Enterprise Information Networks and the Threat Environment
Enterprise information networks and the threat environment are more intertwined than ever. Think about it – your company’s entire digital lifeblood, from customer data to financial records, flows through these networks. But lurking in the shadows are sophisticated cyberattacks, data breaches, and insider threats, all vying to disrupt operations and steal sensitive information. This post dives deep into the vulnerabilities, threats, and best practices for securing your enterprise network, offering a practical guide for navigating this complex landscape.
We’ll explore the architecture of typical enterprise networks, identifying key vulnerabilities like outdated software, weak passwords, and phishing scams. We’ll examine the evolving threat landscape, including advanced persistent threats (APTs) and the ever-increasing sophistication of cybercriminals. We’ll also discuss essential security measures, from robust access controls and data encryption to the crucial role of employee training and incident response planning.
Finally, we’ll touch on the impact of emerging technologies like cloud computing, AI, and IoT on network security, and how to adapt your strategies to stay ahead of the curve.
Defining Enterprise Information Networks
Enterprise information networks are the nervous systems of modern businesses, facilitating communication, data sharing, and resource management across geographically dispersed locations and diverse departments. They are complex, interwoven systems encompassing hardware, software, data, and people, all working together to support the organization’s strategic goals. Understanding their architecture and functionality is crucial for effective management and security.Enterprise information networks are not monolithic entities; rather, they represent a collection of interconnected systems and technologies.
Their architecture is typically layered, with each layer providing specific functionalities and supporting the layers above. This layered approach allows for scalability, flexibility, and easier management of the network as a whole.
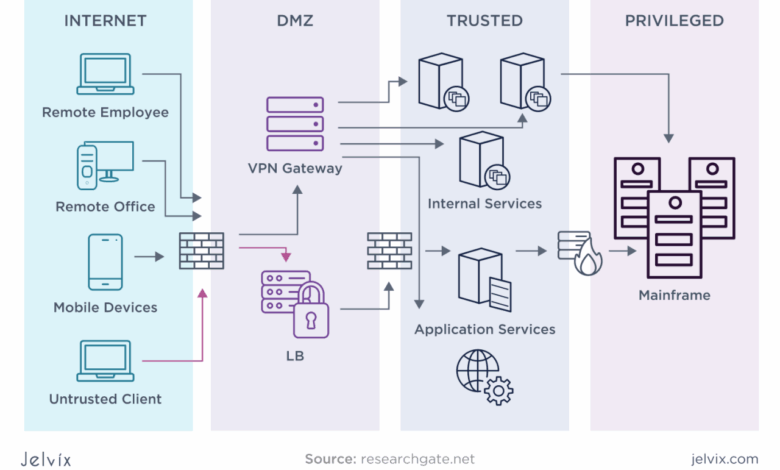
Enterprise Information Network Architecture
A typical enterprise information network architecture can be visualized as a layered model. The foundation comprises the physical infrastructure – servers, routers, switches, cabling, and other hardware components. Above this lies the network layer, responsible for data transmission and routing. The application layer then houses the software applications that utilize the network for data access and processing.
Finally, the data layer holds the organization’s valuable information, ranging from transactional data to strategic insights. This layered approach allows for modularity and facilitates easier troubleshooting and upgrades.
Components of an Enterprise Information Network
The components of an enterprise information network are diverse and interdependent. Hardware includes servers (for data storage and processing), routers (for directing network traffic), switches (for connecting devices within a local area network), and network interface cards (NICs) for individual devices. Software components include operating systems, network management tools, security software (firewalls, intrusion detection systems), and applications such as enterprise resource planning (ERP) systems, customer relationship management (CRM) systems, and supply chain management (SCM) systems.
The data itself – the lifeblood of the network – encompasses various formats, including structured data (databases), semi-structured data (XML files), and unstructured data (documents, images, videos).
Types of Enterprise Information Networks
Different types of networks cater to specific organizational needs. Local Area Networks (LANs) connect devices within a single location, such as an office building. Wide Area Networks (WANs) connect geographically dispersed locations, often utilizing leased lines or the internet. Virtual Private Networks (VPNs) create secure connections over public networks, allowing remote access to the enterprise network. Each type has its strengths and weaknesses, and the choice depends on the organization’s size, geographical spread, and security requirements.
For example, a global corporation might utilize a WAN to connect its offices worldwide, supplemented by LANs within each office and VPNs for secure remote access.
Industry Examples of Enterprise Information Network Utilization
Industries utilize enterprise information networks in diverse ways. In finance, networks support high-frequency trading, risk management, and regulatory compliance. Healthcare utilizes networks for electronic health records (EHRs), telehealth services, and patient data management. Retail uses networks for inventory management, point-of-sale (POS) systems, and customer loyalty programs. Manufacturing employs networks for supply chain optimization, production monitoring, and quality control.
The specific applications vary across industries, but the underlying principle remains consistent: efficient information flow is vital for operational efficiency and strategic decision-making. For instance, a large retail chain might use a sophisticated ERP system integrated with its POS systems and supply chain management software, all connected through a robust WAN, to optimize inventory levels and respond quickly to changing customer demand.
Identifying Key Vulnesses in Enterprise Information Networks
Enterprise information networks, despite robust security measures, remain vulnerable to a range of cyber threats. Understanding these vulnerabilities is crucial for effective risk management and the implementation of appropriate security controls. This section will delve into five prevalent vulnerabilities, their impact on data, and how different network architectures influence their potential for exploitation.
Top Five Vulnerabilities Affecting Enterprise Networks
The following five vulnerabilities consistently rank among the most significant threats to enterprise networks: weak or default passwords, unpatched software, phishing attacks, malware infections, and misconfigured security settings. These vulnerabilities represent points of entry for attackers seeking to compromise confidentiality, integrity, or availability of sensitive data.
- Weak or Default Passwords: Many breaches stem from easily guessable passwords or those left unchanged from factory defaults. This allows unauthorized access, compromising all three data pillars: confidentiality (sensitive data exposed), integrity (data altered or deleted), and availability (systems disrupted).
- Unpatched Software: Outdated software contains known vulnerabilities that attackers actively exploit. This compromises confidentiality (data leaks through exploits), integrity (data corruption due to malicious code), and availability (system crashes or denial-of-service attacks).
- Phishing Attacks: These deceptive emails or messages trick users into revealing credentials or downloading malware. This directly impacts confidentiality (stolen credentials expose data), integrity (malware alters data), and availability (systems disabled through ransomware).
- Malware Infections: Viruses, worms, and ransomware can infiltrate networks through various vectors, including phishing, unpatched software, or compromised devices. This affects all three data pillars: confidentiality (data exfiltration), integrity (data modification or deletion), and availability (system disruption or data encryption by ransomware).
- Misconfigured Security Settings: Incorrectly configured firewalls, access controls, or other security mechanisms create significant weaknesses. This compromises confidentiality (unauthorized access to data), integrity (data alteration due to lack of control), and availability (systems vulnerable to attacks).
Impact of Vulnerabilities on Data Confidentiality, Integrity, and Availability (CIA Triad)
The CIA triad—confidentiality, integrity, and availability—provides a framework for understanding the impact of vulnerabilities. A breach can affect one, two, or all three aspects, depending on the nature of the attack and the vulnerability exploited. For example, a successful phishing attack might compromise confidentiality by stealing credentials and integrity by installing malware that alters data. Ransomware attacks directly impact availability by encrypting data and demanding a ransom for its release.
Weak passwords directly affect confidentiality by allowing unauthorized access to data.
Vulnerability Comparison Across Network Architectures
Different network architectures exhibit varying degrees of vulnerability. For instance, a centralized network might be more susceptible to a single point of failure, while a decentralized network might be more resilient but harder to manage securely. Cloud-based networks present unique challenges related to data security and access control. Legacy networks with outdated protocols are inherently more vulnerable than modern networks with robust security features.
The complexity of the network also plays a role; larger, more complex networks are generally harder to secure effectively.
Hypothetical Cyberattack Scenario
Imagine a scenario where an attacker exploits a known vulnerability in a company’s unpatched web server (a common vulnerability). The attacker uses a publicly available exploit to gain initial access. Once inside, they deploy ransomware, encrypting sensitive financial data and demanding a ransom for its release. This attack simultaneously compromises confidentiality (sensitive financial data is accessed), integrity (data is encrypted and potentially altered), and availability (access to critical data is denied).
The company’s failure to patch the web server allowed this attack to succeed. The impact extends beyond financial loss to include reputational damage and potential legal repercussions.
Analyzing the Threat Landscape: Enterprise Information Networks And The Threat Environment
The digital landscape is a constantly shifting battlefield, and enterprise information networks are prime targets for a growing array of sophisticated cyber threats. Understanding the evolution of these threats and the various attack vectors is crucial for effective security planning and mitigation. This section explores the evolving threat landscape, focusing on advanced persistent threats and common attack types, as well as the often-overlooked danger of insider threats.
The Evolution of Cyber Threats
Cyber threats have evolved from simple malware infections to highly coordinated, multi-stage attacks. Early threats focused on individual vulnerabilities, often exploiting known weaknesses in software. Today’s threats are more complex, leveraging social engineering, zero-day exploits, and automated tools to bypass traditional security measures. The shift towards cloud computing and the Internet of Things (IoT) has expanded the attack surface, creating new vulnerabilities and increasing the potential for damage.
Attackers are becoming more organized and financially motivated, with sophisticated criminal enterprises and nation-state actors driving much of the activity. The increasing reliance on interconnected systems means that a breach in one area can quickly cascade throughout an entire organization.
Advanced Persistent Threats (APTs) and Their Impact
Advanced Persistent Threats (APTs) represent a particularly dangerous class of cyberattacks. These are highly targeted, long-term attacks often conducted by state-sponsored actors or highly organized criminal groups. APTs are characterized by their stealthy nature, ability to evade detection, and focus on stealing valuable intellectual property, trade secrets, or sensitive data. For example, the notorious SolarWinds attack involved the compromise of the SolarWinds Orion software, allowing attackers to infiltrate numerous government and private sector organizations.
The impact of such attacks can be devastating, leading to significant financial losses, reputational damage, and legal repercussions. The long-term nature of APTs means that damage can continue to accrue long after the initial breach is discovered. Another example is the NotPetya attack, which, while not strictly an APT, demonstrated the potential for widespread disruption and significant financial damage through a sophisticated malware campaign.
Types of Cyber Threats and Mitigation Strategies
The following table compares different types of cyber threats, their impact, and potential mitigation strategies.
| Threat Type | Impact | Mitigation Strategies |
|---|---|---|
| Malware (e.g., viruses, ransomware) | Data loss, system disruption, financial losses, reputational damage | Antivirus software, regular software updates, employee training, data backups, network segmentation |
| Phishing | Data breaches, credential theft, malware infections | Security awareness training, multi-factor authentication (MFA), email filtering, strong password policies |
| Denial-of-Service (DoS) Attacks | Service disruption, loss of revenue, reputational damage | Network monitoring, intrusion detection systems (IDS), DDoS mitigation services, robust infrastructure |
| SQL Injection | Data breaches, unauthorized access, system compromise | Input validation, parameterized queries, regular security audits, web application firewalls (WAFs) |
The Role of Insider Threats
Insider threats, originating from employees, contractors, or other individuals with legitimate access to an organization’s network, represent a significant and often underestimated risk. These threats can range from unintentional mistakes, such as accidentally sharing sensitive information, to malicious acts like data theft or sabotage. The motivations behind insider threats can vary, including financial gain, revenge, negligence, or even ideological reasons.
Mitigating insider threats requires a multi-layered approach, including robust access control policies, regular security audits, employee background checks, and strong security awareness training. Effective monitoring of user activity and data access patterns can also help identify suspicious behavior and prevent potential breaches. The human element remains a critical vulnerability, highlighting the importance of a comprehensive security culture that emphasizes responsible data handling and security awareness.
Security Measures and Best Practices
Protecting enterprise information networks is paramount in today’s interconnected world. A robust security posture isn’t just a compliance requirement; it’s a business imperative, safeguarding sensitive data, maintaining operational continuity, and protecting the organization’s reputation. Failing to implement strong security measures can lead to devastating financial losses, legal repercussions, and irreparable damage to customer trust. This section Artikels crucial security measures and best practices for building a resilient defense against cyber threats.Implementing comprehensive security measures requires a multi-faceted approach.
It’s not enough to rely on a single solution; a layered defense, combining various technologies and strategies, is essential to effectively mitigate risks. This layered approach should address vulnerabilities at each point of entry and throughout the network infrastructure. This section will delve into specific strategies and technologies to help build a more secure network environment.
Access Control
Effective access control is foundational to network security. This involves limiting access to sensitive data and systems based on the principle of least privilege – granting users only the access necessary to perform their job functions. Implementing strong authentication mechanisms, such as multi-factor authentication (MFA), significantly enhances security by adding an extra layer of verification beyond passwords. Role-based access control (RBAC) further refines access management by assigning permissions based on an individual’s role within the organization.
Regularly reviewing and updating access permissions ensures that only authorized personnel retain access, minimizing the risk of unauthorized access or data breaches. For example, a junior employee should not have access to sensitive financial data, only those in the finance department with appropriate authorization should.
Data Encryption
Data encryption is a critical security measure that transforms readable data into an unreadable format, protecting it from unauthorized access even if intercepted. Both data at rest (stored on servers or storage devices) and data in transit (transmitted over networks) should be encrypted using strong encryption algorithms. This includes encrypting databases, files, and communication channels using protocols like TLS/SSL for secure web traffic and VPNs for secure remote access.
Key management is crucial for data encryption; secure key storage and rotation practices are essential to prevent unauthorized decryption. Consider the impact of a data breach: encrypted data remains unusable to attackers, significantly reducing the potential damage.
Regular Security Audits
Regular security audits are vital for identifying vulnerabilities and weaknesses in an organization’s security posture. These audits should involve both internal assessments and penetration testing by external security experts. Internal audits evaluate existing security controls and procedures, identifying gaps and areas for improvement. Penetration testing simulates real-world attacks to identify exploitable vulnerabilities before malicious actors can exploit them.
Regular audits provide valuable insights into the effectiveness of security measures and inform the ongoing development and improvement of the organization’s security strategy. For instance, a regular vulnerability scan can identify outdated software versions that need updating.
Multi-Layered Security Approach
A multi-layered security approach utilizes a combination of security controls to create a defense-in-depth strategy. This approach involves implementing security measures at various levels of the network infrastructure, including:
- Network Perimeter Security: Firewalls, intrusion detection/prevention systems (IDS/IPS), and virtual private networks (VPNs) protect the network from external threats.
- Host-Based Security: Antivirus software, endpoint detection and response (EDR) solutions, and operating system hardening protect individual computers and servers.
- Application Security: Secure coding practices, input validation, and regular security updates protect applications from vulnerabilities.
- Data Security: Encryption, access control, and data loss prevention (DLP) tools protect sensitive data.
- User Education and Awareness: Training employees on security best practices helps prevent social engineering attacks and phishing scams.
This layered approach ensures that even if one security control fails, others are in place to mitigate the risk.
Security Information and Event Management (SIEM) Systems
SIEM systems collect and analyze security logs from various sources across the network, providing a centralized view of security events. They can detect malicious activities, identify security incidents, and provide real-time alerts. This allows security teams to respond quickly to threats, reducing the impact of security breaches. SIEM systems also help in compliance auditing and reporting, demonstrating adherence to security regulations and standards.
For example, a SIEM system can detect unusual login attempts from unusual geographical locations, indicating a potential breach attempt. This allows security teams to investigate and block the suspicious activity.
Enterprise information networks face a constantly evolving threat landscape, especially with the increasing reliance on cloud services. Managing this risk requires robust security measures, and that’s where solutions like cloud security posture management (CSPM) become crucial. To learn more about a leading CSPM solution and how it addresses these challenges, check out this article on bitglass and the rise of cloud security posture management ; understanding its capabilities is key to bolstering your enterprise’s defenses against modern threats.
Ultimately, a strong security posture is vital for protecting sensitive data within complex enterprise networks.
Incident Response and Recovery
A robust incident response plan is the cornerstone of any effective cybersecurity strategy for enterprise information networks. Without a well-defined plan, even the best preventative measures can be rendered useless when a security breach occurs. A swift and organized response minimizes damage, maintains business continuity, and strengthens future defenses. This section details the critical components of developing and implementing such a plan, along with the importance of employee training and real-world examples of successful responses.
Developing an Incident Response Plan
Creating a comprehensive incident response plan requires a structured approach. The plan should clearly define roles and responsibilities, escalation procedures, and communication protocols. It needs to cover all phases of incident handling, from initial detection to post-incident activity. This includes establishing a clear chain of command, identifying key personnel responsible for specific tasks (e.g., system administrators, security analysts, legal counsel, public relations), and outlining communication channels for internal and external stakeholders.
The plan should also detail procedures for evidence preservation, system restoration, and post-incident analysis. Regular testing and updates are crucial to ensure the plan remains relevant and effective. A table outlining the key phases and activities within each would be beneficial.
| Phase | Activities |
|---|---|
| Preparation | Risk assessment, policy development, team formation, resource allocation |
| Identification | Detection of security incidents through monitoring systems and alerts |
| Containment | Isolation of affected systems and networks to prevent further damage |
| Eradication | Removal of malware, vulnerabilities, and compromised accounts |
| Recovery | Restoration of systems and data from backups, security hardening |
| Post-Incident Activity | Analysis of the incident, lessons learned, updates to security policies and procedures |
The Importance of Security Awareness Training
Regular security awareness training is not merely a “nice-to-have”; it’s a critical component of a strong security posture. Human error remains a leading cause of security breaches. Employees often fall victim to phishing scams, social engineering attacks, or unintentionally introduce malware through unsafe browsing habits. Comprehensive training programs educate employees on recognizing and avoiding these threats. This training should include practical exercises and simulated phishing campaigns to reinforce learning and build awareness.
Effective training programs also cover password management, data protection policies, and incident reporting procedures. By empowering employees to be vigilant and informed, organizations significantly reduce their vulnerability to human-driven security incidents.
Securing enterprise information networks is a constant battle against evolving threats. Building robust, adaptable applications is key, and that’s where the future of app development comes in. Check out this article on domino app dev the low code and pro code future to see how streamlined development can help bolster your network’s defenses against sophisticated attacks.
Ultimately, secure application development directly impacts the overall resilience of your enterprise information network.
Handling a Security Incident: A Flowchart
The following describes a flowchart illustrating the incident response process. The flowchart begins with the detection of a potential security incident, followed by verification and analysis. If the incident is confirmed, the next step is containment, followed by eradication, recovery, and post-incident activities. Each step involves specific actions and decisions, and the flowchart provides a visual representation of the process flow, ensuring a systematic approach to incident handling.[Imagine a flowchart here.
The flowchart would visually represent the following steps: 1. Incident Detection; 2. Incident Verification; 3. Incident Analysis; 4. Containment; 5.
Eradication; 6. Recovery; 7. Post-Incident Activity. Arrows would connect each step, indicating the flow of the process. Decision points (e.g., “Is the incident confirmed?”) would be included with branches leading to different actions based on the outcome.]
Examples of Successful Incident Response Strategies
Several organizations have demonstrated effective incident response strategies. For example, Target’s response to the 2013 data breach, while initially criticized, ultimately led to significant improvements in their security infrastructure and procedures. Their experience highlighted the importance of swift communication, thorough investigation, and proactive remediation. Similarly, the response by Equifax to their 2017 data breach, although initially met with criticism for the delayed disclosure, illustrates the importance of proactive remediation and cooperation with authorities.
These examples, while showcasing failures initially, emphasize the critical role of transparency, accountability, and continuous improvement in effective incident response. These cases demonstrate the need for a well-defined incident response plan and the importance of learning from past mistakes to strengthen future defenses.
The Role of Emerging Technologies
The rapid advancement of technology is fundamentally reshaping the enterprise information network landscape, presenting both significant opportunities and considerable challenges for security professionals. Understanding how emerging technologies impact security is crucial for building robust and resilient networks capable of withstanding modern threats. This section explores the influence of cloud computing, artificial intelligence, blockchain, and the Internet of Things (IoT) on enterprise network security.
Cloud Computing’s Impact on Enterprise Network Security
Cloud computing offers scalability, cost-effectiveness, and accessibility, but it also introduces new security considerations. The shared responsibility model, where security responsibilities are divided between the cloud provider and the organization, requires careful planning and execution. Organizations must carefully vet cloud providers, ensuring they meet stringent security standards and compliance requirements. Data breaches within cloud environments, though often attributed to misconfigurations or vulnerabilities in customer applications, highlight the importance of robust access control, data encryption, and regular security audits.
For example, a misconfigured cloud storage bucket could expose sensitive company data to unauthorized access, leading to significant financial and reputational damage. Furthermore, the complexities of multi-cloud environments, where organizations use services from multiple cloud providers, can increase the difficulty of maintaining a unified security posture.
Artificial Intelligence and Machine Learning in Network Security Enhancement
AI and ML are revolutionizing network security by automating threat detection and response. AI-powered security information and event management (SIEM) systems can analyze vast amounts of data to identify anomalies and potential threats far more efficiently than traditional methods. Machine learning algorithms can be trained to recognize patterns indicative of malicious activity, such as phishing attempts or malware infections, enabling proactive threat mitigation.
For instance, an ML model trained on historical network traffic data can identify unusual communication patterns that may signal a denial-of-service attack, allowing security teams to take preventative measures before significant damage occurs. Furthermore, AI can automate incident response, reducing the time it takes to contain and remediate security breaches.
Blockchain Technology’s Role in Improving Data Security and Integrity
Blockchain’s decentralized and immutable nature offers significant advantages for enhancing data security and integrity. Its distributed ledger technology ensures that any changes to data are recorded and verifiable across the network, making it extremely difficult to tamper with information. This can be particularly beneficial for protecting sensitive data, such as intellectual property or financial records. For example, a company could use blockchain to securely track the provenance of its products, ensuring authenticity and preventing counterfeiting.
Each step in the supply chain could be recorded on the blockchain, creating a tamper-proof audit trail. Furthermore, blockchain can facilitate secure data sharing between organizations, allowing for collaboration while maintaining data confidentiality and integrity.
Internet of Things (IoT) Challenges and Opportunities in Enterprise Network Security
The proliferation of IoT devices within enterprise networks presents both opportunities and challenges for security. The sheer number and diversity of IoT devices, many of which lack robust security features, create a vast attack surface. These devices can be easily compromised, potentially providing attackers with a foothold into the enterprise network. For example, a compromised smart thermostat could be used to launch a denial-of-service attack against the company’s servers.
However, IoT devices also offer valuable data that can be used to improve security. IoT sensors can monitor network traffic and identify anomalies, providing early warnings of potential threats. Securely managing and integrating IoT devices requires a robust security strategy that includes device authentication, encryption, and regular firmware updates. Implementing a zero-trust security model, where every device is authenticated and authorized before accessing network resources, is crucial for mitigating the risks associated with IoT devices.
Regulatory Compliance and Legal Considerations
Navigating the complex world of enterprise information network security isn’t just about firewalls and intrusion detection systems; it’s also about understanding and adhering to a web of regulations and legal frameworks. Failure to comply can result in crippling fines, reputational damage, and even criminal prosecution. This section explores the key legal and regulatory aspects of securing enterprise information networks.
The legal landscape surrounding data security is constantly evolving, driven by increasing data breaches and a growing awareness of the potential harm caused by data misuse. Organizations must proactively manage their cybersecurity risks to minimize legal exposure and maintain public trust. A robust compliance program is essential, not just to avoid penalties but to foster a culture of security throughout the organization.
Key Regulatory Frameworks and Standards, Enterprise information networks and the threat environment
Numerous regulations govern the collection, storage, and processing of data, varying significantly based on industry, geography, and the type of data involved. Key frameworks include the General Data Protection Regulation (GDPR) in Europe, the Health Insurance Portability and Accountability Act (HIPAA) in the United States for healthcare data, and the California Consumer Privacy Act (CCPA) in the United States for consumer data.
These regulations establish stringent requirements for data security, breach notification, and data subject rights. For example, GDPR mandates organizations to implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk. HIPAA, on the other hand, focuses on the protection of protected health information (PHI) and requires organizations to implement safeguards to prevent unauthorized access, use, or disclosure.
Compliance necessitates a thorough understanding of the specific requirements applicable to the organization’s operations and the data it handles.
Legal Implications of Data Breaches and Security Failures
Data breaches can have severe legal consequences. Organizations may face lawsuits from affected individuals, regulatory fines, and reputational damage, impacting their bottom line and long-term viability. The legal implications depend on various factors, including the nature and scope of the breach, the type of data compromised, the organization’s response, and the applicable laws. For instance, a failure to comply with mandatory breach notification requirements under GDPR can lead to substantial fines.
Similarly, HIPAA violations can result in significant penalties and even criminal charges in severe cases. Legal action can also arise from negligence, failure to implement reasonable security measures, or failure to adequately respond to a breach.
Best Practices for Ensuring Regulatory Compliance
Maintaining regulatory compliance requires a proactive and multi-faceted approach. It’s not merely a checklist exercise but a continuous process of assessment, improvement, and adaptation.
- Conduct regular risk assessments: Identify vulnerabilities and potential threats to data security.
- Implement robust security controls: Employ a layered security approach incorporating firewalls, intrusion detection systems, access controls, data encryption, and employee training.
- Develop and maintain a comprehensive data security policy: This policy should Artikel procedures for data handling, access control, incident response, and breach notification.
- Establish a data breach response plan: This plan should detail steps to take in the event of a data breach, including notification procedures, forensic investigation, and remediation efforts.
- Provide regular employee training: Educate employees on security best practices and the importance of data protection.
- Monitor and audit security controls: Regularly assess the effectiveness of security measures and make necessary adjustments.
- Maintain accurate records: Document all security-related activities and compliance efforts.
The Role of Legal Counsel in Managing Cybersecurity Risks
Legal counsel plays a critical role in managing cybersecurity risks. Their expertise is crucial in navigating the complex regulatory landscape, interpreting legal requirements, and developing strategies to mitigate legal exposure.
- Conduct legal risk assessments: Identify potential legal liabilities related to data security.
- Develop and review data security policies: Ensure compliance with applicable laws and regulations.
- Provide guidance on incident response: Advise on the legal implications of data breaches and the appropriate response measures.
- Represent the organization in legal proceedings: Defend the organization against lawsuits or regulatory investigations.
- Stay informed on evolving legal and regulatory changes: Keep the organization abreast of changes in data protection laws and regulations.
Ultimate Conclusion
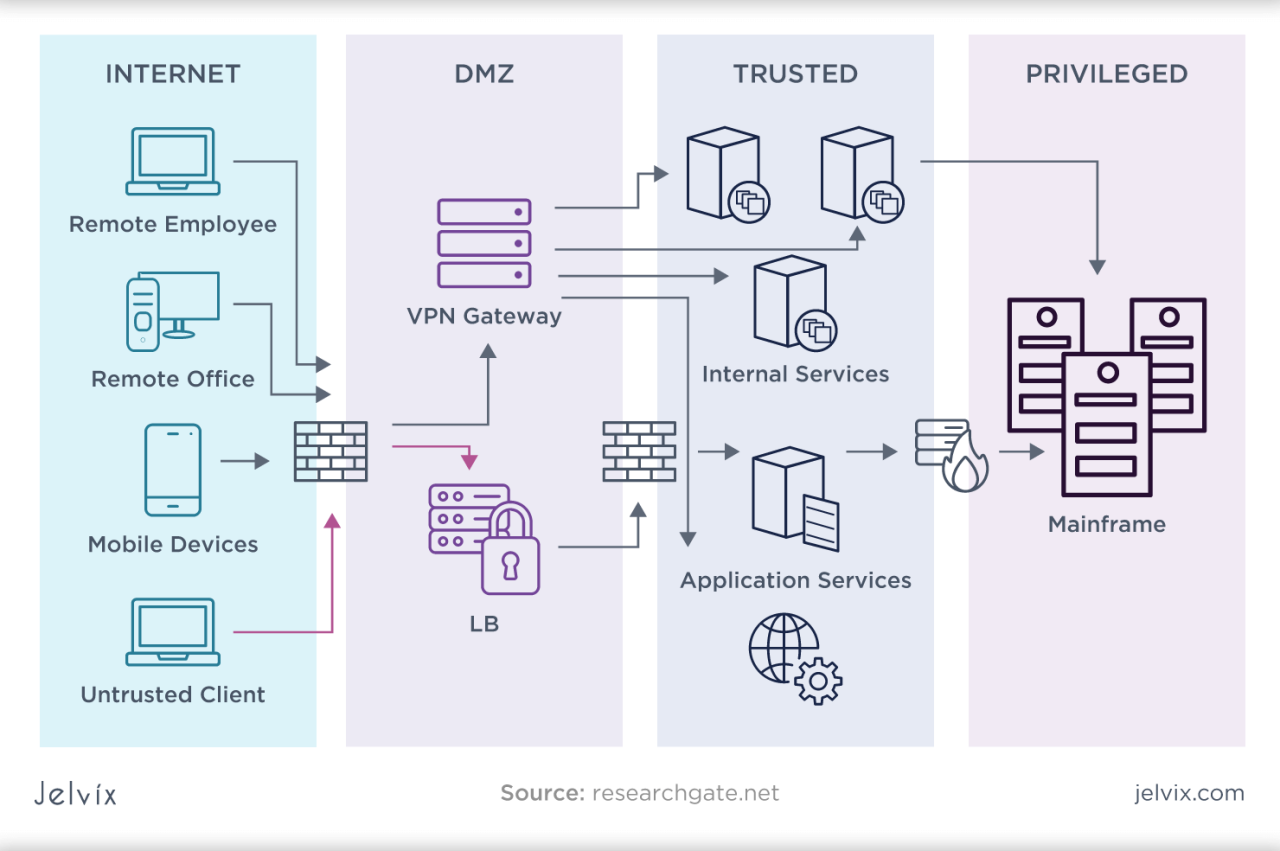
Securing your enterprise information network isn’t a one-time fix; it’s an ongoing process that requires vigilance, adaptation, and a multi-layered approach. By understanding the vulnerabilities, recognizing the evolving threats, and implementing robust security measures, organizations can significantly reduce their risk exposure. Remember, proactive security is not just about technology; it’s about people, processes, and a commitment to continuous improvement.
Staying informed, investing in training, and regularly reviewing your security posture are critical steps in protecting your valuable data and ensuring business continuity in today’s increasingly hostile digital world.
FAQ Corner
What is the difference between a vulnerability and a threat?
A vulnerability is a weakness in a system that can be exploited. A threat is a potential danger that could exploit that weakness. Think of it like a lock (system) with a broken latch (vulnerability) and a thief (threat) trying to open it.
How often should security audits be conducted?
The frequency of security audits depends on your industry, regulatory requirements, and risk tolerance. However, at a minimum, annual audits are recommended, with more frequent assessments for high-risk environments.
What is the role of a Chief Information Security Officer (CISO)?
A CISO is responsible for developing and implementing an organization’s overall cybersecurity strategy. They oversee security policies, risk management, incident response, and compliance with relevant regulations.
What are some common signs of a data breach?
Unusual login attempts, unauthorized access to systems, unusual network activity, missing or compromised data, and suspicious emails are all potential indicators of a data breach.