Expert Comments on Five Guys Data Breach
Expert comments on Five Guys data breach are all over the internet, and for good reason! This massive security incident highlighted the vulnerabilities within even seemingly secure organizations. We’ll dive into the expert analysis, exploring everything from the timeline of the breach and the types of data stolen to the potential long-term impacts on Five Guys and the broader fast-food industry.
Get ready for a deep-dive into the cybersecurity world and the lessons learned from this significant event.
This post will cover the specifics of the breach, including the suspected methods used by the attackers and a comparison to other similar incidents in the fast-food sector. We’ll examine the experts’ assessments of Five Guys’ response, both in terms of their communication and their mitigation efforts. Finally, we’ll discuss the long-term implications and provide actionable recommendations for businesses looking to improve their own cybersecurity posture.
The Scope of the Five Guys Data Breach
The Five Guys data breach, while not as widely publicized as some other large-scale incidents, serves as a stark reminder of the persistent vulnerability of even seemingly secure businesses to cyberattacks. Understanding the scope of this breach is crucial for businesses to learn from past mistakes and implement robust security measures. This analysis will delve into the timeline, compromised data, likely attack methods, and a comparison with similar breaches in the fast-food industry.
Timeline of the Five Guys Data Breach
The Five Guys data breach was discovered in March 2023, although the exact date remains undisclosed. The company announced the breach publicly on June 8, 2023, revealing that unauthorized access to their systems had occurred. This delay between discovery and public disclosure highlights the challenges companies face in investigating and assessing the full impact of a data breach before going public.
The length of the intrusion before discovery is also unknown, further complicating the assessment of the breach’s scope.
Types of Customer Data Compromised
The compromised data included customer names, payment card information (including card numbers, expiration dates, and CVV codes), and in some cases, driver’s license numbers. The exact number of affected customers remains undisclosed by Five Guys, contributing to the uncertainty surrounding the overall impact of the breach. The inclusion of sensitive personal data like driver’s license numbers significantly elevates the risk to affected individuals, increasing the potential for identity theft and fraud.
Suspected Attack Methods, Expert comments on five guys data breach
While Five Guys hasn’t publicly disclosed the specific methods used by the attackers, common attack vectors in similar breaches suggest several possibilities. These include malware infections, phishing campaigns targeting employees, or exploitation of vulnerabilities in Five Guys’ systems. The lack of transparency regarding the attack method hinders the ability to fully assess the company’s security posture and the effectiveness of its preventative measures.
Further investigation by independent security experts may shed light on these details.
Comparison with Other Fast-Food Restaurant Data Breaches
Several major fast-food chains have experienced significant data breaches in recent years. Comparing the Five Guys breach to these incidents provides valuable context. While precise figures for the Five Guys breach are unavailable, we can analyze the available data for other breaches to illustrate the potential impact.
| Company | Breach Size (Approximate) | Data Compromised | Response Time (Days from Discovery to Public Disclosure) | Financial Impact (Estimated) |
|---|---|---|---|---|
| Five Guys | Undisclosed | Names, Payment Card Information, Driver’s License Numbers (in some cases) | Undisclosed (but at least 78 days) | Undisclosed |
| Wendy’s (2016) | 1.1 Million | Payment card information | Undisclosed | Millions of dollars (including legal fees and remediation costs) |
| Sonic Drive-In (2017) | Over 7 Million | Payment card information, names, addresses, emails, and birthdates | Undisclosed | Millions of dollars (including legal fees and remediation costs) |
| Arby’s (2017) | Over 1.5 Million | Payment card information | Undisclosed | Millions of dollars (including legal fees and remediation costs) |
Expert Opinions on the Breach’s Causes

The Five Guys data breach, while not disclosing the exact nature of the attack, highlights critical vulnerabilities common in many organizations. Experts point to a confluence of factors likely contributing to the incident, underscoring the need for a multi-layered security approach. Understanding these causes is crucial for preventing similar breaches in the future.The attackers likely exploited several potential vulnerabilities.
These could include outdated or improperly configured software, weak or easily guessed passwords, phishing attacks targeting employees, or vulnerabilities in the point-of-sale (POS) systems themselves. The lack of robust multi-factor authentication (MFA) could have significantly weakened Five Guys’ defenses, making it easier for attackers to gain unauthorized access. Moreover, the possibility of unpatched software, leaving systems exposed to known exploits, cannot be ruled out.
A combination of these weaknesses likely provided a pathway for the attackers to infiltrate Five Guys’ systems.
Vulnerabilities Exploited
The attackers may have targeted known vulnerabilities in the POS systems used by Five Guys. Many POS systems, particularly older models, have a history of security flaws that can be exploited by malicious actors. These vulnerabilities could range from insecure network configurations to flaws in the software itself, allowing attackers to gain control of the system and access sensitive customer data.
Additionally, the use of outdated operating systems and applications on POS terminals would significantly increase the risk of successful attacks. A failure to regularly update and patch these systems would create significant vulnerabilities.
Role of Security Protocols
The absence or inadequacy of robust security protocols played a significant role in the breach. A lack of strong password policies, insufficient employee training on cybersecurity best practices, and the absence of comprehensive security monitoring and incident response plans likely contributed to the attackers’ success. Without real-time monitoring, anomalies in system activity might have gone unnoticed, allowing the attackers to operate undetected for an extended period.
Furthermore, a lack of proper data encryption both in transit and at rest would have made sensitive customer information readily available if accessed.
Best Practices to Prevent Future Breaches
Implementing robust security measures is paramount. Five Guys could have benefited from implementing a comprehensive security information and event management (SIEM) system to monitor network activity and detect suspicious behavior in real-time. Regular security audits and penetration testing would have identified potential vulnerabilities before they could be exploited. The adoption of a strong multi-factor authentication (MFA) system would have made it significantly harder for attackers to gain unauthorized access.
Furthermore, regularly updating software and patching known vulnerabilities is crucial for minimizing the attack surface. Investing in advanced threat detection technologies would have provided an additional layer of protection.
Importance of Employee Training
Employee training in data security is often overlooked but is critical. Employees are frequently the weakest link in any security system. Phishing attacks, social engineering, and other techniques can easily compromise even the most robust security measures if employees are not adequately trained to identify and report suspicious activities. Comprehensive training programs should cover topics such as password security, phishing awareness, data handling procedures, and the importance of reporting suspicious emails or websites.
Regular security awareness training, including simulated phishing attacks, can effectively reinforce these crucial security practices. This proactive approach is essential in mitigating the human element in data breaches.
Expert Assessment of Five Guys’ Response: Expert Comments On Five Guys Data Breach
Five Guys’ response to the 2023 data breach, while not perfect, offers valuable lessons in crisis communication and data breach mitigation. Analyzing their actions against industry best practices reveals areas of strength and significant room for improvement. A thorough examination of their communication strategies, mitigation efforts, and overall response is crucial for understanding how to better protect customer data in the future.
The initial response from Five Guys was characterized by a delay in public notification, a factor that significantly impacted public perception and trust. While they eventually issued statements, the timing and clarity of these communications were criticized by cybersecurity experts and consumer advocates. This delayed response allowed the news to spread through unofficial channels, leading to a more chaotic and damaging narrative than a proactive, transparent approach would have likely generated.
Five Guys’ Communication with Customers and Regulatory Bodies
Five Guys’ communication efforts were notably reactive rather than proactive. The company’s initial silence amplified concerns, and subsequent statements lacked detailed information regarding the scope of the breach and the steps taken to address it. This contrasted sharply with the more transparent and timely communications often seen from companies that have proactively prepared for such events. Their communication with regulatory bodies, while ultimately compliant, could have benefited from earlier and more comprehensive engagement.
A more proactive approach, involving earlier notification and consistent updates, would have mitigated public distrust and demonstrated a commitment to accountability.
Mitigation Efforts and Data Protection Measures
Following the breach, Five Guys implemented various measures to mitigate further damage and protect customer data. These included working with cybersecurity experts to investigate the breach, enhance their security systems, and implement additional safeguards. However, the specifics of these measures were not widely publicized, leaving customers with unanswered questions. While they likely followed internal protocols, the lack of transparency undermined public confidence.
Examples of what might have been included are detailed explanations of system upgrades, improved monitoring protocols, and employee retraining programs. This opacity contrasts with companies like Capital One, which, while facing a similar situation, offered a more comprehensive public account of their mitigation efforts.
Reading expert comments on the Five Guys data breach really highlighted the urgent need for robust security measures. It made me think about how crucial proactive solutions are, and learning more about bitglass and the rise of cloud security posture management seems incredibly relevant. Ultimately, preventing breaches like the one at Five Guys requires a multi-layered approach, and that includes strong cloud security.
Comparison to Industry Best Practices
Five Guys’ response fell short of industry best practices in several key areas. Leading organizations typically prioritize immediate and transparent communication with customers and regulatory bodies. They provide detailed information about the breach, the affected data, and the steps taken to remediate the situation. Companies like Okta, for example, have demonstrated a commitment to rapid communication and proactive engagement with stakeholders.
Five Guys’ slower response and limited transparency led to negative publicity and damaged customer trust. This underscores the importance of proactive planning and preparation for data breaches, including the development of comprehensive communication protocols.
Hypothetical Improved Communication Strategy
An improved communication strategy for Five Guys would involve immediate and transparent disclosure of the breach upon confirmation. This would include a detailed explanation of the incident, the types of data affected, and the steps being taken to mitigate the damage. Regular updates should be provided to customers and regulatory bodies, ensuring clear, concise, and empathetic communication. Furthermore, a dedicated website and customer support channels should be established to address customer concerns and provide assistance.
This proactive approach, modeled on the crisis communications of companies like T-Mobile, which consistently updated the public during their data breaches, would have significantly improved public perception and fostered greater trust.
Long-Term Implications and Recommendations

The Five Guys data breach, while seemingly contained, carries significant long-term consequences for the company. Its impact extends beyond immediate financial losses and customer service disruptions, potentially shaping its future trajectory and influencing industry best practices. Understanding these implications and implementing robust preventative measures are crucial for Five Guys and other businesses in the fast-food sector.
Reading expert comments on the Five Guys data breach really highlights the importance of robust security systems. It makes you think about how much easier it would be to build and maintain those systems if developers utilized modern tools like those discussed in this insightful article on domino app dev, the low-code and pro-code future. Ultimately, preventing future breaches requires a blend of strong security practices and efficient development processes, as evidenced by the ongoing fallout from the Five Guys incident.
Financial and Reputational Impacts
The financial ramifications of the breach are multifaceted. Direct costs include incident response, legal fees, potential fines from regulatory bodies, and the cost of credit monitoring services offered to affected customers. Indirect costs could be far more substantial, encompassing lost customer trust, decreased sales due to negative publicity, and increased difficulty attracting and retaining both customers and employees.
Reputational damage can be particularly persistent, impacting future expansion plans and investor confidence. For instance, consider the long-term struggles faced by companies like Equifax after their significant data breach; regaining full customer trust took years, even with substantial efforts. The Five Guys brand, known for its focus on quality and customer experience, needs to address this reputational risk proactively.
Legal and Regulatory Ramifications
Five Guys faces potential legal challenges from multiple fronts. Class-action lawsuits from affected customers are highly likely, alleging negligence and financial damages. Furthermore, depending on the location of the breach and the specifics of data handling practices, Five Guys could face penalties from various regulatory bodies, including the FTC (Federal Trade Commission) in the US, and potentially similar agencies in other countries where it operates.
These penalties can range from hefty fines to mandatory security improvements, impacting both the company’s finances and operational procedures. The severity of these ramifications depends on factors such as the extent of the data compromised, the adequacy of Five Guys’ security measures, and the speed and transparency of their response.
Recommendations for Cybersecurity Improvement
Strengthening Five Guys’ cybersecurity infrastructure requires a multi-pronged approach. This involves investing in robust endpoint detection and response (EDR) systems to proactively identify and mitigate threats. Implementing a comprehensive security information and event management (SIEM) system is crucial for centralizing security logs and detecting anomalies. Furthermore, employee training on cybersecurity awareness is essential to prevent phishing attacks and other social engineering techniques.
Regular penetration testing and vulnerability assessments should be conducted to identify and address weaknesses in the system before they can be exploited. Finally, adopting a zero-trust security model, which verifies every user and device before granting access, would significantly enhance security posture. Failure to implement these measures increases the risk of future breaches and escalating financial and legal repercussions.
Key Takeaways for the Fast-Food Industry
The Five Guys breach serves as a stark reminder of the vulnerabilities faced by businesses, even those seemingly less susceptible to cyberattacks. The following key takeaways should guide other fast-food companies:
- Strengthen data encryption: Employ strong encryption both in transit and at rest to protect sensitive customer data.
- Implement multi-factor authentication: Require multiple forms of authentication for all access points to reduce the risk of unauthorized access.
- Conduct regular security audits: Regularly assess vulnerabilities and update security protocols to stay ahead of evolving threats.
- Invest in employee training: Educate employees about cybersecurity best practices and the importance of recognizing and reporting suspicious activity.
- Develop an incident response plan: Create a comprehensive plan for handling data breaches, including communication strategies and procedures for minimizing damage.
- Comply with relevant data privacy regulations: Stay informed about and adhere to all applicable regulations like GDPR, CCPA, etc. to avoid penalties.
The Role of Third-Party Vendors
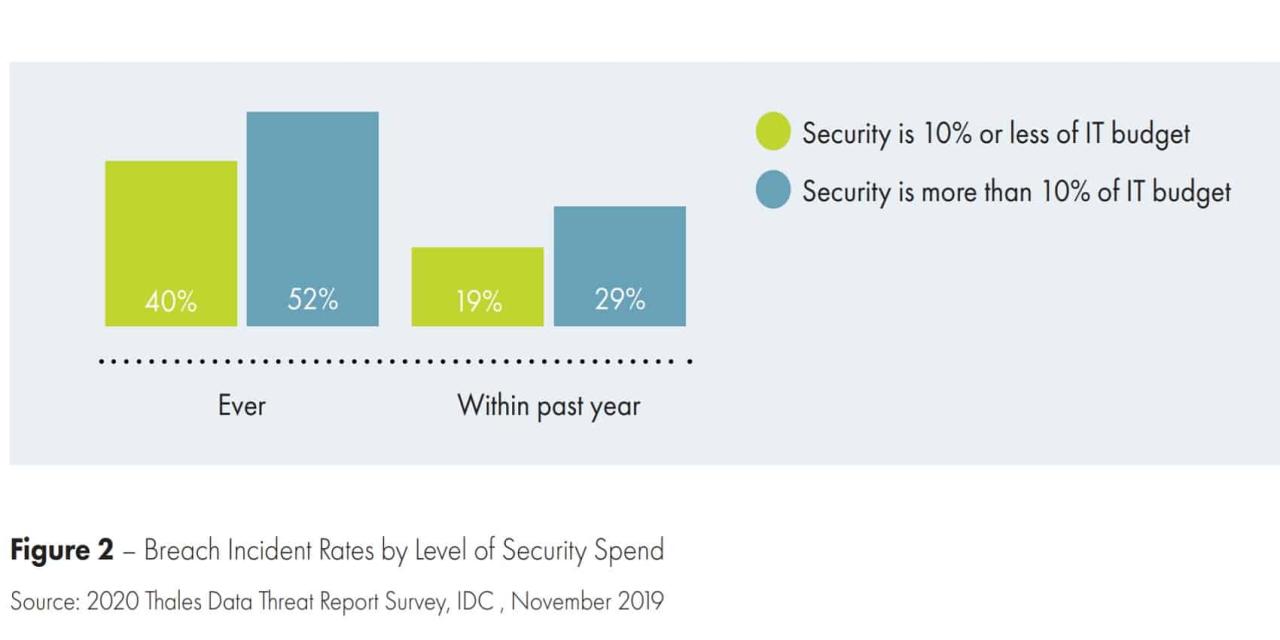
The Five Guys data breach highlights the critical role third-party vendors play in maintaining overall data security. A company’s reliance on external providers for various services, from payment processing to IT infrastructure, inherently expands its attack surface. Understanding the responsibilities and potential liabilities associated with these relationships is crucial for preventing future breaches.The involvement of third-party vendors in the Five Guys breach, while not explicitly detailed in public reports, is a strong possibility.
Many large restaurant chains utilize various vendors for point-of-sale (POS) systems, payment processing, and data storage. A compromise in any of these areas could have facilitated the breach. It’s important to note that even with robust internal security measures, a weak link in a third-party’s system can compromise the entire chain.
Vendor Responsibility and Due Diligence
Five Guys, like any company utilizing third-party vendors, bears the responsibility of ensuring those vendors maintain adequate security measures. This includes rigorous vetting processes before engaging a vendor, ongoing monitoring of their security practices, and clear contractual obligations regarding data protection. Failure to exercise due diligence in selecting and managing vendors can lead to significant legal and financial repercussions, beyond the immediate costs of a data breach.
A robust vendor management program is not a “nice-to-have” but a critical component of a comprehensive security strategy.
A Secure Vendor Management Process
A secure vendor management process involves several key steps. First, a thorough risk assessment should be conducted for each potential vendor, considering factors such as their security certifications (e.g., ISO 27001), past security incidents, and the sensitivity of the data they will handle. This is followed by a detailed review of their security policies and procedures, including incident response plans.
Contracts should explicitly Artikel security responsibilities, including data breach notification procedures and liability clauses. Ongoing monitoring and audits of vendor security practices are crucial to ensure continued compliance and identify potential vulnerabilities. Regular security assessments by independent third-party security firms can provide an objective evaluation of vendor security posture. Finally, a formal process for terminating vendor relationships should be in place, to ensure a smooth and secure transition of data and services.
This multi-layered approach minimizes the risk of a vendor compromise impacting the organization.
Epilogue
The Five Guys data breach serves as a stark reminder of the ever-present threat of cyberattacks, even for established companies. Expert opinions underscore the critical need for robust security protocols, employee training, and proactive vendor management. While the immediate fallout of the breach is significant, the lasting impact will depend on Five Guys’ ability to learn from this experience and implement lasting changes to their cybersecurity infrastructure.
The key takeaway for all businesses is simple: proactive security is not an expense, but an investment in your future.
Questions Often Asked
What types of data were compromised in the Five Guys breach?
Reports suggest that the breach compromised customer payment card information, including credit and debit card numbers, expiration dates, and CVV codes. Potentially, other personal information was also compromised, but the exact scope varies depending on the source.
What was Five Guys’ financial impact from the breach?
The exact financial impact is not publicly available. However, it likely involved significant costs related to investigation, remediation, legal fees, and potential fines and settlements.
How long did it take Five Guys to discover and respond to the breach?
The exact timeline isn’t fully public, but reports indicate a delay between the discovery of the breach and public disclosure. This delay is a significant factor in the expert assessments.
What legal ramifications could Five Guys face?
Five Guys faces potential legal action from affected customers, as well as investigations and penalties from regulatory bodies such as the FTC and state attorneys general. The severity of these ramifications will depend on the details of the breach and their response.





