EU Proposes Joint Cyber Unit for Large-Scale Attacks
European Union proposes joint cyber unit for large scale cyber attacks – a bold move in the face of increasingly sophisticated digital threats! Imagine a unified EU force, ready to tackle massive cyberattacks that could cripple entire nations. This isn’t just about theoretical risks; we’re talking about real-world scenarios, from crippling infrastructure to widespread data breaches. The proposal Artikels a new joint cyber unit, aiming to coordinate defenses and responses across all member states.
But will it be enough? And what are the potential implications for national sovereignty and individual privacy?
The plan details a structure for this unit, outlining its mandate, responsibilities, and how it will interact with existing national cyber defense systems. It addresses the crucial technological capabilities needed to effectively combat these attacks, as well as strategies for coordinating responses across borders. Naturally, there are significant legal and ethical considerations to navigate, particularly regarding cross-border operations and the potential for conflicts with existing international laws.
The Proposed Joint Cyber Unit
The European Union’s proposal for a joint cyber unit represents a significant step towards bolstering collective cybersecurity defenses against increasingly sophisticated and large-scale cyberattacks. This move reflects a growing recognition that a coordinated, EU-wide response is necessary to effectively counter threats that transcend national borders. The unit aims to enhance cooperation, resource sharing, and the overall effectiveness of cyber defense efforts across the bloc.
Proposed Structure and Mandate of the Joint Cyber Unit
The exact organizational structure of the proposed unit is still under development, but initial proposals suggest a tiered system. A central coordinating body, likely located in Brussels, would oversee operations and strategy. This central body would be supported by national cyber defense teams contributing expertise and resources. The level of integration between the central body and national teams will be a key factor in determining the unit’s overall effectiveness.
The unit’s mandate would encompass a broad range of activities, including threat intelligence gathering and sharing, incident response coordination, and the development of common cybersecurity standards and best practices. Furthermore, it would likely play a crucial role in conducting joint cyber exercises and capacity building initiatives for member states.
Comparison with Existing National Cyber Defense Structures
Currently, each EU member state maintains its own national cyber defense structures, varying significantly in size, capabilities, and resources. Some countries possess highly developed and well-funded national cyber agencies, while others have more limited capabilities. The proposed joint unit aims to address this disparity by providing a framework for cooperation and resource pooling, thereby strengthening the overall cybersecurity posture of the EU.
The success of this initiative will depend on the ability to harmonize diverse national approaches and ensure effective communication and collaboration across different organizational structures and legal frameworks. This will require careful consideration of national sovereignty concerns and the need to avoid duplication of efforts.
Potential Powers, Limitations, and Reporting Structures of the Joint Cyber Unit
| Power | Limitation | Reporting Structure |
|---|---|---|
| Coordinate incident response across member states | Limited direct operational control over national cyber defense teams | Reports to the European Commission and potentially a newly created EU cybersecurity council. |
| Develop and implement common cybersecurity standards | Requires consensus among member states on policies and procedures | Subject to oversight by the European Parliament and Council of the European Union. |
| Share threat intelligence and best practices | Data privacy concerns and the need to protect sensitive information | Internal reporting mechanisms and potentially external audits. |
| Conduct joint cyber exercises and training | Requires significant investment in resources and infrastructure | Transparency and accountability mechanisms to ensure effectiveness and prevent abuse of power. |
Responding to Large-Scale Cyber Attacks
The proposed EU joint cyber unit represents a significant step towards bolstering the continent’s collective defense against increasingly sophisticated and devastating cyberattacks. Its effectiveness will hinge on its ability to rapidly respond to a wide range of threats, coordinating actions across multiple member states with diverse technological capabilities and legal frameworks. This requires a clear understanding of the types of attacks it will face, the necessary technological infrastructure, and robust strategies for cross-border collaboration.The unit is designed to address a broad spectrum of large-scale cyberattacks, ranging from widespread denial-of-service (DDoS) attacks crippling critical infrastructure to targeted intrusions aimed at stealing sensitive data or disrupting governmental operations.
These attacks can be financially motivated, politically driven, or even part of a state-sponsored campaign. The scale of the threat necessitates a coordinated, multi-national response exceeding the capabilities of any single member state.
Types of Large-Scale Cyber Attacks Addressed
The unit will need to be prepared for various attack vectors. These include large-scale DDoS attacks targeting government websites, financial institutions, or essential services like power grids and healthcare systems. Sophisticated advanced persistent threats (APTs), often state-sponsored, aiming to infiltrate networks and steal intellectual property or sensitive data, also fall within its remit. Supply chain attacks, compromising software or hardware used across multiple organizations, will require a coordinated response to mitigate the widespread impact.
The EU’s proposal for a joint cyber unit to combat large-scale attacks is a crucial step, highlighting the growing need for robust cybersecurity infrastructure. This initiative underscores the importance of proactive security measures, especially given the increasing reliance on cloud services. Understanding how solutions like Bitglass, as detailed in this insightful article on bitglass and the rise of cloud security posture management , can bolster defenses is key to effectively supporting the EU’s ambitious plan to fight off sophisticated cyber threats.
Ultimately, a strong collective response, bolstered by advanced cloud security, is our best defense.
Finally, ransomware attacks targeting critical infrastructure or large corporations, demanding substantial ransoms and potentially causing significant disruption, are a major concern.
Examples of Scenarios Requiring Intervention
Imagine a coordinated ransomware attack targeting multiple hospitals across several EU member states, encrypting patient records and disrupting essential medical services. The joint cyber unit would be crucial in coordinating a response, sharing intelligence, and potentially providing technical assistance to affected hospitals. Alternatively, a massive DDoS attack could overwhelm the online banking systems of multiple countries, causing widespread financial disruption.
The unit’s expertise in mitigating DDoS attacks and identifying the source would be vital in restoring services and preventing further damage. A final example would be a sophisticated APT campaign targeting multiple government agencies across the EU, aiming to steal sensitive information or disrupt governmental operations. The unit would play a key role in identifying the threat actors, containing the breach, and preventing further compromise.
Technological Capabilities Required
To be effective, the joint cyber unit will require advanced technological capabilities. This includes robust threat intelligence platforms to monitor and analyze cyber threats across the EU, enabling proactive identification of potential attacks. The unit will also need sophisticated incident response tools to quickly contain and mitigate ongoing attacks, including forensic capabilities to investigate breaches and attribute attacks to their perpetrators.
Furthermore, secure communication channels and data sharing mechanisms are crucial for effective collaboration between member states. Finally, access to and expertise in utilizing cutting-edge technologies like AI and machine learning for threat detection and response will be vital.
Strategies for Coordinating Responses Across Multiple EU Member States
Effective coordination across multiple EU member states is paramount. This necessitates the establishment of clear communication protocols and standardized procedures for incident reporting and response. A centralized platform for sharing threat intelligence and coordinating responses would be essential. Legal frameworks need to be harmonized to ensure seamless data sharing and cross-border collaboration, while respecting individual member state sovereignty.
Regular joint exercises and training programs will be crucial in developing effective coordination mechanisms and building trust among participating nations. The establishment of clear roles and responsibilities for each member state within the unit’s structure is also critical to avoid confusion and ensure efficient operations.
Legal and Ethical Considerations
The proposal for a joint EU cyber unit raises significant legal and ethical questions. Successfully navigating these complexities is crucial for the unit’s legitimacy and effectiveness. Failure to do so could lead to international disputes, erode public trust, and ultimately undermine the unit’s mission. A careful consideration of existing legal frameworks and ethical principles is paramount.The establishment and operation of a cross-border cyber unit present a multitude of legal challenges.
Jurisdictional issues are particularly thorny. Determining which nation’s laws apply when a cyberattack originates in one country, transits through others, and targets a system in yet another creates significant complexity. Data protection laws, varying widely across EU member states, present another hurdle. The unit must ensure compliance with the GDPR and other relevant regulations, potentially requiring complex data handling protocols and cross-border data transfer agreements.
Furthermore, the unit’s powers of investigation and response must be clearly defined within a legal framework that respects individual rights and avoids exceeding its mandate. The potential for conflicts with national sovereignty must also be carefully addressed.
Jurisdictional Challenges in Cross-Border Cyber Operations
Establishing clear jurisdictional rules for the joint cyber unit’s actions is crucial. The unit’s operations must comply with the laws of all involved nations. This necessitates international cooperation and agreement on which jurisdiction has primary responsibility in specific scenarios. The absence of a unified international legal framework for cybersecurity exacerbates this problem. For example, a cyberattack originating in Russia, passing through servers in Germany, and targeting a French bank would require careful coordination and agreement between the three countries regarding the investigation and response.
Existing international treaties, like the Budapest Convention on Cybercrime, provide a framework, but they lack the comprehensive scope needed for large-scale, cross-border operations.
Ethical Implications of Cross-Border Cyber Operations
The ethical implications of cross-border cyber operations are substantial. The potential for misuse of power, disproportionate responses, and violations of privacy are significant concerns. The unit must adhere to strict ethical guidelines to ensure its actions are proportionate, necessary, and respectful of human rights. Transparency and accountability are vital. Clear procedures for authorization, oversight, and reporting are necessary to prevent abuse.
For instance, the unit must establish clear criteria for deciding when to intervene in a cyberattack, considering the potential collateral damage and the proportionality of its response. The risk of inadvertently targeting innocent parties or exceeding the scope of legitimate self-defense needs careful mitigation.
Procedures for Ensuring Legal and Ethical Compliance
To ensure compliance, the unit should establish robust internal procedures. These procedures should include rigorous pre-authorization processes for any cyber operation, detailed documentation of all actions, and independent oversight mechanisms. Regular audits and external reviews can help maintain transparency and accountability. Ethical guidelines should be clearly defined and regularly reviewed, taking into account evolving technologies and legal precedents.
Training programs for unit personnel should emphasize the importance of adhering to legal and ethical standards. A clear complaints mechanism, accessible to affected individuals and organizations, is also essential for addressing potential grievances.
Comparison with Existing International Laws and Treaties
The unit’s actions must be compatible with existing international laws and treaties, including the Budapest Convention on Cybercrime and the Charter of the United Nations. This requires careful analysis of the legal basis for each operation to ensure compliance with international norms. Any action taken should respect state sovereignty and avoid actions that could be interpreted as an infringement upon the jurisdiction of other nations.
The unit’s mandate should be clearly defined and limited to activities explicitly authorized by international law and the EU’s legal framework. The potential for conflicts with national laws requires careful consideration and preemptive measures to ensure harmonious cooperation.
Resource Allocation and Funding

Establishing and maintaining a joint EU cyber unit to combat large-scale attacks will require significant financial investment and careful resource allocation. The costs involved are multifaceted and will depend on the unit’s size, scope, and technological capabilities. A robust funding model is crucial for ensuring the unit’s effectiveness and long-term sustainability.The estimated costs associated with creating and running this unit are substantial and encompass several key areas.
These include salaries for highly skilled cybersecurity professionals (analysts, engineers, incident responders), investment in advanced technologies (threat intelligence platforms, intrusion detection systems, incident response tools), infrastructure development (secure data centers, communication networks), and ongoing training and professional development for staff. A realistic budget would need to consider initial setup costs, annual operational expenses, and potential costs associated with responding to major cyber incidents.
We can reasonably expect initial setup costs to run into the tens of millions of Euros, with annual operational budgets potentially reaching hundreds of millions depending on the unit’s scale and ambition. For example, comparable national cyber security agencies often have budgets in the hundreds of millions annually. This joint unit, operating at a pan-European level, would necessitate a considerably larger budget.
Potential Funding Sources
Several funding mechanisms could support the joint cyber unit. Direct contributions from member states, based on their GDP or cyber threat exposure, are a primary option. The EU budget itself could also contribute significantly, perhaps through existing cybersecurity programs or new initiatives specifically dedicated to the unit. Additional funding avenues might include public-private partnerships, where private sector companies specializing in cybersecurity contribute resources or expertise in exchange for access to the unit’s intelligence or services.
Innovative funding models could also be explored, such as a dedicated cyber security tax on relevant industries or a levy on cross-border data transfers. The optimal mix of these sources will require careful consideration of political feasibility, economic impact, and the need for sustainable long-term funding.
Resource Allocation Models Across Member States
Different models can be employed to distribute resources among participating member states. A proportional model, based on each state’s GDP, could ensure larger economies contribute more financially. However, this approach might not accurately reflect a state’s cyber threat exposure or its capacity to contribute skilled personnel. An alternative model could prioritize resource allocation based on a state’s assessed vulnerability to cyberattacks, allocating more resources to countries deemed more at risk.
A third approach could involve a hybrid model, combining GDP-based contributions with a risk-based allocation of specific resources like personnel or specialized equipment. The chosen model should strive for fairness, efficiency, and ensure that all member states perceive the process as equitable.
Comparison of Funding Models
| Funding Model | Advantages | Disadvantages | Example |
|---|---|---|---|
| GDP-Based Contribution | Simple, transparent, reflects economic capacity | May not reflect cyber risk or capability differences | Germany contributes a larger share than Malta based on relative GDP |
| Risk-Based Allocation | Prioritizes resources to most vulnerable states | Difficult to objectively assess cyber risk, potential for political disputes | Estonia receives more resources due to its higher perceived cyber threat exposure |
| Hybrid Model (GDP & Risk-Based) | Balances economic capacity with cyber risk | Complex to implement, requires sophisticated risk assessment | France contributes a significant portion based on GDP, but receives additional resources due to specific critical infrastructure vulnerabilities |
| Public-Private Partnerships | Leverages private sector expertise and resources | Potential conflicts of interest, dependence on private sector goodwill | Cybersecurity firms provide specialized tools and training in exchange for access to threat intelligence |
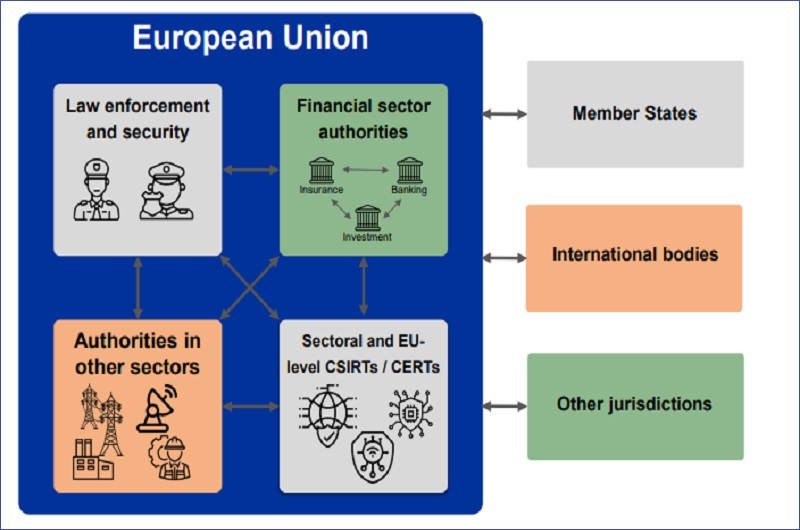
International Cooperation and Partnerships: European Union Proposes Joint Cyber Unit For Large Scale Cyber Attacks
The proposed EU joint cyber unit’s effectiveness hinges significantly on its ability to collaborate internationally. Effective cybersecurity in the 21st century transcends national borders; threats are often transnational, requiring a coordinated global response. International partnerships aren’t merely beneficial – they are essential for combating large-scale cyberattacks effectively.International collaboration in cybersecurity offers several avenues for enhancing the EU’s capabilities.
Sharing threat intelligence, coordinating responses to major incidents, and jointly developing defensive technologies are all key areas where partnerships can yield significant returns. However, challenges such as differing national legal frameworks, varying levels of cybersecurity maturity, and concerns about data sovereignty must be addressed to ensure successful collaborations.
Potential Partners for Information Sharing and Joint Operations
Several international organizations and individual nations present themselves as ideal partners for the EU’s joint cyber unit. Organizations like Interpol, Europol, and NATO already possess established frameworks for international cooperation in law enforcement and security, providing a solid foundation for cyber-related collaboration. Furthermore, partnerships with countries possessing advanced cybersecurity capabilities, such as the United States, Israel, and the United Kingdom, could provide access to cutting-edge technologies and expertise.
Bilateral agreements with individual nations facing similar cyber threats could also prove highly beneficial. The EU could also explore collaborations with private sector cybersecurity companies with global reach, leveraging their expertise and resources.
Benefits and Challenges of International Cooperation in Cybersecurity
The benefits of international cooperation are numerous. Improved threat intelligence sharing leads to earlier detection and mitigation of attacks. Joint operations allow for a more coordinated and effective response to large-scale incidents, reducing the overall impact. Collaborative research and development can lead to advancements in cybersecurity technologies that benefit all participating entities. Furthermore, enhanced trust and confidence among nations in their shared cybersecurity posture can help deter malicious actors.However, challenges remain.
Differing national laws and regulations regarding data privacy and sharing can create obstacles. Concerns about national sovereignty and the potential for sensitive information to be compromised can inhibit cooperation. Building trust and establishing clear communication channels are also crucial but can be time-consuming. Harmonizing cybersecurity standards and practices across different nations presents a significant logistical hurdle.
Finally, the allocation of resources and responsibilities within international collaborations can lead to disagreements and friction.
Models of International Collaboration in Cybersecurity
Several models exist for international cybersecurity collaboration. Formal agreements, such as treaties or bilateral agreements, provide a strong legal framework but can be slow to negotiate and ratify. Informal cooperation, such as information sharing through existing channels, is faster but lacks the same level of legal certainty. Joint task forces or working groups can be established to address specific threats or challenges, offering a more flexible and targeted approach.
The choice of model depends on the specific context and objectives of the collaboration. For example, a joint task force might be ideal for responding to a specific cyberattack, while a formal treaty might be more appropriate for establishing long-term cooperation on cybersecurity standards.
Public Perception and Communication
The success of the EU’s proposed joint cyber unit hinges not only on its technical capabilities but also on public understanding and trust. Effective communication is crucial to ensure transparency, address concerns, and garner support for this vital initiative. Without public buy-in, the unit’s effectiveness will be significantly hampered. Building trust requires a proactive and multifaceted approach, demonstrating the unit’s commitment to protecting citizens and upholding democratic values.The EU must adopt a clear and consistent communication strategy to inform the public about the unit’s purpose, activities, and safeguards.
This involves explaining its role in preventing and responding to large-scale cyberattacks, emphasizing its commitment to respecting privacy and human rights, and highlighting the benefits of a coordinated European response to increasingly sophisticated cyber threats. Transparency regarding the unit’s operations, including its decision-making processes and accountability mechanisms, will be paramount in fostering public confidence.
Strategies for Building Public Trust, European union proposes joint cyber unit for large scale cyber attacks
Building public trust requires demonstrating competence, transparency, and accountability. The EU can achieve this by regularly publishing reports on the unit’s activities, including the number and nature of cyber threats addressed, the measures taken, and the results achieved. Independent audits of the unit’s operations could further enhance transparency and accountability. Engaging with civil society organizations, experts, and the public through consultations and public forums can also foster trust and ensure the unit’s actions align with public expectations and concerns.
Clear and accessible information about the unit’s legal framework, including data protection and privacy safeguards, is essential to address potential concerns.
Examples of Effective Communication Strategies
Several international organizations have successfully communicated complex technical issues to the public. For example, NATO’s communication strategies often focus on clear and concise messaging, emphasizing the organization’s role in protecting member states’ security. They utilize various channels, including social media, websites, and press releases, to reach diverse audiences. Similarly, the Cybersecurity and Infrastructure Security Agency (CISA) in the United States employs a proactive communication strategy, regularly issuing alerts and advisories about cyber threats, providing guidance on cybersecurity best practices, and engaging with the public through educational campaigns.
These organizations’ success stems from their commitment to clear, consistent, and accessible communication.
The EU’s proposal for a joint cyber unit to combat large-scale attacks is a crucial step, highlighting the need for robust, adaptable security systems. Building these systems requires efficient development, which is where advancements like those discussed in this article on domino app dev the low code and pro code future become incredibly relevant. Ultimately, effective cybersecurity relies on both strong defensive strategies and the agility to quickly implement and update those strategies – something low-code/no-code solutions can greatly facilitate in the face of evolving cyber threats.
Communication Plan Artikel
A comprehensive communication plan should define key messages, target audiences, and communication channels. Key messages should emphasize the unit’s role in protecting critical infrastructure, defending against cyberattacks, and safeguarding citizens’ data. Target audiences should include the general public, policymakers, businesses, and cybersecurity professionals. Communication channels should encompass a range of media, including traditional media outlets, social media platforms, websites, and educational materials.
Regular updates and feedback mechanisms will be vital to ensure the plan remains relevant and effective. The plan should also include a process for responding to criticism and addressing public concerns promptly and transparently. This proactive approach will build trust and ensure the unit’s long-term success.
Potential Impacts on National Sovereignty
The proposal for a joint EU cyber unit, while promising enhanced collective security against large-scale cyberattacks, inevitably raises questions about its potential impact on the national sovereignty of member states. Balancing the need for a unified response to increasingly sophisticated cyber threats with the preservation of individual nation-state autonomy is a complex challenge requiring careful consideration. The very act of pooling resources and decision-making power in a centralized unit necessitates a degree of relinquishment of control by individual nations.The creation of a joint cyber unit could be perceived as a shift in power dynamics within the EU, potentially leading to concerns about the erosion of national sovereignty in the realm of cybersecurity.
Member states might worry about a loss of control over their own critical infrastructure and data, particularly sensitive national security information. There’s a risk that the unit’s decisions, even if well-intentioned, could inadvertently conflict with national laws or policies, creating friction and potentially undermining national autonomy in the face of cyber threats.
Concerns Regarding the Balance Between Collective Security and National Autonomy
The core concern revolves around the delicate balance between the benefits of collective action in cybersecurity and the preservation of individual member states’ ability to independently manage their own digital security. A centralized unit, while offering economies of scale and potentially superior expertise, could inadvertently lead to a situation where individual nations feel their unique security needs and priorities are overlooked.
For example, a small member state might feel its specific vulnerabilities are not adequately addressed within the framework of a larger, more generalized strategy. This imbalance could lead to resentment and resistance towards the joint unit’s effectiveness.
Strategies for Mitigating Concerns About the Erosion of National Sovereignty
Several strategies can mitigate concerns about the erosion of national sovereignty. Firstly, establishing clear lines of responsibility and decision-making authority is crucial. This involves defining the precise mandate of the joint unit, specifying the circumstances under which it can intervene in national cybersecurity matters, and ensuring robust mechanisms for member states to voice their concerns and objections. Secondly, transparent and inclusive decision-making processes are essential.
Member states must have a meaningful say in the unit’s strategic direction, operational procedures, and resource allocation. Finally, robust oversight mechanisms, including independent audits and parliamentary scrutiny, can help build trust and ensure accountability.
Balancing Collective Action with Respect for National Interests
Achieving a balance between collective action and respect for national interests requires a nuanced approach that acknowledges the diverse security landscapes of EU member states. This involves designing the joint cyber unit with flexibility and adaptability in mind. The unit should be able to tailor its responses to the specific needs and circumstances of individual member states while maintaining a coordinated approach to major cyber threats.
This could involve establishing tiered levels of intervention, with the unit providing support and assistance to member states while allowing them to retain control over their own responses in less critical situations. Furthermore, mechanisms for dispute resolution and conflict management are essential to address potential disagreements between the unit and member states. For example, an independent arbitration panel could be established to resolve conflicts arising from the unit’s actions.
Ultimate Conclusion
The EU’s proposal for a joint cyber unit represents a significant step towards bolstering collective cybersecurity within the bloc. While the challenges are immense – from funding and resource allocation to navigating complex legal and ethical considerations – the potential benefits of a coordinated, unified response to large-scale cyberattacks are undeniable. The success of this initiative will depend on effective international cooperation, transparent communication with the public, and a careful balancing of collective security with the preservation of national sovereignty.
It’s a complex issue, and the debate is only just beginning.
Question Bank
What specific types of cyberattacks will this unit target?
The unit is likely to address a wide range, including large-scale DDoS attacks, sophisticated malware campaigns targeting critical infrastructure, and state-sponsored espionage operations.
How will the unit ensure data privacy and avoid overreach?
This is a key concern. The proposal will need to include robust oversight mechanisms and strict protocols to ensure compliance with data protection laws and prevent abuses of power.
What about smaller member states with limited cybersecurity resources?
The proposal needs to address resource allocation fairly. A potential solution could involve a tiered system where larger members provide support and expertise to smaller ones.
What is the timeline for implementation?
The timeline isn’t specified in the proposal yet. Implementation will likely involve extensive negotiations and approvals from various EU bodies and member states.