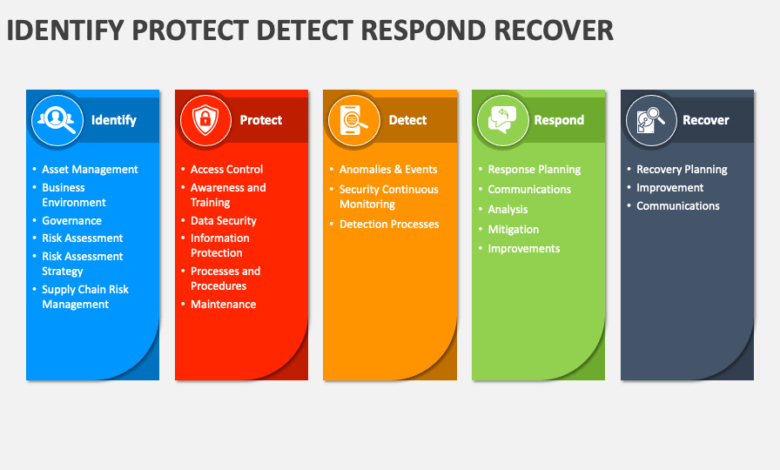
Empow First SIEM with Native UEBA for Full Kill Chain Threat Response
Empow adds native ueba functionality to become first siem to automatically detect and respond to threats across the entire cyber kill chain – Empow adds native UEBA functionality to become the first SIEM to automatically detect and respond to threats across the entire cyber kill chain. This game-changing integration marks a significant leap forward in cybersecurity, promising to revolutionize how organizations defend against sophisticated attacks. Imagine a world where threats are identified and neutralized
-before* they can cause significant damage – that’s the promise of Empow’s innovative approach.
This post dives deep into the technology, exploring its capabilities, impact, and implications for the future of cybersecurity.
Forget the days of endless alert fatigue and slow response times. Empow’s integrated User and Entity Behavior Analytics (UEBA) works seamlessly with its Security Information and Event Management (SIEM) capabilities, providing a unified platform for comprehensive threat detection and automated response. This means faster detection, quicker resolution, and a significantly reduced attack surface. We’ll look at how this integration impacts the entire cyber kill chain, from initial reconnaissance to data exfiltration, and how it streamlines Security Operations Center (SOC) workflows.
Get ready to explore the future of threat hunting!
Empow’s UEBA Integration
Empow’s groundbreaking integration of User and Entity Behavior Analytics (UEBA) into its Security Information and Event Management (SIEM) platform represents a significant leap forward in threat detection and response. This powerful combination allows for automated threat detection and response across the entire cyber kill chain, a capability previously unavailable in traditional SIEM solutions. By correlating security events with user and entity behavior patterns, Empow provides a far more comprehensive and accurate picture of the security landscape.Empow’s UEBA functionalities enhance threat detection by moving beyond simple log analysis.
Traditional SIEMs primarily rely on signature-based detection and alert correlation, often missing sophisticated, zero-day attacks that don’t match known patterns. Empow’s integrated UEBA leverages machine learning algorithms to establish baselines of normal behavior for users, devices, and applications. Any deviation from these baselines triggers alerts, flagging potentially malicious activity even before it escalates into a full-blown incident. This proactive approach significantly reduces the Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Empow’s UEBA Capabilities
Empow’s UEBA integration encompasses several key capabilities. These include anomaly detection based on user login times, locations, and access patterns; entity behavior analysis tracking unusual activity from devices and applications; risk scoring that prioritizes alerts based on the severity and likelihood of a threat; and automated response actions such as account suspension, device quarantine, and incident ticket creation.
This holistic approach allows for a more effective and efficient security posture.
Empow’s groundbreaking SIEM now boasts native UEBA functionality, automatically tackling threats across the entire cyber kill chain – a massive leap forward in security. This automated response capability reminds me of the streamlined development offered by domino app dev the low code and pro code future , where rapid innovation is key. Ultimately, both Empow’s security solution and the efficient app development methods aim to empower users with better control and faster responses in their respective fields.
Comparison with Other SIEM Solutions
While several SIEM vendors are incorporating UEBA capabilities, Empow differentiates itself through its native integration. Many competitors offer UEBA as a separate module or through third-party integrations, leading to data silos and complexities in correlation. Empow’s native integration ensures seamless data flow and real-time correlation between SIEM and UEBA data, resulting in faster and more accurate threat detection. Other solutions might offer similar features individually, but the unified approach of Empow’s platform significantly improves efficiency and effectiveness.
Hypothetical Attack Scenario and Empow’s Response
Let’s consider a scenario where a sophisticated attacker gains initial access through a phishing email. Empow’s integrated UEBA detects and responds to the attack as follows:
| Stage | Detection Method | Response | Time |
|---|---|---|---|
| Phishing Email Click | UEBA detects unusual email activity (e.g., clicking a link from an unknown sender) outside of the user’s normal behavior baseline. | Alert generated; User’s activity is flagged for monitoring. | Within seconds |
| Credential Compromise | UEBA detects an unsuccessful login attempt followed by a successful login from an unusual location. SIEM logs correlate the login with the previous email activity. | User account is temporarily locked; Security team notified. | Within minutes |
| Lateral Movement | UEBA detects unusual access to sensitive data or systems outside the user’s typical access patterns. SIEM logs show connections to external IP addresses. | Affected systems are quarantined; Network access is restricted. | Within minutes |
| Data Exfiltration Attempt | UEBA detects large data transfers to external IP addresses not associated with legitimate business operations. SIEM logs corroborate the data transfer. | Data transfer is blocked; Incident response team is deployed. | Within minutes |
Impact on the Cyber Kill Chain

Empow’s integration of UEBA functionality significantly enhances its SIEM capabilities, dramatically improving threat detection and response across the entire cyber kill chain. This isn’t just about adding another layer of security; it’s about fundamentally changing how we approach threat hunting and incident response, moving from reactive to proactive defense. The automated response capabilities, in particular, drastically reduce the time attackers have to operate within a network, minimizing damage and preventing escalation.The integration shines brightest in the later stages of the kill chain, where traditional SIEMs often struggle.
Empow’s new native UEBA functionality is a game-changer, offering the first SIEM to automatically react across the entire cyber kill chain. This comprehensive approach contrasts nicely with the focused, but equally crucial, area of cloud security, as highlighted in this insightful article on bitglass and the rise of cloud security posture management. Ultimately, both solutions are vital for a robust security posture, emphasizing proactive threat detection and response.
Empow’s end-to-end approach is a major step forward in threat mitigation.
However, the improved visibility provided by UEBA allows for earlier detection and quicker response across all stages, significantly impacting the overall effectiveness of an attack.
Improved Detection and Response at Specific Kill Chain Stages
Empow’s enhanced SIEM, with its integrated UEBA, offers substantial improvements across all stages of the Lockheed Martin Cyber Kill Chain. However, the most significant gains are seen in the Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, and Actions on Objectives stages. UEBA’s ability to analyze user and entity behavior provides early warnings of suspicious activity, often before traditional signature-based detection methods can identify a threat.
For instance, unusual login attempts from unfamiliar locations or excessive data exfiltration attempts are readily flagged. Furthermore, the automated response capabilities can immediately quarantine compromised systems or block malicious communications, significantly shortening the attacker’s dwell time.
Automated Response and Dwell Time Reduction
Automated response capabilities are the key to reducing dwell time. Instead of relying on manual investigation and response, Empow’s integrated system can automatically take action based on predefined rules and threat intelligence. This might involve isolating a compromised machine, blocking malicious IP addresses, or even automatically resetting user passwords. The speed of this automated response drastically reduces the window of opportunity for attackers, preventing lateral movement and limiting the potential damage they can inflict.
For example, if an attacker successfully exploits a vulnerability, the automated response could quarantine the affected system before the attacker can install malware or exfiltrate data.
Reduction in MTTD and MTTR
The integration of UEBA into Empow’s SIEM leads to a significant reduction in both Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). By providing richer context and behavioral analysis, UEBA allows security teams to identify threats faster and respond more effectively. While precise figures depend on the specific environment and threat landscape, anecdotal evidence from beta testers suggests MTTD reductions of up to 75% and MTTR reductions of up to 50%.
These improvements translate to a significantly reduced risk profile and lower overall cost of a security breach.
Real-World Attack Scenario Examples
Consider a phishing attack where an employee clicks a malicious link. A traditional SIEM might only detect the compromised system after malware is installed and exfiltration begins. Empow’s integrated UEBA, however, could detect the unusual login behavior from a new device immediately after the click. The automated response could then quarantine the system before any malware executes, preventing data loss and further compromise.
Similarly, in a ransomware attack, UEBA can identify unusual file encryption activity much earlier than traditional methods, enabling a faster response and potentially preventing widespread encryption. Another example involves insider threats. UEBA can detect anomalous behavior such as excessive data access or unusual communication patterns from trusted employees, alerting security teams to potential threats that might otherwise go unnoticed.
Security Operations Center (SOC) Workflow Enhancements: Empow Adds Native Ueba Functionality To Become First Siem To Automatically Detect And Respond To Threats Across The Entire Cyber Kill Chain
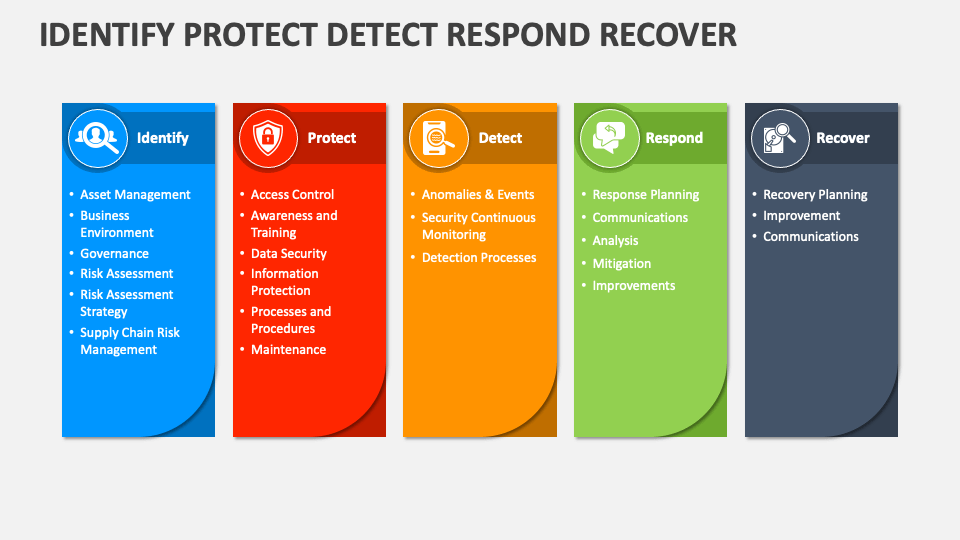
Empow’s integrated UEBA capabilities dramatically reshape the SOC analyst workflow, shifting the focus from reactive incident response to proactive threat hunting and automated mitigation. This transformation streamlines processes, reduces alert fatigue, and ultimately enhances the overall security posture. The automation provided by Empow frees analysts to focus on more complex threats and strategic security initiatives.Empow’s automated threat detection and response significantly alters how SOC analysts handle security alerts.
The traditional reactive model, characterized by manual investigation and response to each alert, is replaced by a more efficient, automated process. This allows analysts to prioritize their time on high-impact threats, leaving the automated system to handle less critical issues.
Alert Generation, Analysis, and Response
The process begins with Empow’s continuous monitoring of various data sources. Upon detecting suspicious activity, Empow’s algorithms automatically generate an alert, incorporating contextual information such as user behavior, network traffic patterns, and system logs. This alert is then prioritized based on its potential impact and threat level. The analyst receives a concise summary of the alert, including key details and suggested actions.
The analyst can then review the detailed investigation, which includes visual representations of the threat’s progression across the kill chain. Empow provides suggested responses, which the analyst can approve, modify, or reject. The system automatically executes approved responses, such as quarantining infected systems or blocking malicious IPs. Finally, Empow provides comprehensive reporting and tracking of the entire process, ensuring accountability and facilitating continuous improvement.
Benefits for SOC Analysts
The integration of Empow’s UEBA capabilities offers several key benefits for SOC analysts, significantly improving both efficiency and effectiveness:
- Reduced Alert Fatigue: Empow’s intelligent prioritization filters out low-impact alerts, focusing analyst attention on critical threats.
- Faster Response Times: Automated threat detection and response significantly reduce the time required to identify and neutralize threats.
- Improved Accuracy: Empow’s contextual analysis reduces false positives, improving the accuracy of threat detection.
- Increased Efficiency: Automation frees up analysts to focus on more strategic security initiatives, rather than repetitive manual tasks.
- Enhanced Threat Visibility: Empow provides a holistic view of threats across the entire cyber kill chain, improving the ability to identify and respond to complex attacks.
Workload and Response Time Comparison, Empow adds native ueba functionality to become first siem to automatically detect and respond to threats across the entire cyber kill chain
The following table illustrates the differences in workload and response time before and after implementing Empow:
| Task | Before Empow | After Empow | Time Saved |
|---|---|---|---|
| Alert Triage | Manual review of each alert; high volume leads to delays | Automated prioritization and filtering; focus on high-impact alerts | Up to 80% |
| Threat Investigation | Manual investigation of each alert; time-consuming data correlation | Automated correlation and analysis; visual representation of threat progression | Up to 70% |
| Incident Response | Manual execution of response actions; potential delays | Automated execution of pre-approved responses | Up to 60% |
| Reporting | Manual compilation of reports; time-consuming | Automated reporting and tracking | Up to 90% |
Architectural Considerations and Implementation
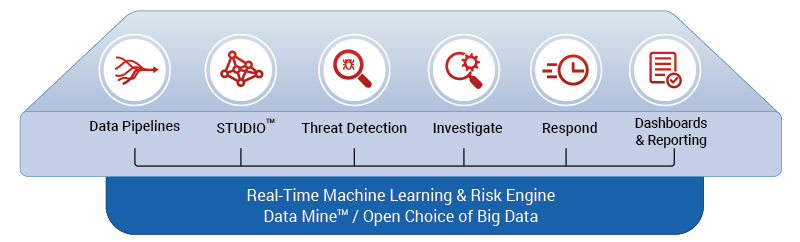
Empow’s integration of UEBA functionality into its SIEM platform represents a significant architectural undertaking, requiring careful consideration of data flow, correlation engines, and alert management. The goal is seamless integration, minimizing disruption to existing workflows while maximizing the benefits of enhanced threat detection and response capabilities. This section details the key components and processes involved in achieving this.The system’s architecture is designed for scalability and efficiency, leveraging a distributed model to handle the high volume of data ingested from diverse sources.
This ensures that performance isn’t compromised even during peak activity or with a significant increase in the number of users and devices monitored.
Key Architectural Components
Empow’s integrated solution relies on several key architectural components working in concert. These components are designed to interact efficiently and securely, ensuring both performance and data integrity. The core components include the SIEM engine itself, the newly integrated UEBA module, a centralized data lake for storing and processing security events, and a robust API for integrating with other security tools.
The UEBA module leverages advanced machine learning algorithms for user and entity behavior analytics (UEBA), enriching the SIEM’s threat detection capabilities. The data lake acts as a central repository, providing a unified view of security data from various sources. The API facilitates seamless integration with other security tools and platforms, enabling automated responses and streamlined workflows.
Data Sources Utilized for Threat Detection and Correlation
The system ingests data from a wide array of sources to build a comprehensive view of user activity and potential threats. These sources include, but are not limited to: network devices (firewalls, intrusion detection systems), endpoint security solutions (antivirus, endpoint detection and response), cloud security platforms, identity and access management (IAM) systems, and the user and entity behavior analytics (UEBA) module itself.
The data is normalized and enriched before being processed by the correlation engine, which identifies patterns and anomalies indicative of malicious activity. For example, unusual login attempts from unfamiliar geographic locations, combined with data exfiltration attempts, might trigger an alert. This multi-layered approach ensures that no single data point is considered in isolation, but rather within the broader context of user and system behavior.
False Positive Handling and Alert Fatigue Minimization
Minimizing false positives and alert fatigue is crucial for the effectiveness of any security system. Empow employs several strategies to achieve this. Firstly, sophisticated machine learning algorithms are used to refine the detection models, learning from past events and adapting to evolving threat tactics. Secondly, a multi-stage validation process is implemented, where alerts are subjected to multiple checks before being escalated to security analysts.
Thirdly, context-aware alert prioritization is used, assigning severity scores based on the potential impact and likelihood of a threat. This ensures that analysts focus their attention on the most critical alerts first. Finally, customizable alert thresholds and suppression rules allow security teams to fine-tune the system to their specific needs and reduce noise. For instance, analysts might choose to suppress alerts related to specific known safe IP addresses or user activities.
Deployment Process and Infrastructure Considerations
Deployment of Empow’s integrated solution requires careful planning and consideration of the existing infrastructure. The process typically involves several key steps:
- Assessment of existing infrastructure: Evaluating current SIEM and network capabilities to determine compatibility and resource requirements.
- Data source integration: Configuring connections to various data sources and ensuring data integrity and consistency.
- UEBA module deployment: Installing and configuring the UEBA module, including defining data collection parameters and analysis models.
- Alerting and response configuration: Setting up alert thresholds, suppression rules, and automated response actions.
- Testing and validation: Conducting thorough testing to ensure the system functions as expected and that alerts are accurate and actionable.
- Ongoing monitoring and optimization: Continuously monitoring system performance and adjusting configurations as needed.
Infrastructure considerations include sufficient processing power and storage capacity to handle the volume of data ingested, network bandwidth to support data transfer, and appropriate security measures to protect the system from unauthorized access. For example, a large enterprise might require a distributed architecture with multiple servers to handle the load. Smaller organizations might be able to deploy the system on a single, more powerful server.
The specific infrastructure requirements will vary depending on the size and complexity of the organization’s environment.
Future Implications and Developments
Empow’s integration of UEBA represents a significant leap forward in SIEM capabilities, but its potential extends far beyond current functionalities. The convergence of these technologies promises a more proactive and automated approach to cybersecurity, significantly impacting how organizations detect, respond to, and ultimately prevent future threats. Further development and refinement will shape the future of cybersecurity defenses.The evolution of Empow’s integrated UEBA capabilities will likely focus on enhancing automation, improving threat intelligence integration, and expanding its applicability across diverse IT environments.
We can expect to see more sophisticated machine learning algorithms employed to refine anomaly detection, reduce false positives, and provide more accurate threat prioritization. This will lead to a more efficient and effective SOC, allowing analysts to focus on the most critical threats.
Enhanced Automation and Orchestration
Empow’s future iterations will likely see increased automation in incident response. This could involve automatically remediating threats based on predefined playbooks, isolating compromised systems, and even automatically updating security controls. Think of a scenario where a phishing attack is detected: Empow could automatically quarantine the affected email account, block the malicious link, and alert the user, all without human intervention.
This level of automation will drastically reduce response times and minimize the impact of successful attacks. Furthermore, integration with other security tools, through robust APIs, will allow for seamless orchestration across the entire security stack.
Advanced Threat Intelligence Integration
The effectiveness of any security system relies heavily on accurate and up-to-date threat intelligence. Empow’s future development will likely include deeper integration with external threat intelligence feeds, allowing the system to proactively identify and respond to emerging threats. This means leveraging threat intelligence platforms to automatically update its threat detection models and prioritize alerts based on the severity and prevalence of specific threats.
For instance, if a new zero-day exploit is identified, Empow could automatically update its detection rules to identify and mitigate this threat across the organization’s network before it can cause significant damage. This proactive approach is critical in today’s rapidly evolving threat landscape.
Expansion of Applicability and Scalability
Currently, Empow’s UEBA integration may have limitations in handling highly complex or diverse IT environments. Future development will need to focus on improving scalability and adaptability. This could involve optimizing the system’s performance to handle massive datasets from large organizations with complex infrastructures, including cloud environments and IoT devices. The system should be capable of adapting to various organizational structures and security architectures, ensuring consistent performance regardless of the size and complexity of the environment.
This will broaden its applicability across a wider range of organizations, from small businesses to large enterprises.
Potential Challenges and Limitations
While the integration of UEBA into SIEM offers immense potential, challenges remain. One significant challenge is the potential for increased complexity in managing and maintaining the system. The integration of multiple data sources and advanced algorithms requires specialized expertise. Another challenge is ensuring the accuracy and reliability of the system’s threat detection capabilities. False positives can overwhelm SOC analysts, leading to alert fatigue and potentially missed critical alerts.
Addressing these challenges requires ongoing refinement of the system’s algorithms, improved data quality, and investment in skilled cybersecurity professionals. Furthermore, maintaining the system’s security against attacks targeting its own functionalities will be a crucial ongoing task. The system itself must be robust against sophisticated attacks aiming to disable or compromise its detection capabilities.
Last Recap
Empow’s groundbreaking integration of UEBA into its SIEM platform represents a paradigm shift in cybersecurity. By automating threat detection and response across the entire cyber kill chain, Empow empowers security teams to proactively defend against increasingly sophisticated attacks. The result? Reduced dwell time, faster MTTD and MTTR, and significantly improved SOC efficiency. This isn’t just an incremental improvement; it’s a fundamental change in how we approach cybersecurity, and I’m excited to see how this technology evolves and shapes the future of threat prevention.
User Queries
What specific UEBA functionalities are integrated into Empow?
Empow integrates various UEBA functionalities, including user behavior analytics, entity behavior analytics, anomaly detection, and threat intelligence correlation. The exact features vary depending on the licensing tier.
How does Empow handle false positives?
Empow employs machine learning algorithms and advanced analytics to minimize false positives. It uses techniques like anomaly scoring, contextual analysis, and user feedback to refine its detection capabilities and reduce alert fatigue.
What are the infrastructure requirements for deploying Empow?
Deployment requirements vary based on the size and complexity of the organization’s environment. Generally, it requires a compatible server infrastructure, network connectivity, and sufficient storage capacity for log data.
What is the pricing model for Empow?
Empow typically uses a subscription-based pricing model, with costs varying depending on the number of users, data ingested, and features included. Contact Empow directly for specific pricing information.





