indicates potential issues in the development process or inadequate testing. Analyzing trends over time can highlight specific phases or modules with consistently high defect rates, allowing for targeted improvements in coding practices, testing strategies, or developer training.
- Mean Time To Resolution (MTTR): Measure the average time taken to resolve a defect once it’s reported. A high MTTR suggests inefficiencies in the defect resolution process, potentially due to inadequate documentation, lack of skilled resources, or complex debugging processes. Analyzing the root causes of delays can inform process improvements and resource allocation.
- Customer Satisfaction (CSAT): Gather feedback from users through surveys or feedback forms to assess their satisfaction with the application’s functionality, usability, and overall performance. Low CSAT scores indicate areas where the application falls short of user expectations, necessitating improvements in design, functionality, or user experience.
- Test Coverage: Measure the percentage of code covered by automated tests. Low test coverage indicates higher risk of undiscovered defects. Analyzing uncovered code segments can prioritize testing efforts and improve the overall robustness of the application.
Using Application Governance Data for Continuous Improvement
Application governance provides a framework for collecting and analyzing data related to software quality. This data can be leveraged to drive continuous improvement through various mechanisms.
Continuous improvement is an iterative process that requires regular monitoring, analysis, and adaptation. Using application governance data to inform these steps is key to creating a culture of quality.
Communicating Software Quality Metrics and Improvement Plans
Effective communication is essential for ensuring that stakeholders understand the software quality status and the plans for improvement. This includes using clear, concise visualizations and regular reporting.
Transparency and open communication build trust and ensure everyone is aligned on quality goals. Regular reporting on key metrics, coupled with clear explanations of improvement initiatives, fosters a shared understanding and commitment to quality.
Collaboration and Communication
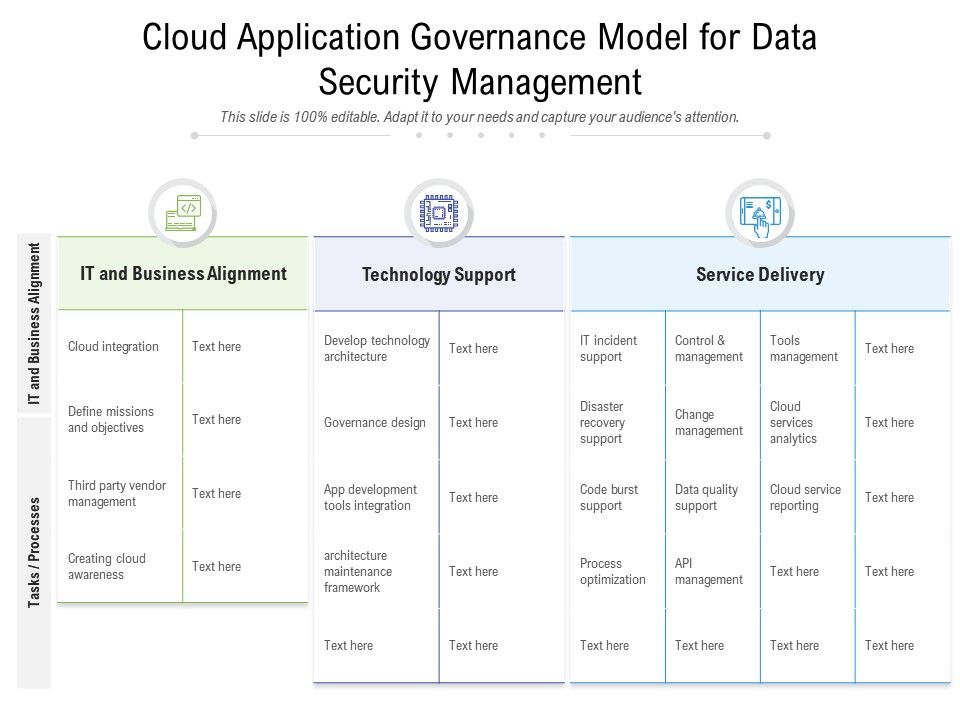
Effective communication and collaboration are the cornerstones of successful application governance. Without a clear understanding of roles, responsibilities, and shared goals, even the most meticulously designed governance framework will falter. Open communication channels and a collaborative spirit ensure that software quality initiatives are aligned with business objectives, leading to improved products and reduced risks.Stakeholder involvement is paramount, requiring a proactive approach to information sharing and conflict resolution.
A well-defined communication plan, coupled with a robust conflict resolution process, fosters a productive environment where all parties contribute to achieving high software quality.
Stakeholder Roles and Responsibilities
Successful application governance relies on the coordinated efforts of various stakeholders. Each group plays a vital role throughout the software development lifecycle (SDLC). Understanding these roles and responsibilities is crucial for effective communication and conflict resolution.
| Stakeholder | Responsibilities |
|---|---|
| Development Team | Develops, tests, and deploys software; adheres to coding standards and quality guidelines. |
| Quality Assurance (QA) Team | Performs testing and analysis to identify defects; provides feedback to the development team. |
| Operations Team | Deploys and manages the application in production; monitors performance and availability. |
| Business Stakeholders | Define requirements and acceptance criteria; provide feedback on the application’s functionality and usability. |
| Application Governance Team | Establishes and enforces governance policies; monitors compliance and addresses risks. |
| Security Team | Ensures the application is secure and protects sensitive data. |
Communication Plan for Application Governance
A comprehensive communication plan ensures that relevant information is disseminated effectively and efficiently to all stakeholders. This plan should include various communication channels tailored to the specific needs and preferences of each group.
- Regular Meetings: Scheduled meetings for different stakeholder groups (e.g., weekly development meetings, monthly governance reviews) to discuss progress, challenges, and risks.
- Project Management Tools: Utilizing platforms like Jira or Asana for task management, issue tracking, and progress updates, ensuring transparency across teams.
- Email and Instant Messaging: For quick updates, announcements, and informal communication.
- Formal Reports and Dashboards: Providing regular reports on software quality metrics, compliance status, and risk assessments.
- Knowledge Base: Creating a centralized repository for policies, procedures, and best practices related to application governance.
Conflict Resolution Process
Disagreements regarding software quality are inevitable. A formal process for resolving conflicts is essential to maintain productivity and ensure timely project completion.
- Identification and Documentation: Clearly define the nature of the conflict and document all relevant information.
- Mediation: A neutral party (e.g., a project manager or governance team member) facilitates communication and helps stakeholders find common ground.
- Negotiation: Stakeholders engage in constructive dialogue to identify mutually acceptable solutions.
- Escalation: If mediation and negotiation fail, the conflict is escalated to a higher authority (e.g., a steering committee or executive sponsor) for resolution.
- Documentation and Follow-up: The resolution is documented, and follow-up actions are implemented to prevent similar conflicts in the future.
Epilogue: Improve Software Quality With Application Governance
Ultimately, improving software quality through application governance isn’t just about ticking boxes; it’s about fostering a culture of responsibility and continuous improvement. By implementing a robust framework, embracing automation, and prioritizing clear communication, you can create a more efficient, predictable, and ultimately, more successful software development process. Ready to build better software? Let’s get started!
Question Bank
What’s the difference between application governance and project management?
Project management focuses on the execution of a specific project, while application governance provides the overarching framework and policies that guide all software development projects within an organization. Governance sets the standards, while project management applies them.
How can I get buy-in from my team for application governance?
Start by showcasing the benefits – reduced risks, improved quality, and increased efficiency. Involve the team in the process of defining and implementing the framework. Highlight successes and address concerns openly and transparently.
What if my organization is too small for application governance?
Even small organizations benefit from establishing basic governance principles. Start small, focusing on key areas like code quality and security. You can scale the framework as your organization grows.
How do I measure the success of my application governance program?
Track key metrics like defect rates, deployment frequency, security vulnerabilities, and customer satisfaction. Regularly review these metrics and adjust your approach as needed.