ESG Insights for Vulnerability Remediation
ESG insights for vulnerability remediation are no longer a niche topic; they’re a crucial element of responsible business practices. This post dives into how environmental, social, and governance (ESG) factors directly influence a company’s ability to identify, address, and prevent security vulnerabilities. We’ll explore the interconnectedness of sustainability initiatives and robust cybersecurity, examining how proactive ESG strategies can lead to stronger defenses against cyber threats and improve overall organizational resilience.
Get ready to rethink your approach to vulnerability management!
We’ll cover everything from integrating ESG into your existing vulnerability management lifecycle to leveraging cutting-edge technologies like AI and blockchain for enhanced security and transparency. We’ll also delve into reporting and disclosure, showing you how to effectively communicate your progress to stakeholders and demonstrate your commitment to both cybersecurity and ESG best practices. Think of this as your guide to building a more secure and sustainable future for your organization.
ESG Risks and Vulnerability Remediation
Effective vulnerability remediation is no longer solely an IT concern; it’s deeply intertwined with a company’s Environmental, Social, and Governance (ESG) performance. Ignoring the ESG implications of cybersecurity risks can lead to significant financial losses, reputational damage, and legal repercussions. This discussion explores the crucial connections between ESG factors and vulnerability management, highlighting the need for a holistic and integrated approach.
Three Major ESG Factors Impacting Vulnerability Remediation Strategies
Environmental, social, and governance factors significantly influence a company’s capacity to effectively identify, address, and mitigate IT vulnerabilities. Failing to consider these interconnected factors can lead to incomplete remediation strategies and increased exposure to risk.
- Climate Change: Extreme weather events can disrupt IT infrastructure, leading to data loss and operational downtime. Vulnerabilities in backup systems and disaster recovery plans exacerbate these risks.
- Supply Chain Ethics: Relying on unethical or unsustainable supply chains can introduce vulnerabilities through compromised components or inadequate security practices within the supplier’s ecosystem. This includes issues such as the use of conflict minerals or lack of security certifications.
- Employee Training and Awareness: A lack of employee training on cybersecurity best practices creates significant vulnerabilities. Phishing attacks, social engineering, and insider threats are all amplified by inadequate security awareness.
The Relationship Between Environmental Risks and IT Infrastructure Vulnerabilities
Climate change poses a direct threat to IT infrastructure. Rising sea levels, extreme heat, and severe weather events can damage data centers, disrupt network connectivity, and cause widespread outages. For example, Hurricane Sandy in 2012 caused significant damage to New York City’s IT infrastructure, highlighting the vulnerability of critical systems to extreme weather. The lack of robust disaster recovery plans and resilient infrastructure increases the risk of prolonged downtime and data loss, resulting in substantial financial and reputational damage.
Furthermore, the increased reliance on renewable energy sources introduces new vulnerabilities that need to be addressed through effective risk management and remediation strategies.
How Social Factors Influence Vulnerability Remediation Effectiveness
Social factors, particularly employee training and supply chain ethics, play a critical role in effective vulnerability remediation. Inadequate employee training on cybersecurity best practices increases the likelihood of successful phishing attacks, malware infections, and insider threats. Similarly, unethical or unsustainable supply chain practices can introduce vulnerabilities through the use of counterfeit or compromised components. Companies must prioritize employee training programs that emphasize security awareness and implement robust supply chain risk management processes to mitigate these risks.
For example, a company that relies on a supplier with weak security practices is more vulnerable to supply chain attacks.
Governance Aspects Impacting Vulnerability Management and ESG Compliance
Effective governance is essential for integrating ESG considerations into vulnerability management. Different governance models influence a company’s ability to identify, assess, and mitigate ESG-related vulnerabilities.
| Governance Model | Strengths | Weaknesses | Effectiveness in Mitigating ESG-Related Vulnerabilities |
|---|---|---|---|
| Compliant-only | Meets minimum regulatory requirements. | Limited proactive risk management. Focuses on compliance rather than holistic risk mitigation. | Low |
| Best-Practice Based | Adopts industry best practices and standards. | Can be complex and resource-intensive to implement. | Medium |
| Integrated ESG | Embeds ESG considerations into all aspects of the business, including vulnerability management. | Requires significant organizational change and commitment. | High |
| Proactive and Predictive | Utilizes advanced analytics and threat intelligence to anticipate and mitigate future risks. | Requires significant investment in technology and expertise. | High |
Integrating ESG into Vulnerability Management Programs: Esg Insights For Vulnerability Remediation
Integrating Environmental, Social, and Governance (ESG) factors into vulnerability management isn’t just a trend; it’s a crucial step towards building resilient and responsible organizations. By acknowledging the interconnectedness of IT security and broader societal impacts, businesses can proactively mitigate risks and enhance their overall ESG performance. This approach moves beyond simply patching vulnerabilities to understanding the wider consequences of security breaches and prioritizing remediation based on both technical severity and ESG implications.
A robust framework is essential for effectively integrating ESG considerations into your existing vulnerability management lifecycle. This requires a holistic approach, moving beyond traditional technical assessments to encompass social and environmental impacts. This involves analyzing the potential consequences of a vulnerability exploit, considering not only financial losses but also reputational damage, employee safety, and environmental consequences.
A Framework for Integrating ESG Considerations
This framework integrates ESG considerations into the traditional vulnerability management lifecycle (identification, assessment, remediation, reporting). The key is to map ESG risks to specific vulnerabilities and prioritize remediation efforts accordingly. For example, a vulnerability affecting a critical system managing environmental data would be prioritized higher than a less critical vulnerability in a non-essential system, due to the environmental implications of the former.
Similarly, vulnerabilities impacting sensitive employee data would be prioritized based on social implications.
Conducting an ESG-Integrated Risk Assessment
A step-by-step procedure for conducting a risk assessment that integrates IT security vulnerabilities and ESG factors is crucial.
- Identify Vulnerabilities: Conduct standard vulnerability scans and penetration testing to identify existing security weaknesses.
- ESG Impact Assessment: For each identified vulnerability, assess its potential impact across ESG dimensions. This might involve considering the potential for data breaches leading to reputational damage (Social), environmental damage from system failure (Environmental), or governance failures related to non-compliance (Governance).
- Risk Prioritization: Prioritize vulnerabilities based on a combined score considering both technical severity and ESG impact. A weighted scoring system could be used, assigning different weights to technical severity and ESG impact based on organizational priorities.
- Remediation Planning: Develop a remediation plan outlining steps to mitigate the identified vulnerabilities, taking into account the ESG implications. This includes timelines, resource allocation, and communication strategies.
- Monitoring and Reporting: Regularly monitor the effectiveness of remediation efforts and report on progress to stakeholders. This reporting should include both technical and ESG metrics.
Communicating ESG-Related Vulnerability Remediation Efforts
Effective communication is paramount. Transparency builds trust with stakeholders.
Stakeholder communication should be tailored to their specific needs and interests. Investors will be interested in financial risks and the organization’s resilience. Employees need to understand their roles in security and the impact of vulnerabilities. Customers need assurance that their data is protected.
Regular reporting, including both quantitative and qualitative data, demonstrates commitment and allows for continuous improvement. This might include metrics such as the number of vulnerabilities remediated, the reduction in ESG-related risks, and improved stakeholder satisfaction.
Comparison of Traditional and ESG-Integrated Vulnerability Management
| Feature | Traditional Vulnerability Management | ESG-Integrated Vulnerability Management | Key Differences |
|---|---|---|---|
| Focus | Technical security vulnerabilities | Technical security vulnerabilities and their ESG implications | Expands scope beyond technical to include broader societal and environmental considerations. |
| Risk Assessment | Primarily based on technical severity | Considers both technical severity and ESG impact | Prioritization considers broader impacts beyond technical factors. |
| Remediation Prioritization | Based on technical severity and business impact | Based on a combined score of technical severity and ESG impact | Prioritizes vulnerabilities with significant ESG implications, even if technically less severe. |
| Reporting | Focuses on technical metrics | Includes both technical and ESG metrics | Provides a more holistic view of security performance and its impact on ESG goals. |
ESG Reporting and Disclosure of Vulnerability Remediation Efforts
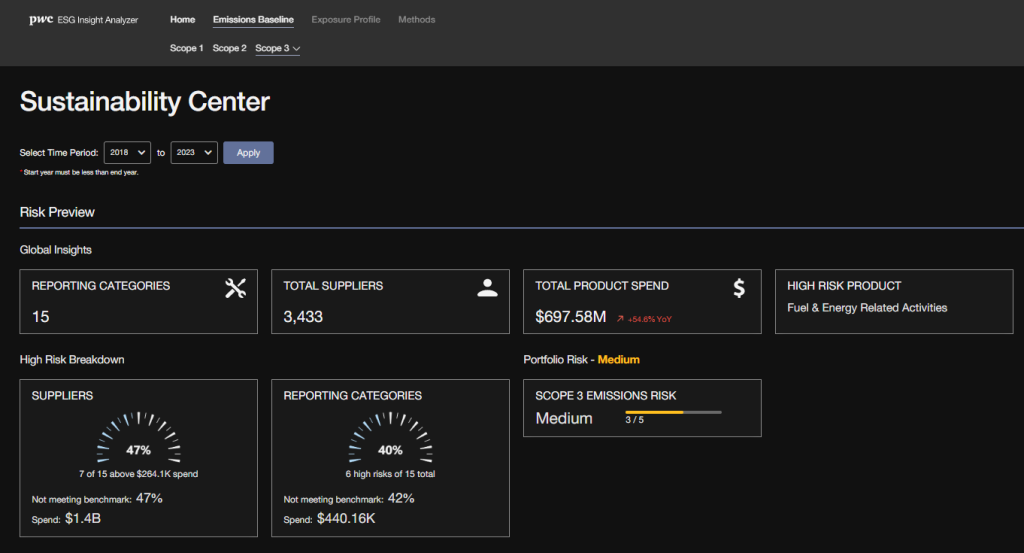
Effective ESG reporting on vulnerability remediation demonstrates a company’s commitment to transparency and accountability in managing its cybersecurity risks. This goes beyond simply stating that vulnerabilities are addressed; it requires quantifiable metrics and a clear demonstration of progress towards a more secure and resilient organization. This section explores how to effectively measure, report, and visualize these efforts.
Measuring the effectiveness of an ESG-integrated vulnerability remediation program necessitates the use of key performance indicators (KPIs). These KPIs provide tangible evidence of progress and allow stakeholders to assess the impact of the implemented strategies. Reporting these KPIs in accordance with established frameworks like the Global Reporting Initiative (GRI) and the Sustainability Accounting Standards Board (SASB) ensures consistency and comparability across organizations.
Key Performance Indicators for Vulnerability Remediation
Selecting the right KPIs is crucial for accurate and meaningful reporting. The following KPIs offer a comprehensive overview of vulnerability management and remediation efforts:
- Mean Time To Remediation (MTTR): This metric measures the average time taken to resolve a vulnerability from the moment it’s identified. A lower MTTR indicates a more efficient and responsive remediation process.
- Number of Critical Vulnerabilities Remediated: Prioritizing critical vulnerabilities is essential. Tracking the number remediated demonstrates focus on the most significant risks.
- Percentage of Vulnerabilities Remediated within Defined SLAs: Setting service level agreements (SLAs) for remediation ensures timely action. This KPI measures adherence to those SLAs.
- Vulnerability Density: This KPI tracks the number of vulnerabilities per device or system, providing insight into the overall security posture.
- Reduction in Security Incidents Due to Remediation Efforts: This directly links remediation efforts to a reduction in actual security breaches, demonstrating the program’s effectiveness.
Reporting on ESG-Related Vulnerabilities and Remediation Activities
Reporting on ESG-related vulnerabilities and remediation activities requires alignment with relevant frameworks like GRI and SASB. GRI Standards focus on environmental, social, and governance performance, while SASB Standards provide industry-specific metrics. Both frameworks emphasize transparency and materiality, meaning only relevant information needs to be reported. For example, a financial institution would likely report on cybersecurity vulnerabilities more prominently than a retail company, reflecting the differing levels of risk and impact.
Sample ESG Report Section: Vulnerability Remediation
The following is an example of how vulnerability remediation efforts could be presented in an ESG report. This section highlights quantifiable results and demonstrates progress over time:
Vulnerability Remediation: Strengthening Our Cybersecurity Posture
Our commitment to cybersecurity is integral to our ESG strategy. We actively manage and remediate vulnerabilities to protect our assets, data, and stakeholders. Key achievements in the past fiscal year include:
- Reduced Mean Time To Remediation (MTTR) by 25%, from 72 hours to 54 hours.
- Remediated 98% of critical vulnerabilities identified.
- Achieved 95% compliance with established SLAs for vulnerability remediation.
- Decreased vulnerability density by 15% across our critical infrastructure.
- Experienced a 20% reduction in security incidents directly attributable to improved vulnerability management.
Data Visualization for Vulnerability Remediation Progress
Effective communication of ESG-related vulnerability remediation progress requires clear and concise data visualization. A compelling visual representation can significantly improve stakeholder understanding and engagement.
Consider a dashboard showing key KPIs over time. For example, a line graph could illustrate the trend of MTTR reduction over the past three years. A bar chart could compare the number of critical, high, medium, and low vulnerabilities remediated during the reporting period. A pie chart could represent the percentage of vulnerabilities remediated within SLAs versus those exceeding SLAs.
Color-coding can further highlight progress (e.g., green for improved metrics, red for areas needing attention). This comprehensive dashboard, combining various chart types, provides a holistic view of vulnerability remediation performance and facilitates effective communication with stakeholders.
Technological Solutions for ESG-Driven Vulnerability Remediation
The integration of technology is crucial for effectively addressing ESG risks related to vulnerabilities. Emerging technologies offer powerful tools to enhance vulnerability detection, remediation, and reporting, ultimately improving an organization’s ESG performance and bolstering stakeholder trust. This section will explore how specific technologies contribute to a more robust and efficient vulnerability management program aligned with ESG principles.
AI and Machine Learning in Vulnerability Detection and Remediation
AI and machine learning (ML) are transforming vulnerability management by automating and accelerating several key processes. These technologies can analyze vast amounts of data from various sources – including network traffic, log files, and security assessments – to identify patterns and anomalies indicative of vulnerabilities. This proactive approach allows for quicker detection of potential threats, reducing the window of opportunity for exploitation.
Furthermore, ML algorithms can prioritize vulnerabilities based on their severity and potential ESG impact, allowing organizations to focus resources on the most critical risks. For example, an ML model could identify vulnerabilities affecting sensitive customer data, thus prioritizing remediation efforts to comply with data privacy regulations and avoid reputational damage, both key ESG considerations. The integration of AI and ML also allows for the automation of remediation tasks, such as patching systems and configuring security settings, improving efficiency and reducing human error.
Blockchain Technology for Enhanced Transparency and Accountability
Blockchain technology, known for its immutability and transparency, offers a powerful solution for improving accountability in ESG-related vulnerability management. A blockchain-based system can create a permanent and auditable record of all vulnerability discoveries, remediation efforts, and related ESG impacts. This provides increased transparency to stakeholders, demonstrating the organization’s commitment to addressing vulnerabilities and mitigating associated risks. For example, a company could use a blockchain to record the details of a vulnerability discovered in its supply chain, the steps taken to remediate it, and the resulting reduction in environmental or social impact.
This verifiable record enhances trust and accountability, improving the organization’s ESG rating and reputation. Moreover, blockchain can facilitate secure and efficient sharing of vulnerability information among different stakeholders, improving collaborative efforts in vulnerability remediation across the supply chain.
Automation in ESG-Driven Vulnerability Remediation
Automation plays a vital role in improving the efficiency and effectiveness of ESG-driven vulnerability remediation. By automating various tasks, organizations can reduce the time and resources required to address vulnerabilities, freeing up security personnel to focus on more strategic initiatives.
Here are some examples of how automation can enhance ESG-driven vulnerability remediation:
- Automated Vulnerability Scanning and Reporting: Regularly scheduled automated scans identify vulnerabilities across systems and networks, generating reports that highlight critical risks and prioritize remediation efforts based on their ESG impact.
- Automated Patching and Configuration Management: Automated systems can deploy patches and updates to address identified vulnerabilities, reducing the window of vulnerability and minimizing downtime. This is particularly crucial for critical infrastructure and systems with significant ESG implications.
- Automated Incident Response: Automated systems can detect and respond to security incidents, minimizing the impact of breaches and preventing further damage. This reduces the risk of data breaches and reputational damage, key ESG concerns.
- Automated ESG Reporting: Automation can streamline the process of collecting and analyzing data related to vulnerability management and its ESG implications, generating reports that comply with relevant standards and frameworks.
Case Studies and Best Practices
Integrating ESG considerations into vulnerability remediation isn’t just a trend; it’s a necessity for responsible and resilient organizations. This section explores real-world examples of successful integration, highlighting challenges overcome and best practices to emulate. We’ll then analyze these case studies to identify common themes and strategies for optimizing your own ESG performance through enhanced vulnerability management.
Case Study 1: Financial Institution Strengthening Data Security
This large financial institution faced increasing pressure from regulators and investors to improve its cybersecurity posture and demonstrate its commitment to ESG principles. Their challenge was twofold: a legacy IT infrastructure with numerous vulnerabilities and a lack of clear processes for prioritizing remediation based on both financial and environmental/social impact. Their solution involved a multi-pronged approach: first, a comprehensive vulnerability scan identified critical weaknesses across their systems.
Second, a risk assessment framework was developed that weighted vulnerabilities based on their potential financial impact (e.g., fines, data breaches), environmental impact (e.g., carbon footprint of remediation efforts), and social impact (e.g., reputational damage). Finally, they implemented a phased remediation plan, prioritizing the most impactful vulnerabilities first. The outcome was a significant reduction in vulnerabilities, improved regulatory compliance, enhanced investor confidence, and a demonstrably lower environmental footprint due to optimized remediation processes.
Case Study 2: Tech Company Prioritizing Supply Chain Security
A global technology company recognized the significant ESG risks associated with its extensive supply chain. Their challenge was to assess and mitigate vulnerabilities within their supplier network, ensuring responsible sourcing and ethical manufacturing practices. Their solution involved implementing a robust supplier security assessment program, requiring all suppliers to undergo regular security audits and vulnerability assessments. They also developed a clear escalation path for addressing critical vulnerabilities, working collaboratively with suppliers to remediate identified issues.
The outcome was a strengthened supply chain security posture, improved supplier relationships, and reduced risk of disruptions due to security breaches. Furthermore, this improved transparency throughout the supply chain led to more sustainable and ethical sourcing practices, contributing positively to their ESG performance.
Case Study 3: Energy Company Reducing Operational Risks, Esg insights for vulnerability remediation
A major energy company faced increasing scrutiny regarding its operational safety and environmental impact. Their challenge involved identifying and mitigating vulnerabilities in their critical infrastructure, reducing the risk of environmental accidents and ensuring business continuity. Their solution involved implementing a comprehensive cybersecurity and physical security program that incorporated risk assessments based on environmental, social, and governance factors. This included investing in advanced threat detection systems, improving employee training on security protocols, and strengthening physical security measures at critical facilities.
The outcome was a demonstrably lower risk of operational disruptions, reduced environmental impact, and enhanced safety for employees and the surrounding community. This improved safety record also positively impacted their investor relations and public image.
Best Practices for Enhancing ESG Performance Through Vulnerability Management
Effective vulnerability management is crucial for improving ESG performance. A proactive approach, focusing on prevention and mitigation, is far more effective and cost-efficient than reactive measures. Here are some best practices:
- Conduct regular vulnerability assessments and penetration testing.
- Develop a robust risk assessment framework that incorporates ESG factors.
- Prioritize vulnerabilities based on their potential financial, environmental, and social impact.
- Implement a phased remediation plan, focusing on the most critical vulnerabilities first.
- Establish clear communication channels with stakeholders, including investors, regulators, and employees.
- Invest in employee training and awareness programs to reduce human error.
- Regularly review and update your vulnerability management program to adapt to evolving threats.
- Integrate vulnerability management into your broader ESG strategy and reporting.
Comparison of Case Study Approaches
The following table compares and contrasts the approaches used in the three case studies, highlighting common themes and best practices:
| Case Study | Challenge | Solution | Outcome |
|---|---|---|---|
| Financial Institution | Legacy infrastructure, lack of ESG-integrated prioritization | Comprehensive vulnerability scan, ESG-weighted risk assessment, phased remediation | Reduced vulnerabilities, improved compliance, enhanced investor confidence, lower environmental footprint |
| Tech Company | Supply chain vulnerabilities | Supplier security assessment program, collaborative remediation | Strengthened supply chain security, improved supplier relationships, more sustainable sourcing |
| Energy Company | Operational safety and environmental risks | Comprehensive cybersecurity and physical security program, ESG-based risk assessment | Reduced operational disruptions, lower environmental impact, enhanced safety |
Ending Remarks

Successfully integrating ESG considerations into your vulnerability remediation strategy isn’t just about ticking boxes; it’s about building a more resilient, ethical, and sustainable organization. By understanding the interplay between ESG factors and cybersecurity, you can proactively mitigate risks, enhance your reputation, and contribute to a more secure digital world. Remember, a robust cybersecurity posture is an integral part of responsible business, and adopting an ESG-informed approach is the key to unlocking a future where security and sustainability go hand in hand.
Start incorporating these insights today – your organization (and the planet) will thank you.
FAQ Resource
What are the potential financial implications of neglecting ESG factors in vulnerability remediation?
Ignoring ESG in vulnerability management can lead to significant financial losses from data breaches, regulatory fines, reputational damage, and investor distrust. Proactive ESG integration, however, can lead to cost savings through improved efficiency and reduced risk.
How can small businesses effectively implement ESG-driven vulnerability remediation?
Small businesses can start by conducting a basic risk assessment, focusing on high-impact vulnerabilities and prioritizing employee training. They can also leverage free or low-cost tools and resources, and collaborate with other businesses to share best practices.
What are the key differences between traditional and ESG-integrated vulnerability management reporting?
Traditional reporting focuses solely on technical aspects of vulnerability management. ESG-integrated reporting expands this to include the social and environmental impact of vulnerabilities and remediation efforts, aligning with relevant frameworks like GRI and SASB.