Endpoint Detection Response Guide A Practical Overview
Endpoint detection response guide – Endpoint Detection and Response (EDR) Guide: This deep dive isn’t just another tech manual; it’s your passport to understanding how to proactively defend your digital assets. We’ll unravel the mysteries of EDR, from its core functionalities and the benefits it offers to mastering its deployment and leveraging its powerful threat detection capabilities. Get ready to navigate the world of advanced threat hunting and incident response like a pro!
We’ll cover everything from choosing the right EDR solution (cloud-based, on-premises, or a hybrid approach) to integrating it seamlessly with your existing security infrastructure. Learn how to configure alerts, analyze data, and even create compelling reports to showcase your improved security posture. Think of this as your ultimate toolkit for building a robust and resilient security defense.
Introduction to Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) has become a critical component of modern cybersecurity strategies. It’s more than just antivirus; it’s a proactive approach to threat hunting and incident response, providing organizations with a deep understanding of their endpoint security posture. This introduction will delve into the core functionalities, benefits, and various types of EDR solutions available.EDR solutions go beyond traditional antivirus by continuously monitoring endpoints for malicious activity, analyzing system events for suspicious behavior, and providing the tools to respond to threats in real-time.
This allows security teams to detect and remediate threats that might otherwise go unnoticed by traditional security measures. Think of it as a highly sophisticated security guard constantly patrolling your digital environment.
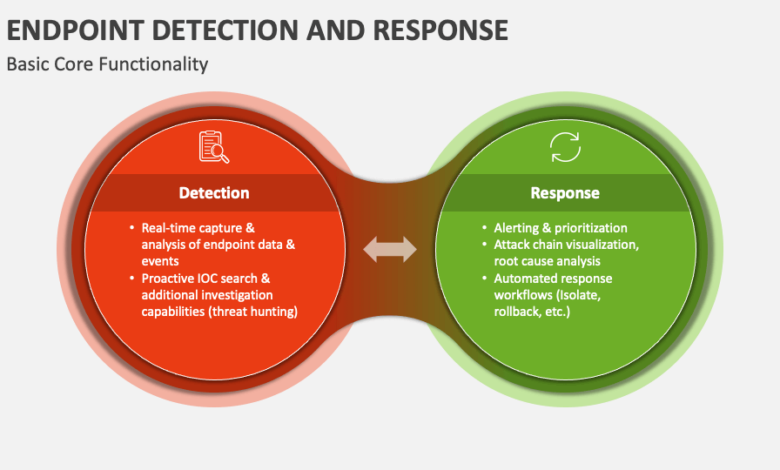
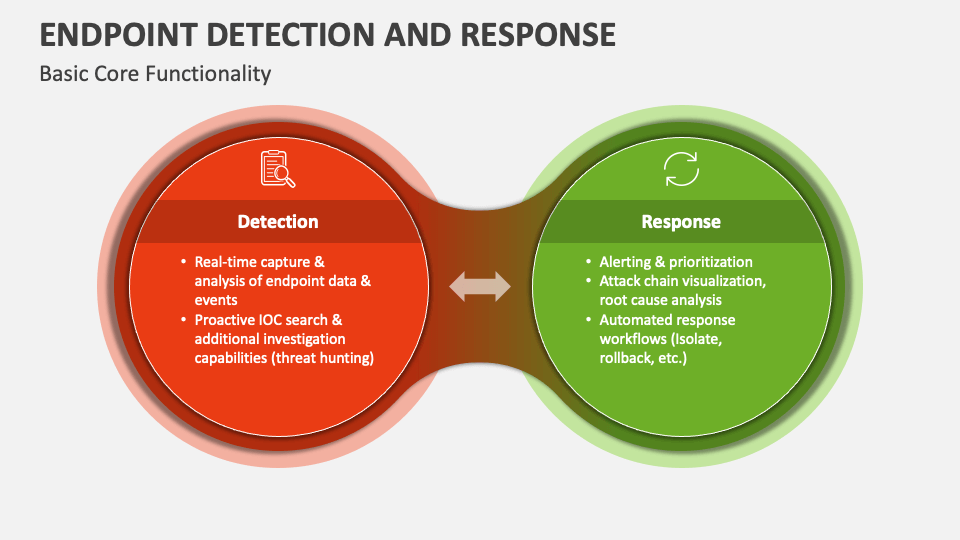
EDR Core Functionalities
EDR solutions offer a range of core functionalities designed to provide comprehensive endpoint security. These typically include real-time monitoring of endpoint activity, threat detection using advanced analytics, automated incident response capabilities, and detailed forensic investigation tools. The ability to quickly identify, investigate, and respond to threats is crucial in minimizing the impact of a security breach. For example, an EDR system might detect unusual network connections from a compromised machine, automatically quarantine the affected system, and provide investigators with a detailed timeline of the attack.
Benefits of Implementing an EDR Solution
Implementing an EDR solution offers numerous benefits, significantly enhancing an organization’s security posture. Improved threat detection, faster incident response times, and reduced dwell time of attackers are key advantages. EDR systems often provide detailed forensic data, enabling security teams to thoroughly investigate security incidents and understand the techniques used by attackers. This information can be invaluable in preventing future attacks and improving overall security practices.
Consider the scenario of a ransomware attack; an EDR system can help pinpoint the initial infection point, contain the spread, and assist in data recovery, significantly reducing the overall damage.
Types of EDR Solutions
EDR solutions are available in various deployment models, each with its own advantages and disadvantages. Cloud-based EDR solutions are typically easier to manage and deploy, often offering scalability and centralized management capabilities. On-premises solutions provide greater control over data and security policies, but often require more significant IT infrastructure and management resources. Hybrid approaches combine elements of both, allowing organizations to tailor their deployment to meet specific needs.
The choice depends heavily on an organization’s infrastructure, technical expertise, and security requirements.
A Brief History of EDR and Its Evolution
EDR’s evolution is closely tied to the increasing sophistication of cyberattacks. Initially, EDR solutions focused primarily on endpoint protection, largely building upon the capabilities of traditional antivirus software. However, as cyberattacks became more advanced and stealthy, EDR evolved to incorporate advanced analytics, threat hunting capabilities, and automated response features. The rise of cloud computing and the increasing reliance on remote work have further accelerated the adoption and evolution of EDR, driving the need for solutions that can effectively protect endpoints across diverse environments.
This continuous evolution reflects the ongoing arms race between attackers and defenders in the cybersecurity landscape.
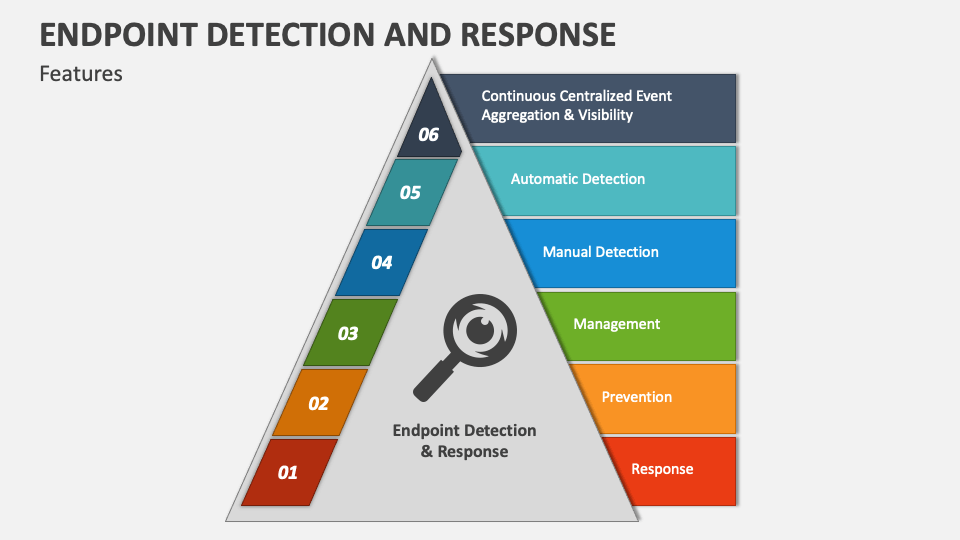
Key Components of an EDR System
A robust Endpoint Detection and Response (EDR) system isn’t a single piece of software; it’s a sophisticated ecosystem of interacting components working together to protect your endpoints. Understanding these components and how they function is crucial to effectively leveraging EDR’s capabilities. Think of it like a well-oiled machine – each part plays a vital role, and a failure in one area can impact the entire system’s effectiveness.The core components of a typical EDR system work in concert to provide comprehensive endpoint security.
These components include the agent, the sensor, and the console. Their interactions allow for real-time monitoring, threat detection, and incident response. Different vendors may implement these components slightly differently, leading to variations in architecture.
EDR Agent
The EDR agent is the software installed directly on the endpoint device (computer, server, mobile device). It’s the eyes and ears on the ground, constantly monitoring system activity for suspicious behavior. This involves collecting various telemetry data, including process execution details, network connections, file system changes, and registry modifications. The agent’s capabilities often determine the granularity and depth of threat detection.
A sophisticated agent might employ techniques like behavioral analysis to identify anomalies that signature-based antivirus solutions might miss. For example, it might detect unusual process creation patterns indicative of malware execution even if the malware itself is unknown. The agent then transmits this data to the EDR console for analysis and response.
EDR Sensor
While often used interchangeably with the agent, the sensor represents a more specialized component focused on specific data collection tasks. Sensors might focus on network traffic analysis, providing deep packet inspection to detect malicious communications. Other sensors might concentrate on specific applications or data types, enabling enhanced monitoring and threat detection within those contexts. For instance, a database sensor might monitor queries and access patterns to detect unauthorized data access attempts.
The sensor’s output feeds into the agent, which then aggregates and forwards the information to the console. This modular approach allows for customization and scalability based on specific organizational needs.
EDR Console
The EDR console is the central management interface for the entire system. Security analysts use the console to monitor alerts, investigate suspicious activity, and orchestrate incident response actions. The console aggregates data from all deployed agents and sensors, providing a centralized view of the security posture across all endpoints. Sophisticated consoles provide advanced features like threat hunting, automated response capabilities (e.g., isolating infected machines), and reporting/analytics dashboards.
Think of it as the control center, providing the overview and the tools necessary to effectively manage and respond to security threats.
EDR Architectures
Different EDR vendors employ varying architectures, influencing their performance, scalability, and overall capabilities. Some utilize a cloud-based architecture, where all data is processed and analyzed in the vendor’s cloud infrastructure. This offers centralized management and scalability but may raise concerns about data privacy and latency. Others opt for on-premises or hybrid deployments, offering more control over data but requiring more significant internal infrastructure and expertise.
The choice of architecture depends heavily on an organization’s specific security requirements, infrastructure capabilities, and risk tolerance.
Diagram of EDR Component Interaction
Imagine a simple diagram: Three boxes representing the Agent, Sensor, and Console. Arrows point from the Agent and Sensor to the Console, indicating data flow. A smaller box labeled “Endpoint” connects to the Agent, representing the monitored device. Another set of arrows could represent the Console sending commands back to the Agent, such as isolating a compromised machine or initiating a malware removal process.
This visual representation simplifies the interaction between the core components. The key takeaway is the continuous flow of information from the endpoint to the console, enabling real-time threat detection and response.
EDR Deployment and Configuration

Deploying and configuring an Endpoint Detection and Response (EDR) system is a crucial step in bolstering your organization’s cybersecurity posture. A well-implemented EDR solution provides real-time visibility into endpoint activity, enabling faster threat detection and response. However, the process requires careful planning and execution to ensure optimal performance and effectiveness across diverse environments. This section details best practices, common challenges, and mitigation strategies for a successful EDR deployment.Successfully deploying an EDR solution across a diverse environment requires a phased approach and careful consideration of various factors.
This includes understanding your existing infrastructure, the heterogeneity of your endpoints (operating systems, hardware, software), and the specific security needs of your organization. A poorly planned deployment can lead to integration issues, performance bottlenecks, and ultimately, reduced effectiveness of the EDR system.
Best Practices for EDR Deployment in Diverse Environments
Prioritizing a phased rollout allows for thorough testing and refinement of the deployment strategy. Begin with a pilot program in a smaller, less critical environment to identify and resolve any unforeseen issues before expanding to the entire organization. This minimizes disruption and allows for iterative improvements to the deployment process. Comprehensive documentation of the deployment process, including configurations and troubleshooting steps, is also critical for future maintenance and updates.
Regular testing and validation of the EDR system’s functionality are essential to ensure ongoing effectiveness. Finally, integrating the EDR solution with existing security tools and workflows streamlines incident response and enhances overall security posture.
Configuring an EDR System to Meet Specific Security Needs
EDR system configuration is highly dependent on your organization’s specific security requirements and risk profile. Consider factors like the types of threats you’re most concerned about (e.g., malware, ransomware, insider threats), the level of detail required in event logs, and the desired level of automation in threat response. This often involves customizing detection rules, defining alert thresholds, and configuring automated responses to specific events.
For example, you might configure the system to automatically quarantine a file exhibiting malicious behavior or to block network connections to suspicious IP addresses. Regularly reviewing and adjusting these configurations based on evolving threat landscapes and organizational needs is essential for maintaining optimal protection.
Challenges During EDR Deployment and Mitigation Strategies
One common challenge is ensuring compatibility across diverse endpoint environments. Different operating systems, software versions, and hardware configurations can lead to compatibility issues and require careful testing and configuration. Mitigation strategies include thorough pre-deployment testing, utilizing virtualization for testing different configurations, and implementing robust change management processes. Another challenge is managing the volume of data generated by an EDR system.
This can strain resources and require careful planning for data storage and analysis. Mitigation strategies include implementing data retention policies, using data aggregation and summarization techniques, and leveraging cloud-based EDR solutions for scalable data management. Finally, ensuring sufficient staffing and training for EDR management is crucial. This requires investment in skilled personnel and ongoing training to effectively manage and interpret the data generated by the system.
Step-by-Step Guide for Configuring Alerts and Notifications
First, identify critical events that warrant immediate attention. This could include detection of known malware, suspicious process executions, or unauthorized access attempts. Next, define alert thresholds and severity levels for each event. For instance, a critical alert might be triggered by the detection of ransomware, while a less critical alert might be triggered by unusual login attempts. Then, configure notification methods, such as email, SMS, or integration with a Security Information and Event Management (SIEM) system.
Specify recipients for each alert based on their roles and responsibilities. Test the alert configuration thoroughly to ensure that notifications are delivered promptly and accurately. Finally, regularly review and adjust alert configurations based on your organization’s evolving security needs and the performance of the EDR system. This iterative process ensures that the alert system remains effective in identifying and responding to threats.
Threat Detection Capabilities of EDR
Endpoint Detection and Response (EDR) solutions are powerful tools in the fight against modern cyber threats. Their effectiveness hinges on a sophisticated suite of threat detection techniques that go beyond simple signature-based antivirus. By combining various approaches, EDR systems provide a multi-layered defense capable of identifying and responding to even the most advanced attacks.EDR systems leverage a variety of methods to detect malicious activity.
These techniques fall broadly into the categories of signature-based detection, heuristic analysis, behavioral analysis, and machine learning. The interplay between these techniques allows for a comprehensive approach, significantly improving detection rates and reducing the time to response.
Signature-Based Detection
Signature-based detection relies on identifying known malicious code through the use of signatures – unique patterns of bytes or code sequences characteristic of specific malware. While effective against known threats, this method struggles with zero-day attacks and polymorphic malware that constantly changes its signature. EDR systems often incorporate signature-based detection as a foundational layer, but they rely heavily on more advanced techniques for comprehensive threat hunting.
Heuristic Analysis
Heuristic analysis examines the behavior of a program to identify potentially malicious activities. This method looks for suspicious actions, such as attempts to modify system files, create network connections to known malicious servers, or access sensitive data without authorization. While less reliant on known signatures, heuristic analysis can still generate false positives if the heuristics are not carefully tuned.
Behavioral Analysis
Behavioral analysis goes beyond simple heuristics by building a baseline of “normal” system behavior. It then monitors for deviations from this baseline, flagging any unusual activity as potentially malicious. This approach is particularly effective in detecting advanced persistent threats (APTs) and other stealthy attacks that may evade signature-based detection. For example, an EDR system might flag unusual file access patterns or network connections as suspicious, even if the involved files or servers are not known to be malicious.
The system learns what’s normal for a specific endpoint and alerts when significant departures occur.
Machine Learning
Machine learning (ML) algorithms play an increasingly crucial role in modern EDR systems. These algorithms can analyze vast amounts of data from various sources to identify patterns and anomalies indicative of malicious activity. ML models can be trained on large datasets of known malicious and benign behavior, allowing them to identify subtle indicators of compromise that might be missed by other methods.
This enables the detection of novel threats and zero-day exploits that traditional signature-based approaches cannot handle.
Malware, Ransomware, and Advanced Threat Detection, Endpoint detection response guide
EDR systems employ a combination of the techniques described above to detect various types of threats. Malware detection often relies on a combination of signature-based detection, heuristic analysis, and behavioral analysis. Ransomware detection, however, often leverages behavioral analysis and machine learning to identify unusual encryption activity or attempts to exfiltrate data. Advanced threats, such as APTs, often require a more sophisticated approach, utilizing machine learning to identify subtle indicators of compromise that might be missed by other methods.
Comparison of Detection Methods
The effectiveness of different detection methods varies depending on the type of threat. Signature-based detection is effective against known threats but ineffective against zero-day exploits. Heuristic analysis and behavioral analysis are more effective against unknown threats but can produce false positives. Machine learning offers a powerful approach to detecting both known and unknown threats, but requires significant amounts of data for training and can be computationally expensive.
EDR Detection Methods by Threat Type
| Threat Type | Signature-Based Detection | Heuristic Analysis | Behavioral Analysis | Machine Learning |
|---|---|---|---|---|
| Malware (known) | High | Medium | Medium | Medium |
| Malware (unknown) | Low | Medium | High | High |
| Ransomware | Low | Medium | High | High |
| APT | Low | Low | High | High |
Incident Response with EDR
Endpoint Detection and Response (EDR) solutions are invaluable during security incidents, providing the crucial visibility and context needed for swift and effective response. By leveraging the rich data collected by EDR, security teams can significantly reduce the impact of breaches and improve overall security posture. This section details how EDR facilitates the various stages of incident response.EDR assists in all phases of incident response, from initial detection to full recovery.
Its ability to provide comprehensive visibility into endpoint activity allows for rapid identification of compromised systems, the extent of the breach, and the attacker’s tactics, techniques, and procedures (TTPs). This detailed insight streamlines the entire process, minimizing downtime and damage.
Containment Strategies Using EDR
Effective containment involves isolating infected systems to prevent further lateral movement and data exfiltration. EDR facilitates this by providing the capability to remotely shut down processes, block network connections, and quarantine affected endpoints. For instance, if EDR detects malicious code attempting to access sensitive data, it can immediately block the connection, preventing data loss. This immediate response is crucial in limiting the damage caused by a security incident.
Another example involves isolating a workstation exhibiting suspicious network activity, preventing further spread of malware within the network. The granular control offered by EDR allows for precise containment strategies tailored to the specific threat.
Eradication Techniques with EDR
Once contained, the next step is eradication – completely removing the threat from the affected system. EDR helps in this phase by providing detailed information about the malware, including its location, behavior, and associated files. This information allows security teams to develop targeted removal strategies. For example, EDR can pinpoint the registry keys, files, and processes associated with malware, allowing for precise removal without affecting the system’s functionality.
Furthermore, EDR can assist in the verification of complete malware removal by monitoring system activity for any residual malicious behavior.
Recovery Procedures with EDR
The recovery phase involves restoring affected systems to their pre-incident state. EDR can aid in this process by providing a historical record of system activity, enabling the rollback of changes made by the attacker. This could involve restoring files from backups or reverting system settings to a known good state. EDR’s forensic capabilities are crucial here, allowing investigators to analyze the timeline of events and identify any data that may have been compromised, assisting in the prioritization of recovery efforts.
By reviewing EDR logs, the team can verify the effectiveness of the eradication process and ensure no malicious components remain.
Root Cause Analysis Using EDR
Understanding the root cause of a security breach is vital for preventing future incidents. EDR’s detailed logs and event correlation capabilities are crucial for conducting thorough root cause analysis. For example, if a phishing email led to a successful compromise, EDR logs can show the exact time the email was opened, the malicious link clicked, and the subsequent actions taken by the malware.
This detailed timeline allows security teams to pinpoint vulnerabilities in their security posture, such as insufficient employee training or outdated security software. By meticulously tracing the attacker’s actions, the organization can implement corrective measures to strengthen its defenses and prevent similar incidents in the future. This analysis might reveal the need for improved endpoint security controls, stronger network segmentation, or enhanced security awareness training.
Integration with Other Security Tools
EDR systems are incredibly powerful on their own, but their effectiveness is significantly amplified when integrated with other security tools within your organization’s overall security architecture. This integration creates a synergistic effect, enhancing threat detection, accelerating incident response, and providing a more comprehensive view of your security posture. By sharing data and automating workflows, these integrated systems work together more efficiently than they could in isolation.Integrating EDR with other security tools creates a unified security ecosystem.
This holistic approach enables faster detection and response to threats, reducing the time it takes to identify and neutralize malicious activity. Moreover, the automated data sharing reduces the manual effort required by security analysts, allowing them to focus on more complex investigations and proactive security measures.
Data Sharing and Enhanced Threat Detection
The key benefit of integrating EDR with other security tools lies in the enhanced data sharing capabilities. EDR provides rich endpoint-level telemetry, including process activity, network connections, and file system changes. When this data is correlated with information from other security tools like Security Information and Event Management (SIEM) systems, a far more complete picture of a potential threat emerges.
For instance, an unusual process execution detected by EDR can be correlated with suspicious network activity identified by a network intrusion detection system (NIDS), and further contextualized with user activity logs from a SIEM. This correlation helps analysts to quickly identify malicious behavior that might otherwise go unnoticed. This combined view allows for quicker identification of sophisticated attacks that utilize multiple attack vectors.
For example, a ransomware attack might initially manifest as unusual file access patterns on endpoints (EDR data), followed by data exfiltration via the network (NIDS data), and finally culminating in unusual login attempts (SIEM data). This comprehensive view is crucial for effective incident response.
Integration Methods and Effectiveness
Several methods facilitate integration between EDR and other security tools. Direct API integrations offer the most robust and flexible approach, allowing for real-time data exchange and automated workflows. This method enables seamless sharing of alerts and data between systems. For example, an EDR system can automatically forward alerts about suspicious processes to a SIEM, triggering automated investigations and response actions.
Alternatively, less tightly coupled methods like Syslog or file-based data sharing can be used, but they may lack the speed and efficiency of direct API integrations. The effectiveness of each method depends on factors like the specific tools involved, the desired level of integration, and the organization’s technical capabilities. A well-planned integration strategy should consider factors such as data volume, latency requirements, and security implications.
For example, organizations with large datasets and strict latency requirements might benefit from optimized, direct API integrations, while smaller organizations might find file-based sharing sufficient.
Potential Integration Points
Effective integration extends the capabilities of both EDR and other security tools. Consider these potential integration points:
- SIEM (Security Information and Event Management): EDR data enriches SIEM logs, providing detailed context for security events. This improves threat detection accuracy and speeds up incident response.
- SOAR (Security Orchestration, Automation, and Response): EDR alerts can trigger automated playbooks in SOAR, streamlining incident response processes. This automation reduces manual effort and improves response time.
- CASB (Cloud Access Security Broker): Integrating EDR with CASB provides visibility into user activity on cloud applications, enabling better detection of data breaches and insider threats.
- Endpoint Protection Platforms (EPP): Combining EDR with EPP offers a comprehensive endpoint security solution. EDR provides advanced threat detection, while EPP offers preventative measures.
- Vulnerability Management Systems: Integrating EDR with vulnerability management systems helps prioritize remediation efforts by identifying endpoints with known vulnerabilities that have been actively exploited.
- Network Intrusion Detection/Prevention Systems (IDS/IPS): Correlating EDR data with network traffic analysis from IDS/IPS improves threat detection and provides a complete view of attacks.
- Threat Intelligence Platforms: Integrating EDR with threat intelligence platforms enables faster identification of known malicious activities and facilitates proactive threat hunting.
EDR Management and Monitoring
Effective EDR management and monitoring are crucial for maximizing its security benefits. A well-managed EDR system provides real-time visibility into endpoint activity, enabling proactive threat hunting and rapid incident response. Neglecting this aspect can significantly diminish the system’s effectiveness, leaving your organization vulnerable to cyberattacks. Regular maintenance and proactive monitoring are key to ensuring your EDR solution remains a robust part of your overall security posture.
Best Practices for Managing and Monitoring an EDR System
Effective EDR management involves a multi-faceted approach encompassing proactive monitoring, regular updates, performance optimization, and incident response planning. Centralized management consoles allow for streamlined oversight of all endpoints, simplifying tasks like policy deployment and alert management. Establishing clear roles and responsibilities within the security team is also vital for efficient management and incident response. Regularly reviewing system logs and alerts allows for the identification of potential issues before they escalate into major security incidents.
Proactive threat hunting, utilizing the EDR’s capabilities to search for suspicious activity beyond immediate alerts, adds another layer of protection.
The Importance of Regular Updates and Patches
EDR systems, like any software, require regular updates and patches to address vulnerabilities and enhance their capabilities. These updates often include new threat signatures, improved detection algorithms, and critical bug fixes. Failing to apply updates promptly exposes your organization to known vulnerabilities, potentially allowing attackers to bypass the EDR’s protections. A robust patch management process, including automated update deployment and rigorous testing in a staging environment before rollout to production, is essential.
This process should also include a system for tracking patch deployment across all endpoints to ensure complete coverage. Consider using a vulnerability scanner integrated with your EDR to identify and prioritize patches for known exploits.
Strategies for Optimizing EDR Performance and Resource Utilization
Optimizing EDR performance is vital to prevent resource exhaustion and maintain system stability. Excessive resource consumption can negatively impact endpoint performance, leading to reduced productivity. Strategies for optimization include regularly reviewing and refining EDR policies to minimize unnecessary data collection and processing. Careful consideration of the data types collected and the frequency of data transmission can significantly reduce the system’s footprint.
Implementing efficient data retention policies can also help to minimize storage requirements. Regularly analyzing EDR performance metrics, such as CPU and memory utilization, can pinpoint areas for improvement. Consider load balancing techniques to distribute the processing workload across multiple servers in a large-scale deployment. Regularly assess the need for each EDR agent and consider disabling it on endpoints where it is not critical for security.
Regular EDR System Maintenance Checklist
A well-defined maintenance checklist ensures consistent upkeep of the EDR system. This checklist should be integrated into a larger security operations plan.
- Daily Tasks: Review of critical alerts and system logs for any unusual activity.
- Weekly Tasks: Verification of EDR agent status on all endpoints, review of EDR system performance metrics, and investigation of any unresolved alerts.
- Monthly Tasks: Application of security updates and patches, review and refinement of EDR policies, and execution of scheduled scans for malware and vulnerabilities.
- Quarterly Tasks: Conduct a full system audit of the EDR infrastructure, including its configuration and performance. Review and update incident response plans. Perform a comprehensive threat hunt to identify any latent threats.
- Annual Tasks: Conduct a complete security assessment of the EDR system, review and update the EDR system’s overall security strategy, and consider upgrading to the latest version of the software.
EDR Reporting and Analytics: Endpoint Detection Response Guide
Effective endpoint detection and response (EDR) isn’t just about detecting threats; it’s about understanding them and proactively improving your security posture. This involves leveraging the wealth of data generated by your EDR system to create insightful reports and perform comprehensive security analytics. These reports provide crucial context, allowing you to identify trends, assess vulnerabilities, and ultimately strengthen your defenses.EDR systems generate a wide variety of reports, each offering a different perspective on your security landscape.
The specific reports available will depend on the EDR solution you are using, but most offer a core set of capabilities. Understanding how to interpret and utilize this data is critical for effective security management.
Types of EDR Reports
EDR systems provide various report types, offering diverse views of security events and trends. Common reports include summary reports showing overall system health and threat activity, detailed incident reports focusing on individual events, and compliance reports demonstrating adherence to security policies. Many also provide custom report generation capabilities, enabling tailored analysis based on specific needs. For example, a report might focus on specific threat actors, highlighting their tactics, techniques, and procedures (TTPs).
Another report could analyze the effectiveness of specific security controls, such as the efficacy of endpoint detection and response.
Using EDR Data for Security Assessments and Trend Analysis
EDR data is a goldmine for security assessments. By analyzing historical data, security teams can identify patterns in attacks, vulnerabilities exploited, and the effectiveness of existing security measures. This allows for proactive remediation of vulnerabilities and improvement of security strategies. For instance, a spike in phishing attempts targeting a specific department could indicate a need for targeted security awareness training.
Similarly, frequent detection of a particular malware family suggests a vulnerability in your security controls that needs addressing. Trend analysis allows for predictive security management, enabling proactive mitigation of potential threats before they cause significant damage. This proactive approach minimizes the impact of security incidents and reduces recovery time.
Examples of Effective Visualizations of EDR Data
Effective visualization is key to understanding complex EDR data. Dashboards displaying key metrics like the number of alerts, malware detections, and successful remediation attempts provide a quick overview of the security status. Charts showing the trends in specific threats over time can highlight emerging threats and patterns. Heatmaps can visually represent the geographical distribution of attacks or the concentration of vulnerabilities within a network.
For instance, a bar chart might display the top five most prevalent malware families detected over the past month, allowing for prioritized remediation efforts. A geographical heatmap could show the locations of compromised endpoints, providing insights into potential attack vectors.
Sample EDR Security Report
The following table presents a sample report summarizing key security metrics from an EDR system over a one-month period.
| Metric | Value | Trend | Status |
|---|---|---|---|
| Total Alerts | 1250 | Increased (15%) | Warning |
| Malware Detections | 75 | Decreased (10%) | Good |
| Phishing Attempts | 200 | Increased (25%) | Critical |
| Successful Remediation | 95% | Stable | Good |
Case Studies
Real-world examples highlight the effectiveness and value of Endpoint Detection and Response (EDR) solutions. These case studies demonstrate how EDR can prevent, mitigate, and respond to security incidents, ultimately reducing the impact on organizations. We’ll explore scenarios showcasing successful threat prevention and improved incident response times.
EDR Preventing a Ransomware Attack
A large financial institution implemented an EDR solution across its network. A sophisticated ransomware attack targeted the organization, attempting to exploit a newly discovered vulnerability in a widely used accounting software. The EDR system, however, detected the malicious activity almost immediately. The system’s behavioral analysis flagged the unusual file execution patterns and data exfiltration attempts as suspicious.
The EDR automatically blocked the ransomware’s execution, preventing the encryption of critical financial data. Furthermore, the system generated detailed alerts, allowing the security team to quickly identify the compromised machine and isolate it from the network, thus preventing lateral movement of the malware. The outcome was a complete prevention of a potentially devastating ransomware attack, saving the company millions in potential losses and reputational damage.
The rapid response enabled by the EDR minimized downtime and the disruption to business operations.
EDR Improving Incident Response Time in a Phishing Campaign
A mid-sized manufacturing company experienced a successful phishing attack. An employee clicked a malicious link in a seemingly legitimate email, resulting in the installation of a keylogger. The EDR system, integrated with the company’s Security Information and Event Management (SIEM) system, detected the keylogger’s installation and data exfiltration attempts in real-time. The immediate alerts triggered an automated response, isolating the compromised machine and initiating a forensic investigation.
The rapid identification of the compromised system, facilitated by the EDR’s detailed logs and event timelines, significantly reduced the window of opportunity for the attackers. The company was able to contain the breach within hours, minimizing the exposure of sensitive data. The incident response time was drastically reduced compared to previous incidents, where manual investigation and analysis would have taken days or even weeks.
The quick response and containment prevented further compromise of the company’s network and data.
Challenges Faced and Overcome with EDR
During the incidents described above, several challenges were encountered. In the ransomware attack scenario, the challenge lay in identifying and isolating the compromised machine quickly enough to prevent lateral movement. The EDR’s automated response and detailed threat intelligence played a crucial role in overcoming this challenge. In the phishing campaign, the challenge was to quickly identify the source of the compromise and the extent of the data exfiltration.
The EDR’s integration with the SIEM and its comprehensive logging capabilities were vital in addressing this. In both cases, the initial challenge involved the sheer volume of security alerts generated by the EDR system. However, through effective configuration, alert filtering, and incident response processes, the security teams were able to manage the alerts effectively, focusing on high-priority threats.
The use of automated workflows and playbooks further streamlined the response, enabling quicker containment and remediation.
Final Thoughts
Mastering Endpoint Detection and Response isn’t just about deploying software; it’s about building a proactive security mindset. By understanding the intricacies of EDR, you’ll be better equipped to anticipate threats, respond swiftly to incidents, and ultimately, protect your organization from the ever-evolving landscape of cyberattacks. This guide serves as a foundation – continue learning, experimenting, and refining your approach to stay ahead of the curve.
Your digital fortress awaits!
FAQ Compilation
What’s the difference between EDR and Antivirus?
Antivirus focuses on signature-based detection of known threats. EDR goes further, using behavioral analysis and machine learning to detect unknown and sophisticated attacks.
How much does EDR software cost?
Pricing varies widely depending on the vendor, features, and number of endpoints. Expect a range from several hundred to thousands of dollars annually.
Is EDR suitable for small businesses?
Yes, while larger organizations often benefit most, even smaller businesses can leverage EDR’s capabilities to enhance their security posture, especially with cloud-based solutions.
How long does it take to implement EDR?
Implementation time depends on the size and complexity of your environment, but expect several weeks to months for full deployment and configuration.