Cyber Resilience IriusRisk & Threat Modeling
Ensuring cyber resilience the critical role of threat modeling in software security iriusrisk – Ensuring cyber resilience: the critical role of threat modeling in software security IriusRisk – it sounds intense, right? But honestly, it’s all about building stronger, safer software. Think of it like this: you wouldn’t build a house without blueprints; similarly, robust software needs a solid security plan. Threat modeling, using tools like IriusRisk, is that blueprint. It helps us anticipate potential problems before they become major headaches (and security breaches!).
This post dives into how threat modeling, specifically with IriusRisk, is crucial for building truly resilient software.
We’ll explore how IriusRisk helps identify vulnerabilities, prioritize risks, and create actionable mitigation strategies. From understanding the basics of cyber resilience to mastering advanced threat modeling techniques, we’ll cover it all. Get ready to level up your software security game!
Introduction to Cyber Resilience and Threat Modeling
Cybersecurity is no longer a luxury; it’s a necessity. In today’s interconnected world, software applications are the lifeblood of businesses and organizations, making their security paramount. Cyber resilience, therefore, is not just about preventing attacks, but about the ability to withstand, recover from, and adapt to them. This blog post delves into the critical role of threat modeling, specifically using IriusRisk, in building robust cyber resilience into software.Cyber resilience in the context of software security refers to the ability of a software system to maintain its essential functions and services in the face of cyber threats.
It’s about building systems that are not only secure but also adaptable and able to bounce back from attacks quickly and efficiently. This involves proactively identifying vulnerabilities, mitigating risks, and having robust recovery plans in place. It’s a holistic approach, considering the entire lifecycle of the software, from design and development to deployment and maintenance.
Threat Modeling and its Importance
Threat modeling is a systematic process of identifying potential threats to a software system and evaluating the likelihood and impact of those threats. It’s a proactive approach that allows developers and security professionals to address vulnerabilities before they can be exploited. By understanding the potential attack vectors and their consequences, organizations can prioritize their security efforts and allocate resources effectively.
Threat modeling is crucial for achieving cyber resilience because it helps to identify and mitigate weaknesses before they become significant problems. A well-executed threat modeling process can significantly reduce the risk of successful cyberattacks and minimize the impact of any incidents that do occur.
Integrating IriusRisk into Threat Modeling
IriusRisk is a collaborative threat modeling platform that streamlines the entire process, from identifying assets and threats to assessing risks and generating mitigation strategies. Integrating IriusRisk offers several key benefits:* Improved Collaboration: IriusRisk facilitates collaboration among developers, security engineers, and other stakeholders, ensuring that everyone is on the same page throughout the threat modeling process.
Centralized Repository
It provides a centralized repository for all threat modeling artifacts, making it easy to track progress, manage changes, and ensure consistency.
Automated Risk Assessment
IriusRisk automates much of the risk assessment process, saving time and resources. Its algorithms help to prioritize threats based on their likelihood and impact, allowing teams to focus on the most critical issues.
Comprehensive Reporting
It generates comprehensive reports that document the entire threat modeling process, including identified threats, vulnerabilities, and mitigation strategies. This documentation is invaluable for auditing and compliance purposes.
Scalability
IriusRisk can scale to accommodate projects of any size and complexity, making it suitable for organizations of all sizes.
Comparison of Threat Modeling Methodologies
Choosing the right threat modeling methodology is crucial for effective risk management. Different methodologies cater to varying project needs and team expertise. Here’s a comparison of some popular methodologies:
| Methodology | Strengths | Weaknesses | Suitability for IriusRisk Integration |
|---|---|---|---|
| STRIDE | Simple, easy to understand and implement; good for initial threat identification. | Can be overly simplistic; may miss less obvious threats. | Excellent; easily adaptable within IriusRisk’s framework. |
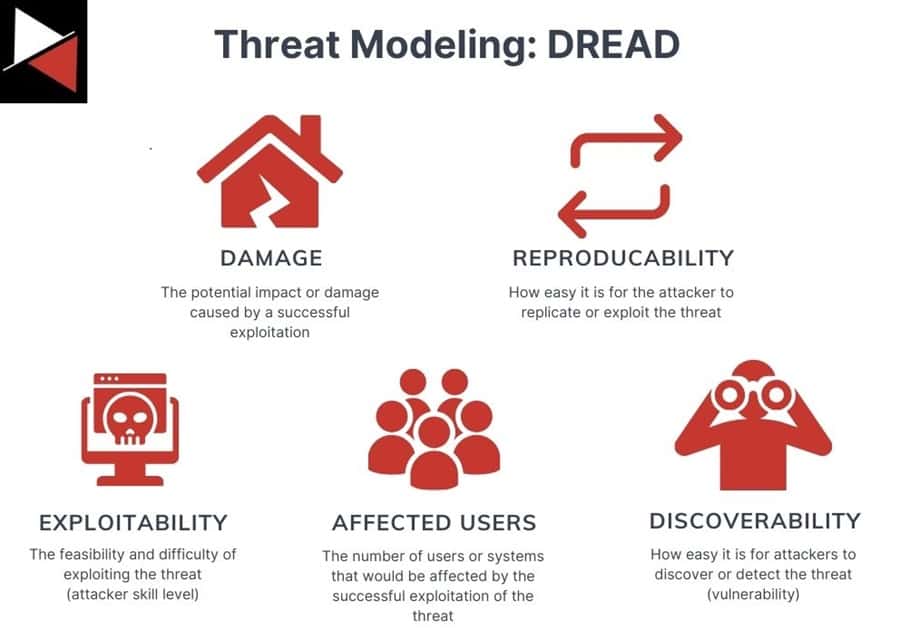
| PASTA | Comprehensive and systematic; covers a wide range of threats. | Can be complex and time-consuming; requires specialized expertise. | Good; IriusRisk can help manage the complexity. |
| DREAD | Focuses on risk prioritization; helps to focus on the most critical threats. | Subjective risk scoring; can be influenced by biases. | Good; IriusRisk can assist with objective risk scoring. |
| OWASP Threat Dragon | Visual and collaborative; facilitates easy understanding and communication. | Requires dedicated software; learning curve for new users. | Good; data can be imported and exported for integration. |
The IriusRisk Platform and its Features
IriusRisk is a collaborative threat modeling platform designed to streamline the process of identifying and mitigating security risks in software development. It moves beyond simple checklists, offering a visual and interactive approach that allows teams to work together effectively, regardless of their technical expertise. The platform’s core strength lies in its ability to translate complex security concepts into easily digestible diagrams and reports, fostering a shared understanding of risk across the entire development lifecycle.IriusRisk facilitates a structured approach to threat modeling, enabling teams to systematically identify, analyze, and prioritize potential vulnerabilities.
This structured approach reduces the chances of overlooking critical threats and ensures a more comprehensive security assessment. The platform’s features are designed to support various threat modeling methodologies, making it adaptable to different organizational contexts and project needs.
Core Functionalities of the IriusRisk Platform
The IriusRisk platform offers a range of functionalities designed to support the entire threat modeling process. These functionalities include a visual modeling tool for creating and managing threat models, a comprehensive threat library with pre-defined threats and vulnerabilities, a risk assessment engine for prioritizing threats based on their likelihood and impact, and reporting capabilities for documenting and sharing threat modeling findings.
The platform also supports collaboration features, allowing multiple users to work on the same threat model simultaneously. Furthermore, IriusRisk integrates with various development tools and processes, streamlining the incorporation of security considerations into the software development lifecycle.
Threat Identification and Assessment in IriusRisk
IriusRisk simplifies threat identification through its intuitive interface and structured approach. Users can define their system architecture visually, using pre-defined components or creating custom ones. Once the architecture is defined, the platform guides users through a structured process of identifying potential threats associated with each component and the interactions between them. The platform’s threat library provides a wealth of pre-defined threats, categorized by type and severity, speeding up the identification process.
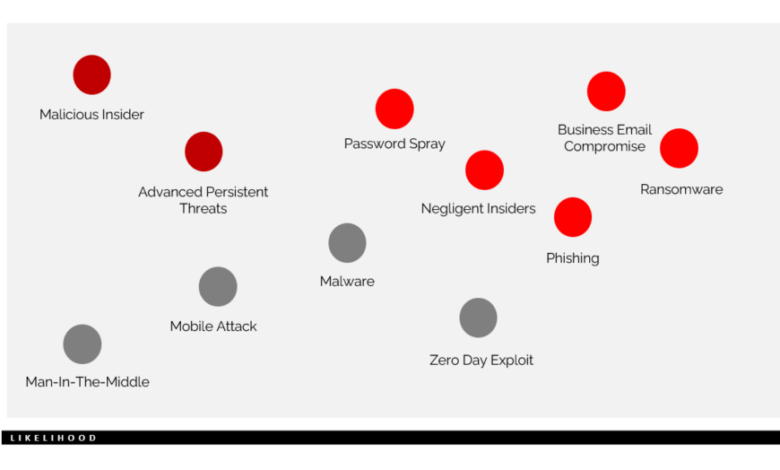
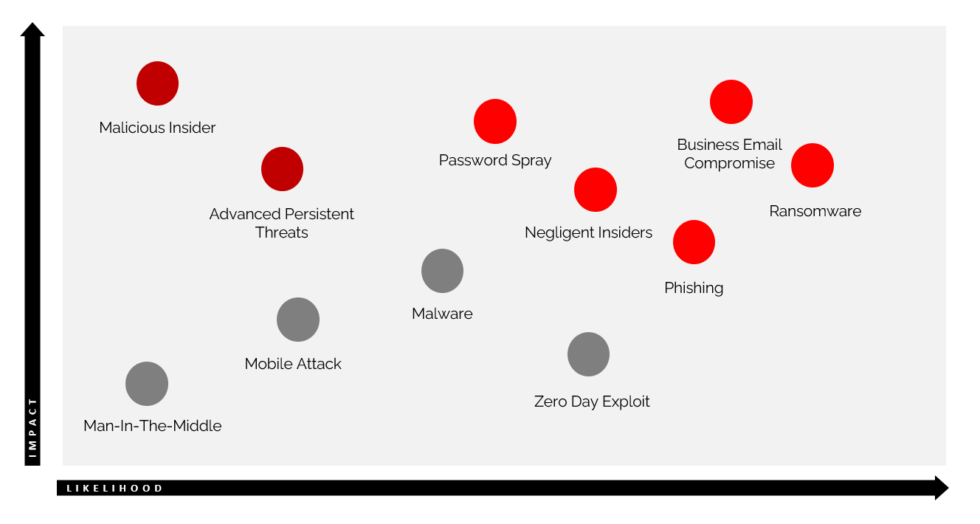
After identifying threats, IriusRisk facilitates risk assessment by allowing users to assign likelihood and impact scores to each threat. This process enables the prioritization of threats based on their potential to cause damage, guiding remediation efforts towards the most critical vulnerabilities. This structured approach ensures that no critical threat is overlooked, leading to a more robust and secure system.
Threat Modeling a Simple Web Application Using IriusRisk: A Step-by-Step Guide
Let’s consider a simple web application with three components: a web server, a database, and a client-side application. Here’s a simplified step-by-step guide:
1. Define the System Architecture
Building truly resilient software requires a proactive approach, and threat modeling with tools like IriusRisk is key. But how does this translate to the rapid development cycles we see today? The answer lies in understanding the implications of modern development trends, such as those discussed in this excellent article on domino app dev, the low-code and pro-code future , where efficient development practices must be paired with robust security measures.
Ultimately, integrating threat modeling early and often is crucial for ensuring cyber resilience, regardless of your development methodology.
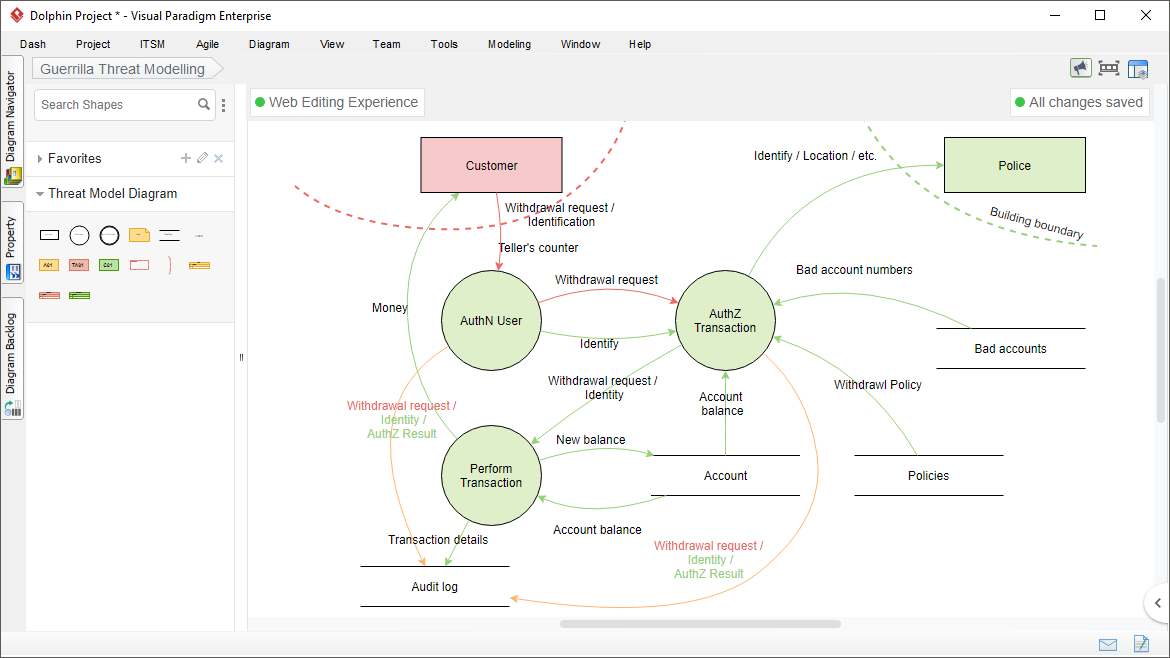
In IriusRisk, you would visually represent the web application’s architecture, showing the connections between the web server, database, and client. This involves adding components and defining their interactions using the platform’s visual modeling tools.
2. Identify Threats
For each component and interaction, IriusRisk facilitates the identification of potential threats. For example, for the web server, you might identify threats such as SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks. The platform’s threat library assists in this process.
3. Assess Risks
For each identified threat, assign likelihood and impact scores. This might involve considering factors such as the frequency of similar attacks and the potential damage if the attack is successful. IriusRisk provides a structured framework for this assessment.
4. Prioritize Threats
Based on the risk assessment, prioritize the identified threats. This prioritization guides remediation efforts, focusing on the most critical vulnerabilities first. IriusRisk helps visualize and manage this prioritization.
5. Document and Report
Generate reports documenting the identified threats, their associated risks, and the proposed mitigation strategies. These reports can be shared with stakeholders to ensure a shared understanding of the security posture of the web application.
Threat Modeling Workflow in IriusRisk: A Flowchart
Imagine a flowchart. It begins with “Define System Context and Scope,” flowing into “Create Visual Model of System Architecture.” This then branches into “Identify Threats,” and “Assess Risks.” These two branches converge into “Prioritize Threats.” From there, the flow continues to “Develop Mitigation Strategies,” followed by “Implement and Validate Mitigation,” and finally, “Document and Report Findings.” Each stage involves interaction with IriusRisk’s features, such as the visual modeling tools, threat library, risk assessment engine, and reporting capabilities.
The cyclical nature of threat modeling is implied, suggesting that the process may be repeated iteratively throughout the software development lifecycle.
Practical Application of Threat Modeling with IriusRisk
IriusRisk, a collaborative threat modeling platform, offers a structured approach to identifying and mitigating security risks in software development. Its practical application spans various industries and project sizes, providing tangible benefits throughout the software development lifecycle (SDLC). This section delves into real-world examples, implementation challenges, key performance indicators, and a comparison with other threat modeling tools.
Real-World IriusRisk Implementations
Several organizations have successfully leveraged IriusRisk to improve their software security posture. For instance, a large financial institution used IriusRisk to model its core banking application, identifying previously unknown vulnerabilities related to data access control. This proactive approach allowed them to address these risks before they could be exploited, preventing potential financial losses and reputational damage. Another example is a healthcare provider that utilized IriusRisk to model its patient management system, revealing weaknesses in data encryption and authentication.
By addressing these vulnerabilities, they enhanced patient data privacy and compliance with relevant regulations. These successful implementations demonstrate IriusRisk’s adaptability across diverse sectors and applications.
Challenges and Solutions in IriusRisk Implementation
While IriusRisk streamlines threat modeling, implementation can present challenges. One common hurdle is integrating IriusRisk into existing SDLC workflows. This often requires training and process adjustments to ensure team buy-in and consistent usage. Solutions include phased implementation, starting with a pilot project to demonstrate value, followed by gradual integration across teams. Another challenge is maintaining data accuracy and consistency across multiple users.
IriusRisk addresses this through its collaborative features, allowing for version control and audit trails. Finally, some organizations face difficulties in defining clear scope and objectives for their threat modeling efforts. Careful planning and stakeholder engagement are crucial to overcome this challenge, ensuring that the threat modeling process aligns with overall security goals.
Key Metrics for Measuring IriusRisk Effectiveness
Measuring the effectiveness of threat modeling with IriusRisk requires focusing on relevant metrics. Key indicators include the number of vulnerabilities identified and mitigated, the reduction in security incidents post-implementation, and the improvement in overall security posture as measured by penetration testing results. Tracking the time spent on threat modeling, the number of threats mitigated per unit of time, and the cost savings achieved by proactively addressing vulnerabilities are also valuable metrics.
These metrics provide quantifiable evidence of IriusRisk’s impact on software security.
Comparison of IriusRisk with Other Threat Modeling Tools, Ensuring cyber resilience the critical role of threat modeling in software security iriusrisk
IriusRisk offers several advantages compared to other threat modeling tools. The following table highlights some key differences:
| Tool | Key Features | Cost |
|---|---|---|
| IriusRisk | Collaborative platform, STRIDE and DREAD support, automated risk analysis, integration with other tools | Subscription-based, varying tiers |
| OWASP Threat Dragon | Open-source, visual modeling, various threat modeling methodologies supported | Free |
| Microsoft Threat Modeling Tool | Integrated with Visual Studio, focuses on .NET applications | Free |
Mitigating Risks Identified Through Threat Modeling
Threat modeling, using a platform like IriusRisk, isn’t just about identifying vulnerabilities; it’s about proactively mitigating them. The process transforms theoretical risks into actionable steps, improving your overall cyber resilience. This involves prioritizing mitigation strategies based on their feasibility and impact, and documenting everything in a clear, accessible risk register.
IriusRisk facilitates this transition seamlessly. Once threats and vulnerabilities are identified within the platform, you can directly link them to specific mitigation strategies. The platform’s visual representation of your system architecture allows for easy identification of the most critical areas needing attention. Furthermore, IriusRisk offers features for assigning risk scores and prioritizing mitigation efforts based on factors like likelihood and impact, ensuring you focus on the most pressing issues first.
Prioritizing Mitigation Strategies
Effective risk mitigation requires prioritization. IriusRisk allows you to assign severity levels to each identified threat and vulnerability, based on predefined criteria or custom scales. This enables a clear ranking of mitigation strategies, allowing resources to be allocated effectively. High-priority threats, those with a high likelihood and significant impact, should receive immediate attention. Lower-priority threats, while still needing addressing, can be scheduled for later implementation.
This prioritization process ensures a balanced approach, maximizing your security posture with available resources. For example, a critical vulnerability allowing remote code execution would receive a higher priority than a low-impact vulnerability affecting only a minor system component.
Creating a Risk Register
A comprehensive risk register is crucial for tracking and managing identified threats, vulnerabilities, and mitigation plans. This document serves as a central repository for all security-related information, enabling effective communication and collaboration across teams. IriusRisk can be used to generate reports that form the basis of your risk register. These reports can be tailored to include specific information, such as threat descriptions, vulnerability details, mitigation strategies, assigned owners, and deadlines.
| Threat | Vulnerability | Mitigation Strategy | Priority |
|---|---|---|---|
| SQL Injection | Unvalidated user input in database queries | Implement parameterized queries and input validation | High |
| Cross-Site Scripting (XSS) | Improper sanitization of user-supplied data | Encode user input before displaying it on the website | Medium |
| Denial of Service (DoS) | Lack of rate limiting on API endpoints | Implement rate limiting and traffic shaping mechanisms | High |
| Unauthorized Access | Weak password policy | Enforce strong password policies and implement multi-factor authentication | High |
Continuous Monitoring and Improvement
Cyber resilience isn’t a one-time achievement; it’s an ongoing process. Once mitigation strategies are implemented, continuous monitoring is essential to ensure their effectiveness and identify any emerging threats. Regular threat modeling exercises, utilizing IriusRisk for updates and analysis, are vital. The platform allows you to easily update your threat model as your system evolves, incorporating new components and functionalities.
This iterative process, coupled with regular security assessments, ensures your defenses remain robust and adapt to the ever-changing threat landscape. For instance, the discovery of a new zero-day exploit necessitates an immediate review and update of your threat model and mitigation strategies. This continuous cycle of assessment, mitigation, and monitoring is the cornerstone of a truly resilient security posture.
Integrating Threat Modeling into the Software Development Lifecycle (SDLC)
Integrating threat modeling effectively into your SDLC is crucial for building truly resilient software. By proactively identifying and mitigating vulnerabilities throughout the development process, you significantly reduce the risk of costly security breaches and ensure your application meets the highest security standards. This isn’t a bolt-on process; it needs to be seamlessly woven into the fabric of your development workflow.Threat modeling should be a continuous activity, not a one-off exercise.
IriusRisk facilitates this by providing a collaborative platform that supports various SDLC methodologies.
Threat Modeling Across SDLC Stages
The optimal approach involves incorporating threat modeling into multiple stages of the SDLC. This allows for iterative refinement and ensures that security considerations are addressed early and often, preventing issues from escalating later in the development cycle. Consider these key phases:
- Requirements Gathering: During this initial phase, IriusRisk can be used to analyze the proposed functionality and identify potential security risks associated with the high-level design. This early identification prevents building insecure features into the application from the outset.
- Design: This is a critical phase for threat modeling. IriusRisk allows you to model the system architecture, identify data flows, and pinpoint potential vulnerabilities before any code is written. This proactive approach saves significant time and resources later on.
- Implementation: As development progresses, IriusRisk can be used to track the implementation of security controls and verify that they are effectively mitigating the identified risks. This ensures that the design-level security considerations are translated into secure code.
- Testing: Threat modeling findings can inform the testing strategy, ensuring that test cases adequately cover the identified vulnerabilities. IriusRisk’s reporting features can help track the progress of remediation efforts.
- Deployment and Maintenance: Even after deployment, threat modeling remains relevant. IriusRisk helps monitor the system’s security posture and identify new vulnerabilities that may emerge over time, enabling proactive updates and patching.
Integrating IriusRisk into Agile Development
Agile methodologies, with their iterative and incremental approach, necessitate a flexible and adaptable threat modeling process. IriusRisk supports this through its collaborative features and ability to integrate with existing Agile tools. Threat modeling workshops can be integrated into sprint planning, allowing for quick identification and prioritization of security risks. The platform’s intuitive interface allows for quick updates and collaboration among developers, security experts, and stakeholders.
Regular threat modeling sessions throughout the sprints allow for continuous security improvement.
Visual Representation of IriusRisk Integration in a Waterfall SDLC
Imagine a diagram depicting a Waterfall SDLC model with its various phases: Requirements, Design, Implementation, Testing, Deployment, and Maintenance. Arrows connect each phase, representing the sequential flow. Within each phase, a smaller, nested box represents IriusRisk. The arrows entering the IriusRisk box represent the input of system information (e.g., requirements documents, design specifications, code), and the arrows exiting represent outputs (e.g., threat model diagrams, risk assessments, remediation plans).
This visually represents how IriusRisk supports each stage, providing continuous feedback and improvement throughout the entire SDLC. The size of the IriusRisk box could even visually represent the increased involvement and effort in earlier phases compared to later ones, reflecting the principle of shifting security left.
Advanced Threat Modeling Techniques with IriusRisk: Ensuring Cyber Resilience The Critical Role Of Threat Modeling In Software Security Iriusrisk
IriusRisk, while excellent for standard threat modeling, truly shines when tackling more complex scenarios. Its capabilities extend beyond basic threat identification, allowing for the application of advanced techniques that provide a deeper, more nuanced understanding of potential vulnerabilities. This section explores how IriusRisk facilitates these advanced methods and addresses some of its limitations.This section will delve into the practical application of attack trees within IriusRisk, followed by a discussion of threat modeling for cloud-based systems.
We’ll then explore IriusRisk’s limitations and propose strategies to enhance its effectiveness.
Attack Tree Modeling in IriusRisk
Attack trees provide a hierarchical representation of potential attack paths, visually illustrating how an attacker might exploit vulnerabilities to achieve a specific objective. IriusRisk doesn’t directly support the creation of attack trees in a visual, drag-and-drop manner like some specialized tools. However, its strength lies in its ability to model the components and relationships within a system, which serves as an excellent foundation for constructing an attack tree.
By meticulously documenting system components, data flows, and security controls within IriusRisk, you can effectively map out potential attack paths and subsequently represent them as an attack tree in a separate document. This indirect approach allows for a detailed and comprehensive representation of the attack surface. For instance, by identifying all authentication mechanisms within IriusRisk, you can easily translate those into the nodes of an attack tree, branching out to represent different attack vectors against each mechanism (e.g., brute-force attacks, phishing, exploiting vulnerabilities in the authentication process itself).
The detailed information captured in IriusRisk’s model greatly simplifies the creation and analysis of the attack tree.
Threat Modeling for Cloud-Based Applications with IriusRisk
Cloud environments introduce a unique set of security challenges. IriusRisk effectively addresses these by allowing the modeling of distributed systems and their various components, including cloud services, APIs, and databases. For example, you can model a three-tier architecture with a front-end application running on AWS, a backend service on Azure, and a database on GCP. By defining the interactions between these components within IriusRisk, you can identify vulnerabilities related to data transit, API security, and misconfigurations within each cloud provider’s environment.
The platform’s ability to model dependencies between components is particularly crucial for cloud environments, allowing for a holistic understanding of potential vulnerabilities across the entire system. This detailed representation helps pinpoint weaknesses related to cloud-specific threats, such as unauthorized access to storage buckets or vulnerabilities in cloud-based APIs. Identifying and mitigating these risks is crucial for ensuring the security of cloud-based applications.
Limitations of IriusRisk and Workarounds
While IriusRisk is a powerful tool, it has limitations. One is the lack of direct support for certain advanced threat modeling techniques like attack trees (as discussed above). Another is the potential for model complexity to become overwhelming for very large and intricate systems. However, workarounds exist. For complex systems, breaking the system down into smaller, manageable modules and modeling them separately before integrating the results can mitigate complexity.
The lack of direct attack tree visualization can be addressed by using IriusRisk for the foundational system modeling and then employing a separate attack tree modeling tool to visually represent the identified attack paths. This hybrid approach leverages the strengths of both platforms.
Recommendations for Improving Threat Modeling Effectiveness with IriusRisk
To maximize the effectiveness of threat modeling with IriusRisk, regular training for team members on the platform’s features and advanced techniques is essential. Establishing clear guidelines and templates for threat modeling exercises will ensure consistency and quality. Integrating threat modeling into the SDLC early on is crucial, ideally at the design phase, to allow for proactive mitigation of risks.
Finally, regular review and updates of the threat model are vital to reflect changes in the system and the threat landscape. This iterative process ensures the ongoing relevance and accuracy of the threat model, leading to more robust and secure applications.
Concluding Remarks
So, there you have it – a deep dive into the world of cyber resilience and the vital role threat modeling plays. IriusRisk emerges as a powerful ally in this journey, simplifying complex processes and empowering developers to build secure software from the ground up. Remember, proactive security isn’t just a good idea; it’s a necessity in today’s digital landscape.
By embracing threat modeling and leveraging tools like IriusRisk, we can significantly reduce our attack surface and build a more secure future for everyone. Ready to get started? Let’s build some resilient software!
Quick FAQs
What if I don’t have a large security team? Can I still use IriusRisk?
Absolutely! IriusRisk is designed to be user-friendly and accessible, regardless of team size. Its intuitive interface makes it easy to learn and implement, even for smaller teams.
How much does IriusRisk cost?
IriusRisk offers various pricing plans to suit different needs and budgets. Check their website for the most up-to-date pricing information.
Is IriusRisk only for web applications?
No, IriusRisk can be applied to a wide range of applications, including mobile apps, IoT devices, and more. Its flexibility makes it adaptable to various systems and architectures.
How often should I conduct threat modeling?
The frequency depends on your project’s complexity and risk profile. For high-risk projects, regular threat modeling throughout the SDLC is recommended. For others, periodic reviews might suffice.





