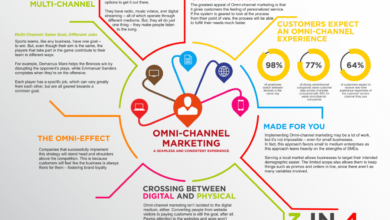
Creating B2C-like Online Shopping Experiences in B2B
Creating b2c like online shopping experiences in b2b – Creating B2C-like online shopping experiences in B2B isn’t just a trend; it’s a revolution. For years, B2B e-commerce has lagged behind the consumer experience, often clunky and frustrating. But times are changing. Businesses are realizing that the same ease and convenience that customers expect in their personal shopping should be extended to the professional sphere. This post dives into how to bridge that gap, transforming the often-daunting B2B buying journey into something smooth, intuitive, and even enjoyable.
We’ll explore how to adapt the best practices of B2C e-commerce—from streamlined checkout processes to personalized recommendations—to the unique needs of B2B clients. Think intuitive navigation, seamless integration with existing systems, and a focus on building trust and transparency. We’ll even touch on the technology that makes it all possible, from AI-powered chatbots to sophisticated CRM systems. Get ready to rethink your B2B online presence!
Defining the B2B Customer Journey Mirroring B2C: Creating B2c Like Online Shopping Experiences In B2b
The rise of e-commerce has revolutionized the B2C landscape, creating seamless and engaging online shopping experiences. Businesses are now looking to replicate this success in the B2B sphere, recognizing the potential for increased efficiency and customer satisfaction. By understanding the key touchpoints of a successful B2C journey and adapting them for the B2B context, companies can cultivate stronger relationships and drive sales.The typical B2C online shopping experience is characterized by its ease and convenience.
Customers can browse products, compare prices, read reviews, and make purchases with minimal friction. This simplicity, however, often masks a complex underlying process.
Key Touchpoints in B2C and B2B Online Purchases, Creating b2c like online shopping experiences in b2b
A successful B2C online purchase typically involves several key touchpoints: discovery (finding the product), research (comparing options), evaluation (reading reviews and specifications), purchase (adding to cart and checkout), and post-purchase (delivery and customer service). These stages are often interwoven and iterative, with customers frequently revisiting previous stages before committing to a purchase.Adapting these touchpoints for a B2B context requires a shift in focus.
While the core stages remain similar, the needs and expectations of B2B customers are significantly different. B2B buyers are often involved in complex decision-making processes, requiring more information, specialized support, and personalized service. The emphasis shifts from individual impulse purchases to strategic procurement decisions.
Comparing B2C and B2B Customer Needs and Expectations
B2C customers primarily prioritize convenience, price, and product features. Their purchase decisions are often driven by individual needs and preferences. In contrast, B2B customers are concerned with factors such as price, quality, reliability, and long-term partnerships. They often require detailed technical specifications, customized solutions, and dedicated account management. The purchase process itself is often more complex, involving multiple stakeholders and approval levels.
B2B Customer Journey Map
The following table Artikels a B2B customer journey map that incorporates elements of successful B2C online experiences. It demonstrates how a B2B company can leverage the simplicity and efficiency of B2C best practices while addressing the unique needs of its professional clientele.
| Stage | Action | Customer Need | B2C Equivalent |
|---|---|---|---|
| Awareness | Discovering relevant products or services through online search, industry publications, or referrals. | Understanding market solutions and identifying potential vendors. | Discovering products through social media ads or search engine results. |
| Consideration | Comparing offerings from multiple vendors, reviewing case studies, and requesting quotes. | Evaluating solutions based on specifications, pricing, and vendor reputation. | Comparing products based on reviews, features, and prices. |
| Decision | Negotiating contracts, securing approvals from multiple stakeholders, and finalizing purchase orders. | Ensuring alignment with business needs, securing favorable terms, and minimizing risk. | Completing the checkout process and confirming the order. |
| Action | Onboarding, implementation, and ongoing support. | Successful integration of the product or service and access to ongoing technical assistance. | Receiving the product and accessing customer support. |
Streamlining the B2B Purchasing Process
The traditional B2B purchasing process is often a labyrinthine affair, characterized by complex workflows, multiple stakeholders, and lengthy approval cycles. This contrasts sharply with the streamlined, user-friendly experiences offered by B2C e-commerce platforms, leaving many B2B businesses lagging behind in terms of customer satisfaction and efficiency. Adopting a B2C-like approach to the B2B buying journey can significantly improve the overall experience and drive positive business outcomes.
Complexities of Typical B2B Procurement Processes
B2B procurement often involves intricate processes, far removed from the simplicity of a typical online retail purchase. Multiple departments and individuals are usually involved, leading to delays in approvals and a lack of transparency. Negotiations over pricing, contract terms, and delivery schedules can be protracted, further extending the purchase cycle. The need for customized products or services adds another layer of complexity, requiring detailed specifications and potentially lengthy lead times.
Finally, the sheer volume of paperwork and documentation involved in B2B transactions can be overwhelming. For example, a large manufacturing company might require multiple purchase orders, approvals, and invoices for a single large-scale equipment purchase, involving finance, procurement, and operations teams.
Improving the B2B Buying Experience with B2C-like Simplicity
By mirroring the ease and speed of B2C e-commerce, B2B businesses can drastically improve the customer experience. This involves creating a user-friendly online portal that allows customers to easily browse products, compare options, and place orders. Self-service tools, such as online account management and order tracking, empower buyers and reduce their reliance on sales representatives for basic information.
Automated workflows can streamline the approval process, while integrated payment gateways offer secure and convenient payment options. For instance, a company selling software licenses could implement a streamlined online store where customers can easily select their desired package, enter their billing information, and receive an instant license key.
Simplifying Complex Product Configurations in a B2B Setting
Many B2B products require complex configurations to meet specific customer needs. To simplify this process, businesses can leverage interactive product configurators. These tools allow customers to visually customize products by selecting options, adding features, and specifying requirements. Real-time pricing updates and 3D visualizations further enhance the user experience. For example, a manufacturer of industrial machinery could use a configurator that allows customers to select specific components, power ratings, and accessories, instantly seeing the impact on price and delivery time.
This reduces errors and clarifies the specifications, accelerating the sales cycle.
Reducing Friction During the B2B Checkout Process
A cumbersome checkout process can deter customers and negatively impact conversion rates. To minimize friction, B2B businesses should focus on providing multiple payment options, including purchase orders, credit cards, and electronic transfers. Pre-filled forms based on customer data can significantly speed up the process, while clear and concise order summaries ensure transparency. Integration with existing ERP (Enterprise Resource Planning) systems streamlines backend processes and reduces manual data entry.
A company selling office supplies could pre-populate a customer’s address and billing information during checkout, based on their existing account profile. This simplifies the process and reduces the chance of errors.
Simplified B2B Checkout Flow
A simplified B2B checkout flow should aim for speed and clarity. Here’s a possible design:
- Review Order Summary: A clear and concise summary of all items, quantities, pricing, and discounts.
- Select Payment Method: Offer multiple secure payment options, clearly displaying the associated fees.
- Confirm Shipping Details: Pre-filled address information based on customer profile, with options for modifications.
- Review and Approve: A final review screen allowing customers to check all details before submitting the order.
- Order Confirmation: An immediate order confirmation with an order number and expected delivery date.
Leveraging Technology for an Enhanced B2B Experience
The digital transformation sweeping across all industries is particularly impactful for B2B businesses. To compete effectively and deliver exceptional customer experiences, B2B companies must leverage technology to streamline operations, personalize interactions, and ultimately drive sales. This involves a fundamental shift in thinking, moving away from traditional transactional approaches and embracing a more customer-centric, B2C-inspired model.
Personalized Recommendations in B2B E-commerce
Personalized product recommendations, a staple of successful B2C e-commerce, are equally valuable—if not more so—in the B2B context. By analyzing purchasing history, browsing behavior, and even industry trends, sophisticated algorithms can suggest products and services highly relevant to individual businesses’ needs. This targeted approach improves customer engagement, reduces search time, and increases the likelihood of conversion. For example, a supplier of industrial components could recommend specific fasteners based on a customer’s past orders of similar machinery, anticipating their future needs before they even articulate them.
This proactive approach fosters stronger customer relationships and increases sales.
AI-Powered Chatbots for B2B Customer Support
AI-powered chatbots are revolutionizing customer support across various sectors. In B2B, their ability to handle routine inquiries, provide instant answers to frequently asked questions, and even guide customers through the purchasing process is invaluable. This frees up human agents to focus on more complex issues and build stronger relationships with key accounts. Imagine a chatbot that can instantly provide tracking information for an order, answer questions about pricing and availability, or even initiate a return authorization – all without the need for a phone call or email exchange.
This improves response times, reduces wait times, and enhances customer satisfaction.
Technologies for a Seamless B2B Online Shopping Experience
Creating a truly seamless B2B online shopping experience requires a strategic integration of various technologies. A robust and scalable e-commerce platform forms the foundation, providing a user-friendly interface for browsing, searching, and purchasing. This platform should seamlessly integrate with existing enterprise resource planning (ERP) systems to ensure accurate inventory management, order processing, and invoicing. Secure payment gateways are essential, offering multiple payment options to cater to diverse business needs.
Furthermore, robust analytics dashboards provide crucial insights into customer behavior, allowing businesses to optimize their strategies.
Comparison of CRM Systems for B2B E-commerce
Several CRM systems cater specifically to the needs of B2B e-commerce. Salesforce, for instance, offers a comprehensive suite of tools for managing customer interactions, tracking sales pipelines, and automating marketing campaigns. HubSpot provides a similar range of features with a strong emphasis on inbound marketing. The choice between different systems often depends on the size and complexity of the business, its specific requirements, and its existing IT infrastructure.
Smaller businesses might find simpler, more affordable solutions sufficient, while larger enterprises might require the scalability and advanced features of a more comprehensive platform like Salesforce. Factors to consider include ease of integration with other systems, reporting capabilities, and customization options.
Key Technologies for Improving the B2B Online Shopping Experience
- E-commerce Platforms: Shopify Plus, Magento, Salesforce Commerce Cloud – provide robust online stores tailored for B2B needs, including features like bulk ordering, customized pricing, and complex approval workflows.
- Customer Relationship Management (CRM) Systems: Salesforce, HubSpot, Microsoft Dynamics 365 – centralize customer data, streamline communications, and personalize interactions.
- Enterprise Resource Planning (ERP) Systems: SAP, Oracle NetSuite, Microsoft Dynamics 365 – integrate various business processes, including inventory management, order fulfillment, and financial accounting.
- Artificial Intelligence (AI) and Machine Learning (ML): Power personalized recommendations, automate customer support through chatbots, and predict customer behavior.
- Business Intelligence (BI) and Analytics: Tableau, Power BI – provide insights into customer behavior, sales trends, and operational efficiency, informing data-driven decisions.
Building Trust and Transparency in B2B E-commerce
In the increasingly digital B2B landscape, building trust and transparency is paramount. Unlike traditional B2B relationships built on personal connections, online interactions require a different approach to foster confidence and encourage sales. Transparency, particularly in pricing and product information, is crucial for establishing credibility and fostering long-term partnerships. This is especially important given the higher value transactions typical in B2B.
The Importance of Trust in B2B Online Interactions
Trust is the bedrock of any successful B2B relationship, and this is amplified in the online environment. Without it, businesses are hesitant to share sensitive information, make large purchases, or enter into long-term contracts. Building trust online requires demonstrating competence, reliability, and integrity through consistent communication, high-quality products or services, and a commitment to customer satisfaction. A lack of trust can lead to lost sales, damaged reputation, and difficulty in acquiring new clients.
For example, a B2B software company that fails to deliver on promised features or provide adequate customer support will quickly lose the trust of its clients, impacting future business.
Strategies for Enhancing Transparency in Pricing and Product Information
Transparency in pricing and product information is vital for building trust. Ambiguous pricing structures or unclear product descriptions can lead to suspicion and hesitation. Clearly stating pricing, including any potential hidden fees or surcharges, builds confidence. Detailed product specifications, high-quality images and videos, and downloadable brochures or data sheets provide potential customers with the information they need to make informed decisions.
Consider using interactive product configurators to allow clients to customize products and see the impact on pricing in real-time. This approach eliminates guesswork and empowers buyers.
Communicating Value Propositions to B2B Buyers
Effectively communicating value propositions is key to converting potential customers. Instead of simply listing features, focus on the benefits those features deliver. Quantify the value whenever possible, using metrics such as ROI, cost savings, or increased efficiency. Case studies showcasing successful implementations with similar businesses provide compelling evidence of the value proposition. For example, a logistics company might highlight how its software solution reduced a client’s shipping costs by 15% and improved delivery times by 10%.
This data-driven approach strengthens the value proposition and builds confidence.
Handling Customer Reviews and Feedback in a B2B Context
Customer reviews and feedback are invaluable for building trust and improving products or services. While public reviews might be less common in B2B than B2C, actively soliciting and responding to feedback is crucial. This can be done through surveys, personalized emails, or dedicated feedback forms on the website. Publicly displaying positive reviews, while addressing negative ones professionally and transparently, demonstrates commitment to customer satisfaction and fosters trust.
Ignoring negative feedback can severely damage reputation. Addressing concerns publicly shows a willingness to improve and can even turn negative experiences into positive ones.
Displaying Customer Testimonials and Reviews
A dedicated section on the website showcasing customer testimonials and reviews is highly beneficial. Imagine a section titled “Client Success Stories” featuring a clean, modern design. Each testimonial would be presented within a visually appealing box or card. The card would include a headshot of the client, their company logo (if permitted), their title, and a concise, impactful quote from their review.
Below the quote, a small “Read More” link could lead to a full testimonial on a dedicated page. The overall design should be clean, professional, and easily scannable. The section should be prominently featured on the homepage and potentially other relevant pages, to maximize visibility and impact. This visual presentation reinforces the positive experiences of other businesses and instills confidence in potential clients.
Personalization and Account Management in B2B

Providing a personalized and efficient online experience is crucial for success in the B2B e-commerce landscape. Just as B2C businesses leverage personalization to boost sales and customer loyalty, B2B companies can significantly improve their bottom line by tailoring their online offerings to individual client needs and preferences. This involves not only customizing the shopping experience itself but also providing dedicated support and account management.
Strategies for Personalizing the B2B Online Shopping Experience
Effective personalization in B2B e-commerce goes beyond simply remembering a customer’s name. It involves leveraging data to understand their specific business needs, purchasing history, and industry trends. This allows for the creation of targeted product recommendations, customized pricing structures, and tailored content. For instance, a company selling industrial equipment could personalize the website to showcase equipment relevant to a customer’s specific industry, offering case studies and testimonials from similar businesses.
Another example would be offering customized bundles or packages based on past purchases and projected future needs. This approach fosters a sense of value and demonstrates a deep understanding of the customer’s business. Further personalization can be achieved through targeted email marketing campaigns showcasing relevant products or services, and personalized dashboards offering quick access to order history, invoices, and account information.
Benefits of Dedicated Account Management for B2B Clients
Dedicated account management significantly enhances the B2B customer experience. A dedicated account manager acts as a single point of contact, providing personalized support, proactive communication, and building strong, long-term relationships. This proactive approach reduces friction in the purchasing process, leading to increased customer satisfaction and loyalty. Account managers can anticipate client needs, offer tailored solutions, and resolve issues quickly and efficiently.
They also provide valuable insights into the client’s business, enabling the company to better understand their evolving needs and proactively offer relevant products and services. The result is stronger relationships, increased sales, and improved customer retention. For example, a dedicated account manager could proactively reach out to a client nearing the end of their service contract, offering renewal options and discussing potential upgrades.
Best Practices for Managing Customer Accounts and Relationships Online
Effective online account management requires a robust system capable of handling various aspects of the customer relationship. This includes secure access to account information, order history, invoices, and communication logs. A well-designed system should provide a clear and intuitive interface, allowing clients to easily manage their accounts and access necessary information. Regular communication is key, keeping clients updated on order status, new product releases, and relevant industry news.
Proactive outreach, such as personalized email campaigns or targeted offers, strengthens the relationship and demonstrates value. Furthermore, implementing a customer relationship management (CRM) system allows for efficient tracking of customer interactions, ensuring consistent and personalized service. Regular feedback mechanisms, such as surveys or feedback forms, allow for continuous improvement of the account management process.
Comparison of Account Management Software Solutions
Choosing the right account management software is critical for success. Different solutions offer varying levels of functionality, integration capabilities, and scalability. Some solutions are designed for small businesses, while others cater to large enterprises with complex requirements. Factors to consider include ease of use, reporting capabilities, integration with other business systems, and cost. Popular options include Salesforce, HubSpot, and Zoho CRM.
Each offers a range of features, but the best choice depends on specific business needs and budget. A thorough evaluation of different solutions is necessary to determine the best fit.
Comparison of Account Management Approaches
| Approach | Features | Pros | Cons |
|---|---|---|---|
| Self-Service Portal | Online access to account information, order history, invoices, FAQs, and support resources. | Cost-effective, readily available 24/7, empowers customers with control. | May not be suitable for complex issues, requires strong online support. |
| Dedicated Account Manager | Personalized support, proactive communication, tailored solutions, relationship building. | High customer satisfaction, strong relationship building, proactive issue resolution. | Higher cost, requires more resources, scalability can be challenging. |
| Hybrid Approach | Combines self-service portal with dedicated account management for complex issues or high-value clients. | Balances cost-effectiveness with personalized support, scalable to various customer needs. | Requires careful planning and execution, needs a robust system for seamless transition between approaches. |
Epilogue

Ultimately, creating a B2C-like experience in B2B is about putting the customer first. By simplifying processes, personalizing interactions, and leveraging the right technology, you can transform your B2B e-commerce platform into a powerful engine for growth. It’s not just about selling products; it’s about building lasting relationships. By focusing on user experience, you’ll not only increase sales but also cultivate loyalty and enhance your brand reputation.
Ready to make the switch? The future of B2B is here, and it’s surprisingly user-friendly.
Query Resolution
What are the biggest challenges in implementing B2C-like features in B2B?
Balancing the need for personalization with the complexities of B2B transactions (like complex pricing, approvals, and bulk ordering) is a major hurdle. Overcoming legacy systems and internal resistance to change can also be significant.
How can I measure the success of my B2C-inspired B2B changes?
Track key metrics like conversion rates, average order value, customer satisfaction scores (CSAT), and Net Promoter Score (NPS). Monitor website analytics to identify areas for improvement in user experience.
What if my B2B customers aren’t tech-savvy?
Prioritize intuitive design and offer excellent customer support. Provide comprehensive documentation and tutorials. Consider offering phone support in addition to online resources.
Are there any security concerns I should address?
Absolutely. Prioritize data security and implement robust security measures to protect sensitive customer information. Comply with all relevant data privacy regulations.