Exploring SASE & SSE Roadmaps with AI and Quantum
Exploring sase and sse roadmaps with the two taylor swifts of the decade ai and quantum – Exploring SASE and SSE roadmaps with the two Taylor Swifts of the decade, AI and quantum computing, is like charting a course through uncharted technological waters. These cutting-edge technologies are poised to revolutionize how we approach network security and performance. Imagine a world where AI anticipates and neutralizes threats before they even materialize, and quantum computing provides an impenetrable shield against future attacks.
This journey delves into the core functionalities of SASE (Secure Access Service Edge) and SSE (Secure Service Edge), comparing their architectures and exploring how AI and quantum computing will shape their future.
We’ll unpack the ways AI enhances security, from threat detection to performance optimization, within both SASE and SSE frameworks. Then, we’ll confront the potential impact of quantum computing—the challenges it presents to current cryptographic methods and the innovative solutions being developed to mitigate these risks. Finally, we’ll explore the exciting possibilities of integrating AI and quantum computing, envisioning a future where these technologies work in synergy to create truly impenetrable and efficient security systems.
Get ready for a wild ride!
Introduction to SASE and SSE
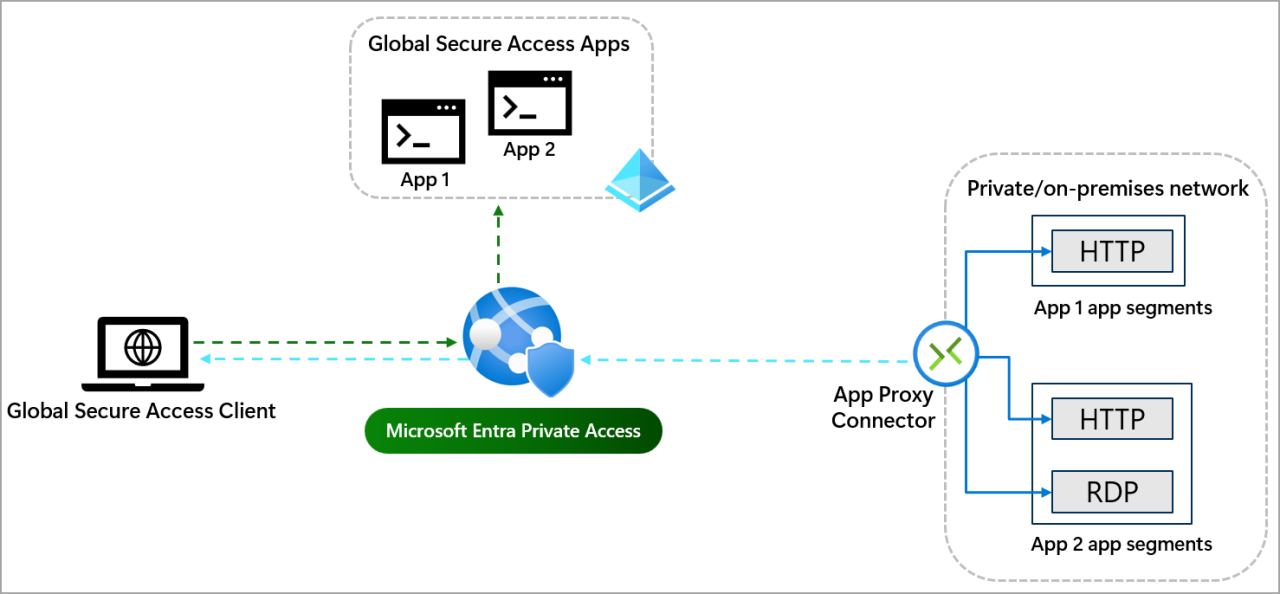
The convergence of cloud adoption, remote work, and increasingly sophisticated cyber threats has driven the need for innovative security architectures. Secure Access Service Edge (SASE) and Secure Service Edge (SSE) represent two key advancements in this area, offering integrated security and networking capabilities to protect modern, distributed enterprises. While closely related, they possess distinct focuses and implementations. This exploration will delve into the core functionalities of each, comparing and contrasting their approaches to secure access and service delivery.
SASE Core Functionalities
SASE, a holistic security architecture, integrates network and security functions into a cloud-delivered service. Its core functionalities revolve around providing secure access to applications and data regardless of user location or device. Key features include secure web gateways (SWG), cloud access security brokers (CASB), zero trust network access (ZTNA), firewall as a service (FWaaS), and secure web gateway (SWG).
These components work in concert to inspect traffic, enforce policies, and protect users and data across various environments. The inherent scalability and agility of a cloud-based architecture are central to SASE’s effectiveness.
SSE Key Components
SSE, a subset of SASE, focuses specifically on securing access to cloud services and applications. It builds upon the principles of SASE but concentrates on the security aspects of the service layer. Key components include secure web gateways (SWG), CASB, and data loss prevention (DLP) capabilities. SSE solutions often leverage advanced threat protection techniques, such as machine learning and AI, to identify and mitigate sophisticated threats targeting cloud resources.
The emphasis is on ensuring secure access and data protection for cloud-based applications and services, irrespective of the user’s location or device.
SASE and SSE Architecture Comparison
SASE provides a comprehensive, integrated security and networking solution covering the entire access path, from user to application. SSE, on the other hand, focuses specifically on securing the access to and use of cloud services. While SSE is a component of a full SASE implementation, SASE encompasses a broader range of network and security services beyond those directly addressed by SSE.
The overlap lies primarily in the shared security services like SWG and CASB. The key difference lies in scope: SASE is holistic, while SSE is focused on the service edge.
SASE and SSE Feature Comparison
| Vendor | Feature | SASE Implementation | SSE Implementation |
|---|---|---|---|
| Example Vendor A | Secure Web Gateway (SWG) | Integrated into the overall SASE platform | Standalone or integrated into a broader SSE platform |
| Example Vendor B | Cloud Access Security Broker (CASB) | Integrated with other SASE components | Provides security for cloud services and data |
| Example Vendor C | Zero Trust Network Access (ZTNA) | Essential component for secure access | May be integrated for enhanced security |
| Example Vendor D | Firewall as a Service (FWaaS) | Provides network-level security | Generally not a primary SSE function |
| Example Vendor E | Data Loss Prevention (DLP) | Integrated for comprehensive data protection | Crucial for preventing data breaches in cloud environments |
The Role of AI in SASE/SSE Roadmaps
The convergence of AI and SASE/SSE is rapidly reshaping the cybersecurity landscape. AI’s ability to process vast amounts of data and identify complex patterns makes it an invaluable tool for enhancing security, optimizing performance, and ultimately, simplifying the management of these increasingly complex architectures. This isn’t just about incremental improvements; it’s about fundamentally changing how we approach security in the cloud-first world.AI enhances security in SASE architectures by providing a level of automation and intelligence previously unattainable.
Traditional security methods often struggle to keep pace with the ever-evolving threat landscape. AI, however, can adapt and learn, constantly refining its defenses based on new data and emerging threats. This proactive approach significantly reduces the risk of successful attacks.
AI-Driven Threat Detection and Prevention in SSE Frameworks
AI significantly improves threat detection and prevention within Secure Service Edge (SSE) frameworks. By analyzing network traffic, user behavior, and application data in real-time, AI algorithms can identify anomalies indicative of malicious activity far more effectively than rule-based systems. This includes detecting sophisticated attacks like zero-day exploits and advanced persistent threats (APTs) that often evade traditional signature-based detection.
For example, an AI system might detect unusual login attempts from an unexpected geographic location or identify subtle patterns in network traffic that suggest a data exfiltration attempt. This proactive identification allows for immediate mitigation, minimizing the impact of potential breaches.
AI Applications in Optimizing SASE/SSE Performance
AI plays a crucial role in optimizing the performance of SASE and SSE architectures. By analyzing network traffic patterns and user behavior, AI can intelligently route traffic, optimize bandwidth usage, and predict potential bottlenecks. This leads to improved application performance, reduced latency, and a better user experience. For instance, AI can dynamically adjust network configurations based on real-time demand, ensuring optimal performance during peak usage periods.
Furthermore, AI can predict potential outages or performance degradations, allowing for proactive intervention and preventing disruptions. This predictive capability is particularly valuable in complex, geographically distributed environments.
Hypothetical AI-Powered Security System for a SASE/SSE Environment
Imagine a SASE/SSE environment protected by an AI-powered security system called “Sentinel.” Sentinel continuously monitors all network traffic, user activity, and application data, leveraging machine learning algorithms to identify and respond to threats in real-time. Its core functionalities include: (1) Advanced Threat Detection: Sentinel uses anomaly detection and behavioral analysis to identify malicious activity, including zero-day exploits and APTs.
(2) Automated Response: Upon detecting a threat, Sentinel automatically implements appropriate mitigation strategies, such as blocking malicious traffic, quarantining infected devices, or alerting security personnel. (3) Predictive Security: Sentinel analyzes historical data and current trends to predict potential threats and proactively implement preventative measures. (4) Adaptive Security Policies: Sentinel dynamically adjusts security policies based on real-time threat intelligence and user behavior, ensuring optimal protection while minimizing disruption.
The benefits of such a system include enhanced security posture, reduced response times to security incidents, improved operational efficiency, and a significant reduction in the overall risk of security breaches. This hypothetical system mirrors real-world advancements already being integrated into commercial SASE/SSE solutions.
Quantum Computing’s Potential Impact
The advent of quantum computing presents both exciting opportunities and significant challenges for the security and performance of SASE and SSE architectures. While still in its nascent stages, the potential power of quantum computers to break current encryption methods necessitates a proactive approach to mitigating future risks and leveraging its unique capabilities for enhanced security and efficiency.Quantum computers leverage quantum mechanics to perform calculations in ways fundamentally different from classical computers.
This allows them to tackle problems currently intractable for even the most powerful supercomputers, including breaking many of the widely used public-key cryptographic algorithms that underpin the security of SASE and SSE.
Quantum Computing’s Threat to Current Cryptography
The most immediate concern is the vulnerability of widely used asymmetric encryption algorithms like RSA and ECC to attacks from sufficiently powerful quantum computers. These algorithms are foundational to many SASE/SSE security features, including secure communication channels, authentication, and data integrity checks. Algorithms like Shor’s algorithm demonstrate the theoretical capability of a sufficiently advanced quantum computer to efficiently factor large numbers (crucial to breaking RSA) and solve the discrete logarithm problem (underlying ECC), rendering these currently secure methods obsolete.
This would compromise the confidentiality and integrity of sensitive data transmitted and processed within the SASE/SSE framework. For example, a quantum computer could decrypt VPN traffic secured with RSA, exposing sensitive business information or personal data.
Mitigation Strategies and Post-Quantum Cryptography
Addressing this threat requires a multi-pronged approach focusing on the transition to post-quantum cryptography (PQC). PQC encompasses cryptographic algorithms designed to be resistant to attacks from both classical and quantum computers. Standardization efforts are underway to identify and implement these algorithms, including lattice-based, code-based, multivariate, and hash-based cryptography. Implementing PQC involves upgrading cryptographic libraries, updating protocols, and potentially redesigning existing security infrastructure.
This transition will require careful planning and significant investment to ensure a smooth and secure migration. For instance, organizations could begin pilot programs to test and integrate PQC algorithms into their SASE/SSE systems, gradually phasing out vulnerable algorithms.
Quantum Computing’s Potential Benefits for SASE/SSE
Beyond the threat, quantum computing also offers exciting possibilities for enhancing SASE/SSE. Its inherent parallelism and ability to perform complex computations could revolutionize areas like threat detection and response. For example, quantum machine learning algorithms could analyze vast amounts of network traffic data far more efficiently than classical algorithms, identifying subtle patterns indicative of sophisticated cyberattacks. Furthermore, quantum key distribution (QKD) offers the potential for unconditionally secure communication, leveraging the principles of quantum mechanics to guarantee the secrecy of communication keys.
While still facing technological hurdles, QKD could be integrated into SASE/SSE to establish secure communication channels impervious to even quantum computer attacks. This would represent a paradigm shift in network security, providing an unparalleled level of protection.
Integrating AI and Quantum Computing
The convergence of artificial intelligence (AI) and quantum computing presents a transformative opportunity for enhancing the security of SASE/SSE architectures. While both technologies offer unique strengths, their combined power promises a new level of sophistication in threat detection, response, and overall system resilience. This integration is crucial given the ever-evolving landscape of cyber threats, many of which are becoming increasingly sophisticated and difficult to combat with traditional methods.AI and quantum computing offer distinct advantages and disadvantages in securing SASE/SSE.
AI excels at pattern recognition, anomaly detection, and predictive analysis, allowing for proactive security measures. However, its reliance on classical computing limits its ability to handle certain complex cryptographic challenges. Quantum computing, on the other hand, possesses the potential to break widely used encryption algorithms, posing a significant threat but simultaneously offering the power to create unbreakable encryption.
The challenge lies in harnessing these contrasting capabilities synergistically.
AI Management of Quantum Computing Resources in SASE/SSE
AI can play a crucial role in managing and optimizing the use of quantum computing resources within a SASE/SSE framework. This includes tasks such as resource allocation, scheduling quantum computations for cryptographic key generation and management, and monitoring the performance and security of quantum components. For instance, an AI system could dynamically allocate quantum processing units (QPUs) based on the urgency and complexity of security tasks, ensuring efficient utilization of these potentially expensive resources.
Furthermore, AI algorithms could be used to detect and mitigate potential errors or vulnerabilities within the quantum computing infrastructure, enhancing overall system stability and security. Imagine an AI system predicting potential QPU failures and automatically rerouting tasks to prevent service disruptions. This proactive management is crucial for the successful integration of quantum computing into SASE/SSE.
Hypothetical Research Agenda: Synergistic AI and Quantum Computing for SASE/SSE Security
A focused research agenda should explore several key areas to unlock the full potential of this synergistic approach. This agenda should prioritize:
- Developing AI-driven algorithms for optimizing quantum key distribution (QKD) protocols within SASE/SSE environments. This includes exploring adaptive QKD strategies that respond dynamically to changing network conditions and threat landscapes.
- Creating AI-powered anomaly detection systems capable of identifying subtle patterns indicative of quantum-based attacks. This requires training AI models on datasets that include both classical and quantum attack signatures.
- Investigating the use of quantum machine learning algorithms for enhancing threat intelligence and predictive security analytics. Quantum machine learning algorithms could potentially offer significant speedups in analyzing vast amounts of security data.
- Designing robust and secure mechanisms for managing and controlling access to quantum computing resources within a SASE/SSE framework. This involves addressing issues such as authentication, authorization, and data encryption for quantum computations.
This research should involve close collaboration between computer scientists, cryptographers, and security experts, fostering the development of practical and secure solutions. Success will depend on a robust understanding of both AI and quantum computing principles, and their interplay within a real-world security context.
Illustrative Flowchart: AI and Quantum Computing Interaction in Future SASE/SSE Architecture
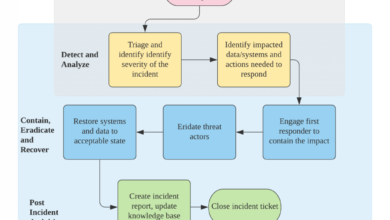
Imagine a flowchart depicting the interaction. The flowchart would begin with a security event (e.g., a suspicious network activity detected by AI). This event triggers an AI-driven risk assessment. If the risk is high and requires the computational power beyond classical computing, the AI system would then initiate a quantum computation (e.g., for advanced encryption or decryption). The results of this quantum computation are then fed back to the AI system for further analysis and decision-making, leading to an appropriate security response (e.g., blocking malicious traffic, generating a new encryption key).
The AI system continuously monitors the quantum computing resources, optimizing their usage and ensuring system stability. This dynamic interplay between AI and quantum computing ensures a robust and adaptable security posture within the SASE/SSE framework. The flowchart would visually represent this continuous feedback loop, illustrating the synergistic nature of the two technologies.
Future Trends and Predictions for SASE/SSE: Exploring Sase And Sse Roadmaps With The Two Taylor Swifts Of The Decade Ai And Quantum
The convergence of AI and quantum computing is poised to revolutionize SASE and SSE architectures in the coming years, leading to more secure, efficient, and intelligent network solutions. We’re on the cusp of a significant shift, moving beyond reactive security measures to proactive, predictive systems that anticipate and neutralize threats before they can even materialize. This evolution will be driven by the increasing sophistication of cyberattacks and the growing demand for seamless, secure access to applications and data across increasingly distributed environments.The next five years will witness a dramatic increase in the adoption and sophistication of AI-driven features within SASE/SSE.
We can expect to see a shift from rule-based systems to AI-powered systems capable of autonomously identifying and responding to threats with minimal human intervention. This will include advancements in anomaly detection, threat prediction, and automated remediation. The integration of quantum computing, while still in its early stages, promises to further enhance these capabilities by enabling the processing of exponentially larger datasets and the breaking of currently unbreakable encryption algorithms.
This will necessitate the development of new, quantum-resistant cryptographic methods, which will themselves become integral components of future SASE/SSE solutions.
AI-Driven Automation and Orchestration, Exploring sase and sse roadmaps with the two taylor swifts of the decade ai and quantum
AI will significantly enhance automation and orchestration within SASE/SSE. For example, we’ll see AI-powered systems dynamically adjusting security policies based on real-time threat intelligence and network conditions. This will lead to a self-healing network that automatically adapts to changing circumstances, minimizing downtime and improving overall security posture. Imagine a system that automatically reroutes traffic around a detected DDoS attack, adjusts bandwidth allocation based on user demand, and proactively patches vulnerabilities before they can be exploited – all without human intervention.
So, I’ve been deep diving into SASE and SSE roadmaps, trying to wrap my head around how AI and quantum computing – the two Taylor Swifts of this decade, in my opinion – will reshape them. This got me thinking about how these advancements will impact app development, and I stumbled upon this fascinating article on domino app dev the low code and pro code future , which really highlights the changing landscape.
It’s all connected, you see; faster app development directly influences how quickly we can implement and adapt SASE/SSE strategies in this rapidly evolving tech world.
This level of automation will be crucial for managing the complexity of increasingly distributed and dynamic networks.
Quantum-Resistant Cryptography and Enhanced Security
The integration of quantum-resistant cryptographic algorithms will be paramount. As quantum computers become more powerful, existing encryption methods will become vulnerable. SASE/SSE solutions will need to incorporate post-quantum cryptography (PQC) to protect sensitive data and communications. This will involve a significant shift in infrastructure and require collaboration across the industry to standardize and deploy these new algorithms. We might see the emergence of hybrid cryptographic systems that combine classical and quantum-resistant methods for enhanced security.
The transition to PQC will be a multi-year process, but its implementation within SASE/SSE is crucial for long-term security.
Predictive Threat Intelligence and Proactive Security
AI-powered threat intelligence platforms will become even more sophisticated, moving beyond reactive analysis to predictive capabilities. These systems will analyze vast amounts of data to identify potential threats before they occur, allowing for proactive mitigation strategies. This will involve the use of machine learning models to predict attack vectors, identify vulnerable systems, and prioritize security resources. For instance, a system might predict a phishing campaign targeting a specific organization based on historical data and current trends, allowing for preemptive measures such as employee training or enhanced email filtering.
Societal and Economic Implications of Advanced SASE/SSE
Widespread adoption of advanced SASE/SSE systems will have profound societal and economic impacts. Improved cybersecurity will lead to increased trust in digital services and transactions, fostering economic growth and innovation. Reduced downtime and improved operational efficiency will benefit businesses of all sizes. However, the transition will also require significant investments in infrastructure, training, and skilled personnel. The potential for job displacement in certain areas due to automation should also be addressed through reskilling and upskilling initiatives.
Increased security will also benefit society by protecting critical infrastructure and sensitive data from cyberattacks.
Skills and Expertise for Future SASE/SSE Professionals
Professionals working with future AI and quantum-enhanced SASE/SSE systems will need a diverse skillset. This will include expertise in network security, cloud computing, AI/ML, quantum computing, and cryptography. Strong analytical and problem-solving skills will be crucial for interpreting data and responding to complex security threats. Collaboration and communication skills will also be essential for working effectively within multidisciplinary teams.
Furthermore, professionals will need to stay abreast of the rapidly evolving technological landscape through continuous learning and professional development. The demand for specialists with this unique combination of skills will likely grow significantly in the coming years.
Ultimate Conclusion

The convergence of SASE/SSE, AI, and quantum computing represents a paradigm shift in cybersecurity. While challenges exist, the potential benefits—enhanced security, improved performance, and proactive threat mitigation—are immense. The future of network security isn’t just about reacting to threats; it’s about anticipating and preventing them. By embracing the power of AI and preparing for the quantum era, we can build a more secure and resilient digital world.
The journey ahead is filled with innovation, and the rewards for those who navigate these technological currents wisely will be significant.
Detailed FAQs
What is the main difference between SASE and SSE?
While both improve security, SASE is a comprehensive, cloud-delivered security architecture, whereas SSE focuses specifically on security services in the cloud.
How does AI improve SASE/SSE performance?
AI optimizes resource allocation, predicts and prevents bottlenecks, and personalizes security policies for improved efficiency.
What are the biggest risks posed by quantum computing to current SASE/SSE security?
Quantum computers could break current encryption algorithms, rendering existing security measures ineffective.
What are some potential solutions to quantum computing threats?
Post-quantum cryptography, improved key management, and AI-driven anomaly detection are potential solutions.